Chapter 4 Common Botnets
Introduction
According to the Web@Work Survey conducted in early 2006 by the Computer Crime Research Center, “Only 34 percent of IT decision makers said they are very or extremely confident that they can prevent bots from infecting employees’ PCs when not connected to the corporate network. Furthermore, 19 percent of IT decision makers indicated that they have had employees’ work-owned computers or laptops infected with a bot.”
With bots emerging as possibly the biggest threat to Internet and Web security, numbers like these are of grave concern. Botherders or botmasters can typically amass an army of 10,000 to 100,000 compromised machines with which to do their malicious bidding. It is estimated that as many as 100 million machines on the Internet are compromised, and botnets of up to 350,000 or more have been detected.
Some of the more common bots just continue to evolve. In fact, rather than new bots being developed from scratch, it seems that malicious developers almost exclusively adapt or modify an existing bot program into a new variant. Some bots, such as SDBot, have hundreds of variants and make the standard antivirus-naming convention of using the alphabet (variant A, variant B, etc.) cumbersome at best.
The bots covered in this chapter are the most common, but this list is by no means comprehensive. Because they are common, they also have many variants. Some have hundreds of variations. Understand that the information covered in this chapter is generic to some degree and that you might have to do research to find details of the specific variant that has compromised your system.
SDBot
The SDBot family of bots has been around for almost five years and has grown to include hundreds of variants and offshoots. One of the elements that has added to the longevity of the SDBot family is that the original developer essentially made it into an open-source malware program. The original SDBot author released the source code for the bot and included his contact information, providing a means of public collaboration and evolution to continue developing and improving the code.
The other key to the success of SDBot is poor security on the compromised systems. SDBot relies on spreading itself primarily via network shares using blank or common passwords. Systems with solid security and more complex passwords will not be compromised by SDBot.
With so many variants, a comprehensive description of each would require a book of its own. The following are the general details of how SDBot works and propagates and how you can recognize common signs that could indicate that your computer has been compromised by SDBot.
Aliases
Antivirus and security vendors rarely agree on naming conventions, so the same threat can have multiple names, depending on which vendor is supplying the information. Here are some aliases for SDBot from the top antivirus vendors:
Infection
The method of infection varies from one variant to the next, but SDBot traditionally takes advantage of insecure network shares or uses known vulnerability exploits to compromise systems. Once SDBot is able to connect to a vulnerable system, it will execute a script that will download and execute SDBot to infect the system.
SDBot typically includes some sort of backdoor that allows an attacker to gain complete access to compromised systems. The Remote Access Trojan (RAT) component of SDBot connects to an IRC server and lies silently waiting for instructions from a botherder.
Using the RAT, a botherder can collect information about the compromised system, such as the operating system version, computer name, IP address, or the currently logged-in username. A botherder can also run IRC commands directing the compromised computer to join an IRC channel, download and execute files, or connect to a specific server or Web site to initiate a distributed denial-of-service (DDoS) attack.
Signs of Compromise
If you believe that your computer might be infected with SDBot, there are a few clues you can look for to verify your suspicions.
System Folder
Upon execution, SDBot will place a copy of itself in the System folder. Typically, this folder is C:WindowsSystem32, but SDBot uses the %System% variable to find out where it is and then places a copy of itself in that folder. The filename used can vary, but Table 4.1 contains a list of known filenames.
Table 4.1 Known Filenames Used by Backdoor*
| Aim95.exe | service.exe |
| CMagesta.exe | sock32.exe |
| Cmd32.exe | spooler.exe |
| Cnfgldr.exe | Svchosts.exe |
| cthelp.exe | svhost.exe |
| Explorer.exe | Sys32.exe |
| FB_PNU.EXE | Sys3f2.exe |
| IEXPL0RE.EXE | Syscfg32.exe |
| iexplore.exe | Sysmon16.exe |
| ipcl32.exe | syswin32.exe |
| Mssql.exe | vcvw.exe |
| MSsrvs32.exe | winupdate32.exe |
| MSTasks.exe | xmconfig.exe |
| quicktimeprom.exe | YahooMsgr.exe |
| Regrun.exe |
*SDBot copies itself to the %System% folder, according to Symantec.
Source: Symantec Corp. (www.symantec.com/security_response/writeup.jsp?docid=2002-051312-3628-99&tabid=2)
Registry Entries
SDBot also makes modifications to the Windows Registry, aimed primarily at making sure that the SDBot software is automatically started each time Windows is booted up. Typically, one of the Registry values displayed in Table 4.2, or something similar, is added to one of the following Registry keys:
![]() HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun
![]() HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRunServices
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRunServices
![]() HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
Table 4.2 Registry Values Used by SDBot*
*These registry values are used to modify the Windows registry so that SDBot is started when Windows starts.
