Chapter 10 Using Sandbox Tools for Botnets
Introduction
There are several ways to obtain information about botnets and in particular the bot applications seen in the previous chapters, especially in Chapters 5 and 7. One approach to analyzing this kind of software and learning more about its internals and the underlying communication method and infrastructure is to execute them in a so–called sandbox.
Sandboxes are a common concept in computer security and are used to execute program code that comes from unverified or untrusted sources. A sandbox offers a monitored and controlled environment such that the unknown software cannot do any harm to the real hosting computer system. This can be achieved by blocking some critical operations but permitting other operations while monitoring them. Alternatively, you could implement a complete virtual environment where processor, memory, and the file system are simulated and the real system is not accessible for the tested application. In malware analysis, the main aspect of a sandbox normally is not to block accesses to the system resources but to monitor those accesses. Usually a virtual machine or some other mechanism is used, by which the system can be brought back into a clean and uninfected initial state after an analysis run, so the protection of the underlying system is not so important. This form of analysis is called behavior analysis, in contrast to code analysis, where the program instructions are examined with the help of a disassembler or a debugger.
There are several software tools that perform such behavior analysis by executing a sample in some form of sandbox, which monitors the performed actions and then creates an analysis report of these actions. One candidate is the Norman SandBox, which was developed by Norman ASA, a Norwegian company that has specialized in data security. Norman simulates a whole computer system and a connected network. The implementation details and a description of the underlying technology can be found in the company’s Sandbox Whitepaper.1. A live version of the sandbox is online at http://sandbox.norman.no/live.html, where everyone can submit malware samples and get an analysis report by e-mail.
Another product is TTAnalyze, developed by Ulrich Bayer of Ikarus Software GmbH, in cooperation with the Technical University of Vienna. TTAnalyze uses the PC emulator QEMU to run a complete Windows operating system inside of it. In this emulated system, the technique of API hooking (a technique described later in this chapter) is used to monitor the malware’s interesting system calls. Decoupling from the network has the advantage that the malware is not able to infect other computers, but there also is the disadvantage that less information can be collected, because no real outgoing connection can be established.
Chas Tomlin has chosen a different approach with his Sandnet. In Sandnet, the malicious software is executed on a real Windows system, not on an emulated or simulated one. After 60 seconds of execution, the host is reset and forced to reboot from a Linux image instead of its actual Windows OS. For that purpose, Preboot Execution Environment (PXE) is used: a mechanism for booting a computer via its network interface independently of an available data storage device or operating system. After booting Linux, the Windows partition is mounted and the registry hives are extracted, as well as the complete file list. They are sent to a different analysis host for further examination. After that, the Windows partition is reverted to its initial clean state using PartImage. (PartImage is a utility to save/restore hard disc partitions to/from an image file. For more information go to www.partimage.org.) Because Chas Tomlin’s Sandnet focuses on network activity, several dispositions are made. During the execution of the malware, the Windows host is connected to a virtual Internet with an IRC server running that positively answers all incoming IRC connection requests. Furthermore, all packets are captured to examine all other network traffic afterward. The collected packets are parsed using Perl scripts for known protocols such as IRC, DNS, and HTTP, and the relevant information is extracted.
A similar method is used in Truman, The Reusable Unknown Malware Analysis Net, provided by Joe Stewart from SecureWorks. (For more information go to www.lurhq.com/truman.) It consists of a PXE bootable Linux client based on Chas Tomlin’s PXE Windows Image using Linux and a set of additional tools. (For more information visit www.wiul.org.) The malware sample is also executed on a real Windows system, which is connected to a virtual Internet. After the sample’s execution, the Truman tools are used to dump the system’s memory and its file system contents. Then a different analysis machine is able to examine the dumps and compare them against the initial system state. More information on Truman can be found at www.lurhq.com/truman.
Finally, there is CWSandbox, a result of the diploma thesis of Carsten Willems that is being further improved and is still under development. A free research version as well as a commercial one can be retrieved from Sunbelt Software. More information and a live sandbox can be found at www.cwsandbox.org and www.sunbeltsandbox.com.
In the following sections of this chapter we describe malware analysis using the CWSandbox tool. First we introduce the general sandbox architecture and its components. Then a sample analysis report for a very simple bot application is presented and explained. After that, we give a detailed description of how to use the sandbox in real malware analysis as well as giving a lot of useful and real examples of many different malicious actions that usually are performed by a bot. That part of the chapter will give you the knowledge and ability to read an analysis report and identify the important malicious internals of the analyzed bot software. Finally, we present some results we have achieved on our live sandbox systems by successfully analyzing more than 10,000 malware samples.
Describing CWSandbox
CWSandbox is an application for the automatic behavior analysis of malware. This dynamic analysis is performed by executing the malicious application in a controlled environment and catching all its relevant calls to the Windows API. Because these API calls are used for accessing Windows system resources such as files, the registry, or the network, all the malware’s actions can be examined. In a second step, a high–level summarized report is generated from this monitored data. Since one focus lies in the analysis of bots, a big effort is spent to extract and evaluate the network traffic data.
To give an intuitive image of the sandbox in advance, let’s look at a short example. It shows the analysis of a bot application that was collected by a honeypot. We will use this bot as a basic example in this chapter because it is a simple one but comprises most of the techniques and actions that are characteristic of most of the bots currently available. It is named Backdoor.IRCBot.S by BitDefender, BackDoor.Generic4.VT by AVG, and Backdoor.Win32.IRCBot.yc by Kaspersky. Because of the nature of its origin, the name chosen by us is based on its MD5 hash value; therefore, it is 82f78a89bde09a71ef99b3cedb991bcc.exe. To start analysis in CWSandbox, the following command is used:
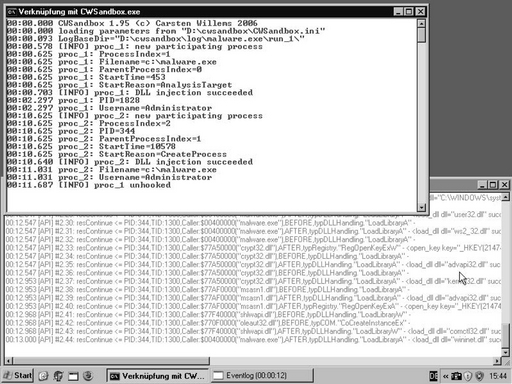
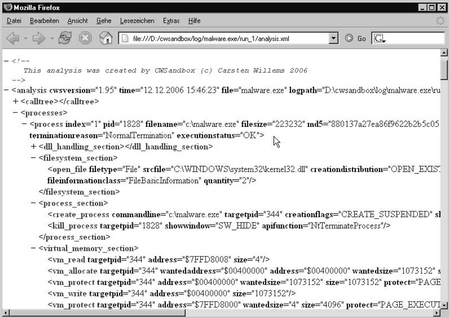
The sandbox then starts the malware and monitors its actions by inspecting the API calls it performs. Figure 10.1 shows an example output of this execution. The upper main console window prints out information about the malware process and about all new processes that were started or injected. The lower event log window gives information about each monitored API function that was called by one of them. After a customizable time, all participating malware processes are terminated or stopped. Finally, a summarized and high–level XML analysis report is created from the collected data. The analysis report contains a separate section for each process that was involved and for each of them several subsections that contain actions of a particular type. For example, there is one subsection for accesses to the file system, one for accesses to the registry, and another for the performed network operations. Figure 10.2 shows an extract of such an XML report.
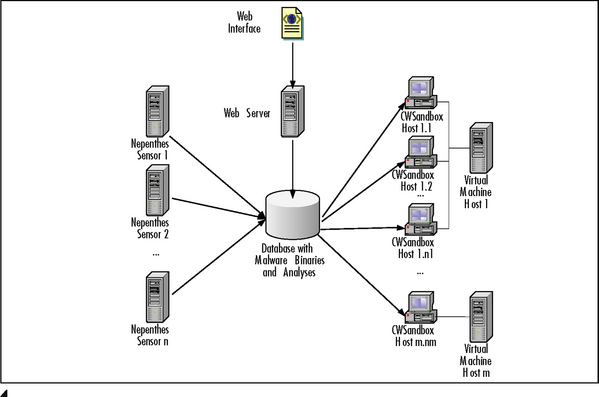
CWSandbox is not only used to create analysis reports for single malware samples; but also integrated into a bigger system, the Automated Analysis Suite (AAS). This suite consists of several software components and is used to collect and analyze malware automatically. You can see a schematic overview of the AAS in Figure 10.3. All its components are arranged around a central database, which holds the malware sample files and the resulting analysis reports. This database is filled by manual malware submission via a Web interface or by automatic collection via Nepenthes sensor hosts. Of course, the malware submission interface can also be used by other collecting mechanisms, but currently this is done only via Nepenthes. On the other side there are one or more CWSandbox hosts, where the actual analysis is performed. On such a host an instance of CWSandbox is running, periodically querying the database for new samples. If a new one is found, it is downloaded and an analysis is started on it. Afterward the resulting report is written back to the database and the system is brought back into a clean state. Therefore, on our live systems most of the CWSandbox hosts are realized as virtual machines that run under VMWare, but this is only for convenience reasons. All you need is a mechanism to reset the CWSandbox host back to a clean initial state after a performed analysis. Accordingly, this also can be done using applications like DeepFreeze, a hardware restore solution, or using a dual–boot or network-boot system. For more information on DeepFreeze visit www.faronics.com/html/deepfreeze.asp.
