Chapter 1 Botnets: A Call to Action
Introduction
Throughout 2006, technical security conferences have been discussing the latest “killer Web app.” Unfortunately, this Web technology works for the bad guys. With funding from organized crime and spam lords, a generation of talented hackers without morals has created a devastating arsenal of deadly toys, in the form of botnets. Norman Elton and Matt Keel from the College of William & Mary in the 2005 presentation “Who Owns Your Network?” called bot networks “the single greatest threat facing humanity.” This may be an exaggeration, but Botnets are arguably the biggest threat that the Internet community has faced. John Canavan, in a whitepaper titled “The Evolution of Malicious IRC Bots,” says that Botnets are “the most dangerous and widespread Win32 viral threat.” According to the cover of eWEEK magazine for October 16, 2006, we are “Losing the Botnet War.” The article by Ryan Naraine titled “Is the Botnet Battle Already Lost?” describes the current state of the Botnet environment: Botnets are “the key hub for well-organized crime rings around the globe, using stolen bandwidth from drone zombies to make money from nefarious Internet activity.” (for more information, go to www.eweek.com/article2/0,1895,2029720,00.asp.) By contrast the security response is in its infancy with several vendors releasing version 1 of botnet-related products. Badly needed intelligence information is locked away with only the slightest means of communicating it to the security professionals that need it. There isn’t any such thing as an information security professional security clearance. One vendor told us that the quality of their product depends on the quality of their intelligence sources and then went on to say that they could give us no information that could vouch for the quality of their intelligence sources.
Our early weapon against botnets involved removing the bot server, the strategy of “removing the head of the serpent.” Recent articles about the state of the security profession response to botnets have lamented the discovery that we are not fighting a snake, but rather, a hydra. It has not one head but many and cutting off one spawns two to replace it. Much has been made of the loss of this weapon by the press. In the article, several security professionals admit that the battle is lost. In real warfare, generals must battle the enemy, but just as important, they must battle against the loss of morale. Many of the security professionals who pioneered the fight against botnets are demoralized by the realization that taking out the Command and Control (C&C) server is no longer as effective as it once was. Imagine how the first invading army that encountered a castle felt. Imagine the castle owner’s reaction upon the invention of the siege tower, catapult, or mortar. Yet, in the years following the introduction of each of these weapons, castle design changed. A single wall surrounding the castle became a series of walls. The rectangular castle shape gave way to irregular shapes intended to deflect instead of stopping enemy weapons. The loss of a major weapon doesn’t mean the loss of the war unless the general lets morale plummet and does not evolve to meet the new environment.
This book will attempt to add new soldiers and new weapons to the battle. In doing so, the authors hope to stem the tide of lost morale and help security professionals regain focus. It is necessary to lay a foundation for deeper discussions.
This chapter describes the current state and how we got to this place. We come from many levels and as such we must start from the very beginning. What is a botnet? In its simplest form, it is an army of compromised computers that take orders from a botherder. A botherder is an immoral hacker who uses the botnet for financial gain or as a weapon against others.
The Killer Web App
How does this make a botnet a “killer Web app?” The software that creates and manages a botnet makes this threat much more than the previous generation of malicious code. It is not just a virus; it is a virus of viruses. The botnet is modular—one module exploits the vulnerabilities it finds to gain control over its target. It then downloads another module that protects the new bot by stopping antivirus software and firewalls; the third module may begin scanning for other vulnerable systems.
A botnet is adaptive; it can be designed to download different modules to exploit specific things that it finds on a victim. New exploits can be added as they are discovered. This makes the job of the antivirus software much more complex. Finding one component of a botnet does not imply the nature of any of the other components because the first component can choose to download from any number of modules to perform the functionality of each phase in the life cycle of a botnet. It also casts doubt on the capability of antivirus software to claim that a system is clean when it encounters and cleans one component of a multicomponent bot. Because each component is downloaded when it is needed after the initial infection, the potential for a system to get a zero day exploit is higher. If you are in an enterprise setting, you take the risk of putting a bot back into circulation if the effort to clean the malicious code isn’t comprehensive. Rather than take that risk, many IT departments opt to re-image the system from a known clean image.
Botnet attacks are targetable. That is, the hacker can target a company or a market sector for these attacks. Although botnets can be random, they can also be customized to a selected set of potential hosts. The botherder can configure the bot clients to limit their scanning to hosts in a defined set of Internet Protocol (IP) addresses. With this targeting capability comes the capability to market customized attacks for sale. The targeting capability of botnets is adaptive as well. The bot client can check the newly infected host for applications that it knows how to exploit. When it determines that the host owner is a customer of, for example, an e-gold account, the client can download a component that piggybacks over the next connection to e-gold the customer makes. While the host owner is connected to their e-gold account, the exploit will siphon the funds from the account by submitting an electronic funds transfer request.
How Big Is the Problem?
The latest Internet Threat report (Sept 2006) released by Symantec states that during the six-month period from January to June 2006 Symantec observed 57,717 active bot network computers per day. Symantec also stated that it observed more than 4.5 million distinct, active bot network computers. From our experience in an academic environment, many bots we saw were not usually detected until the botherder had abandoned the computer. As soon as the bot client stopped running, the remnants were detected. This is to say, the actual number is much larger than what Symantec can report. Recall that one of the bot client modules is supposed to make the antivirus tool ineffective and prevent the user from contacting the antivirus vendor’s Web site for updates or removal tools.
