IN THIS CHAPTER, YOU WILL LEARN ABOUT THE FOLLOWING:
- Packets, frames, and bits
- Data-Link layer
- MAC Service Data Unit (MSDU)
- MAC Protocol Data Unit (MPDU)
- Physical layer
- PLCP Service Data Unit (PSDU)
- PLCP Protocol Data Unit (PPDU)
- 802.11 and 802.3 interoperability
- Three 802.11 frame types
- Management frames
- Control frames
- Data frames
- Beacon management frame (beacon)
- Passive scanning
- Active scanning
- Authentication
- Open System authentication
- Shared Key authentication
- Association
- Authentication and association states
- Basic and supported rates
- Roaming
- Reassociation
- Disassociation
- Deauthentication
- ACK frame
- Fragmentation
- Protection mechanism
- RTS/CTS
- CTS-to-Self
- Data frames
- Power management
- Active mode
- Power Save mode
- Traffic indication map (TIM)
- Delivery traffic indication message (DTIM)
- Announcement traffic indication message (ATIM)
- WMM Power Save (WMM-PS) and U-APSD
- 802.11n power management
 This chapter presents all of the components of the 802.11 MAC architecture. We discuss how upper-layer information is encapsulated within an 802.11 frame format. We cover the three major 802.11 frame types and a majority of the 802.11 frame subtypes. We examine many MAC layer tasks, such as active scanning, and the specific 802.11 frames that are used to accomplish these tasks. An often misunderstood capability of 802.11 is the ERP protection mechanism. We describe how 802.11b and 802.11g stations can coexist in the same BSS by using either the RTS/CTS or CTS-to-Self protection mechanism. This protection mechanism is also the foundation for coexistence between 802.11n devices and earlier legacy devices. Near the end of this chapter we discuss legacy 802.11 power management and enhanced WMM-PS power management, which are methods used to save battery life.
This chapter presents all of the components of the 802.11 MAC architecture. We discuss how upper-layer information is encapsulated within an 802.11 frame format. We cover the three major 802.11 frame types and a majority of the 802.11 frame subtypes. We examine many MAC layer tasks, such as active scanning, and the specific 802.11 frames that are used to accomplish these tasks. An often misunderstood capability of 802.11 is the ERP protection mechanism. We describe how 802.11b and 802.11g stations can coexist in the same BSS by using either the RTS/CTS or CTS-to-Self protection mechanism. This protection mechanism is also the foundation for coexistence between 802.11n devices and earlier legacy devices. Near the end of this chapter we discuss legacy 802.11 power management and enhanced WMM-PS power management, which are methods used to save battery life.
Packets, Frames, and Bits
When learning about any technology, at times you need to step back and focus on the basics. If you have ever flown an airplane, you know that it is important, when things get difficult, to refocus on the number one priority, the main objective—and that is to fly the airplane. Navigation and communications are secondary to flying the airplane. When dealing with any complex technology, it is easy to forget the main objective; this is as true with 802.11 communications as it is with flying. With 802.11 communications, the main objective is to transfer user data from one computing device to another.
As data is processed in a computer and prepared to be transferred from one computer to another, it starts at the upper layers of the OSI model and moves down until it reaches the Physical layer, where it is ultimately transferred to the other devices. Initially, a user may want to transfer a word processing document from their computer to a shared network disk on another computer. This document will start at the Application layer and work its way down to the Physical layer, get transmitted to the other computer, and then work its way back up the layers of the OSI model to the Application layer on the other computer.
As data travels down the OSI model for the purpose of being transmitted, each layer adds header information to that data. This enables the data to be reassembled when it is received by the other computer. At the Network layer, an IP header is added to the data that came from layers 4–7. A layer 3 IP packet, or datagram, encapsulates the data from the higher layers. At the Data-Link layer, a MAC header is added and the IP packet is encapsulated inside a frame. Ultimately, when the frame reaches the Physical layer, a PHY header with more information is added to the frame.
Data is eventually transmitted as individual bits at the Physical layer. A bit is a binary digit, taking a value of either 0 or 1. Binary digits are a basic unit of communication in digital computing. A byte of information consists of 8 bits.
