Chapter 10. Endpoint Security Technologies
This chapter covers the following topics:
![]() Antimalware and antivirus software
Antimalware and antivirus software
![]() Host-based firewalls and host-based intrusion prevention
Host-based firewalls and host-based intrusion prevention
![]() Application-level whitelisting and blacklisting
Application-level whitelisting and blacklisting
This chapter describes different endpoint security technologies available to protect desktops, laptops, servers, and mobile devices. It covers details about antimalware and antivirus software, as well as what are host-based firewalls and host-based intrusion prevention solutions. You will also learn the concepts of application-level whitelisting and blacklisting, as well as system-based sandboxing.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz helps you identify your strengths and deficiencies in this chapter’s topics. The eight-question quiz, derived from the major sections in the “Foundation Topics” portion of the chapter, helps you determine how to spend your limited study time. You can find the answers in Appendix A Answers to the “Do I Know This Already?” Quizzes and Q&A Questions.
Table 10-1 outlines the major topics discussed in this chapter and the “Do I Know This Already?” quiz questions that correspond to those topics.
1. What is a Trojan horse?
a. A piece of malware that downloads and installs other malicious content from the Internet to perform additional exploitation on an affected system.
b. A type of malware that executes instructions determined by the nature of the Trojan to delete files, steal data, and compromise the integrity of the underlying operating system, typically by leveraging social engineering and convincing a user to install such software.
c. A virus that replicates itself over the network infecting numerous vulnerable systems.
d. A type of malicious code that is injected into a legitimate application. An attacker can program a logic bomb to delete itself from the disk after it performs the malicious tasks on the system.
2. What is ransomware?
a. A type of malware that compromises a system and then often demands a ransom from the victim to pay the attacker in order for the malicious activity to cease or for the malware to be removed from the affected system
b. A set of tools used by an attacker to elevate his privilege to obtain root-level access in order to completely take control of the affected system
c. A type of intrusion prevention system
d. A type of malware that doesn’t affect mobile devices
3. Which of the following are examples of free antivirus software? (Select all that apply.)
a. McAfee Antivirus
b. Norton AntiVirus
c. ClamAV
d. Immunet
4. Host-based firewalls are often referred to as which of the following?
a. Next-generation firewalls
b. Personal firewalls
c. Host-based intrusion detection systems
d. Antivirus software
5. What is an example of a Cisco solution for endpoint protection?
a. Cisco ASA
b. Cisco ESA
c. Cisco AMP for Endpoints
d. Firepower Endpoint System
6. What is a graylist?
a. A list of separate things, such as hosts, applications, email addresses, and services, that are authorized to be installed or active on a system in accordance with a predetermined baseline.
b. A list of different entities that have been determined to be malicious.
c. A list of different objects that have not yet been established as not harmful or malicious. Once additional information is obtained, graylist items can be moved onto a whitelist or a blacklist.
d. A list of different objects that have not yet been established as not harmful or malicious. Once additional information is obtained, graylist items cannot be moved onto a whitelist or a blacklist.
7. Which of the following are examples of application file and folder attributes that can help with application whitelisting?
a. Application store
b. File path
c. Filename
d. File size
8. Which of the following are examples of sandboxing implementations?
a. Google Chromium sandboxing
b. Java Virtual Machine (JVM) sandboxing
c. HTML CSS and JavaScript sandboxing
d. HTML5 “sandbox” attribute for use with iframes
Foundation Topics
Antimalware and Antivirus Software
As you probably already know, computer viruses and malware have been in existence for a long time. On the other hand, the level of sophistication has increased over the years. There are numerous antivirus and antimalware solutions on the market designed to detect, analyze, and protect against both known and emerging endpoint threats. Before diving into these technologies, you should learn about viruses and malicious software (malware) and some of the taxonomy around the different types of malicious software.
The following are the most common types of malicious software:
![]() Computer virus: A malicious software that infects a host file or system area to perform undesirable actions such as erasing data, stealing information, and corrupting the integrity of the system. In numerous cases, these viruses multiply again to form new generations of themselves.
Computer virus: A malicious software that infects a host file or system area to perform undesirable actions such as erasing data, stealing information, and corrupting the integrity of the system. In numerous cases, these viruses multiply again to form new generations of themselves.
![]() Worm: Viruses that replicate themselves over the network, infecting numerous vulnerable systems. In most occasions, a worm will execute malicious instructions on a remote system without user interaction.
