This chapter covers the following Cisco-specific objective for the “Implement and verify WAN links” section of the 640-822 ICND1 exam:
<objective>Describe different methods for connecting to a WAN
</objective> <objective>Configure and verify a basic WAN serial connection
</objective> </feature><feature><title>Outline</title>518 | |||
518 | |||
519 | |||
519 | |||
519 | |||
520 | |||
520 | |||
521 | |||
521 | |||
522 | |||
523 | |||
523 | |||
524 | |||
524 | |||
524 | |||
524 | |||
524 | |||
525 | |||
525 | |||
525 | |||
527 | |||
527 | |||
527 | |||
529 | |||
530 | |||
531 | |||
532 | |||
532 | |||
532 | |||
534 | |||
535 | |||
537 | |||
539 | |||
539 | |||
540 | |||
540 | |||
543 | |||
544 | |||
546 | |||
546 | |||
548 | |||
Read the information presented in the chapter, paying special attention to tables, Notes, and Exam Alerts.
Although Wide Area Network configuration is important, many of the advanced configuration options discussed are reserved for the CCNP BCRAN exam. At the CCNA level, be sure to focus on understanding the concepts thoroughly.
Because it is in widespread use, focus your energy on learning the ideas behind the PPP protocol. Be sure to pay special attention to the authentication concepts.
In nearly all traditional Cisco texts, Wide Area Networks (WANs) are typically moved to the end of the book. This is amusing to me because WAN connectivity is usually listed in the top three functions of a router. WAN connections do just that: connect networks that have a wide area separating them. This type of connection requires you to work with one or more service providers that supply the logical connections between your locations.
The good news about WAN connections is this: These technologies only encompass only the Physical and Data Link layers of the OSI Model. Just like the concepts of ethernet and token ring, WAN links are just another method of transporting data between devices. So with only two layers worth of technology, WAN links should be fairly simple to learn, right? Well, that’s the bad news: Because of the ever-increasing demands of the IT machine, WAN links have become increasingly complex to the point where they can be a specialization in themselves. Thankfully, the CCNA exam focuses primarily on two specific types of WAN connections:
Although there are many more WAN connection types, these are currently the most popular. By studying these WAN connections you will learn the foundation concepts behind WAN connections in general, making it easier to learn any new WAN technologies as they emerge.
Objective:
Describe different methods for connecting to a WAN
The following three categories of WAN connections comprise most of the connections used by businesses around the world. As the name implies, each of the WAN connection categories contains multiple connection types. If you ever called a service provider and asked for a packet-switched connection, the next question would inevitably be, “What type?.”
This connection category is what most people are familiar with when they hear the term, “WAN connection.” A leased line connection provides a dedicated, point-to-point link between two locations. The beauty of this connection type is that you have a virtual private road between your sites. You have complete control over the traffic on that road; nobody else can share the road with you. If you have a T1-speed connection (1.544Mbps) between your locations, that bandwidth is always dedicated to you, regardless of whether you use it or not. Therefore, leased lines are typically the most expensive connection types.
The two factors that directly affect the cost of a leased line are:
How far apart, geographically, the sites are located
The amount of bandwidth required
Leased lines are the most appropriate when you need a fixed amount of bandwidth and complete control over all your traffic. Companies that are implementing Voice over IP (VoIP), which runs their telephone system over the data network, will usually vie for leased line connections. Because the telecommunications carrier (service provider) is dedicating the leased line bandwidth to you, they can provide a guaranteed level of service. This not only includes the uptime (reliability) of the line, but also delay requirements. The delay of the line is how long it takes a packet to get from the entry point to the end of the connection. Long delays can cause the quality of a VoIP call to degrade to the point of sounding like a bad cellular phone call. Because the service provider typically has end-to-end control over a leased line connection, they can guarantee a specific level of delay.
Anytime you hear the hum of a dial tone followed by the rhythmic beeping of digits, you are more than likely connected to a circuit-switched network. This type of connection establishes a dedicated channel (or circuit) for the duration of the transmission, and then tears down the channel when the transmission is complete. This is known as a dial-on-demand connection. The largest circuit-switched network in the world is the telephone system, which links together many different network segments to create an end-to-end circuit for each telephone call.
Circuit-switched networks can be called a “connection-oriented” network type. They are most useful when you have small amounts of data to reliably send at a time. Some circuit-switched networks charge on a per-use or per-minute basis (primarily ISDN), so the amount you pay for the connection is directly related to how much you use it. This type of connection would be ideal for a small office that uses local area network (LAN) connectivity during the day and then replicates all the updated data back to the main site in the evening. For example, you might have a sales office that creates a log of transactions that it sends back to the corporate headquarters at night.
Packet-switched networks enable the service provider to create a large pool of bandwidth for their clients, rather than dedicate specific amounts of bandwidth to each client (as in leased lines). The client can then dictate what circuits they would like established through the service provider network between their sites (these are called permanent virtual circuits), providing an end-to-end connection. By using packet-switched networks to provide WAN connectivity, you can gain lower-cost WAN connections that can potentially provide more bandwidth to your locations.
When you sign up for a packet-switched network, the service provider gives you a guaranteed level of bandwidth. The higher your service guarantee, the more you pay for the connection on a monthly basis. The great aspect of a packet switched network is that you usually get more than you are guaranteed; depending on the type of contract you negotiate with the service provider, you could get much more bandwidth than you are guaranteed. However, you must realize that this bandwidth is just that: non-guaranteed. If you send extra traffic during a busy time of day, the service provider can drop the traffic and be well within the service contract. This also applies for delay guarantees. Because traffic sent through a packet-switched network may take different paths (depending on the service provider’s infrastructure) to reach the destination, most service providers offer a very loose delay guarantee (if they decide to offer one at all).
Broadband technology, in its base definition, is a system that enables you to send multiple signals over a wire at one time. The alternative technology, baseband, enables you to send only a single signal over the wire at a time. Broadband connections primarily encompass small office/home office (SOHO) WAN links that use cable modem or DSL technology to connect to the Internet. A cable service provider sends multiple signals over a cable coaxial line, enabling a home user to run many services, such as cable television, high-speed Internet, and telephone service, over a single line. Telephone providers are offering the same services through the copper phone line connections.
Medium and large businesses are just now beginning to consider cable and DSL connections as backup Internet connections for their main offices. Broadband technology is one of the newest WAN connection offerings to market, and has yet to prove its reliability on a long-term basis.
