Appendix: Self Test
Chapter 2: Domain 1: Security and Risk Management
1. Which of the following would be an example of a policy statement?
A. Protect PII by hardening servers
B. Harden Windows 7 by first installing the pre-hardened OS image
C. You may create a strong password by choosing the first letter of each word in a sentence and mixing in numbers and symbols
D. Download the CISecurity Windows benchmark and apply it
Correct Answer and Explanation: A. Answer A is correct; policy is high level and avoids technology specifics.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. B is a procedural statement. C is a guideline. D is a baseline.
2. Which of the following describes the money saved by implementing a security control?
A. Total Cost of Ownership
B. Asset Value
C. Return on Investment
D. Control Savings
Correct Answer and Explanation: C. Answer C is correct; Return on Investment (ROI) is the amount of money saved by protecting an asset with a security control.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. Total Cost of Ownership is the cost of implementing a security control. Asset Value is the value of the protected asset. Control Savings is a distracter answer that describes ROI without using the proper term.
3. Which of the following is an example of program policy?
A. Establish the information security program
B. Email Policy
C. Application development policy
D. Server policy
Correct Answer and Explanation: A. Answer A is correct; the program policy establishes the information security program.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. Email policy and application development policy are issue-specific policies. Server policy is system-specific policy.
4. Which of the following proves an identity claim?
A. Authentication
B. Authorization
C. Accountability
D. Auditing
Correct Answer and Explanation: A. Answer A is correct; authentication proves an identity claim.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. Authorization describes the actions a subject is allowed to take. Accountability holds users accountable by providing audit data. Auditing verifies compliance with an information security framework.
5. Which of the following protects against unauthorized changes to data?
A. Confidentiality
B. Integrity
C. Availability
D. Alteration
Correct Answer and Explanation: B. Answer B is correct; integrity protects against unauthorized changes to data.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. Confidentiality protects against unauthorized disclosure of data. Availability means systems are available for normal business use. Alteration is unauthorized changes to data: the opposite of integrity.
Use the following scenario to answer questions 6–8:
Your company sells Apple iPods online and has suffered many denial of service (DoS) attacks. Your company makes an average $20,000 profit per week, and a typical DoS attack lowers sales by 40%. You suffer seven DoS attacks on average per year. A DoS-mitigation service is available for a subscription fee of $10,000 per month. You have tested this service, and believe it will mitigate the attacks.
6. What is the Annual Rate of Occurrence in the above scenario?
A. $20,000
B. 40%
C. 7
D. $10,000
Correct Answer and Explanation: C. Answer C is correct; the Annual Rate of Occurrence is the number of attacks in a year.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. $20,000 is the Asset value (AV). Forty percent is the Exposure Factor (EF). $10,000 is the monthly cost of the DoS service (used to calculate TCO).
7. What is the annualized loss expectancy (ALE) of lost iPod sales due to the DoS attacks?
A. $20,000
B. $8000
C. $84,000
D. $56,000
Correct Answer and Explanation: D. Answer D is correct; Annualized Loss Expectancy (ALE) is calculated by first calculating the Single Loss Expectancy (SLE), which is the Asset Value (AV, $20,000) times the Exposure Factor (EF, 40%). The SLE is $8000; multiply by the Annual rate of Occurrence (ARO, 7) for an ALE of $56,000.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. $20,000 is the Asset Value. $8000 is the Single Loss Expectancy.
8. Is the DoS mitigation service a good investment?
A. Yes, it will pay for itself
B. Yes, $10,000 is less than the $56,000 Annualized Loss Expectancy
C. No, the annual Total Cost of Ownership is higher than the Annualized Loss Expectancy
D. No, the annual Total Cost of Ownership is lower than the Annualized Loss Expectancy
Correct Answer and Explanation: C. Answer C is correct; the Total Cost of Ownership (TCO) of the DoS mitigation service is higher than Annualized Loss Expectancy (ALE) of lost sales due to DoS attacks. This means it’s less expensive to accept the risk of DoS attacks (or find a less expensive mitigation strategy).
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. A is incorrect: the TCO is higher, not lower. $10,000 is the monthly TCO; you must calculate yearly TCO to compare with the ALE. D is wrong: the annual TCO is higher, not lower.
9. Which of the following steps would be taken while conducting a Qualitative Risk Analysis?
A. Calculate the Asset Value
B. Calculate the Return on Investment
C. Complete the Risk Analysis Matrix
D. Complete the Annualized Loss Expectancy
Correct Answer and Explanation: C. Answer C is correct; the Risk Analysis Matrix uses approximate values, from 1 through 5 to qualitatively analyze risks according to likelihood and consequences.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. All are quantitative Risk Analysis steps.
10. What is the difference between a standard and a guideline?
A. Standards are compulsory and guidelines are mandatory
B. Standards are recommendations and guidelines are requirements
C. Standards are requirements and guidelines are recommendations
D. Standards are recommendations and guidelines are optional
Correct Answer and Explanation: C. Answer C is correct; Standards are requirements (mandatory) and guidelines are recommendations.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. For A, Guidelines are recommendations (compulsory and mandatory are synonyms). Answer B has the recommendations and requirements flipped. For D, standards are mandatory, not recommendations.
11. An attacker sees a building is protected by security guards, and attacks a building next door with no guards. What control combination are the security guards?
A. Physical/Compensating
B. Physical/Detective
C. Physical/Deterrent
D. Physical/Preventive
Correct Answer and Explanation: C. Answer C is correct; the guards deterred the attack.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. In a different scenario a guard could be any of these, but all are incorrect given the question. Compensating controls compensate for a weakness in another control. Detective controls detect a successful attack during or after it has occurred. Preventive controls prevent successful attacks.
12. Which canon of The (ISC)2® Code of Ethics should be considered the most important?
A. Protect society, the commonwealth, and the infrastructure
B. Advance and protect the profession
C. Act honorably, honestly, justly, responsibly, and legally
D. Provide diligent and competent service to principals
Correct Answer and Explanation: A. Answer A is correct; to protect society, the commonwealth, and the infrastructure is the first canon, and is thus the most important of the four canons of The (ISC)2® Code of Ethics
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. The canons of The (ISC)2® Code of Ethics are presented in order of importance. The second canon requires the security professional to act honorably, honestly, justly, responsibly, and legally. The third mandates that professionals provide diligent and competent service to principals. The final, and therefore least important canon, wants professionals to advance and protect the profession.
13. Which doctrine would likely allow for duplication of copyrighted material for research purposes without the consent of the copyright holder?
A. First sale
B. Fair use
C. First privilege
D. Free dilution
Correct Answer and Explanation: B. Answer B is correct; fair use limits the rights of the copyright holder by making some exceptions to the copyright holder’s exclusive monopoly on the intellectual property in question. There is no explicit rule as to how much material can be duplicated and still constitute fair use.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. First sale allows a legitimate purchaser of copyrighted material the right to sell the material to another party. First privilege and free dilution are both made up terms.
14. Which type of intellectual property is focused on maintaining brand recognition?
A. Patent
B. Trade Secrets
C. Copyright
D. Trademark
Correct Answer and Explanation: D. Answer D is correct; trademarks are intended to allow an organization to create a recognizable brand associated with the company’s goods or services.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. Patents are associated with inventions. Trade secrets are those materials that an organization protects in order to maintain their competitive stance in the marketplace. Copyright covers the form of expression in creative works.
15. Drag and drop: Identify all objects listed below. Drag and drop all objects from left to right.
Correct Answer and Explanation: Files, database tables and tax forms are example of objects, so they should be dragged to the right.
Incorrect Answers and Explanations: A running process and a user are examples of subjects.

Figure SelfTest.1 Drag and Drop

Figure SelfTest.2 Drag and Drop Answer
Chapter 3: Domain 2: Asset Security
1. What type of memory is used often for CPU registers?
A. DRAM
B. Firmware
C. ROM
D. SRAM
Correct Answer and Explanation: D. Answer D is correct; SRAM (Static Random Access Memory is fast and expensive, often used for cache memory including CPU registers).
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. DRAM is slower and less expensive than SRAM, often used as main RAM. Firmware is a technology used by PLDs such as EEPROMs. Read-Only Memory is a type of Firmware, providing nonvolatile memory for uses such as the BIOS.
2. What type of firmware is erased via ultraviolet light?
A. EPROM
B. EEPROM
C. Flash memory
D. PROM
Correct Answer and Explanation: A. Answer A is correct; EPROM (Erasable Programmable Read Only Memory) is erased by exposure to ultraviolet light.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. EEPROMs (Electrically Erasable Programmable Read Only Memory) are erased electronically, via flashing programs. Flash memory is a type of EEPROM, also erased electronically. PROM (Programmable Read Only Memory) cannot be erased.
