Chapter 14. Security Evasion Techniques
This chapter covers the following topics:
Describe the following concepts as they relate to security evasion techniques:
![]() Protocol-level misinterpretation
Protocol-level misinterpretation
![]() Traffic substitution and insertion
Traffic substitution and insertion
The last chapter provided an overview of some common methods malicious parties and contracted penetration testers use to breach networks. In summary, an attacker looks to abuse a vulnerability to accomplish something; however, there is another element that can make or break the success of the attack. That missing element is stealth, meaning attackers must also consider the amount of exposure an attack may cause as well as the expected countermeasures if the attack is noticed by the target’s defense measures.
In this chapter, we look at how attackers obtain stealth as well as the tricks used to negatively impact detection and forensic technologies. An example of this concept is a robber kicking in a door verses picking a lock when breaking into a house. Both methods will accomplish the same goal of gaining access to the property. The difference is that kicking in a door will be louder and leave a mess behind that will quickly attract attention, whereas picking a lock is slower but leaves little evidence and is much quieter, which is why it is the more common choice for a robbery. Another example would be the robber picking the lock and setting off the alarm system every few days before actually attempting to enter the property. The idea is that the people monitoring the system will assume the attempt following multiple false alarms is another false alarm, thus giving the attacker access without concern for the alarm attracting attention to his or her actions. This ignoring the alarm behavior can be seen in some neighborhoods with car alarms that continually go off on their own.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz helps you identify your strengths and deficiencies in this chapter’s topics. The ten-question quiz, derived from the major sections in the “Foundation Topics” portion of the chapter, helps you determine how to spend your limited study time. You can find the answers in Appendix A Answers to the “Do I Know This Already?” Quizzes and Q&A Questions.
Table 14-1 outlines the major topics discussed in this chapter and the “Do I Know This Already?” quiz questions that correspond to those topics.
1. Which of the following is when the attacker sends traffic slower than normal, not exceeding thresholds inside the time windows the signatures use to correlate different packets together?
a. Traffic insertion
b. Protocol manipulation
c. Traffic fragmentation
d. Timing attack
2. Which of the following would give an IPS the most trouble?
a. Jumbo packets
b. Encryption
c. Throughput
d. Updates
3. Which type of attack is when an IPS receives a lot of traffic/packets?
a. Resource exhaustion
b. DoS (denial of service)
c. Smoke and mirrors
d. Timing attack
4. Which of the following is not an example of traffic fragmentation?
a. Modifying routing tables
b. Modifying the TCP/IP in a way that is unexpected by security detection devices
c. Modifying IP headers to cause fragments to overlap
d. TCP segmentation
5. What is the best defense for traffic fragmentation attacks?
a. Deploying a passive security solution that monitors internal traffic for unusual traffic and traffic fragmentation
b. Deploying a next-generation application layer firewall
c. Configuring fragmentation limits on a security solution
d. Deploying a proxy or inline security solution
6. Which of the following is a TCP-injection attack?
a. Forging a TCP packet over an HTTPS session
b. Replacing legitimate TCP traffic with forged TCP packets
c. The addition of a forged TCP packet to an existing TCP session
d. Modifying the TCP/IP in a way that is unexpected by security detection
7. A traffic substitution and insertion attack does which of the following?
a. Substitutes the traffic with data in a different format but with the same meaning
b. Substitutes the payload with data in the same format but with a different meaning, providing a new payload
c. Substitutes the payload with data in a different format but with the same meaning, not modifying the payload
d. Substitutes the traffic with data in the same format but with a different meaning
8. Which of the following is not a defense against a traffic substitution and insertion attack?
a. Unicode de-obfuscation
b. Using Unicode instead of ASCII
c. Adopting the format changes
d. Properly processing extended characters
9. Which of the following is not a defense against a pivot attack?
a. Content filtering
b. Proper patch management
c. Network segmentation
d. Access control
10. Which security technology would be best for detecting a pivot attack?
a. Virtual private network (VPN)
b. Host-based antivirus
c. NetFlow solution looking for anomalies within the network
d. Application layer firewalls
Foundation Topics
Encryption and Tunneling
A very simple definition of encryption in the context of the SECFND exam is “to hide or encode something so the content is protected from unwanted parties.” The content could be network traffic, such as a virtual private network (VPN) between two systems encrypting traffic to prevent eavesdropping on a conversation. Encryption could also mean rendering a file unreadable unless the user is able to decrypt the file. Although encryption might sound like something very positive, attackers can use it to hide data when leaving a victim’s network after successfully breaching it or to mask an attack from a security defense tool. For example, encrypting an attack would hide it from many signature-based detection technologies such as an Intrusion Prevention System (IPS).
