IN THIS CHAPTER, YOU WILL LEARN ABOUT THE FOLLOWING:
- CSMA/CA vs. CSMA/CD
- Collision detection
- Distributed Coordination Function (DCF)
- Interframe space (IFS)
- Duration/ID field
- Carrier sense
- Random backoff timer
- Point Coordination Function (PCF)
- Hybrid Coordination Function (HCF)
- Enhanced Distributed Channel Access (EDCA)
- HCF Controlled Channel Access (HCCA)
- Block acknowledgment (BA)
- Wi-Fi Multimedia (WMM)
- Airtime Fairness
 One of the difficulties we had in writing this chapter was that in order for you to understand how a wireless station gains access to the media, we have to teach more than what is needed for the CWNA exam. The details are needed to grasp the concepts; however, it is the concepts that you will be tested on. If you find the details of this chapter interesting, then after reading this book, you should consider reading CWAP Certified Wireless Analysis Professional Official Study Guide: Exam PW0-270 by David A. Westcott, David D. Coleman, et al. (Sybex, 2011), which gets into the nitty-gritty details of 802.11 communications. If you decide to take the CWAP exam, at that time you will need to know details far beyond what we have included in this chapter. But for now, take the details for what they are: a foundation for helping you understand the overall process of how a wireless station gains access to the half-duplex medium.
One of the difficulties we had in writing this chapter was that in order for you to understand how a wireless station gains access to the media, we have to teach more than what is needed for the CWNA exam. The details are needed to grasp the concepts; however, it is the concepts that you will be tested on. If you find the details of this chapter interesting, then after reading this book, you should consider reading CWAP Certified Wireless Analysis Professional Official Study Guide: Exam PW0-270 by David A. Westcott, David D. Coleman, et al. (Sybex, 2011), which gets into the nitty-gritty details of 802.11 communications. If you decide to take the CWAP exam, at that time you will need to know details far beyond what we have included in this chapter. But for now, take the details for what they are: a foundation for helping you understand the overall process of how a wireless station gains access to the half-duplex medium.
CSMA/CA vs. CSMA/CD
Network communication requires a set of rules to provide controlled and efficient access to the network medium. Media Access Control (MAC) is the generic term used when discussing the general concept of access. There are many ways of providing media access. The early mainframes used polling, which sequentially checked each terminal to see whether there was data to be processed. Later, token-passing and contention methods were used to provide access to the media. Two forms of contention that are heavily used in today's networks are Carrier Sense Multiple Access with Collision Detection (CSMA/CD) and Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA).
CSMA/CD is well known and is used by Ethernet networks. CSMA/CA is not as well known and is used by 802.11 networks. Stations using either access method must first listen to see whether any other device is transmitting; otherwise, the station must wait until the medium is available. The difference between CSMA/CD and CSMA/CA exists at the point when a client wants to transmit and no other clients are presently transmitting. A CSMA/CD node can immediately begin transmitting. If a collision occurs while a CSMA/CD node is transmitting, the collision will be detected and the node will temporarily stop transmitting. 802.11 wireless radios are not capable of transmitting and receiving at the same time, so they are not capable of detecting a collision during their transmission. For this reason, 802.11 wireless networking uses CSMA/CA instead of CSMA/CD to try to avoid collisions.
When a CSMA/CA station has determined that no other stations are transmitting, the 802.11 radio will choose a random backoff value. The station will then wait an additional period of time, based on that backoff value, before transmitting. During this time, the station continues to monitor to make sure that no other stations begin transmitting. Because of the half-duplex nature of the RF medium, it is necessary to ensure that at any given time only one 802.11 radio has control of the medium. CSMA/CA is a process used to ensure that only one 802.11 radio is transmitting at a time. Is this process perfect? Absolutely not! Collisions still do occur when two or more radios transmit at the same time. However, the IEEE 802.11-2012 standard defines a function called Distributed Coordination Function (DCF) as a medium access method that utilizes multiple checks and balances to try to minimize collisions. These checks and balances can also be thought of as several lines of defense. The various lines of defense are put in place to once again hopefully ensure that only one radio is transmitting while all other radios are listening. CSMA/CA minimizes the risk of collisions without excessive overhead.
The 802.11-2012 standard also defines an optional function called Point Coordination Function (PCF) that allows for the access point (AP) to poll client stations about their need to transmit data. Finally, the 802.11-2012 standard also encompasses a Hybrid Coordination Function (HCF) that specifies advanced quality of service (QoS) methods.
This entire process is covered in more detail in the next section of this chapter.
CSMA/CA Overview
Carrier sense determines whether the medium is busy. Multiple access ensures that every radio gets a fair shot at the medium (but only one at a time). Collision avoidance means only one radio gets access to the medium at any given time, hopefully avoiding collisions.