Worm: Viruses that replicate themselves over the network, infecting numerous vulnerable systems. In most occasions, a worm will execute malicious instructions on a remote system without user interaction.
![]() Mailer and mass-mailer worm: A type of worm that sends itself in an email message. Examples of mass-mailer worms are Loveletter.A@mm and W32/SKA.A@m (a.k.a. the Happy99 worm), which sends a copy of itself every time the user sends a new message.
Mailer and mass-mailer worm: A type of worm that sends itself in an email message. Examples of mass-mailer worms are Loveletter.A@mm and W32/SKA.A@m (a.k.a. the Happy99 worm), which sends a copy of itself every time the user sends a new message.
![]() Logic bomb: A type of malicious code that is injected into a legitimate application. An attacker can program a logic bomb to delete itself from the disk after it performs the malicious tasks on the system. Examples of these malicious tasks include deleting or corrupting files or databases and executing a specific instruction after certain system conditions are met.
Logic bomb: A type of malicious code that is injected into a legitimate application. An attacker can program a logic bomb to delete itself from the disk after it performs the malicious tasks on the system. Examples of these malicious tasks include deleting or corrupting files or databases and executing a specific instruction after certain system conditions are met.
![]() Trojan horse: A type of malware that executes instructions determined by the nature of the Trojan to delete files, steal data, or compromise the integrity of the underlying operating system. Trojan horses typically use a form of social engineering to fool victims into installing such software on their computers or mobile devices. Trojans can also act as backdoors.
Trojan horse: A type of malware that executes instructions determined by the nature of the Trojan to delete files, steal data, or compromise the integrity of the underlying operating system. Trojan horses typically use a form of social engineering to fool victims into installing such software on their computers or mobile devices. Trojans can also act as backdoors.
![]() Backdoor: A piece of malware or configuration change that allows attackers to control the victim’s system remotely. For example, a backdoor can open a network port on the affected system so that the attacker can connect and control the system.
Backdoor: A piece of malware or configuration change that allows attackers to control the victim’s system remotely. For example, a backdoor can open a network port on the affected system so that the attacker can connect and control the system.
![]() Exploit: A malicious program designed to “exploit” or take advantage of a single vulnerability or set of vulnerabilities.
Exploit: A malicious program designed to “exploit” or take advantage of a single vulnerability or set of vulnerabilities.
![]() Downloader: A piece of malware that downloads and installs other malicious content from the Internet to perform additional exploitation on an affected system.
Downloader: A piece of malware that downloads and installs other malicious content from the Internet to perform additional exploitation on an affected system.
![]() Spammer: Systems or programs that send unsolicited messages via e-mail, instant messaging, newsgroups, or any other kind of computer or mobile device communication. Spammers use the type of malware that’s sole purpose is to send these unsolicited messages, with the primary goal of fooling users into clicking malicious links, replying to emails or messages with sensitive information, or performing different types of scams.
Spammer: Systems or programs that send unsolicited messages via e-mail, instant messaging, newsgroups, or any other kind of computer or mobile device communication. Spammers use the type of malware that’s sole purpose is to send these unsolicited messages, with the primary goal of fooling users into clicking malicious links, replying to emails or messages with sensitive information, or performing different types of scams.
The attacker’s main objective is to make money.
![]() Key logger: A piece of malware that captures the user’s keystrokes on a compromised computer or mobile device. It collects sensitive information such as passwords, PINs, personal identifiable information (PII), credit card numbers, and more.
Key logger: A piece of malware that captures the user’s keystrokes on a compromised computer or mobile device. It collects sensitive information such as passwords, PINs, personal identifiable information (PII), credit card numbers, and more.
![]() Rootkit: A set of tools used by an attacker to elevate his privilege to obtain root-level access to be able to completely take control of the affected system.
Rootkit: A set of tools used by an attacker to elevate his privilege to obtain root-level access to be able to completely take control of the affected system.
![]() Ransomware: A type of malware that compromises a system and then often demands a ransom from the victim to pay the attacker in order for the malicious activity to cease or for the malware to be removed from the affected system. The following are examples of ransomware:
Ransomware: A type of malware that compromises a system and then often demands a ransom from the victim to pay the attacker in order for the malicious activity to cease or for the malware to be removed from the affected system. The following are examples of ransomware:
![]() Reveton
Reveton
![]() SamSam
SamSam
![]() Crypto Locker
Crypto Locker
![]() CryptoWall
CryptoWall
There are numerous types of commercial and free antivirus software, including the following:
![]() Avast!
