Chapter 8. Windows-Based Analysis
The next area of focus for preparing for the SECFND is evaluating Windows-based systems. Other operating systems such as Linux and Mac OS X are covered in Chapter 9, “Linux- and Mac OS X–Based Analysis.” We’ll start with Windows based on its popularity in the business market space, although Apple continues to grow in popularity for enterprise mobile and desktop platforms.
The goal for this section is to understand the basics of how a system running Windows handles applications. This includes details from how memory is used to how resources are processed by the operating system. There are many versions of Windows between the current and older releases; however, the SECFND exam does not ask about or compare features among the various versions. The SECFND only focuses on the core concepts.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz helps you identify your strengths and deficiencies in this chapter’s topics. The ten-question quiz, derived from the major sections in the “Foundation Topics” portion of the chapter, helps you determine how to spend your limited study time. You can find the answers in Appendix A Answers to the “Do I Know This Already?” Quizzes and Q&A Questions.
Table 8-1 outlines the major topics discussed in this chapter and the “Do I Know This Already?” quiz questions that correspond to those topics.
1. Which of the follow best describes Windows process permissions?
a. User authentication data is stored in a token that is used to describe the security context of all processes associated with the user.
b. Windows generates processes based on super user–level security permissions and limits processes based on predefined user authentication settings.
c. Windows process permissions are developed by Microsoft and enforced by the host system administrator.
d. Windows grants access to all processes unless otherwise defined by the Windows administrator.
2. Which of the following of the following is a true statement about a stack and heap?
a. Heaps can allocate a block of memory at any time and free it at any time.
b. Stacks can allocate a block of memory at any time and free it at any time.
c. Heaps are best for when you know exactly how much memory you should use.
d. Stacks are best when you don’t know how much memory to use.
3. What is the Windows registry?
a. A list of registered software on the Windows operating system
b. Memory allocated to running programs
c. A database used to store information necessary to configure the system for users, applications, and hardware devices
d. A list of drivers for applications running on the Windows operating system
4. Which of the following is a function of the Windows registry?
a. To register software with the application provider
b. To load device drivers and start up programs
c. To back up application registration data
d. To log upgrade information
5. Which of the following statements is true?
a. WMI is a command standard used by most operating systems.
b. WMI cannot run on older versions of Windows such as Windows 98.
c. WMI is a defense program designed to prevent scripting languages from managing Microsoft Windows computers and services.
d. WMI allows scripting languages to locally and remotely manage Microsoft Windows computers and services.
6. What is a virtual address space in Windows?
a. The physical memory allocated for processes
b. A temporary space for processes to execute
c. The set of virtual memory addresses that reference the physical memory object a process is permitted to use
d. The virtual memory address used for storing applications
7. What is the difference between a handle and pointer?
a. A handle is an abstract reference to a value, whereas a pointer is a direct reference.
b. A pointer is an abstract reference to a value, whereas a handle is a direct reference.
c. A pointer is a reference to a handle.
d. A handle is a reference to a pointer.
8. Which of the following is true about handles?
a. When Windows moves an object such as a memory block to make room in memory and the location of the object is impacted, the handles table is updated.
b. Programmers can change a handle using Windows API.
c. Handles can grant access rights against the operating system.
d. When Windows moves an object such as a memory block to make room in memory and the location of the object is impacted, the pointer to the handle is updated.
9. Which of the following is true about Windows services?
a. Windows services only function when a user has accessed the system.
b. The Services Control Manager is the programming interface for modifying the configuration of Windows Services.
c. Microsoft Windows services run in their own user session.
d. Stopping a service requires a system reboot.
10. What is an IIS parser log used for?
a. For logging specific Windows events
b. For backing up Windows logs
c. To generate alerts and log events
d. To provide universal query access to text-based data such as logs
Foundation Topics
Windows was introduced by Microsoft in 1984 as a graphical user interface (GUI) for Microsoft DOS. Over time, Windows has matured in stability and capabilities with many releases, ranging from Windows 3.0 back in 1990 to the 2015 Windows 10 release. More current releases of Windows have offered customized options; for example, Windows Server was designed for provisioning services to multiple hosts, and Windows Mobile was created for Windows-based phones.
The Windows operating system architecture is made up of many components, such as the control panel, administrative tools, and software. The control panel permits users to view and change basic system settings and controls. This includes adding hardware and removing software as well as changing user accounts and accessibility options. Administrative tools are more specific to administrating Windows. For example, System Restore is used for rolling back Windows, and Disk Defragment is used to optimize performance. Software can be various types of applications, from the simple calculator application to complex programing languages.
As stated in the introduction of this chapter, the SECFND won’t ask for specifics about each version of Windows; nor will it expect you to know every component within the Windows architecture. That would involve a ton of tedious detail that is out of scope for the learning objectives of the certification. The content covered in this chapter targets the core concepts you are expected to know about Windows. We will start with how applications function by defining processes and threads.