Collision Detection
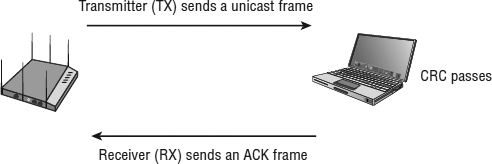
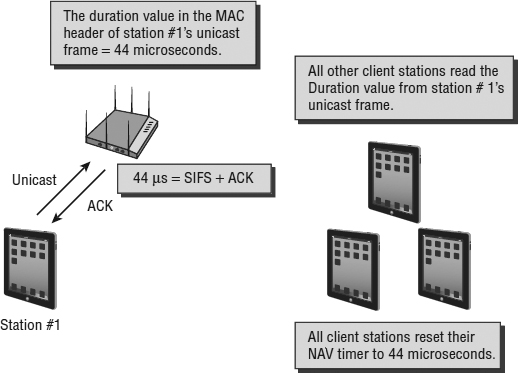
In the previous section, we mentioned that 802.11 radios were not able to transmit and receive at the same time and therefore cannot detect collisions. So, if they cannot detect a collision, how do they know whether one occurred? The answer is simple. As shown in Figure 8.1, every time an 802.11 radio transmits a unicast frame, if the frame is received properly, the 802.11 radio that received the frame will reply with an acknowledgment (ACK) frame. The ACK frame is a method of delivery verification of unicast frames. 802.11n and 802.11ac radios make use of frame aggregation, which groups multiple unicast frames together. The delivery of aggregated frames is verified using a block ACK.
The majority of unicast 802.11 frames must be acknowledged. Broadcast and multicast frames do not require an acknowledgment. If any portion of a unicast frame is corrupted, the cyclic redundancy check (CRC) will fail and the receiving 802.11 radio will not send an ACK frame to the transmitting 802.11 radio. If an ACK frame is not received by the original transmitting radio, the unicast frame is not acknowledged and will have to be retransmitted.
FIGURE 8.1 Unicast acknowledgment
This process does not specifically determine whether a collision occurs; in other words, there is no collision detection. However, if an ACK frame is not received by the original radio, there is collision assumption. Think of the ACK frame as a method of delivery verification for unicast 802.11 frames. If no proof of delivery is provided, the original radio assumes there was a delivery failure and retransmits the frame.
Distributed Coordination Function
Distributed Coordination Function (DCF) is the fundamental access method of 802.11 communications. DCF is the mandatory access method of the 802.11 standard. The 802.11 standard also has an optional access method known as Point Coordination Function (PCF), which is covered later in this chapter. With the addition of the 802.11e amendment, which is now part of the 802.11-2012 standard, a third coordination function known as Hybrid Coordination Function (HCF) has been added, which also is covered later in this chapter. In the following sections, you will learn about some of the components that are part of the CSMA/CA process. Here are the four main components of DCF:
- Interframe space
- Duration/ID field
- Carrier sense
- Random backoff timer
Think of these four components as checks and balances that work together at the same time to ensure that only one 802.11 radio is transmitting on the half-duplex medium. These four components will be explained separately, but it is important to understand that all four mechanisms are functioning at the same time.
Interframe Space (IFS)
Interframe space (IFS) is a period of time that exists between transmissions of wireless frames. There are six types of interframe spaces, which are listed here in order of shortest to longest:
- Reduced interframe space (RIFS), highest priority
- Short interframe space (SIFS), second highest priority
- PCF interframe space (PIFS), middle priority
- DCF interframe space (DIFS), lowest priority
- Arbitration interframe space (AIFS), used by QoS stations
- Extended interframe space (EIFS), used after receipt of corrupted frames
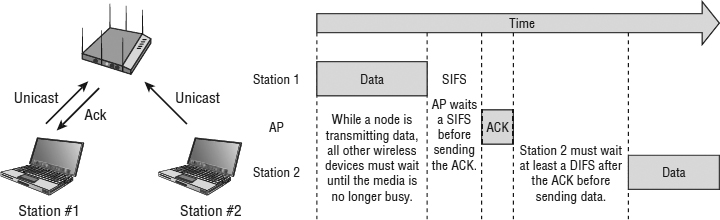
The actual length of time of each of the interframe spaces varies depending on the transmission speed of the network. Interframe spaces are one line of defense used by CSMA/CA to ensure that only certain types of 802.11 frames are transmitted following certain interframe spaces. For example, only ACK frames, block ACK frames, data frames, and clear-to-send (CTS) frames may follow a SIFS. The two most common interframe spaces used are the SIFS and the DIFS. As pictured in Figure 8.2, the ACK frame is the highest-priority frame, and the use of a SIFS ensures that it will be transmitted first, before any other type of 802.11 frame. Most other 802.11 frames follow a longer period of time called a DIFS.