Source: Symantec Corp. (www.symantec.com/security_response/writeup.jsp?docid=2002-051312-3628-99&tabid=2)
Additional Files
Some variants of SDBot can also create new files in the %System% directory for additional functionality. Two files that have been identified from known SDBot variants are SVKP.sys and msdirectx.sys.
The SVKP.sys file is a component of SVK Protector, a copy protection utility that prevents the software from being reverse-engineered. Some variants use this technique in an attempt to prevent security researchers or antivirus firms from being able to analyze the malware and determine how it works.
Msdirectx.sys is designed to provide rootkit functionality for the software and allow an attacker to gain complete access and control of the target system without being detected.
Unexpected Traffic
Another sign that might identify an SDBot infection is open ports or unexpected network connections on your system. Some variants of SDBot will establish an IRC connection via TCP port 6667, and others have been known to use port 7000.
Check for Open Ports on Your System
Windows comes with a built-in command-line utility that you can use to see what ports are active on your system. Click Start | Run and type cmd, then press Enter. At the command prompt, type netstat –a followed by pressing Enter to get a complete listing of the open ports on your system and the current state of communication.
For more information about the features of netstat, you can also type netstat /? to find out what other switches are available and the functions they perform.
If you are really paranoid that your system could be compromised, even the netstat utility could be called into question. Perhaps the malware has replaced it with a modified or malicious version. If you are concerned that this might be the case, you can use nmap from a remote system and scan the suspected computer for open ports instead.
The SDBot program might attempt to communicate with a variety of IRC channels using its own IRC client software. Some examples of IRC channels used by known SDBot variants are:
Propagation
To spread effectively, SDBot relies on weak security on target systems or the ability to leverage the current user credentials to connect with other network resources. SDBot assumes the same access rights and privileges as the user that is currently logged into the system.
SDBot will attempt to connect to and spread via default administrative shares found on a typical Windows system, such as PRINTS, C$, D$, E$, ADMIN$, or IPCS. Some variants come bundled with a listing of common username and password combinations, such as abc123 or password for the password, which can be used to attempt to connect with network resources as well.
Variants of SDBot are also known to scan for Microsoft SQL Server installations with weak administrator passwords or security configurations.
RBot
The RBot family of bots is one of the most pervasive and complex out there. Originated in 2003, the core functionality of RBot continues to drive the primary functionality of hundreds of RBot variants. By its very nature, however, RBot morphs and evolves over time. Filenames and techniques vary from one variant to the next and might even be randomized as a function of the malware, making accurate identification difficult.
RBot was the first of the bot families to use compression or encryption algorithms. Most RBot variants rely on one or more runtime executable-packing utilities such as Morphine, UPX, ASPack, PESpin, EZIP, PEShield, PECompact, FSG, EXEStealth, PEX, MoleBox, or Petite.
Once infected with RBot, a compromised system can be controlled by a botherder and used for a variety of functions, including downloading or executing files from the Internet, retrieving CD keys for some computer games, creating a SOCKS proxy, participating in DDoS attacks, sending e-mail, logging keystrokes, or capturing video from a Webcam if the compromised system has one connected.
Aliases
Antivirus and security vendors rarely agree on naming conventions, so the same threat can have multiple names, depending on the vendor supplying the information. Here are some aliases for RBot from the top antivirus vendors:
Infection
The RBot family of worms uses a few different methods to seek out vulnerable targets and find systems to infect. Like the SDBot family, RBot attempts to exploit weak passwords and poor security on administrative shares to spread across the network. Systems with simple or blank passwords on network shares are easy prey.
In addition to spreading via weak security on network shares, RBot also leverages a variety of known software vulnerabilities in the Windows operating system and common software applications. Some variants are also capable of exploiting backdoors or open ports created by other malware infections.
Signs of Compromise
If you believe that your computer might be infected with RBot, there are a few clues you can look for to verify your suspicions.
System Folder
On initial execution, RBot copies itself into the %System% directory (typically C:WindowsSystem32). A common filename RBot uses is wuamgrd.exe, but different variants may use different filenames. Some variants might actually randomize the filename so that it is different for each infected system. The file is copied to the %System% directory with the read–only, hidden, and system file attributes set and the date/timestamp of the file altered to match the date/timestamp on the explorer.exe file. As a result, even if a user stumbles on the file, it gives the appearance of being an old file that was installed with the operating system.
Registry Entries
RBot is highly configurable and has evolved significantly over time. RBot will add entries to the Windows registry to ensure that it runs automatically each time Windows is started. The registry value is configurable, though, so it changes from one variant to the next. A common one among some RBot variants is wuamgrd.exe. The registry keys RBot typically modifies are:
(The source of the aforementioned registry keys is CA. Go to www3.ca.com/securityadvisor/virusinfo/virus.aspx?ID=39437 for more information.)
RBot has some added intelligence as well. Some variants of RBot are programmed to check the registry periodically and reset the registry values if they have been changed or deleted. RBot also creates a mutex to make sure that only one copy of RBot runs on a system at a time. Different variants of RBot use different names for the mutex, but one example that has been identified is rxlsass01b.