3. What describes the process of determining which portions of a standard will be employed by an organization?
A. Baselines
B. Policies
C. Scoping
D. Tailoring
Correct Answer and Explanation: C. Answer C is correct; scoping is the process of determining which portions of a standard will be employed by an organization.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. Baselines are uniform ways to implement a safeguard, administrative control. Policies are high-level management directives. Tailoring is the process of customizing a standard for an organization.
4. What nonvolatile memory normally stores the operating system kernel on an IBM PC-compatible system?
A. Disk
B. Firmware
C. RAM
D. ROM
Correct Answer and Explanation: A. Answer A is correct; the kernel is stored on disk, and is loaded into volatile memory by the BIOS.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. ROM (including firmware) is nonvolatile memory that stores the BIOS. RAM is volatile memory that holds the kernel after the system has booted.
5. What was ISO 17799 renamed as?
A. BS 7799-1
B. ISO 27000
C. ISO 27001
D. ISO 27002
Correct Answer and Explanation: D. Answer D is correct; ISO 17799 was renamed as ISO 27002.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. BS 7799-1 was the precursor to ISO 17799. ISO 27000 is a series of information security standards documents. ISO 27001 is another ISO 27000-series document designed to support auditing.
6. Which of the following describes a duty of the Data Owner?
A. Patch systems
B. Report suspicious activity
C. Ensure their files are backed up
D. Ensure data has proper security labels
Correct Answer and Explanation: D. Answer D is correct; the Data Owner ensures that data has proper security labels.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. Custodians patch systems. Users should be aware and report suspicious activity. Ensuring files are backed up is a weaker answer for a Data Owner duty, used to confuse the Data Owner with “the owner of the file” on a discretionary access control system.
7. Which control framework has 34 processes across four domains?
A. COSO
B. COBIT
C. ITIL
D. OCTAVE
Correct Answer and Explanation: B. Answer B is correct; COBIT has 34 Information Technology processes across the four domains.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. All are audit or control frameworks, but only COBIT has 34 processes across four domains.
8. Which phase of OCTAVE identifies vulnerabilities and evaluates safeguards?
A. Phase 1
B. Phase 2
C. Phase 3
D. Phase 4
Correct Answer and Explanation: B. Answer B is correct; Phase 2 identifies vulnerabilities and evaluates safeguards.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. Phase 1 identifies staff knowledge, assets, and threats. Phase 3 conducts the Risk Analysis and develops the risk mitigation strategy. There is no Phase 4 in OCTAVE.
9. Which of the following is the best method for securely removing data from a Solid State Drive that is not physically damaged?
A. ATA secure erase
B. Bit-level overwrite
C. Degaussing
D. File shredding
Correct Answer and Explanation: A. Answer A is correct; ATA Secure erase will reliably remove data from an undamaged Solid State Drive (SSD).
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. A bit-level overwrite will not reliably destroy all data on a Solid State Drive. Degaussing has no effect on non-magnetic media. File shredding (overwriting a file’s contents before deleting) will also not reliably destroy all data on a Solid State Drive.
10. The release of what type of classified data could lead to “exceptionally grave damage to the national security”?
A. Confidential
B. Secret
C. Sensitive but Unclassified (SBU)
D. Top Secret
Correct Answer and Explanation: D. Answer D is correct; the release of top secret data could lead to “exceptionally grave damage to the national security.”
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. The release of confidential data could lead to “damage to the national security.” The release of secret data could lead to “serious damage to the national security.” The release of SBU data is not a matter of national security, but is important for other reasons, including protecting individual’s PII.
11. A company outsources payroll services to a 3rd party company. Which of the following roles most likely applies to the 3rd party payroll company?
A. Data controller
B. Data hander
C. Data owner
D. Data processor
Correct Answer and Explanation: D. Answer D is correct; a 3rd party payroll company is an example of a data processor.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. A data controller is someone who creates PII, such as an HR department. “Data handler” is not a formal term, and is a distractor answer. A data owner is a management employee responsible for assuring that specific data is protected.
12. Which managerial role is responsible for the actual computers that house data, including the security of hardware and software configurations?
A. Custodian
B. Data owner
C. Mission owner
D. System owner
Correct Answer and Explanation: D. Answer D is correct; a system owner is responsible for the actual computers that house data, including the security of hardware and software configurations.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. A custodian is a non-manager who provides hands-on protection of assets. A data owner is a management employee responsible for assuring that specific data is protected. A mission owner is a member of senior management who create the information security program and ensure that it is properly staffed, funded, and has organizational priority.
13. What method destroys the integrity of magnetic media such as tapes or disk drives by exposing them to a strong magnetic field, destroying the integrity of the media and the data it contains?
A. Bit-level overwrite
B. Degaussing
C. Destruction
D. Shredding
Correct Answer and Explanation: B. Answer B is correct; degaussing destroys the integrity of magnetic media such as tapes or disk drives by exposing them to a strong magnetic field, destroying the integrity of the media and the data it contains.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. A bit-level overwrite removes data by overwriting every sector of a disk. Destruction physically destroys data, for example via incineration. Shredding electronic data involves overwriting a file’s contents before deleting the file.
14. What type of relatively expensive and fast memory uses small latches called “flip-flops” to store bits?
A. DRAM
B. EPROM
C. SRAM
D. SSD
Correct Answer and Explanation: C. Answer C is correct; SRAM is relatively expensive and fast memory uses small latches called “flip-flops” to store bits.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. DRAM is relatively inexpensive memory that uses capacitors. EPROM is Erasable Programmable Read Only Memory, memory which may be erased with ultraviolet light. SSD is a Solid State Drive, a combination of DRAM and EEPROM.
15. What type of memory stores bits in small capacitors (like small batteries)?
A. DRAM
B. EPROM
C. SRAM
D. SSD
Correct Answer and Explanation: A. Answer A is correct; DRAM stores bits in small capacitors (like small batteries).
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. EPROM is Erasable Programmable Read Only Memory, memory which may be erased with ultraviolet light. SRAM is relatively expensive and fast memory uses small latches called “flip-flops” to store bits. SSD is a Solid State Drive, a combination of DRAM and EEPROM.
Chapter 4: Domain 3: Security Engineering
1. What type of sprinkler system would be best for an art gallery?
A. Wet pipe
B. Dry pipe
C. Deluge
D. Pre-action
Correct Answer and Explanation: D. Answer D is correct; pre-action sprinkler systems lower the chance of accidental discharge by requiring two separate triggers to deploy: the sprinkler head must open and the fire alarm must trigger. These systems lower the risk of false alarms, typically used in areas where water would cause expensive damage.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect; all release water after a single trigger. This increases the chance of a false alarm causing expensive damage.
2. What is the primary drawback to using dogs as a perimeter control?
A. Training
B. Cost
C. Liability
D. Appearance
Correct Answer and Explanation: C. Answer C is correct; liability is the primary drawback to using dogs as a security control. Dogs may mistakenly attack a person who accidentally enters a controlled area.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect; they are all potentially valid issues, but are lesser concerns than liability and safety.
3. The RSA algorithm is based on which one-way function?
A. Elliptic curves
B. Discrete logarithm
C. Frequency distribution
D. Factoring composite numbers into their primes
Correct Answer and Explanation: D. Answer D is correct; RSA is based on the difficulty of factoring large composite numbers into their primes.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. Elliptic curve and discrete logarithms are other types of one-way functions. Frequency distribution is a way to perform cryptanalysis.
4. Which of the following is true for digital signatures?
A. The sender encrypts the hash with a public key
B. The sender encrypts the hash with a private key
C. The sender encrypts the plaintext with a public key
D. The sender encrypts the plaintext with a private key
Correct Answer and Explanation: B. Answer B is correct; the sender generates a hash of the plaintext and encrypts the hash with a private key. The recipient decrypts the hash with a public key.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. The sender encrypts the hash with the private key, not public. The plaintext is hashed, and not encrypted.
5. Which algorithm should you use for a low-power device that must employ digital signatures?
A. AES
B. RSA
C. ECC
D. ElGamal
Correct Answer and Explanation: C. Answer C is correct; digital signatures require asymmetric encryption. ECC is the strongest asymmetric algorithm per bit of key length. This allows shorter key lengths that require less CPU resources.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. AES is a symmetric cipher; symmetric ciphers are not used in digital signatures. RSA is based on factoring composite numbers into their primes, and ElGamal is based on discrete logarithms. Both methods provide roughly the same strength per bit and are far weaker per bit than ECC.