In this chapter, we discuss how upper-layer information moves down the OSI model through the Data-Link and Physical layers from an 802.11 perspective.
Data-Link Layer
The 802.11 Data-Link layer is divided into two sublayers. The upper portion is the IEEE 802.2 Logical Link Control (LLC) sublayer, which is identical for all 802-based networks, although it is not used by all IEEE 802 networks. The bottom portion of the Data-Link layer is the Media Access Control (MAC) sublayer. The 802.11 standard defines operations at the MAC sublayer.
MAC Service Data Unit
When the Network layer (layer 3) sends data to the Data-Link layer, that data is handed off to the LLC and becomes known as the MAC Service Data Unit (MSDU). The MSDU contains data from the LLC and layers 3–7. A simple definition of the MSDU is that it is the data payload that contains the IP packet plus some LLC data.
Later in this chapter, you will learn about the three major 802.11 frame types. 802.11 management and control frames do not carry upper-layer information. Only 802.11 data frames carry an MSDU payload in the frame body. The 802.11-2012 standard states that the maximum size of the MSDU is 2,304 bytes. The maximum frame body size is determined by the maximum MSDU size (2,304 octets) plus any overhead from encryption. With the ratification of the 802.11n-2009 amendment, aggregate MSDU (A-MSDU) was introduced. With A-MSDU, the maximum frame body size is determined by the maximum A-MSDU size of 3,839 or 7,935 octets, depending upon the STA's capability, plus any overhead from encryption. In Chapter 18, “802.11n,” you will learn more about A-MSDUs.
MAC Protocol Data Unit
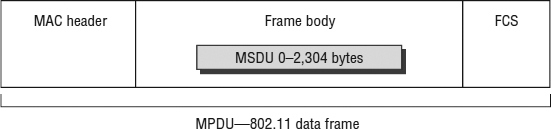
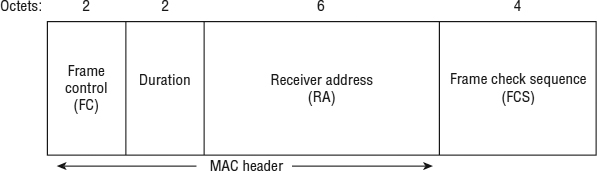
When the LLC sublayer sends the MSDU to the MAC sublayer, the MAC header information is added to the MSDU to identify it. The MSDU is now encapsulated in a MAC Protocol Data Unit (MPDU). A simple definition of an 802.11 MPDU is that it is an 802.11 frame. As shown in Figure 9.1, an 802.11 MPDU consists of the following three basic components:
MAC Header Frame control information, duration information, MAC addressing, and sequence control information are all found in the MAC header. Furthermore, QoS data frames contain specific QoS control information.
Frame Body The frame body component can be variable in size and contains information that is different depending on the frame type and frame subtype. The MSDU upper layer payload is encapsulated in the frame body. The MSDU layer 3–7 payload is protected when using encryption.
Frame Check Sequence (FCS) The FCS comprises a 32-bit cyclic-redundancy check (CRC) that is used to validate the integrity of received frames.
The 802.11 MAC header is discussed in more detail later in this chapter.
FIGURE 9.1 802.11 MPDU
At this point, the frame is ready to be passed onto the Physical layer, which will then further prepare the frame for transmission.
Physical Layer
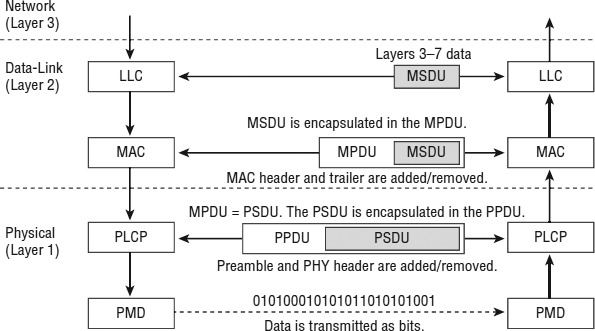
Similar to the way the Data-Link layer is divided into two sublayers, the Physical layer is also divided into two sublayers. The upper portion of the Physical layer is known as the Physical Layer Convergence Procedure (PLCP) sublayer, and the lower portion is known as the Physical Medium Dependent (PMD) sublayer. The PLCP prepares the frame for transmission by taking the frame from the MAC sublayer and creating the PLCP Protocol Data Unit (PPDU). The PMD sublayer then modulates and transmits the data as bits.