Terminated Processes
Many of the RBot variants also attempt to terminate processes associated with various security or antivirus programs, to avoid being detected or removed. Some variants also seek out and terminate processes from other malware, such as the Blaster worm. Table 4.3 lists some of the processes known to be targeted by some RBot variants.
Table 4.3 A Sample of Processes Sometimes Terminated by RBot
| regedit.exe | MSBLAST.exe |
| msconfig.exe | teekids.exe |
| netstat.exe | Penis32.exe |
| msblast.exe | bbeagle.exe |
| zapro.exe | SysMonXP.exe |
| navw32.exe | winupd.exe |
| navapw32.exe | winsys.exe |
| zonealarm.exe | ssate.exe |
| wincfg32.exe | rate.exe |
| taskmon.exe | d3dupdate.exe |
| PandaAVEngine.exe | irun4.exe |
| sysinfo.exe | i11r54n4.exe |
| mscvb32.exe |
Source: CA (www3.ca.com/securityadvisor/virusinfo/virus.aspx?ID=39437)
Unexpected Traffic
Once a system is infected, RBot will attempt to connect to the IRC server it is configured to join. The IRC server, channel, port number, and password differ among variations, so it is not possible to list them here. Aside from looking for unknown or suspicious connections or open ports on your system, you can also look for activity on TCP port 113 (ident). RBot uses this port for ident services required by some IRC servers.
RBot (and many of the other bot programs as well as other malware) often attempts to connect to network shares and other resources using the credentials and access rights of the currently logged-in user. You should use a login with restricted or limited access for day-to-day tasks and only log in with full administrative privileges when it is necessary. This practice will limit malware’s ability to exploit the privileges of the logged-in user to spread itself.
Propagation
The primary means of propagation for the RBot family is through Windows network shares. RBot scans on ports 139 and 445 looking for open connections. If a target is found, RBot then attempts to connect to the IPC$ administrative share on that system.
If RBot is successful at connecting with the target system, it will try to obtain a list of the usernames on the target machine that it can use to gain access. If RBot cannot get the list of usernames from the target system, some variants will simply try a default list of usernames (like those listed in Table 4.4), which are preconfigured into the malware.
Table 4.4 Usernames That Some RBot Variants Will Attempt to Use to Connect With Network Resources
| administrator | student |
| administrador | teacher |
| administrateur | wwwadmin |
| administrat | guest |
| admins | default |
| admin | database |
| staff | dba |
| root | oracle |
| computer | db2 |
| owner |
Source: CA (www3.ca.com/securityadvisor/virusinfo/virus.aspx?ID=39437)
For each username that RBot finds on the target system or the usernames it is preconfigured with, RBot attempts to authenticate using a list of commonly used weak passwords. The list of passwords varies from one version of RBot to the next, but it commonly includes passwords like those found in Table 4.5.
Table 4.5 Weak Passwords Commonly Found in RBot Variants*
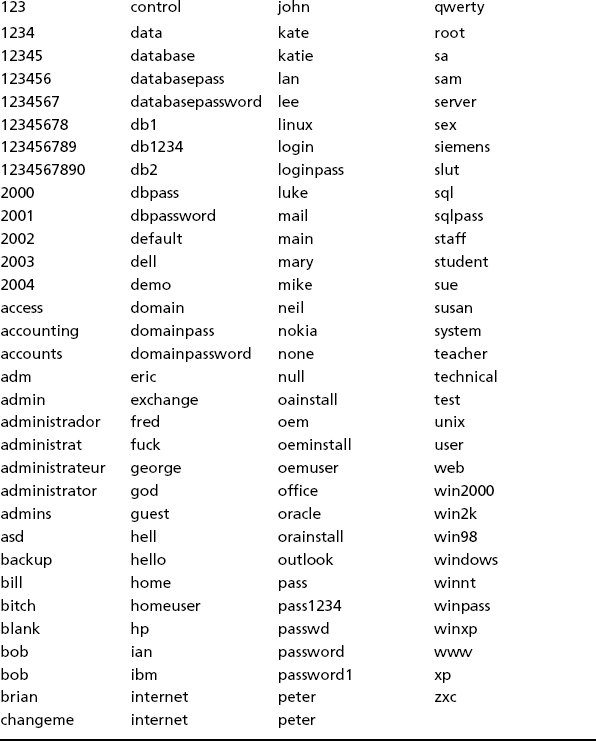
Source: CA (www3.ca.com/securityadvisor/virusinfo/virus.aspx?ID=39437)
If it authenticates successfully with the target machine, RBot then attempts to copy itself to the following locations and schedules a remote job to execute the RBot software and infect the target machine:
Using Known Vulnerability Exploits
Another method RBot uses to propagate itself is to use exploits of known vulnerabilities. RBot variants may attempt to exploit one or more of the vulnerabilities listed in Table 4.6. If a vulnerable target is found, RBot executes a small program instructing the target machine to connect to a remote server to download the complete RBot code. The connections back to the RBot source may use alternate port assignments but are typically made via HTTP (port 81) or TFTP (port 69).