6. What model should you use if you are primarily concerned with confidentiality of information?
A. Bell-LaPadula
B. Biba
C. Clark-Wilson
D. Confidentiality Model
Correct Answer and Explanation: A. Answer A is correct; the Bell-LaPadula model protects confidentiality of data.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. Biba and Clark-Wilson are integrity models. There is no “Confidentiality Model.”
7. On Intel ×86 systems, the kernel normally runs in which CPU ring?
A. Ring 0
B. Ring 1
C. Ring 2
D. Ring 3
Correct Answer and Explanation: A. Answer A is correct; the kernel normally runs in ring 0, the most trusted part of the system.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. Ring 1 is theoretically used for parts of the OS that do not fit in ring 0. Ring 2 is theoretically used for device drivers. Ring 3 is used for user applications.
8. Which type of cloud service level would Linux hosting be offered under?
A. IaaS
B. IDaaS
C. PaaS
D. SaaS
Correct Answer and Explanation: A. Answer A is correct; IaaS (Infrastructure as a Service) provides an entire virtualized operating system, which the customer configures from the OS on up.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. IDaaS (Identity as a Service) is also called cloud identity, allows organizations to leverage cloud service for identity management. PaaS (Platform as a Service) provides a pre-configured operating system, and the customer configures the applications. SaaS (Software as a Service) is completely configured, from the operating system to applications, and the customer simply uses the application.
9. You are surfing the Web via a wireless network. Your wireless connection becomes unreliable, so you plug into a wired network to continue surfing. While you changed physical networks, your browser required no change. What security feature allows this?
A. Abstraction
B. Hardware Segmentation
C. Layering
D. Process Isolation
Correct Answer and Explanation: C. Answer C is correct; Layering means a change in one layer (hardware) has no direct effect on a nonadjacent layer (application).
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. Abstraction hides unnecessary details from the user, which is related to (but different) from layering. Hardware segmentation provides dedicated hardware or portions of hardware to specific security domains. Process isolation prevents one process from affecting the confidentiality, integrity or availability of another.
10. A criminal deduces that an organization is holding an offsite meeting and has few people in the building, based on the low traffic volume to and from the parking lot, and uses the opportunity to break into the building to steal laptops. What type of attack has been launched?
A. Aggregation
B. Emanations
C. Inference
D. Maintenance Hook
Correct Answer and Explanation: C. Answer C is correct; Inference requires an attacker to “fill in the blanks,” and deduce sensitive information from public information.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. Aggregation is a mathematical operation where all questions are asked and all answers are received: there is no deduction required. Emanations are energy broadcast from electronic equipment. Maintenance Hooks are system maintenance backdoors left by vendors.
11. EMI issues such as crosstalk primarily impact which aspect of security?
A. Confidentiality
B. Integrity
C. Availability
D. Authentication
Correct Answer and Explanation: B. Answer B is correct; while EMI issues such as crosstalk could impact all aspects listed, it most commonly impacts integrity.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect; confidentiality can be impacted (such as hearing another conversation on a voice phone call), and in extreme cases availability and authentication could be impacted (where crosstalk is so severe as to stop systems from functioning). These scenarios are far less common than simple integrity violation caused by EMI issues such as crosstalk.
12. What is the most important goal of fire suppression systems?
A. Preservation of critical data
B. Safety of personnel
C. Building integrity
D. Quickly extinguishing a fire
Correct Answer and Explanation: B. Answer B is correct; personnel safety is the paramount concern of the physical (environmental) security domain.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect; all are valid concerns, but less important than safety. Data protection is always a secondary concern to safety; this is why water is the recommended fire extinguishing agent. Building integrity and quickly extinguishing the fire are also important and impact safety, but safety itself is the goal, and thus a stronger answer. The integrity of an empty building is a lesser concern, for example, and while the speed of extinguishing a fire is important, the safety of personnel who must evacuate is a more important concern. The fastest way to extinguish a fire is to starve it of oxygen, which would be deadly to people.
13. What type of network cable should be used to eliminate the chance of crosstalk?
A. Shielded twisted pair
B. Unshielded twisted pair
C. Coaxial
D. Fiber optic
Correct Answer and Explanation: D. Answer D is correct; fiber optic cable uses light instead of electricity and is not subject to electro-magnetic interference (EMI) issues such as crosstalk.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. Unshielded twisted pair is susceptible to EMI when improperly routed. Shielded twisted pair and coaxial cable are better choices for avoiding crosstalk, but they still carry electricity, and could have EMI issues under certain circumstances.
14. Nonrepudiation is best described as what?
A. Proving a user performed a transaction
B. Proving a transaction did not change
C. Authenticating a transaction
D. Proving a user performed a transaction that did not change
Correct Answer and Explanation: D. Answer D is correct; nonrepudiation is proof that a user performed a transaction and proof that it did not change.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. Proving a transaction did not change is one half of nonrepudiation; proving a user performed a transaction is the other half. Nonrepudiation requires both. Authenticating a transaction is another way of saying a user performed the transaction, and is also one half of nonrepudiation.
15. Hotspot: you receive the following signed email from Roy Batty. You determine that the email is not authentic, or has changed since it was sent. Click on the locally-generated message digest that proves the email lacks non-repudiation.
Correct Answer and Explanation: The output of a hash algorithm such as SHA-1 is called a message digest. The message digest on the top right of the diagram below is the locally-generated hash that does not match the original hash received by decrypting the digital signature with the creator’s public key.
Incorrect Answers and Explanations: the other clickable areas of the hotspot are not locally-generated hashes that proves the email lacks non-repudiation.
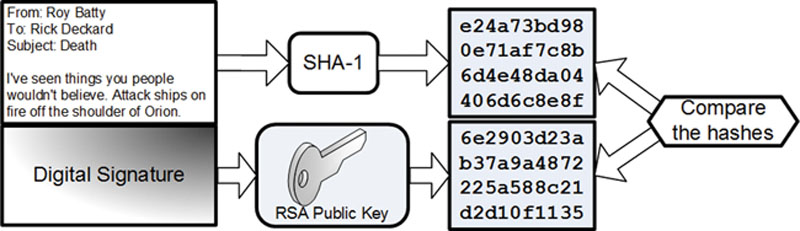
Figure SelfTest.3 Hotspot

Figure SelfTest.4 Hotspot Answer
Chapter 5: Domain 4: Communication and Network Security
1. Which protocol should be used for an audio streaming server, where some loss is acceptable?
A. IP
B. ICMP
C. TCP
D. UDP
Correct Answer and Explanation: D. Answer D is correct; UDP is used for high-speed applications that can handle some loss.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. IP is a carrier protocol, which would require a higher-layer protocol such as UDP to support an application. ICMP is a helper protocol, and does not carry application data. TCP is a reliable and slow protocol, not the best choice when speed is required, and loss is OK.
2. What network technology uses fixed-length cells to carry data?
A. ARCNET
B. ATM
C. Ethernet
D. FDDI
Correct Answer and Explanation: B. Answer B is correct; ATM is a networking technology that uses 53 byte fixed-length cells.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. ARCNET passes tokens. Ethernet uses frames. FDDI also uses tokens.
3. Secure Shell (SSH) servers listen on what port and protocol?
A. TCP port 20
B. TCP port 21
C. TCP port 22
D. TCP port 23
Correct Answer and Explanation: C. Answer C is correct; SSH servers listen on TCP port 22.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. FTP uses TCP ports 20 and 21. Telnet uses TCP port 23.
4. What network cable type can transmit the most data at the longest distance?
A. Coaxial
B. Fiber Optic
C. Shielded Twisted Pair (STP)
D. Unshielded Twisted Pair (UTP)
Correct Answer and Explanation: B. Answer B is correct; Fiber Optic Network Cable can transmit the most data the furthest.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. Among the four answers, STP and UTP can transmit the shortest distance. Coaxial network cable can transmit more data further than twisted pair cabling, but not nearly as far as fiber.
5. Which device operates at Layer 2 of the OSI model?
A. Hub
B. Firewall
C. Switch
D. Router
Correct Answer and Explanation: C. Answer C is correct; A switch operates at layer 2 (data link layer) of the OSI model.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. A hub operates at layer 1 (physical). Packet filter and stateful firewalls operate at layers 3 and 4, Circuit-Level Proxies (such as SOCKS) operate up to layer 5 (session), and application-layer proxies operate up to layer 7 (application). Routers operate at layer 3 (network).