FIGURE 8.2 SIFS and DIFS
Interframe spaces are all about what type of 802.11 traffic is allowed next. Interframe spacing also acts as a backup mechanism to virtual carrier sense, which is discussed later in this chapter. The main thing that you need to understand at this time is that there are six interframe spaces of different durations of time, and the order is RIFS < SIFS < PIFS < DIFS < AIFS < EIFS.
As you read further in this chapter, you will learn that timing is an important aspect of successful wireless communications. Interframe spaces are just one component of this tightly linked environment.
Duration/ID Field
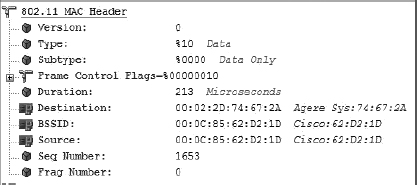
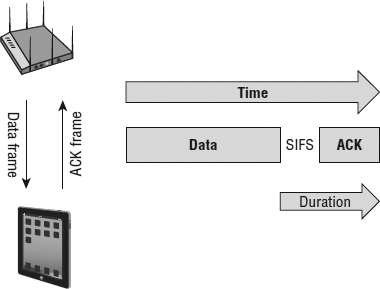
As pictured in Figure 8.3, one of the fields in the MAC header of an 802.11 frame is the Duration/ID field. When a client transmits a unicast frame, the Duration/ID field contains a value from 0 to 32,767. The Duration/ID value represents the time, in microseconds, that is required to transmit an active frame exchange process so that other radios do not interrupt the process. In the example shown in Figure 8.4, the client that is transmitting the data frame calculates how long it will take to receive an ACK frame and includes that length of time in the Duration/ID field in the MAC header of the transmitted unicast data frame. The value of the Duration/ID field in the MAC header of the ACK frame that follows is 0 (zero). To summarize, the value of the Duration/ID field indicates how long the RF medium will be busy before another station can contend for the medium.
FIGURE 8.3 Duration/ID field
FIGURE 8.4 Duration value of SIFS + ACK
The majority of the time, the Duration/ID field contains a Duration value that is used to reset other stations' network allocation vector (NAV) timers. In the rare case of a PS-Poll frame, the Duration/ID is used as an ID value of a client station using legacy power management. Power management is discussed in Chapter 9, “802.11 MAC Architecture.”
Carrier Sense
The first step that an 802.11 CSMA/CA device needs to do to begin transmitting is to perform a carrier sense. This is a check to see whether the medium is busy. Think of it like listening for a busy signal when you call someone on the phone. There are two ways that a carrier sense is performed: virtual carrier sense and physical carrier sense.
Virtual Carrier Sense
Virtual carrier sense uses a timer mechanism known as the network allocation vector (NAV). The NAV timer maintains a prediction of future traffic on the medium based on Duration value information seen in a previous frame transmission. When an 802.11 radio is not transmitting, it is listening. As depicted in Figure 8.5, when the listening radio hears a frame transmission from another station, it looks at the header of the frame and determines whether the Duration/ID field contains a Duration value or an ID value. If the field contains a Duration value, the listening station will set its NAV timer to this value. The listening station will then use the NAV as a countdown timer, knowing that the RF medium should be busy until the countdown reaches 0.
FIGURE 8.5 Virtual carrier sense
This process essentially allows the transmitting 802.11 radio to notify the other stations that the medium will be busy for a period of time (Duration/ID value). The stations that are not transmitting listen and hear the Duration/ID, set a countdown timer (NAV), and wait until their timer hits 0 before they can contend for the medium and eventually transmit on the medium. A station cannot contend for the medium until its NAV timer is 0, nor can a station transmit on the medium if the NAV timer is set to a nonzero value. As stated earlier, there are several lines of defense used by CSMA/CA to prevent collisions, and the NAV timer is often considered the first line of defense. Because the Duration/ID value inside an 802.11 MAC header is used to set the NAV timer, virtual carrier sense is a layer 2 carrier sense mechanism.
Physical Carrier Sense
Virtual carrier sense is one method of keeping other stations from transmitting while another radio has control of the RF medium. However, it is possible that a station did not hear the other radio transmitting and was therefore unable to read the Duration/ID field and set its NAV timer. There could be numerous reasons why, but that is irrelevant at the moment. CSMA/CA utilizes another line of defense to ensure that a station does not transmit while another is already transmitting: The 802.11-2012 standard also defines a physical carrier sense mechanism to determine if the medium is busy.
Physical carrier sensing is performed constantly by all stations that are not transmitting or receiving. When a station performs a physical carrier sense, it is actually listening to the channel to see whether any other transmitters are taking up the channel.