Process and Threads
Let’s first run through some technical definitions of processes and threads. When you look at what an application is built from, you will find one or more processes. A process is a program that the system is running. Each process provides the required resources to execute a program. A process is made up of one or more threads, which are the basic units an operating system allocates process time to. A thread can be executed during any part of the application runtime, including being executed by another thread. Each process starts with a single thread, known as the primary thread, but can also create additional threads from any of its threads.
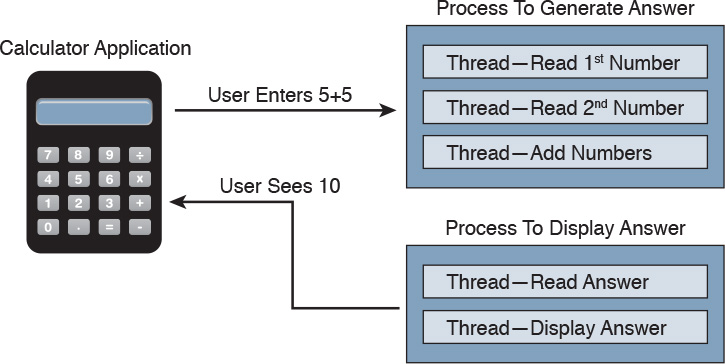
For example, the calculator application could run multiple processes when a user enters numbers to be computed, such as the process to compute the math as well as the process to display the answer. You can think of a thread as each number being called while the process is performing the computation that will be displayed by the calculator application. Figure 8-1 shows this relationship from a high-level view.
Processes can be grouped together and managed as a unit called a job object, which can be used to control the attributes of those processes. Grouping processes together simplifies impacting those processes because any operation performed on a specific job object will impact all associated processes. A thread pool is a group of worker threads that efficiently execute asynchronous callbacks for the application. This is done to reduce the number of application threads and to manage the worker threads. A fiber is unit of execution that is manually scheduled by an application. Threads can schedule multiple fibers; however, fibers do not outperform properly designed multithreaded applications.
Whew, that’s a lot of technical definitions to understand! Although these are the foundation concepts to be aware of, it is more important to understand how these items are generally used within Windows for security purposes. Knowing that a Windows process is a running program is important, but it’s equally as import to understand that processes must have permission to run. This keeps processes from hurting the system as well as unauthorized actions from being performed. For example, the process to delete everything on the hard drive should have some authorization settings to avoid killing the computer.
Windows permissions are based on access control to process objects tied to user rights. This means that super users such as administrators will have more rights than other user roles. Windows uses tokens to specify the current security context for a process. This can be accomplished using the CreateProcessWithTokenW function.
Authentication is typically used to provision authorization to a user role. For example, you would log in with a username and password to authenticate to an access role that has specific user rights. Windows would validate this login attempt, and if authentication is successful, you will be authorized for a specific level of access. Windows stores user authentication data in a token that describes the security context of all processes associated with the user role. This means administrator tokens would have permission to delete items of importance whereas lower-level user tokens would provide the ability to view but not be authorized to delete.
Figure 8-2 ties this token idea to the calculator example, showing processes creating threads. The basic idea is that processes create threads, and threads validate whether they can run using an access token. In this example, the third thread is not authorized to operate for some reason, whereas the other two are permitted.
It is important to understand how these components all work together when developing applications and later securing them. Threats to applications, known as vulnerabilities, could be abused to change the intended outcome of an application. This is why it is critical to include security at all stages of application development to ensure these and other application components are not abused. The next section reviews how processes and threads work within Windows memory.
The list that follows highlights the key process and thread concepts:
![]() A process is a program the system is running and is made of one or more threads.
A process is a program the system is running and is made of one or more threads.
![]() A thread is a basic unit an operating system allocates process time to.
A thread is a basic unit an operating system allocates process time to.
![]() A job is a group of processes.
A job is a group of processes.
![]() A thread pool is a group of worker threats that efficiently execute asynchronous callbacks for the application.
A thread pool is a group of worker threats that efficiently execute asynchronous callbacks for the application.
![]() Processes must have permission to run within Windows.
Processes must have permission to run within Windows.
![]() You can use a Windows token to specify the current security context for a process using the CreateProcessWithTokenW function.
You can use a Windows token to specify the current security context for a process using the CreateProcessWithTokenW function.
![]() Windows stores data in a token that describes the security context of all processes associated with a particular user role.
Windows stores data in a token that describes the security context of all processes associated with a particular user role.
Memory Allocation
Now that we have covered how applications function, let’s look at where they are installed and how they run. Computer memory is any physical device capable of storing information in a temporary or permanent state. Memory can be volatile or nonvolatile. Volatile memory is memory that loses its contents when the computer or hardware storage device loses power. RAM is an example of volatile memory. That’s why you never hear people say they are saving something to RAM. It’s designed for application performance.