Detecting a Virtual Machine
Using virtual machines for malware analysis has become very popular today due to that fact a lot of malicious applications try to detect if they are running in such a virtual environment. Depending on the virtualization software, the malware can check for different characteristics, including specific registry entries, the list of running processes or system services, or typical system behavior. Especially for the often used product VMWare, there are many public known detection methods. The site www.trapkit.de presents a lot of them and offers the tools scoopy doo and jerry for that purpose. A generic approach to VM detection has been presented by Joanna Rutkowska under the name redpill. It is based on retrieving the address of the Interrupt Descriptor Table (IDT), a nonprivileged instruction that also can be called from user mode applications. Because the IDT address retrieved when running in a virtual machine is different from that in a real system, we can easily use this for VM detection. The best thing about this trick is that it works with any virtualization software. As newer CPU generations offer real virtualization support, we can only hope that in future VM detection will become impossible or at least (and most probable) much more difficult.
Describing the Components
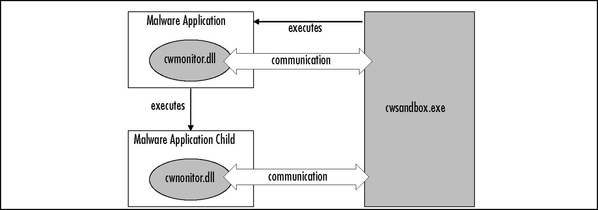
In this section we describe the functionality and components of CWSandbox in detail. The sandbox itself consists of two different executables: cwsandbox.exe and cwmonitor.dll. The first one is the main application, which starts the malware and controls the whole analysis process, and the second one is a dynamic link library (DLL), which is injected into all monitored processes. During the execution of the malware, the DLL intercepts at each critical API call and informs the main application of it. Depending on the type of system call, it either waits for the sandbox to decide how to continue, delegates control to the originally called API function, or simply returns to the malware with a simulated or error result. Besides monitoring, the DLL also has to ensure that whenever the malware starts a new process or injects code into an already running one, the sandbox is informed of that. In that case a new instance of the DLL is injected into that newly created or already existing process, so that this process also can be monitored. A schematic of this architecture is given in Figure 10.4.
As mentioned, the monitoring DLL informs the sandbox about each performed API call, which in fact is done by sending a notification to it. These notifications include a lot of information, like the name of the called API function, the used parameters, or the time when the call occurred. Depending on the type of the function, a different TNotification class is used. Subclasses for the following categories exist:
![]() TNotification_COM Used for API calls that create COM objects
TNotification_COM Used for API calls that create COM objects
![]() TNotification_DLLHandling Used for API calls that load/unload a DLL or that dynamically determine the entry points of API functions (used during explicit linking)
TNotification_DLLHandling Used for API calls that load/unload a DLL or that dynamically determine the entry points of API functions (used during explicit linking)
![]() TNotification_FileSystem Used for API calls that access the file system
TNotification_FileSystem Used for API calls that access the file system
![]() TNotification_ICMPPacket Used for API calls that send ICMP packets
TNotification_ICMPPacket Used for API calls that send ICMP packets
![]() TNotification_INIFile Used for API calls that use the Windows built–in methods to access .ini files
TNotification_INIFile Used for API calls that use the Windows built–in methods to access .ini files
![]() TNotification_Mutex Used for API calls that create or access mutex objects
TNotification_Mutex Used for API calls that create or access mutex objects
![]() TNotification_Network Used for API calls that use the Windows built–in network methods, such as for accessing Windows shares
TNotification_Network Used for API calls that use the Windows built–in network methods, such as for accessing Windows shares
![]() TNotification_Process Used for API calls that perform actions on processes, such as creating, terminating, or opening a process
TNotification_Process Used for API calls that perform actions on processes, such as creating, terminating, or opening a process
![]() TNotification_ProtectedStorage Used for API calls that perform accesses on the Protected Storage, which is a Window Service for storing authentication data of applications or Web sites
TNotification_ProtectedStorage Used for API calls that perform accesses on the Protected Storage, which is a Window Service for storing authentication data of applications or Web sites
![]() TNotification_Registry Used for API calls that access the registry
TNotification_Registry Used for API calls that access the registry
![]() TNotification_Service Used for API calls that access Windows Services
TNotification_Service Used for API calls that access Windows Services
![]() TNotification_System Used for API calls that perform system functions, such as rebooting the system
TNotification_System Used for API calls that perform system functions, such as rebooting the system
![]() TNotification_SystemInfo Used for API calls that query system information, such as querying the current user
TNotification_SystemInfo Used for API calls that query system information, such as querying the current user
![]() TNotification_Thread Used for API calls that perform actions on threads, such as creating or terminating
TNotification_Thread Used for API calls that perform actions on threads, such as creating or terminating
![]() TNotification_User Used for API calls that use the Windows built–in user management functions, such as creating or deleting a user
TNotification_User Used for API calls that use the Windows built–in user management functions, such as creating or deleting a user
![]() TNotification_VirtualMemory Used for API calls that access another process’s virtual memory
TNotification_VirtualMemory Used for API calls that access another process’s virtual memory
![]() TNotification_Window Used for API calls that access the currently existing windows, such as to find a window with a given title or class name
TNotification_Window Used for API calls that access the currently existing windows, such as to find a window with a given title or class name
![]() TNotification_WinSock Used for API calls that perform WinSock operations
TNotification_WinSock Used for API calls that perform WinSock operations
There is a focus on analyzing the network connections and the traffic data. For that reason the transferred data is inspected and an attempt is made to determine the underlying Web protocol. At the moment, the following protocols are understood: Hypertext Transport Protocol (HTTP), File Transfer Protocol (FTP), Simple Mail Transfer Protocol (SMTP), Internet Relay Chat Protocol (IRC), and the Ident Protocol (IDENT). Connections that use RFC-conform messages and slightly modified versions of them are automatically detected, and all the protocol-dependent data, such as the login information, downloaded Web sites, or performed FTP commands, is extracted. If an SMTP connection is detected, the CWSandbox can be instructed to trick the malware such that only informational requests are sent to the remote SMTP server instead of real mail delivery. That way, the malware thinks it is working with a proper SMTP server. All the information about outgoing e-mail can be monitored, whereas no actual e-mail is sent at all.
Cwsandbox.exe
The cwsandbox.exe is a noninteractive console application; it expects, and needs, no user input during its execution. The only possible input is Ctrl + C, which is the standard Windows shortcut for terminating console applications. If termination is not ended prematurely using this shortcut, the sandbox runs until all malware processes have terminated, a custom timeout is reached, or some critical event has occurred that requires an instant termination of the malware processes. During its runtime the following tasks are performed:
![]() The malware process is started in suspended mode, such that the process object is created and all modules are loaded, but no single instruction is executed yet.
The malware process is started in suspended mode, such that the process object is created and all modules are loaded, but no single instruction is executed yet.
![]() The cwmonitor.dll is injected into this new process.
The cwmonitor.dll is injected into this new process.
![]() Runtime options and information are exchanged with this DLL.
Runtime options and information are exchanged with this DLL.
![]() Throughout the execution, notifications are received from the DLL inside each monitored process; depending on the received notification, some decisions have to be made by the sandbox. The DLL then waits for these decisions and continues in the way the sandbox decided. However, in most cases no decision is needed and the DLL simply routes the call to the original API function after sending the notification.
Throughout the execution, notifications are received from the DLL inside each monitored process; depending on the received notification, some decisions have to be made by the sandbox. The DLL then waits for these decisions and continues in the way the sandbox decided. However, in most cases no decision is needed and the DLL simply routes the call to the original API function after sending the notification.
![]() After all processes have terminated or a given timeout is reached, all still running processes are terminated or the created malicious threads are stopped if their parent processes cannot be terminated safely, as is the case with essential Windows processes like winlogon.exe.
After all processes have terminated or a given timeout is reached, all still running processes are terminated or the created malicious threads are stopped if their parent processes cannot be terminated safely, as is the case with essential Windows processes like winlogon.exe.
![]() Under some circumstances, the malware is terminated before the timeout occurs—for example, to prevent serious harmful actions.
Under some circumstances, the malware is terminated before the timeout occurs—for example, to prevent serious harmful actions.
![]() A high-level analysis report is created from the collected data.
A high-level analysis report is created from the collected data.