VPNs are not a specific type of WAN connection, but are often used to accomplish the same purpose as a WAN connection. Connections to the Internet have become widely available at an extremely low cost (when compared against the other types of WAN connectivity). Rather than purchasing dedicated circuits between locations, you can just purchase a standard Internet connection at each site. The quality of your Internet connection determines the quality of your WAN connectivity. After all sites have a connection to the Internet, you can then create tunnels through the Internet to each location, enabling the sites to connect through a full-mesh relationship (every site is directly connected, through the Internet, to every other site). These tunnels isolate the interoffice connectivity from the rest of the Internet traffic and secure the traffic through heavy encryption algorithms.
The VPN tunnels are created with the application of a heavy amount of encryption to the traffic sent between the locations. Because sending your company’s private data across a public network, such as the Internet, could be perilous, you should scramble (encrypt) your data before sending it. Because the process of encrypting and de-encrypting data is extremely hard on a router processor, you may choose to offload this work to a router VPN card (a hardware add-on), a PIX firewall (Cisco’s firewall platform), or a VPN concentrator (a specific device manages and maintains many VPN connections). Within this concept lie the advantages and disadvantages of using VPNs for your WAN connections. The major advantage is the cost: You can establish full connectivity between all your locations for a small fraction of what it would cost to purchase dedicated WAN links. You can also allow home users to connect into the office through a VPN connection to allow for telecommuting employees. The disadvantage is the delay incurred in applying the VPN encryption algorithms and the unreliable nature of the Internet. Although the Internet is the most redundant network in the world, because of the massive amount of traffic that crosses the Internet daily, the delay can be inconsistent.
Metro ethernet technology began to emerge early in the new millennium as a viable alternative to traditional WAN connections when connecting offices within a metropolitan area (primarily major cities). At the end of the century, .com-based businesses were booming. Many of these companies began laying complex fiber optic–based networks throughout many of the major metropolitan areas of the nation. When the world economy plummeted at the turn of the century, many of these .com companies went out of business, leaving huge amounts of unmanaged fiber cable under the city streets. This fiber was quickly acquired by local service providers and is slowly being leased to their customers.
Using this fiber to connect offices in the same general region allows for WAN links at speeds of 1000Mbps or greater, at a fraction of the cost of a standard T1 line. The WAN link can even terminate onto a standard Category 5E/6 UTP copper cable and plug directly into a switch using a fiber to copper converter at the customer premise. This enables the WAN connections to be managed completely through VLANs with no dedicated router hardware in place. The connections, which are already fast enough, become even faster.
Metro ethernet is beginning to stretch even between cities, as service providers are planting fiber-optic cable runs between major metropolitan areas. It shouldn’t be too long before intranation WAN links are rated in terms of Gbps as a standard. Metro ethernet is becoming quite popular in government organizations that have many locations in the same general geographic region.
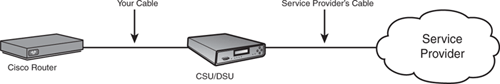
The physical connections for WANs are very diverse, primarily because of the diverse form factors that were created by CSU/DSU manufacturers. The Channel Service Unit/Data Service Unit (CSU/DSU) device is the box that connects and converts your WAN cabling to the service provider’s WAN cabling. Although CSU/DSUs often have many lights, buttons, and LCD displays, they are typically nothing more than a glorified terminal adapter, converting between the service provider’s cable and your local router connection. Figure 17.1 shows a typical physical layout for a WAN connection.
If a CSU/DSU is involved, you will be responsible for purchasing the cable that connects your router to the CSU/DSU unit.
Cisco routers primarily use serial interfaces when connecting to a WAN. The Cisco interfaces come in two types: DB-60 serial interfaces and Smart Serial interfaces. Typically, older routers use the DB-60 style interfaces, whereas newer routers use the Smart Serial interfaces. The DB-60 interface received its name because of the 60 pins in the interface. Smart Serial interfaces are much more space efficient, and can squeeze two interfaces into the same WAN Interface Card (WIC) that the DB-60 interface used.
These WIC interfaces can be installed into any of Cisco’s mainline routers (1700 series, 2600/2800 series, 3600/3800 series).
After you have installed the interface, you must then purchase the cable that connects your router to the CSU/DSU. This cable converts from one of Cisco’s two proprietary interface types (DB-60 or Smart Serial) to a standards-based CSU/DSU connector. Five primary standard connectors have been created for the CSU/DSU units: V.35, X.21, EIA/TIA-232, EIA/TIA-449, and EIA/TIA-530. The most common connector in North America is V.35.
Notice how these cables convert from the Cisco proprietary Smart Serial or V.35 connector to the industry standard V.35 connector, which would connect to the CSU/DSU device.
T1 interfaces use an RJ-48 connector. These interface types usually come with a built-in CSU/DSU, which eliminates the need to purchase an outside box and thereby eliminates another point of potential failure in your network. Upon initial inspection, the RJ-48 connector looks exactly like the RJ-45 connector used for ethernet technology, but don’t be fooled! The RJ-48 connector is very different. First off, it is fastened to Shielded Twisted Pair cabling (STP) instead of the standard Unshielded Twisted Pair (UTP) of ethernet. This reduces line noise on these connections. This is important because WAN connectivity is much more susceptible to interference than LAN cabling. In addition, the voltage sent across these wires, the pin-out arrangement, and the line capacitance is different on the RJ-48 connection than RJ-45.
After you have the Physical layer plugged in, you must move up to the Data Link WAN encapsulation. Just as with the Physical layer, a variety of standards are available for the data link connections. However, the choice of the Data Link protocol is usually much simpler. As long as your WAN connection supports the Data Link encapsulation you use and you are using the same type of encapsulation on both ends of the connection, the WAN link will work. Sometimes, the type of WAN connection you are using forces you to choose one, specific Data Link encapsulation. For example, if you sign up with a service provider for a Frame Relay connection, you must use Frame Relay Data Link encapsulation. Likewise, if you sign up for an ATM connection, you must use ATM encapsulation. Other times, there may be some flexibility on the choice of protocol you can use. For example, if you sign up for a point-to-point T1 connection, you can use Cisco HDLC, SLIP, or PPP for your data link encapsulation. Here is a brief description of each of the encapsulation types.
SLIP is a standards-based protocol for point-to-point serial connections that use only TCP/IP. This was primarily used for dial-up connections to the Internet back in the earlier days of the Internet. It has been widely replaced by PPP.
