Needless to say, with every new day web applications play a bigger role in the life of the modern Internet than they have ever played before and their security stays among the most important and complicated tasks for various companies.
Most of them are custom written proprietary applications developed without proper application security management processes in place and often without security considerations and controls. That is why probably the most demanded penetration testing service nowadays is web application security analysis and we are going to review the most popular tool used by web hackers and pentesters.
Burp Suite is a tool of the class called intercepting or attacking proxy, which allows its users to inspect and manipulate web traffic passing through it.
There are other free and non-free intercepting (attack) proxies available. However, the authors of this book got used to and stuck to Burp Suite, and that is why we are going to describe this framework.
Note
The main functions and capabilities of various attack proxies are the same (or at least, very similar), so you can treat the following Burp Suite review more or less as a review of the whole class of tools, rather than a certain software.
You can find comparisons of various attack proxies using Google search and choose the one that fits your needs best and is the most comfortable for you personally to work with.
The other alternative intercepting proxies that are worth trying could be:
- OWASP Zed attack proxy (ZAP)
- OWASP WebScarab
- Watobo
Burp Suite is a cross-platform Java framework with various tools combined in one GUI, which works under any OS with appropriate Java software installed. One of the main advantages of the Burp Suit is its extensibility through a special API and numerous extensions.
There are two variants of Burp Suite available on the official website (https://portswigger.net/burp/): free and Pro versions.
The free version contains the same tools as the Pro version, but with limited capabilities and less automation. Those tools are:
- Intercepting proxy: This allows you to review and modify web traffic
- Information aggregation tool: This represents gathered information about targets in a convenient way
- Spider: Spiders inspects all links and pages of target web resources to determine their structures and pass this information to the aggregation tool
- Repeater: This allows us to send customized requests and analyze responses
- Intruder: This is the attack automation and customization tool
- Decoder: This is helpful to encode-decode character blocks
- Sequencer: This analyzes the entropy of various tokens
- Comparer: This compares requests and responses in a convenient way
- Extender: This allows installation and management of numerous Burp extensions
When talking about the most significant distinctions between the free and Pro versions, the Pro version also allows the following:
- Carrying out passive security analysis of web traffic and active web vulnerability scans using the Scanner tool
- Saving and restoring framework state including all requests and responses (especially useful for big projects)
- Using various built-in attack payloads for automated attacks with the Intruder tool
- Performing search and various analysis types of targets and captured web traffic
- Taking advantage of a better performance in the Intruder tool
- Installing some extensions available only for the Pro version
After introducing Burp Suite, we would like to show you an example of a sample web application testing. Let's work with DVWA in our lab environment. We assume that you have already downloaded and started a free version on an attacking machine.
Note
Another useful tool for web pentesting is a proxy switching browser extension. Since most of the web application testing activities are done in a browser, it is not very convenient to always change browser or OS settings when you need to switch between proxies or turn off passing traffic through a proxy at all. The better and faster way is to have a button on a toolbar provided by special browser extensions. We use the FoxyProxy extension for Mozilla Firefox and Google Chrome browsers.
- Start the DVWA VM and set the appropriate network interface settings according to the way your attacking machine is connected to the lab environment (in our case, we don't start the whole lab network but just start the DVWA VM with an interface in host-only mode and attack it from the host machine).
- Start Burp Suite, go to Proxy | Options, and check if there is an activated proxy listener on
localhost:8080(activate it if not). It should look like this:
- Go to the Proxy | Intercept tab and check whether the Intercept button is selected. It will intercept web requests instead of just recording them.
- Configure a local proxy on port 8080 in your browser or create and activate it in the FoxyProxy browser extension:

- Open DVWA in browser with the
http://10.0.0.5/DVWAlink and you will see the request in Burp:
- Just inspect the request and turn interception off. It will allow to forward the next request to its target and not intercept the following requests.
- Log in to the application in the browser, switch to the Proxy | HTTP History tab in Burp, find the initial request to DVWA in the list, right-click on it, and click on Add to scope in the context menu.
- Go to the Target tab. Here, you will see domains and hosts (targets) that your browser has requested since you have started intercept. On the Target | Scope tab, you will see which targets are currently added to the scope of your security assessment. Check whether
10.0.0.5/dvwa/is among them. - Now, you can make Burp hide everything that is not in the scope. It will still capture all web traffic, but it will not bother you by displaying it. To hide everything not in scope, just click on the filter line under tab menu and select the Show only in-scope items checkbox:

Do the same for the Proxy | HTTP history tab.
- Turn intercept on again and log into DVWA with empty credentials and go to the Proxy | Intercept in Burp. You will see the
usernameandpasswordparameters without values in thePOSTrequest body. - Right-click on the request body and choose Send to intruder in the context menu. Switch to the Intruder tab.
- Now, we will perform a dictionary guessing attack on the authentication subsystem of DVWA. We will try to guess the correct credentials. Go to the Positions subtab and click on the Clear § button to reset all positions suggested by Burp.
- Place the cursor after
username=and type in the§character twice or click on the Add § button twice. Do the same with the password parameter. You should have the following:
- Choose the attack type Cluster bomb and go to the next Payloads tab.
- Add several words to the Payload Options section and add the real DVWA username too:
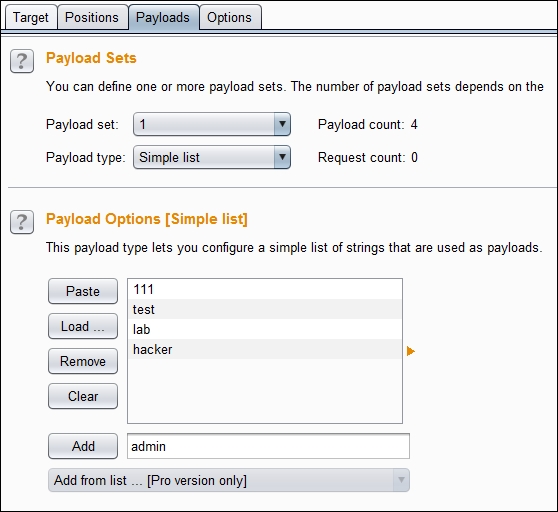
- Change the payload set to 2 and add several words for the password payload, including the real password:

- Go to Options, scroll down, and select the In-scope only radio button in the Redirections section.
- Now, scroll back up and click on the Start attack button in the top-right corner and a new window will open. It will show you the progress of the attack and all sent and received requests and responses.
- Sort the list by response length by clicking on the corresponding column and you will see which payloads have succeeded (successful logon and failure responses will be of different lengths in the current example):

The authentication credentials are guessed! Of course, in real projects you will not have a guarantee that correct credentials are in your payload list, so the success of an attack will depend on your dictionaries.
It was just a quick and short lab example, but there are numerous ways of intercepting proxy utilization and they are different for different targets. Take your time and properly learn manuals for the tools that you choose for work.