Table 4.6 Known Vulnerabilities Commonly Exploited by RBot Variants
Microsoft Windows LSASS buffer overflow vulnerability (TCP port 445)
Microsoft Windows ntdll.dll buffer overflow vulnerability (Webdav vulnerability) (TCP port 80)
Microsoft Windows RPC malformed message buffer overflow vulnerability (TCP ports 135, 445, 1025)
Microsoft Windows RPCSS malformed DCOM message buffer overflow vulnerabilities (TCP port 135)
Exploiting weak passwords on MS SQL servers, including Microsoft SQL
Server Desktop Engine blank sa password vulnerability (TCP port 1433)
Microsoft Universal Plug and Play (UPnP) NOTIFY directive buffer overflow and DoS vulnerabilities (TCP port 5000)
DameWare Mini Remote Control buffer overflow (TCP port 6129)
Microsoft Windows Workstation service malformed message buffer overflow vulnerability (TCP port 445)
Microsoft Windows WINS replication packet memory overwrite vulnerability (TCP port 42)
RealSystem Server SETUP buffer overflow vulnerability
Microsoft SQL Server 2000 Resolution service buffer overflow vulnerability
Microsoft Windows Plug and Play service buffer overflow vulnerability
Source: CA (www3.ca.com/securityadvisor/virusinfo/virus.aspx?ID=39437)
Exploiting Malware Backdoors
Some variants of RBot take the easy route and let other malware do the hard work. These variants are programmed to seek out the default backdoors opened by other malware such as the Bagle or Mydoom worms. Malware backdoors known to be targeted by some RBot variants include:
Agobot
Agobot, also commonly referred to as Gaobot or Phatbot, depending on the variant and the AV vendor naming it, introduced the idea of modular functionality to the world of malicious bots. Rather than infecting a system with all the Agobot functionality at once, this threat occurs in three distinct stages.
First, Agobot infects the computer with the bot client and opens a backdoor to allow the attacker to communicate with and control the machine. The second phase attempts to shut down processes associated with antivirus and security programs, and the final phase tries to block access from the infected computer to a variety of antivirus and security-related Web sites.
The modular approach makes sense from a design perspective because it allows the developer to update or modify one portion, or module, without having to rewrite or recompile the entire bot code.
Aliases
Antivirus and security vendors rarely agree on naming conventions, so the same threat can have multiple names, depending on which vendor is supplying the information. Here are some aliases for Agobot from the top antivirus vendors:
Naming Confusion
Another major bot family is the Polybot family. There is a great deal of confusion when it comes to malware naming, however. One vendor might decide to call a threat one thing, and a different vendor might give it a completely different name. The other issue when it comes to bots is that many of the bots are offshoots or evolutions of each other, blurring the lines and sometimes making it difficult to choose whether a new variant is part of the original or part of the new offshoot strain of malware.
Polybot is an example of such a threat. Polybot is essentially Agobot but with a polymorphic technique thrown in. Polybot adds an “envelope” to the Agobot code that reencrypts the whole file each time it runs, essentially providing each new infection a unique signature to evade detection by antivirus or intrusion detection products.
Infection
The Agobot family of malware propagates via network shares, as is common among the major bot families. However, Agobot also adds the ability to propagate using peer-to-peer (P2P) networking systems such as Kazaa, Grokster, BearShare, and others. Agobot makes itself available on the P2P network using a randomized filename that is designed to have mass appeal in an attempt to lure unsuspecting users into downloading and executing it on their computers.
The offshoot variants dubbed Phatbot use WASTE, a P2P protocol designed by AOL. WASTE was designed to use encryption for more secure file transfers via P2P, but the sharing of public keys was too complicated and AOL eventually scrapped the project. Using WASTE creates some unique methods of propagation but also limits the scalability of the bot army because WASTE can only manage 50 to 100 client nodes at a time.
It seeks to terminate a wide variety of antivirus and security programs on infected systems and attempts to modify the Hosts file on the infected computer, to prevent the ability to communicate with Web sites associated with antivirus and security applications. Agobot singles out the Bagle worm, terminating processes associated with that malware if they exist on the infected system.
Signs of Compromise
If you believe that your computer is infected with Agobot, there are a few clues you can look for to verify your suspicions.
System Folder
Agobot will drop a copy of itself into the %System% folder (typically C:WindowsSystem32) on the target system. The filename used depends on the variant, but common filenames Agobot uses include syschk.exe, svchost.exe, sysmgr.exe, and sysldr32.exe.