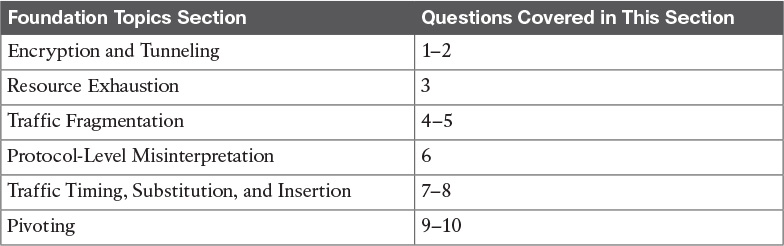
Starting with protecting data in transit, the use of virtual private networks (VPNs) is a common method for providing security for network traffic. A VPN can exist between two or more locations; this is known as a site-to-site VPN. Its purpose is to connect two or more locations in a secure manner over an unsecure medium. An example is an organization having two locations in different countries. A site-to-site VPN could be set up so that someone at location A could plug in his or her laptop and access resources at location B without any network changes. This means that communication between sites A and B travels over an encrypted tunnel. Any unwanted parties who attempt to capture and view the traffic would be unable to decipher it because they don’t have the ability to decrypt the traffic. Figure 14-1 illustrates how a typical site-to-site VPN session functions.
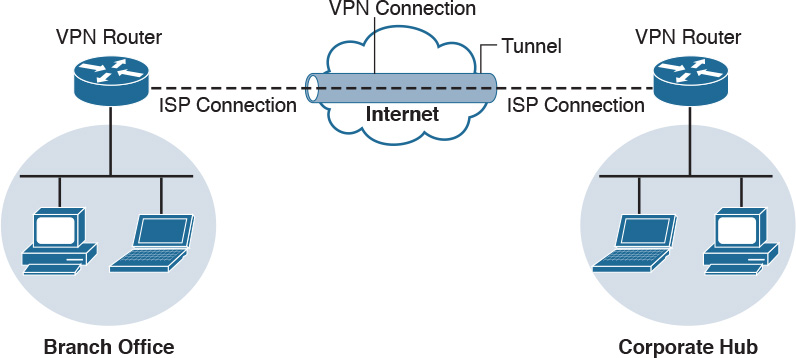
Another form of VPN technology involves securing traffic from a specific host to another location known as a remote-access VPN. As with a site-to-site VPN, the traffic between the host and remote connection is encrypted to prevent eavesdropping. The two forms of remote-access VPN are client based and clientless. Client-based remote-access VPN requires a hardware or software client to establish, maintain, and terminate the VPN connection. This approach is typically used for employees and other users who require a certain level of access to a remote location on a continuous basis. VPN security policy can be enforced to ensure the proper access level is maintained. An example of a remote-access VPN technology is Cisco AnyConnect; however, there are many other open source and commercial options. Figure 14-2 shows an example of a typical remote-access VPN session.
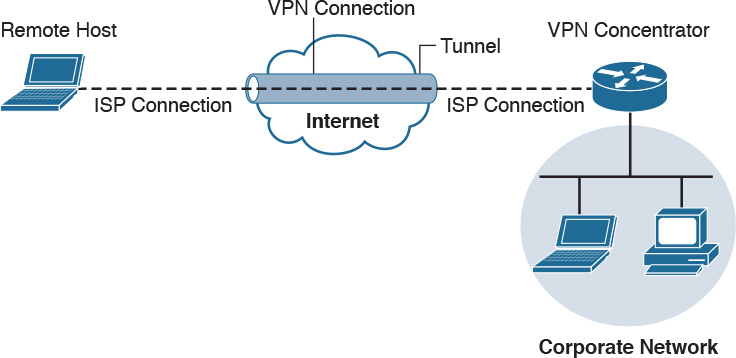
Cisco AnyConnect offers many security features to ensure the right person, device, or level of access is provisioned to the end user. Here’s a remote-access VPN example: Suppose user Joey needs to access the Cisco network, so he launches a remote-access VPN. Joey’s computer is then evaluated for specific checks, such as making sure that antivirus and system software are running the latest versions and that certain applications are not installed. Also, multifactor authentication can be enforced using a password combined with a valid certificate before access is permitted. The access that is permitted might be on a specific VLAN that limits access to email and certain web resources. Figure 14-3 shows an example of the Cisco AnyConnect client providing a connection from Joey’s laptop to the remote location titled RTP.
Clientless VPN, also known as a secure portal, does not require software on the end device. This is typically accomplished by providing access to a portal that keeps services within the secured container and wipes the history of the session from the device once the session is terminated. Typically, the portal is opened when an authorized user accesses it using an Internet browser and then is later terminated once the user logs out of the portal or the web browser is closed. Administrators can provision and monitor specific access inside the container such as links to websites, provide a terminal to manage network devices, and so on. Clientless VPNs are common solutions for temporary access from unsecure devices such as a shared computer in a hotel or airport terminal. Figure 14-4 shows an example of setting up a Cisco clientless VPN portal.