The November 17 issue of E-WEEK’s online magazine featured the news that the recent surge in penny stock and penile enhancement spam was being carried out by a 70,000-member botnet operated by Russian botherders. If left unabated, the botnet plague could threaten the future of the Internet, just as rampant crime and illegal drug use condemn the economic future of real neighborhoods.
Examine the extraordinary case documented by McAfee in its white paper, “Killing Botnets—A view from the trenches,” by Ken Baylor and Chris Brown. Even though the conclusion of the paper is clearly a sales pitch, the case it documents is real and potentially prophetic. In March of 2006, McAfee was called in to, in essence, reclaim a Central American country’s telecommunications infrastructure from a massive botnet. In the first week of the engagement McAfee documented 6.9 million attacks of which 95 percent were Internet Relay Chat (IRC) bot related. The national telco reported the following resulting problems:
Since January 2005, Microsoft has been delivering the Windows Malicious Software Removal Tool to its customers. After 15 months, Microsoft announced that it had removed 16 million instances of malicious software from almost six million unique computers. According to the Microsoft report “Progress Made, Trends Observed,” bots represented a majority of the removals. Use of the tool is voluntary; that is to say, the vast majority of Microsoft users are not running it. Before someone interprets these numbers as positive, remember that this action is reactive. The computer was successfully infected and put to some use prior to being detected and removed. A Microsoft patch was released during the last week of 2006, and within three days after the release, exploits for those patches were already being distributed throughout the Internet.
Consider the power in one botnet attack alone, the distributed denial-of-service (DDoS) attack. A small botnet of 10,000 bot clients with, conservatively, 128Kbps broadband upload speed can produce approximately 1.3 gigabits of data per second. With this kind of power, two or three large (one million plus) botnets could, according to McAfee, “threaten the national infrastructure of most countries.” Individually, these large botnets are probably powerful enough to take down most of the Fortune 500 companies.
A Conceptual History of Botnets
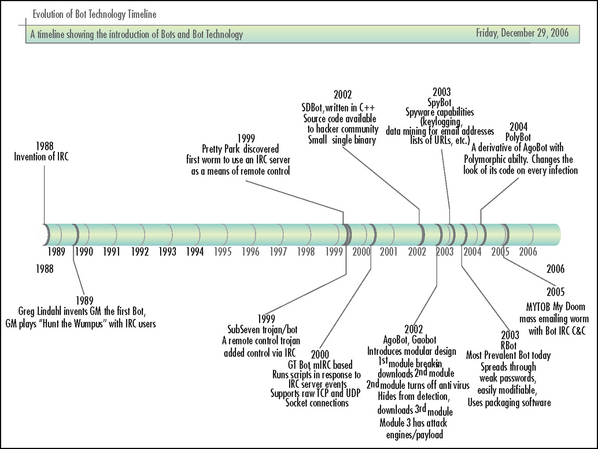
Like many things on the Internet today, bots began as a useful tool without malicious overtones. Bots were originally developed as a virtual individual that could sit on an IRC channel and do things for its owner while the owner was busy elsewhere. IRC was invented in August of 1988 by Jarkko “WiZ” Oikarinen of the University of Oulu, Finland. Figure 1.1 traces the evolution of bot technology.
GM
The original IRC bot (or robot user), called GM according to Wikipedia, was developed the next year, in 1989, by Greg Lindahl, an IRC server operator. This benevolent bot would play a game of Hunt the Wumpus with IRC users. The first bots were truly robot users that appeared to other IRC netizens as other users. Unlike today’s bot net clients (robots), these robots were created to help a user enjoy and manage their own IRC connections.
From this simple example, other programmers realized they could create robot users to perform many tasks currently done by humans for both users and the IRC operator, such as handling tedious 24-hour-a-day requests from many users. An important bot development was the use of bots to keep a channel open and prevent malicious users from taking over the channel when the operator was busy doing other things. In order to assist the IRC operator, bots needed to be able to operate as a channel operator. The bots had evolved from being code that helps a single user to code that manages and runs IRC channels as well as code that provides services for all users. Service is the term used for functionality that is offered by server-side bots as opposed to client-side bots. Around this time, some IRC servers and bots began offering the capability to make OS shell accounts available to users. The shell account permits users to run commands on the IRC host. Wikipedia notes that “a lot of shell providers disappear very fast because of abusive behavior of their members.”
Pretty Park
In May 1999, Pretty Park, a bot client written in Delphi, was discovered. PrettyPark, according to “The Evolution of Malicious IRC Bots,” a Symantec white paper authored by John Canavan, had several functions and concepts that are common in today’s bots, including:
![]() The capability to retrieve the computer name, OS version, user information, and other basic system information.
The capability to retrieve the computer name, OS version, user information, and other basic system information.
![]() The capability to search for and retrieve e-mail addresses and ICQ login names
The capability to search for and retrieve e-mail addresses and ICQ login names
![]() The capability to retrieve usernames, passwords, and dial-up network settings
The capability to retrieve usernames, passwords, and dial-up network settings
![]() The capability to update its own functionality
The capability to update its own functionality
![]() The capability to upload/download files
The capability to upload/download files
![]() The capability to redirect (tunnel) traffic
The capability to redirect (tunnel) traffic
SubSeven Trojan/Bot
By the late 1990s, a few worms (such as IRC/Jobbo) had exploited vulnerabilities in IRC clients (particularly mIRC) that let the clients be remote controlled via a “backdoor.” In June, 1999, version 2.1 of the SubSeven Trojan was released. This release was significant in that it permitted a SubSeven server to be remotely controlled by a bot connected to an IRC server. This set the stage for all malicious botnets to come. SubSeven was a remote-controlled Trojan, also written in Delphi, touted by its author as a remote administration tool. Its toolset, however, includes tools a real administrator would not use, such as capabilities to steal passwords, log keystrokes, and hide its identity. SubSeven gave bot operators full administrative control over infected systems.
