Information technology and electronic commerce
7.1 IT and change in organizations
IT (which is sometimes called ICT, information and communications technology in the academic world) has produced and is producing vast changes in the way companies and organizations function. This section describes the main IT influences and their impact.
• Large payments can now be made instantly and securely.
• The time taken to process a document – respond to an order or pay a bill – has decreased from days to hours or less.
• Next day delivery is expected. Without it the order is often lost.
• Work analysis processes are removing slack time from work schedules (far more effectively than time-and-motion studies ever did).
• Sophisticated data analysis systems allow much more efficient targeting of direct mail (already the most cost-effective form of advertising).
• Internet processes threaten to wipe out many middlemen, wholesalers, retailers and brokers by allowing direct sales of products and services.
• The legal framework in which a company operates changes frequently as the law tries to keep up with new issues created by the technology.
To master the IT field requires a raft of skills to be acquired or at least to be understood well enough to direct others (and the old advice not to direct others to do something you cannot do yourself still holds in the e-commerce age). But do not get bogged down with details. Whichever software application you are using, the next version is likely to function slightly differently; with an uncluttered head you will be able to find out how and convert.
The effect of the speed of change
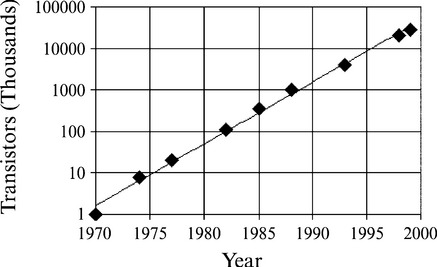
People have difficulty coping with exponential change. Explosions cause damage! In the two decades between 1980 and 2000 computer technology, particularly PC technology, has changed dramatically. The speed of processor chips, typical memory sizes (both working RAM and backing disk storage) and communications speeds have increased 1000 times or more. This exponential growth of the power of the technology (see Figure 7.1.1), with the number of transistors per chip continuing to obey Graham Moore’s law of 1985 and double in less than two years, makes prophecy about the capabilities of IT a very inexact science.
Whole industries need to rethink their structure. When data could be communicated at 300 bit/s, the digital data on a CD would have taken nearly a year to send from Hollywood to London. Prevention of copyright was a matter of keeping tight control of originals, and of seizing poor copies of copies ‘in the interests of preventing the customer suffering from an inferior product’. With cable modem internet connections at 1 Mbit/s, a single bootleg copy of a music album, or video of a new film can be broadcast round the world in about an hour, seriously disrupting the neatly phased marketing strategies and income generation of the entertainment industry.
Working smarter not harder?
The implication of much IT advertising is that if you buy more computing power people will be able to compete more effectively whilst working no harder. In practice the effort saved is illusory, and the expectation is that this time is available for equally productive work. Some concern has already been raised about this. In Japan the phenomenon, called ‘karoshi’, has been known for some years, and in 2000 the first Japanese family was compensated for their son dying through overwork (Financial Times, London, 24/06/00). The problem is not restricted to Japan.
The solution is not easy to find since karoshi affects all walks of life. With IT systems in place, work time may be measured far more exactly than could ever previously be done, and everyone is encouraged to compete with the best, until they ‘burn out’. Continuous change devalues experience and the opportunities for the older slower brain to rest awhile and let the young and thrusting forge ahead until they meet an obstacle that only the experienced have met are diminishing.
Data mining
Large organizations have decades of archive data, once simply kept for the historical record, for ‘just in case’. With hindsight it is possible to see uses for this data that were not perceived at the time, or simply not possible at the time due to lack of number-crunching power. Data mining reuses all this old data to answer useful questions.
One very serious question was the discovery, on old tapes of meteorological records of the Antarctic bases, of baseline data from which the rate of development of the hole in the ozone layer could be established and its link to the growth in CFCs established. One interesting feature of this was the difficulty the scientists had in reading the tapes. These had been archived properly, in secure, dry conditions, but the tape readers had become obsolete and only a frantic search revealed the existence of a working model.
Engineering museums might be necessary as reservoirs of technological artefacts in the future.
Direct sales
Commercial organizations also have large repositories of information, and use it to target their customers with direct mail, from which they claim to get a good response despite the amount of such paper that is thrown away daily. (To put this in perspective, 3% is regarded as an excellent reply rate for direct mail.)
Big supermarket chains remain quite open about the value of their store cards as marketing tools. They could go much further and link the store card data with their sales data, building up a detailed profile that would permit personalized letters reminding about particular products that, for example, had not been bought for at least two weeks.
Consumer groups have declared this intrusive and some supermarkets have publicly denied considering doing it, or that their computer systems have such capacity at present. The Data Protection Act will also limit the ability to use such personal data.
The legal framework
The law affects computing in several ways. It protects the buyer from shoddy goods; it protects the producer from being undercut by a copy from whose sales the development costs do not have to be reclaimed. It protects everyone from the misuse of personal data. It discourages those who would maliciously damage software systems.
The sale and supply of Goods Act 1994 and the Sale of Goods Act 1979
These laws state that items sold must be fit for their purpose as described or recommended by the seller, provided the customer is using it according to instructions. So it is possible to take that computer program back, even with its broken seal, and demand your money back if you were led to believe that it would do more than it did. It is difficult, however, since imperfect performance seems to be tolerated much more in the IT industry than in other industries, and proving that you did not take an illicit copy is impossible.
Intellectual property: overview
Legal protection of intellectual property, the right to exploit ideas that someone thought of first, has a long history. Charles Dickens campaigned for the first Copyright Act to protect his income as a writer. Patents originated in the 1623 English ‘Statute of Monopolies’ that gave inventors a monopoly on their ideas if they agreed to publish them. In the UK the Copyright, Patents and Registered Designs Act 1988 and the Trade Marks Act 1994 are most recent. In the US there is a Digital Millennium Copyright Act 1998 among others.
Copyright
Copyright originally applied to written materials only. The definition has been extended to cover recorded music and video, broadcast media and computer software. Essentially it is illegal to copy any of these unless the author’s permission is given, but there are many exceptions and the length of time for their protection varies from 15 to 70 years.
Patent
Patents were originally designed to allow inventors to make money from their ideas by preventing illicit copying, with the additional benefit to society of having their details published and thus promoting innovation. They largely apply to innovatory things and processes that are useful in the real world. Some overlap with copyrights may occur in a product design, where a new software idea might be patented, and its documentation and ‘look and feel’ copyrighted.
Trade mark
Trade marks apply to the names, logos and other devices – such as color, sound and smell – that are used to identify the source of goods or services and distinguish them from their competition.
Application of IP laws
Application of these laws to IT and computing continues to require modifications to original definitions, and has become much more complex with the speed with which ideas can be spread across the world. In software the value of the merchandise is entirely in the thoughts of its creators and in what it can do, and many person-years of work can be copied in a few seconds. For this reason a lot of effort has been expended by FAST, the industry-sponsored Federation against Software Theft (website: http://www.fast.org.uk) to investigate and act against software piracy.
The laws also vary from country to country. US law often predominates because the US has the largest market, and currently dominates the Internet, and so IT users have to comply with US regulations.
Commercial pressure from major multinationals is slowly forcing countries to enact similar laws in order that, eventually, no one will be able to buy a $500 software package legally for $20 as has been possible.
Details of US law can be obtained from the US State Department’s website, or one of many legal advice sites, e.g. http://www.nolo.com.
Possible abuses of intellectual property protection
Some trade marks are potentially problematical, e.g. Microsoft™ have trade marked Windows™. Fortunately commonsense prevents this becoming a problem for double-glazing firms.
More seriously, there is an increasing number of patents (applied for and even granted) which if enforceable could have far-reaching effects. In the computer-based learning domain, for example world patent WO9822864 has been granted:
COMPUTER EDUCATION AND EXECUTION INTERFACE OPERABLE OVER A NETWORK
A computerized, multimedia education and execution interface system and method for educating and entertaining a student user according to a teacher user’s options. The system incorporates the education techniques of video segments, online student and/or teacher activity, written instructions, student’s activity monitoring, student rewarding and education and entertainment program content filtering. The environment uses various input devices including a mouse and a keyboard. Compact disk drive with main memory and disk drive store the various programs and education data. An audio interface and video controller and screen with a central processing unit communication over a bus complete the system.