An example of using a clientless VPN would be when user Joey wants to check his email from his friend’s computer. That computer is not considered a trusted system by Joey’s company policy, so a direct connection to the internal network is not permitted. A clientless portal is an alternative option Joey can access. This option requires authentication and a scan of the system he is on for specific items before access is permitted to specific resources. If Joey’s temporary untrusted computer passes the policy checks, he can access a secure portal that has a link to his Outlook email. Once Joey closes his Internet browser, a popup will inform him that his browser history will be erased and the secure session will be closed.
Secure Shell (SSH) encrypts traffic between a client and an SSH server. SSH was developed as a secure alternative to Telnet, because Telnet is vulnerable to man-in-the-middle attacks due to its lack of encryption. The most common use of SSH is protecting traffic between an administrator remotely accessing and administrating network device command-line terminals.
SSH uses public-key cryptography to authenticate the remote computer and permit it to authenticate the user. A number of cryptographic algorithms can be used to generate SSH keys, such as Rivest, Shamir, and Adelman (RSA), Digital Signature Algorithm (DSA), and Elliptic Curve Digital Signature Algorithm (ECDSA). Essentially, the components of an SSH system are the SSH server, clients, and keys. The industry TCP port used for SSH servers is 22. Many sources can be found online for learning more details about how to develop an SSH solution. Building an SSH solution, however, is out of scope for the SECFND exam.
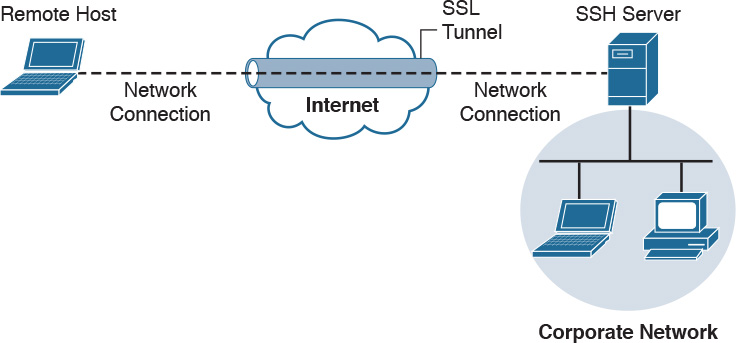
Attackers can use SSH to hide traffic, such as creating a reverse SSH tunnel from a breached system back to an external SSH server, hiding sensitive data as the traffic leaves the network. Figure 14-5 provides an example of how a typical SSH session functions.
There are many use cases where an attacker breaches a network and launches some form of a VPN session. An example is using Hak5’s LAN Turtle USB adaptor, which can be configured to auto-launch a reverse SSH tunnel to a cloud storage server, essentially creating a cloud-accessible back door to a victim’s network. Figure 14-6 shows a LAN Turtle plugged into a laptop.
It is challenging for an administrator to identify the LAN Turtle because it sits on a trusted system and does not require an IP address of its own to provide the reverse encrypted tunnel out of the network. Figure 14-7 shows an example of a LAN Turtle plugged into a server, providing an encrypted tunnel to an attacker’s remote server. This would represent a physical attack that leads to a back door for external malicious parties to access.
The LAN Turtle is just one example of the many tools available that can be planted on a network to create an unauthorized back door. The people at www.pwnieexpress.com develop various types of hacking tools designed to look like office items, such as power strips and printer plugs. Most of their tools offer various forms of encrypting access to the compromised network using LAN, wireless, and VPN technologies to accomplish the goal. The Pwnie Express team even offers a Raspberry Pi image, turning a Raspberry Pi into a remotely accessible penetration tool for under US$50. You can learn more at http://blog.pwnieexpress.com/post/24967860602/raspberry-pwn-a-pentesting-release-for-the.
Another encryption concept is hiding the actual data. There are many techniques for doing this, such as enterprise file encryption technologies that encrypt files and control access to opening them. An example is having a software agent installed on a server that specifies which files should be encrypted. When a file is removed that should be encrypted, it is tagged and encrypted, with access only provided to people within a specific authentication group. People within that group can use a host-based agent that auto-logs them in to the file, or they could be sent to an online portal to authenticate to gain access to the file.
The term data at rest means data that is placed on a storage medium. Data-at-rest security requirements typically refer to the ability to deny all access to stored data that is deemed sensitive and at risk of being exposed. Typically this is done by encrypting data and later removing all methods to unencrypt the data. Examples include hard disk encryption where a hard drive is encrypted, making it impossible to clone. The same concept can be applied to file encryption technology, where the data owner can expire access to the file, meaning all users won’t be able to unencrypt it.
Many attackers abuse encryption concepts such as file and protocol encryption to hide malicious code. An example would be an attack happening from a web server over SSL encryption to hide the attack from network intrusion detection technologies. This works because a network intrusion detection tool uses signatures to identify a threat, which is useless if the traffic being evaluated is encrypted. Another example would be encoding a malicious file with a bunch of pointless text, with the goal of confusing an antivirus application. Antivirus applications also use signatures to detect threats, so adding additional text to malicious code could possibly change the code enough to not be tied to a known attack when evaluated by a security tool.
