Chapters 2 and 3 focused on the core processes that must in place when embarking on an IoT and advanced analytics digital transformation journey, namely DevOps and Device Management. This chapter looks at the world of sensors, devices, and gateways. Although we won’t be able to cover all the possible permutations of hardware and software, we will touch upon some of the more common scenarios we encounter and how they relate and work together to create a consistent, secure, and reliable network of connected things.
Sensors
The purpose of a sensor is to measure. Sensors take a measurement of a physical parameter and turn it into a value that can be read electrically using analog or digital circuitry. The physical shape, construction materials, and electronics are dependent on the application. There are many classes of sensors that are differentiated by accuracy, environmental resilience, range, resolution detail, ability to calibrate, and cost (see Figure 4-1).

Figure 4-1. Different types of sensors
There is a robust industry of sensor manufacturers that provide sensor hardware solutions for collecting measurable qualities, including but not limited to:
Position, proximity, dimension, distance, inclination, and motion
Air quality, air pollution, levels of carbon dioxide, hydrocarbon, hydrogen, methane, and oxygen
Electrical current, eddy current, electrical field, magnetic field, and voltage
Weather conditions including temperature, humidity, dew point, heat flow, and smoke
Human and animal blood flow, blood glucose level, blood pressure, body temperature, and heart rate
Acoustic parameters such as loudness, noise, resonance, ultrasound, and direction
Fluid measurements including gauge pressure, mass, volume flow, bulk, and level
vision and identification including image sensors, code detection, and object detection
Optical and luminosity including radiation, light, turbidity, UV, and visible light
This list could go on and on. The key point is that the world of sensors is rich and wonderful, and the cost of these sensors along with the analog to digital converters and microprocessor hardware to connect and communicate has made IoT a ubiquitous commodity. We can measure anything and turn it into a floating-point number.
Tip
When planning your IoT solution, document the properties and capabilities of each of the sensors, as those values have direct impact on your canonical message format and downstream analytics.
If you are using a Single-Board Computer (SBC) such as a Raspberry Pi, you can connect analog sensors using Analog-to-Digital (ADC) adapter shields. These adapters read the voltage coming from the analog sensor and turn that into a digital value. You can communicate with sensors through the UART, I2C, and GPIO interfaces as well.
It is not uncommon to connect your SBC to an intermediary device such as a Programmable Logic Controller (PLC). Sensors may be attached directly to the PLC, or the PLC may gather readings from sensor enabled hardware that is attached to the PLC. PLCs and single-board computers communicate using a serial interface or Ethernet. The SBC software uses a library such as Modbus or Ethernet/IP to communicate with the PLC.
Note
Modbus is a serial communications protocol originally published by Schneider Electric in 1979 for use with its PLC products. Due to its ease of use and popularity, Modbus has become a de facto standard protocol for communicating with PLCs. Ethernet/IP is an industrial network protocol that adapts the Common Industrial Protocol (CIP) to standard Ethernet, and CIP is another popular protocol for industrial automation applications.
Programmable Logic Controllers
Programmable Logic Controllers (PLCs) play an important role in industrial IoT. PLCs are ruggedized computers that are used to provide a programmable interface to industrial machinery, cameras and sensors. A PLC may be used, for example, to control a valve on a chemical storage tank; it monitors the fluid level using a sensor and opens a valve to dispense when the sensor is triggered.
PLCs use special programming languages to customize how they control the machinery and attached sensors. There are five PLC programming approaches that are in use today:
Function block diagram
Ladder logic diagram
Structured text
Instruction list
Sequential function chart
Here is an example of a PLC program that increments a counter each time a pulse generator fires (see Figure 4-2).
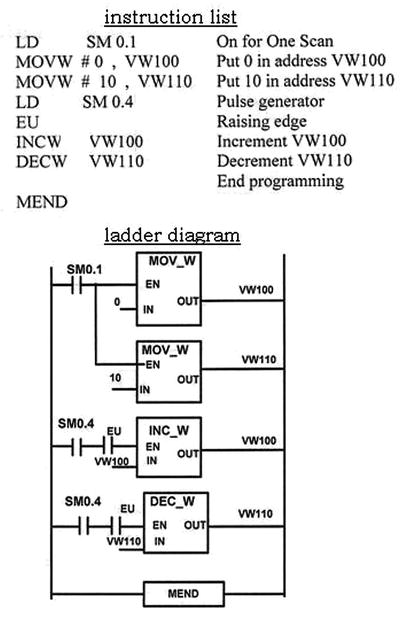
Figure 4-2. Example PLC program from plcmanual.com
PLCs are often used to connect light to heavy industrial equipment to a Supervisory Control And Data Acquisition (SCADA) system, a solution that provides process control for plants and factories. We encounter PLCs when working with clients who are looking to take advantage of IoT to connect their remote products, plants, and factories to the cloud to take advantage of predictive analytics to calculate mean-time-to-failure of their remote systems (see Figure 4-3). If you can predict mean-time-to-failure, you can reduce operating costs by optimizing scheduled maintenance.

