Follow the given instructions to get started:
- EAP-TTLS is also enabled by default in
eap.conf. Let us start the Radius server and monitor the log file: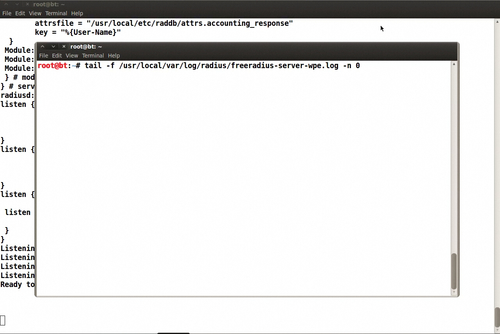
- We connect the client and enter the credentials SecurityTube as the Username and demo12345 as the Password:
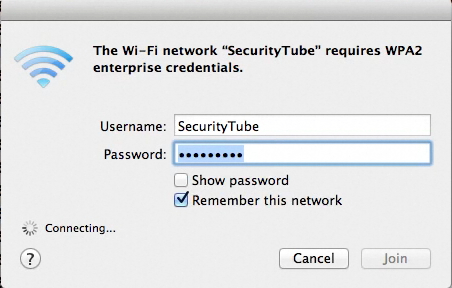
- Immediately, the
MSCHAP-v2challenge / response appears in the log file: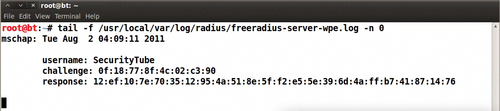
- We again use Asleap to crack the password used. It is important to note that any password list you use, must contain the password used by the user. In order to illustrate that if this is not true, we will not be able to crack the password, we have deliberately ensured that the password is not there in the default list on BackTrack:

..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