Such a broadly defined patent, if enforceable, would cover a huge slice of computer-based learning and make some corporations extremely wealthy. Its enforcement would enrich many lawyers!
Shareware and freeware
Authors who do not wish to market their software conventionally, either because their product is too similar to another, which is already well marketed, or because their target audience is too small/specialist to make marketing practicable, can use the shareware option. In this they retain copyright, but allow free copying of their software with the proviso that after a trial period a token sum is sent to the author, often in exchange for an up-to-date version or manuals. Though many people do not pay up, a sizeable income can be obtained from marketing a good product in this way.
Authors with altruistic tendencies can distribute their work as freeware, whereby they retain copyright but allow free use of the software. There is a whole sector of the computer industry involved in production of products for LINUX (the freeware version of UNIX originally developed by Linus Torvalds), and sharing ideas about development and bug elimination.
Shareware and freeware authors must be careful not to infringe the patents of others. Unisys, who currently own the patent for the type of data compression used in the popular GIF graphics files, now ask for a fee before allowing authors to use this type of file. The sum required is enough to deter anyone unsure of any profit, and has added impetus to the development of a freeware PNG portable network graphic standard.
It is quite possible to make money from freeware! Red-Hat and Caldera, among others, have built businesses by packaging up LINUX and its tools and applications, freely available from the Internet but distributed in many places, and selling them on as (relatively cheaper than on-line charges) CD-ROMs.
Data protection
The Data Protection Acts 1984 and 1998 protect people from the electronic equivalent of gossip, malicious and otherwise. Before 1984 it was possible to be told you were a ‘bad risk’ for a loan, and to be unable to do anything about it. Now those who have personal data on their systems have to reveal its existence by registering with the Data Protection Registrar, only to retain it for the purpose for which it was gathered, and protect it from illicit access. We have rights to find out whether data is held about us, what data is held, and to have it corrected where there are errors. Everyone should be aware of the eight basic principles (from the Data Protection Registrar’s website, http://www.dpr.gov.uk), either as a data user or as a data subject:
Anyone processing personal data must comply with the eight enforceable principles of good practice. They say that data must be:
1. fairly and lawfully processed;
2. processed for limited purposes;
3. adequate, relevant and not excessive;
5. not kept longer than necessary;
6. processed in accordance with the data subject’s rights;
8. not transferred to countries without adequate protection.
Personal data covers both facts and opinions about the individual. It also includes information regarding the intentions of the data controller towards the individual, although in some limited circumstances exemptions will apply. With processing, the definition is far wider than before. For example, it incorporates the concepts of ‘obtaining’, ‘holding’ and ‘disclosing’.
The Computer Misuse Act 1990
The Computer Misuse Act was designed to discourage tampering with computer systems by hacking, either software or data, or by the writing of malicious programs, e.g. viruses. There are three types of offence:
(1) Unauthorized access to computer material (i.e. hacking and attempted hacking into a system).
(2) Unauthorized access with intent to commit or facilitate commission of further offences (the further offences are unspecified, but the penalty is higher than in 1).
(3) Unauthorized modification of computer material (this is interpreted to include both hacking in and changing something and the writing of viruses).
There have not been many prosecutions under the Act, since evidence is very hard to acquire and action is hard to take. It would be a brave bank that helped prosecution of a hacker for successfully breaching their security, since such revelations would seriously damage its own credibility. And though viruses regularly appear it is difficult to pursue someone living across the other side of the world.
Health and safety
Organizations have a major responsibility when it comes to health and safety. Fortunately most computer systems are relatively safe (against electrocution, for example), but it is still possible to break the law with trailing power leads or jury-rigged network cables.
VDU radiation
Concern is still shown by some as to the effect of low-level radiation from computer monitors. No real proof has come to light. Unborn children were thought to be particularly at risk and pregnant women advised to work elsewhere. However, both mother and child are currently thought to be more at risk from restricted movement due to poor sitting arrangements.
Posture and general ambience
Working long hours sitting slumped over a computer terminal with poor lighting is the most likely cause of workplace related illness for users of IT. Regular eye tests are prescribed for employees working at a terminal for several hours per day. There are fairly stiff guidelines for positioning of monitor, keyboard and chair, and for window blinds and types of lighting, to try to eliminate the major effects of eyestrain, back problems and repetitive strain injury (RSI). RSI is a serious problem for those who must input large amounts of text or data. These guidelines should be followed, together with the advice to take regular breaks, if you have to take on such a task, even for a limited period. See the Health and Safety Executive’s website at http://www.hse.gov.uk for more information.
Problems 7.1.1
(1) What does Moore’s law say about the growth in power of the microchip? Why does this make the effects of change in IT difficult to predict?
(2) Estimate the number of bytes required to store the text of an encyclopaedia (any large book will do – count the characters per line including spaces then multiply by the number of lines and the number of pages). How many such books would fit on a CD-ROM of 600 MB? How long would it take to transmit such a book across a network at 100 Mbit/s (roughly 10 Mbyte/s)?
(3) You have received a shareware program from a friend. Which laws protecting intellectual property affect your use of it?
(4) What is RSI? How can you protect yourself against its effects?
7.2 Using computer applications efficiently
Applications are the programs for which computers are bought, in order that letters can be written and edited, CAD drawings modified, databases accessed, etc. Every application has its own set of methods and processes, but there are many common ones that apply. You need a portfolio of skills in the use of these applications. You will find it most profitable to notice the features common to all (most?) of the applications (these, like cut and paste, only need learning once). Then get a grasp of the main processes in particular types of application (these, like mail merge in a word processor, differ in detail only with manufacturer and version, and a little investigation of a new package can usually make it work).
This chapter is too short to teach you all these skills, and certainly not in detail, especially since the precise detail varies between packages, and also between versions. The aim is to outline what you should try out on the software that is available to you most abundantly whilst studying so that you can be confident when starting work. Above all you need understanding and an overall grasp. The detail of the software changes, from source to source, and from version to version. What you can do with it is much more constant.
Operating systems processes
The operating system is the software that runs the basic processes of the computer. It permits storage of computer data in named files, and allows those files to be stored systematically in folders (also known as directories) and sub-folders. It further allows such files to be loaded and saved, created and copied, moved and destroyed, printed and executed.
File naming conventions
Filename rules vary. Some early PC operating systems, e.g. MS-DOS, were limited to 8 letters, plus a 3-letter extension (the 8.3 convention, e.g. MYLETTER.DOC), but most allow much longer names, with longer extensions. It is even possible to have a space in a name, e.g. MY LETTER.DOC, though this is best avoided since it minimizes compatibility across platforms. Some computer users join words with an underscore as in My_letter.doc, or use the increasingly popular CapitaliseEachWord convention, producing MyLetter.doc. The extension, e.g. .doc, is often used by the operating system to link the file with the application that produced it, allowing it to be opened more easily.
Some operating systems, e.g. UNIX, are case sensitive, and will treat MyLetter.doc, myletter.doc, and Myletter.doc as three different names. You will have to learn when to be careful.
Graphical user interfaces
Operating systems processes are all defined so that applications programs, the ones you actually buy the computer to use, can carry out these basic processes in a straightforward fashion by using pre-defined routines. To provide some manual control there was generally a command-line interpreter so that such processes as copying a file (i.e. loading it and saving it somewhere else) could be carried out using a typed command. Most modern systems, e.g. Windows™, have added (or even replaced it with) a graphical user interface or GUI, where such processes can be carried out by moving a mouse to control a pointer on screen, and pushing icon buttons, or even by dragging and dropping the files where required. The UNIX/LINUX family of operating systems has its own X-Windows equivalent.
GUI processes are preferred to command-line processes by most users since they are found to be more intuitive and easier to operate. Occasionally still there are processes that can be carried out better by command line, particularly where a series of processes can be executed in sequence using a batch file.
Detailed knowledge helps, once basic principles are understood. For example, in most mouse-driven environments, the left mouse button picks objects, operates programs, and uses them to open files. However, in Windows™ you also find that:
• It is possible to swap left and right buttons, or change the sensitivity of the mouse.
• The right button gives access to properties of the object, allowing it to be made read-only, for example, or to actions related to the item letting it be copied easily.
• <SHIFT> with the right button may allow better control of those actions, e.g. opening a Word™ document with a different package from the desktop.
Exploring the use of such options and processes can greatly increase your productivity (and hence salary).