Avast!
![]() AVG Internet Security
AVG Internet Security
![]() Bitdefender Antivirus Free
Bitdefender Antivirus Free
![]() ZoneAlarm PRO Antivirus + Firewall and ZoneAlarm Internet Security Suite
ZoneAlarm PRO Antivirus + Firewall and ZoneAlarm Internet Security Suite
![]() F-Secure Anti-Virus
F-Secure Anti-Virus
![]() Kaspersky Anti-Virus
Kaspersky Anti-Virus
![]() McAfee AntiVirus
McAfee AntiVirus
![]() Panda Antivirus
Panda Antivirus
![]() Sophos Antivirus
Sophos Antivirus
![]() Norton AntiVirus
Norton AntiVirus
![]() ClamAV
ClamAV
![]() Immunet AntiVirus
Immunet AntiVirus
TIP
ClamAV is an open source antivirus engine sponsored and maintained by Cisco and non-Cisco engineers. You can download ClamAV from http://www.clamav.net. Immunet is a free community-based antivirus software maintained by Cisco Sourcefire. You can download Immunet from http://www.immunet.com.
There are numerous other antivirus software companies and products. The following link provides a comprehensive list and comparison of the different antivirus software available on the market: http://en.wikipedia.org/wiki/Comparison_of_antivirus_software.
Host-Based Firewalls and Host-Based Intrusion Prevention
Host-based firewalls are often referred to as “personal firewalls.” Personal firewalls and host intrusion prevention systems (HIPSs) are software applications that you can install on end-user machines or servers to protect them from external security threats and intrusions. The term personal firewall typically applies to basic software that can control Layer 3 and Layer 4 access to client machines. HIPS provides several features that offer more robust security than a traditional personal firewall, such as host intrusion prevention and protection against spyware, viruses, worms, Trojans, and other types of malware.
Today, more sophisticated software is available on the market that makes basic personal firewalls and HIPS obsolete. For example, Cisco Advanced Malware Protection (AMP) for Endpoints provides more granular visibility and controls to stop advanced threats missed by other security layers. Cisco AMP for Endpoints takes advantage of telemetry from big data, continuous analysis, and advanced analytics provided by Cisco threat intelligence in order to detect, analyze, and stop advanced malware across endpoints.
Cisco AMP for Endpoints provides advanced malware protection for many operating systems, including the following:
![]() Windows
Windows
![]() Mac OS X
Mac OS X
![]() Android
Android
Attacks are getting very sophisticated, and they can evade detection of traditional systems and endpoint protection. Nowadays, attackers have the resources, knowledge, and persistence to beat point-in-time detection. Cisco AMP for Endpoints provides mitigation capabilities that go beyond point-in-time detection. It uses threat intelligence from Cisco to perform retrospective analysis and protection. Cisco AMP for Endpoints also provides device and file trajectory capabilities to allow the security administrator to analyze the full spectrum of an attack.
Cisco acquired a security company called Threat Grid that provides cloud-based and on-premises malware analysis solutions. Cisco integrated Cisco AMP and Threat Grid to provide a solution for advanced malware analysis with deep threat analytics. The Cisco AMP Threat Grid integrated solution analyzes millions of files and correlates them against hundreds of millions of malware samples. This provides a lot of visibility into attack campaigns and how malware is distributed. This solution provides security administrators with detailed reports of indicators of compromise and threat scores that help them prioritize mitigations and recovery from attacks.
In addition to host-based firewalls and HIPS, there are several solutions that provide hardware and software encryption of endpoint data. Several solutions provide capabilities to encrypt user data “at rest,” and others provide encryption when transferring files to the corporate network.
When people refer to email encryption, they often are referring to encrypting the actual email message so that only the intended receiver can decrypt and read the message. To effectively protect your emails, however, you should make sure of the following:
![]() The connection to your email provider or email server is actually encrypted.
The connection to your email provider or email server is actually encrypted.
![]() Your actual email messages are encrypted.
Your actual email messages are encrypted.
![]() Your stored, cached, or archived email messages are also protected.
Your stored, cached, or archived email messages are also protected.