Figure 4-3. Examples of light and heavy industrial PLCs
PLCs are not IoT-enabled by default. While it is common today to use an SBC to provide cloud connectivity and communication, GSM modems have been handling these duties for many years. Let’s venture now into the world of devices by first looking at early versions of network capable devices and how they have evolved to what we now call smart devices.
Devices
As stated in Chapter 1, IoT is not new. For certain industries, the ability to track and communicate has been central to their businesses such as the shipping container, vending machine, and trucking industries. Before today’s explosion of connected “things” that leverage the latest advancements in microprocessor technology and low-power wireless technology, the use of cellular modems had been in wide use to provide machine-to-machine (M2M) communication. It is common for companies to look to take advantage of the public cloud while also supporting their legacy M2M ecosystem using the same IoT infrastructure.
GSM Modems
GSM modems are cellular capable devices. They can accept a SIM card and host-embedded software and connect to a cellular provider such as ATT or Verizon. They use an RS232, RS485, or RS422 serial port to connect to a PLC that provides the data to be transmitted (see Figure 4-4). Once connected to the carrier, the embedded software uses a VPN connection to a corporate network to connect to a known IP address—a server—that accepts incoming data and provides responses. The connection from the carrier through the VPN to the server and the transmission of data is not continuous, as we have come to expect in our world of ubiquitous networking and connected things. The cadence is usually a few times a day and in some cases less often to control costs.

Figure 4-4. Elementz engineers guild GSM modem
To integrate a GSM modem with our Azure-hosted IoT sub-system, we need to provide a proxy that sits between the GSM modem and Azure IoT Hub. This proxy presents itself to the GSM modem as an IP addressable server sitting behind a secure VPN network and manages the interactions with the cloud. We refer to this proxy as a protocol gateway as its job is to translate from the legacy data formats and GSM modem commands supported by the modem’s embedded software to the canonical message formats expected by our services.
Protocol Gateway
A protocol gateway is a cloud service deployed in the context of a VPN and made IP-addressable through cloud configuration. The protocol gateway provides a message and command-and-control translation layer between the GSM modem and Azure IoT Hub. The protocol gateway acts as a device management proxy as well, invoking the device startup process as outlined in Chapter 3, leveraging the device API to look up the device manifest and use that information to connect to IoT Hub on behalf of the GSM modem.
Microsoft provides the Azure Protocol Gateway as a starting point for a protocol gateway implementation. The Azure Protocol Gateway is a framework that enables bidirectional communication with Azure IoT Hub. The protocol gateway programming model also allows you to plug in custom components for specialized processing such as authentication, message transformations, compression, decompression, and encryption and decryption of traffic between the remote devices and IoT Hub. Since GSM modems are occasionally connected, this feature could be used to add a plugin for caching device management commands that are applied the next time the modem dials in (see Figure 4-5).
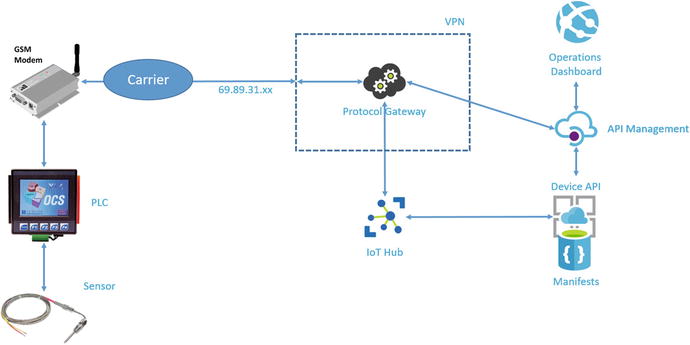
Figure 4-5. GSM modem integration using a protocol gateway
Note
For additional information on the Azure Protocol Gateway, see https://github.com/Azure/azure-iot-protocol-gateway .
GSM Modems and SMS
Since a GSM modem is essentially a mobile phone without the keyboard, screen, speakers, and headphone jack (is that still a thing?), and it can use Short Message Service (SMS) to send and receive messages. While this is not the most reliable communication option, it can still play a role in communicating small pieces of information for occasionally connected scenarios in a cost-effective way.
To support SMS communication, we can use a service such as Twilio to provide two-way communication with the GSM modem. To complete the communication chain, we can add an additional ReST service that provides an endpoint for Twilio and provides the protocol translation between the SMS messages coming from Twilio and our services. Let’s call this service the SMS Gateway API.
The GSM modem sends SMS messages to Twilio which in turn forwards that message to the SMS Gateway API. The SMS Gateway follows the device startup process outlined in Chapter 3, invoking the device API to retrieve the manifest for the GSM modem and using that information to connect to IoT Hub (see Figure 4-6).