You might be thinking that there isn’t a lot of value for the data stored in RAM; however, from a digital forensics viewpoint, the following data could be obtained by investigating RAM. (In case you’re questioning some of the items in the list, keep in mind that data that is encrypted must be unencrypted when in use, meaning its unencrypted state could be in RAM. The same goes for passwords!)
![]() Running processes: Who is logged in
Running processes: Who is logged in
![]() Passwords in cleartext: Unencrypted data
Passwords in cleartext: Unencrypted data
![]() Instant messages: Registry information
Instant messages: Registry information
![]() Executed console commands: Attached devices
Executed console commands: Attached devices
![]() Open ports: Listening applications
Open ports: Listening applications
Nonvolatile memory (NVRAM), on the other hand, holds data with or without power. EPROM would be an example of nonvolatile memory.
NOTE
Memory and disk storage are two different things. Computers typically have anywhere from 1GB to 16GB of RAM, but they can have hundreds of terabytes of disk storage. A simple way to understand the difference is memory is the space applications use when they are running while storage is where applications store data for future use.
Memory can be managed in different ways, referred to as memory allocation or memory management. Static memory allocation is when a program allocates memory at compile time. Dynamic memory allocation is when a program allocates memory at runtime. Memory can be assigned in blocks representing portions of allocated memory dedicated to a running program. A program can request a block of memory, which the memory manager will assign to the program. When the program completes whatever it’s doing, the allocated memory blocks are released and available for other uses.
Next up are stacks and heaps. A stack is memory set aside as spare space for a thread of execution. A heap is memory set aside for dynamic allocation (that is, where you put data on the fly). Unlike a stack, a heap doesn’t have an enforced pattern for the allocation and deallocation of blocks. With heaps, you can allocate a block at any time and free it at any time. Stacks are best when you know ahead of time how much memory is needed, whereas heaps are better for when you don’t know how much data you will need at runtime or if you need to allocate a lot of data. Memory allocation happens in hardware, in the operating system, and in programs and applications.
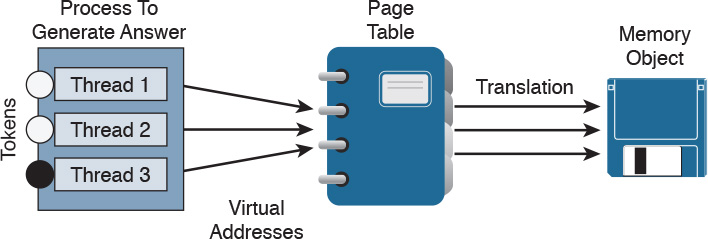
Processes function in a set of virtual memory known as virtual address space. The virtual address space for each process is private and cannot be accessed by other processes unless it is specifically shared. The virtual address does not represent the actual physical location of an object in memory; instead, it’s simply a reference point. The system maintains a page table for each process that is used to reference virtual memory to its corresponding physical address space. Figure 8-3 shows this concept using the calculator example, where the threads are pointing to a page table that holds the location of the real memory object.
The virtual address space of each process can be smaller or larger than the total physical memory available on the computer. A working set is a subset of the virtual address space of an active process. If a thread of a process attempts to use more physical memory than is currently available, the system will page some of the memory contest to disk. The total amount of virtual address space available to process on a specific system is limited by the physical memory and free space on the hard disks for the paging file.
We will now touch on a few other concepts of how Windows allocates memory. The ultimate result is the same, but the approach for each is slightly different. VirtualAlloc is a specialized allocation of OS virtual memory system; it allocates straight into virtual memory by reserving memory blocks. HeapAlloc allocates any size of memory requested, meaning it allocates by default regardless of size. Malloc is another memory allocation option, but it is more programming focused and not Windows dependent. It is not important for the SECFND to know the details of how each memory allocation option functions. The goal is just to have a general understanding of memory allocation.
The list that follows highlights the key memory allocation concepts:
![]() Volatile memory is memory that loses its contents when the computer or hardware storage device loses power.
Volatile memory is memory that loses its contents when the computer or hardware storage device loses power.
![]() Nonvolatile memory (NVRAM) holds data with or without power.
Nonvolatile memory (NVRAM) holds data with or without power.
![]() Static memory allocation is when a program allocates memory at compile time.
Static memory allocation is when a program allocates memory at compile time.
![]() Dynamic memory allocation is when a program allocates memory at runtime.
Dynamic memory allocation is when a program allocates memory at runtime.
![]() A heap is memory set aside for dynamic allocation.
A heap is memory set aside for dynamic allocation.
![]() A stack is the memory set aside as spare space for a thread of execution.
A stack is the memory set aside as spare space for a thread of execution.
![]() A virtual address space is the virtual memory used by processes.
A virtual address space is the virtual memory used by processes.
![]() A virtual address is a reference to the physical location of an object in memory. A page table translates virtual memory into its corresponding physical addresses.
A virtual address is a reference to the physical location of an object in memory. A page table translates virtual memory into its corresponding physical addresses.