PLCP Service Data Unit
The PLCP Service Data Unit (PSDU) is a view of the MPDU from the Physical layer. The MAC layer refers to the frame as the MPDU, while the Physical layer refers to this same frame as the PSDU. The only difference is from which layer of the OSI model you are looking at the frame.
PLCP Protocol Data Unit
When the PLCP receives the PSDU, it then prepares the PSDU to be transmitted and creates the PLCP Protocol Data Unit (PPDU). The PLCP adds a preamble and PHY header to the PSDU. The preamble is used for synchronization between transmitting and receiving 802.11 radios. It is beyond the scope of this book and the CWNA exam to discuss all the details of the preamble and PHY header. When the PPDU is created, the PMD sublayer takes the PPDU and modulates the data bits and begins transmitting.
Figure 9.2 depicts a flowchart that shows the upper-layer information moving between the Data-Link and Physical layers.
FIGURE 9.2 Data-Link and Physical layers
802.11 and 802.3 Interoperability
As you learned in Chapter 7, “Wireless LAN Topologies,” the 802.11-2012 standard defines an integration service (IS) that enables delivery of MSDUs between the distribution system (DS) and a non-IEEE-802.11 local area network (LAN), via a portal. A simpler way of defining the integration service is to characterize it as a frame format transfer method. The portal is usually either an access point or a WLAN controller. As mentioned earlier, the payload of a wireless 802.11 data frame is the upper layer 3–7 information known as the MSDU. The eventual destination of this payload usually resides on a wired network infrastructure. Because the wired infrastructure is a different physical medium, an 802.11 data frame payload (MSDU) must be effectively transferred into an 802.3 Ethernet frame. For example, a VoWiFi phone transmits an 802.11 data frame to an access point. The MSDU payload of the frame is the VoIP packet with a final destination of a PBX server residing on the wired network. The job of the integration service is to first remove the 802.11 header and trailer and then encase the MSDU VoIP payload inside an 802.3 Ethernet frame. Normally, the integration service transfers frame payloads between an 802.11 and 802.3 medium. However, the IS could transfer an MSDU between the 802.11 medium and some sort of other medium, such as a cell phone data network. All of the IEEE 802 frame formats share similar characteristics, including the 802.11 frame format. Because the frames are similar, it makes it easier to translate the frames as they move from the 802.11 wireless network to the 802.3 wired network, and vice versa.
One of the differences between 802.3 Ethernet and 802.11 wireless frames is the frame size. 802.3 frames have a maximum size of 1,518 bytes with a maximum data payload of 1,500 bytes. If the 802.3 frames are 802.1Q tagged for VLANs and user priority, the maximum size of the 802.3 frame is 1,522 bytes with a data payload of 1,504 bytes. As you have just learned, 802.11 frames are capable of transporting frames with an MSDU payload of 2,304 bytes of upper-layer data. This means that as the data moves between the wireless and the wired network, the AP may receive a data frame that is too large for the wired network. This is rarely a problem thanks to the TCP/IP protocol suite. TCP/IP, the most common communications protocol used on networks, typically has an IP maximum transmission unit (MTU) size of 1,500 bytes. IP packets are usually 1,500 bytes based on the MTUs. When the IP packets are passed down to 802.11, even though the maximum size of the MSDU is 2,304 bytes, the size will be limited to the 1,500 bytes of the IP packets.
Much like in an 802.3 Ethernet frame, the header of an 802.11 frame contains MAC addresses. A MAC address is one of the following two types:
Individual Address Individual addresses are assigned to unique stations on the network (also known as a unicast address).