Help!
Modern software generally comes with an on-line help facility that can be actioned simply with a keystroke or two. Help files are a preferred means of documenting features of the program, especially where it would take up an inordinate amount of paper.
Learning to find out what help is available, as documentation or as examples, is a skill that will enable software to be learned more quickly. Many computer users read the manual as a last resort. Use the help facility more frequently.
If you prefer books there are a plethora of new ones produced every time a popular package is launched or updated. You may find that even The Complete Moron’s Guide to X has useful information for beginners. If you have to buy an expensive book, check out the ‘sale’ shelves for guides to a previous version; the basic software may not have changed much.
Networks
Most computer installations are networked, even if only by modem to the Internet, in order that outside resources, e.g. websites or software archives, can be accessed. Their use requires you to be able to connect to and disconnect from the resources you require, to understand and operate the password and other security requirements of the system, and to have some grasp of the complex data structures that a large network houses.
Auxiliary hardware: peripherals, connections and storage
A peripheral is an extra piece of equipment attached to the computer and controlled by it, such as a printer or scanner. Network connections and disk storage systems used to be peripherals, but are now generally housed in the main processor box and considered as part of the main computer system (except for handheld computers, and this may yet change).
You need to know how to service these items, preparing them for use by replacing disks, paper, ink or leads, and cleaning them when required. When working with a complex system it is useful to know how to troubleshoot (and to know when to call in the experts!).
The mouse is a simple example, particularly when heavily used in a greasy or dusty environment, when the pointer action it produces becomes erratic. Cleaning the accumulated grime from its rollers by opening it up and swabbing them with a small amount of methylated spirit is not difficult. Nor is replacing it with another mouse costing a few pounds; the latter may be more cost-effective.
When things go wrong
Each part of the ‘Standard’ PC, the processor, the circuitry, the operating system, each peripheral, and each application program, has probably been worked on by thousands of people. It is a miracle that it works at all, and hardly surprising when things go wrong. When it does you have two choices – to send for the repairers or to fix it yourself. Either way you will save a lot of time by being able to describe what is wrong clearly, using correct terminology. The computer, just like, say, the motor car, gives off audible and visual signals as it works, and changes to these (particularly smells!) can be significant.
Disaster recovery
Even though these may amount to several thousand pounds the most valuable part of many computer systems is neither the hardware nor the software but the data that it contains.
Consider the simple data input costs and how they mount up. A good typist might manage 50 words per minute, for 8 hours per day, for 250 days in a year. At an average of 6 letters per word this is 600 000 characters/bytes or 0.6 Mbytes. Now estimate salary and on-costs of £20 000 per annum (this is £10 per hour). Each £1 of salary buys 30 bytes of data.
So a 3.5-in floppy full of text data could hold about £40 000 of data, and a 600 Mbyte CD-ROM of documentation could cost £20 million just to type in! (For real data this would be an exaggeration, since so much is in graphical form, and a scanned photo or other graphic could easily take up 0.6 Mbytes, and take less than 5 minutes to produce. At £10 per hour this might cost less than £1 to produce, plus copyright costs of course.)
Of course the value of data stored, and of its organization into searchable and usable form, may be many times the cost of its production. When this is taken into account, the need to keep the data secure is clear. At least one large (computer!) company, and doubtless many small ones, has been brought to bankruptcy by the loss of its data in a fire.
Fire is reckoned to be the major cause of serious loss of data. Fireproof safes are available, designed to keep magnetic media protected for 30 minutes, giving time for data to be rescued.
Problems 7.2.1
(1) What problems were there for users of the old 8.3 filename convention? Why does the use of spaces in long filenames sometimes produce problems? What alternatives are there to make long filenames easier to understand?
(2) List some of the advantages and disadvantages of using a networked computer. When is it essential to change your network password? What potential problems are there in keeping the same password for a long time?
(3) List some of the problems that dust can cause in a computer system. What practical steps can be taken to reduce the potential damage to the computer?
(4) What is involved in a disaster recovery plan? List the software and the data that you would need to install if your computer had to be replaced after a fire.
7.3 Using the major office applications
There is a wide range of applications available for computer users, ranging from the general word processor to specific industry packages, e.g. lighting design.
Initially, each application, being written by a different team with their own perspectives, had its own set of keystrokes and mouse actions to drive it, often linked to the computer operating system on which it was first produced. With the increasing predominance of a small number of operating systems, most notably the Windows™ GUI, a standard set of processes has been enforced, both across different vendors of the same type of package, and across different types of package. The preponderance of Microsoft Office in the PC world is due to its having a headstart in this, since they also owned the operating system.
General application skills
There are some processes, often related to the GUI, that are common to most applications. Practise them in each! This will enable you to learn a new package more quickly, and, generally, to integrate your usage of the packages. For example, in Windows™ text can be moved inside a document by:
• highlighting it (pointing to the start with the mouse, holding the left button down and wiping over the chosen area);
• cutting it (holding (CTRL) key down whilst tapping the ‘X’ key;
(Note: there are alternative ways of carrying out each operation in Windows™, and similar techniques in every other operating system.) Once you have learned to copy and paste inside Word™, say, you can copy inside WordPerfect™, or from Word™ to WordPerfect™, or from Notepad to Aldus PageMaker, or from Paradox to Lotus 123, etc. The result is sometimes different from what you might expect, but there are generally alternative options if you do not agree with what the programmer thought was the ‘obvious’ outcome.
Document production technology
In the beginning was the text processor, devised by programmers to enable them to code their programs, and as a spin-off to write and (above all) to edit text documents. Then someone invented word wrapping and the word processor was born. Some time later the desktop publisher appeared, as a means of taking the relatively crude text from a WP and merging it with pictures, to produce, for example, a newsletter or brochure, and making a lot of skilled typesetters redundant at the same time.
Currently standard word processors can do anything a desk-top publisher package could five years ago, and have largely usurped their old market in small business advertising. Desk-top publisher packages have become specialist publishing software handling colour separation (for printing with yellow, blue, magenta and black ink), image editing, chapters, indexes and any other publishing features that would slow down a standard word processor if it were included. The text of this book was produced using word processors. The vast majority of the layout was decided by the publisher, who was supplied the content as plain text.
Word processing
However, until you begin to publish commercially, your documents will normally be produced using a word processor. Since you may be using it (or its derivative – the e-mail editor) rather a lot, it is worth getting to know its main features, because you will want to use bold type, different fonts, and many of the other features available. If you do not, your documents will be outshone by more eye-catching competition. You will certainly have to comply with (company) document standards (heading position, fonts, etc.). You will also want to ensure that you do not lose work and that you can keep track of changes.
Elementary WP skills: data input and editing
There are some skills you probably already have or can pick up easily once you can activate your chosen word processor. These allow you to produce a basic document or message, and are similar to those required for e-mail messaging.
Intermediate WP skills: formatting your document
There are many examples of inferior products winning the battle for market share by better marketing. Some would argue that the PC is a case in point. Similarly ideas which are more smartly expressed often win out too; as a sixties guru, McLuhan, said ‘It is the medium that matters, not the message.’ An attractively laid out document is more likely to be read. Only the really dedicated, such as those marking exam scripts, feel the need to read scrappy documents.
What makes a document ‘attractive’
Over the years some basic principles have emerged. There is no reason why you should not break these rules; indeed slavish adherence to any system leaves the way open for the iconoclast to attract attention by being perverse. But at least be aware of why they are there, so that you break them for a purpose.
• Keep the number of fonts (the word most programs use for typefaces) on a page to a minimum to avoid the ‘busy’ or ‘muddled’ look. The same typeface may be of different sizes, underlined, italicized, etc. Serif fonts (with tails, like Times Roman) allow for easy reading and are useful for body text. Sans-serif fonts (without tails, like Arial or Helvetica) are believed to slow the reader. These are best for headings (unless you want your reader to read more slowly of course).
• Typescript is more difficult to read than text printed with proportional fonts. Reserve fixed-width fonts like Courier only for data that has been structured by spaces, e.g. directory listings. Computer programs are conventionally laid out in fixed-width fonts.
• Use the Styles feature of your WP to control the appearance of your text. Then if you wish you can modify the appearance of each paragraph or of each type of heading in one hit. When you have hit upon a suitable set of styles, create your own template so you can use it in further documents.