![]() The virtual address space of each process can be smaller or larger than the total physical memory available on the computer.
The virtual address space of each process can be smaller or larger than the total physical memory available on the computer.
Windows Registration
Now that we have covered what makes up an application and how it uses memory, let’s look at Windows registration. Basically anything performed in Windows refers to or is recorded into the registry. Therefore, any actions taken by a user reference the Windows registry. The Windows registry is a hierarchical database for storing the information necessary to configure a system for one or more users, applications, and hardware devices.
Some functions of the Windows registry are to load device drivers, run startup programs, set environment variables, and store user settings and operating system parameters. You can view the Windows registry by typing the command regedit in the Run window. Figure 8-4 shows a screenshot of the Registry Editor window.
The registry is like a structured file system. The five hierarchal folders on the left are called hives and begin with HKEY (meaning the handle to a key). Two of the hives are real locations: HKEY_USERS (HKU) and HKEY_LOCAL_MACHINE (HKLM). The remaining three are shortcuts to branches within the HKU and HKLM hives. Each of the five main hives is composed of keys that contain values and subkeys. Values pertain to the operation system or applications within a key. The Windows registry is like an application containing folders. Inside an application, folders hold files. Inside the Windows registry, the hives hold values.
The following list defines the functions of the five hives within the Windows registry:
![]() HKEY_CLASSES_ROOT (HKCR): HKCR information ensures that the correct program opens when it is executed in Windows Explorer. HKCR also contains further details on drag-and-drop rules, shortcuts, and information on the user interface. The reference location is HKLMSoftwareClasses.
HKEY_CLASSES_ROOT (HKCR): HKCR information ensures that the correct program opens when it is executed in Windows Explorer. HKCR also contains further details on drag-and-drop rules, shortcuts, and information on the user interface. The reference location is HKLMSoftwareClasses.
![]() HKEY_CURRENT_USER (HKCU): HKCU contains configuration information for any user who is currently logged in to the system, including user folders, screen colors, and control panel settings. The reference location for a specific user is HKEY_USERS. The reference for general use is HKU.DEFAULT.
HKEY_CURRENT_USER (HKCU): HKCU contains configuration information for any user who is currently logged in to the system, including user folders, screen colors, and control panel settings. The reference location for a specific user is HKEY_USERS. The reference for general use is HKU.DEFAULT.
![]() HKEY_CURRENT_CONFIG (HCU): HCU stores information about the system’s current configuration. The reference for HCU is HKLMConfigprofile.
HKEY_CURRENT_CONFIG (HCU): HCU stores information about the system’s current configuration. The reference for HCU is HKLMConfigprofile.
![]() HKEY_LOCAL_MACHINE (HKLM): HKLM contains machine hardware-specific information that the operating system runs on. This includes a list of drives mounted on the system and generic configurations of installed hardware and applications. HKLM is a hive that isn’t referenced from within another hive.
HKEY_LOCAL_MACHINE (HKLM): HKLM contains machine hardware-specific information that the operating system runs on. This includes a list of drives mounted on the system and generic configurations of installed hardware and applications. HKLM is a hive that isn’t referenced from within another hive.
![]() HKEY_USERS (HKU): HKU contains configuration information of all user profiles on the system. This includes application configurations and visual settings. HKU is a hive that isn’t referenced from within another hive.
HKEY_USERS (HKU): HKU contains configuration information of all user profiles on the system. This includes application configurations and visual settings. HKU is a hive that isn’t referenced from within another hive.
Some interesting data points can be gained from analyzing the Windows registry. All registries contain a value called LastWrite time, which is the last modification time of a file. This can be used to identify the approximate date and time an event occurred. Autorun locations are registry keys that launch programs or applications during the boot process. Autorun is extremely important to protect because it could be used by an attacker for executing malicious applications. The most recently used (MRU) list contains entries made due to actions performed by the user. The purpose of the MRU list is to contain items in the event the user returns to them in the future. Think of the MRU list as how a cookie is used in a web browser. The UserAssist key contains a document of what the user has accessed.
Network settings, USB devices, and mounted devices all have registry keys that can be pulled up to identify activity within the operating system. Having a general understanding of Windows registration should be sufficient for questions found on the SECFND exam.
The list that follows highlights the key Windows registration concepts:
![]() The Windows registry is a hierarchical database used to store information necessary to configure the system for one or more users, applications, and hardware devices.
The Windows registry is a hierarchical database used to store information necessary to configure the system for one or more users, applications, and hardware devices.
![]() Some functions of the registry are to load device drivers, run startup programs, set environment variables, and store user settings and operating system parameters.
Some functions of the registry are to load device drivers, run startup programs, set environment variables, and store user settings and operating system parameters.
![]() The five main folders in the Windows registry are called hives. Three of these hives are reference points inside of another primary hive.
The five main folders in the Windows registry are called hives. Three of these hives are reference points inside of another primary hive.
![]() Hives contain values pertaining to the operation system or applications within a key.