Figure 4-6. GMS modem integration using Twilio and a custom SMS Gateway API
RFID
Radio Frequency Identification (RFID) is a system that uses tags that are attached to or embedded in things. The tag can be passive or active. Active tags are battery powered and are activated when an RFID reader is within proximity. Tags contain a unique ID, a serial number, and application-specific data. For example, if the RFID tag were attached to a piece of clothing in a retail store, the tag would contain its unique serial number along with the product details for the clothing such as SKU number, name, color, size, etc.
To communicate with tags, two-way radio RFID readers send signals to the tags and receive the stored data in response (see Figure 4-7). Tags may be read-only or writable, i.e., the RFID readers can update the contents of the tag. RFID reader systems have a transmit/receive range anywhere from 1 to 2,000 feet. The range can be calibrated so that RFID tags are only read when they are within a well-defined zone around the reader. This is useful, for instance, if you want to set up a zone on a conveyor belt so that tags are read when they pass underneath the reader.

Figure 4-7. RFID tags and readers
When used in IoT scenarios, RFID tags and RFID readers are used in conjunction with smart devices that communicate to the cloud as well as transform, filter, and aggregate the RFID data.
For example, a clothing store could RFID tag all the merchandise and mount RFID readers in the ceiling to continually communicate with the RFID tags to track product location and SKU information. Using this information, you would be able to construct a real-time view of store inventory and product location using IoT services. While some retailers are using RFID, they are tracking inventory manually using RFID handheld devices and they are not coordinating the store inventory data with the inventory levels advertised on their web sites. A solution that provides real-time inventory and product location visualized through web and mobile applications for store management, employees, and customers would be transformative in the retail industry.
The smart device, in this scenario, would provide data filtering and transformation in addition to handling communication with the cloud services (see Figure 4-8).
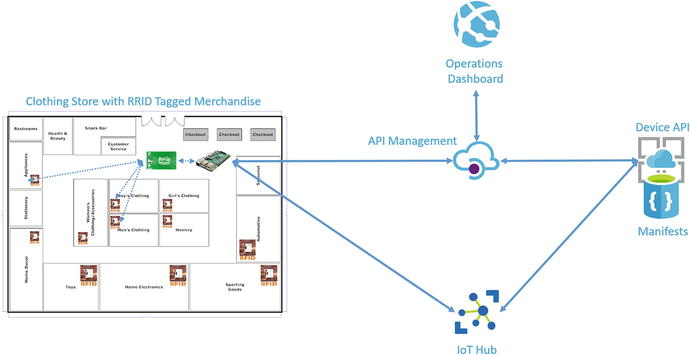
Figure 4-8. Clothing store using RFID to track real-time inventory and product location
Bluetooth Beacons
Bluetooth is a wireless technology standard for exchanging data over short distances. Bluetooth beacons are small, battery powered devices that can be attached to or embedded in things. Any Bluetooth enabled receiver such as a mobile phone or smart device with the Bluetooth stack installed can connect to and communicate with beacons when they are within range. Ranges vary by class of device from less than a meter to upwards of 100 meters (see Figure 4-9).