Group Address A multiple destination address (group address) could be used by one or more stations on a network. There are two kinds of group addresses:
Multicast-Group Address An address used by an upper-layer entity to define a logical group of stations is known as a multicast-group address.
Broadcast Address A group address that indicates all stations that belong to the network is known as a broadcast address. A broadcast address, all bits with a value of one, defines all stations on a local area network. In hexadecimal, the broadcast address would be FF:FF:FF:FF:FF:FF.
Although there are similarities, the MAC addressing used by 802.11 frames is much more complex than Ethernet frames. 802.3 frames have only a source address (SA) and destination address (DA) in the layer 2 header. As pictured in Figure 9.3, 802.11 frames have up to four address fields in the MAC header. 802.11 frames typically use only three of the MAC address fields. However, as we discussed in Chapter 7, an 802.11 frame sent within a wireless distribution system (WDS) requires all four MAC addresses.
Depending on whether the 802.11 traffic is upstream or downstream, the definition of each of the four MAC address fields in the layer 2 header will change. The five definitions are as follows:
Source Address (SA) The MAC address of the original sending station is known as the SA. The source address can originate from either a wireless station or the wired network.
Destination Address (DA) The MAC address that is the final destination of the layer 2 frame is known as the DA. The final destination may be a wireless station or could be a destination on the wired network such as a server or a router.
Transmitter Address (TA) The MAC address of an 802.11 radio that is transmitting the frame onto the half-duplex 802.11 medium is known as the TA.
Receiver Address (RA) The MAC address of the 802.11 radio that is intended to receive the incoming transmission from the transmitting station is known as the RA.
Basic Service Set Identifier (BSSID) This is the MAC address that is the layer 2 identifier of the basic service set (BSS). The BSSID is the MAC address of the AP's radio or is derived from the MAC address of the AP's radio if multiple basic service sets exist.
Certain frames may not contain some of the address fields. Even though the number of address fields is different, both 802.3 and 802.11 identify a source address and a destination address and use the same MAC address format. The first three octets are known as the Organizationally Unique Identifier (OUI), and the last three octets are known as the extension identifier.
FIGURE 9.3 802.11 MAC header
 For an in-depth look at 802.11 frame format, we suggest you read CWAP Certified Wireless Analysis Professional Official Study Guide: Exam PW0-270 (Sybex, 2011). It is beyond the scope of the CWNA exam to explain the purpose of every field in the 802.11 MAC header. However, a very important field that was discussed earlier in the book is the Duration/ID field. As you learned in Chapter 8, “802.11 Medium Access,” the duration value in the MAC header of a transmitting station is used to reset the NAV timer of other listening stations.
For an in-depth look at 802.11 frame format, we suggest you read CWAP Certified Wireless Analysis Professional Official Study Guide: Exam PW0-270 (Sybex, 2011). It is beyond the scope of the CWNA exam to explain the purpose of every field in the 802.11 MAC header. However, a very important field that was discussed earlier in the book is the Duration/ID field. As you learned in Chapter 8, “802.11 Medium Access,” the duration value in the MAC header of a transmitting station is used to reset the NAV timer of other listening stations.
Three 802.11 Frame Types
Unlike many wired network standards, such as the IEEE 802.3 Std, which uses a single data frame type, the IEEE 802.11 standard defines three major frame types: management, control, and data. These frame types are further subdivided into multiple subtypes. In Chapter 8, you learned about the optional medium contention method of Point Coordination Function (PCF) and the quality-of-service (QoS) medium contention method called Hybrid Coordination Function (HCF). Some of the frame subtypes are defined to perform functions associated with PCF. PCF is optional and, to date, there are no known APs that support this technology. We have indicated any subtypes that are solely defined for PCF by placing PCF only next to these subtypes but will not address or describe them. It is also beyond the scope of this book to discuss all the frame subtypes used for QoS in HCF. We have placed HCF next to these subtypes but will not address or describe them.