GT Bot
A botnet client based on the mIRC client appeared in 2000. It is called Global Threat (GT) Bot and was written by Sony, mSg, and DeadKode. mIRC is an IRC client software package. mIRC has two important characteristics for botnet construction: it can run scripts in response to events on the IRC server, and it supports raw TCP and UDP socket connections.
GT bot had the following capabilities:
![]() Port Scanning It can scan for open ports.
Port Scanning It can scan for open ports.
![]() Flooding It can conduct DDoS attacks.
Flooding It can conduct DDoS attacks.
![]() Cloning A clone is any connection to an IRC server over and above the first connection.
Cloning A clone is any connection to an IRC server over and above the first connection.
![]() BNC (Bounce) A method for anonymizing Bot client access to a server.
BNC (Bounce) A method for anonymizing Bot client access to a server.
Today, all variations of bot technology that are based on mIRC are said to be members of the GT Bot family. These bot clients did not include a mechanism for spreading itself directly. Instead, they would use variations on social engineering ploys. A common ploy used to infect systems was an e-mail that claimed to be from a security vendor. If the user clicked on the embedded link they were taken to a Web site that delivered the client to the victim. These early botnet clients were not modular, but rather were all contained in a single package.
SDBot
Early in 2002, SDBot appeared. It was written by a Russian programmer known as sd. SDBot is a major step up the evolutionary chain for bots. It was written in C++. More important to the evolution of botnet technology, the author released the source code, published a Web page, and provided e-mail and ICQ contact information. This made it accessible to many hackers. It was also easy to modify and maintain. As a result, many subsequent bot clients include code or concepts from SDBot. SDBot produced a small single binary file that contained only 40KB of code.
A major characteristic of the SDBot family is the inclusion and use of remote control backdoors.
SDBot family worms spread by a variety of methods, including:
![]() MS RPC service and Windows Messenger port (TCP 1025)
MS RPC service and Windows Messenger port (TCP 1025)
![]() ASN.1 vulnerability, affects Kerberos (UDP 88), LSASS.exe, and Crypt32.dll (TCP ports 135, 139, 445), and IIS Server using SSL
ASN.1 vulnerability, affects Kerberos (UDP 88), LSASS.exe, and Crypt32.dll (TCP ports 135, 139, 445), and IIS Server using SSL
The SDBot exploits two server application vulnerabilities: WebDav (port 80) and MSSQL (port 1433). It exploits two third-party application vulnerabilities: DameWare remote management software (port 6129) and Imail IMAPD Login username vulnerability (port 143). It also exploits the following Cisco router vulnerability: CISCO IOS HTTP authorization (Port 80) vulnerability.
The following backdoors are exploited by SDBot:
If an exploit is successful, the worm creates and runs a script that downloads SDBot onto the new victim and executes it. Once executed, the new victim is infected. Note that many of these attacks are still used today, especially brute force and password guessing attacks targeted at ports 139, 445, and 1433.
Today, variants are spread by many other means including spam attacks in Instant Messaging (SPIM), CDs, infected attachments to e-mails, and hidden downloads on phishing sites. In 2002, the motivation for SDBot was to build a capability to launch DoS attacks. In November 2006, Panda labs reported that SDBot.ftp.worm, a component of SDBot, was the most frequently detected virus. This is a testament to the staying power and adaptability of this approach. The June 2006 Microsoft report about the Malicious Software Removal Tool listed the SDBot as having been detected on 678,000 infected PCs, the second-highest total.
Agobot
Agobot (aka Gaobot) arrived in 2002 and added modular design and significant functionalities. By modular design, we mean that Agobot does not infect a system with the entire bot code at one time. Agobot has three modules.
1. The initial module delivered contains the IRC bot client and the remote access backdoor.
2. Module 2 attacks and shuts down antivirus processes.
3. Module 3 prevents the user from accessing a list of Web sites (usually antivirus vendor sites).
Each module retrieves the next module when it completes its primary tasks. This aspect permits the botherder to update modules 2 and 3 as new techniques or sites are available. This modular update capability makes the list of variants soar into the thousands. Agobot uses IRC for C&C, but is spread using peer–to-peer (P2P) file-sharing applications (for example, Kazaa, Grokster, and Bear Share). The bot client could be commanded through IRC, but Agobot also opened a remote access backdoor to permit individual clients to be accessed directly. Agobot has the following capabilities:
![]() Scans for certain vulnerabilities
Scans for certain vulnerabilities
![]() Can launch a variety of DDoS attacks
Can launch a variety of DDoS attacks
![]() Terminates antivirus and monitoring processes
Terminates antivirus and monitoring processes
![]() Modifies the host files to prevent access to antivirus Web sites
Modifies the host files to prevent access to antivirus Web sites
![]() Hunts for systems with the Bagle worm and if it infects one, shuts down the Bagle processes
Hunts for systems with the Bagle worm and if it infects one, shuts down the Bagle processes
Other related bots include Phatbot, Forbot, Polybot, and XtremBot. Phatbot added the capability to use WASTE, a P2P for C&C that uses public key crypto.