This protocol has largely replaced SLIP connections for point-to-point WAN connections and dial-up networking. PPP was released as an improvement to SLIP and added support for non-TCP/IP protocols and encrypted authentication (among many other features). PPP is the most popular protocol for connecting point-to-point WAN connections.
HDLC was originally designed as an open standard protocol, meaning all routers could support it. However, the open standard version of HDLC was pretty horrible. It did not support multiple network-layer protocols, which meant that you could support only one protocol (such as TCP/IP, IPX/SPX, or AppleTalk) over your WAN connection. In view of this shortcoming, Cisco modified the standard HDLC to support this missing feature. However, anytime a standard is modified, the protocol becomes proprietary. In this case, you can use HDLC only on Cisco routers to connect to other Cisco routers. HDLC is the default encapsulation on all serial interfaces on Cisco routers. Although HDLC does not have as many features as PPP, it does offer very low overhead, which makes your WAN connections very efficient.
This encapsulation is used on X.25-based networks, which is the predecessor to Frame Relay. Although X.25 is used rarely in well-developed countries, it has widespread use in countries not as technologically advanced.
This encapsulation relates directly to the Frame Relay WAN connection, which is the faster successor to X.25. Frame Relay increased its speed capabilities by removing much of the error correction that is no longer needed on the more reliable circuits of today. Frame Relay has widespread use in nearly all well-developed areas.
This technology is very similar to frame relay, but chops packets into very small pieces (53 bytes each) called cells. Because all the frames are exactly the same size, routers are able to process them much quicker. ATM also has the capability to run at very fast speeds because it adapts to run over fiber optic cabling.
As mentioned previously, HDLC in its truest form is an industry standard created by the International Organization for Standardization (ISO). These are the same folks who created the OSI Model (bless their hearts). Because the ISO version of HDLC lacked the support for multiple protocol use, Cisco modified it and caused HDLC on Cisco routers to become a proprietary protocol.
The beauty of HDLC is that it is very simple and works out of the box. Typically, if you are deploying a WAN connection with a Cisco router on each side of the link, it eliminates plenty of troubleshooting involved in trying to enable the connection with HDLC, even if you plan on using PPP in the long run. Because HDLC is so simple, there are no options to negotiate and you can rule it out of any troubleshooting you may encounter. If the link is not coming up, it is usually something on the service provider side of the business.
Because HDLC is enabled by default, you don’t need to perform any additional configuration for the data link configuration of your serial interfaces. However, if the data link encapsulation was changed to something other than HDLC, you can re-enable HDLC by moving into interface configuration mode for the serial interface you want to use and type the command encapsulation hdlc.
Objective:
Configure and verify a basic WAN serial connection
The PPP protocol has become the industry standard for connecting multi-vendor environments over WANs. Whenever people think about using an “industry standard” for anything, they usually think of the bland, saltine-cracker type of protocol. Surprisingly, PPP defies the norm and is one of the most feature-packed WAN protocols in existence. Although it functions at the Data Link layer of network connectivity, it comprises multiple sub-protocols that serve multiple functions. This provides you with a feature-rich connection, even when bringing up a WAN link between non-Cisco devices.
PPP can function over nearly any type of WAN connection that does not implement its own, specific mechanism for transporting data (such as frame relay and ATM). This means you can use PPP to connect if you are using an asynchronous (modem-like) connection or a synchronous (high-speed) point-to-point serial connection.
Although PPP fills a single layer on the OSI Model (the Data Link layer), it has multiple “sub-layers” that give it all its functionality. Each sub-layer adds specific functionality to the PPP protocol suite. Figure 17.2 depicts the three PPP sub-layers as they relate to the OSI model. Notice that all three of these sub-layers fit into the single Data Link layer.
It is easy to get confused when expanding the already confusing OSI model into sub-layers for a specific protocol. This is just a logical view of the PPP protocol describing how it is able to include all the functions it advertises. The following sections look at each of these sub-layers, one at a time.
Exam Alert
You need to know the sub-layers of PPP and their functions for the CCNA exam because these directly relate to the features PPP provides.
Initially, seeing this layer in PPP seems quite odd. Wasn’t HDLC a competing protocol to PPP? This sub-layer of PPP comprises the industry standard ISO HDLC. This sub-layer is responsible for allowing PPP to be supported by multiple devices. It gives the devices that run PPP common ground to stand on when they communicate with each other. As you will see in just a moment, the LCP layer above is responsible for negotiating all the features of HDLC. Because all devices that run HDLC may not support every single feature, the HDLC sub-layer enables the base PPP communication to continue, even if the platforms support different features.
You can think of the LCP sub-layer as the feature negotiation layer. All the features that PPP supports are negotiated by LCP. These features are:
The authentication features of PPP enable you to require a username and password for the connecting device to bring up the WAN connection. This is not a very important feature on leased line, point-to-point connections because the only way a hacker would be able to get a device connected to the WAN would be to render one of the on-site administrators unconscious and replace the on-site router with one of the hacker’s own. The PPP authentication features are most useful for dial-up connections that could be reached by users connected to the Public Switched Telephone Network (PSTN).
For example, you may choose to connect a modem to your router through the AUX port to allow dial-up access, should all the LAN and WAN connectivity to the router fail. This modem would be assigned a phone number, accessible from any computer modem in the world. PPP authentication would require a username and password to be entered before the modem connection would bridge a successful connection.
There are two types of authentication supported by PPP: the Password Authentication Protocol (PAP) and the Challenge Handshake Authentication Protocol (CHAP).
This authentication protocol is one of the earliest authentication types to be released for WAN connectivity. If PAP is enabled for the connection, the call flow progresses as follows:
Client dials up to a router running PPP.
After the link (connection) is established, the client sends its username and password at the LCP (feature) layer.
The PPP router checks the username and password against its user database and allows or denies the client.
Although this list of three steps is a logical authentication process, it has a few flaws. First off, the client dictates the timing of sending the username and password; the server (router running PPP) receives the username and password whenever the client decides to send it. This causes the PAP mechanism to be susceptible to playback attacks. This is a type of attack where a hacker captures (sniff) packets from a conversation and then plays the packets back in an attempt to mirror the connection. Because the client is in complete control of the authentication attempt, the server accepts the played-back packets whenever the client decides to send them.
The authentication of PAP is also done in clear text, which makes it even more vulnerable to packet-sniffing intruders. Anyone who does have a way of monitoring the connection can capture the packets, break them open, and find the username and password used for authentication in clear text. Can you say, “network devastation”?