Physical carrier sense has two purposes:
- The first purpose is to determine whether a frame transmission is inbound for a station to receive. If the medium is busy, the radio will attempt to synchronize with the transmission.
- The second purpose is to determine whether the medium is busy before transmitting. This is known as the clear channel assessment (CCA). The CCA involves listening for RF transmissions at the Physical layer. The medium must be clear before a station can transmit.
It is important to understand that both virtual carrier sense and physical carrier sense are always happening at the same time. Virtual carrier sense is a layer 2 line of defense, while physical carrier sense is a layer 1 line of defense. If one line of defense fails, hopefully the other will prevent collisions from occurring.
Random Backoff Timer
An 802.11 station may contend for the medium during a window of time known as the backoff time. At this point in the CSMA/CA process, the station selects a random backoff value using a pseudo-random backoff algorithm.
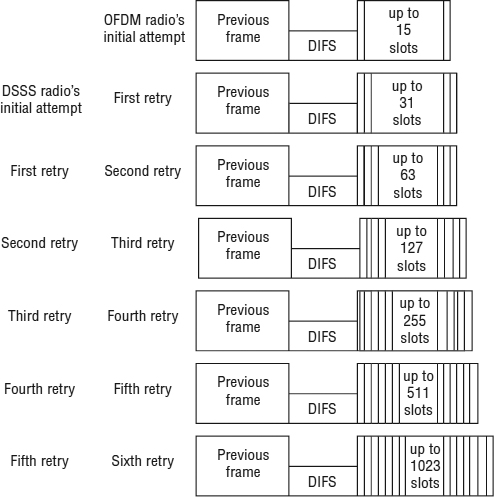
The station chooses a random number from a range called a contention window (CW) value. After the random number is chosen, the number is multiplied by the slot time value. Slot time sizes are dependent on the physical layer specification (PHY) in use (DSSS, OFDM, etc.). This starts a random backoff timer. The random backoff timer is the final timer used by a station before it transmits. The station's backoff timer begins to count down ticks of a clock known as slots. When the backoff time is equal to 0, the client can reassess the channel and, if it is clear, begin transmitting.
If no medium activity occurs during a particular slot time, then the backoff timer is decremented by a slot time. If the physical or virtual carrier sense mechanisms sense a busy medium, the backoff timer decrement is suspended, and the backoff timer value is maintained. When the medium is idle for a duration of a DIFS, AIFS, or EIFS period, the backoff process resumes and continues the countdown from where it left off. When the backoff timer reaches 0, transmission commences. Unsuccessful transmissions cause the CW size to increase exponentially up to a maximum value, as shown in Figure 8.6.
The following example is a simple review of the process:
- An OFDM station selects a random number from a contention window of 0–15. For this example, the number chosen is 4.
- The station multiplies the random number of 4 by a slot time of 9μs.
- The random backoff timer has a value of 36μs (4 slots).
- For every slot time during which there is no medium activity, the backoff time is decremented by a slot time.
- The station decrements the backoff timer until the timer is zero.
- The station transmits if the medium is clear.
FIGURE 8.6 Contention window length
The random backoff timer is another line of defense and helps minimize the likelihood of two stations trying to communicate at the same time, although it does not fully prevent this from occurring. If a station does not receive an ACK, it starts the carrier sense process over again.
Point Coordination Function
In addition to DCF, the IEEE 802.11-2012 standard defines an additional, optional medium access method known as Point Coordination Function (PCF). This access method is a form of polling. The AP performs the function of the point coordinator (PC). Because an AP is taking the role of the point coordinator, the PCF medium access method will work in only a basic service set (BSS). PCF cannot be utilized in an ad hoc network because no AP exists in an independent basic service set (IBSS). Because polling is performed from a central device, PCF provides managed access to the medium.
In order for PCF to be used, both the AP and the station must support it. If PCF is enabled, DCF will still function. The AP will alternate between PCF mode and DCF mode. While the AP is functioning in PCF mode, that time is known as the contention-free period (CFP). During the contention-free period, the AP polls only clients in PCF mode about their intention to send data. This is a method of prioritizing clients. While the AP is functioning in DCF mode, that time is known as the contention period (CP).
 If you would like to learn more about PCF, we suggest that you read the 802.11-2012 standard document, which you can download from the IEEE website:
If you would like to learn more about PCF, we suggest that you read the 802.11-2012 standard document, which you can download from the IEEE website:
http://standards.ieee.org/about/get/802/802.11.html
As we stated earlier, PCF is an optional access method, and as of this writing, we do not know of any vendor that has implemented it. You will not be tested on PCF.