Hives contain values pertaining to the operation system or applications within a key.
Windows Management Instrumentation
The next topic focuses on managing Windows systems and sharing data with other management systems. Windows Management Instrumentation (WMI) is a scalable system management infrastructure built around a single, consistent, standards-based, extensible, object-oriented interface. Basically, WMI is Microsoft’s approach to implementing Web-Based Enterprise Management (WBEM), which is a tool used by system management application developers for manipulating system management information. WMI uses the Common Information Model (CIM) industry standard to represent systems, applications, networks, devices, and other managed components. CIM is developed and maintained by the Distributed Management Task Force (DMTF).
It is important to remember that WMI is only for computers running Microsoft Windows. WMI comes preinstalled on all computers running Windows Millennium Edition (ME), Windows 2000, Windows XP, or Windows Server 2003; however, it can be downloaded to older systems running Windows 95, Windows 98, or Windows NT 4.0. Figure 8-5 shows a Windows computer displaying the WMI service.
The purpose of WMI is to define a set of proprietary environment-independent specifications used for management information that’s shared between management applications. WMI allows scripting languages to locally and remotely manage Microsoft Windows computers and services. The following list provides examples of what WMI can be used for:
![]() Providing information about the status of local or remote computer systems
Providing information about the status of local or remote computer systems
![]() Configuring security settings
Configuring security settings
![]() Modifying system properties
Modifying system properties
![]() Changing permissions for authorized users and user groups
Changing permissions for authorized users and user groups
![]() Assigning and changing drive labels
Assigning and changing drive labels
![]() Scheduling times for processes to run
Scheduling times for processes to run
![]() Backing up the object repository
Backing up the object repository
![]() Enabling or disabling error logging
Enabling or disabling error logging
Using WMI by itself doesn’t provide these capabilities or display any data. You must pull this information using scripts and other tools. WMI can be compared to the electronics data of a car, where the car dashboard is the tool used to display what the electronics are doing. Without the dashboard, the electronics are there, but you won’t be able to interact with the car or obtain any useful data. An example of WMI would be using a script to display the time zone configured on a Windows computer or issuing a command to change the time zone on one or more Windows computers.
When considering Windows security, you should note that WMI could be used to perform malicious activity. Malicious code could pull sensitive data from a system or automate malicious tasks. An example would be using WMI to escalate privileges so that malware can function at a higher privilege level if the security settings are modified. Another attack would be using WMI to obtain sensitive system information.
There haven’t been many WMI attacks seen in the wild; however, Trend Micro published a whitepaper on one piece of WMI malware called TROJ_WMIGHOST.A. So although such attacks are not common, they are possible. WMI requires administrative permission and rights to be installed; therefore, a best practice to protect systems against this form of exploitation is to restrict access to the WMI service.
The list that follows highlights the key WMI concepts:
![]() WMI is a scalable system management infrastructure built around a single, consistent, standards-based, extensible, object-oriented interface.
WMI is a scalable system management infrastructure built around a single, consistent, standards-based, extensible, object-oriented interface.
![]() WMI is only for Windows systems.
WMI is only for Windows systems.
![]() WMI comes preinstalled on many Windows systems. For older Windows versions, you may need to download and install it.
WMI comes preinstalled on many Windows systems. For older Windows versions, you may need to download and install it.
![]() WMI data must be pulled in with scripting or tools because WMI by itself doesn’t show data.
WMI data must be pulled in with scripting or tools because WMI by itself doesn’t show data.
Handles
In Microsoft Windows, a handle is an abstract reference value to a resource. Putting this another way, a handle identifies a particular resource you want to work with using the Win32 APIs. The resource is often memory, an open file, a pipe, or an object managed by another system. Handles hide the real memory address from the API user while permitting the system to reorganize physical memory in a way that’s transparent to the program.
Handles are like pointers, but not in the sense of dereferencing a handle to gain access to some data. Instead, a handle is passed to a set of functions that can perform actions on the object the handle identifies. In comparison, a pointer contains the address of the item to which it refers, whereas a handle is an abstract of a reference and is managed externally. A handler can have its reference relocated in memory by the system without it being invalidated, which is impossible to do with a pointer because it directly points to something (see Figure 8-6).
An important security concept is that a handle not only can identify a value but also associate access rights to that value. Consider the following example:
int fd = open("/etc/passwd", O_RDWR);
In this example, the program is requesting to read the system password file “/etc/passwd” in read/write mode (noted as 0_RDWR). This means the program is asking to open this file with the specified access rights, which are read and write. If this is permitted by the operating system, it will return a handle to the user. The actual access is controlled by the operating system, and the handle can be looked at as a token of that access right provided by the operating system. Another outcome could be the operating system denying access, which means not opening the file or providing a handle. This shows why handles can be stored but never changed by the programmer—they are issued and managed by the operating system and can be changed on the fly by the operating system.