Key Encryption and Tunneling Concepts
The list that follows highlights the key encryption and tunneling concepts:
![]() A VPN is used to hide or encode something so the content is protected from unwanted parties.
A VPN is used to hide or encode something so the content is protected from unwanted parties.
![]() Encryption traffic can be used to bypass detection, such as by an IPS.
Encryption traffic can be used to bypass detection, such as by an IPS.
![]() The two forms of remote-access VPN are client based and clientless.
The two forms of remote-access VPN are client based and clientless.
![]() A site-to-site VPN connects two or more networks.
A site-to-site VPN connects two or more networks.
![]() SSH connects a host to an SSH server and uses public-key cryptography to authenticate the remote computer and permit it to authenticate the user.
SSH connects a host to an SSH server and uses public-key cryptography to authenticate the remote computer and permit it to authenticate the user.
![]() File encryption technology protects files from unauthorized users.
File encryption technology protects files from unauthorized users.
Next, we will look at exhausting resources to bypass detection and gain unauthorized access to systems and networks.
Resource Exhaustion
Resource exhaustion is a type of denial-of-service attack; however, it can also be used to evade detection by security defenses. A simple definition of resource exhaustion is “consuming the resources necessary to perform an action.” For example, a service can be a website, such as one of the authors’ blog called www.thesecurityblogger.com. The server hosting this website can only provide services to a certain number of systems using digital communication, meaning the server will fail if too many systems access a specific resource at the same time. One denial-of-service attack tool that can exhaust the available resources of the server hosting such a website is called Slowloris, which can be found at http://chers.org/slowloris. This tool holds connections by sending partial HTTP requests to the website. The tool continues sending several hundred subsequent headers at regular intervals to keep sockets from closing, thus overwhelming the target’s resources. This causes the website to be caught up with existing requests, thus delaying responses to legitimate traffic. Figure 14-8 shows the Slowloris tool being used against the www.thesecurityblogger.com website.
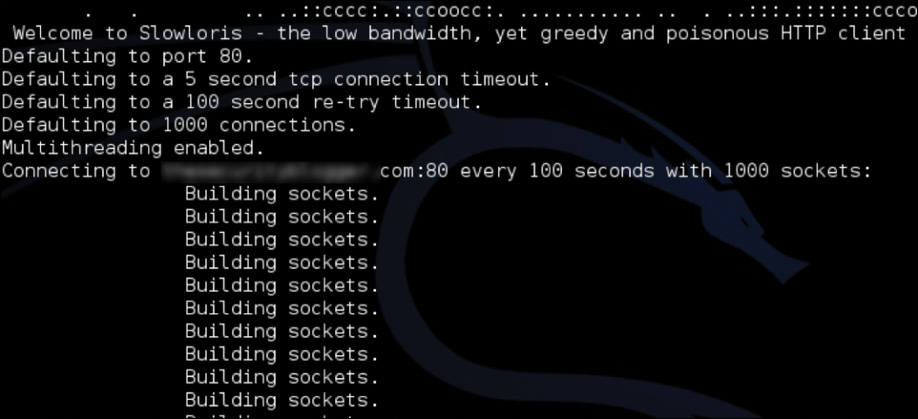
Figure 14-8 Slowloris attack against thesecurityblogger.com
When it comes to bypassing access-control security, resource exhaustion attacks can consume all processes to force a system to fail open, meaning to permit access to unauthorized systems and networks. This attack can be effective against access-control technologies that administrators typically configure to fail open if a service failure is detected. The same approach could be used to exhaust systems that have tracking capabilities, such as intrusion detection tools or other network sensors, causing a blackout period for an attacker to abuse without being recorded. Attackers will use resource exhaustion attacks against logging systems they identify during an attack, knowing many administrators do not have the skills or understanding to defend against resource exhaustion attacks and therefore will be unable to prevent the monitoring blackouts from occurring. This also prevents the evidence required for a forensic investigation from being collected, thus legally protecting the attacker from being incriminated by a future post-breach investigation. The most common example of a resource exhaustion attack involves sending a bunch of traffic directly at the IPS.
Defensive strategies should be implemented in order to prevent resource exhaustion attacks. The first defense layer, which involves having checks for unusual or unauthorized methods of requesting resources, is usually built in by the vendor. The idea is to recognize when an attack is being attempted and to deny the attacker further access for a specific amount of time so that the system resources can sustain the traffic without impacting service. One simple method to enforce this effect involves using throttling, which is limiting the amount of service a specific user or group can consume, thus enforcing an acceptable amount of resource consumption. Sometimes these features need to be enabled before they can be enforced, so best practice is to validate whether resource exhaustion defenses exist within a security solution.
The list that follows highlights the key resource exhaustion concepts:
![]() Resource exhaustion refers to consuming the resources necessary to perform an action.