With all this being said, the only reason you would choose to use the PAP method for authentication is if you were using very old equipment that did not support the newer method of authentication, CHAP.
CHAP is a much more secure procedure for connecting to a PPP-based system. The authentication process for CHAP goes like this:
Client dials up to a router running PPP.
The router sends a challenge message to the client.
The client responds with the hash of the password it is configured to use.
The router looks up the password hash against its database. If the hash matches, the client is allowed into the network.
After the client is authenticated, the router sends re-authentication messages at random intervals, requiring the client to send the password hash whenever prompted.
Doesn’t that list already make you feel better than PAP? The first thing to notice is that the router (server) is in control of the authentication process. Rather than accepting the username and password whenever the client decides to send it, the router demands the username and password on its timeframe. If the client isn’t ready to ante up with the credentials, the server immediately terminates the connection. This makes performing a playback attack much more difficult to accomplish.
Even if a hacker were to successfully execute a playback attack with CHAP, the random authentication interval ensures the hacker will not be connected for long. Executing the initial playback attack would require intricate timing for the hacker to be successful. The random authentication requests would be nearly impossible to keep up.
The clear text issues have also been solved by using a system known as password hashing. Without getting too deep into cryptography and security mechanisms, you must understand that this is not the same thing as encrypting a password and sending it across the network. Given the time, nearly any encryption algorithm can be broken if the data is captured. Using a hashed version of the password means that the client never actually sends the real password across the line. To accomplish this, the router (PPP server) and the PPP client must be configured to have the identical password. Before the client sends the password, it runs an irreversible mathematical algorithm on the password. The result of that algorithm is called the hash, which is sent to the server. The server runs the same algorithm on its password and compares the two hashes. If the answer is the same, the client successfully authenticates.
Now, you may be thinking the same thing I did when I first heard about this process, “Well, can’t you just get the mathematical formula and reverse it to figure out what the password is from the hash? For example, if the formula is (the password) 2 = the hash, could you just take the (hash÷2) = the password?” Fair question, but just wait until you see the formula. The hashing method (formula) used is known as the MD5 hash. This formula has been engineered with the sole purpose of being irreversible. With that in mind, someone might capture the password hash and find out that it is 5,381,120,123,590. Now the trick is to reverse-engineer an irreversible formula to figure out how the algorithm came up with that answer. It would be much easier for hackers to render the IT staff unconscious at whatever site they were looking to compromise and steal the servers containing the data they needed.
Just as the name implies, the PPP callback functionality enables a dial-up server (or router) running PPP to use a predefined number to call the person back who initially dialed into the location. One of the major advantages of this function is the increased security: It requires the dial-up user to authenticate and then be present at the predefined phone number to be able to receive the return call. The other advantage is the toll consolidation. If you have long distance users dialing into the network, you leave your company at the mercy of the long distance carriers of your users. By using PPP callback, you can ensure that the company long distance charges are applied, which are typically much lower than normal carrier charges.
A PPP callback process goes through the following steps:
A user dials into a router using PPP and authenticates.
Upon a successful authentication, the router terminates the connection (typically without any notification) and dials the user back at the predefined number configured by the administrator.
Upon reconnect, the user authenticates a second time.
Upon a successful authentication, the user is granted network access.
When I first heard about compression on a WAN link, my mind flashed back to the days of the Stacker compression program of Microsoft DOS. This program slowed your computer down to a crawl to gain a few megabytes of storage space on a hard disk. Surprisingly, one of the two compression algorithms used on PPP WAN connections is named “Stacker”; however, the effects are much less devastating than they were with the old DOS program.
Using compression to make your WAN connection more efficient is not a new concept. These technologies have been around since the days of DOS. However, these technologies have become much more viable on today’s networks because of the increase in CPU and memory resources on network equipment. The tradeoff when choosing to use compression is that you gain more WAN bandwidth by sacrificing your router’s processor and memory resources. How much you sacrifice depends on the type of compression algorithm you use.
The compression type analyzes the data that is being sent and replaces continuous streams of characters with codes. These codes are stored in a dictionary and looked up on the other end of the connection to rebuild the original data. The Stacker algorithm (which is actually called Lempel-Ziv) uses a “flat dictionary-style compression.” This means that for every packet of data, it goes through the same process: Look up the character streams in the dictionary, replace the characters with codes, begin again. Therefore, it is very good for network connections that have constantly varying data types (such as SQL, HTTP, FTP, and so on) crossing them. It doesn’t matter what the previous traffic was; the same compression algorithm is applied. The Stacker algorithm is notoriously heavy on CPU resources and has less effect on the router’s memory resources.
This compression algorithm received its name because it literally attempts to predict the next character stream that will be sent or received. It uses a similar dictionary lookup process as Stacker; however, it takes the most common characters looked up and builds a cached index file. Anytime some traffic needs to be sent or received, the index file is checked first. If the character stream (or codes) is not found in the index file, it then consults the full dictionary to find the necessary compression or decompression algorithm. Therefore, the Predictor algorithm works best on network connections that have fairly similar traffic patterns (that can be cached in the index file). For example, perhaps you have a WAN link back to a central office that houses an intranet server that users access to update the corporate e-commerce website. In this case, the traffic patterns would be very similar (HTTP/HTTPS) for most times of the day. The Predictor algorithm usually uses more memory resources and has less effect on the router’s CPU than the Stacker algorithm (as long as the traffic patterns do not vary largely).
Microsoft has its own compression algorithm for PPP, aptly named the Microsoft Point-to-Point Compression (MPPC). This protocol offers slightly improved processor and bandwidth utilization for Microsoft Windows–based clients. Because other devices, such as Cisco routers, would need to support this compression algorithm for Microsoft Windows to use it, Microsoft released the algorithm as an RFC standard (RFC 2118). Under the licensing in this RFC, Microsoft permits other vendors to implement MPPC solely for the purpose of connecting to other MPCC clients. MPPC therefore is used only to allow Windows dial-up users to use compression.
PPP multilink enables you to bundle multiple WAN connections into a single, logical connection. This could be as small as bundling two 33.6Kbps modems together to make a 67.2Kbps connection, or bundling four T1 lines together to give yourself a 6.176Mbps connection. The separate interfaces that are bundled together are no longer seen as individual interfaces, but rather join a larger “logical” multilink interface. You can assign this single interface its own IP address, configure authentication, or optimize the logical line with compression. It acts and feels like a real interface, even though it could potentially comprise many physical links.