6. What are the names of the OSI model, in order from bottom to top?
A. Physical, Data Link, Transport, Network, Session, Presentation, Application
B. Physical, Network, Data Link, Transport, Session, Presentation, Application
C. Physical, Data Link, Network, Transport, Session, Presentation, Application
D. Physical, Data Link, Network, Transport, Presentation, Session, Application
Correct Answer and Explanation: C. Answer C is correct; The OSI model from bottom to top is: Physical, Data Link, Network, Transport, Session, Presentation, and Application. Remember “Please Do Not Throw Sausage Pizza Away” as a useful mnemonic to remember this.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. All are in the wrong order.
7. Which of the following authentication protocols uses a 3-way authentication handshake?
A. CHAP
B. EAP
C. Kerberos
D. PAP
Correct Answer and Explanation: A. Answer A is correct; CHAP (Challenge Handshake Authentication Protocol) uses a 3-way authentication handshake.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. EAP is the Extensible Authentication Protocol, an authentication framework describing multiple authentication methods. Kerberos is a Single Sign On system that uses tickets. PAP is the Password Authentication Protocol, which is simpler (and has less steps) than CHAP.
8. Restricting Bluetooth device discovery relies on the secrecy of what?
A. MAC Address
B. Symmetric key
C. Private Key
D. Public Key
Correct Answer and Explanation: A. Answer A is correct; Restricting Bluetooth device discovery relies on the secrecy of the 48-bit Bluetooth MAC address.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. While E0 is a symmetric cipher, it is not used to restrict discovery (it is used to encrypt data). Public or Private keys are also not used for Bluetooth Discovery.
9. Which wireless security protocol is also known as the RSN (Robust Security Network), and implements the full 802.11i standard?
A. AES
B. WEP
C. WPA
D. WPA2
Correct Answer and Explanation: D. Answer D is correct; WPA2 (Wi-Fi Protected Access 2) implements AES and CCMP (Counter Mode CBC MAC Protocol), as defined by 802.11i.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. AES is part of WPA2, which also includes CCMP, so it is a weaker answer than WPA2. WEP is Wired Equivalent Privacy, and older and insecure security protocol that should no longer be used. WPA is less secure than WPA2, using RC4 and TKIP.
10. Which endpoint security technique is the most likely to prevent a previously unknown attack from being successful?
A. Signature-based antivirus
B. Host Intrusion Detection Systems (HIDS)
C. Application Whitelisting
D. Perimeter firewall
Correct Answer and Explanation: C. Answer C is correct: Application Whitelisting is the most likely to be successful of the options listed.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are all incorrect. Signature-based antivirus is most successful at preventing known rather than unknown attacks. Host Intrusion Detection Systems (HIDS) do not prevent attacks from being successful, but rather can help detect them. A perimeter firewall is not an endpoint security product.
11. Which transmission mode is supported by both HDLC and SDLC?
A. Asynchronous Balanced Mode (ABM)
B. Asynchronous Response Mode (ARM)
C. Normal Balanced Mode (NBM)
D. Normal Response Mode (NRM)
Correct Answer and Explanation: D. Answer D is correct; both HDLC and SDLC support Normal Response Mode (NRM), where secondary nodes can transmit when given permission by the primary.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. HDLC supports Asynchronous Balanced Mode (ABM) and Asynchronous Response Mode (ARM), while SDLC does not. There is no such mode as Normal Balanced Mode (NBM).
12. What is the most secure type of EAP?
A. EAP-TLS
B. EAP-TTLS
C. LEAP
D. PEAP
Correct Answer and Explanation: A. Answer A is correct; EAP-TLS is the most secure (and costly) form of EAP because it requires both server and client-side certificates.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. EAP-TTLS and PEAP are similar and don’t require client-side certificates. LEAP is a Cisco-proprietary protocol that does not require client-side certificates, and also has fundamental security weaknesses.
13. What WAN Protocol has no error recovery, relying on higher-level protocols to provide reliability?
A. ATM
B. Frame Relay
C. SMDS
D. X.25
Correct Answer and Explanation: B. Answer B is correct; Frame Relay is a packet switched Layer 2 WAN protocol that features no error recovery.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. ATM and SMDS are cell-based WAN protocols that provide error correction. X.25 is a packet switched protocol similar to Frame Relay, but X.25 features error recovery.
14. What is the most secure type of firewall?
A. Packet Filter
B. Stateful Firewall
C. Circuit-level Proxy Firewall
D. Application-layer Proxy Firewall
Correct Answer and Explanation: D. Answer D is correct; application-layer firewalls are the most secure: they have the ability to filter based on OSI layers three through seven.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. All are firewalls. A packet filter is the least secure of the four, due to the lack of state. A stateful firewall is more secure than a packet filter, but its decisions are limited to layers 3 and 4. Circuit-level proxy firewalls operate at layer 5, and cannot filter based on application-layer data.
15. Accessing an IPv6 network via an IPv4 network is called what?
A. CIDR
B. NAT
C. Translation
D. Tunneling
Correct Answer and Explanation: D. Answer D is correct; accessing an IPv6 network via an IPv4 network is called tunneling.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. CIDR is Classless Inter-domain Routing, a way to create flexible subnets. NAT is Network Address Translation, which translates one IP address for another. Translation is a distracter answer.
Chapter 6: Domain 5: Identity and Access Management
1. What type of password cracking attack will always be successful?
A. Brute Force
B. Dictionary
C. Hybrid
D. Rainbow Table
Correct Answer and Explanation: A. Answer A is correct; brute force attacks are always successful, given enough time.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. Dictionary attacks will only crack passwords that exist in a dictionary or word list. Hybrid attacks append, prepend, or alter characters in words from a dictionary. A rainbow table uses pre-computed hashes. Not all rainbow tables are complete, and rainbow tables are less effective against salted hashes.
2. What is the difference between password cracking and password guessing?
A. They are the same
B. Password guessing attempts to log into the system; password cracking attempts to determine a password used to create a hash
C. Password guessing uses salts; password cracking does not
D. Password cracking risks account lockout, password guessing does not
Correct Answer and Explanation: B. Answer B is correct; password cracking relies on cracking the hash of a password; password guessing attempts to log into a system.
Incorrect Answers and Explanations: A, C, and D. A is incorrect: Password guessing is not the same as password cracking. C is incorrect because salts are a password cracking issue, not a password guessing issue. D is incorrect: password guessing risks account lockout.
3. Two users on the same system have the same password, but different hashes are stored in the /etc/shadow file. What is the most likely reason the hashes are different?
A. The usernames are different, so the hashes will be different
B. Use of multiple hashing algorithms
C. Use of rainbow tables
D. Use of salts
Correct Answer and Explanation: D. Answer D is correct; a salt is a random number that is hashed along with the user’s password, making it highly unlikely that two users with the same password would also have the same hash.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. Different usernames will have no impact on password hashes on most systems. The use of multiple hashing algorithms on the same system is possible, but unlikely. Rainbow tables are not used to create hashes; they act as database that contains the hashed output for most or all possible passwords.
4. What authentication method exposes the password in clear text?
A. CHAP
B. Kerberos
C. PAP
D. SESAME
Correct Answer and Explanation: C. Answer C is correct; the Password Authentication Protocol (PAP) exposes the password in plaintext on the network.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. CHAP, Kerberos and SESAME do not expose the clear text password.
5. What are the main differences between retina scans and iris scans?
A. Retina scans are not invasive and iris scans are
B. Iris scans invade a person’s privacy and retina scans do not
C. Iris scans change depending on the person’s health, retina scans are stable
D. Retina scans change depending on the person’s health, iris scans are stable
Correct Answer and Explanation: D. D is the correct answer because the blood vessels in the retina may change depending on certain health conditions.
Incorrect Answers and Explanations: A, B, and C. A is incorrect because Retina scans are invasive—they can relay user health information. B is incorrect because Iris scans are not invasive. C is incorrect because Iris scans remain (comparatively) stable regarding the general health of the user attempting access.
6. What is the most important decision an organization needs to make when implementing Role Based Access Control (RBAC)?
A. Each user’s security clearance needs to be finalized
B. The roles users have on the system needs to be clearly defined
C. Users’ data needs to be clearly labeled
D. Users must be segregated from one another on the IT system to prevent spillage of sensitive data
Correct Answer and Explanation: B. B is the correct answer because in Role Based Access Control (RBAC), users’ roles must be clearly defined so access to data based upon those roles can be limited according to organization policy.