Resource exhaustion refers to consuming the resources necessary to perform an action.
![]() Attackers use resource exhaustion to bypass access control and security detection capabilities. A common example is sending a ton of traffic at an IPS.
Attackers use resource exhaustion to bypass access control and security detection capabilities. A common example is sending a ton of traffic at an IPS.
![]() Resource exhaustion can be used to render logging unusable.
Resource exhaustion can be used to render logging unusable.
![]() Throttling is a method to prevent resource exhaustion by limiting the amount of processes that can be consumed at one time.
Throttling is a method to prevent resource exhaustion by limiting the amount of processes that can be consumed at one time.
Now let’s look at dicing up and modifying the traffic to bypass detection. This is known as traffic fragmentation.
Traffic Fragmentation
Network technologies expect traffic to move in a certain way. This is known as the TCP/IP suite. Understanding how this works can help you identify when something is operating in an unusual manner. Fragmenting traffic is a method of avoiding detection by breaking up a single Internet Protocol (IP) datagram into multiple, smaller-size packets. The goal is to abuse the fragmentation protocol within IP by creating a situation where the attacker’s intended traffic is ignored or let through as trusted traffic. The good news is that most modern intrusion detection systems (IDSs) and intrusion prevention systems (IPSs) are aware of this attack and can prevent it. Best practice is to verify that your version of IDS/IPS has traffic fragmentation detection capabilities.
IPS products should be able to properly reassemble packets to evaluate whether there is malicious intent. This includes understanding the proper order of the packets. Unfortunately, attackers have various techniques they can use to confuse an IPS solution during its reassembly process. An example of this involves using a TCP segmentation and reordering attack that is designed to confuse the detection tool by sending traffic in an uninspected method with the hope it can’t properly reassemble the traffic and identify it as being malicious. Security devices that can’t perform traffic reassembly will automatically fail to prevent this attack. Some security devices will fail when the attacker reorders or fragments the traffic with enough tweaks to accomplish the bypass.
Another example of a fragmentation attack involves using overlapping fragments. This attack works by setting the offset values in the IP header so that they do not match up, thus causing one fragment to overlap another. The confusion could cause the detection tool to ignore some traffic, letting malicious traffic slip through.
Best practice for avoiding traffic fragmentation attacks is verifying with your security solution provider that the solution is capable of detecting traffic fragmentation. Solutions that operate in full proxy type modes are not susceptible to this type of attack (for example, content filters and inline security devices).
The list that follows highlights the key traffic fragmentation concepts:
![]() Traffic fragmentation attacks modify the TCP/IP traffic in a way that is unexpected by security detection devices; the goal is to confuse the detection functions.
Traffic fragmentation attacks modify the TCP/IP traffic in a way that is unexpected by security detection devices; the goal is to confuse the detection functions.
![]() Using TCP segmentation and reordering attacks is one way to modify traffic to bypass detection.
Using TCP segmentation and reordering attacks is one way to modify traffic to bypass detection.
![]() Causing fragments to overlap by modifying IP headers is another type of traffic fragmentation attack.
Causing fragments to overlap by modifying IP headers is another type of traffic fragmentation attack.
![]() Proxies and in-line security devices can help prevent traffic fragmentation attacks.
Proxies and in-line security devices can help prevent traffic fragmentation attacks.
Like with TCP/IP traffic, protocols can also be modified to bypass security devices. Let’s look at how this works.
Protocol-Level Misinterpretation
A protocol is a set of rules or data structures that governs how computers or other network devices exchange information over a network. Protocols can be manipulated to confuse security devices from properly evaluating traffic since many devices and applications expect network communication to follow the industry-defined rules when a protocol is used. The key is understanding how the protocol should work and attempting to see if the developer of the receiving system defined defenses such as limitations on what is accepted, a method to validate what is received, and so on. The second key piece is identifying what happens when a receiving system encounters something it doesn’t understand (meaning seeing the outcome of a failure). A security device misinterpreting the end-to-end meaning of network protocols could cause traffic to be ignored, dropped, or delayed, all of which could be used to an attacker’s advantage.