From Code-Based Families to Characteristic-Based Families
From this point in the evolution of bots, bot family groups are being created less based on the original code and based more on unique characteristics. Take note of family names like Spybot, MyTob, and Polybot. While MyTob does indicate a code base, it is also a new characteristic, the mass mailing bot that happens to be based on MyDoom. Similarly, detections by antivirus (A/V) vendors are becoming less concerned with identifying the overall bot. Instead, they are tagging components they find with functional identifiers. Symantec, for example, tags individual components it finds with names like Hacktool.HideWindow and Trojan.Dropper. The overall bot was an RBot, but Symantec never identified that connection. To the A/V vendor, they’ve done their job if they find the malicious code and deal with it. However, the corporate security officer would really like to know more. The organizing schema for the bot tells the security officer what potential attack vectors were used to infect the computer so that they might plug the holes instead of just fixing the broken machines.
Each of the original bot families has evolved to incorporate improvements that are seen in other bots. Since many of the bots are open source, modular, and in C/C++, it is easy to take source from one bot and add its capabilities to another bot. There is also a tendency for the A/V companies to use the names that they designated to the exclusion of other vendor-created names. Partially, this is because there are so many variants of each bot family that two bots in the same family can have significantly different capabilities. For example, one variant may use IRC as its C&C and have keylogging capabilities, while the other variant may use P2P networks for C&C and search its botclients for PGP public and private keys, cached passwords, and financial account information. One vendor may call them both variants while another may tag one of the variants as a new family.
New family names from this point have tended to highlight a new capability.
Spybot
Spybot is an open source Trojan, a derivative of SDBot. It has also been called Milkit. Spybot emerged in 2003. Spybot adds spyware capabilities, such as collecting logs of activity, data from Web forms, lists of e-mail addresses, and lists of visited URLs. In addition to spreading via file sharing applications (PnP apps) and by exploiting known vulnerabilities, Spybot also looks for systems that were previously compromised by the SubSeven or the Kuang2 Trojan. Like SDBot and Agobot, Spybot is easily customizable, a fact that complicates attempts to detect and identify this bot. According to some, this bot client is poorly written. It is similar in function to Agobot and is related to SDBot, Rbot, URBot, and URXBot. Different variants of Spybot have the following capabilities:
![]() Launching DDoS attacks like UDP and SYN flooding
Launching DDoS attacks like UDP and SYN flooding
![]() Checking to prune or manage older systems (Win 9x) and systems that connect via modem
Checking to prune or manage older systems (Win 9x) and systems that connect via modem
![]() Using social engineering to entice P2P users to download the infection module of Spybot
Using social engineering to entice P2P users to download the infection module of Spybot
![]() Attempting to deceive users by posting a fake error message after the user runs the infection module
Attempting to deceive users by posting a fake error message after the user runs the infection module
![]() Logging of all keystrokes or only of keystrokes entered in Internet Explorer
Logging of all keystrokes or only of keystrokes entered in Internet Explorer
![]() Logging of everything copied to the Windows clipboard
Logging of everything copied to the Windows clipboard
![]() Grabbing cached passwords on Win 9x systems
Grabbing cached passwords on Win 9x systems
![]() Some newer variants of Spybot capture screenshots around the part of the screen where a mouse click has occurred. This capability permits the botherder to defeat new security measures taken by some banks. These banks have users click on a graphical keypad to enter their PIN or password.
Some newer variants of Spybot capture screenshots around the part of the screen where a mouse click has occurred. This capability permits the botherder to defeat new security measures taken by some banks. These banks have users click on a graphical keypad to enter their PIN or password.
![]() Although rare, some variants of Spybot are capable of sending spam messagesover instant messaging systems. These messages are reffered to as spim.
Although rare, some variants of Spybot are capable of sending spam messagesover instant messaging systems. These messages are reffered to as spim.
![]() Sniffing the network, sometimes for user IDs and passwords, sometimes for the presence of other IRC channels to exploit.
Sniffing the network, sometimes for user IDs and passwords, sometimes for the presence of other IRC channels to exploit.
![]() Killing the processes of antivirus and other security products
Killing the processes of antivirus and other security products
![]() Newer variants have begun including a rootkit, usually a hacked or modified version of the FU rootkit.
Newer variants have begun including a rootkit, usually a hacked or modified version of the FU rootkit.
![]() Control of webcams, including streaming video capture
Control of webcams, including streaming video capture
![]() Recent exploit scanning. According to John Canavan’s whitepaper titled “The Evolution of Malicious IRC Bots,” variants in 2005 included:
Recent exploit scanning. According to John Canavan’s whitepaper titled “The Evolution of Malicious IRC Bots,” variants in 2005 included:
For more information, go to www.symantec.com/avcenter/reference/the.evolution.of.malicious.irc.bots.pdf.
RBot
RBot first appeared in 2003. According to the June 2006 MSRT report from Microsoft (“MSRT: Progress Made, Trends Observed” by Matthew Braverman), the RBot family had the most detections, with 1.9 million PCs infected. It is a backdoor Trojan with IRC C&C. It introduced the idea of using one or more runtime software package encryption tools (for example, Morphine, UPX, ASPack, PESpin, EZIP, PEShield, PECompact, FSG, EXEStealth, PEX, MoleBox, and Petite). RBot scans for systems on ports 139 and 445 (systems with open Microsoft shares). It then attempts to guess weak passwords. It can use a default list or a list provided by the botherder. It can attempt to enumerate a list of users on the target system, a default list of user IDs and passwords, or try a list of user IDs and password combinations it found on other systems.