Incorrect Answers and Explanations: A, C, and D. Answer A is incorrect because in RBAC user’s clearances are not considered. Answer C is incorrect because MAC labels every object and compares it to a subject’s clearance, not RBAC. Answer D is incorrect because in RBAC users are not segregated from one another.
7. What access control method weighs additional factors such as time of attempted access before granting access?
A. Content-dependent access control
B. Context-dependent access control
C. Role-based access control
D. Task-based access control
Correct Answer and Explanation: B. Answer B is correct; Context-dependent access control adds additional factors beyond username and password, such as the time of attempted access.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. Content-dependent access control uses the content (such as file contents) as an additional factor. Role-based control is based on the subject’s role. Task-based access control is based on the tasks the subject needs to perform.
8. What service is known as cloud identity, and allows organizations to leverage cloud service for identity management?
A. IaaS
B. IDaaS
C. PaaS
D. SaaS
Correct Answer and Explanation: B. Answer B is correct; Identity as a Service, also called cloud identity, allows organizations to leverage cloud service for identity management.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. IaaS (Infrastructure as a Service) provides an entire virtualized operating system, which the customer configures from the OS on up. PaaS (Platform as a Service) provides a pre-configured operating system, and the customer configures the applications. SaaS (Software as a Service) is completely configured, from the operating system to applications, and the customer simply uses the application.
9. A type II biometric is also known as what?
A. Crossover Error Rate (CER)
B. Equal Error Rate (EER)
C. False Accept Rate (FAR)
D. False Reject Rate (FRR)
Correct Answer and Explanation: C. Answer C is correct; the False Accept Rate (FAR) is known as a type II error. Remember that false accepts are normally worse than false rejects, and II is greater than I.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. The Crossover Error Rate (CER) and Equal Error Rate (EER) are synonyms used to gauge the accuracy of a biometric system. A False Reject Rate (FRR) is a type I error.
10. Within Kerberos, which part is the single point of failure?
A. The Ticket Granting Ticket
B. The Realm
C. The Key Distribution Center
D. The Client-Server session key
Correct Answer and Explanation: C. C is the correct answer because the KDC is the only service within Kerberos that can authenticate subjects. If the KDC loses availability, then ticket granting tickets will not be issued and no new authentications may take place.
Incorrect Answers and Explanations: A, B, and D. A is incorrect because the TGT is received by the subject from the KDC. B is incorrect because the realm is a Kerberos network that shares authentication. D is incorrect because new C-S session keys can be issued.
11. What is an XML-based framework for exchanging security information, including authentication data?
A. Kerberos
B. OpenID
C. SAML
D. SESAME
Correct Answer and Explanation: C. Answer C is correct; SAML is an XML-based framework for exchanging security information, including authentication data.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. Kerberos is a third-party authentication service that may be used to support Single Sign On. OpenID is a framework for exchanging authentication data, but is not XML-based. SESAME stands for Secure European System for Applications in a Multi-vendor Environment, a single sign-on system that supports heterogeneous environments
12. What protocol provides a common open protocol for interfacing and querying directory service information provided by network operating systems, using port 389 via TCP or UDP?
A. CHAP
B. LDAP
C. PAP
D. RADIUS
Correct Answer and Explanation: B. Answer B is correct; Lightweight Directory Access Protocol, an open protocol for interfacing and querying directory service information provided by network operating systems, using port 389 via TCP or UDP.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. CHAP, PAP and RADIUS do not provide directory service information provided by network operating systems, using port 389 via TCP or UDP.
13. Server A trusts server B. Server B trusts Server C. Server A therefore trusts server C. What term describes this trust relationship?
A. Domain trust
B. Forest trust
C. Nontransitive trust
D. Transitive Trust
Correct Answer and Explanation: D. D is the correct answer. Transitive trusts exist between two partners and all of their partners. For example: if A trusts B, in a transitive trust, A will trust B and all of B’s trust partners.
Incorrect Answers and Explanations: A, B, and C. Domain and Forest trust are less-specific terms that are not required to be transitive. Nontransitive trust is the opposite of transitive trust.
14. A policy that states a user must have a business requirement to view data before attempting to do so is an example of enforcing what?
A. Least privilege
B. Need to know
C. Rotation of duties
D. Separation of duties
Correct Answer and Explanation: B. Answer B is correct; need to know means the user must have a need (requirement) to access a specific object before doing so.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. Least privilege is less granular than need to know: users have the least amount of privilege to do their jobs, but objects are still typically grouped together (such as allowing access to all backup tapes for a backup administrator). Separation of duties is designed to divide sensitive tasks among multiple subjects. Rotation of duties is designed to mitigate collusion.
15. What technique would raise the False Accept Rate (FAR) and Lower the False Reject Rate (FRR) in a fingerprint scanning system?
A. Decrease the amount of minutiae that is verified
B. Increase the amount of minutiae that is verified
C. Lengthen the enrollment time
D. Lower the throughput time
Correct Answer and Explanation: A. Answer A is correct; decreasing the amount of minutiae will make the accuracy of the system lower, which lower false rejects but raise false accepts.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. Increasing the amount of minutiae will make the system more accurate, increasing the FRR and lowering the FAR. Enrollment and throughput time are not directly connected to FAR and FRR.
Chapter 7: Domain 6: Security Assessment and Testing
1. Which software testing level tests software after updates, modifications or patches?
A. Acceptance Testing
B. Integration Testing
C. Regression Testing
D. Unit Testing
Correct Answer and Explanation: C. Answer C is correct; Regression Testing tests software after updates, modifications or patches.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. Acceptance Testing tests software to ensure the software meets the customer’s operational requirements. Integration Testing tests multiple software components as they are combined into a working system. Unit Testing tests low-level software components, such as functions, procedures or objects.
2. What type of testing enters random malformed data as inputs into software programs to determine if they will crash?
A. Black box testing
B. Combinatorial testing
C. Fuzzing
D. Pairwise testing
Correct Answer and Explanation: C. Answer C is correct; Fuzzing is a form of black box software testing that enters random malformed data as inputs into software programs to determine if they will crash.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. Black box testing gives the tester no internal details: the software is treated as a black box that receives inputs. Fuzzing is a form of black box testing and is more specific, so it is a better answer. Combinatorial software testing is a black box testing method that seeks to identify and test all unique combinations of software inputs. Pairwise testing is a form of combinatorial testing that identifies unique pairs of inputs.
3. What type of software testing tests code passively?
A. Black box testing
B. Dynamic testing
C. Static testing
D. White box testing
Correct Answer and Explanation: C. Answer C is correct; static testing tests code passively. This includes walkthroughs, syntax checking and code reviews.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. Black box testing gives the tester no internal details: the software is treated as a black box that receives inputs. Dynamic testing tests the code while executing it. White box software testing gives the tester access to program source code, data structures, variables, etc.
4. What type of penetration test begins with no external or trusted information, and begins the attack with public information only?
A. Full knowledge
B. Partial knowledge
C. Grey box
D. Zero knowledge
Correct Answer and Explanation: D. Answer D is correct; A zero knowledge test begins with no external or trusted information, and begins the attack with public information only.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. A full-knowledge test (also called crystal-box) provides internal information to the penetration tester, including network diagrams, policies and procedures, and sometimes reports from previous penetration testers. Grey box is not a valid term on the exam. Partial-knowledge tests are in between zero and full knowledge: the penetration tester receives some limited trusted information.
5. What type of assessment would best demonstrate an organization’s compliance with PCI-DSS (Payment Card Industry Data Security Standard)?
A. Audit
B. Penetration test
C. Security assessment
D. Vulnerability assessment
Correct Answer and Explanation: A. Answer A is correct; an audit is used to verify compliance with a published specification.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. A penetration test is designed to determine if an attacker can penetrate an organization. A security assessment is a holistic approach to assessing the effectiveness of access control. A vulnerability assessment is designed to discover poor configurations and missing patches in an environment.
6. What type of test provides internal information to the penetration tester, including network diagrams, policies and procedures, and sometimes reports from previous penetration testers?
A. Full knowledge
B. Partial knowledge
C. Grey box
D. Zero knowledge
Correct Answer and Explanation: A. Answer A is correct; A full-knowledge test provides internal information to the penetration tester, including network diagrams, policies and procedures, and sometimes reports from previous penetration testers.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. Partial-knowledge tests are in between zero and full knowledge: the penetration tester receives some limited trusted information. Grey box is not a valid term on the exam. A zero knowledge test begins with no external or trusted information, and begins the attack with public information only.