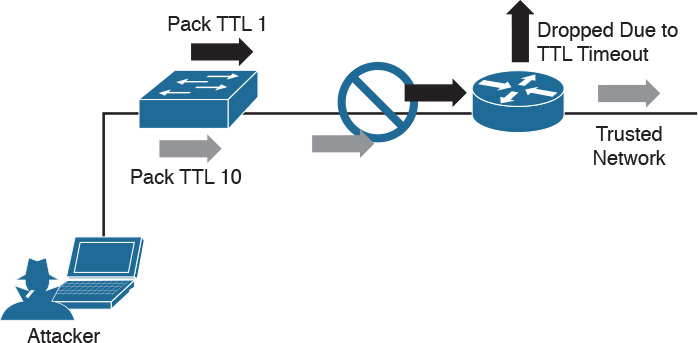
Another example of a protocol-level misinterpretation is abusing the “time to live” (TTL) of traffic. TTL is a protocol within a packet that limits the lifespan of data in a computer network. This prevents a data packet from circulating indefinitely. Abusing TTL works by first sending a short TTL value with the goal of passing the security receiver, assuming it will be dropped by a router later. This dropping occurs after the security device (meaning between the target and the security device) due to the TTL equaling a value of zero before the packet can reach its intended target. The attacker follows up the first packet with a TTL that has too high a value, with the goal of looking like duplicate traffic to the security device so that the security device will ignore it. By having the longer TTL, the packet will make it all the way to the host because now it has a high enough TTL value while being ignored by the network security solutions. Figure 14-9 shows an example of how this attack works. The first packet has a TTL value of 1, meaning it will hop past the security device but be dropped by the router due to having a value equal to 0. The second packet has a large enough TTL to make it to the host, yet if it’s the same data, the security device will assume it’s a duplicate, thus giving the attacker the ability to sneak in data.
Like with IP fragmentation attacks, the good news is that many security solutions are aware of this form of attack and have methods to validate and handle protocol manipulation. Best practice is to verify with your security solution providers whether their products are aware of protocol-level misinterpretation attacks.
The list that follows highlights the key protocol misinterpretation concepts:
![]() Protocols can be manipulated to confuse security devices from properly evaluating traffic.
Protocols can be manipulated to confuse security devices from properly evaluating traffic.
![]() TCP checksum and time-to-live protocols can be manipulated to first look like one thing and later to look like something else, with the goal of tricking the security defenses.
TCP checksum and time-to-live protocols can be manipulated to first look like one thing and later to look like something else, with the goal of tricking the security defenses.
Now let’s look at another evasion technique that takes a different approach to modifying network traffic.
Traffic Timing, Substitution, and Insertion
A traffic timing attack is when the attacker evades detection by performing his or her actions slower than normal while not exceeding thresholds inside the time windows the detection signatures use to correlate different packets together. A traffic timing attack can be mounted against any correlating engine that uses a fixed time window and a threshold to classify multiple packets into a composite event. An example of this attack would be sending packets at a slower rate than the detection system would be tuned to alarm to via sampling, making the attack unacceptably long in the eyes of the detection system.
A traffic substitution and insertion attack involves substituting the payload data with data in a different format but that has the same meaning, with the goal of it being ignored due to not being recognized by the security device. Some methods for changing the format include exchanging spaces with tabs, using Unicode instead of ASCII strings or characters in HTTP requests, modifying legitimate shell code with exploit code, and abusing case-sensitive communication. Most security devices can decode traffic; however, this attack is successful when a flaw is found in the decoding process. An example of a traffic substitution and insertion attack would be hiding malicious code by using Latin characters, knowing that the receiver will translate the code into ASCII. If this vulnerability exists, the security device will translate the text without verifying whether it is a threat, thus permitting the attack into the environment.
Defending against traffic timing attacks as well as substitution and insertion attacks once again requires features typically found in many security products offered by leading security vendors. Security features need to include the ability to adapt to changes in the timing of traffic patterns as well as changes in the format, to properly process extended characters, and to perform Unicode de-obfuscation. Unicode decoding examples include identifying ambiguous bits, double-encoding detection, and multidirectory delimiters. It is recommended that you verify with your trusted security solution provider whether your security solution has these detection capabilities.
The list that follows highlights the key traffic substitution and insertion concepts:
![]() Traffic timing attacks are when the attacker evades detection by performing his or her actions slower than normal while not exceeding thresholds inside the time windows the detection signatures use to correlate different packets together.
Traffic timing attacks are when the attacker evades detection by performing his or her actions slower than normal while not exceeding thresholds inside the time windows the detection signatures use to correlate different packets together.
![]() A traffic substitution and insertion attack substitutes the payload with data in a different format but that has the same meaning.
A traffic substitution and insertion attack substitutes the payload with data in a different format but that has the same meaning.
![]() Some methods to accomplish a traffic substitution and insertion attack include exchanging spaces with tabs, using Unicode instead of ASCII, and abusing case-sensitive communication.
Some methods to accomplish a traffic substitution and insertion attack include exchanging spaces with tabs, using Unicode instead of ASCII, and abusing case-sensitive communication.
![]() Security products can stop this type of attack by being able to adapt to format changes, properly processing extended characters, and providing Unicode de-obfuscation.
Security products can stop this type of attack by being able to adapt to format changes, properly processing extended characters, and providing Unicode de-obfuscation.
One final evasion technique we will cover is pivoting inside a network.