Handles generally end with “.h” (for example, WinDef.h) and are unsigned integers that Windows uses to internally keep track of objects in memory. When Windows moves an object, such as a memory block, to make room in memory and thus impacts the location of the object, the handles table is updated. Think of a handle as a pointer to a structure Windows doesn’t want you to directly manipulate. That is the job of the operating system.
One security concern with regard to handles is a handle leak. This occurs when a computer program requests a handle to a resource but does not free the handle when it is no longer used. The outcome of this is a resource leak, which is similar to a pointer causing a memory leak. A handle leak could happen when a programmer requests a direct value while using a count, copy, or other operation that would break when the value changes. Other times it is an error caused by poor exception handling. An example would be a programmer using a handle to reference some property and proceeding without releasing the handle. If this issue continues to occur, it could lead to a number of handles being marked as “in use” and therefore unavailable, causing performance problems or a system crash.
The list that follows highlights the key handle concepts:
![]() A handle is an abstract reference value to a resource.
A handle is an abstract reference value to a resource.
![]() Handles hide the real memory address from the API user while permitting the system to reorganize physical memory in a way that’s transparent to the program.
Handles hide the real memory address from the API user while permitting the system to reorganize physical memory in a way that’s transparent to the program.
![]() A handle not only can identify a value but also associate access rights to that value.
A handle not only can identify a value but also associate access rights to that value.
![]() A handle leak can occur if a handle is not released after being used.
A handle leak can occur if a handle is not released after being used.
Services
The next topic to tackle is Windows services, which are long-running executable applications that operate in their own Windows session. Basically, they are services that run in the background. Services can automatically kick off when a computer starts up, such as the McAfee security applications shown in Figure 8-7, and they must conform to the interface rules and protocols of the Services Control Manager.
Services can also be paused and restarted. Figure 8-7 shows some services started under the Status tab. You can see whether a service will automatically start under the Startup Type tab. To view the services on a Microsoft Windows system as shown in Figure 8-7, type services.msc in the Run window. This brings up the Services Control Manager.
Services are ideal for running things within a user security context, starting applications that should always be run for a specific user, and for long-running functionally that doesn’t interfere with other users who are working on the same computer. An example would be monitoring whether storage is consumed past a certain threshold. The programmer could create a Windows service application that monitors storage space and set it to automatically start at bootup so it is continuously monitoring for the critical condition. If the user chooses not to monitor his system, he could open the Services Control Manager and change the startup type to Manual, meaning it must be manually turned on. Alternatively, he could just stop the service. The services inside the Services Control Manager can be started, stopped, or triggered by an event. Because services operate in their own user account, they can operate when a user is not logged in to the system, meaning that the storage space monitoring application could be set to automatically run for a specific user or for any other users, including when no user is logged in.
Windows administrators can manage services using the Services snap-in, Sc.exe, or Windows PowerShell. The Services snap-in is built into the Services Management Console and can connect to a local or remote computer on a network, thus enabling the administrator to perform some of the following actions:
![]() View installed services
View installed services
![]() Start, stop, or restart services
Start, stop, or restart services
![]() Change the startup type for a service
Change the startup type for a service
![]() Specify service parameters when available
Specify service parameters when available
![]() Change the startup type
Change the startup type
![]() Change the user account context where the service operates
Change the user account context where the service operates
![]() Configure recovery actions in the event a service fails
Configure recovery actions in the event a service fails
![]() Inspect service dependencies for troubleshooting
Inspect service dependencies for troubleshooting
![]() Export the list of services
Export the list of services
Sc.exe, also known as the Service Control utility, is a command-line version of the Services snap-in. This means it can do everything the Services snap-in can do as well as install and uninstall services. Windows PowerShell can also manage Windows services using the following commands, also called cmdlets:
![]() Get-Service: Gets the services on a local or remote computer
Get-Service: Gets the services on a local or remote computer
![]() New-Service: Creates a new Windows service
New-Service: Creates a new Windows service
![]() Restart-Service: Stops and then starts one or more services
Restart-Service: Stops and then starts one or more services
![]() Resume-Service: Resumes one or more suspended (paused) services
Resume-Service: Resumes one or more suspended (paused) services
![]() Set-Service: Starts, stops, and suspends a service, and changes its properties
Set-Service: Starts, stops, and suspends a service, and changes its properties
![]() Start-Service: Starts one or more stopped services
Start-Service: Starts one or more stopped services
![]() Stop-Service: Stops one or more running services
Stop-Service: Stops one or more running services
![]() Suspend-Service: Suspends (pauses) one or more running services
Suspend-Service: Suspends (pauses) one or more running services
Other tools that can manage Windows services are Net.exe, Windows Task Manager, and MSConfig; however, their capabilities are limited compared to the other tools mentioned. For example, MSConfig can enable or disable Windows services, and Windows Task Manager can show a list of installed services as well as start or stop them.