Registry Entries
To ensure that the bot functionality is operational, Agobot creates registry entries to automatically start the bot each time Windows starts. Some variants add a value called Config Loader and others add a value called Svhost Loader to the HKEY_Local_MachineSoftwareMicrosoftWindowsCurrentVersionRun key in the registry.
Agobot will sometimes add a registry entry aimed at the Windows 95, Windows 98, or Windows ME operating systems. By referencing the dropped malicious file using the HKEY_Local_MachineSoftwareMicrosoft WindowsCurrentVersionRunServices registry key, the bot software will execute, but the service will not be displayed on the Close Program dialog box, making it effectively invisible to the user.
Terminated Processes
Agobot contains arguably the most comprehensive listing of programs and services to target for termination. Agobot seeks out processes associated with antivirus or other security software, as well as processes associated with competing malware, and shuts them down.
Modify Hosts File
Above and beyond terminating the processes associated with antivirus and security software, variants of Agobot also modify the hosts file of the infected machine to redirect attempts to reach the Web sites of antivirus and security vendors.
The Hosts file, typically found at %System%driversetchosts, is appended with entries for Web sites such as Symantec’s LiveUpdate site or McAfee’s download site, among others. The entries direct any attempts to connect with these sites to the loopback address, 127.0.0.1, preventing the connection and blocking the machine from communicating with those sites.
Theft of Information
Another aspect of Agobot that sets it apart from some of the other major bot families is the theft of information. Specifically, Agobot will seek out and steal the CD keys for a variety of popular games (see Table 4.7).
Table 4.7 Games Vulnerable to Agobot Searches
| Battlefield 1942 | Industry Giant 2 |
| Battlefield 1942: Secret Weapons Of WWII | James Bond 007 Nightfire |
| Battlefield 1942: The Road To Rome | Medal of Honor: Allied Assault |
| Battlefield 1942: Vietnam | Medal of Honor: Allied Assault: Breakthrough |
| Black and White | Medal of Honor: Allied Assault: Spearhead |
| Call of Duty | Nascar Racing 2002 |
| Command and Conquer: Generals | Nascar Racing 2003 |
| Command and Conquer: Generals: Zero Hour | Need For Speed: Hot Pursuit 2 |
| Command and Conquer: Red Alert2 | Need For Speed: Underground |
| Command and Conquer: Tiberian Sun | Neverwinter Nights |
| Counter-Strike | NHL 2002 |
| FIFA 2002 | NHL 2003 |
| FIFA 2003 | Ravenshield |
| Freedom Force | Shogun: Total War: Warlord Edition |
| Global Operations | Soldier of Fortune II - Double Helix |
| Gunman Chronicles | Soldiers Of Anarchy |
| Half-Life | The Gladiators |
| Hidden and Dangerous 2 | Unreal Tournament 2003 |
| IGI2: Covert Strike | Unreal Tournament 2004 |
Source: Trend Micro Inc. (www.trendmicro.com/vinfo/virusencyclo/default5.asp?VName=WORM%5FAGOBOT%2EGEN&VSect=T)
Unexpected Traffic
Like other bot families, Agobot variants also open a backdoor on the infected system and establish communication with a designated IRC server. This allows a botherder to issue commands to or take control of the compromised system.
The backdoor provides functionality for the botherder to do just about anything, including executing files on the infected machine, downloading additional files from Web or FTP sites, redirecting TCP traffic to the system, using the compromised system as a part of a DDoS attack, and more.
Propagation
Like other bot families, Agobot variants attempt to spread via open network shares. Once a system is infected, Agobot will seek out usernames and passwords on the network using NetBEUI. It will then search for open shares such as the default administrative shares (c$, admin$, print$, etc.) and attempt to log in using the usernames and passwords it has found as well as a preconfigured list of common usernames and passwords.
Agobot also attempts to spread malware via P2P networks by making itself available on those networks using enticing filenames designed to draw attention and increase the odds that the file will be downloaded and executed. It uses a predefined list of options (see Table 4.8) to randomly create filenames that could be of interest to users. For example, Agobot will take a random entry from Set A in Table 4.8 and combine it with a variable entry from Set B to create a filename.