Management Frames
802.11 management frames make up a majority of the frame types in a WLAN. Management frames are used by wireless stations to join and leave the basic service set (BSS). They are not necessary on wired networks, since physically connecting or disconnecting the network cable performs this function. However, because wireless networking is an unbounded medium, it is necessary for the wireless station to first find a compatible WLAN, then authenticate to the WLAN (assuming they are allowed to connect), and then associate with the WLAN (typically with an AP) to gain access to the wired network (the distribution system).
Another name for an 802.11 management frame is Management MAC Protocol Data Unit (MMPDU). Management frames do not carry any upper-layer information. There is no MSDU encapsulated in the MMPDU frame body, which carries only layer 2 information fields and information elements. Information fields are fixed-length fields in the body of a management frame. Information elements are variable in length.
Following is a list of all 14 of the management frame subtypes as defined by the 802.11 standard and ratified amendments:
- Association request
- Association response
- Reassociation request
- Reassociation response
- Probe request
- Probe response
- Beacon
- Announcement traffic indication message (ATIM)
- Disassociation
- Authentication
- Deauthentication
- Action
- Action No ACK
- Timing advertisement
Control Frames
802.11 control frames assist with the delivery of the data frames and are transmitted at one of the basic rates. Control frames are also used to clear the channel, acquire the channel, and provide unicast frame acknowledgments. They contain only header information.
Following is a list of all nine of the control frame subtypes as defined by the 802.11 standard:
- Power Save Poll (PS-Poll)
- Request to send (RTS)
- Clear to send (CTS)
- Acknowledgment (ACK)
- Contention Free-End (CF-End) [PCF Only]
- CF-End + CF-ACK [PCF Only]
- Block ACK Request (BlockAckReq) [HCF Only]
- Block ACK (BlockAck) [HCF Only]
- Control wrapper
Data Frames
Most 802.11 data frames carry the actual data that is passed down from the higher-layer protocols. The layer 3 – 7 MSDU payload is normally encrypted for data privacy reasons. However, some 802.11 data frames carry no MSDU payload at all but do have a specific MAC control purpose within a BSS. Any data frames that do not carry an MSDU payload are not encrypted because a layer 3 – 7 data payload does not exist. There are a total of 15 data frame subtypes. The data subtype is usually referred to as the simple data frame. The simple data frame has MSDU upper-layer information encapsulated in the frame body. The integration service that resides in access points and WLAN controllers takes the MSDU payload of a simple data frame and transfers the MSDU into 802.3 Ethernet frames. Null function frames are sometimes used by client stations to inform the AP of changes in Power Save status.
The following is a list of all 15 of the data frame subtypes as defined by the 802.11 standard:
- Data (simple data frame)
- Null function (no data)
- Data + CF-ACK [PCF only]
- Data + CF-Poll [PCF only]
- Data + CF-ACK + CF-Poll [PCF only]
- CF-ACK (no data) [PCF only]
- CF-Poll (no data) [PCF only]
- CF-ACK + CF-Poll (no data) [PCF only]
- QoS Data [HCF]
- QoS Null (no data) [HCF]
- QoS Data + CF-ACK [HCF]
- QoS Data + CF-Poll [HCF]
- QoS Data + CF-ACK + CF-Poll [HCF]
- QoS CF-Poll (no data) [HCF]
- QoS CF-ACK + CF-Poll (no data) [HCF]
Beacon Management Frame
One of the most important frame types is the beacon management frame, commonly referred to as the beacon. Beacons are essentially the heartbeat of the wireless network. The AP of a basic service set sends the beacons while the clients listen for the beacon frames. Client stations only transmit beacons when participating in an independent basic service set (IBSS), also known as Ad Hoc mode. Each beacon contains a time stamp, which client stations use to keep their clocks synchronized with the AP. Because so much of successful wireless communications is based on timing, it is imperative that all stations be in sync with each other. By performing Exercise 9.1, you will be able to inspect the contents of a beacon frame using a wireless packet analyzer. Some of the information that can be found inside the body of a beacon frame is listed in Table 9.1.