There are many commercial and free email encryption software programs. The following are examples of email encryption solutions:
![]() Pretty Good Privacy (PGP)
Pretty Good Privacy (PGP)
![]() GNU Privacy Guard (GnuPG)
GNU Privacy Guard (GnuPG)
![]() Secure/Multipurpose Internet Mail Extensions (S/MIME)
Secure/Multipurpose Internet Mail Extensions (S/MIME)
![]() Web-based encryption email services such as Sendinc and JumbleMe
Web-based encryption email services such as Sendinc and JumbleMe
S/MIME requires you to install a security certificate on your computer, and PGP requires you to generate a public and private key. Both require you to give your contacts your public key before they can send you an encrypted message. Similarly, the intended recipients of your encrypted email must install a security certificate on their workstation or mobile device and provide you with their public key before they send the encrypted email (so that you can decrypt it). Many email clients and web browser extensions for services such as Gmail provide support for S/MIME. You can obtain a certificate from a certificate authority in your organization or from a commercial service such as DigiCert or VeriSign. You can also obtain a free email certificate from an organization such as Comodo.
Many commercial and free pieces of software are available that enable you to encrypt files in an end-user workstation or mobile device. The following are a few examples of free solutions:
![]() GPG: GPG enables you to encrypt files and folders on a Windows, Mac, or Linux system.
GPG: GPG enables you to encrypt files and folders on a Windows, Mac, or Linux system.
![]() The built-in Mac OS X Disk Utility: Disk Utility enables you to create secure disks by encrypting files with AES 128-bit or AES 256-bit encryption.
The built-in Mac OS X Disk Utility: Disk Utility enables you to create secure disks by encrypting files with AES 128-bit or AES 256-bit encryption.
![]() TrueCrypt: An encryption tool for Windows, Mac, and Linux systems.
TrueCrypt: An encryption tool for Windows, Mac, and Linux systems.
![]() AxCrypt: A Windows-only file encryption tool.
AxCrypt: A Windows-only file encryption tool.
![]() BitLocker: A full disk encryption feature included in several Windows operating systems.
BitLocker: A full disk encryption feature included in several Windows operating systems.
![]() Many Linux distributions such as Ubuntu: Allow you to encrypt the home directory of a user with built-in utilities.
Many Linux distributions such as Ubuntu: Allow you to encrypt the home directory of a user with built-in utilities.
![]() Mac OS X FileVault: Supports full disk encryption on Mac OS X systems.
Mac OS X FileVault: Supports full disk encryption on Mac OS X systems.
The following are a few examples of commercial file encryption software:
![]() Symantec Endpoint Encryption
Symantec Endpoint Encryption
![]() PGP Whole Disk Encryption
PGP Whole Disk Encryption
![]() McAfee Endpoint Encryption (SafeBoot)
McAfee Endpoint Encryption (SafeBoot)
![]() Trend Micro Endpoint Encryption
Trend Micro Endpoint Encryption
Application-Level Whitelisting and Blacklisting
Three different concepts are defined in this section:
![]() Whitelist: A list of separate things (such as hosts, applications, email addresses, and services) that are authorized to be installed or active on a system in accordance with a predetermined baseline.
Whitelist: A list of separate things (such as hosts, applications, email addresses, and services) that are authorized to be installed or active on a system in accordance with a predetermined baseline.
![]() Blacklist: A list of different entities that have been determined to be malicious.
Blacklist: A list of different entities that have been determined to be malicious.
![]() Graylist: A list of different objects that have not yet been established as not harmful or malicious. Once additional information is obtained, graylist items can be moved onto a whitelist or a blacklist.
Graylist: A list of different objects that have not yet been established as not harmful or malicious. Once additional information is obtained, graylist items can be moved onto a whitelist or a blacklist.
TIP
The National Institute of Standards and Technology (NIST) defines the concept of whitelisting and blacklisting applications in their special publication NIST.SP.800-167 (http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-167.pdf).
Application whitelisting can be used to stop threats on managed hosts where users are not able to install or run applications without authorization. For example, let’s imagine that you manage a kiosk in an airport where users are limited to running a web-based application. You may want to whitelist that application and prohibit running any additional applications in the system.
One of the most challenging parts of application whitelisting is the continuous management of what is and is not on the whitelist. It is extremely difficult to keep the list of what is and is not allowed on a system where there are hundreds of thousands of files with a legitimate need to be present and running on the system; however, several modern application whitelisting solutions are available that can help with this management nightmare. Several of these modern application whitelisting systems are quite adept at tracking what is happening on a system when approved changes are made and managing the whitelist accordingly. These solutions do this by performing system application profiling.