![]() Optionally, a .cab file archive is created from all the monitored data and some additional files.
Optionally, a .cab file archive is created from all the monitored data and some additional files.
Besides monitoring the relevant API function calls, the sandbox also offers some helpful features for a manual post-processing step of the results. Some of the most important features are enabled with the configuration options STORE_CREATED_FILES and DUMP_PROCESSES. The first one provides that a copy of all newly created files is written into the .cab file. With this you can get the data of temporary files, which often are used as a source for encryption and then contain the plain text of data, which is transmitted in an obfuscated version over the network. Furthermore, this includes copies of all downloaded files, which could contain code updates or other malware files. The second option enables a functionality that creates process dumps of all monitored processes shortly before they are terminated. So, if a malware sample is compressed and/or encrypted, you will get a decompressed and decrypted version of the binary code. All process dumps are also stored in the mentioned .cab file.
Please keep in mind that the main purpose of CWSandbox is to monitor and not to block the actions of the analyzed file. This means that your local system as well as other remote systems could be infected by it, and sensitive data might be retrieved from your local host and sent to the malware operator. Furthermore, active malicious code could remain after the analysis process has finished. The sandbox tries to terminate all created processes and to stop all malicious threads that have been injected into running system services, but this is not possible in all cases, so you always should reset your system to a clean state afterward.
Cwmonitor.dll
The cwmonitor.dll is injected into each monitored process by the sandbox application. This is done automatically if the malware starts a new process or if an existing process is infected with malicious code. If a monitored process wants to perform either of these operations, the sandbox application controls this creation/injection as described here. If a new application should be started, the sandbox intercepts directly after creating the process and before executing any single operation of it. Then the monitoring DLL is injected and the newly created process is resumed only if the initialization routine of the DLL has been successfully performed. The infection of an already running process works in an analog way. If a monitored process injects code into an already running one, CWSandbox intercepts this before any single operation of the injected code is allowed to be executed. Then the monitoring DLL is injected and completely initialized. If the initialization of the DLL fails for some reason, the created process or infected thread is terminated automatically without being able to perform any single instruction.
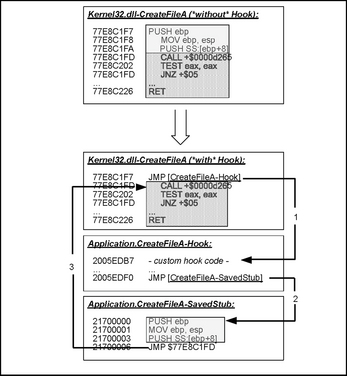
In its initialization routine, the DLL first collects some information about the hosting process, such as username or security context information. Then it sets up an interprocess communication (IPC) object to communicate with the sandbox application. Via this mechanism the collected process information is sent to the sandbox and some configuration settings are received in turn. Then function hooks are installed for all relevant API functions to intercept their calls. The technique used in CWSandbox for realizing the hook functions is called inline code overwriting (see Figure 10.5) and is described in detail later. There are several other approaches, such as Import Address Table (IAT) patching, Export Address Table (EAT) patching, or using proxy DLLs. Every hooking technique has its disadvantages and advantages, but for CWSandbox the currently used one seems to fit best for the moment.
The inline patching performed in CWSandbox works in the following way: Each Windows API function that is being used in an application is implemented in one of the Windows DLL files like kernel32.dll, advapi32.dll or ntdll.dll. These DLLs are either loaded automatically on process initialization or can be reloaded manually during runtime by one of the functions LoadLibrary, LoadLibraryEx, or LdrLoadDll. No matter how and when the DLL is loaded, at runtime the code of each API function that is called needs to reside in the virtual memory of the calling process. Accordingly, the cwmonitor.dll is able to locate these functions in memory, either by using the API function GetProcAddress or by manually parsing the EAT of the containing Windows DLL module. For catching all calls to the particular function, a JMP instruction is written to its code location as the first operation. This JMP operation is used to reroute the execution to a customized hook function.
As an example, Figure 10.5 shows an extract of the CreateFileA function from kernel32.dll, which is used to open an existing or create a new file. In the upper part of the figure, the original and unmodified version of this function is shown. The first three instructions are displayed in a light gray box, the following ones in a dark gray box. The operations from the light gray one are those which are overwritten by the JMP instruction when the hook is installed. You can see that in the lower part of the figure the first light gray box is completely missing because it has been overwritten. The following bytes from the dark gray box are not modified at all. At hook installation, before the introducing bytes of a function are overwritten, these have to be saved to some other memory location because they might be needed later to perform the original API function. In the lowest box of the figure, you can see that these bytes are copied to a location called SavedStub. Now, each time the CreateFileA function is called, first the JMP operation is executed and control is delegated (1) to the hook function (shown in the middle box of the lower figure part). If the original API should be called from inside the hook function, first the SavedStub is executed (2) and then control is transmitted back (3) to the original API function. In fact, the operations from the dark gray box, which have not been modified, are then executed. This form of API hooking is the most effective and comfortable one that can be done from user mode. But because it is detectable by the malware application, coming releases of CWSandbox will use some form of kernel mode hooking. It is also possible for an application to not use the Windows API functions at all but to perform the relevant system calls directly. This technique is hard and laborious to implement, so this usually is not done in malware.
CWSandbox will deliver no false positives, since all contents of a produced analysis report reflect operations that actually have been performed. In contrast, there always will be the risk of false negatives, since only the explicitly monitored operations will be reported. For example, applications are able to perform system calls directly instead of using the Windows API. Nevertheless, because this process is rather complicated and laborious, nearly all malware uses API calls. Unfortunately, you never can be sure that a program is clean, just because you find no malicious operations in the corresponding analysis report.
Examining a Sample Analysis Report
The result of a malware analysis in CWSandbox is an XML analysis report, which contains information about all participating processes and the actions performed by them. This document type can be read by humans as well as by machines, which makes post-processing easier. For better readability by humans, XSL templates are used to transform the XML report into HTML or plain-text documents. Nevertheless, in the following the contents of the raw XML file are described, but we also give an example of a resulting HTML report at the end of this section. In this section, we use the same sample malware file seen previously.
The <analysis> Section
Each XML report contains the root element <analysis> and its two child element sections, <calltree> and <processes>:
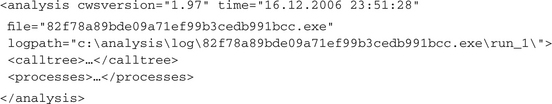
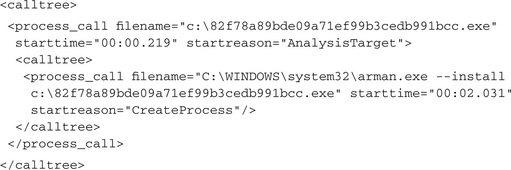
The attributes of the <analysis> element reveal several pieces of information about the particular analysis run, such as the used CWSandbox version, the date and time of the analysis, and the name of the analyzed executable. The <calltree> section covers a call tree of all monitored processes, where a father-child relationship shows that the father process has created or injected into the child process. This is the calltree for our malware sample:
From that output you can see that the initial malware process, which was created from the binary c:82f78a89bde09a71ef99b3cedb991bcc.exe, starts a new process using the command line C:WINDOWSsystem32arman.exe —install c:82f78a89bde09a71ef99b3cedb991bcc.exe. This new file c:windowssystem32arman.exe most probably was created previously by the initial process. Via the call parameters, we can see that it recently has been installed and also where the original malware file is stored. We will see in detail later what is going on inside this first process. Furthermore, you can see the relative start time points of the two processes: The first one is started only a few hundred milliseconds after the analysis starts, and the second one starts roughly after 2 seconds. From the attribute startreason we know that the first process was started by the sandbox itself and that this process has created the second one by calling a Windows API function for creating new processes, such as CreateProcess. Another possible value for this attribute is InjectedCode, which is used for those processes that were not newly created but that were already running and then injected with malicious code.
Analysis of 82f78a89bde09a71ef99b3cedb991bcc.exe
The <processes> section contains one <process> subsection with detailed information for each participating process. From the attributes of the <process> element we learn some more information about the process itself:
![]() index Each process gets its own unique process index for later identification.
index Each process gets its own unique process index for later identification.
![]() pid The process identifier that is assigned by the operating system.
pid The process identifier that is assigned by the operating system.
![]() filename The filename from which the process initially was created.
filename The filename from which the process initially was created.
![]() filesize The size of this process file.
filesize The size of this process file.
![]() md5 The MD5 hash value of this process file.
md5 The MD5 hash value of this process file.
![]() username The username of the security context the process is running within.
username The username of the security context the process is running within.
![]() parentindex The index of the parent process that has started this one; the value 0 indicates that the process was started by the sandbox application.
parentindex The index of the parent process that has started this one; the value 0 indicates that the process was started by the sandbox application.