• Use plenty of white space. It may be environmentally more friendly to pack the words on the page, but it can overface the reader. Break your paragraphs up with subheadings summarizing their contents to improve readability. Headings should be separated from their paragraphs by half a line, and blocked paragraphs (i.e. with no indent on the first line – normal in reports) separated by a full line. Headings of most formal documents need numbering in some systematic fashion.
• Size matters! 10 point text (a point is 1/72 of an inch – an old printing measure) is as small as you should use in multi-page documents for readability. 12 pt is easier for most people to read.
• Colour is excellent for emphasis, decoration and graphics, provided you can print it. But colour photocopying is not cheap, and if your document is copied in black and white your careful emphasis will be replaced by greying out!
• Columns may be useful in newsletters. Newspaper columns are designed so the reader can read a line with minimal eye movement and hence can scan quickly down the page.
– use the tab key and left, right, centre and decimal tabs set in the ruler to line up the text at absolute positions, or
– use the very flexible table feature of your word processor (turn off the borders if necessary). In tables, individual cells, columns and rows can be formatted separately to give the desired effect.
More intermediate WP skills: including graphics
Many documents include graphics, either as decoration or to display information in an easily accessible form. It is useful to know how to insert the graphic, perhaps by cutting and pasting it from elsewhere. It may need to be cropped, to remove extraneous detail, and then must be positioned at an appropriate point in the narrative, with text perhaps flowing round it. It will need to be labelled so that it may be referred to.
Advanced WP skills: document automation and management
The beauty of preparing documents on a computer is not speed – most could be produced faster by hand – but in their editing and reuse. A document may have a table of contents and index added automatically. It may then be reformatted with a different number of columns, different size of paper and font, and yet have all the page references changed correctly.
It may be rehashed into a handbook, developed into a presentation or published as a web page. It may even be automatically translated (not perfectly but intelligibly) into a foreign language.
A document may have to be saved in a different format, ready for a different processor, even in text-only format. If available in text-only format some judicious use of Search and Replace facilities may be needed before paragraphs wrap correctly.
Mail merging is another example of automation, linking one document to another. A letter is linked to an external data file, and instead of actual names and addresses, a reference to different parts of the name and address is placed appropriately. Then when the merge process is executed, a series of letters is printed, one to each recipient. A merged document need never actually exist.
This produces an interesting problem for those who keep records of everything. How is the creation of such a letter recorded? If the source letter and/or database are subsequently modified for another letter, the only possible record is a merged file, which is subsequently archived.
Modifications to files at least may be recorded. Where a source file is edited, perhaps by more than one person, a modern word processor may be set up to highlight the additions and deletions in different colours, at least until the latest version is agreed and the highlights then removed. The problem of keeping records of files in various stages of development has to be solved by archiving them to some permanent storage periodically. This may be done as an addition to the back-up process, as described later.
Financial and numerical technologies
Some say that it was the spreadsheet, first VisiCalc on the Apple II and then Lotus 1–2–3 on the first IBM personal computers, that really sold the PC to business. Prior to that keyboards were nasty things that typists used, and managers didn’t want to handle. Suddenly it was possible to set up whole business scenarios like ‘What would happen to our current situation if we reduced our spending on computers?’ in a couple of hours, rather than go begging the data processing department for the use of one of their programmers. (Doubtless the possibility of doing it without anyone else having to know also appealed.)
Spreadsheets are the all-purpose tool for setting up numerical models to answer such questions (and many other non-financial queries as well). There is also a range of specialist software available, particularly for accounts. Each of these has their place in the modern business.
Spreadsheet introduction
A spreadsheet is a rectangular array of boxes or cells into which numbers and letters can be placed. It is initially two dimensional, rather like the layout of a book-keeping page. These may be linked to make a workbook.
The columns are labelled with letters, from A to Z, AA to AZ, BA to BZ as far as I V. Rows are labelled with a number, from 1 to 800 or more. Each cell has its own name or cell reference, made from the column letter or letters, and the row number, for example, A1, B23, BZ235.
From one set of data it is possible to produce a second that depends on it by known factors. Hence it is possible to use this year’s figures, with an estimate of possible inflation factors, to predict likely future performance.
As well as giving the possibility of setting up arrays of figures and providing rapid totalling of the rows and columns, spreadsheets have facilities for simple production of graphics from the data.
Cell entries
From Figure 7.3.1 we can see that a cell in a worksheet can store one of the following:
• Text, useful for labelling cells.
• A number or value stored typically to 18 decimal place accuracy.
• A cell reference so that B2 might contain =C2 so when C2 changes so will B2.
• A function, often referring to a cell reference, e.g. SUM(B2:B5), adding up all the values in cells B2, B3, B4, and B5.
Spreadsheet general principles
Distinguish between the data and its appearance. For example, the number 36 526.6 may appear as £36,526.60, the date 01-Jan-2000 (using just the whole number), the time 14:24:00 (using only the fraction 0.6 of a day), as a percentage 3 652 660.00% or even as an improper fraction 36 526 3/5. These are interchangeable by reformatting the underlying number.
Do not leave unnecessary gaps between rows or columns of data. Add any extra rows and columns, to separate data and make the printout clearer, last of all. Extra rows often get in the way of efficient formula copying, among other irritations. Extra columns, added simply to separate data, are unnecessary; widen the columns instead. It is relatively simple to change fonts, add borders, and to shadow areas of the sheet for extra clarity.
Spreadsheet graphics
Apart from simple number handling, producing row and column totals with more reliability than most humans, spreadsheets are often used for production of simple graphs, particularly for display purposes. The days of hand-drawn graphs on displays are long gone.
The range of options is enormous, so it is important to have some clear principles in mind. You can break them, just as in word processing, but have a good reason.
(1) Colour aids clarity wonderfully on screen. Ensure that it will print and copy well when that is necessary.
(2) Graphs should be clear and uncluttered. 2D graphs are generally more easily interpreted than 3D graphs, particularly if forward-placed data series obscure others. Resist the temptation to add unnecessary detail such as picture backgrounds unless you are deliberately trying to mislead your audience.
(3) Pie charts are simple statements of different contributions to a whole, usually 100%. Too many slices confuse, so some may have to be aggregated into ‘the rest’. 3D pie charts may make it difficult for those without good perspective awareness to compare areas.
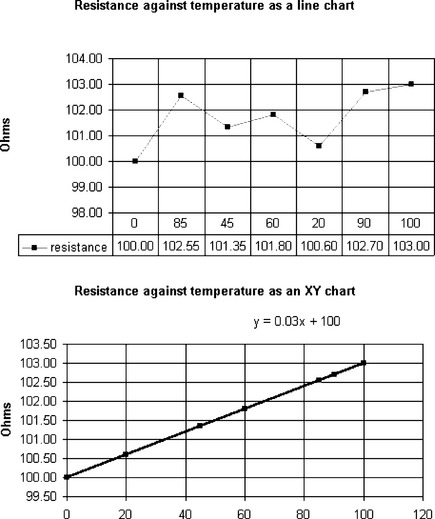
Figure 7.3.3 Line and XY charts of unsorted data. Notice that the relationship is lost on the line chart, and X values are irregular and not on gridlines
(4) Line charts and bar/column charts are used to show change in a variable when a category changes, e.g. salary against employee, pollution level against town. When a line chart is used for X–Y data the X values, however irregular and in whatever order, are drawn equally spaced; the Y axis does not pass through X = 0.
(5) Bar/column charts tend to be used for items that mount up, especially for discrete data that counts up, e.g. number of days of sunshine, salary, rainfall. Line charts are more useful for data that is continuously variable, like temperature.
(6) Where continuous data is grouped (it may be discrete data measured in tiny steps) and plotted, e.g. number of houses in different price ranges, the gaps in the resultant bar chart may be reduced to zero producing a histogram.
(7) XY chart data may need to be sorted in ascending order of X. Alternatively, if available, plot the points and get the package to plot its best-fit line (and give the equation if Excel 97 or similar). X–Y chart axes have lots of options, including reverse plotting and logarithmic scales. Use them appropriately. Beware of heavy gridlines. At graph-paper densities you will see nothing else.
(8) There are many specialist graph options, such as radar charts. Make sure you know when it is appropriate to use them.