Polybot
The Polybot appeared in March of 2004 and is derived from the AgoBot code base. It is named for its use of polymorphism, or its capability to appear in many different forms. Polybot morphs its code on every infection by encasing the compiled code in an “envelope” code. The envelope re-encrypts the whole file every time it is run.
Mytob
The Mytob bot was discovered in February 2005. The bot is characterized as being a hybrid since it used source code from My Doom for the e-mail mass mailing portion of code and bot IRC C&C functionality. Note that “tob” is “bot” backwards.
Mytob uses social engineering and spoofed e-mail addresses, carries its own SMTP client, and has C&C capabilities similar to Spybot.
Capabilities Coming to a Bot Near You
This section contains brief descriptions of a few new bot components:
![]() GpCoder A potential bot component that encrypts a user’s files then leaves a message to the user on how they can buy the decoder. Current versions can be decrypted by A/V vendor “fix” tools, but if later versions use stronger encryption the potential for damage could be big.
GpCoder A potential bot component that encrypts a user’s files then leaves a message to the user on how they can buy the decoder. Current versions can be decrypted by A/V vendor “fix” tools, but if later versions use stronger encryption the potential for damage could be big.
![]() Serv-U Installed on botclients, the Serv-U ftp server enables botherders to store stolen movies, software, games, and illegal material (for example, child pornography) on their botnets and serve the data upon demand. Using other software, the Serv-U ftp server appears to be Windows Explorer in Task Manager. The data is being stored in hidden directories that can’t be reached using Windows.
Serv-U Installed on botclients, the Serv-U ftp server enables botherders to store stolen movies, software, games, and illegal material (for example, child pornography) on their botnets and serve the data upon demand. Using other software, the Serv-U ftp server appears to be Windows Explorer in Task Manager. The data is being stored in hidden directories that can’t be reached using Windows.
![]() SPIM Spam for Instant Messaging. Bots have now been used to send phishing attacks and links to Web sites that upload malicious code to your PC.
SPIM Spam for Instant Messaging. Bots have now been used to send phishing attacks and links to Web sites that upload malicious code to your PC.
ATTENTION…Windows.has.found.55.Critical.System.Errors…
To fix the errors please do the following:..
1. Download Registry Update from: www.regfixit.com.
FAILURE TO ACT NOW MAY LEAD TO SYSTEM FAILURE!
McAfee’s Site Advisor flags the aforementioned site as one that uploads malicious code.
Cases in the News
With bot authors publishing so many variants, you would think that it might be easier to eventually catch some of these people. And you would be right.
“THr34t–Krew”
In February 2003, Andrew Harvey and Jordan Bradley (two authors of TK worm), a GT Bot variant, were arrested in County Durham, in the U.K. The U.K.’s National Hi-Tech Crime Unit worked in conjunction with the United States multiagency CATCH team (Computer and Technology Crime Hi-Tech Response Team). According to the NHTCU, the two men were members of the International Hacking group “THr34t-Krew.” Rick Kavanagh, in an article on IT Vibe (www.itvibe.com), Oct 10, 2005, reported that “Harvey, 24, and Bradley, 22, admitted ‘conspiracy to cause unauthorized modification of computers with intent,’ between 31 December 2001 and 7 February 2003.” It’s estimated that the worm did £5.5 million, or approximately US$11 million in damage. TK worm exploited a common Unicode vulnerability in Internet Explorer.
Additional evidence was seized from an address in Illinois through a simultaneous search warrant. The worm had infected over 18,000 infected computers. The American member, Raymond Steigerwalt, was sentenced to 21 months in jail and ordered to pay $12,000 in restitution.
Axel Gembe
Axel Gembe is the author of Agobot (aka Gaobot, Nortonbot, Polybot), a 21-year-old hacker reported by police at the time of his arrest as “Alex G.” He was arrested May 7, 2004, at his home in Germany (Loerrach or Waldshut, different reports conflict) in the southwestern state of Baden-Württemberg. He was charged under Germany’s computer sabotage law for creating malicious computer code. He has admitted responsibility for creating Agobot in Oct 2002. Five other men have also been charged.
180Solutions Civil Law Suit
Sometime prior to 2004, a Lithuanian mob contacted Dutch hackers and asked them to create a botnet. The hackers created and delivered the botnet. It occurred to the hackers that the Lithuanians must be using it in some way to make money. They reasoned that they could do the same thing for themselves. They created their own botnet with 1.5 million zombie clients.
In one venture, they were using the botnet to install software for an adware company, 180Solutions. 180Solutions had been under pressure from the public to clean up its act for years. In January 2005, they changed their policy to exclude paying for software installations that the user did not authorize. In doing so they began to terminate agreements with distributors that installed their software without the user’s approval. By August, according to 180Solutions, they had terminated 500 distributors. The Dutch hackers then employed the botnet to extort money by DDoSing 180Solutions until they paid. The company brought in the FBI who tracked down the hackers. On August 15, 2005, 180Solutions filed a civil suit against seven hackers involved in the DDoS attacks: Eric de Vogt of Breda, the Netherlands; Jesse Donohue of South Melbourne, Australia; Khalil Halel of Beirut; Imran Patel of Leicester, England; Zarox Souchi of Toronto; Youri van den Berg of Deventer, the Netherlands; and Anton Zagar of Trbovlje, Slovenia.