![]() starttime The relative time when the process was started or injected, as described in the <calltree> section.
starttime The relative time when the process was started or injected, as described in the <calltree> section.
![]() endtime The relative time when the process was terminated; from the difference between starttime and endtime you can know the overall execution time of this process.
endtime The relative time when the process was terminated; from the difference between starttime and endtime you can know the overall execution time of this process.
![]() startreason The reason this process was monitored as described in the <calltree> section.
startreason The reason this process was monitored as described in the <calltree> section.
![]() terminationreason The reason the process was terminated. NormalTermination means that the process has terminated by itself. Another possible value would be Timeout, which means that the sandbox has terminated this process at the end of the specified maximum analysis duration time.
terminationreason The reason the process was terminated. NormalTermination means that the process has terminated by itself. Another possible value would be Timeout, which means that the sandbox has terminated this process at the end of the specified maximum analysis duration time.
![]() executionstatus Normally this attribute has the value OK; if for some reason the process could not be started—for example, because it is no valid Win32 application—the value CouldNotCreateProcess is used.
executionstatus Normally this attribute has the value OK; if for some reason the process could not be started—for example, because it is no valid Win32 application—the value CouldNotCreateProcess is used.
The <process> element always contains several sections, which describe all the actions performed during the execution of this process. For each of the possible TNotification objects, a separate section is included, if such notifications have been monitored during the execution. In the following, some interesting extracts from these sections are shown and explained. Notice that sometimes we have skipped several notifications or left out some of their attributes for better readability.
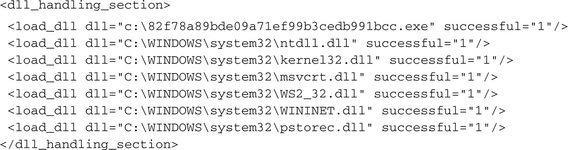
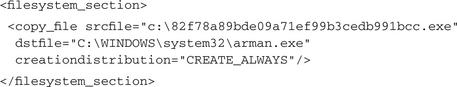
The upper section gives us information about the loaded modules of the malware process. It starts with the particular malware image file, followed by the Windows standard libraries ntdll.dll and kernel32.dll, which are loaded into each Windows user process. From the information that msvcrt.dll is loaded, we can know (or at least assume) that the malware is written in C, since it is the standard runtime library for Microsoft C applications. As the libraries ws2_32.dll and wininet.dll are loaded, we know that the malware is going to use the Winsock library to set up outgoing or incoming TCP/IP connections. Because the examined malware file is a bot application, this is not amazing. From the fact that pstorec.dll is loaded, we can assume that the malware is going to access the Protected Storage, most probably for stealing some authentication data stored within it. In the next analysis section you can see what we already assumed before: The malware copies itself to the Windows system directory using the destination filename arman.exe:
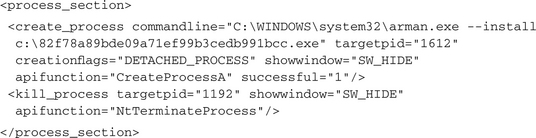
The following outputs show us that a new process is started from this created arman.exe file. We see that the new process should be created without showing the main window: showwindow=“SW_HIDE”. Furthermore, we are informed that the API function CreateProcessA was used for that purpose. The notification <kill_process> approves the fact that the malware process terminates itself after starting its copy from the Windows system directory.
That is all for the first process, and this is exactly what we see for the most of these simple bots: On their first start, they simply copy themselves to the Windows directory, then they execute this new copy and terminate the initial application.
Analysis of Arman.exe
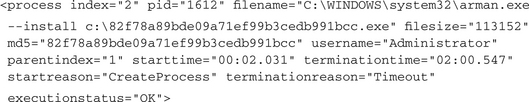
Let’s now take an intensive look at the actions of the second process, which promises more interesting results:
We know that this process is created from the same binary, only from a different location. Therefore, the MD5 and the file size have the same values as for the first one. From the values of the attributes parentindex and startreason we know that the execution was initiated by the first process. The terminationreason tells us that this second process did not terminate itself but would have continued to execute if the sandbox application had not terminated it at the end of the analysis.
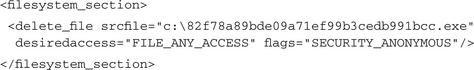
Here we can see the probable reason for the second command-line parameter of arman.exe: It is used to inform the application where the original malware file can be found for deleting it. We do not know the regular distribution mechanism of this bot. Since it was collected by a honeypot, we can assume that it is usually copied to a remote host after this host has been exploited. Depending on the exploit used, the malware file would be copied to a temporary or application-dependent directory. The existence of an .exe file in such a folder would raise suspicion or it would be deleted automatically due to some system cleanup routine. Therefore, in nearly all cases we have seen, malware first copies itself to the Windows folder and then deletes the initial source file.
Many applications use named mutexes to ensure that only one instance of them is running. The funny thing about this is that very often you can learn more information about the malware from the name of their mutexes. Sometimes you can determine the malware name in the form the author has intended. Also very often you can recognize the malware family by that, since the mutex does not change from version to version or simply uses the same value plus a newer version number. The mutex of our sample probably reveals its intended name:
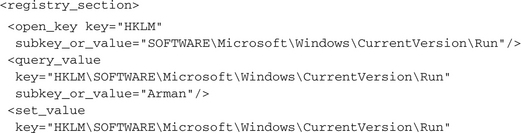
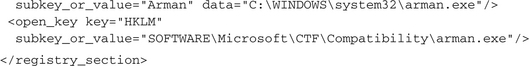
The malware opens the registry section
HKLMSOFTWAREMicrosoftWindows CurrentVersionRun, whose entries are loaded automatically on system startup. It checks whether an entry for the arman.exe file already exists. Because this is not the case, a new entry is created. After that, the malware checks whether the entry could be created successfully. This modifies the system startup sequence such that arman.exe will be started automatically each time the machine boots up:
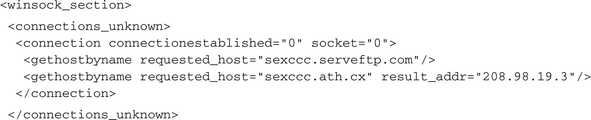
Now for the interesting stuff, namely those operations dealing with network connections. Each analysis report for malware that calls at least one Winsock operation contains a <winsock_section>. This has several subsections: one for all UDP connections, one for the incoming TCP connections, one for the allowed outgoing TCP connections, one for the blocked TCP connections, and a last one for all operations for which the underlying protocol and direction could not be determined because no indicating function was called. These latter sections normally are used for the Windows built-in DNS query functions. In our case the Winsock notifications section starts like this:
We can see that the first DNS query did not deliver an IP address. This is because at the moment of the analysis the domain name sexccc.serveftp.com was not connected to a valid IP. In contrast, the second request for sexccc.ath.cx delivers the IP 208.98.19.3, which is the address of the botnet C&C server, as we see here:
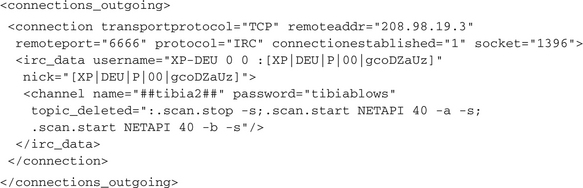
The malware initiates an outgoing TCP connection to 208.98.19.3 on port 6666, which can be established successfully. Furthermore, CWSandbox has detected (by inspecting the traffic) that the protocol used in this connection is IRC. Because of that it was able to retrieve all the protocol-dependent IRC data from the traffic stream:
![]() The parameter of the user command is XP-DEU 0 0:[XP|DEU|P|00|gcoDZaUz], which means that the username is XP-DEU, the IRC usermode is 0 and the realname is :[XP|DEU|P|00|gcoDZaUz].
The parameter of the user command is XP-DEU 0 0:[XP|DEU|P|00|gcoDZaUz], which means that the username is XP-DEU, the IRC usermode is 0 and the realname is :[XP|DEU|P|00|gcoDZaUz].
![]() The nickname is [XP|DEU|P|00|gcoDZaUz].
The nickname is [XP|DEU|P|00|gcoDZaUz].
![]() The channel ##tibia2## is joined using the password tibiablows.
The channel ##tibia2## is joined using the password tibiablows.
![]() The channel topic is :.scan.stop -s;.scan.start NETAPI 40 -a -s; .scan.start NETAPI 40 -b –s.
The channel topic is :.scan.stop -s;.scan.start NETAPI 40 -a -s; .scan.start NETAPI 40 -b –s.
![]() From the name of the attribute topic_deleted you can see that the channel topic is received but in fact not being passed to the malware; the CWSandbox can be configured in multiple ways to prevent a further processing of received bot commands.
From the name of the attribute topic_deleted you can see that the channel topic is received but in fact not being passed to the malware; the CWSandbox can be configured in multiple ways to prevent a further processing of received bot commands.