There are two major benefits to using Multilink PPP (MLPPP). First off, the logical link becomes a single point of management. Rather than figuring out what the traffic utilization is on all the individual physical lines, you can focus your monitoring software (if you have some) on just a single interface. The second benefit to MLPPP is the fact that all physical links bundled in the logical group get exact load balancing. When I say “exact,” I mean the down-to-the-exact-bit-level kind of exact. MLPPP chops all your packets (referred to as fragmentation) into exactly equal sizes before it sends them across the line. This leads to the one drawback of using MLPPP: slightly increased processor and memory utilization on your router.
The final sub-layer of PPP is what gives it the functionality to allow multiple Network layer protocols to run across a single WAN link at any given time. I think of this layer as the PPP DUPLO® LEGO® block connector. Have you ever seen the DUPLO® blocks for small children? They all have that standard connector with which any other DUPLO® can connect so the child can put any two pieces together (which provides positive affirmation, I’m sure). In that same sense, the Network Control Protocol (NCP) sub-layer of PPP has open-source, network-layer connectors that anyone can plug into. For example, the TCP/IP protocol has a connector called IPCP (the CP stands for “control protocol”) that enables TCP/IP to run across a PPP WAN link. IPX/SPX has a connector called IPXCP. With the open-source nature of this protocol, I could create a “Jeremy protocol” and then write a JeremyCP to allow it to run across a PPP WAN link. Cisco has written its own extension called CDPCP that enables the Cisco Discovery Protocol to run across a PPP WAN link, which enables the routers on each end of the connection to use CDP to see each other.
Objective:
Configure and verify a basic WAN serial connection
The configuration of PPP without any options does not even deserve its own section. All you need to do is access the interface you would like to enable to run PPP and type the command encapsulation ppp. After you do that on both sides of the connection, you’re finished. For example, if I wanted to configure PPP on the Serial 0 interface of a router, here is the process:
AccessServer#configure terminal Enter configuration commands, one per line. End with CNTL/Z. AccessServer(config)#interface serial 0 AccessServer(config-if)#encapsulation ppp
After you begin turning on the options, the configuration can get a little more complex. This chapter discusses turning on PPP authentication and compression technology.
The CCNA exam focuses on configuring PPP authentication between two Cisco routers rather than using authentication for dial-up users (this is covered in the Building Cisco Remote Access Networks CCNP course). Typically, when Cisco routers are performing authentication on a WAN link, the routers will be configured as two-way authentication. Two-way authentication means that both routers authenticate each other. Typically, when a dial-up user connects to a router, one-way authentication is performed (the user must authenticate to the Cisco router, not vice-versa).
To set up CHAP PPP authentication, you must do the following:
Turn on PPP encapsulation.
Configure the necessary hostname for the authenticating routers.
Create user accounts on each side of the connection.
Turn on CHAP PPP authentication.
At first, these steps may seem somewhat cryptic, but let me walk you through a configuration example and explain how all these pieces fit together. Refer to Figure 17.3 for a visual of this example configuration.
This sample configuration enables two-way, CHAP PPP authentication between the Robin and Pigeon routers. For the sake of brevity, assume the router hostnames are already configured and PPP encapsulation has been enabled under the serial interfaces.
Before you begin, you need to understand the significance of the router hostname. By default, when a Cisco router attempts to authenticate with another router, it uses the router hostname as its PPP username to authenticate with the other side. In this example, the router with the hostname “Robin” crosses the PPP link and attempts to authenticate with the Pigeon router, using the username “Robin.” The Pigeon router attempts to authenticate with the Robin router, using the username “Pigeon.” You therefore need to create user accounts on each router that match the usernames the routers will use when authenticating. The following syntax accomplishes this:
Pigeon#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Pigeon(config)#username Robin password cisco Robin#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Robin(config)#username Pigeon password cisco
Now, when the Robin router comes over to the Pigeon router and says “My username is Robin,” the Pigeon router has a user database that identifies that username. Likewise, the Pigeon router can now authenticate the Robin router. If you have any experience with Windows administration, this is an identical concept to creating user accounts for people to log on to their PCs.
Caution
The CHAP username and passwords are both case sensitive. If the hostname of your router begins with a capital letter, ensure you create the user account the same way.
When using CHAP authentication, you must use the same password for both user accounts. In this case, both the Pigeon and Robin router share the password “cisco.” It must remain the same on both sides because CHAP never actually sends the password across the wire; it sends only the MD5 hash version of it. When the receiving side gets the hash, it runs the MD5 algorithm on its own password and compares the two hashes. If they match, authentication succeeds. The following is the complete configuration of both the Pigeon and Robin routers to enable CHAP PPP authentication:
Pigeon#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Pigeon(config)#username Robin password cisco Pigeon(config)#interface serial 0 Pigeon(config-if)#encapsulation ppp Pigeon(config-if)#ppp authentication chap Robin#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Robin(config)#username Pigeon password cisco Robin(config)#interface serial 0 Robin(config-if)#encapsulation ppp Robin(config-if)#ppp authentication chap
Enabling PPP compression is a piece of cake. You just have to make sure that both sides of the connection enable it; if only one side of the connection enables it, the link fails. Using the Pigeon and Robin scenario again, the following shows the steps you can take to enable compression:
Pigeon#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Pigeon(config)#interface serial 0 Pigeon(config-if)#compress ? mppc MPPC compression type predictor predictor compression type stac stac compression algorithm <cr>
That’s it! Just use the compress command and type the mode of compression you would like to use, and let the bandwidth savings begin.
Objective:
Configure and verify a basic WAN serial connection
To ensure your PPP connection came up successfully, you can always use the ol’ faithful show ip interface brief command.
Pigeon#show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0 10.1.1.2 YES NVRAM up up
Serial0 10.2.2.2 YES manual up upIn this case, all is well with the Serial 0 PPP connection between the routers because the Protocol is stated as up. Remember, the Status column generally dictates the Physical layer connectivity, whereas the Protocol column focuses on the Data Link connectivity.