Back calculation: using goal seek to find the answer
One of the most useful features of a spreadsheet is its ability to back calculate. Given that y = x2 + 3.5x −7 it is not difficult to work out a value for y, given values of x. Much more problematical is finding both x values given a y value. Plotting the graph, we find:
To find the solutions of the equation, where y = 0 the Tools>Goal Seek function is used on the contents of cells B8 and A8. (Other values could be used but close values are safest – there are two crossing points):
and the value is given as:

Let us assume that 0.000 009 32 is close enough to zero!
Similarly we can find the other crossing point by goal seeking on A14 and B14, say:
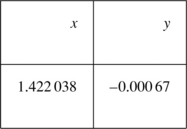
This time y is negative and a little bigger in size but probably good enough
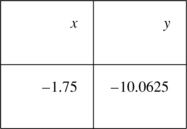
An even more powerful tool exists. Remember ploughing through all that calculus, simply to find a minimum value. Tools>Solver will find that too:
Pressing the Solve button gives the answer that y has a minimum of −100625 when x = −1.75.
Databases
Whereas probably more than half the PC screens in use at any one time are showing a document processor, most overall computing time is devoted to database handling. Huge databases of personal and stock-control information are held by the government, utilities, banks, supermarkets, etc. Most engineering and business catalogues come in the form of CD-ROM databases. And then there is the Internet.
An engineer should have some database searching skills for use in, for example, libraries or CD-ROM catalogues. Since most records systems are becoming electronic it is helpful to know some of the basics of setting up a database so that the importance of keeping data in a structured fashion is appreciated.
Database basics
Data is stored as bytes, 8 bits = 1 byte. Modern computers handle data in 1-, 2-, 4- or 8-byte chunks, 8-bit, 16-bit, 32-bit or 64-bit data.
Creating an example database
Databases are built from tables, each of which should describe some individual type of entity, e.g. a person, an invoice, an item of stock, etc. The exercise below takes you through some of the decisions that have to be made in order to create one table in that database.
Suppose a small company wants to set up a stock database. Each item of stock is an example of the stock entity.
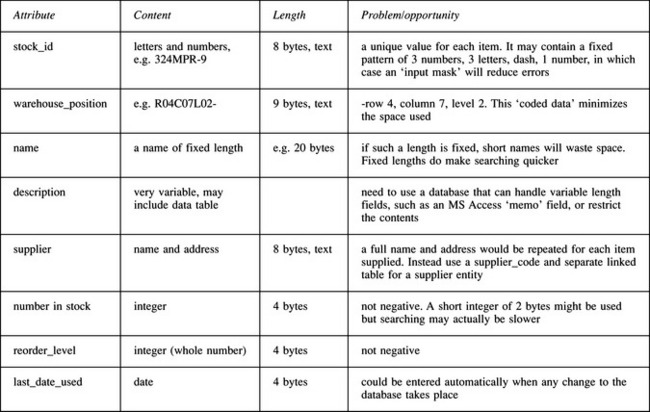
The stock entity has attributes that describe it. Notice that it is a bad habit to have spaces in attribute names since, as with filenames, some software treats the space as an end-marker. Notice also the beginnings of an extended database. The supplier is just given a reference to supplier table; this will eliminate address space and, more important, the need to update many records should details like phone numbers change.
Designing the table
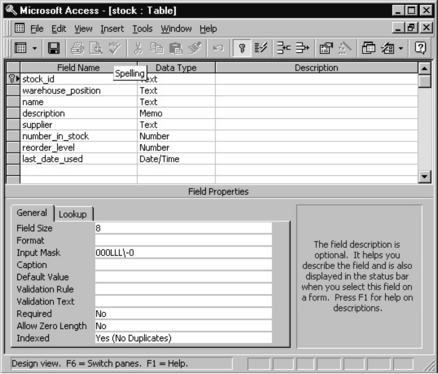
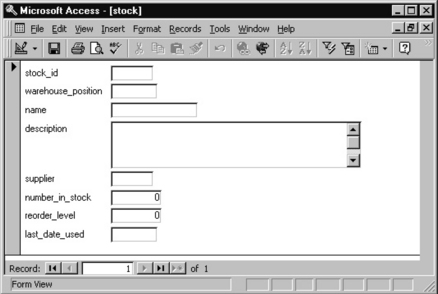
The next stage is to specify the table contents in the package you are using. This is very package specific. Opening an MS Access database and designing a new table produces screens like Figures 7.3.9 and 7.3.10.
In Figure 7.3.9 the field names have been inserted, and the stock_id attribute put in the first field. The key button makes it the primary key field that defines the order in which the data will be stored. The field size is set to 8, and the mask set to be 000LLL-0, which means 3 numbers, 3 letters, a dash and 1 number, all compulsory.
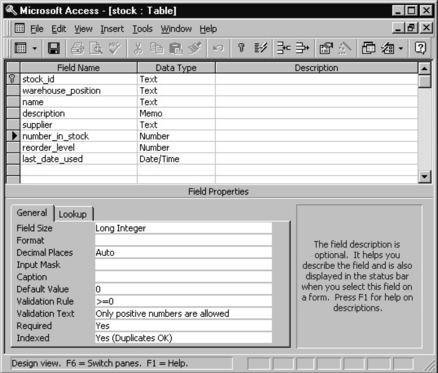
In Figure 7.3.10 the number_in_stock field is being defined. The field size is Long Integer (4 bytes for Access) and the validation rule prevents the error of the value entered being negative.
Data input forms
Having defined the fields the data is inserted. The simplest way is to create an input form for the table (Figure 7.3.11).
Most database software has tools to help speed frequent processes. This form was generated automatically from the stock table. It can be edited, and the order of the data input changed.
The form adheres to rules already defined in the table. In Figure 7.3.12 an attempt was made to input a negative number_in_stock, and a pop-up warning was produced.
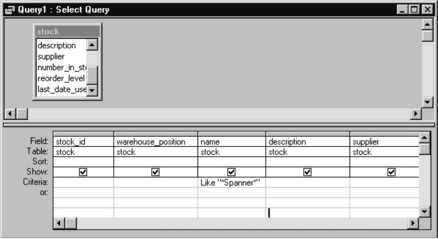
Querying a database
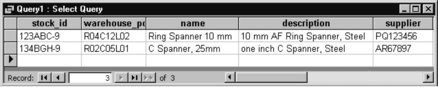
The simplest way to query a database is to use QBE, query by example. An MS Access query shown in Figure 7.3.13 will give the data in Figure 7.3.14.
Reports from the data
The object in inputting data is to be able to retrieve it in a more organized form, usually called ‘reports’. Access will produce a report from a table, or from a query on the table (see Figure 7.3.15).
Database conclusions
Databases can become very complex, with hundreds of tables spread across many computers and many countries. A small-scale PC database can, however, handle the stock requirements for a small business, and its use improves skills that may then be used in the extraction of data from larger systems. Crucial concepts are:
• GIGO: garbage in, garbage out. If inaccurate data is input an excellently presented report is useless.
• Input validation: Trying to prevent inaccurate input by automatic checking of values by rules.
• Refining queries: Trying to be precise about what is wanted (see Finding information on the Internet, page 351).
Personal information managers (PIMs)
PIMs are specialist databases used to keep track of diaries, contacts, etc. When networked they enable diaries to be shared, times of common meetings to be inserted, and other information to be shared around colleagues in a business. Such information may be kept on portable systems as small as a palm top or Psion and synchronized with a large central database at regular intervals.
Synchronization of data between databases
Where multiple database systems carry the same information there is potential for confusion. In database design a major principle is that any given data item should only be kept in one place. This is part of the process of normalization of a relational database.
However, duplication is inevitable where a company representative carries information away on a portable system, whether it be as contact or sales information or just a personal diary. If as a result of visits the portable data is changed, there will obviously be a difference in the data held. On return to the company and plugging in to the central system, synchronization software must add new information in either direction, and where discrepancies occur (e.g. representative and boss schedule a new appointment at the same date and time), resolve them.
Presentations
The cartoon Dilbert has many jokes about ‘Death by Powerpoint’. Despite their overuse, and particularly the overuse of some of the facilities, they are very valid tools for engineers, both in providing rolling displays for exhibitions, and in providing focus for lectures/seminars, etc. Presentations are easy to put together and provided you can guarantee a suitable projector or screen, easy to carry on a floppy disk.