Like other aspects of Windows, services are targeted by attackers. Microsoft has improved the security of services in later versions of the Windows operating system after finding various attack methods that compromise and completely own older versions of Windows. However, even the newer versions of Windows are not perfect, so best practice dictates securing (disabling) services such as the following unless they are needed:
![]() TCP 53: DNS Zone Transfer
TCP 53: DNS Zone Transfer
![]() TCP 135: RPC Endpoint Mapper
TCP 135: RPC Endpoint Mapper
![]() TCP 139: NetBIOS Session Service
TCP 139: NetBIOS Session Service
![]() TCP 445: SMB Over TCP
TCP 445: SMB Over TCP
![]() TCP 3389: Terminal Services
TCP 3389: Terminal Services
![]() UDP 137: NetBIOS Name Service
UDP 137: NetBIOS Name Service
![]() UDP 161: Simple Network Management Protocol
UDP 161: Simple Network Management Protocol
![]() TCP/UDP 389: Lightweight Directory Access Protocol
TCP/UDP 389: Lightweight Directory Access Protocol
In addition, you should enable host security solutions, such as the Windows Firewall services. Enforcing least privilege access as well as using restricted tokens and access control can reduce the damage that could occur if an attacker successfully compromises a Windows system’s services. Basically applying best practices to secure hosts and your network will also help to reduce the risk of attacks against Microsoft Windows system services.
The list that follows highlights the key services concepts:
![]() Microsoft Windows services are long-running executable applications that operate in their own Windows session.
Microsoft Windows services are long-running executable applications that operate in their own Windows session.
![]() Services Control Manager enforces the rules and protocols for Windows services.
Services Control Manager enforces the rules and protocols for Windows services.
![]() Services are ideal for running things within a user security context, starting applications that should always be run for a specific user, and for long-running functionally that doesn’t interfere with other users who are working on the same computer.
Services are ideal for running things within a user security context, starting applications that should always be run for a specific user, and for long-running functionally that doesn’t interfere with other users who are working on the same computer.
![]() Windows administrators can manage services using the Services snap-in, Sc.exe, or Windows PowerShell.
Windows administrators can manage services using the Services snap-in, Sc.exe, or Windows PowerShell.
Windows Event Logs
The final topic to address in this chapter is Windows event logs. Logs, as a general definition, are records of events that happened in your computer. The purpose of logging in Windows is to record errors and events in a standard, centralized way. This helps you track what happened and troubleshoot problems. The most common place for Windows logs is the Windows event log, which contains logs for the operating system and several applications, such as SQL Server and Internet Information Server (IIS). Logs are structured in a data format so they can be easily searched and analyzed. The tool commonly used to do this is the Windows Event Viewer.
The Windows event logging service records events from many sources and stores them in a single collection known as the event log. The event log typically maintains three event log types: Application, System, and Security log files. You can generally find the Windows event logs in the C:Windowsystem3config directory. You can open the Windows Event Viewer to view these logs by simply searching for Event Viewer in the Run tab. Figure 8-8 shows an example of viewing logs in the Event Viewer. The panel on the left shows the Application, System, and Security log categories, whereas the panel on the right shows the actions.
There are many panels in the Event Viewer as well as many different ways you can view the data. Although the SECFND exam won’t have you dig through a Windows log, it is good practice to have a basic understanding of what type of data can be found in a log file. In general, you will find five event types when viewing Windows event logging:
![]() Error: Events that represent a significant problem such as loss of data or loss of functionality.
Error: Events that represent a significant problem such as loss of data or loss of functionality.
![]() Warning: Theses events are not significant, but may indicate a possible future issue.
Warning: Theses events are not significant, but may indicate a possible future issue.
![]() Information: Theses events represent the successful operation of an application, drive, or service.
Information: Theses events represent the successful operation of an application, drive, or service.
![]() Success Audit: Theses events record audited security access attempts that were successful.
Success Audit: Theses events record audited security access attempts that were successful.
![]() Failure Audit: Theses events record audited security access attempts that failed.
Failure Audit: Theses events record audited security access attempts that failed.
Logs can eat up storage, so administrators should either set a time to have older logs deleted or export them to a storage system. Some security tools such as Security Information and Event Managers (SIEMs) can be used as a centralized tool for reading logs from many devices. The challenge for any system attempting to use a log is ensuring that the system is able to understand the log format.
If a system reading the file does not understand the file type or expects data in a specific format, weird results could happen or the system might reject the file. Administrators can adjust the system receiving the logs from Windows to accept the standard event format or use a parser in Windows to modify how the data is sent.
A log parser is a versatile tool that provides universal query access to text-based data such as event logs, the registry, the file system, XML files, CVE files, and so on. A parser works by you telling it what information you need and how you want it processed. The results of a query can be custom formatted in text-based output, or the output can be customized to a specialty target system such as SQL, SYSLOG, or a chart. Basically, a log parser gives you tons of flexibility for manipulating data. An example would be using a Windows IIS log parser to format event logs to be read by a SQL server.