Table 4.8 File Names Agobot Uses to Spread Malware via P2P
| Set A | Set B (%s =) |
|---|---|
| %s - ADSL Playfix | Alessandra Ambrosia |
| %s - Autotuning (for Newbies) | Amanda Peet |
| %s - Cable Modem Playfix | Anna Kournikova |
| %s - CD Key Generator | Ashley Judd |
| %s - Character Cheat | Belinda Chapple |
| %s - Crack all versions | Britney Spears |
| %s - Game Trainer | Cameron Diaz |
| %s - Idem Duplicator | Carmen Electra |
| %s - Internet Play Fix | Chandra North |
| %s - Item Hack | Charlize Theron |
| %s - Map Hack | Christina Aguilera |
| %s - Multiplayer Cheat | Donna D’Erico |
| %s - Newest Patch | Emma Sjoberg |
| %s - NOCD Patch | Gillian Anderson |
| %s - Tweaking utility | Halle Berry |
| %s - Unlimited Healt Trainer | Helena Christensen |
| %s - Unlock Everything Trainer | Jessica Alba |
| %s 3D Setup | Jolene Blalock |
| %s newest version crack | Karina Lombard |
| Kate Moss | |
| Katie Price | |
| Kelly Hu | |
| Kirsten Dunst | |
| Kylie Bax | |
| Kylie Minogue | |
| Lexa Doig | |
| Michelle Behennah | |
| Pamela Anderson | |
| Salma Hayek | |
| Samantha Mumba | |
| Sandra Bullock | |
| Shakira | |
| Stacey Keibler |
Source: Trend Micro Inc. (www.trendmicro.com/vinfo/virusencyclo/default5.asp?VName=WORM%5FAGOBOT%2EGEN&VSect=T)
Spybot
Spybot is an evolution of SDBot. Like SDBot, the Spybot code is open source and available for the public to modify and contribute to, to help develop further functionality for the product.
The main differentiator for Spybot from SDBot is that Spybot adds a number of spyware-like capabilities such as keystroke logging, e-mail address harvesting, Web-surfing activities, and more.
Aliases
Again, antivirus and security vendors rarely agree on naming conventions, so the same threat can have multiple names, depending on which vendor is supplying the information. Here are some aliases for Spybot from the top antivirus vendors:
Infection
Spybot spreads through a variety of methods, including the standard attempt to propagate by finding open network shares with weak or nonexistent security. Spybot also spreads via some P2P networks and seeks out systems compromised by other worms or malware to leverage existing backdoors or open ports to infect systems.
Spybot contains the standard bot functionality of providing a backdoor for a botherder to command and control the infected machine, but it also adds some unique new features, such as the ability to broadcast Spam over Instant Messaging (SPIM). It also attempts to modify the registry to prevent various functions such as blocking the user from installing Windows XP SP2 or disabling the Windows XP Security Center.
Signs of Compromise
If you believe that your computer could be infected with Spybot, there are a few clues you can look for to verify your suspicions.
System Folder
Spybot will place a copy of itself in the %System% folder (typically C:WindowsSystem32). Common filenames used by Spybot include:
Registry Entries
Depending on the variant, Spybot could make a broad range of potential registry entries. The following are some examples of common registry modifications found with Spybot variants.
Spybot could add a value to create a shared folder on the Kazaa P2P network, such as:
Spybot adds an entry to ensure tha it is started automatically when Windows starts, such as:
Spybot may modify the following registry key to enable or disable DCOM:
Spybot may modify the following registry key to restrict network access:
Spybot may modify the following registry key to disable specific services:
Spybot may modify the following registry key to prevent Windows XP SP2 from being installed:
![]() Value: “DoNotAllowXPSP2” = “1”
Value: “DoNotAllowXPSP2” = “1”
![]() Registry key: HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsWindowsUpdate
Registry key: HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsWindowsUpdate
Spybot may modify the following registry key to disable the Microsoft Security Center:
Spybot may modify the following registry key(s) to disable the Windows Firewall:
Unexpected Traffic
Spybot will connect to a designated IRC server, specified by the Spybot variant, and join an IRC channel to receive commands from a botherder. Some variants will also start a local HTTP, FTP, or TFTP server. Scans of the computer that show unusual services or unknown ports open could be evidence of these types of connections.
Keystroke Logging and Data Capture
An added feature of Spybot is the ability to capture keystrokes and retrieve personal information that can be used for further system compromise or identity theft. Variants of Spybot will scan the infected computer for cached passwords and will log the keystrokes typed on the computer to try to get information such as usernames, passwords, credit card or bank account numbers, and more. The keystroke logging specifically targets windows with titles that include bank, login, e-bay, ebay, or paypal.
Propagation
Spybot propagates through the same standard means as other bot families. Locating open or poorly secured network shares and leveraging them to spread and compromise other systems is a primary method of propagation. Spybot comes preconfigured with a list of commonly used usernames and passwords for general purposes as well as passwords designated specifically for SQL Server account logins.
In addition to network shares, Spybot also seeks out and targets systems that are vulnerable to specific vulnerabilities (see Table 4.9). Spybot will do vulnerability scans of the computers it can communicate with and find systems that can be exploited using these known vulnerabilities.