Different application file and folder attributes can help with application whitelisting. The following are a few examples:
![]() File path: The process to permit all applications contained within a particular path or directory/folder. This is a very weak attribute if used by itself because it allows any malicious files residing in such path/directory to be executed.
File path: The process to permit all applications contained within a particular path or directory/folder. This is a very weak attribute if used by itself because it allows any malicious files residing in such path/directory to be executed.
![]() Filename: This is also a weak attribute if used in isolation because an attacker could simply change the name of the file to be the same as a common benign file. It is recommended to combine path and filename attributes with strict access controls or to combine a filename attribute with a digital signature attribute.
Filename: This is also a weak attribute if used in isolation because an attacker could simply change the name of the file to be the same as a common benign file. It is recommended to combine path and filename attributes with strict access controls or to combine a filename attribute with a digital signature attribute.
![]() File size: Monitoring the file size assumes that a malicious version of an application would have a different file size than the original. However, attackers can also change the size of any given file. It is better to use attributes such as digital signatures and cryptographic hashes (MD5 or SHA).
File size: Monitoring the file size assumes that a malicious version of an application would have a different file size than the original. However, attackers can also change the size of any given file. It is better to use attributes such as digital signatures and cryptographic hashes (MD5 or SHA).
Application blacklisting works by keeping a list of applications that will be blocked on a system, preventing such applications from installing or running on that system. One of the major drawbacks of application blacklisting is that the number, diversity, and complexity of threats are constantly increasing. This is why it is very important to implement modern systems with dynamic threat intelligence feeds such as the Cisco Firepower solutions. The Cisco Firepower solutions include the Security Intelligence feature, which allows you to immediately blacklist (block) connections, applications, and files based on the latest threat intelligence provided by the Cisco Talos research team, removing the need for a more resource-intensive, in-depth analysis.
Additionally, the security intelligence feature from Cisco Firepower next-generation IPS appliances and Cisco next-generation firewalls works by blocking traffic to or from IP addresses, URLs, or domain names that have a known-bad reputation. This traffic filtering takes place before any other policy-based inspection, analysis, or traffic handling.
NOTE
For more information about the Cisco Firepower Security Intelligence Blacklisting feature, go to http://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmc-config-guide-v60/Security_Intelligence_Blacklisting.html.
Some security professionals claim that, although whitelisting is a more thorough solution to the problem, it is not practical because of the overhead and resources required to create and maintain an effective whitelist.
System-Based Sandboxing
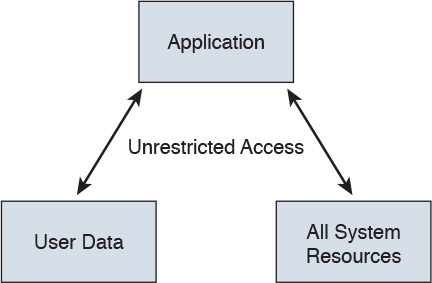
Sandboxing limits the impact of security vulnerabilities and bugs in code to only run inside the “sandbox.” The goal of sandboxing is to ensure software bugs and exploits of vulnerabilities cannot affect the rest of the system and cannot install persistent malware in the system. In addition, sandboxing prevents exploits or malware from reading and stealing arbitrary files from the user’s machine. Figure 10-1 shows an application without being run in a sandbox. The application has complete access to user data and other system resources.
Figure 10-2 shows the concept of a sandbox, where the application does not have access to user data or the rest of the system resources.
Several system-based sandboxing implementations are available. The following are a few examples:
![]() Google Chromium sandboxing
Google Chromium sandboxing
![]() Java JVM sandboxing
Java JVM sandboxing
![]() HTML5 “sandbox” attribute for use with iframes
HTML5 “sandbox” attribute for use with iframes
Figure 10-3 illustrates the Google Chromium sandbox high-level architecture.
In Google Chromium’s implementation, the target process hosts all the code that runs inside the sandbox and the sandbox infrastructure client side. The broker is always the browser process, and it is a privileged controller of the activities of the sandboxed processes. The following are the responsibilities of the broker:
![]() Detail the policy for each target process.
Detail the policy for each target process.
![]() Spawn the target processes.
Spawn the target processes.
![]() Host the sandbox policy engine service.
Host the sandbox policy engine service.
![]() Host the sandbox interception manager.
Host the sandbox interception manager.
![]() Host the sandbox interprocess communication (IPC) service to the target processes. IPC is a collection of programming interfaces that allows the coordination of activities among different program processes that can run concurrently in an operating system.