7. What can be used to ensure software meets the customer’s operational requirements?
A. Integration testing
B. Installation testing
C. Acceptance testing
D. Unit testing
Correct Answer and Explanation: C. Answer C is correct; acceptance testing is designed to ensure the software meets the customer’s operational requirements.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. Integration testing tests multiple software components as they are combined into a working system. Installation testing tests software as it is installed and first operated. Unit Testing is a low-level test of software components, such as functions, procedures or objects.
8. What term describes a no-tech or low-tech method that uses the human mind to bypass security controls?
A. Fuzzing
B. Social engineering
C. War dialing
D. Zero knowledge test
Correct Answer and Explanation: B. Answer B is correct; social engineering is a no-tech or low-tech method that uses the human mind to bypass security controls.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. Fuzzing is a type of black box testing that enters random malformed data as inputs into software programs to determine if they will crash. War dialing uses modems to dial a series of phone numbers, looking for an answering modem carrier tone. A zero knowledge penetration test begins with no external or trusted information, and begins the attack with public information only.
9. What term describes a black-box testing method that seeks to identify and test all unique combinations of software inputs?
A. Combinatorial software testing
B. Dynamic testing
C. Misuse case testing
D. Static Testing
Correct Answer and Explanation: A. Answer A is correct; Combinatorial software testing is a black-box testing method that seeks to identify and test all unique combinations of software inputs.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. Dynamic testing tests code while executing it. Misuse case testing formally models how security impact could be realized by an adversary abusing the application. Static testing tests the code passively; the code is not running. This includes walkthroughs, syntax checking, and code reviews.
10. What term describes a holistic approach for determining the effectiveness of access control, and has a broad scope?
A. Security assessment
B. Security audit
C. Penetration test
D. Vulnerability assessment
Correct Answer and Explanation: A. Answer A is correct; A security assessment is a holistic approach for determining the effectiveness of access control, and has a broad scope.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. A security audit verifies compliance with an information security framework or standard. A penetration test is designed to determine if an attacker can penetrate an organization. A vulnerability assessment is designed to discover poor configurations and missing patches in an environment.
Use the following scenario to answer questions 11 through 14:
You are the CISO of a large bank and have hired a company to provide an overall security assessment, and also provide a penetration test of your organization. Your goal is to determine overall information security effectiveness. You are specifically interested in determining if theft of financial data is possible.
Your bank has recently deployed a custom-developed three-tier web application that allows customers to check balances, make transfers, and deposit checks by taking a photo with their smartphone and then uploading the check image. In addition to a traditional browser interface, your company has developed a smartphone app for both Apple iOS and Android devices.
The contract has been signed, and both scope and rules of engagement have been agreed upon. A 24/7 operational IT contact at the bank has been made available in case of any unexpected developments during the penetration test, including potential accidental disruption of services.
11. Assuming the penetration test is successful: what is the best way for the penetration testing firm to demonstrate the risk of theft of financial data?
A. Instruct the penetration testing team to conduct a thorough vulnerability assessment of the server containing financial data
B. Instruct the penetration testing team to download financial data, redact it, and report accordingly
C. Instruct the penetration testing team that they may only download financial data via an encrypted and authenticated channel
D. Place a harmless ‘flag’ file in the same location as the financial data, and inform the penetration testing team to download the flag
Correct Answer and Explanation: D. Answer D is correct; A flag is a dummy file containing no regulated or sensitive data, placed in the same area of the system as the credit card data, and protected with the same permissions. If the tester can read and/or write to that file, then they prove they could have done the same to the credit card data.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. Answer A is a vulnerability assessment, not a penetration test. Answers B and C are dangerous, and could involve unauthorized access of regulated data, such as health care records.
12. What type of penetration test will result in the most efficient use of time and hourly consultant expenses?
A. Automated knowledge
B. Full knowledge
C. Partial Knowledge
D. Zero Knowledge
Correct Answer and Explanation: B. Answer B is correct; a full knowledge test is far more efficient than other forms of penetration tests, allowing the penetration tester to find weaker areas more quickly.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. Automated knowledge is not a valid exam term. Both zero and partial knowledge tests will be less efficient than full knowledge.
13. You would like to have the security firm test the new web application, but have decided not to share the underlying source code. What type of test could be used to help determine the security of the custom web application?
A. Secure compiler warnings
B. Fuzzing
C. Static testing
D. White box testing
Correct Answer and Explanation: B. Answer B is correct; Fuzzing is a black box testing method that does not require access to source code.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. All are static methods that require access to source code.
14. During the course of the penetration test: the testers discover signs of an active compromise of the new custom-developed three-tier web application. What is their best source of action?
A. Attempt to contain and eradicate the malicious activity
B. Continue the test
C. Quietly end the test, immediately call the operational IT contact, and escalate the issue
D. Shut the server down
Correct Answer and Explanation: C. Answer C is correct; attackers will often become more malicious if they believe they have been discovered, sometimes violating data and system integrity. The integrity of the system is at risk in this case, and the penetration tester should end the penetration test, and immediately escalate the issue.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. The client must be notified immediately, and incident handling is not the penetration tester’s responsibility.
15. Drag and drop: Which of the following statements about Syslog are true? Drag and drop all correct answers from left to right.
Correct Answer and Explanation: Syslog uses UDP, which offers unreliable transport, so the data is easily spoofed. The data is also not encrypted.
Incorrect Answers and Explanations: Syslog does not use TCP, is not encrypted, and uses no authentication.
Figure SelfTest.5 Drag and Drop
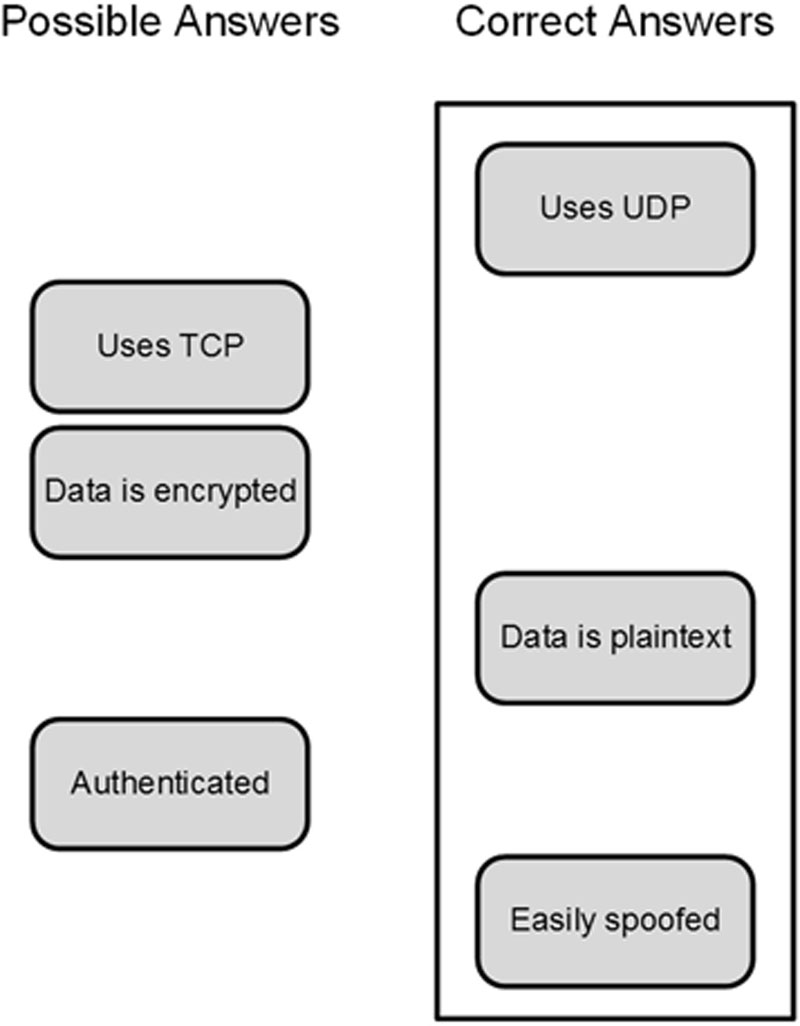
Figure SelfTest.6 Drag and Drop Answer
Chapter 8: Domain 7: Security Operations
1. What type of backup is obtained during the Response (aka Containment) phase of Incident Response?
A. Incremental
B. Full
C. Differential
D. Binary
Correct Answer and Explanation: D. Answer D is correct; binary, or bit by bit, backups are what is obtained during the containment phase of incident response. Strong preference is also for a forensically sound binary backup that leverages a hashing algorithm to convey reliability. The other types of backups will not capture unallocated space, and could cause the analyst to miss some data that had been marked for deletion.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. Incremental, Full, and Differential are all common backup techniques, but will only backup allocated space rather than the full drive. These techniques are used for simple backup/restore capabilities rather than incident response or forensics.