Pivoting
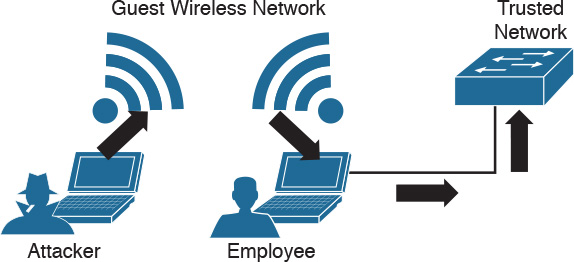
Although cyber attacks can vary in nature, one common step in the attack process, according to the “kill chain” concept first introduced by Lockheed Martin, is the idea of establishing a foothold in the target network and attempting to pivot to a more trusted area of the network. Establishing a foothold means breaching the network through exploiting a vulnerability and creating access points into the compromised network. The challenge for the attacker is the level of access granted with the exploit. For example, breaching a guest system on a network would typically mean gaining access to a guest network that is granted very limited access to network resources. An attacker would want to pivot from the guest network to another network with more access rights, such as the employee network. In regards to the kill chain, a pivot would be an action taken to start the sequence over once the attacker reached the “action” point. As illustrated in Figure 14-10, the attacker would first perform reconnaissance on other systems on the same network as the compromised system, weaponize an attack, and eventually move through the attack kill chain with the goal of gaining command and control abilities on other systems with greater network access rights.
Usually privileges and available resources on a network are grouped together into silos; this is known as network segmentation. Access to each network segment is typically enforced through some means of network access control. Figure 14-11 demonstrates the concept of segmentation and access control, where printers, guests, and a trusted network are on different network segments.
Pivoting, also known as island hopping, means to attack other systems on the same network. The idea is to identify a system with higher level access rights, such as administrator. This is also known as a form of privilege escalation. Identifying other systems with different levels of network access privileges can also be used to provide more doorways into the network in the event the original breach is closed, to identify systems to leverage for another form or attack, to hide data by using multiple systems as exit points from the network, and so on. It is also important to understand that privilege escalation can occur within a system. This involves breaching a server with a guest account and then later obtaining root access in order to provide more resource rights on that system. Figure 14-12 shows an attacker pivoting through a vulnerable system sitting on a trusted network. This could be accomplished by identifying a vulnerability on the employee’s laptop, placing a remote-access tool (RAT) on it, and then remotely connecting to the system to use it to surf inside the trusted network. The pivot is when the threat actor first gains access to the employee computer and “pivots” from that system to another system on the same network to gain further access to the target network.
There are different methods for pivoting across a network. The first involves using the existing network connections and ports available on the compromised system, essentially turning that system into a proxy pivot point. Although this provides some access, the attacker would be limited to the available TCP and UDP ports on the compromised system. A second approach that provides full access is setting up a VPN connection from the compromised system to the trusted network, giving the attacker full access by having all ports available from the attacker’s system to the point of VPN termination.
Figure 14-13 shows an example of using a system connected to two networks as a pivot point for a remote attack. I have found that many organizations are vulnerable to this type of attack during assessments, meaning their host systems aren’t disabling wireless connections made to a network through a device’s Ethernet port.
Defending against pivoting can be addressed a few ways. The first method is to enforce proper network access control and segmentation by limiting what can access specific network segments and filtering access to only what is required to operate the business within those segments. This approach limits the available systems an attacker can pivot to as well as what new network services would become available by breaching other systems on the same network. For example, if all printers are limited to a specific network segment and one printer is breached, the attacker could only attack other printers and access printer-related traffic. We find pivoting occurs when a poor security architecture is implemented, such as putting all devices on the same network segment and not validating what can plug into a network. There are many penetration-testing stories about organizations that forgot about an older, vulnerable system sitting on the same network as the administrators and critical servers.
Cisco Identity Services Engine (ISE) is the Cisco flagship identity management and policy enforcement solution designed for address pivoting risks. An example is providing an employee named Julie limited access to specific resources due to her device being an iPhone, which doesn’t require the same access as her laptop. Figure 14-14 represents how ISE would identify user Julie and limit her access to only specific resources. Different access would be provisioned to her printer, laptop, and desk phone, depending on each device’s posture status and how the administrators configured the ISE solution. This is just one of the many ways ISE dramatically simplifies enforcing segmentation through a centralized policy.
Another defense strategy is to provide proper endpoint security practices such as patch management, antivirus, breach detection technologies, and so on. Typically systems are breached though a vulnerability, where a payload such as a remote-access tool (RAT) is delivered to give access to an unwanted remote party. Preventing the breach stops the attacker from having access to the network.
NetFlow security products such as Cisco Stealthwatch can be used to identify unusual traffic, giving you a “canary in the coalmine” defense. An example of this concept in regard to Stealthwatch would be an attacker compromising an employee’s system and using it to pivot into the network. If Julie is in the sales department and she starts scanning the network and accessing critical systems for the first time, it probably means something bad is happening, regardless of whether she is authorized to do so. Although NetFlow might not be able to tell you why the situation is bad at first, it can quickly alarm you that something bad is happening so that you can start to investigate the situation—just like miners would do when they noticed the canary had died in the coalmine.