Hybrid Coordination Function
The 802.11e quality of service amendment added a new coordination function to 802.11 medium contention, known as Hybrid Coordination Function (HCF). The 802.11e amendment and HCF have since been incorporated into the 802.11-2012 standard. HCF combines capabilities from both DCF and PCF and adds enhancements to them to create two channel-access methods: Enhanced Distributed Channel Access (EDCA) and HCF Controlled Channel Access (HCCA).
DCF and PCF medium contention mechanisms discussed earlier allow for an 802.11 radio to transmit a single frame. After transmitting a frame, the 802.11 station must contend for the medium again before transmitting another frame. HCF defines the ability for an 802.11 radio to send multiple frames when transmitting on the RF medium. When an HCF-compliant radio contends for the medium, it receives an allotted amount of time to send frames. This period of time is called a transmit opportunity (TXOP). During this TXOP, an 802.11 radio may send multiple frames in what is called a frame burst. A short interframe space (SIFS) is used between each frame to ensure that no other radios transmit during the frame burst.
Enhanced Distributed Channel Access
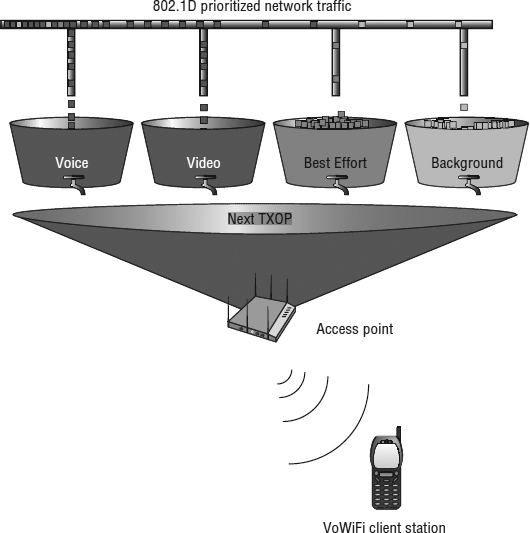
Enhanced Distributed Channel Access (EDCA) is a wireless media access method that provides differentiated access that directs traffic to four access-category QoS priority queues. EDCA is an extension of DCF. The EDCA medium access method prioritizes traffic using priority tags that are identical to 802.1D priority tags. Priority tags provide a mechanism for implementing QoS at the MAC level.
Different classes of service are available, represented in a 3-bit user priority field in an IEEE 802.1Q header added to an Ethernet frame. 802.1D enables priority queuing (enabling some Ethernet frames to be forwarded ahead of others within a switched Ethernet network). Figure 8.7 depicts 802.1D priority tags from the Ethernet side that are used to direct traffic to access-category queues.
FIGURE 8.7 EDCA and 802.1D priority tags
EDCA defines four access categories, based on the eight UPs. The four access categories from lowest priority to highest priority are AC_BK (Background), AC_BE (Best Effort), AC_VI (Video), and AC_VO (Voice). For each access category, an enhanced version of DCF known as Enhanced Distributed Channel Access Function (EDCAF) is used to contend for a TXOP. Frames with the highest-priority access category have the lowest backoff values and therefore are more likely to get a TXOP. The specific details of this process are beyond the scope of the CWNA exam.
HCF Controlled Channel Access
HCF Controlled Channel Access (HCCA) is a wireless media access method that uses a QoS-aware centralized coordinator known as a hybrid coordinator (HC), which operates differently than the point coordinator in a PCF network. The HC is built into the AP and has a higher priority of access to the wireless medium. Using this higher priority level, it can allocate TXOPs to itself and other stations to provide a limited-duration controlled access phase (CAP), providing contention-free transfer of QoS data. The specific details of this process are beyond the scope of the CWNA exam. As with PCF, as of this writing we do not know of any vendor that has implemented HCCA.
Block Acknowledgment
The 802.11e amendment also introduced a Block acknowledgment (BA) mechanism that is defined in the 802.11-2012 standard. A Block ACK improves channel efficiency by aggregating several acknowledgments into one single acknowledgment frame. There are two types of Block ACK mechanisms: immediate and delayed.
- The immediate Block ACK is designed for use with low-latency traffic.
- The delayed Block ACK is more suitable for latency-tolerant traffic.
For the purposes of this book, we will discuss only the immediate Block ACK.