The basis of a presentation is a series of slides that can be sequenced by timing, use of buttons or both. Each slide has:
• a background which needs to be chosen to suit the subject;
• ‘pretty’ backgrounds that obscure the text/images. Backgrounds are rarely the point of the presentation;
• excessive amounts of text. These are bullet points. Your talk is much fuller;
• images that are overcomplex. They need to illustrate a single message;
• sound that is intrusive. That wake-up call may be effective first time. After that it becomes annoying;
• video may be better projected separately, rather than in a reduced-size window;
• animation, particularly of text bullet points. Though text can fly in from all directions with a screaming sound does not mean that it should;
• slide printouts. These are great if given out first, since the audience can use them as a basis for notes (assuming that they are legible with a contrast between back- and foreground). If given out as a summary they are probably inadequate, and a two-page summary sheet would be far better.
Problems 7.3.1
(1) What features of a word processor allow you to take plain text and improve it to produce a readable document? List some of the pitfalls of overusing some of these features.
(2) A company can either invest £1000 capital and make objects at £5 each, or invest £5000 and make them at £3 each. By setting up a table of differences between total costs for different numbers of items using the two processes, work out using Goal Seek at what number of items it becomes cheaper to make the greater capital investment.
(3) Estimate the number of bytes required to record the information given when applying for a driving licence. By multiplying by the number of drivers on the country’s roads (estimate it if necessary) work out how much storage would be required for the drivers’ data file.
(4) List some of the problems likely to be encountered when a sales representative returns to head office and attempts to synchronize the data on his or her laptop with that on the main office machine.
7.4 Industry specific applications
Every sector of engineering involves the design of new products and has its own computer aided design applications, capable of providing different sorts of drawing models. Some generic packages, e.g. AutoCAD, provide a general drawing environment which may be enhanced with add-ins, for example their own architectural engineering and construction extension that will draw images of 3D walls, insert windows, doors and winding staircases, and give perspective views of what has been produced. Companies like HevaComp have converted their own package so that it works in conjunction with AutoCAD, since they can then set up the required lighting and other services.
There are electronic add-ins to these generic packages, but the pressure to produce a circuit that can be tested electronically (for example, be seen to oscillate or amplify) as well as be converted into a printed circuit board layout, results in a wider range of specific products.
The trends in the CAD world are to:
• draw in 3D if perspective/isometric views are required. This means that there is only one model of the item, rather than plan, front elevation, side elevation and third angle projection to be changed when modifications are made;
• work with libraries of pre-produced, editable and reusable components to save costs. A manufacturer may provide a library of their accessories ready for insertion into a product drawing (thereby locking them in as supplier, of course);
• design not just draw. It is increasingly possible to ask the questions ‘Will that type of cooker fit here?’, ‘How would its temperature change if it was painted black?’, and ‘Would the circuit performance change if I used a smaller battery here?’
• to be able to interchange data with others electronically, either by standardization on particular packages, or by using some of the drawing conversion processes that are available.
Project management
Good project management is vital if a project is to succeed, and most developments these days are in project form, where a team of people with different backgrounds and skills is put together to satisfy a need. All the project management tools, such as arrow diagrams, PERT diagrams, Gannt charts, etc. are available to display the plan for the project, and to monitor its progress. The computer can track efficiently the usage of each resource (person, tool, and raw material) and measure the effectiveness of the various processes. Resource levelling may be provided in which checks are made (for example, that the plan needs three mechanical engineers at this time and only two are employed; therefore either the job must be rephased or a temporary person appointed). Project management is dealt with more fully in Chapter 4.
Simulation software
As already stated under CAD, computer models can now be used to test circuits before they are built. This process of simulation depends upon accurate knowledge of the behaviour of components and accurate calculations, together with a great deal of testing of computer models against known reality. Once the system has been created and tested adequately, however, it permits expensive systems to be tested to destruction, even nuclear weapons to be designed without explosions. Similarly aircraft pilots can be trained to fly a plane before it is off the ground, and to land many times in hazardous conditions before it is necessary to do so.
Computer-based learning (CBL)
The provision of learning opportunities is expensive. Setting up large study groups in which each student gets the same delivery can minimize its costs. Particularly in specialist subjects this conventionally implies gathering from a large region at a particular time which is not always practicable.
The ‘solution’ is to put the delivery on a computer – CD-ROM, Internet, etc. – and deliver it to the student in their own time, with some access to tutors but most interaction using computerized systems, e.g. automatic testing and e-mail. There are many people working on providing such CBL, and there is evidence of its working effectively in some areas, particularly where companies want their staff (who will get a pay rise if they succeed) trained in the use of a specific product. But most of the ‘Let’s teach this by computer’ initiatives founder on the lack of motivation of the students. All the enthusiasm the CBL people see and wish to harness in a crowd of disaffected adolescents playing ‘Quake’ evaporates when they have the option of ‘Basic Maths’ or ‘Solving Kirchhoff’s Equations’ tuition.
Students of engineering are assumed to be motivated. They also come in relatively small, expensive classes. They may well find their time increasingly being devoted to CBL packages. Their use to replace or supplement lectures is sometimes understandable, particularly where students have difficulties with time and place. Their use to replace hands-on use of equipment is a particular problem if it removes the chance to carry out real operations. An analogy is driving tuition; you may learn the basic ideas practising on a simulator (and it is certainly a safer way of learning to change gear whilst moving), but you are not safe, and would not pass a driving test without significant road experience.
Problems 7.4.1
(1) What are the major differences between drawing something on a CAD system and drawing the same item on a drawing board? (Consider scales, accuracy, speed, editing, flexibility, sharing of information.)
(2) In what circumstances can a simulation be as good or better than the ‘real thing’? (Consider detail required, hazard avoidance, levels of supervision required.)
(3) Under what circumstances would you accept computer-based learning in place of tutor-guided learning? Are there circumstances in which you would prefer it, and why?
7.5 Electronic commerce
The power of modern communications, particularly networked computers, is changing the face of commerce. Its effect on engineering is to reduce the time-to-market for products by:
• increasing the speed at which new products ideas spread, thus creating a demand. When a new games console is produced in Japan, publicity about it spreads fast. If sufficient demand is built up by this the distributors may be forced to export more quickly to avoid too many internet purchases distorting their carefully phased marketing plans;
• allowing more rapid dissemination of ideas to a vaster audience. As these ideas spread there is a greater possibility of two being put together to produce an unanticipated development.
The greatest influence on this process is the Internet, the huge sprawling network of connected computers that is the basis of most B2B, business to business, and B2C, business to customer, communications.
The Internet
The Internet began as the US Defense Department’s computer network in the early 1970s. At the time there was a small number of isolated mainframe computer networks which could not interconnect because they used incompatible proprietary systems, whose suppliers feared loss of their market if they allowed connection to others. The US Defense Department’s Advanced Research Projects Agency (ARPA) set out to create a decentralized network of computers that would still communicate if some of them were hit by nuclear bombs. The ARPA devised a set of rules, called a protocol, designed to be robust. This has developed into the TCP/IP (transmission control protocol/internet protocol) standard that the Internet uses today
In the following decade universities and research institutes began to be linked to this network and it began to develop into the Internet. In 1989 Tim Berners-Lee, working at the CERN Research Institute for Particle Research in Switzerland, proposed a modification of the hypertext systems then being used for document storage as an easier means of access to data. With this hypertext transfer protocol, the World Wide Web was born. As the Internet became easier to use, so more people outside defence/academic research began to use it through an increasing number of ISPs (internet service providers). As more people began to use it, commercial opportunities began to be seen for advertising and sales, and the letter e began to be tagged on to many words, increasingly without the hyphen, and generally lower-case, hence email, ebusiness, esales, even etailing.
TCP/IP and decentralization
The Internet is nowadays a complex web of intelligent communicating devices called routers, with computers attached as sources of messages. It is decentralized. No one controls it or can switch it off. A computer in the UK uses TCP/IP links to communicate with a computer in Hawaii by chopping its message into packets, putting a header on each which gives the (currently) 4-byte address of the Hawaiian computer, and passing it on to a router in the general direction of the Pacific. The packets are passed from router to router until they reach Hawaii, perhaps in short hops, perhaps by satellite link. At the other end the message reaches its destination computer and is put back together, interpreted and a response or acknowledgement sent.
Each packet may take a different route. If a router breaks down, or if a particular channel becomes overloaded, the messages are routed round it (see Figure 7.5.1). Redundancy, and therefore reliability, is built in.