Operation Cyberslam: Jay Echouafni, Jeanson James Ancheta
The first U.S. criminal case involving a botnet went to trial in November 2005. Jeanson James Ancheta (aka Resili3nt), age 21, of Downey, California, was convicted and sentenced to five years in jail for conspiring to violate the Computer Fraud Abuse Act, conspiring to violate the CAN-SPAM Act, causing damage to computers used by the federal government in national defense, and accessing protected computers without authorization to commit fraud. He was also ordered to pay $57,000 in restitution.
Ancheta’s botnet consisted of thousands of zombies. He would sell the use of his zombies to other users, who would launch DDoS (see Figure 1.2) or send spam.
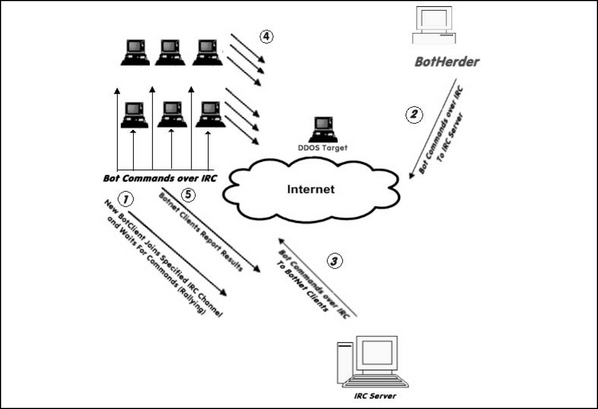
A Simple Botnet
Figure 1.2 depicts a simple botnet being commanded to launch a DDoS attack against a competitor or other individual. The numbered steps illustrate a timeline from a new botclient joining the botnet and then participating in the DDoS attack. Steps 2-5 repeat ad infinitum with step 4 changing to whatever attack was commanded in step 2.
1. When a new botclient has been created (compromised), one of its first duties is to rally back to the C&C server. It does this by joining a specified IRC Channel and waiting for commands to be posted there.
2. The botherder posts a command to the C&C server, possibly in response to a paying customer’s request. In this case, the customer has requested that the botherder prevent a competitor’s Web site from getting any orders for several days. The botherder sends a command to the C&C server, specifying the target, the time and type of attack, and which of the botclients are to participate.
3. The botclients monitor the C&C server on the specified channel. When the botherder sends the command, the botclients see that it has been posted and schedule the requested activity.
4. At the appointed time, all of the selected botclients begin sending network traffic to the target. With enough traffic, the target Web site is unable to process both the attack traffic and the legitimate traffic and soon attempts to process only attack traffic.
5. In step 5, optionally the botclients report back to the C&C server any results or that they have completed the task and are ready for new commands.
He also used a botnet of more than 400,000 zombies to generate income in a “Clicks for Hire scam” by surreptitiously installing adware for which he was paid more than $100,000 by advertising affiliate companies. A U.S. Department of Justice (DOJ) press release stated that Ancheta was able to avoid detection by varying the download times and rates of the adware installations, as well as by redirecting the compromised computers between various servers equipped to install different types of modified adware.
Anthony Scott Clark
In December 2005, Anthony Scott Clark of Beaverton, Oregon, pled guilty to infecting thousands of computers and then to using those computers to conduct a DoS attack. According to the DOJ press release (www.usdoj.gov/criminal/cybercrime/clarkPlea.htm), Mr. Clark admitted to the following:
From July through August 2003, Mr. Clark participated with several others in DDoS attacks on the Internet against eBay, Inc. and other entities. A DDoS attack is one in which many compromised computers (or bots) attack a single target, thereby causing a denial of service for legitimate users of the targeted system.
Mr. Clark and his accomplices accumulated approximately 20,000 bots by using a worm program that took advantage of a computer vulnerability in the Windows Operating System—the “Remote Procedure Call for Distributed Component Object Model,” or RPC-DCOM vulnerability. The bots were then directed to a password-protected IRC server, where they connected, logged in, and waited for instructions. When instructed to do so by Mr. Clark and his accomplices, the bots launched DDoS attacks at computers or computer networks connected to the Internet. Mr. Clark personally commanded the bots to launch DDoS attacks on the nameserver for eBay.com. As a result of these commands, Mr. Clark intentionally impaired the infected computers and eBay.com.
Mr. Clark’s case was investigated by agents of the U.S. Secret Service’s Electronic Crimes Task Force. The effort was overseen by the U.S. Attorney’s Office’s Computer Hacking and Intellectual Property (CHIP) Unit.
Farid Essebar
Farid Essebar, 18, of Morocco, is the author of the Zotob worm. Essebar is facing charges in Morrocco that he released the Zotob worm that crippled the world’s banks and medical companies.
Christopher Maxwell
Botnets can cause unintended damage. This was the case with Christopher Maxwell, aka “donttrip,” 20, of Vacaville, California. According to the DOJ press release announcing his conviction, in January 2005, as his botnet searched for additional computers to compromise, it infected the computer network at Northwest Hospital in Seattle. The increase in computer traffic as the botnet scanned the system interrupted normal hospital computer communications. These disruptions affected the hospital’s systems in numerous ways: Doors to the operating rooms did not open, pagers did not work, and computers in the intensive care unit shut down. According to the DOJ press release (www.usdoj.gov/criminal/cybercrime/maxwellPlea.htm), Maxwell pled guilty to “conspiracy to intentionally cause damage to a protected computer and to commit computer fraud,” and “intentionally causing or intending to cause damage to a protected co-conspirators created the botnet with over one million clients to fraudulently obtain commission income from installing adware on computers without the owners’ permission. The government estimates that Maxwell and friends earned approximately $100,000 from this venture. Maxwell’s bot damaged 400 DoD computers at Germany’s Department of Defense (DoD). He was ordered to pay the hospital and the DoD restitution in the amount of $252,000 and sentenced to 37 months in federal prison.