2. What is the primary goal of disaster recovery planning (DRP)?
A. Integrity of data
B. Preservation of business capital
C. Restoration of business processes
D. Safety of personnel
Correct Answer and Explanation: D. Answer D is correct; Loss of human life is the highest impact of any risk; personnel safety is the primary concern of all 8 domains, including the business continuity and disaster recovery planning section of the Security Operations domain.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. All are valid concerns, but none trump personnel safety.
3. What business process can be used to determine the outer bound of a Maximum Tolerable Downtime?
A. Accounts receivable
B. Invoicing
C. Payroll
D. Shipment of goods
Correct Answer and Explanation: C. Answer C is correct; Most organizations should not allow unmanaged risk of two missed payrolls: if a company pays every 2 weeks, the maximum MTD would be 2 weeks. This is used to determine the outer bound; most organizations will determine a far lower MTD (sometimes in days, hours, or less).
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. All are valid concerns, but the risk of being unable to pay personnel for two consecutive pay periods carries higher risk.
4. Your Maximum Tolerable Downtime is 48 hours. What is the most cost-effective alternate site choice?
A. Cold
B. Hot
C. Redundant
D. Warm
Correct Answer and Explanation: D. Answer D is correct; A warm site is a data center with raised floor, power, utilities, computer peripherals, and fully configured computers; requiring 24–72 hours to become fully operational.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. A cold site has basic physical and environmental controls, but no computer systems. It normally takes a week or more to make fully operational. A hot site is a data center with a raised floor, power, utilities, computer peripherals, and fully configured computers. A hot site takes hours to become fully operational, and is the second-most expensive option. A redundant site is an exact production duplicate of a system that has the capability to seamlessly operate all necessary IT operations, and is the most expensive option.
5. A structured walkthrough test is also known as what kind of test?
A. Checklist
B. Simulation
C. Tabletop Exercise
D. Walkthrough Drill
Correct Answer and Explanation: C. Answer C is correct; a structured walkthrough is also known as a tabletop exercise.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. Checklist testing checks a list of all assets and processes required to recover from a disaster. Both Simulation and Walkthrough Drill recover from a simulated mock emergency.
6. Which type of backup will include only those files that have changed since the most recent Full backup?
A. Full
B. Differential
C. Incremental
D. Binary
Correct Answer and Explanation: B. Answer B is correct; differential backups will only archive those files that have changed since the most recent full backup.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. A full backup would archive all files regardless of whether they had changed or not. An incremental backup will only archive those files that have changed since the last incremental or full backup. Binary backups are used for forensics and incident response purposes and will backup everything on the entire disk, both allocated and unallocated space.
7. Which type of tape backup requires a maximum of two tapes to perform a restoration?
A. Differential backup
B. Electronic vaulting
C. Full backup
D. Incremental backup
Correct Answer and Explanation: A. Answer A is correct; Differential backups archive data that has changed since the last full backup. During restoration, at most only the last full and differential tapes are required.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. Electronic vaulting is a batch process that does not use tape. Full backups archive all data: only one tape is required to restore a full backup. Incremental Backups backup all data that has changed since the last full or incremental backup. Depending on the timing of the restoration, multiple incremental tapes may be required in addition to the most recent full backup.
8. What statement regarding the Business Continuity Plan is true?
A. BCP and DRP are separate, equal plans
B. BCP is an overarching “umbrella” plan that includes other focused plans such as DRP
C. DRP is an overarching “umbrella” plan that includes other focused plans such as BCP
D. COOP is an overarching “umbrella” plan that includes other focused plans such as BCP
Correct Answer and Explanation: B. Answer B is correct; The Business Continuity Plan is an umbrella plan that includes multiple specific plans, most importantly the Disaster Recovery Plan.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. All incorrectly state that BCP is equal to, or a subset of other plans.
9. Which HA solution involves multiple systems all of which are online and actively processing traffic or data?
A. Active-active cluster
B. Active-passive cluster
C. Database shadowing
D. Remote journaling
Correct Answer and Explanation: A. Answer A is correct; an active-active cluster involves multiple systems all of which are online and actively processing traffic or data. This configuration is also commonly referred to as load balancing, and is especially common with public facing systems such as Web server farms.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. An active-passive involves devices or systems that are already in place, configured, powered on and ready to begin processing network traffic should a failure occur on the primary system. Database shadowing uses two or more identical databases that are updated simultaneously. Remote journaling saves the database checkpoints and database journal to a remote site. In the event of failure at the primary site, the database may be recovered.
10. What plan is designed to provide effective coordination among the managers of the organization in the event of an emergency or disruptive event?
A. Call tree
B. Continuity of Support Plan
C. Crisis Management Plan
D. Crisis Communications Plan
Correct Answer and Explanation: C. Answer C is correct; the Crisis Management Plan (CMP) is designed to provide effective coordination among the managers of the organization in the event of an emergency or disruptive event.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. The call tree works by assigning each employee a small number of other employees that are responsible for calling in an emergency event. The Continuity of Support Plan focuses narrowly on support of specific IT systems and applications. Crisis Communications Plan (sometimes simply called the communications plan); a plan for communicating to staff and the public in the event of a disruptive event. This plan is a subset of the CMP.
11. Which plan details the steps required to restore normal business operations after recovering from a disruptive event?
A. Business Continuity Planning (BCP)
B. Business Resumption Planning (BRP)
C. Continuity of Operations Plan (COOP)
D. Occupant Emergency Plan (OEP)
Correct Answer and Explanation: B. Answer B is correct; Business Resumption Planning details the steps required to restore normal business operations after recovering from a disruptive event.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. Business Continuity Planning develops a long-term plan to ensure the continuity of business operations. The Continuity of Operations Plan describes the procedures required to maintain operations during a disaster. The Occupant Emergency Plan provides the response procedures for occupants of a facility in the event a situation poses a threat to the health and safety of personnel, the environment, or property.
12. What metric describes how long it will take to recover a failed system?
A. Minimum Operating Requirements (MOR)
B. Mean Time Between Failures (MTBF)
C. The Mean Time to Repair (MTTR)
D. Recovery Point Objective (RPO)
Correct Answer and Explanation: C. Answer C is correct; The Mean Time to Repair (MTTR) describes how long it will take to recover a failed system. It is the best estimate for reconstituting the IT system so that business continuity may occur.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. Minimum Operating Requirements describes the minimum environmental and connectivity requirements in order to operate computer equipment. Mean Time Between Failures quantifies how long a new or repaired system will run before failing. The Recovery Point Objective (RPO) is the moment in time in which data must be recovered and made available to users in order to resume business operations.
13. What metric describes the moment in time in which data must be recovered and made available to users in order to resume business operations?
A. Mean Time Between Failures (MTBF)
B. The Mean Time to Repair (MTTR)
C. Recovery Point Objective (RPO)
D. Recovery Time Objective (RTO)
Correct Answer and Explanation: C. Answer C is correct; The Recovery Point Objective (RPO) is the moment in time in which data must be recovered and made available to users in order to resume business operations.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. Mean Time Between Failures quantifies how long a new or repaired system will run before failing. Mean Time to Repair describes how long it will take to recover a failed system. Recovery Time Objective describes the maximum time allowed to recover business or IT systems.
14. Maximum Tolerable Downtime (MTD) is comprised of which two metrics?
A. Recovery Point Objective (RPO) and Work Recovery Time (WRT)
B. Recovery Point Objective (RPO) and Mean Time to Repair (MTTR)
C. Recovery Time Objective (RTO) and Work Recovery Time (WRT)
D. Recovery Time Objective (RTO) and Mean Time to Repair (MTTR)
Correct Answer and Explanation: C. Answer C is correct; The Recovery Time Objective (RTO, the time it takes to bring a failed system back online) and Work Recovery Time (WRT, the time required to configure a failed system) are used to calculate the Maximum Tolerable Downtime. RTO + WRT = MTD.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. Maximum Tolerable Downtime does not directly use Recovery Point Objective or Mean Time to Repair as metrics.
15. Which level of RAID does NOT provide additionally reliability?
A. RAID 1
B. RAID 5
C. RAID 0
D. RAID 3
Correct Answer and Explanation: C. Answer C is correct; RAID 0 provides only striping, and is used simply for performance purposes. It offers no additional data redundancy or resiliency.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. RAIDs 1, 3, and 5 all provide reliability gains through either mirroring or parity measures.