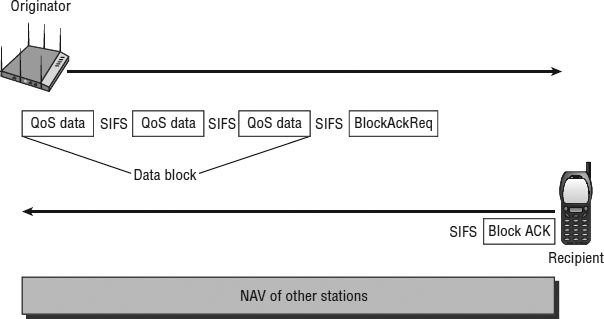
As pictured in Figure 8.8, an originator station sends a block of QoS data frames to a recipient station. The originator requests acknowledgment of all the QoS data frames by sending a BlockAckReq frame. Instead of acknowledging each unicast frame independently, the block of QoS data frames are all acknowledged by a single Block ACK. A bitmap in the Block ACK frame is used to indicate the status of all the received data frames. If only one of the frames is corrupted, only that frame will need to be retransmitted. The use of a Block ACK instead of a traditional ACK is a more efficient method that cuts down on medium contention overhead. Uses of Block ACK mechanisms are further defined in the 802.11n-2009 amendment for the purposes of frame aggregation. Please see Chapter 18, “802.11n,” for more details.
FIGURE 8.8 Immediate Block acknowledgment
Wi-Fi Multimedia
Prior to the adoption of the 802.11e amendment, no adequate QoS procedures had been defined for the use of time-sensitive applications such as Voice over Wi-Fi (VoWiFi). Application traffic such as voice, audio, and video has a lower tolerance for latency and jitter and requires priority before standard data traffic. The 802.11e amendment defined the layer 2 MAC methods needed to meet the QoS requirements for time-sensitive applications over IEEE 802.11 wireless LANs. The Wi-Fi Alliance introduced the Wi-Fi Multimedia (WMM) certification as a partial mirror of 802.11e amendment.
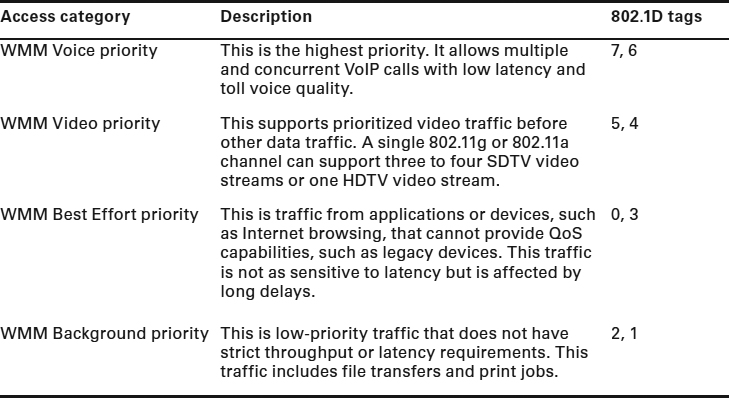
Because WMM is based on EDCA mechanisms, 802.1D priority tags from the Ethernet side are used to direct traffic to four access-category priority queues. The WMM certification provides for traffic prioritization via four access categories, as described in Table 8.1.
TABLE 8.1 Wi-Fi multimedia access categories
The Wi-Fi Alliance also defined WMM-PS (Power Save), which uses 802.11e power-saving mechanisms to increase the battery life via advanced power-saving mechanisms. More information about power management can be found in Chapter 9.
Another Wi-Fi Alliance certification is WMM-Admission Control, which defines the use of management frames for the signaling between an AP and a client station. Client stations can request to send a traffic stream (TS) of frames of a particular WMM access category. A traffic stream can be unidirectional or bidirectional. An AP will evaluate a request frame from a client station against the network load and channel conditions. If the AP can accommodate the request, it accepts the request and grants the client station the medium time for a traffic stream. If the request is rejected, the client device is not allowed to initiate the requested traffic stream and may decide to delay the traffic stream, associate with a different AP, or establish a best-effort traffic stream outside the operation of WMM-Admission Control. WMM-Admission Control improves the performance for time-sensitive data such as video and voice. WMM-Admission Control improves the reliability of applications in progress by preventing oversubscription of bandwidth.
Important Wi-Fi Alliance White Papers
The Wi-Fi Alliance has two white papers that we recommend you read to learn more about WMM. Both white papers are available for download at the WiFi Alliance website: www.wi-fi.org.
- Wi-Fi CERTIFIED for WMM—Support for Multimedia Applications with Quality of Service in Wi-Fi Networks
- WMM Power Save for Mobile and Portable Wi-Fi CERTIFIED Devices
Airtime Fairness
One of the important features of 802.11 is its ability to support many different data rates. This allows older technologies to still communicate alongside newer devices, along with enabling devices to maintain communications by shifting to slower data rates as they move away from an access point. The ability to use these slower data rates is paramount to 802.11 communications; however, it can also be a huge hindrance to the overall performance of the network and to individual devices operating at faster data rates.