Jeffrey Parson
In August of 2003, Jeffrey Parson released a variation of the Blaster Worm, which infected 48,000 computers worldwide. According to a U.S. Department of Justice press release (www.usdoj.gov/criminal/cybercrime/parsonSent.htm), “Parson admitted that he created his worm by modifying the original MS Blaster worm and adding a mechanism that allowed him to have complete access to certain infected computers. Parson then infected approximately fifty computers that he had previously hijacked with his worm. From those fifty computers, Parson’s worm spread to other individual computers. Parson’s worm then directed those infected computers to launch an attack against a Microsoft Web site. Attorneys for the government calculate that more than 48,000 computers were infected by Parson’s worm.”
Parson was sentenced to 18 months in jail, three years of supervised release, and a restitution amount dependent on his observance of the conditions of supervised release. From the DOJ press release, “In sentencing Parson to eighteen months, Judge Pechman said she considered his unique circumstances: that he was just three weeks past his 18th birthday when he released the worm, his history of mental illness, and that his parents had failed to monitor or guide him on his computer activities. Pechman told Parson his community service had to be through face-to-face contact with others and restricted his use of computers to only educational and business purposes. She told him, ‘No video games, no chat rooms. I don’t want you to have anonymous friends; I want you to have real world friends.’ She also stressed that part of Parson’s supervised release would involve a mental health program.
The pattern that you can see in these criminal and civil prosecutions is that the punishment doesn’t appear to fit the crime. In most cases here, there was no record of sentencing.
The Industry Responds
At the TechEd 2006 conference in Boston, Microsoft confirmed that “well-organized mobsters have established control [of] a global billion-dollar crime network using keystroke loggers, IRC bots, and rootkits,” according to “Microsoft: Trojans, Bots Are ‘Significant and Tangible Threat,’” an article by Ryan Naraine in the June 12, 2006, edition of eWEEK.com. Microsoft is basing this conclusion on data collected by its Malicious Software Removal Tool (MSRT). The article says that MSRT has removed 16 million instances of malicious code on 5.7 million unique Windows systems. Sixty-two percent of these systems were found to have a Trojan or bot client.
The Alliance Against IP Theft, an organization in the U.K., published a document titled “Proving the Connection—Links between Intellectual Property Theft and Organised Crime” (www.allianceagainstiptheft.co.uk) that supports Microsoft’s claim.
On August 10, a group of information security professionals, vendors, and law enforcement gathered at Cisco Headquarters in San Jose. With little notice, the “Internet Security Operations and Intelligence Workshop” attracted around 200 attendees. Led by the enigmatic Gadi Evron (security evangelist for Beyond Security and chief editor of the security portal SecuriTeam), speaker after speaker painted a bleak and complex picture. Many lamented the increasing ineffectiveness of the prevailing strategy, which focused on identifying and taking out C&C servers. This is the “kill the head of the snake” approach. Bots have begun to evolve beyond this weakness now. Some now have multiple C&C servers, and, like a Hydra, if you cut off one C&C server, two more pop up. Some used protocols that lend themselves to a more decentralized organization. Some are using “Fast Flux” DNS technology (see Chapter 3) to play an electronic version of the shell game with the C&C server. There was much wailing and gnashing of teeth by the security and network professionals. However, amidst the lamentations, some very interesting and innovative ideas were presented.
These ideas involve different methods of detecting botnets, aggregating this information, and sharing it for the benefit of all. Some ideas were so tempting that participants began trying out aspects of the idea during the presentation. When all was said and done, 200 minds knew what only a handful knew before. Further, a “call to action” had been issued. Come out of our shell, share what we know, organize our responses.
Summary
Botnet technology is the next killer Web application. It is a tremendous force multiplier for organized crime. The money from organized crime has created a fertile technology incubator for the darkside hacker. The problem they have created is huge, global in scope. Their primary victims targeted to become clients are the innocents, the elderly, the young, and the non-computer literate. Many of the botherder schemes also target this defenseless group. The appetite for power doesn’t stop there. In the DDoS attack, bots have grown big enough to be a threat to major corporations and even nations.
Bot technology has evolved from simple agents that played games with users to mercenary robotic armies without morals, ready to carry out designer crimes on demand. From “Hunt the Wumpus” we now have botnets that collect information about customers of a specific bank, then target those customers with special botclients that contain features designed to defeat or bypass that bank’s security. Today’s bots are easy to customize, modular, adaptive, targetable, and stealthy. They are moving to a more decentralized approach and diversifying their C&C techniques.
Law enforcement has begun to catch and arrest some botnet developers and operators. The Microsoft bounty fund has proven useful in improving law enforcement opportunities to find the bad guys. Unfortunately, the court system is in serious need of change. Investigations take months for crimes that are over in seconds. Cases drag out for years, so much so that the affected businesses cannot afford to support prosecution efforts. The penalties being given are rarely more than a slap on the wrist, if anything at all is done. In many cases the arrested individual trades information for little or no punishment. The public reporting of light sentences and fines sends the message that crime does indeed pay and that you will likely never have to pay the piper.