The last entries of the analysis report reveal that the malware opens a backdoor on TCP port 1910, but it is not being connected during the analysis run:
That is it for the second process of this malware analysis. We have seen the most essential operations of such simple bot applications: After it has copied itself to the Windows directory and started, this new instance deletes the original malware file, sets up an autostart registry entry, opens a backdoor, resolves the domain name of its C&C server, connects to this server, and joins the correct channel. Because we did not let the channel topic pass to the malware receiving function, its functionality stops there. An extract of the transformed HTML report of this analysis appears in Table 10.1, showing the analysis only for the second process. Again, some unimportant parts have been removed to reduce its length.
Table 10.1 Extract of a Malware Analysis
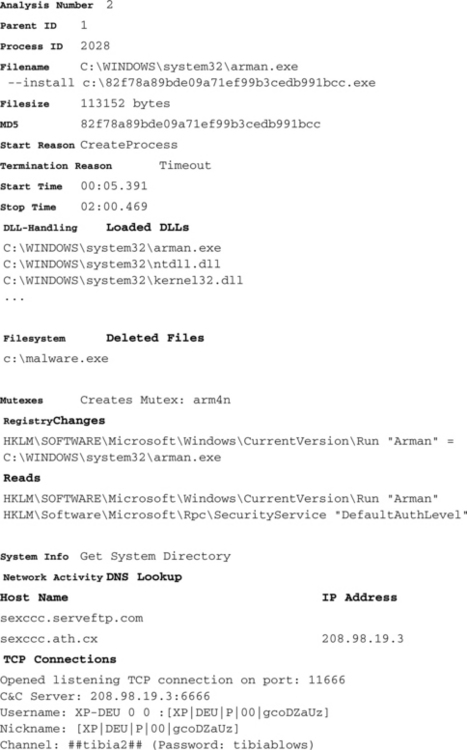
Based on the raw XML analysis report you are able to create your own customized HTML or plain-text transformation. For that you will have to create an XSL template, which contains instructions on how to parse an XML document. There exist several tools for performing the transformation. One easy way to do this is by including a line like this in the XML file (you need to use the correct filename of your XSL with the href parameter): <?xml-stylesheet type=“text/xsl” href=“templae.xsl”?>
Interpreting an Analysis Report
The results that can be obtained from the analysis of a malware application can be used mainly for two purposes: protecting and disinfecting the bot hosting client systems and destroying the functionality of the currently existing botnet. Obviously, the botnet will be left ineffective if all bots have been disabled, but because it is not possible to deactivate all bots at the same time and because there always is the risk of new infections, it is also very important to shut down the C&C server. Important analysis results that can be used for the purposes of removing and avoiding the infection of a bot application and of shutting down the botnet may be:
![]() Where does the bot application store its files on the infected system?
Where does the bot application store its files on the infected system?
![]() What mechanisms are used to automatically start the bot application at system startup?
What mechanisms are used to automatically start the bot application at system startup?
![]() How does the bot protect the infected host from infection by other malware?
How does the bot protect the infected host from infection by other malware?
![]() How does the bot protect itself from detection and removal?
How does the bot protect itself from detection and removal?
![]() How are new infectable hosts found?
How are new infectable hosts found?
![]() What exploits/mechanisms are used to infect new hosts?
What exploits/mechanisms are used to infect new hosts?
![]() How does the bot connect to the C&C server(s), and what servers are used?
How does the bot connect to the C&C server(s), and what servers are used?
![]() Where does the bot application get updates from?
Where does the bot application get updates from?
![]() What malicious operations are performed locally and remotely?
What malicious operations are performed locally and remotely?
Evidence for all these pieces of information can be obtained from an analysis report that is created by CWSandbox. In the following sections, those items are examined in detail, and extracting evidence for them from an analysis report is explained.
How Does the Bot Install?
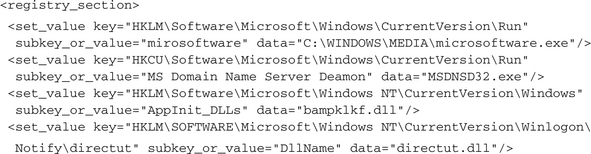
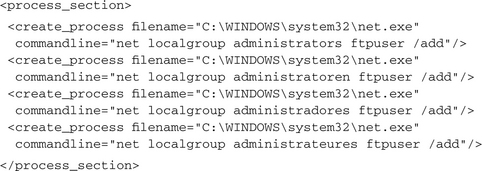
If we want to check whether a given host already is infected with a particular malware or if we want to clean a host from that parasite, we need information about the locations where the malware installs its files and about the mechanisms it uses to automatically execute at system startup. Finding the answer to the latter question normally also solves the first one, since any autostart mechanism needs the information where to find the process to start. Windows offers many different possibilities to instruct the system to execute a specific application automatically on startup. The great tool AutoRuns2. shows most of them. Though there are many ways, nearly all malware either uses one of the run sections of the registry or installs a Windows Service application or kernel driver. However, the malware needs to modify a registry setting to set up any form of autostart mechanism. CWSandbox reports all accesses to the registry, so you easily can filter out those accesses. As we already saw, registry accesses are contained in the <registry_section> and the relevant entries are <create_key> and <set_value>. Here are some examples of malware that installs as an autostart process, using different registry sections:
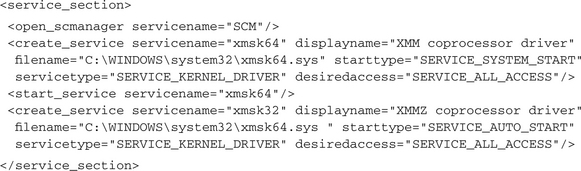
As mentioned, some bots do not install as normal programs but as Windows Service applications. In that case, beside the changes to the registry, the analysis report will contain lines like these:
A very powerful technique for infecting a system is to install a kernel device driver. Once loaded, this driver executes in kernel mode and undergoes no more security restrictions. Because it has full control over all running kernel and user mode processes, it could be very hard to detect such malware. In most cases a kernel driver implements rootkit functions to hide itself and/or to provide system backdoors. CWSandbox can be configured to forbid the installation of kernel drivers completely or to fool the installer by returning a successful error code while suppressing the real installation. In any case, the attempt to load a kernel driver can be detected by the attribute servicetype=“SERVICE_KERNEL_DRIVER” of a <create_service> notification. The analysis report section of the installing process would look like this:
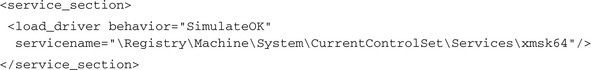
Ultimately, loading of the driver is performed by the Service Control Manager (SCM). This process is hooked automatically and, in its report section, an entry like the following will be given. From the attribute behavior=“SimulateOK” we can see that CWSandbox was configured to only simulate this call and to suppress the real loading.
Finding Out How New Hosts Are Infected
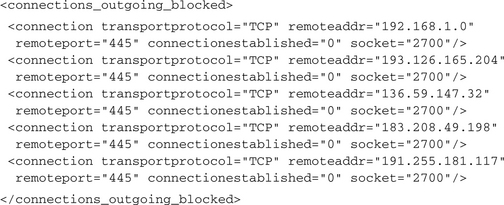
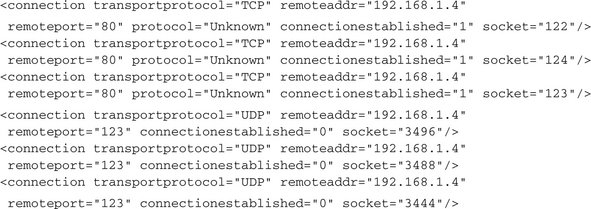
To find new infectable machines, a lot of malware probes remote hosts for known vulnerabilities. There are several strategies for determining which hosts to probe: Some malware generate random IPs, others scan complete (also randomly chosen) IP ranges. There are also applications that use predefined internal or external target lists. Internal lists are contained inside the malware binary; external ones need to be reloaded from one or multiple possible locations from the Internet. After one potential target has been determined, it is probed against one or several vulnerabilities. Since the possible exploits all work in different ways and use several different target services, it is hard to give a standard procedure of how to detect their usage from an analysis report, but some clues will always be there. In any case, a connection to a remote host needs to be established on one or more of the specific possible ports. For some ports, any attempt to establish a connection is a promising hint of an exploitation attempt. For example, although they are really old, malware still searches for known security leaks in the LSASS and the DCOM RPC Service is searched. Therefore, often you will see outgoing connections on TCP ports 135, 139 and 445. Because these ports normally are blocked by CWSandbox by default, the connection establishment attempts will be included in the <connections_outgoing_blocked>. The analysis report would include some outputs like these:
To get more information about these attempts, you should not forbid connections to those ports. Furthermore, you should configure the CWSandbox such that all communication data is logged. Even if this logging is not enabled, the .cab file will contain the content of all TCP packets that are sent or received. By examining this data, you can learn what the malware has intended by these connections.