Internet terminology
The Internet has spawned a host of acronyms: Internet itself, TCP/IP, ISP, B2B, etc. Any that are relevant you rapidly learn. Most books have a glossary of terms used. Some of the most important ones are:
| URL: | uniform resource locator. This is a text alias such as www.freeserve.co.uk for what would otherwise be something like: 195.92.249.48. In an address like http://www.bton.ac.uk/main/index.htm the www.bton.ac.uk is the server address; there could be several servers, in which case the address might be http://library.bton.ac.uk/. After the single ‘/’ follows the directory and/or file address, e.g. ‘/main/index.htm’ which the browser will fetch. If no file address is given a default home page is supplied. |
| hypertext: | text with active links, which when picked with a mouse or otherwise activated, takes the user to a different document or part of a document. |
| http: | hypertext transfer protocol. This is the set of rules obeyed by browsers and servers in interpreting the hypertext pages used on the Web. It also makes such activities as downloading of files easier. |
| server: | a computer that provides information in response to requests from another computer. |
| e-mail address: | a text string such as [email protected] (my e-mail address). The server is the part after the @ symbol; indeed http://www.bton.ac.uk accesses the University of Brighton website. The remainder is unique to me. Anyone else called J. K. Wilkinson would have to be given an alternative address. |
| com: | this is an example of a top-level domain. Others exist like .gov, .edu (and licensing of new ones will happen in 2001). These were originally all US URLs, with other countries adding .uk, .de, .fr, etc., but .com became the symbol of the internet-savvy company, forcing its release to the rest of the world. |
Internet access costs
Most people access the Internet using a phone line. This normally costs money, unless their ISP has provided a freephone number. Freephone connections are not free since someone has to pay the phone charge somewhere, the cost is generally recouped on monthly charges or advertising. ISPs who do not charge a monthly access charge reckon to get revenue from advertising.
In principle, dial-up costs can be minimized by accessing at as high a rate as possible, but since on a normal dial-up line the technical limit is 56 000 bits per minute and has been reached by modems available in every new PC, no more improvement can be expected.
Increasing the speed of access
The other advantage of speedy access is that it enables high bandwidth multimedia applications, such as full screen video, to be accessed. 56 kbit/s lines are inadequate for this. The alternatives are:
| ISDN: | Integrated Services Digital Network, which allows permanent access in both directions at 64 000 bits per second for a significant cost. Extra capacity in units of 64 kbit/s is obtained by using extra parallel phone lines. ISDN is mostly limited to business use because of expense. |
| ADSL: | Asynchronous Digital Subscriber Link, which relies upon a single phone line being able to carry data for short distances (up to 2.5 km) at much greater rates than for longer distances. It assumes that most of the traffic will be to the consumer, and is ideal for services like video where the consumer is less active. |
| Cable modems: | these rely on the much higher bandwidth (carrying capacity) of cable networks than simple phone lines. The capacity does depend on how many users share a cable link to the exchange, however, and will fall as more people use any particular segment of the cable network. |
| Satellite: | satellites have huge capacity, Gbit/s (billions of bits/s) per channel. If used to broadcast data they could provide millions of web pages per second or hundreds of video feeds. This would be adequate for many purposes, provided that the reverse channel via a normal phone line was available to enable the pages broadcast to be selected by the consumer. |
Electronic mail
E-mail is the electronic equivalent of ‘pigeonholes’ into which incoming mail is placed in organizations that do not deliver to desks. It is easier to mass communicate with pigeonholes, since posting memos into adjacent holes is much quicker than giving them to colleagues. However, you cannot guarantee that the mail message is ever received, certainly not that it is read quickly.
E-mail accounts are electronic pigeonholes held on the internet service provider’s computer. The account owner has to access their account to read the mail message. If they are on holiday, no one else will see a piece of paper on their desk and act on it instead. And many e-mail users simply read the message and do not acknowledge it, so you cannot be certain that it has been read.
So e-mail is not a panacea for poor communications. However, it is good for rapid communications between people who read it, particularly where the telephone is problematic. Attaching files (reports, pictures, etc.) allows documents to be shared quickly and easily, and edited and returned where necessary. Co-operative working between people separated by continents is quite possible. And distribution of text to hundreds of e-mail accounts is possible where the access software allows groups to be set up.
Some words of warning
Blanketing large numbers of people with unwanted mail is called spamming, and is definitely against the code known as ‘nettiquette’. It causes great irritation and the spammer may well be ‘flamed’ with large numbers of angry e-mails.
E-mail is more or less permanent. Once the Send button is pressed, a copy of the e-mail is stored on the local computer, one with the local ISP, one with the destination ISP, then with the destination. Because all of these are backed up and archived a record of the message is retained indefinitely, and may be read by anyone with the right to investigate. E-mail is not the medium for private discussions about company policy, enquiry about jobs with deadly rivals, or gossip. Do not send an e-mail that you wouldn’t sign.
Some companies have the policy of attaching a disclaimer on the end of every e-mail, e.g. from REPP:
The information in this internet email is confidential and is intended solely for the addressee(s). Access, copying, dissemination or re-use of information in it by anyone else is unauthorized. Any views or opinions presented are solely those of the author and do not necessarily represent those of Reed Educational & Professional Publishing or any of its affiliates. If you are not the intended recipient please contact Reed Educational & Professional Publishing, Oxford, +44 1865 311366.
The legal status of such disclaimers has not yet been tested.
The World Wide Web
As explained before, the World Wide Web is a huge network of computers around the world that uses TCP/IP and responds to HTTP requests. This sprawling, rather anarchic network contains a huge amount of information, some for sale, mostly free, with varying usefulness and reliability. If someone wants to set up a website devoted to their own obsessions there is little to stop them, provided that no laws are broken in the country of their ISP. (There is currently some legal argument about the liability of the ISP if the law is broken. Some argue that the ISP cannot be held responsible for pages under the control of individuals; most ISPs play safe and, given a complaint threatening legal action simply disconnect the pages.)
Finding information on the World Wide Web
With hundreds of millions of pages of information available, how is the useful sorted from the useless? There are various strategies:
• Use a table of useful links set up by your institution, often the library. This is a web page devoted to links. If you find other useful pages, the information is generally gratefully received and posted as well. Or try a professional body (see Figure 7.5.2).
• Know the URL and type it directly. This obviously works. What is not so clear is that you can often guess the URL by topping and tailing the company name with http:///www.and.com (e.g. Microsoft is at http://www.microsoft.com). Some browsers will top and tail automatically. For UK companies try.co.uk instead of .com (e.g. the BBC at http://www.bbc.co.uk). Sometimes you must be a bit devious; there is a phone enquiry company at http://www.192.com!
• Use a search engine. Which one you use depends on what you want to find. Some, like http://www.yahoo.com, have developed a huge directory of categorized services to which pages have been submitted; this makes them best if your enquiry fits their categories.
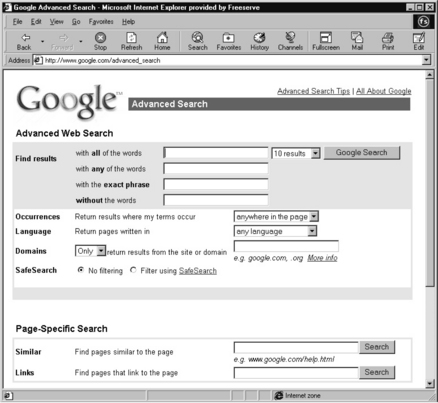
• Others, like http://www.google.com (see Figure 7.5.4), have programs continually scanning the web and keeping their indexes up to date. There are also programs downloadable from the web, such as Web Ferret (from http://www.ferretsoft.com) that know about searching many search engines and can send requests to many and at the same time remove duplicates. This increases the chances of finding a particular page.
If you want specific information from a specific country you can try the national equivalent, e.g. http://www.yahoo.co.fr, but be aware that the information is likely to be in French.
Intelligent searching
Internet searching is like searching any other form of large database. Suppose that you are searching Lycos for articles about CAD. With many millions of pages available, a search for computer aided design will give ‘hits’ on between 10 and 20 pages from millions containing the words computer, aided and/or design. They are often just the last 10 indexed. So you need to be more specific. Try ‘computer-aided design’ in quotes, to search for the exact phrase.