Figure 4-9. A deconstructed Bluetooth beacon
A common scenario is to use Bluetooth beacons positioned within a building along with a mobile phone application to provide location awareness. It is possible to use multiple Bluetooth beacons to perform triangulation and determine not only 2D coordinates within a space but also calculate height providing a 3D location (see Figure 4-10). In an assisted living space, this could be used to determine if someone is standing or lying down on the floor possibly needing assistance. An IoT solution could automatically alert first responders, turn off appliances, and unlock the door when first responders arrive.
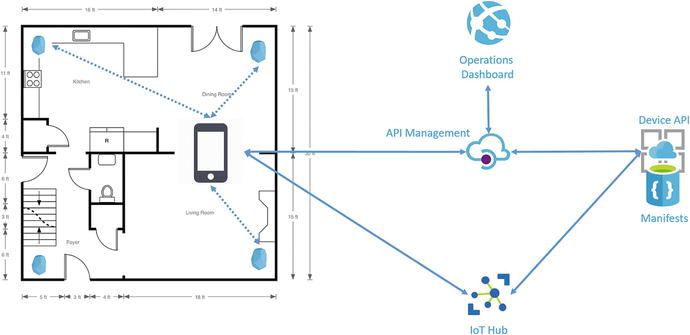
Figure 4-10. Bluetooth beacons and mobile phone used for location awareness
Get Smart
Both RFID and Bluetooth beacons are only useful when combined with a smart device. So, what is a smart device? Hollywood has done the bulk of visionary work in this field. One need only look to popular movies and TV to find the early prototypes of devices and technology we now use every day. Don Adams, who starred in the hit TV series Get Smart from 1965 to 1970, can be seen in Figure 4-11 demonstrating early versions of smart devices we now use every day.

Figure 4-11. Visionary prototypes of smart devices (General Artists Corporation-GAC-management. Transferred from en.wikipedia to commons.)
A smart device , such as a Single-Board Computer (SBC) , consists of a credit-card sized microprocessor board with a powerful chipset, memory, storage, and I/O capabilities. It can connect to and read sensors using technologies such as Modbus for PLCs, radio signals for RFID tags, and Bluetooth for beacons. It can also use the I/O channels on the motherboard to communicate with attached sensors. It may use wired, wireless, or a cellular modem to connect to a local network or carrier and onto the public cloud. It can run applications that process the sensor data, apply mathematical operations, and handle all the interactions with the cloud and APIs. In other words, a smart device can be as smart as you program it to be.
It’s important to note that a mobile phone is a smart device and is frequently used in IoT scenarios as described earlier. The phone itself has embedded sensors such as GPS and accelerometers. It can also run applications that use Bluetooth to connect to Bluetooth beacons when in proximity.
Single-Board Computers
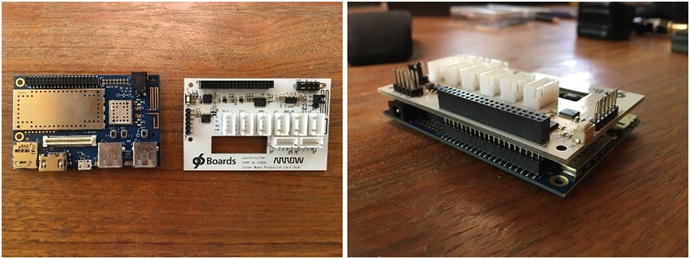
The Raspberry Pi, Qualcomm DragonBoard, and Intel Edison are examples of small, inexpensive, yet powerful SBCs that can run embedded operating systems such as Linux and Windows 10 IoT. They can be customized using shields (add-on boards), sensors, and LCD displays that attach using pins or cables. These microprocessor boards also support connecting HDMI displays, MicroSD cards, and USB devices (see Figure 4-12).

Figure 4-12. Example SBCs with shields and sensor kits
SBCs can be used to prototype your IoT hardware solution and even become the foundation of your device ecosystem. You may need to enclose your SBC in light to heavy industrial materials depending on the environmental conditions into which the device will be deployed (see Figure 4-13). Is the device indoors or outdoors or exposed to extreme heat or cold, dust, humidity, or vibration? This needs to be considered when designing your hardware solution.