If you want to get a little more in depth with the PPP negotiation on the interface, issue the show interface <interface> command as follows:
Pigeon#show interface serial 0
Serial0 is up, line protocol is up
Hardware is PowerQUICC Serial
Internet address is 10.2.2.2/24
MTU 1500 bytes, BW 1544 Kbit, DLY 20000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation PPP, loopback not set
Keepalive set (10 sec)
LCP Open
Open: IPCP, CCP, CDPCP
Last input 00:00:51, output 00:00:01, output hang never
Last clearing of "show interface" counters 05:07:30
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: weighted fair
Output queue: 0/1000/64/0 (size/max total/threshold/drops)
Conversations 0/1/256 (active/max active/max total)
Reserved Conversations 0/0 (allocated/max allocated)
Available Bandwidth 1158 kilobits/sec
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
4127 packets input, 168000 bytes, 0 no buffer
Received 0 broadcasts, 0 runts, 0 giants, 0 throttles
84 input errors, 0 CRC, 84 frame, 0 overrun, 0 ignored, 0 abort
8196 packets output, 404090 bytes, 0 underruns
0 output errors, 0 collisions, 163 interface resets
0 output buffer failures, 0 output buffers swapped out
326 carrier transitions
DCD=up DSR=up DTR=up RTS=up CTS=upAs you can see from the output above, the router has negotiated Link Control Protocol (LCP) options, which is indicated by the LCP Open state. If the LCP negotiations had failed (most likely because of an authentication problem), the LCP state would rotate between Listen, ACKSent, or TERMSent. This is the Cisco router trying to go through the negotiation of the LCP options. In the line below LCP Open, you can verify all the Network layer communication occurring across the PPP link. In this case, you can see IPCP (indicates the TCP/IP protocol), CCP (indicates compression is in effect—compressed control protocol [CCP]), and CDPCP (indicates the Cisco Discovery Protocol [CDP]). Technically, CDP is a Data Link protocol; however, Cisco adopted it to connect into the PPP options as a Layer 3 protocol.
Finally, if you would like to see how your PPP compression is working out, you can type the command show compress. This gives you the compression statistics for the line:
Pigeon#show compress
Serial0
Software compression enabled
uncompressed bytes xmt/rcv 4215/4956
compressed bytes xmt/rcv 0/0
1 min avg ratio xmt/rcv 0.223/4.621
5 min avg ratio xmt/rcv 0.284/4.621
10 min avg ratio xmt/rcv 0.270/1.372
no bufs xmt 0 no bufs rcv 0
resyncs 0In this case, you have no compressed bytes because all the traffic sent over the PPP link was generated by the routers themselves (this traffic is exempt from compression).
Objective:
Configure and verify a basic WAN serial connection
Whenever you reach the troubleshooting section for any topic, you can be guaranteed some debug output. In this case, the debug commands for PPP are pretty darn useful: Most of the output is easy to understand. The most useful command that I have found to troubleshoot a PPP link is the debug ppp negotiation command. Check out this output:
Pigeon#debug ppp negotiation
1d02h: Se0 PPP: Using default call direction
1d02h: Se0 PPP: Treating connection as a dedicated line
1d02h: Se0 PPP: Phase is ESTABLISHING, Active Open [0 sess, 1 load]
1d02h: Se0 LCP: O CONFREQ [Closed] id 157 len 15
1d02h: Se0 LCP: AuthProto CHAP (0x0305C22305)
1d02h: Se0 LCP: MagicNumber 0x0709760C (0x05060709760C)
1d02h: Se0 LCP: I CONFREQ [REQsent] id 208 len 15
1d02h: Se0 LCP: AuthProto CHAP (0x0305C22305)
1d02h: Se0 LCP: MagicNumber 0x22D5B7B3 (0x050622D5B7B3)
1d02h: Se0 LCP: O CONFACK [REQsent] id 208 len 15
1d02h: Se0 LCP: AuthProto CHAP (0x0305C22305)
1d02h: Se0 LCP: MagicNumber 0x22D5B7B3 (0x050622D5B7B3)
1d02h: Se0 LCP: TIMEout: State ACKsent
1d02h: Se0 LCP: O CONFREQ [ACKsent] id 158 len 15
1d02h: Se0 LCP: AuthProto CHAP (0x0305C22305)
1d02h: Se0 LCP: MagicNumber 0x0709760C (0x05060709760C)
1d02h: Se0 LCP: I CONFACK [ACKsent] id 158 len 15
1d02h: Se0 LCP: AuthProto CHAP (0x0305C22305)
1d02h: Se0 LCP: MagicNumber 0x0709760C (0x05060709760C)
1d02h: Se0 LCP: State is Open
1d02h: Se0 PPP: Phase is AUTHENTICATING, by both [0 sess, 1 load]
1d02h: Se0 CHAP: O CHALLENGE id 156 len 27 from "Pigeon"
1d02h: Se0 CHAP: I CHALLENGE id 2 len 26 from "Robin"
1d02h: Se0 CHAP: O RESPONSE id 2 len 27 from "Pigeon"
1d02h: Se0 CHAP: I RESPONSE id 156 len 26 from "Robin"
1d02h: Se0 CHAP: O SUCCESS id 156 len 4
1d02h: Se0 CHAP: I SUCCESS id 2 len 4
1d02h: Se0 PPP: Phase is UP [0 sess, 1 load]
1d02h: Se0 IPCP: O CONFREQ [Closed] id 4 len 10
1d02h: Se0 IPCP: Address 10.2.2.2 (0x03060A020202)
1d02h: Se0 CCP: O CONFREQ [Closed] id 4 len 6
1d02h: Se0 CCP: Predictor1 (0x0102)
1d02h: Se0 CDPCP: O CONFREQ [Closed] id 4 len 4
1d02h: Se0 IPCP: I CONFREQ [REQsent] id 5 len 10
1d02h: Se0 IPCP: Address 10.2.2.1 (0x03060A020201)
1d02h: Se0 IPCP: O CONFACK [REQsent] id 5 len 10
1d02h: Se0 IPCP: Address 10.2.2.1 (0x03060A020201)
1d02h: Se0 CCP: I CONFREQ [REQsent] id 2 len 6
1d02h: Se0 CCP: Predictor1 (0x0102)
1d02h: Se0 CCP: O CONFACK [REQsent] id 2 len 6
1d02h: Se0 CCP: Predictor1 (0x0102)
1d02h: Se0 CDPCP: I CONFREQ [REQsent] id 5 len 4
1d02h: Se0 CDPCP: O CONFACK [REQsent] id 5 len 4
1d02h: Se0 IPCP: I CONFACK [ACKsent] id 4 len 10
1d02h: Se0 IPCP: Address 10.2.2.2 (0x03060A020202)
1d02h: Se0 IPCP: State is Open
1d02h: Se0 CCP: I CONFACK [ACKsent] id 4 len 6
1d02h: Se0 CCP: Predictor1 (0x0102)
1d02h: Se0 CCP: State is Open
1d02h: Se0 CDPCP: I CONFACK [ACKsent] id 4 len 4
1d02h: Se0 CDPCP: State is Open
1d02h: Se0 IPCP: Install route to 10.2.2.1
1d02h: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0,
3changed state to upIsn’t that some great stuff?!? Okay, it does take a little bit of screening through all the output, but if you look about halfway through, you can see the exchange of the Robin and Pigeon hostnames. This shows the challenge/response action of the CHAP protocol. Thankfully, you can see a SUCCESS message to finish it off, showing the Pigeon and Robin routers have successfully authenticated each other. Near the bottom of the output, you see the CCP (compression negotiation) negotiate the Predictor algorithm between the two routers. Finally, at the end of the output, you see the link come up.