NetFlow security doesn’t require a lot of storage, is supported by most vendors, and can be enabled on most device types (routers, switches, wireless apps, virtual switching traffic, data center traffic, and so on). It essentially turns the entire network into a security sensor grid. Figure 14-15 shows the Cisco Stealthwatch dashboard for various internal threats, including suspicious systems that might be infected with malware based on how they are scanning other systems (perhaps to identify new systems to infect).
The list that follows highlights the key pivot concepts:
![]() Pivoting in terms of cyber attacks (also known as island hopping) means to attack other systems on the same network with the goal of gaining accessing to that system.
Pivoting in terms of cyber attacks (also known as island hopping) means to attack other systems on the same network with the goal of gaining accessing to that system.
![]() Best practice is to have networks segmented and to control access between each segment.
Best practice is to have networks segmented and to control access between each segment.
![]() A common goal for a pivot attack is to escalate the attacker’s privileges. This is commonly accomplished by jumping from one system to another system with greater network privileges.
A common goal for a pivot attack is to escalate the attacker’s privileges. This is commonly accomplished by jumping from one system to another system with greater network privileges.
![]() Defending against pivoting can be accomplished by providing proper access control, network segmentation, DNS security, reputation security, and proper patch management.
Defending against pivoting can be accomplished by providing proper access control, network segmentation, DNS security, reputation security, and proper patch management.
![]() NetFlow is a great sensor-based tool for detecting unauthorized pivoting occurring within the network.
NetFlow is a great sensor-based tool for detecting unauthorized pivoting occurring within the network.
Exam Preparation Tasks
Review All Key Topics
Review the most important topics in the chapter, noted with the Key Topic icon in the outer margin of the page. Table 14-2 lists these key topics and the page numbers on which each is found.
Complete Tables and Lists from Memory
Print a copy of Appendix B, “Memory Tables,” (found on the book website), or at least the section for this chapter, and complete the tables and lists from memory. Appendix C, “Memory Tables Answer Key,” also on the website, includes completed tables and lists to check your work.
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
traffic timing attack
resource exhaustion attack
traffic fragmentation attack
protocol misinterpretation attack
traffic substitution and insertion attack
Q&A
The answers to these questions appear in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Q&A Questions.” For more practice with exam format questions, use the exam engine on the website.
1. What is SSH used for?
a. Remote access
b. To provide a client-based VPN solution for remote users
c. Managing network equipment remotely
d. Preventing man-in-the-middle attacks by securing traffic between the client and server
2. Which of the following is a true statement?
a. A remote access VPN must include a host installed on the client.
b. A clientless VPN can connect multiple concentrators together.
c. A remote access VPN may include a host installed on the client.
d. A clientless VPN installs software on the host to establish the VPN connection.
3. Which of the following is not a possible outcome of a resource exhaustion attack?
a. Corrupting applications by modifying their code
b. A denial of server on the target system
c. Bypassing access control security
d. Causing blackouts in network monitoring
4. Which of the following is not a technique used to confuse an IPS from assembling fragmenting packets?
a. Encrypting traffic
b. TCP segmentation and reordering attack
c. Overlapping fragments
d. Sending traffic in very slow method
5. Which of the following is the best explanation of an overlapping fragment attack?
a. This attack works by setting the offset values in the IP header to match up, causing one fragment to overlap another.
b. This attack works by setting the TCP values in the IP header to not match up, causing one fragment to overlap another.
c. This attack works by setting the UDP values in the IP header to match up, causing one fragment to overlap another.
d. This attack works by setting the offset values in the IP header to not match up, causing one fragment to overlap another.
6. Which of the following best describes a timing attack?
a. Sending a ton of traffic to render the system or data useless
b. Sending traffic in a method that is slower than the system can accept
c. Sending traffic slowly enough where the system can accept it but overlooks it
d. Sending the traffic over different protocols
7. Which of the following is an example of a traffic substitution and insertion attack?
a. Inputting more characters than requested
b. Using functions and classes
c. Changing spaces with tabs
d. Inputting wildcard characters
8. Which of the following is not a method used to pivot a network?
a. Exploiting a host on the same network
b. Creating a back door to the network
c. VLAN hopping
d. Exploiting a network server
9. Which is the best answer to explain why Cisco Identity Services Engine would reduce the risk of pivoting to a higher, trusted network?
a. ISE ensures systems have the latest antivirus updates prior to permitting access to the network.
b. ISE can unify and enforce the LAN, wireless, and VPN access control policies into one secure policy.
c. ISE can profile devices, providing greater detail on which ones can access what resources.
d. ISE enforces network segmentation.
10. Which of the following statements is not true about SSH?
a. SSH uses TCP port 22.
b. SSH is composed of an SSH server, clients, and keys.
c. SSH uses asymmetric encryption.
d. SSH encrypts traffic between a client and an SSH server.
References and Further Reading
informationassurance.regis.edu/ia-programs/resources/blog/cybersecurity-pivot