Since 802.11 is contention based, each radio must contend for its turn to communicate, then transmit, and then go back to the contention process. As each radio takes its turn transmitting, the other 802.11 radios must wait. If the transmitting radio is using a fast data rate, the other radios do not have to wait long. If the transmitting radio is using a slow data rate, the other radios will have to wait a much longer period of time. When 802.11 radios transmit at very low data rates such as 1 Mbps and 2 Mbps, effectively they cause medium-contention overhead for higher data rate transmitters due to the long wait time while the slower devices are transmitting.
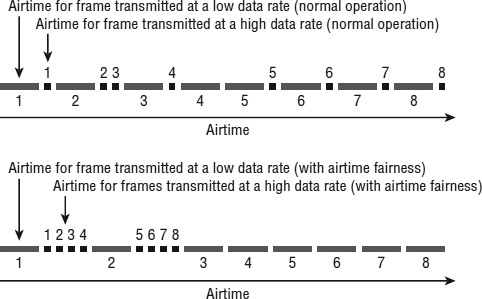
To try to understand this, look at Figure 8.9. The top portion of the figure illustrates the normal operation of two stations each sending eight frames. One station is sending eight frames at a higher data rate and the other station is sending eight frames at a lower data rate. If a high-speed and a low-speed device coexist in the same WLAN, they have to share or contend for the time to transmit. In other words, both stations will statistically get an equal number of times to access the RF medium even though one of the stations is capable of transmitting at a higher rate and requires much less airtime to transmit the same amount of data. Because there is no priority given to the station with the higher data rate, both stations finish transmitting their eight frames over the same period of time.
FIGURE 8.9 Airtime fairness example
Instead of allocating equal access to the network between devices, the goal of airtime fairness is to allocate equal time, as opposed to equal opportunity. Airtime fairness can provide better time management of the RF medium. In the bottom half of Figure 8.9, airtime fairness is enabled; you can see that the station with the higher data rate transmission is given priority before the station with the lower data rates. Effectively this is a much better use of transmission time because the higher data rate station does not have to remain idle waiting during the lower data rate transmission. Notice that the faster station transmitted all eight frames in a much shorter time period, and the slower rate station still sent all eight frames in about the same period as before. Airtime fairness effectively achieves better time management of the medium by cutting down on wait times. The net result is better performance, higher capacity, and more throughput over the Wi-Fi network.
There currently are no 802.11 standards or amendments that define airtime fairness or how to implement it. Nor is there any requirement for a vendor to implement it. Most vendors use airtime fairness mechanisms only for downstream transmissions from an AP to an associated client. Airtime fairness mechanisms are normally used for prioritizing the higher data rate downstream transmissions from an AP over the lower data rate downstream transmissions from an AP. At least one vendor also makes claims of upstream airtime fairness capability. Any implementation of airtime fairness is a proprietary solution developed by each WLAN vendor. No matter how each vendor implements its solution, the underlying goal is essentially the same: to prevent slower devices from bogging down the rest of the network.
Although each WLAN vendor takes its own approach to implementing airtime fairness, it is typical for them to analyze the downstream client traffic and assign different weighting based on such characteristics as current throughput, client data rates, SSID, PHY type, and other variables. Algorithms are used to process this information and determine the number of opportunities for each client's downstream transmissions. If implemented properly, airtime fairness makes better use of the medium by providing preferential access for higher data rate transmissions.
Summary
This chapter focused on 802.11 medium access. Every station has the right to communicate, and the management of access to the wireless medium is controlled through media access control. We discussed the difference between CSMA/CD and CSMA/CA as contention methods. CSMA/CA uses a pseudorandom contention method called Distributed Coordination Function. DCF uses four lines of defense to ensure that only one 802.11 radio is transmitting on the half-duplex medium.
We also discussed an optional contention-free method called Point Coordination Function. The 802.11e quality of service amendment added a new coordination function to 802.11 medium contention, known as Hybrid Coordination Function (HCF). The Wi-Fi Multimedia (WMM) certification was introduced by the Wi-Fi Alliance as a partial mirror of the 802.11e amendment. WMM is designed to meet the QoS requirements for time-sensitive applications such as audio, video, and voice over IEEE 802.11.
Airtime fairness was introduced as a way for vendors to provide faster devices with preferential access to the media when operating alongside devices that are transmitting at slower data rates.
Exam Essentials
Understand the similarities and differences between CSMA/CA and CSMA/CD. Understand both access methods and know what makes them similar and what makes them different.
Define the four checks and balances of CSMA/CA and DCF. Understand that virtual carrier sense, physical carrier sense, interframe spacing, and the random backoff timer all work together to ensure that only one 802.11 radio is transmitting on the half-duplex medium.
Define virtual and physical carrier senses. Understand the purpose and basic mechanisms of the two carrier senses.