Figure 4-13. Examples of Raspberry Pi enclosures
To develop the embedded microcontroller software, Microsoft provides IoT Device SDKs across several different programming languages, including Python, Node.js, Java, C, C++, and C#.
Note
For detailed information on the Azure IoT SDKs, see https://github.com/Azure/azure-iot-sdks .
Azure IoT Device SDKs can be used with a broad range of operating system (OS) platforms and devices. The minimum requirements are that the device platform:
Be capable of establishing an IP connection: Only IP-capable devices can communicate directly with Azure IoT Hub.
Support Transport Layer Security (TLS): Required to establish a secure communication channel with Azure IoT Hub.
Support SHA-256: Necessary to generate the secure token for authenticating the device with the service.
Have a Real-Time Clock or Implement Code to Connect to a Network Time Protocol (NTP) Server: Necessary for establishing the TLS connection and for generating the secure token for authentication.
Have at Least 64KB of RAM: The memory footprint of the SDK depends on the SDK and protocol used as well as the platform targeted. The smallest footprint is achieved using the C SDK targeting microcontrollers.
You can find an exhaustive list of the OS platforms the various SDKs have been tested against in the Azure Certified for IoT device catalog (see Figure 4-14). Note that you might still be able to use the SDKs on OS and hardware platforms that are not listed. All the SDKs are open source and designed to be portable. The Azure-Certified IoT Device Catalog is located at https://catalog.azureiotsuite.com/ .

Figure 4-14. Azure-certified IoT device catalog
Microcontroller Software
Now that you have a small compact device that is running a modern, secure, embedded operating system, and full networking stack, you can leverage that power to implement the controller software that will read sensor data and integrate directly with IoT Hub and the ReST APIs.
There are three core messaging patterns employed by smart devices :
Heartbeat: Send an occasional ping message at regular intervals
Telemetry: Send telemetry at regular intervals often
Command and Control: Receive incoming commands and data
As covered in Chapter 3, IoT Hub provides two additional message patterns that are variations of command and control:
Device Twin Events: Receive device property change events
Direct Methods: Provide function handlers for remote request/response invocations
Each of these operations is handled asynchronously, ensuring that the device is performant and no single operation blocks the others.
In addition to the device client SDK, we want to invoke our Device API to retrieve the device manifest. If you recall, the device manifest contains the URI to your instance of IoT Hub and the symmetric key for the device to authenticate. The following C# example demonstrates what the startup sequence would be for a device running Windows 10 IoT .
// reference the Azure Devices Client SDKusing Microsoft.Azure.Devices.Client;...// device constants; Id, Device API and Dev Keyprivate const string DeviceSerialNumber = "[your-device-id]";private const string DeviceApi ="https://[your-apim-host].azure-api.net/dev/v1/device/manifests/id/" + DeviceSerialNumber;private const string SubscriptionKey ="subscription-key=[your-apim-devkey]";...// properties for manifest and IoT Hub clientprivate static Manifest _deviceManifest;private static DeviceClient _deviceClient;...// invoke the Device API to retrieve the device manifest_deviceManifest = await GetDeviceManifest();// connect to IoT Hub_deviceClient = DeviceClient.Create(_deviceManifest.Hub,AuthenticationMethodFactory.CreateAuthenticationWithRegistrySymmetricKey(_deviceManifest.SerialNumber,_deviceManifest.Key.PrimaryKey),TransportType.Amqp);
These few lines of code provide secure integration with your cloud services (see Figure 4-15). We examine this code in more detail later in this chapter as you create your own smart device-embedded software.