If your PPP connection is failing, this debug command will definitely show you the cause (as long as the failure is related to PPP). Another popular command is debug ppp authentication, which gives the same output, but slims it down to just the authentication information (because this is where many failures occur).
Managing WAN connections is one of the primary functions of a router. WAN connections tie distant locations together into a common network infrastructure. Choosing a WAN connection has become more difficult in recent years because there are now many more WAN connection technologies at our disposal. However, the most popular WAN connection technologies boil down to three main categories: Leased Lines, Circuit Switched, and Packet Switched.
After you have chosen the Physical connection type you would like to use, you can then move up to the Data Link connectivity. For leased line connections, the two major protocols in use today are HDLC and PPP. On a Cisco router, HDLC has been modified to support multiple upper-layer protocols and has thus become proprietary. HDLC’s major feature is the low amount of network overhead it causes on the WAN connection. Other than that, it is featureless. PPP is the more popular data link protocol because it supports multi-vendor interoperability and a plethora of features.
PPP over Ethernet (PPPoE)
PPP over ATM (PPPoA)
One of the most common problems encountered when troubleshooting a PPP connection is authentication failures, which are due to the many parameters that must match for the link to successfully authenticate. In this exercise, you will incorrectly configure PPP authentication and walk through the steps necessary to troubleshoot the connection. Refer to Figure 17.4 for a visual of the connection.
Estimated Time: 5-10 minutes
What you will do is configure the two routers for CHAP authentication across the PPP connection. However, you will configure the username/password combination on one side of the connection as all lowercase and watch the story unfold. First, get the PPP connection running:
Daniel#show ip interface brief Interface IP-Address OK? Method Status Protocol FastEthernet0 10.1.1.2 YES NVRAM up up Serial0 192.168.40.2 YES manual up down Daniel#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Daniel(config)#interface serial 0 Daniel(config-if)#encapsulation ppp
You now have the Daniel router configured for PPP; now configure the Ezekiel router on the other side.
Ezekiel#show ip interface brief Interface IP-Address OK? Method Status Protocol Ethernet0 192.168.1.40 YES NVRAM up up Serial0 192.168.40.1 YES manual up down Serial1 unassigned YES NVRAM administratively down down Ezekiel#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Ezekiel(config)#interface serial 0 Ezekiel(config-if)#encapsulation ppp 00:07:36: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0, 3 changed state to up 1d14h: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0, 3 changed state to up Ezekiel(config-if)#^Z 1d14h: %SYS-5-CONFIG_I: Configured from console by console Ezekiel#ping 192.168.40.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.40.2, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 56/59/72 ms
It looks like the PPP link has been brought up successfully and you are now able to ping between the two routers. Now add the authentication piece to the picture:
Ezekiel#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Ezekiel(config)#username Daniel password examprep Ezekiel(config)#interface serial 0 Ezekiel(config-if)#ppp authentication chap 00:11:11: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0, 3 changed state to down
Notice that as soon as you turned on CHAP authentication for one side of the connection, the link went down. This is because one side of the connection is configured to require authentication while the other is not configured to support it. You can solve that problem and, at the same time, introduce the authentication configuration error.
Daniel#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Daniel(config-if)#exit Daniel(config)#username Ezekiel password examcram Daniel(config)#interface serial 0 Daniel(config-if)#ppp authentication chap Daniel(config-if)#exit Daniel(config)#exit 1d14h: %SYS-5-CONFIG_I: Configured from console by console Daniel#show ip interface brief Interface IP-Address OK? Method Status Protocol FastEthernet0 10.1.1.2 YES NVRAM up up Serial0 192.168.40.2 YES manual up down
Notice that the password examcram was used for the Ezekiel account rather than examprep. Because CHAP requires both passwords to be the same on both sides of the connection, the Serial0 link remains down. Now, if we did not know about this configuration error, the troubleshooting process would go something like this:
Daniel#show interface serial 0
Serial0 is up, line protocol is down
Hardware is PowerQUICC Serial
Internet address is 192.168.40.2/24
MTU 1500 bytes, BW 1544 Kbit, DLY 20000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation PPP, loopback not set
Keepalive set (10 sec)
LCP Listen
Closed: IPCP, CCP, CDPCP
Last input 00:00:01, output 00:00:01, output hang never
Last clearing of "show interface" counters 16:52:28
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: weighted fair
<...output removed for brevity...>Notice first that the line protocol is down, which indicates a Data Link failure. When you look down at the PPP negotiation (LCP), you can see that it is in the Listen state and the NCP protocol communication is Closed. This means the LCP layer of PPP has not successfully negotiated, and points you in the correct direction for troubleshooting. Now is a good time to perform a debug and see whether you can weed out what is going on.