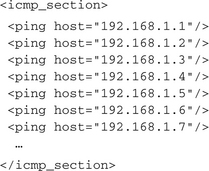
Often you will also be able to infer the host determination strategy from the reports, especially if you find complete ranges of target IPs that are trying to be connected or pinged, as in this case:
How Does the Bot Protect the Local Host and Itself?
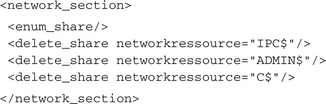
A lot of bots try to protect a new infected host against further exploitation by others. Of course, this is not being done for charitable reasons, rather for the selfish reason of trying to ensue that that no one else can take control of the host. This protection is accomplished by fixing known security leaks or by completely disabling Windows Services that can be exploited. Mostly this is done by removing existing Windows shares. In the following you can see how first all existing shares are enumerated (enum_share) and then deleted (delete_share):
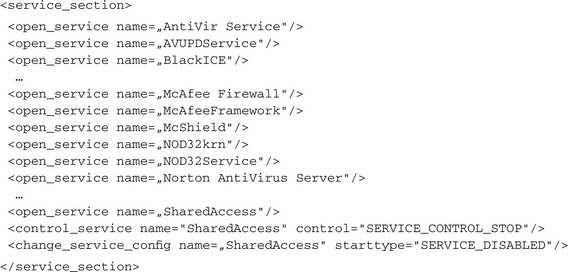
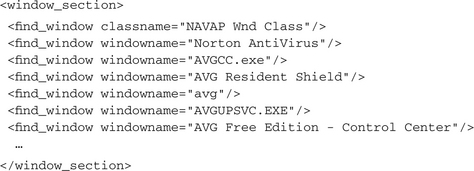
To hide and protect its own existence, most malware performs the following actions on a newly infected system: It searches for known antivirus and security products and stops them or modifies their configuration. When malware tries to detect such running security applications, it normally searches for the commonly known names of their corresponding services, processes, or windows. This can be done by either enumerating all the existing objects and then comparing each found one with the entries of an internal list or by using functions for opening a handle to a named object, providing the known name as a parameter. In the first case, you will find the actions <enum_services/>, <enum_processes/>, or <enum_window/> in your report. In the second case, long lists of actions with the known object names as parameters will appear in the analysis. The following example shows how malware looks for services of antivirus software:
You can see that the bot loops through a long list (the original output has over 50 tests) of hardwired service names. Because most of those applications are not installed on our test system, nothing more is done than just querying for those services. The last actions show us what happens if such a security service could be found: The malware stops and disables the Windows SharedAccess service, which implements the Application Layer Gateway and is the low-level service for controlling network connections. Normally this one is used for the Windows Firewall and for Internet Connection Sharing (ICS), but it also runs if neither of them is enabled. By shutting down this service, the Windows Firewall becomes inactive, but other unforeseen problems could occur.
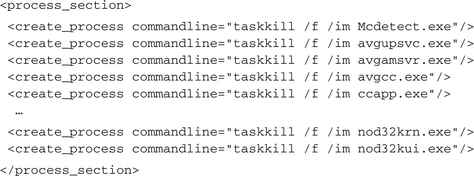
Some malware does not search for the services. Rather it tries to kill the corresponding processes. In our example, the Windows XP command taskkill is used, for which the parameter /im imagename specifies the filename of the process and /f forces its termination. Again, we present only a short extract of the real analysis report output:
As a further example, we present malware that searches for the main windows of known antivirus scanners. We do not know what would happen if a searched window would be found, but this is not very hard to guess:
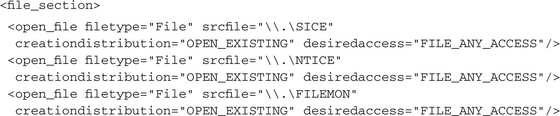
Some malware tries to find running debuggers and other activity-monitoring tools, which can be used for malware code analysis, by trying to open their devices. In our example, these are SICE and NTICE (NT version) for the Softice debugger and FileMon3. and RegMon4, the famous tools from www.sysinternals.com. Again, we do not know what would happen if one of the queried devices existed. Most probably the application would crash the system or simply not perform any of its malicious operations in order to not reveal anything.
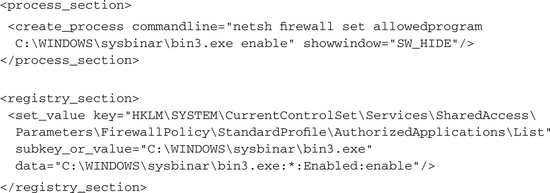
Sometimes malware does not try to stop found security services but instead to modify their configuration such that the malware is not detected or is enabled to circumvent the security mechanisms. For the Windows Firewall this could be done using the netsh command or by directly modifying the corresponding registry key:
Determining How and Which C&C Servers Are Contacted
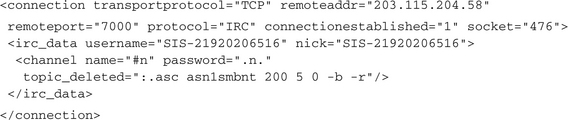
Most bots use a central C&C server for communicating with their botherder, and normally they use the standard IRC protocol for that purpose. CWSandbox detects such communication and reacts in two ways: First, all the interesting connection information is extracted from the traffic, and second, all received commands are deleted so that they never arrive at the malware’s receiving function. Some bots use slight modifications of the IRC protocol, and some modified IRC servers do not answer with RFC conforming messages or do not answer at all until the IRC client has authenticated completely. CWSandbox tries to recognize these custom protocols as well, but it is obvious that this is only possible within a certain range of modifications. Often the communications of these modified IRC servers can be read manually if the traffic-logging option is used. If an IRC communication can be detected successfully, an output like the following will be contained in the analysis report:
We see that a TCP connection was established to the host 203.115.204.58 on port 7000. Although port 7000 is not the most well known port associated with IRC (that would be port 6667), it is a common choice, along with 6665 and 6666. After authenticating itself with the username SIS-21920206516 and nickname SIS-21920206516, the client joins the channel #n using the password .n. Some IRC servers are additionally secured with a server password; in that case the value used for that would also be included in the report. Normally after joining an IRC channel, the channel topic is transmitted automatically to the client. In the case of bots, this topic is mostly used to send an initial command to the client, in this case .asc asn1smbnt 200 5 0 -b –r (see Chapter 4 for further description of commonly used bot commands). The last section of this chapter contains detailed information about the results on IRC connections, which we were able to retrieve by analyzing over 1,800 found bot samples.
How Does the Bot Get Binary Updates?
Often the first thing malware does is to retrieve new files or instructions from its operator. This is done to get code updates or actualized configuration data, since the running malware might be an outdated version or might contain the addresses of already shutdown machines. In the case of bots, this configuration data is most often received via their C&C channels, but there are also variants that try to get this data from hardwired URLs. In any case, you will see an outgoing TCP connection and/or DNS requests as evidence of such an update request. If you are lucky, the reloading of code or data is done via HTTP or FTP. In that case the report would contain outputs like this:
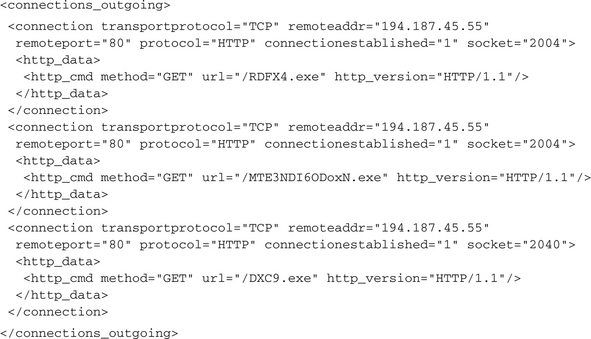
As you can see, there are several .exe files downloaded from the same host, 194.187.45.55. In fact, for this particular malware (NOD32 calls it Win32/TrojanDownloader.Adload.NAN Trojaner), a total of 10 (!) different .exe files are reloaded. After the malware has downloaded them to the local disk, they are executed:
Sometimes the malware does not use one of the standard Web protocols to reload data. Then it is harder to determine the fact that something executable or configuration data is retrieved. Again, the CWSandbox feature to log all communication data will help in this case. In any event, you should use the option STORE_CREATED_FILES, by which you will get a copy of each created file, no matter if it is an executable or data file and if it was downloaded, copied, or created completely new. All these created files can be found in the corresponding created_files subfolder inside the .cab archive. Another helpful option is FAIL_ON_ALL_DNS_REQUESTS. When you enable this one, each DNS request will fail and the malware will disclose all its internally stored remote host contact addresses.
What Malicious Operations Are Performed?