Figure 4-15. Smart device integration to the cloud services
Edge Gateways
Edge gateways are powerful smart devices that act as intermediaries between an ecosystem of devices and the cloud. By introducing this intermediary, you can apply more advanced operations on the sensor data locally before it is sent to the cloud. These local operations include but are not limited to:
Aggregation: Build a collection of sensor readings
Logging: Provide a transient store of the most recent events, collections, alerts, etc.
Analytics: Apply mathematical operations to a collection of sensor readings such as average, standard deviation, Fast Fourier Transform, linear regression, etc.
Filtering: Apply a filter to a collection of sensor readings
Rules: Apply business rules defined by upper and lower thresholds defined by the sensor properties
Alerts: Identify out-of-bounds readings and signal alerts using physical notifications such as flashing lights and whirring sirens or leveraging cellular capabilities to send text and voice messages
Windowing: Collect telemetry and/or alert conditions over a defined period of time and only report when a windowing threshold has been exceeded, e.g., perform an alert when there are more than five errors every minute
The microcontroller software running on an edge gateway device defines a data pipeline for each type of telemetry it is responsible for. The data pipeline is made up of one or more modules that act on the data flowing through the pipeline. The order of operations matters, and you also want to be able to configure the modules at runtime.
Microsoft provides the Azure IoT Gateway SDK to assist in the development of edge gateways. This SDK provides a framework for defining pluggable modules that communicate through a message broker backbone. Each module you define and configure performs its operation on the oncoming message(s) and writes a possibly transformed message back to the broker for the next module.

Figure 4-16. Azure IoT gateway architecture
Note
For more information on the Azure IOT Gateway SDK, see https://azure.microsoft.com/en-us/services/iot-hub/iot-gateway-sdk/ .
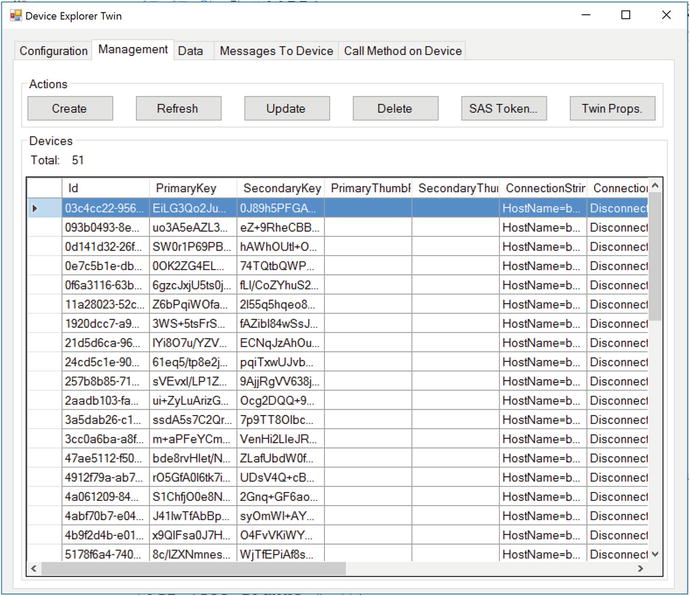
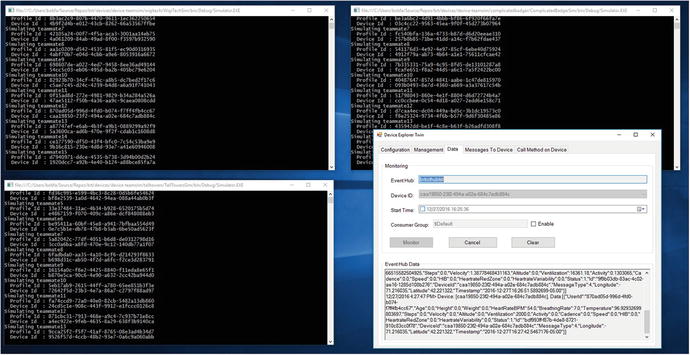
In the following exercises, you learn how to create a simple smart device and deploy an application to an SBC. In addition, you will update the device simulator that is used to generate the biometric data for the IoT solution.
Summary
This chapter examined the rich and wonderful world of sensors and devices and the various ways different configurations can connect to Azure IoT Hub. It examined GSM modems, single-board computer smart devices, and edge gateways. You learned about the Protocol Gateway SDK and how you can use that to provide a translation layer between legacy devices and the new cloud services. You examined the architecture of edge gateways and the IoT Gateway SDK and how to use these devices to provide aggregation, filtering, and analytics at the edge.
Through the exercises, you learned how to implement the microcontroller software that runs on your remote devices, reads sensors, and sends messages to IoT Hub. Finally, you configured the team simulators so you can drive a feature-rich set of advanced analytics provided by the reference implementation.
The next set of chapters turns to those advanced analytics and leverages the data coming from the simulators. They cover stream analytics, data factory, data lake, and Machine Learning.