Host the sandbox interprocess communication (IPC) service to the target processes. IPC is a collection of programming interfaces that allows the coordination of activities among different program processes that can run concurrently in an operating system.
![]() Perform the policy-allowed actions on behalf of the target process.
Perform the policy-allowed actions on behalf of the target process.
The broker should always outlive all the target processes that it spawned. The sandbox IPC is used to transparently forward certain API calls from the target to the broker. These calls are always evaluated against the predefined policy.
Exam Preparation Tasks
Review All Key Topics
Review the most important topics in the chapter, noted with the Key Topic icon in the outer margin of the page. Table 10-2 lists these key topics and the page numbers on which each is found.
Complete Tables and Lists from Memory
There are no memory tables in this chapter.
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
viruses
worms
mailers and mass-mailer worms
logic bombs
exploits
Trojan horses
backdoors
exploits
downloaders
spammers
key loggers
rootkits
Q&A
The answers to these questions appear in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Q&A Questions.” For more practice with exam format questions, use the exam engine on the website.
1. What are worms?
a. A type of malware that compromises a system and then often demands a ransom from the victim to pay the attacker in order for the malicious activity to cease or for the malware to be removed from the affected system.
b. Viruses that replicate themselves over the network, infecting numerous vulnerable systems. On most occasions, a worm will execute malicious instructions on a remote system without user interaction.
c. An exploit of a network infrastructure device vulnerability that installs a backdoor on the affected system.
d. An exploit of a firewall vulnerability that installs a backdoor on the affected system.
2. What is ransomware?
a. A type of malware that compromises a system and then often demands a ransom from the victim to pay the attacker in order for the malicious activity to cease or for the malware to be removed from the affected system.
b. A type of malware that is installed on a stolen laptop or mobile device.
c. A type of malware that compromises a system that has access to sensitive data and can replicate itself in other systems such as firewalls, IPSs, NetFlow collectors, and so on.
d. A type of malware that compromises a system that has access to sensitive data and can replicate itself in other systems such as routers and switches.
3. Which of the following are examples of system-based sandboxing implementations? (Select all that apply.)
a. Google Project Zero
b. Google Chromium sandboxing
c. Java JVM sandboxing
d. Threat Grid
4. Which of the following are benefits of system-based sandboxing?
a. It limits the development of an application inside of a region of memory.
b. It limits the impact of security vulnerabilities and bugs in code to only run inside the “sandbox.”
c. It prevents software bugs and exploits of vulnerabilities from affecting the rest of the system and from installing persistent malware in the system.
d. It limits the communication of kernel modules within the system, controlling the flow of information and data exchange.
5. What is a limitation of application whitelisting?
a. The cost of application whitelisting technologies.
b. The ability to interact with other systems.
c. Scalability in low-power and low-resource IoT.
d. The continuous management of what is and is not on the whitelist.
6. Cisco AMP for Endpoints takes advantage of which of the following?
a. Telemetry from big data, continuous analysis, and advanced analytics provided by Cisco ESA and WSA in order to detect, analyze, and stop advanced malware across endpoints
b. Advanced analytics provided by antivirus software in order to detect, analyze, and stop advanced malware across endpoints
c. Telemetry from big data, continuous analysis, and advanced analytics provided by Cisco threat intelligence in order to detect, analyze, and stop advanced malware across endpoints
d. Telemetry from big data, continuous analysis, and advanced analytics provided by Cisco next-generation firewalls in order to detect, analyze, and stop advanced malware across endpoints.
7. Which of the following is an example of a host-based encryption technology that can help protect files as well as email?
a. Cisco AMP
b. Protected Guided Privacy (PGP)
c. Pretty Good Privacy (PGP)
d. Cisco WSA
8. What is an application blacklist?
a. A list of different entities that have been determined to be malicious
b. A list of different entities that have been determined to be false positives
c. A list of different malicious websites and hosts
d. A list of different domains that are known to host malware
9. Which of the following is software that can enable you to encrypt files on your hard disk drive?
a. BitCrypt
b. CryptoWall
c. CryptoLocker
d. BitLocker
10. To effectively protect your emails, you should make sure of which the following?
a. All your email messages are sent to a sandbox to be evaluated before reaching their destination.
b. The connection to your email provider or email server is actually encrypted.
c. Your actual email messages are encrypted.
d. Your stored, cached, or archived email messages are also protected.