Table 4.9 Vulnerabilities Exploited by Spybot Variants to Help It Propagate
| Vulnerability | Port(s) | Microsoft Security Bulletin |
|---|---|---|
| DCOM RPC vulnerability | TCP 135 | MS03-026 |
| LSASS vulnerability | TCP ports 135, 139, 445 | MS04-011 |
| SQL Server and MSDE 2000 vulnerabilities | UDP 1434 | MS02-061 |
| WebDav vulnerability | TCP 80 | MS03-007 |
| UPnP NOTIFY buffer overflow vulnerability | MS01-059 | |
| Workstation Service buffer overrun vulnerability | TCP 445 | MS03-049 |
| Microsoft Windows SSL Library DoS vulnerability | MS04-011 | |
| Microsoft Windows Plug and Play buffer overflow vulnerability | MS05-039 | |
| Microsoft Windows Server Service remote buffer overflow vulnerability | MS056-040 |
Source: Symantec Corp. (www.symantec.com/security_response/writeup.jsp?docid=2003-053013-5943-99&tabid=2)
Mytob
The Mytob family of worms is an example of the converging world of malware. The originators of Mytob took a mass-mailing worm and combined it with bot functionality based on the SDBot family. The hybrid combination results in faster propagation and more compromised systems lying dormant, waiting for a botherder to give them direction.
Aliases
Antivirus and security vendors rarely agree on naming conventions, so the same threat can have multiple names, depending on which vendor is supplying the information. Here are some aliases for Mytob from the top antivirus vendors:
At the beginning of 2005, the authors of the Mytob worm entered into a malware war against the Sober worm. Each malware attempted to outdo the other, sometimes disabling or removing the opposing worm in the process of infecting a system. The malware war kept antivirus vendors and corporate administrators on their toes because the escalation sometimes resulted in many new variants of each on a given day.
Infection
Mytob arrives on the target system via e-mail with some sort of file attachment. The purpose of the e-mail is to trick or lure the user into opening and executing the file attachment, thereby installing the worm on the user’s system and continuing the cycle of infection and propagation.
Signs of Compromise
If you believe that your computer could be infected with Mytob, there are a few clues you can look for to verify your suspicions.
System Folder
When a system becomes infected with the Mytob worm, a copy of the malware is placed in the %System% directory (typically C:WindowsSystem32) named wfdmgr.exe.
Registry Entries
Mytob alters one or more of the following registry keys to ensure that it is started each time Windows starts:
![]() HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun “LSA” = wfdmgr.exe
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun “LSA” = wfdmgr.exe
![]() HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun “LSA” = wfdmgr.exe
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun “LSA” = wfdmgr.exe
![]() HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRunServices “LSA” = wfdmgr.exe
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRunServices “LSA” = wfdmgr.exe
![]() Additional keys/values are created, which are typically associated with W32/Sdbot.worm:
Additional keys/values are created, which are typically associated with W32/Sdbot.worm:
![]() HKEY_CURRENT_USERSYSTEMCurrentControlSetControlLsa “LSA” = wfdmgr.exe
HKEY_CURRENT_USERSYSTEMCurrentControlSetControlLsa “LSA” = wfdmgr.exe
Unexpected Traffic
Mytob is a mass-mailing worm first and foremost. However, it earned a spot in this book by virtue of being a very successful piece of malware that also includes bot functionality from the SDBot family. An infected system will attempt to connect to irc.blackcarder.net and join a specific IRC channel for further instructions.
Propagation
Mytob spreads almost exclusively via e-mail. Once a system is infected, Mytob will scan the system for files with file extensions like those shown in Table 4.10 from which to harvest e-mail addresses The worm tries to fly under the radar and remain undetected, though. So, the domains listed in Table 4.11 are eliminated from the harvested e-mail addresses before Mytob starts generating the spam e-mail messages to try to propagate itself.
Table 4.10 File Extensions Known to Be Commonly Targeted by Mytob for Harvesting E-mail Addresses
| wab | php |
| adb | sht |
| tbb | htm |
| dbx | txt |
| asp | pl |
Source: McAfee, Inc. (http://us.mcafee.com/virusInfo/default.asp?id=description&virus_k=132158&affid=108)
Table 4.11 Mytob Eliminates Harvested E-mail Addresses with the Following Domains
| .gov | gov. | mydomai |
| .mil | hotmail | nodomai |
| abuse | iana | panda |
| acketst | ibm.com | pgp |
| arin. | icrosof | rfc-ed |
| avp | ietf | ripe. |
| berkeley | inpris | ruslis |
| borlan | isc.o | secur |
| bsd | isi.e | sendmail |
| example | kernel | sopho |
| fido | linux | syma |
| foo. | math | tanford.e |
| fsf. | mit.e | unix |
| gnu | mozilla | usenet |
| msn. | utgers.ed |
Source: McAfee, Inc. (http://us.mcafee.com/virusInfo/default.asp?id=description&virus_k=132158&affid=108)
Summary
Bots are a serious threat to Internet and computer network security. Viruses and worms have certainly wreaked havoc on the Internet, and phishing attacks and spyware are both growing threats to computer security as well, but bots are unique among malware in their ability to provide tens or hundreds of thousands of compromised systems lying dormant and waiting to be used as an army for all kinds of malicious activities.