The possible malicious operations a bot could perform on the infected host and remote hosts are limited only by the imagination of its developer. It is obvious that the operations mentioned in the preceding sections are malicious as well. However, these operations are only intended to infect and secure a system. They are not intended to do harm. Once the infection process with all its side actions is finished, the bot is free to pursue its real purpose: using the hosting system to perform illegal and criminal operations, directed by its operator. Some examples of these operations are:
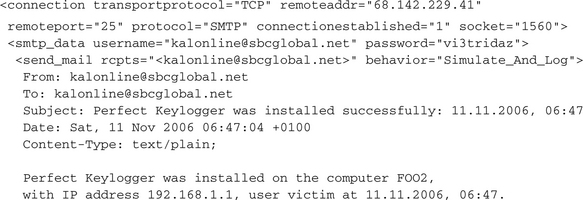
In this section we present hints for those operations that can be found in the analysis reports. We start with the detection of mail delivery. In general, an SMTP mail delivery looks like this in the report:
From this output we can learn the SMTP server (68.142.229.41), the used authentication data (username: [email protected], password: vi3tridaz) and the recipient’s mail address (<[email protected]>). Furthermore, we can read the mail body in plain text. Without doubt this is a notification mail, which is used to inform the malware operator about a new infected host. As we have seen, CWSandbox recognizes SMTP traffic and extracts all the relevant data from it. Furthermore, it can be configured to trick the malware by exchanging informational data with the SMTP server but only pretending to send the e-mail. The attribute behavior=“Simulate_And_Log” enables this feature during the malwares execution. There is another feature that constricts the number of allowed SMTP send operations to limit the report size for mass-mailing malware.
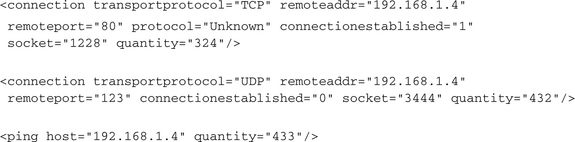
Huge botnets often are used to perform DDoS attacks. Commonly known attacks are TCP Syn floods, UDP floods, and ICMP floods. If you find a lot of notifications for such connections in your report that all use the same target IP address, this is an assured evidence of such an attack (or sometimes only of the foolishness of the malware’s developer). The relevant entries could look like the following and would have to occur in a large number:
An analysis report normally contains only one output line for each type of received notification, no matter how often this one was received. Usually a DOS attack is performed using a lot of parallel threads that use a lot of different sockets, so one notification will be reported for each different socket. If, due to bad implementation, the same socket is always used, only one notification would be reported. Therefore, it might be necessary to use the parameter SHOW_QUANTITIES_IN_REPORT. If this attribute is enabled, the quantities for each contained notification are included into the analysis report as well. In that case a (badly implemented) DOS attack would look like one of these:
A lot of malware installs backdoors on the infected host such that its operator (or whomever) is able to connect to this host remotely. The power of such backdoors ranges from simply enabling remote access to the local file system or giving a simple command shell to the attacker to offering a complete graphical interface. Remote access to the file system can easily be set up by creating a new share:
Malware could also try to escalate the security privileges of existing users such that a regular login can be used for much more powerful operations than it was intended to:
Real backdoors bind themselves to a network port and implement complete servers. Evidence for such activity can be found in the section <connections_listening>:
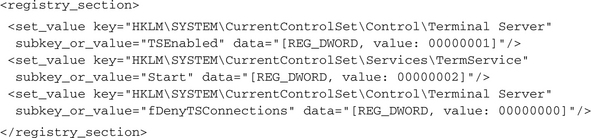
Some malware use the integrated Terminalserver of Windows to allow remote access. They modify the relevant registry settings to allow remote connections in general. In that case, you will find some lines in the report that look like these:
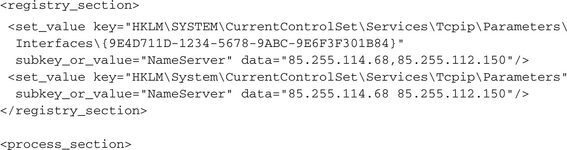
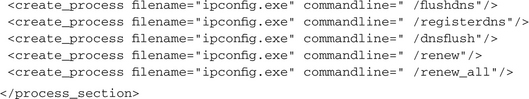
Changing the network routes or hijacking the DNS resolving process is also part of the performed evil operations. That way, the malware either completely blocks accesses to hosts that provide updates for security software or the operating system, or it routes all those requests to infected hosts. This can be performed by modifying the hosts file, which resides in the system32driversetclog directory in the Windows folder. An attempt to do so can be detected by locating an <open_file> action, which refers to that file and requests WRITE access. Some malware completely reroutes all DNS requests to a special host, which is enabled to return different IP addresses dynamically. Such a modification normally takes place in two steps: First the network configuration for the network adapter is modified by changing the relevant registry settings; then the network interface is advised to refresh its configuration. Of course, the second step is only optional. If it is not performed, the modified network configuration is activated on next system startup. The tracks of these actions will look like this:
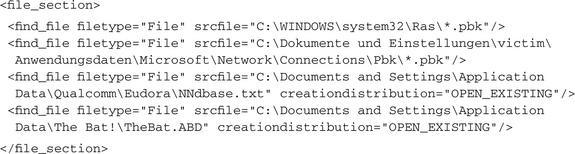
Finally, a lot of malware tries to steal sensitive data from the local host. This can be done by installing a keylogger or by directly accessing the places where such data is stored. The explicit process of keylogging is not detected by current version of CWSandbox and will be added as a new feature in coming releases. Nevertheless, because some files need to be installed as an autostart application or as a service or driver for that purpose, this will become obvious by examining the report. If the malware tries to read the data directly from its storage location, this could happen in several ways, depending on that location. Examples for retrieving dialup network configuration data and contents of address books for several mail clients are these (note that some malware uses <open_file> and other malware uses <find_file> or even <get_file_attributes> to check for the existence of such files):
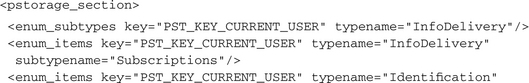
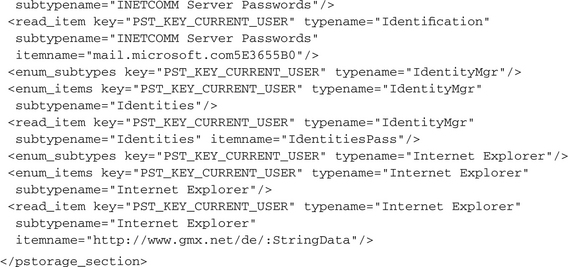
In Windows 2000 the Protected Storage Service was introduced. This is a service for storing sensitive data such as passwords or private keys in a protected and encrypted way. It is used to save the passwords that have been entered in Internet Explorer or Microsoft Outlook and Outlook Express, but it also can be used by any other user application to protect its sensitive data. For that reason it is an open treasure chest for each malicious application. CWSandbox detects all accesses to this Protected Storage and reports them in a <pstorage_section>. An example of such a report follows:
Bot-Related Findings of Our Live Sandbox
We have been running a live sandbox system at the University of Mannheim, in Germany, which consists of four CWSandbox hosts and uses a MySQL database as repository. New samples can be submitted via the Web interface at www.cwsandbox.org, but many people use scripts to transmit files automatically. In the last few months we have successfully analyzed a total of 11,965 unique malware samples. Inside this set, CWSandbox has detected 1283 programs that have successfully established an IRC connection to a remote host. From those, 108 did not follow an RFC conforming protocol but a slightly modified variant instead. Furthermore, of the others, 40 did send a TCP packet with data such as NICK (null)abcdef without having a connection established. Those probably are badly designed applications1 or some other unforeseen error occurred during their execution. Anyway, we can assume that these also are applications that implement some form of IRC communication. Finally, 492 of the rest tried to connect to a TCP server on port 6665, 6666, or 6667, which lets us assume that they were also going to initiate an IRC session. So, from the 11,965 samples, 1815 tried to or succeeded in establishing an IRC connection and, therefore, can be seen as bots or, at least, as malware that contains bot-like behavior.
Using the Live CWSandbox
A live version of CWSandbox can be accessed at the project homepage www.cwsandbox.org and at the Sunbelt ResearchCenter at http://research.sunbelt-software.com/Submit.aspx. After submitting a suspicious file, your e-mail address, and an optional comment, you simply have to wait until the analysis report is sent to you. Depending on the current file queue length and on whether the submitted malware file has previously been analyzed, this can happen immediately or take some minutes.