Intelligent searching requires the use of the Boolean connectives – AND, OR and NOT, with and without brackets. So you might search for (‘computer’ OR ‘electronic’) AND ‘design’ AND NOT ‘manufacture’ to refine a search. Remember that:
| AND | means both must items connected must be present |
| OR | means that either one or the other or both must be present |
| NOT | means what follows must not be present |
The order of processing matters. Use brackets to change the normal ‘order of precedence’. Without them NOT is processed first, then AND, and finally OR. In the example above leaving out the brackets would mean that any article mentioning ‘computer’ would be returned.
Lycos (see http:/www.lycos.com, and Figure 7.5.5) also allows the operators ADJ, NEAR, FAR and BEFORE, giving hits from ‘computer design’ and ‘design computer’, ‘computer’ and ‘design’ within the same paragraph, or within 25 words, ‘computer’ and ‘design’ more than 25 words apart, and ‘computer’ before ‘design’.
Some Internet problem areas
Journalists love scare stories about how bloody crimes were incited or made easier by internet sites. Information is more readily available from a networked computer than from a public library, and without the danger of observation. Nevertheless the ‘Molotov cocktail’ petrol bomb and its effects, as so many other items, have been far more graphically illustrated on TV than on the Internet.
Pornography
There is a lot of pornographic material available on the Internet. A search for ‘porn’ will go directly to a range of salacious material. Occasionally a search for something innocuous like ‘banana’, if someone has recently indexed their site under ‘banana’, will produce an unpleasant surprise. Despite the wishes of some, most pornography is not illegal. Better quality images than are available on the Internet can be found at the local video store, the local newsagent, or even the local art gallery.
Child pornography
Child pornography, however, is illegal, and it is not always possible to determine the age of the subject. As a consequence of the ‘Gary Glitter’ case where an ageing pop star sent his computer for mending and ended up in gaol for 4 months, the holding of such images, even the viewing of them, may be held to be illegal. You are recommended to find out how to clear your workstation of any such material, especially if it is shared with others. The innocence of a user of a machine with such files viewable may be difficult to prove. Temporary copies of links and images are stored in the C:WindowsTemp and C:WindowsTemporary Internet Files directories of a Windows machine.
Company disciplinary measures
Most companies regard the display of pornographic images as being offensive and observation of such material in working hours is a disciplinary offence. Sending such images across the company intranet is generally forbidden too.
Policies generally exist about the use of the Internet for non-company work, either because of the time wasted, or because of the potential for internal competition. Sensible usage, especially outside working hours, is generally allowed; it is often in the company’s interest to have net-aware employees.
E-mail is also the subject of many company policies, both offensive and harassing messages that contravene equal opportunities policies, and excessive use for non-company business.
Evidence on record
The company’s network server will keep a record of every page accessed and every e-mail sent or received in the archive files. Whether or not these are trawled regularly, it would seem foolish to leave evidence of anti-social behaviour available, ready for the next shakeout of underperforming staff.
Web page production
In principle, web pages are quite simple to produce from a word processor. If you type a few sentences of information into Word 97, and then save it as an HTML document, you get a text file resembling Figure 7.5.6.
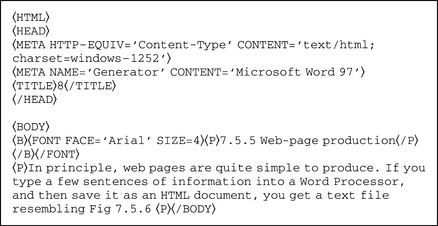
Figure 7.5.6
It appears on screen in a browser as the first paragraph of this section.
The whole document is bracketed by 〈HTML〉 and 〈/HTML〉. These angle bracketed labels are called tags. They usually come in pairs, the second label preceded by a ‘/’ which means cancel.
The header is sandwiched between 〈HEAD〉 and 〈/HEAD〉. It is not displayed and contains useful information about the document, used by indexing programs. It may also contain Javascript (a programming language used to make pages active, produce rollovers, check details entered on forms, etc.).
The body, sandwiched between 〈BODY〉 and 〈/BODY〉, is what appears on screen. It contains some bold text (B), some with a defined font and size 〈FONT FACE=‘Arial’ SIZE=4〉 and a paragraph (P).
Using an HTML editor
It is worth playing with website creation, just to see how it works. There are many introductory texts available to help you. You will also find it easier to create the page using an HTML editor. These vary in price from the free Composer that comes with Netscape Navigator Browser, to packages like Dreamweaver costing a few hundred pounds. You do not often have to go back to the basic HTML to find out why the page will not behave; it is generally easier to redesign the page from scratch using the editor.
Commercial transactions via the World Wide Web
Many people saw the Internet as a ‘new frontier’, a completely new way of doing business; many others who have used telephone sales and mailorder recognize great similarities. In practice many of the early expectations have not borne fruit, except in very specialist areas. The reasons are not difficult to find. The essence of making money from a business is to
(1) Have a product to sell: The Internet has provided its own range of ‘products’ for sale, e.g. website design. Other than these the Internet merely provides another way of selling a product available elsewhere. Where this is more user-friendly, particularly in being less pressurized than, for example, telesales, the Internet scores. Banking services are very open to this; paying a bill is merely the modification of two electronic data values, that of the payer and that of the payee.
(2) Find a customer: Internet businesses have a niche when associated with information sources, e.g. last minute holiday availability. There are also Internet e-marketplaces that allow you to tender to supply goods, often by ‘Dutch auction’.
(3) Do a deal: Electronic systems do not provide good mechanisms for making deals. Until ‘digital signatures’ are easy to work with and legally accepted, it will be very difficult to prove that a deal was made. Legal jurisdiction, for example for a French purchaser accessing a site in Taiwan owned by a US-registered company, is also potentially problematical.
(4) Supply the product: Where this is physical, the Internet cannot help. Where it is a piece of software (music or video would be equally possible) and can be immediately downloaded a big market exists. Other ‘information’ may equally be supplied, e.g. trade reports, or just simply that (having paid), ‘The tickets are waiting at the airport. Give Code: BA173HJK’.
(5) Get paid: Exchange of credit card information is potentially vulnerable to interception. Such information is made more secure by the use of secure encoded information, using the ‘secure sockets layer’ available in TCP/IP. Secure sites direct you to pages with URL starting https:// (the s indicates secure).
The most serious problem that many internet businesses have met is that, in the rush to carve up the available web URLs into lucrative chunks, large sums of money have been invested against projected returns. Where projections were ambitious and income was not generated quickly enough, businesses have foundered. This is hardly a new concept, however; nineteenth century railways were built the same way and investors lost huge sums of money.
Building a commercial system
First you need a product. If it is not transmissible to the customer over the net, e.g. software, designs, information, digital music, do not forget the distribution system (which has to be at least as good as that of your competitors).
Next you need a web server (computer) to deal with http requests arriving from the Internet. It will also have to store data about your products (for advertising) and your customers (their orders and payments). You can outsource this to one of the many internet service providers, who will of course charge. Alternatively you can pay for the technical know-how to do it in-house. Your server will have to be linked to the Internet by, for example, an ISDN link. Negotiate one that can be allowed to grow if the demand is there.
Next you need a designer to produce suitable web pages, attractively laid out but avoiding the overcomplex that are slow to download. These will have to be linked to the database so that you do not have to update your pages every time there is a change of product.
When your web pages are created you will need to let the world know about them. So you will register them with the search engines. This can be done one at a time, on-line, or using a service that will register them with many engines, for a charge.
You’ll need to get registered with a banking service like Visa, so that you can process credit card payments over the net. You may join an internet e-marketplace to get on-line orders and supplies from other traders in your business area.
All this requires investment in equipment and salaries. All you need to ensure is that you have enough capital to cover your outgoings until the money starts rolling in!
Problems 7.5.1
(1) Why was the TCP/IP-based network structure without central control originally set up? Why do you think that academic institutions were ready to join such a system? What effect has this had on the use some have made of the Internet, and the way the Internet is sometimes portrayed in the press.
(2) Some organizations have responded to the Internet by monitoring all usage of both the Web and e-mail. To what extent are they justified in doing so, and what effect would such measures have on your usage of an internet terminal on your desk at work?
(3) Describe the types of company that would find e-commerce particularly beneficial? What would be the major problems that they would have in exploiting their web status?