Chapter 9: Domain 8: Software Development Security
1. What software design methodology uses paired programmers?
A. Agile
B. Extreme Programming (XP)
C. Sashimi
D. Scrum
Correct Answer and Explanation: B. Answer B is correct; Extreme Programming (XP) is an Agile development method that uses pairs of programmers who work off a detailed specification. There is a high level of customer involvement.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. Agile describes numerous development methodologies, including XP: XP is a better answer because it is more specific. Sashimi is a Waterfall Model variant. Scrum is a different Agile methodology that uses small teams.
2. What form of Artificial Intelligence uses a knowledge base and an inference engine?
A. Artificial Neural Network (ANN)
B. Bayesian Filtering
C. Expert System
D. Genetic Algorithm
Correct Answer and Explanation: C. Answer C is correct; an expert system is comprised of two components: a knowledge base that consists of “if/then” statements. These statements contain rules that the expert system uses to make decisions. The second component is an inference engine.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. Artificial Neural Networks (ANN) simulate neural networks found in humans and animals. Bayesian filtering uses mathematical formulas to assign probabilities to make decisions such as identifying spam. Genetic Algorithms and Programming fundamentally change the way software is developed: instead of being coded by a programmer, they evolve to solve a problem.
3. Which of the following definitions describe open source software?
A. Freeware
B. Gnu Public License (GPL) software
C. Public domain software
D. Software released with source code
Correct Answer and Explanation: D. Answer D is correct; open source software has publicly released source code.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. Freeware is software that is free of charge, whether source code is available or not. Software licensed with the GPL is free (libre), but not all open source software is licensed under the GPL. The same is true for public domain software.
4. What describes a more agile development and support model, where developers directly support operations?
A. DevOps
B. Sashimi
C. Spiral
D. Waterfall
Correct Answer and Explanation: A. Answer A is correct; DevOps is a more agile development and support model, where developers directly support operations.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. Sashimi, Spiral and Waterfall are software development methodologies that do not describe a model for developers directly supporting operations.
5. At what phase of the Systems Development Life Cycle (SDLC) should security become part of the process?
A. Before initiation
B. During development/acquisition
C. When the system is implemented
D. SDLC does not include a security process
Correct Answer and Explanation: A. Answer A is correct; Security is a critical component of the entire SDLC process, typically beginning with a security plan before initiation.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. Security is the first step of the SDLC, and is part of every phase of the SDLC.
6. An object acts differently, depending on the context of the input message. What Object-Oriented Programming concept does this illustrate?
A. Delegation
B. Inheritance
C. Polyinstantiation
D. Polymorphism
Correct Answer and Explanation: D. Answer D is correct; polymorphism (based on the Greek roots “poly” and “morph,” meaning many and forms, respectively): allows the ability to overload operators, performing different methods depending on the context of the input message.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. Delegation allows objects to delegate messages to other objects. Inheritance means an object inherits capabilities from its parent class. Polyinstantiation means “many instances,” two objects with the same names that have different data.
7. Two objects with the same name have different data. What Object-Oriented Programming concept does this illustrate?
A. Delegation
B. Inheritance
C. Polyinstantiation
D. Polymorphism
Correct Answer and Explanation: C. Answer C is correct; polyinstantiation means “many instances,” two objects with the same names that have different data.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. Delegation allows objects to delegate messages to other objects. Inheritance means an object inherits capabilities from its parent class. Polymorphism allows the ability to overload operators, performing different methods depending on the context of the input message.
8. What type of testing determines whether software meets various end-state requirements, from a user or customer, contract or compliance perspective?
A. Acceptance Testing
B. Integration Testing
C. Regression Testing
D. Unit Testing
Correct Answer and Explanation: A. Answer A is correct; Acceptance testing determines whether software meets various end-state requirements, from a user or customer, contract or compliance perspective.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. Integration testing tests multiple software components as they are combined into a working system. Regression testing tests software after updates, modifications or patches. Unit testing tests low-level tests of software components, such as functions, procedures or objects.
9. A programmer allocates 20 bytes for a username variable, and an attacker enters a username that is 1,000 bytes long. All 1,000 bytes are copied to the stack. What type of attack did the attacker perform?
A. Buffer Overflow
B. Cross Site Scripting (XSS)
C. Fuzzing
D. Time of Check/Time of Use (TOC/TOU)
Correct Answer and Explanation: A. Answer A is correct; a buffer overflow occurs when a programmer does not perform variable bounds checking,
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. Cross-Site Scripting (XSS) leverages third-party execution of web scripting languages such as JavaScript within the security context of a trusted site. Fuzzing is a form of black box software testing that enters random malformed data as inputs into software programs to determine if they will crash. Time of Check/Time of Use (TOCTOU) attacks are also called race conditions: an attacker attempts to alter a condition after it has been checked by the operating system, but before it is used.
10. What type of database language is used to create, modify and delete tables?
A. Data Definition Language (DDL)
B. Data Manipulation Language (DML)
C. Database Management System (DBMS)
D. Structured Query Language (SQL)
Correct Answer and Explanation: A. Answer A is correct; Data Definition Language (DDL) is used to create, modify and delete tables.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. Data Manipulation Language (DML) is used to query and update data stored in the tables. Database Management System (DBMS) manages the database system and provides security features. Structured Query Language (SQL) is a database query language that includes both DDL and DML. DDL is more specific than SQL, so it is a better answer for this question.
11. A database contains an entry with an empty primary key. What database concept has been violated?
A. Entity Integrity
B. Normalization
C. Referential Integrity
D. Semantic Integrity
Correct Answer and Explanation: A. Answer A is correct; Entity integrity means each tuple has a unique primary key that is not null.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. Normalization seeks to make the data in a database table logically concise, organized and consistent. Referential integrity means that every foreign key in a secondary table matches a primary key in the parent table: if this is not true, referential integrity has been broken. Semantic integrity means each attribute (column) value is consistent with the attribute data type.
12. Which vulnerability allows a third party to redirect static content within the security context of a trusted site?
A. Cross-Site Request Forgery (CSRF)
B. Cross-Site Scripting (XSS)
C. PHP Remote File Inclusion (RFI)
D. SQL Injection
Correct Answer and Explanation: A. Answer A is correct; Cross-Site Request Forgery (CSRF) allows a third party to redirect static content within the security context of a trusted site.
Incorrect Answers and Explanations: B, C, and D. Answers B, C, and D are incorrect. Cross-Site Scripting (XSS): third party execution of Web scripting languages such as Javascript within the security context of a trusted site. XSS is similar to CSRF; the difference is XSS uses active code. PHP Remote File Inclusion (RFI): alters normal PHP variables to reference remote content, which can lead to execution of malicious PHP code. SQL Injection manipulates a back-end SQL server via a front-end Web server.
13. What language allows CORBA (Common Object Request Broker Architecture) objects to communicate via a message interface?
A. Distributed Component Object Model (DCOM)
B. Interface Definition Language (IDL)
C. Object Linking and Embedding (OLE)
D. Object Management Guidelines (OMG)
Correct Answer and Explanation: B. Answer B is correct; Interface Definition Language (IDL) allows CORBA objects to communicate via a message interface.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. DCOM (Distributed Component Object Model) is a Microsoft object broker that locates objects over a network. Object Linking and Embedding (OLE), is a part of DCOM that provides a way to link documents to other documents. Object Management Guidelines is a distracter answer, playing off the ream OMG: Object Management Group (OMG) developed CORBA.
14. What database high availability option allows multiple clients to access multiple database servers simultaneously?
A. Database commit
B. Database journal
C. Replicated database
D. Shadow database
Correct Answer and Explanation: C. Answer C is correct; Database replication mirrors a live database, allowing simultaneous reads and writes to multiple replicated databases by clients.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. DBMSs may attempt to commit updates: make the pending changes permanent. A database journal is a log of all database transactions. A shadow database is similar to a replicated database, with one key difference: a shadow database mirrors all changes made to a primary database, but clients do not access the shadow.
15. What component of an expert system consists of “if/then” statements?
A. Backward chaining
B. Forward chaining
C. Inference engine
D. Knowledge base
Correct Answer and Explanation: D. Answer D is correct; a knowledge base consists of “if/then” statements. These statements contain rules that the expert system uses to make decisions.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. Forward chaining starts with no premise and works forward to determine a solution. Backward chaining begins with a premise and works backwards. The inference engine follows the tree formed by knowledge base, and fires a rule when there is a match.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