It is important to protect logs because they are a critical tool for forensic investigations when an event occurs. Malicious users will likely be aware that their actions are logged by Windows and attempt to either manipulate or wipe all logs to cover their tracks. Savvy attackers will choose to only modify their impact to the log to avoid alerting administrators that an event has occurred.
The list that follows highlights the key Windows event log concepts:
![]() Logs are records of events that happen on a computer.
Logs are records of events that happen on a computer.
![]() The most common place for Windows logs is the Windows event log.
The most common place for Windows logs is the Windows event log.
![]() Windows Event Viewer is a common tool used to view Windows event logs.
Windows Event Viewer is a common tool used to view Windows event logs.
![]() You can generally find the Windows event logs in the C:Windowsystem3config directory.
You can generally find the Windows event logs in the C:Windowsystem3config directory.
![]() Event logs typically maintain three event log types: Application, System, and Security log files
Event logs typically maintain three event log types: Application, System, and Security log files
![]() Within the log types are generally five event types: Error, Warning, Information, Success Audit, and Failure Audit
Within the log types are generally five event types: Error, Warning, Information, Success Audit, and Failure Audit
![]() A log parser is a versatile tool that provides universal query access to text-based data.
A log parser is a versatile tool that provides universal query access to text-based data.
Exam Preparation Tasks
Review All Key Topics
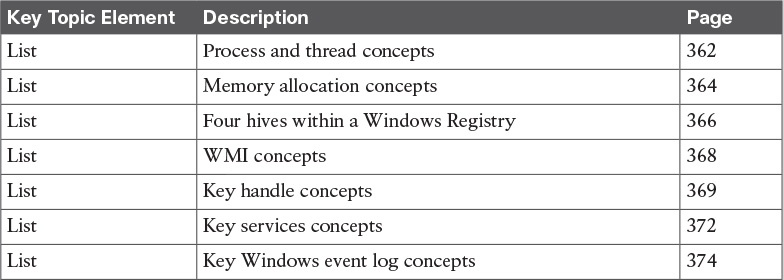
Review the most important topics in the chapter, noted with the Key Topic icon in the outer margin of the page. Table 8-2 lists these key topics and the page numbers on which each is found.
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
Windows process permission
VirtualAlloc
HeapAlloc
Malloc
Windows registration
hives
Windows Management Instrumentation (WMI)
Microsoft Windows services
log parser
Q&A
The answers to these questions appear in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Q&A Questions.” For more practice with exam format questions, use the exam engine on the website.
1. Which is the best definition of a Windows process?
a. A program that is running within Windows
b. The basic unit an operating system allocates process time to
c. A group of worker threads that efficiently execute asynchronous callbacks for the application
d. A unit of execution that is manually scheduled by an application
2. Which statement about virtual address space is true?
a. The virtual address space is shared by the system and referenced by a page table for each process.
b. The virtual address space is private and cannot be accessed by other processes unless it is specifically shared.
c. The virtual address represents the physical location of any object in memory.
d. Virtual address space cannot be shared.
3. RAM is an example of which of the following?
a. Magnetic storage
b. Nonvolatile memory
c. Volatile memory
d. Removable storage
4. Which command is used to view the Windows Registry?
a. winedit
b. winreg
c. regedit
d. cntedit
5. Which of the following is not a Windows Registry hive?
a. HKEY_LOCAL (HKLM)
b. HKEY_CLASSES_ROOT (HKCR)
c. HKEY_CURRENT_CONFIG (HCU)
d. HKEY_USERS (HKU)
6. What does WMI stand for?
a. Windows Management Instructions
b. Windows Management Instrumentation
c. Windows Monitor Instrumentation
d. Windows Monitor Instructions
7. Which of the following is something WMI can’t be used for?
a. To schedule times for processes to run
b. To assign and change drive label
c. To uninstall an application
d. To enable or disable error logging
8. What can cause a handle leak?
a. A loop that leverages a handle
b. A Windows compiler error
c. A handle that’s not released after being used
d. A pointer to a handle
9. What is the command to bring up the Windows Services Control manager?
a. cntmanage
b. services.msc
c. regedit
d. services.exe
10. What tool can be used in Windows to format a log for a SQL server?
a. SIEM
b. Programing Language
c. Event View
d. Log Parser
References and Further Reading
https://msdn.microsoft.com/en-us/library/windows/desktop/ms681917(v=vs.85).aspx
http://la.trendmicro.com/media/misc/understanding-wmi-malware-research-paper-en.pdf
https://msdn.microsoft.com/en-us/library/d56de412%28v=vs.110%29.aspx
https://msdn.microsoft.com/en-us/library/windows/desktop/ms724457%28v=vs.85%29.aspx
https://msdn.microsoft.com/en-us/library/hk1k7x6x.aspx
https://support.microsoft.com/en-us/kb/256986
https://msdn.microsoft.com/en-us/library/aa394582%28v=vs.85%29.aspx