Daniel#debug ppp negotiation
PPP protocol negotiation debugging is on
Daniel#
1d14h: Se0 LCP: TIMEout: State Listen
1d14h: Se0 LCP: O CONFREQ [Listen] id 51 len 15
1d14h: Se0 LCP: AuthProto CHAP (0x0305C22305)
1d14h: Se0 LCP: MagicNumber 0x098EF573 (0x0506098EF573)
1d14h: Se0 LCP: I CONFACK [REQsent] id 51 len 15
1d14h: Se0 LCP: AuthProto CHAP (0x0305C22305)
1d14h: Se0 LCP: MagicNumber 0x098EF573 (0x0506098EF573)
1d14h: Se0 LCP: I CONFREQ [ACKrcvd] id 131 len 15
1d14h: Se0 LCP: AuthProto CHAP (0x0305C22305)
1d14h: Se0 LCP: MagicNumber 0x002934B3 (0x0506002934B3)
1d14h: Se0 LCP: O CONFACK [ACKrcvd] id 131 len 15
1d14h: Se0 LCP: AuthProto CHAP (0x0305C22305)
1d14h: Se0 LCP: MagicNumber 0x002934B3 (0x0506002934B3)
Daniel#
1d14h: Se0 LCP: State is Open
1d14h: Se0 PPP: Phase is AUTHENTICATING, by both [0 sess, 1 load]
1d14h: Se0 CHAP: O CHALLENGE id 144 len 27 from "Daniel"
1d14h: Se0 CHAP: I CHALLENGE id 45 len 28 from "Ezekiel"
1d14h: Se0 CHAP: O RESPONSE id 45 len 27 from "Daniel"
1d14h: Se0 CHAP: I RESPONSE id 144 len 28 from "Ezekiel"
1d14h: Se0 CHAP: O FAILURE id 144 len 25 msg is "MD/DES compare failed"
1d14h: Se0 PPP: Phase is TERMINATING [0 sess, 1 load]
1d14h: Se0 LCP: O TERMREQ [Open] id 52 len 4
1d14h: Se0 CHAP: LCP not open, discarding packet
1d14h: Se0 LCP: I TERMREQ [TERMsent] id 132 len 4
1d14h: Se0 LCP: O TERMACK [TERMsent] id 132 len 4
Daniel#
1d14h: Se0 LCP: TIMEout: State TERMsent
1d14h: Se0 LCP: O TERMREQ [TERMsent] id 53 len 4
1d14h: Se0 LCP: I TERMACK [TERMsent] id 53 len 4
1d14h: Se0 LCP: State is Closed
1d14h: Se0 PPP: Phase is DOWN [0 sess, 1 load]
1d14h: Se0 PPP: Phase is ESTABLISHING, Passive Open [0 sess, 1 load]You can watch in amazement as PPP goes from the Listen state into the REQ/ACK state (where it begins to negotiate the connection and authentication protocol). After the LCP state is Open, the full authentication phase begins. About halfway through the CHALLENGE/RESPONSE messages, you see the glaring FAILURE message that shows that the MD/DES compare failed. This means the password hashes are not the same for these routers. If you kept this debug turned on, it would continue to loop through the process again and again until you fixed the mismatched password. Turn off the debug and fix the password, and see what happens.
Daniel#u all All possible debugging has been turned off Daniel#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Daniel(config)#no username Ezekiel password examcram Daniel(config)#username Ezekiel password examprep Daniel(config)# 00:40:34: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0, 3 changed state to up 1d14h: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0, 3 changed state to up
Wow! Just like that, the link has come online. The configuration is now successful.
The three WAN connection categories are leased line, circuit switched, and packet switched. | |
When configuring the physical connectivity for a serial WAN connection, you need to purchase either a DB-60 or Smart Serial WIC card for your router. From there, you need to purchase a cable that converts from the DB-60 or Smart Serial card of your Cisco router to the industry standard adapter found on the CSU/DSU device that connects to the service provider. | |
The four features negotiated by the PPP Link Control Protocol (LCP) are compression, callback, multilink, and authentication. | |
The Network Control Protocol (NCP) enables the router to encapsulate multiple upper-layer protocols (such as IP, IPX, and Appletalk) over a PPP WAN connection. | |
The two PPP compression algorithms are Stacker and Predictor. The Stacker algorithm requires more processor resources and fewer memory resources. The Predictor algorithm uses more memory resources and fewer processor resources. Stacker is the best algorithm to use when there are varying traffic types crossing the PPP WAN connection. Predictor works best when you have similar traffic types using the PPP WAN connection. |
C. Frame Relay and X.25 fall under the packet-switched networks category. These networks establish connections through a service provider cloud using virtual circuits. Answer B is incorrect because circuit-switched networks include technologies such as modems and ISDN. Answer A is incorrect because leased lines use dedicated bandwidth between locations. Answer D is incorrect because broadband encompasses DSL and cable modem technology. | |
B. The Cisco side of the connection always uses either a DB-60 or Smart Serial connector (these are always male because the router has female ports). Because the CSU/DSU has a V.35 female connector, you should be using a V.35 male transition cable. All other answers are incorrect because they use either the wrong connector type or gender on the Cisco side. | |
B. The Link Control Protocol (LCP) is used to negotiate all options related to PPP during the link establishment phase. The Network Control Protocol (NCP) negotiates the upper-layer protocols only after the initial PPP link has been established. The HDLC layer of PPP is what allows for multi-vendor interoperability with the protocol. Answer A is incorrect because an authentication packet falls under the LCP negotiations. Answer C is incorrect because NCP negotiates the upper-layer protocols. Answer D is incorrect because HDLC is used to give PPP an industry standard foundation when connecting to non-Cisco equipment. | |
A, D. PAP is the older of the two PPP authentication protocols. It has major security flaws, including the sending of passwords in clear text and allowing the client to choose when it sends the password. Answers B and C are incorrect because the MD5 hashing and server control is a function of the CHAP. | |
D. CHAP requires authentication both when the link is initially established and on a periodic basis thereafter. This is awesome because it combats playback attacks and packet sniffing (passwords are not sent). PAP requires authentication only when the link is initially established and when the client chooses to send the credentials, which is why answers B and C are incorrect. Answer A is incorrect because CHAP also sends authentication credentials when the link is initially established. | |
C. You enable PPP authentication from the interface configuration mode by typing the command | |
D. VPNs enable companies to purchase simple Internet connections and tunnel their information through the networks between their sites. This information is heavily encrypted to ensure it is not compromised crossing the public network. This is far cheaper than any other type of WAN connection, but can suffer from the heavy encryption slowdown. Answers A, B, and C are incorrect because leased lines and circuit-switched and packet-switched networks require no tunneling or encryption capabilities. | |
A. The | |
D. NCP is used to negotiate the Network layer protocols. These negotiations are typically shown as in the syntax | |
B. Circuit-switched connections encompass anything that has to dial a number to make a connection. These connections typically use the telephone company as a backbone. Answer C is incorrect as packet-switched networks include technologies such as X.25 and Frame Relay. Answer A is incorrect because leased lines do not dial because they are permanently established connections. Answer D is incorrect because metro ethernet is extremely high-speed connections running through a metropolitan area. |
Cisco Introduction to WAN Technologies, http://www.cisco.com/univercd/cc/td/doc/cisintwk/ito_doc/introwan.htm.
Ward, Chris and Cioara, Jeremy. Exam Cram 2 CCNA Practice Questions. Que Publishing, 2004.
Quinn, Eric and Glauser, Fred. BCRAN Exam Cram 2 (Exam 642-821). Que Publishing, 2003.