In May of 2006, news articles were trumpeting the success of efforts by security and network professionals in taking down C&C servers around the world. By August, the headlines had changed to claims that we’ve already lost the botnet war. The hacker community responded to the security strategy of taking down C&C servers by reducing their dependence on a single C&C server. They’ve shifted their approach by creating multiple C&C servers and by employing “fast flux” DNS. By changing their architecture, they decimated the effectiveness of our best weapon. Many of us had been touting the slogan “cut off the head of the snake.” The network and security professionals had been moving to implement a large-scale implementation of that in May. In hindsight, the war wasn’t lost, although it was a significant battle. This war will never be won or lost. The war between good and evil, like the road, goes ever on.
Instead of declaring surrender, a call to action has been issued. Network and security professionals gathered in August of 2006, with follow-on meetings planned throughout 2007. In these meetings, a clearer view of the problem is emerging. Innovations are being shared and improved upon. For the new threat, new strategies and tools are being forged. The remainder of this book will bring you up to speed to join the battle.
Solutions Fast Track
The Killer Web App
![]() The botnet is modular—one module exploits the vulnerabilities it finds to gain control over its target.
The botnet is modular—one module exploits the vulnerabilities it finds to gain control over its target.
![]() A botnet is adaptive; it can be designed to download different modules to exploit specific things that it finds on a victim.
A botnet is adaptive; it can be designed to download different modules to exploit specific things that it finds on a victim.
![]() Botnet attacks are targetable. That is, the hacker can target a company or a market sector for these attacks.
Botnet attacks are targetable. That is, the hacker can target a company or a market sector for these attacks.
How Big Is the Problem?
![]() Since January 2005, Microsoft has been delivering the Windows Malicious Software Removal Tool to its customers. After 15 months, Microsoft announced that it had removed 16 million instances of malicious software from almost six million unique computers. According to the Microsoft report “Progress Made, Trends Observed,” bots represented a majority of the removals.
Since January 2005, Microsoft has been delivering the Windows Malicious Software Removal Tool to its customers. After 15 months, Microsoft announced that it had removed 16 million instances of malicious software from almost six million unique computers. According to the Microsoft report “Progress Made, Trends Observed,” bots represented a majority of the removals.
![]() If left unabated, the botnet plague could threaten the future of the Internet, just as rampant crime and illegal drug use condemn the economic future of real neighborhoods.
If left unabated, the botnet plague could threaten the future of the Internet, just as rampant crime and illegal drug use condemn the economic future of real neighborhoods.
![]() In March of 2006, McAfee was called in to, in essence, reclaim a Central American country’s telecommunications infrastructure from a massive botnet.
In March of 2006, McAfee was called in to, in essence, reclaim a Central American country’s telecommunications infrastructure from a massive botnet.
The Industry Responds
![]() At the TechEd 2006 conference in Boston, Microsoft confirmed that “well-organized mobsters have established control [of] a global billion-dollar crime network using keystroke loggers, IRC bots, and rootkits,” according to “Microsoft: Trojans, Bots Are ‘Significant and Tangible Threat,’” an article by Ryan Naraine in the June 12, 2006, edition of eWEEK.com.
At the TechEd 2006 conference in Boston, Microsoft confirmed that “well-organized mobsters have established control [of] a global billion-dollar crime network using keystroke loggers, IRC bots, and rootkits,” according to “Microsoft: Trojans, Bots Are ‘Significant and Tangible Threat,’” an article by Ryan Naraine in the June 12, 2006, edition of eWEEK.com.
![]() Some bots now have multiple C&C servers, and, like a Hydra, if you cut off one C&C server, two more pop up.
Some bots now have multiple C&C servers, and, like a Hydra, if you cut off one C&C server, two more pop up.
The following Frequently Asked Questions, answered by the authors of this book, are designed to both measure your understanding of the concepts presented in this chapter and to assist you with real-life implementation of these concepts. To have your questions about this chapter answered by the author, browse to www.syngress.com/solutions and click on the “Ask the Author” form.
Q: Have we lost the war of the botnets?
A: No. Until 2006, security and network professionals had not truly engaged the enemy. For the most part we saw victim response. When the victim was big, the response was big. 2005-2006 marks the beginning of efforts to coordinate larger responses to the threat. Up to this point, many security professionals had not made the connection that these attacks were being fueled by money from organized crime. Now that the connection to organized crime has been made, the playing field is forever altered. Law enforcement and other government agencies are now joining the fight. Several consortiums have emerged to gather, aggregate, and distribute information as well as to coordinate responses. The battle has only begun.
Q: How much is the Microsoft bounty for virus authors and how do I get me some?
A: In 2003, Microsoft established a $5 million antivirus reward program.
Microsoft periodically announces that it is offering a bounty for information leading to the arrest and conviction of authors of a specific virus. Rewards of $250,000 have been paid for the creator of the Sasser worm. Today, awards are posted for the authors of the SoBig virus and the Blaster worm. If you have information about a virus that Microsoft has offered a bounty for, you should contact law enforcement. From the Microsoft Q&A page regarding the bounty (www.microsoft.com/presspass/features/2003/nov03/11-05AntiVirusQA.mspx) “Persons with information should go directly to the law enforcement agencies by calling their local FBI (www.fbi.gov/contact/fo/fo.htm) or Secret Service office, or the Interpol National Central Bureau (www.interpol.int) in any of Interpol’s 181 member countries, or by going to the FBI Internet Fraud Complaint Center Web site (www.ic3.gov).” The Microsoft Web page for information about current rewards is located at www.microsoft.com/security/antivirus/default.mspx.