Explain DCF and PCF. Define the basic operations of both Distributed Coordination Function and Point Coordination Function.
Define HCF quality of service mechanisms. Hybrid Coordination Function defines the use of TXOPs and access categories in EDCA as well as the use of TXOPs and polling during HCCA.
Understand the Wi-Fi Multimedia (WMM) certification. WMM is designed to provide quality of service capabilities to 802.11 wireless networks. WMM is a partial mirror of the 802.11e amendment. WMM currently provides for traffic priority via four access categories.
Understand the importance of airtime fairness and what it does. Airtime fairness provides devices operating at faster data rates with preferential access to the medium. This preferential treatment provides all devices with equal access, resulting in all devices equally sharing the available transmission bandwidth.
Review Questions
- DCF is also known as what? (Choose all that apply.)
- Carrier Sense Multiple Access with Collision Detection (CSMA/CD)
- Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA)
- Data Control Function
- Distributed Coordination Function
- 802.11 collision detection is handled using which technology?
- Network allocation vector (NAV).
- Clear channel assessment (CCA).
- Duration/ID value.
- Receiving an ACK from the destination station.
- Positive collision detection cannot be determined.
- ACK and CTS-to-self frames follow which interframe space?
- EIFS
- DIFS
- PIFS
- SIFS
- LIFS
- The carrier sense portion of CSMA/CA is performed by using which of the following methods? (Choose all that apply.)
- Virtual carrier sense
- Physical carrier sense
- Channel sense window
- Clear channel assessment
- After the station has performed the carrier sense and determined that no other devices are transmitting for a period of a DIFS interval, what is the next step for the station?
- Wait the necessary number of slot times before transmitting if a random backoff value has already been selected.
- Begin transmitting.
- Select a random backoff value.
- Begin the random backoff timer.
- If PCF is implemented, it can function in which of the following network environments? (Choose all that apply.)
- Which of the following terms are affiliated with the virtual carrier sense mechanism? (Choose all that apply.)
- Contention window
- Network allocation vector
- Random backoff time
- Duration/ID field
- The goal of allocating equal time as opposed to equal opportunity is known as what?
- Access fairness
- Opportunistic media access
- CSMA/CA
- Airtime fairness
- CSMA/CA and DCF define which mechanisms that attempt to ensure that only one 802.11 radio can transmit on the half-duplex RF medium? (Choose all that apply.)
- Random backoff timer
- NAV
- CCMP
- CCA
- Interframe spacing
- The Wi-Fi Alliance certification called Wi-Fi Multimedia (WMM) is based on which media access method defined by the 802.11-2012 standard?
- DCF
- PCF
- EDCA
- HCCA
- HSRP
- Hybrid Coordination Function (HCF) defines what allotted period of time in which a station can transmit multiple frames?
- Block acknowledgment
- Polling
- Virtual carrier sense
- Physical carrier sense
- TXOP
- WMM is based on EDCA and provides for traffic prioritization via which of the following access categories? (Choose all that apply.)
- WMM Voice priority
- WMM Video priority
- WMM Audio priority
- WMM Best Effort priority
- WMM Background priority
- The 802.11e amendment (now part of the 802.11-2012 standard) defines which of the following medium access methods to support QoS requirements? (Choose all that apply.)
- Distributed Coordination Function (DCF)
- Enhanced Distributed Channel Access (EDCA)
- Hybrid Coordination Function (HCF)
- Point Coordination Function (PCF)
- Hybrid Coordination Function Controlled Access (HCCA)
- What information that comes from the wired network is used to assign traffic into access categories on a WLAN controller?
- Duration/ID
- 802.1D priority tags
- Destination MAC address
- Source MAC address
- What are the two reasons that 802.11 radios use physical carrier sense? (Choose all that apply.)
- To synchronize incoming transmissions
- To synchronize outgoing transmissions
- To reset the NAV
- To start the random backoff timer
- To assess the RF medium
- What CSMA/CA mechanism is used for medium contention? (Choose all that apply.)
- NAV
- CCA
- Random backoff timer
- Contention window
- Which field in the MAC header of an 802.11 frame resets the NAV timer for all listening 802.11 stations?
- The EDCA medium access method provides for the prioritization of traffic via priority queues that are matched to eight 802.1D priority tags. What are the EDCA priority queues called?
- TXOP
- Access categories
- Priority levels
- Priority bits
- PT
- ACKs are required for which of the following frames?
- Unicast
- Broadcast
- Multicast
- Anycast
- What QoS mechanism can be used to reduce medium contention overhead during a frame burst of low-latency traffic?
- Delayed Block ACK
- Contention period
- Contention window
- Contention-free period
- Immediate Block ACK