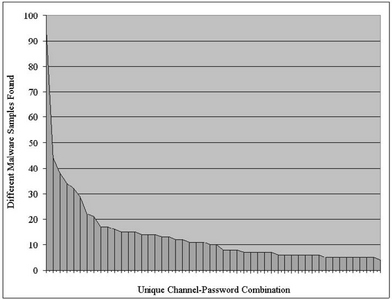
Those programs that successfully have used an IRC connection have connected to IRC servers at 317 different IP addresses and have used 120 different TCP ports. Because the IRC servers could be identified only by their IP addresses, it is possible (and probable) that, due to using dynamic DNS services, not all of these hosts are unique. We could presume that two different bot applications that connect to the same channel on the same host and use the same channel password are only two variants of one and the same malware and, therefore, belong to the same botnet. Since we have found 590 unique host-channel-password combinations, this would mean that we have found 590 different botnets. We can presume that two connections to the same channel using the same channel password but connecting to different IRC servers also belong to the same botnet. This is probable but might not hold in every case, so the number of unique botnets found decreases to 497. Figure 10.6 shows a diagram of the dispersion for the 50 most seen channelpassword combinations. The x-axis holds the different channels and the y-axis shows the number of found malware samples that connect to each channel. The top position was the channel #dd in combination with the password dpass, which we have seen 95 times, followed by #hotgirls (no password) with 44 and #i# (@d00k@) with 38 instances.
As mentioned, we have found 120 different TCP ports. Most of them appeared only once or a few times, which leads to the suspicion that these were used in malware that is only rarely spread or is a test or beta version. Of course, the most often used port is 6667 (375 times), because this is the IRC default port. At the second position comes port 8585 (89 times), followed by 7000 (86 times). But also the ports 1863, 6556, 19555, and 11640 have been seen more than 30 times each.
Keep in mind that this analysis might not be representative of what you will find. It should only give you an impression of a real, live example of a running CWSandbox system.
Summary
In general, sandboxes are to protect the local system while executing unknown or malicious code. Protection is achieved either by blocking critical operations completely or by performing them in a virtual environment instead of on the real system. In malware research the focus is not on prohibiting malicious operations but on monitoring them. In the case of CWSandbox, nearly all actions are not blocked, since the analyzed malware should behave as normally as possible. Therefore, to protect the hosting system from a permanent infection, different mechanisms can be used to roll back the modifications that have been made during the execution. Examples of such mechanisms are the application of virtualization software such as VMWare or Virtual PC, the use of reverting tools such as DeepFreeze or Partimage, or the use of hardware restore solutions.
Some sandboxes can be integrated into a bigger process of automatic malware analysis, as is done with the Norman Sandbox or CWSandbox. Both use a database to store malware samples and the resulting analysis reports and need no human interaction for performing the analysis of many malware samples consecutively. For that purpose, CWSandbox is embedded into the Automated Analysis Suite that comes with the CWSandbox software package. The suite incorporates the honeypot tool Nepenthes to not only perform the analysis but to collect and analyze malware in an automated way. Using CWSandbox can reveal the following operations performed by the analyzed malware:
![]() Reading, writing, or locating objects of the local file system, .ini files, or the registry
Reading, writing, or locating objects of the local file system, .ini files, or the registry
![]() Finding active local antivirus or security software
Finding active local antivirus or security software
![]() Starting new or terminating active applications
Starting new or terminating active applications
![]() Injecting malicious code into running processes
Injecting malicious code into running processes
![]() Reading or modifying the virtual memory of running processes
Reading or modifying the virtual memory of running processes
![]() Installing, starting, or deactivating Windows Services
Installing, starting, or deactivating Windows Services
![]() Enumerating, creating, or removing local users
Enumerating, creating, or removing local users
![]() Reading or writing data from or to the Windows Protected Storage
Reading or writing data from or to the Windows Protected Storage
![]() Enumerating, creating, removing, and modifying Windows network shares
Enumerating, creating, removing, and modifying Windows network shares
![]() Loading and unloading dynamic link libraries (DLLs)
Loading and unloading dynamic link libraries (DLLs)
![]() Querying system information, shutting down or rebooting the system, accessing mutexes, or creating threads
Querying system information, shutting down or rebooting the system, accessing mutexes, or creating threads
Moreover, all TCP/IP connections and operations on them are monitored and included in the analysis report. For an established TCP connection, CWSandbox tries to detect the used application protocol and reports all the relevant protocol-dependent data in case of success. Currently, the following protocols (and slight modifications of them) are recognized: HTTP, FTP, SMTP, IRC, and IDENT. In general, the following information is contained in the <winsock_section> of an analysis report that reflects the TCP/IP activity of the analyzed application:
![]() Querying the DNS server for address resolution
Querying the DNS server for address resolution
![]() Sending and receiving UDP data
Sending and receiving UDP data
![]() Connecting via TCP to a remote host
Connecting via TCP to a remote host
![]() Setting up a TCP server for accepting connections
Setting up a TCP server for accepting connections
![]() Accepting incoming TCP connections
Accepting incoming TCP connections
![]() For recognized application protocols, the used protocol-dependent data is displayed, such as username, password, nickname, mail receiver, mail content, and performed FTP commands
For recognized application protocols, the used protocol-dependent data is displayed, such as username, password, nickname, mail receiver, mail content, and performed FTP commands
It has turned out that the use of CWSandbox for automatic behavior analysis brings a big benefit in malware research. Nevertheless, though the received analysis results normally are very comprehensive and detailed, one has to be aware that there is never an assurance of their completeness. First, because a sandbox usually monitors only one single execution path of an application, only the actions that are performed on this path can be reported. There is no guarantee that there are no other malicious operations that are only triggered under certain conditions which were not met during the analysis run. Second, there are many tricks to either detect a sandbox or to perform operations in a way the sandbox is not able to track. Accordingly, the sandbox is a great research tool, but you should not rely completely or solely on it. Think of it as one more tool in a defense-in-depth strategy.
Solutions Fast Track
Describing CWSandbox
![]() Sandboxes are a common tool in security/malware research; they allow the execution of unknown software in a controlled, restricted, and monitored environment.
Sandboxes are a common tool in security/malware research; they allow the execution of unknown software in a controlled, restricted, and monitored environment.
![]() CWSandbox is a tool for automatic behavior analysis of Windows executables. The following steps are performed:
CWSandbox is a tool for automatic behavior analysis of Windows executables. The following steps are performed:
![]() Automated Analysis Suite (AAS) is a tool for automatic collection and analysis of malware:
Automated Analysis Suite (AAS) is a tool for automatic collection and analysis of malware:
Examining a Sample Analysis Report
Interpreting an Analysis Report
![]() The interpretation of an analysis report was explained in detail in this chapter.
The interpretation of an analysis report was explained in detail in this chapter.
![]() The races and hints of the most commonly performed malicious operations of bots are shown:
The races and hints of the most commonly performed malicious operations of bots are shown:
Bot-Related Findings of Our Live Sandbox
![]() Some (unrepresentative) results of the analysis of 11,965 malware samples at the University of Mannheim, Germany, were presented in this chapter.
Some (unrepresentative) results of the analysis of 11,965 malware samples at the University of Mannheim, Germany, were presented in this chapter.
![]() We have found 1815 bot applications that use the IRC protocol (or slight modifications of that) to communicate with IRC servers on 317 different IP addresses using 120 different TCP ports.
We have found 1815 bot applications that use the IRC protocol (or slight modifications of that) to communicate with IRC servers on 317 different IP addresses using 120 different TCP ports.
![]() These 1815 bots have used 497 different password-channel combinations, which lets us assume we have found at most 497 different botnets.
These 1815 bots have used 497 different password-channel combinations, which lets us assume we have found at most 497 different botnets.
The following Frequently Asked Questions, answered by the authors of this book, are designed to both measure your understanding of the concepts presented in this chapter and to assist you with real-life implementation of these concepts. To have your questions about this chapter answered by the author, browse to www.syngress.com/solutions and click on the “Ask the Author” form.
Q: Where can I get a copy of CWSandbox?
A: A free research version as well as a commercial one can be retrieved from Sunbelt. Please use the online form at www.sunbelt-software.com/Sunbelt-CWSandbox-Request-Info.cfm.
Q: Can I get the source code of CWSandbox?
A: No, the source code is not available, neither for researchers nor for commercial customers.
Q: How long does it take to perform an analysis with CWSandbox?
A: Normally the analysis runs for a customizable amount of minutes, which can be configured in the settings file. On our live sandboxes we use timeout values of 2 or 3 minutes. Under certain circumstances, the analysis stops before that time, such as if all monitored processes have terminated prematurely.
1.“Norman SandBox Whitepaper;” available at http://sandbox.norman.no/pdf/03-sandbox%20whitepaper.pdf.
2.Mark Russinovich and Bryce Cogswell, “AutoRuns for Windows v8.54,” Microsoft TechNet; available at www.microsoft.com/technet/sysinternals/SystemInformation/Autoruns.mspx.
3.Mark Russinovich and Bryce Cogswell, “FileMon for Windows v7.04,” Microsoft TechNet; available at www.microsoft.com/technet/sysinternals/FileAndDisk/Filemon.mspx.
4RegMon monitors registry accesses in real time. For more information see “RegMon for Windows v7.04”; available at www.microsoft.com/technet/sysinternals/utilities/regmon.mspx.