In this chapter we learned about some of the major bot families—specifically, SDBot, RBot, Agobot, Spybot, and Mytob. These bots have been around for as many as five years, and new variants based on the core of the original bot code are still created. Some of these bot families have hundreds and hundreds of variants.
We discussed how almost all the bot families share one propagation method. Seeking out unprotected or poorly secured network shares to attack is a common means shared by virtually every bot family. We also covered ways different bot families have introduced different unique aspects that set them apart. For example, RBot introduced the use of compression algorithms to encrypt the bot code. Agobot pioneered the use of P2P networks as a propagation method. Spybot added spyware functionality such as keystroke logging, and the Mytob worm combined a bot (SDBot) with a mass-mailing worm, marking a shift in malware code to hybrid attacks that combine different types of malware.
The bots discussed in this chapter are by no means all the bot threats out there. Malware has shifted from “carpet-bombing style” viruses and worms, intended to spread the fastest and gain infamy for the malware author, to precision stealth attacks aimed at financial gain. Some worms, such as those in the Mytob family, still gain attention by spreading quickly. But the true goal is to create as many compromised bot systems as possible that will lie dormant and wait for orders from a botherder to initiate some sort of malicious activity.
Solutions Fast Track
Each of the bot families discussed in this chapter provides a fairly significant amount of information. This section boils the information down to the most pertinent or relevant points that you should keep in mind about each bot family.
SDBot
![]() One of the oldest bot families. It has existed for more than five years.
One of the oldest bot families. It has existed for more than five years.
![]() Released by the author as open source, providing the source code for the malware to the general public.
Released by the author as open source, providing the source code for the malware to the general public.
![]() Spreads primarily via network shares. It seeks out unprotected shares or shares that use common usernames or weak passwords.
Spreads primarily via network shares. It seeks out unprotected shares or shares that use common usernames or weak passwords.
![]() Modifies the Windows registry to ensure that it is started each time Windows starts.
Modifies the Windows registry to ensure that it is started each time Windows starts.
RBot
Mytob
![]() Mytob is actually a mass-mailing worm, not a bot, but it infects target systems with SDBot.
Mytob is actually a mass-mailing worm, not a bot, but it infects target systems with SDBot.
![]() A hybrid attack that provides a faster means of spreading and compromising systems to create bot armies.
A hybrid attack that provides a faster means of spreading and compromising systems to create bot armies.
![]() Harvests e-mail addresses from designated file types on the infected system.
Harvests e-mail addresses from designated file types on the infected system.
![]() Eliminates addresses with certain domains to avoid alerting antivirus or security firms to its existence.
Eliminates addresses with certain domains to avoid alerting antivirus or security firms to its existence.
The following Frequently Asked Questions, answered by the authors of this book, are designed to both measure your understanding of the concepts presented in this chapter and to assist you with real-life implementation of these concepts. To have your questions about this chapter answered by the author, browse to www.syngress.com/solutions and click on the “Ask the Author” form.
Q: What is one of the most common methods bots use to spread and infect new systems?
A: All the major bot families target insecure or poorly secured network shares. Typically, the bot contains a list of common usernames and passwords to attempt, as well as some capability to seek out usernames and passwords found on the target system.
Q: How do bots typically ensure that they continue running?
A: Bots generally modify the Windows registry to add values to registry keys to make sure that the bot software is automatically started each time Windows starts.
Q: What unique method of propagation was introduced by the Agobot family?
A: The Agobot family of bots (also known as Gaobot or Phatbot) uses P2P networking as a unique method of spreading to new systems.
Q: Which bot family pioneered the use of encryption algorithms to protect the code from being reverse-engineered or analyzed?
A: The RBot family uses one or more runtime executable packing utilities such as Morphine, UPX, ASPack, PESpin, EZIP, PEShield, PECompact, FSG, EXEStealth, PEX, MoleBox, or Petite to encrypt the bot code.
Q: What is unique about the Spybot family of bots?
A: Spybot is based on SDBot but adds spyware capabilities such as keystroke logging and data theft or password stealing.
Q: What sets Mytob apart among the bot families discussed in this chapter?
A: Mytob is not a bot in and of itself. It is a mass-mailing worm that includes SDBot as part of its payload, providing a hybrid attack that can compromise more systems with the bot software faster.
Q: What is a common method bot families use to avoid detection or removal?
A: Many bots, and even viruses, worms, and other malware, search for and terminate processes associated with common antivirus or security applications to shut them down.
Q: How do some bots ensure that infected systems are not able to research information or obtain updates from antivirus vendors?
A: Some bots modify the Hosts file on the compromised system to redirect requests for antivirus and other security-related Web sites to the loopback address of 127.0.0.1, blocking attempts to reach those sites.
Q: Which bot family creates entries in the Windows registry to prevent users from installing Windows XP Service Pack 2?
A: The Spybot family adds registry entries to block the installation of Windows XP SP2, as well as registry entries to disable the Windows Firewall and the Windows Security Center.