TABLE 9.1 Beacon frame contents
| Information Type | Description |
| Time Stamp | Synchronization information |
| Spread Spectrum Parameter Sets | FHSS-, DSSS-, HR-DSSS-, ERP-, OFDM-, HT-, or VHT-specific information |
| Channel Information | Channel used by the AP or IBSS |
| Data Rates | Basic and supported rates |
| Service Set Capabilities | Extra BSS or IBSS parameters |
| SSID | Logical WLAN name |
| Traffic Indication Map (TIM) | A field used during the Power Save process |
| QoS Capabilities | Quality of service and Enhanced Distributed Channel Access (EDCA) information |
| Robust Security Network (RSN) Capabilities | TKIP or CCMP cipher information and authentication method |
| Vendor Proprietary Information | Vendor-unique or vendor-specific information |
The beacon frame contains all the necessary information for a client station to learn about the parameters of the basic service set before joining the BSS. Beacons are transmitted about 10 times per second. This interval can be configured on some APs, but it cannot be disabled.
Viewing Beacon Frames
- To perform this exercise, you need to first download the CWNA-CH9.PCAP file from the book's online resource area, which can be accessed at www.sybex.com/go/cwna4e.
- After the file is downloaded, you will need packet analysis software to open the file. If you do not already have a packet analyzer installed on your computer, you can download Wireshark from www.wireshark.org.
- Using the packet analyzer, open the CWNA-CH9.PCAP file. Most packet analyzers display a list of capture frames in the upper section of the screen, with each frame numbered sequentially in the first column.
- Click on one of the first eight frames. All of these frames are beacon frames.
- After selecting one of the beacon frames, in the lower section of the screen, browse through the information found inside the beacon frame body. You can expand a section by clicking on the plus sign next to the section.
Passive Scanning
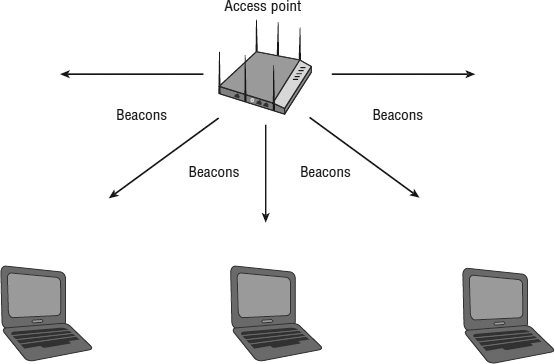
In order for a station to be able to connect to an AP, it must first discover an AP. A station discovers an AP by either listening for an AP (passive scanning) or searching for an AP (active scanning). In passive scanning, the client station listens for the beacon frames that are continuously being sent by the APs, as seen in Figure 9.4.
FIGURE 9.4 Passive scanning
The client station will listen for the beacons that contain the same SSID that has been preconfigured in the client station's software utility. When the station hears one, it can then connect to that WLAN. If the client station hears beacons from multiple APs with the same SSID, it will determine which AP has the best signal, and it will attempt to connect to that AP.
It is important to understand that active and passive scanning can coexist on a network. Also, a station can use either or both methods of scanning to discover the network. Also, when an independent basic service set is deployed, all of the stations in Ad Hoc mode take turns transmitting the beacons since there is no AP. Passive scanning occurs in an ad hoc environment, just as it does in a basic service set.
Active Scanning
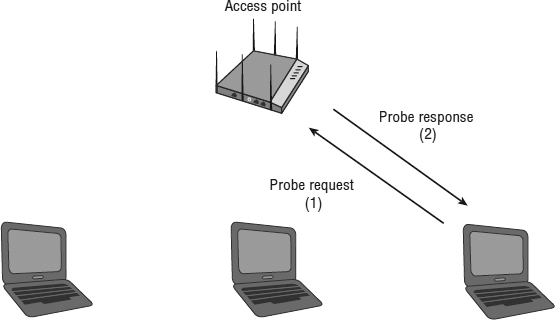
In addition to passively scanning for APs, client stations can actively scan for them. In active scanning, the client station transmits management frames known as probe requests. These probe requests either can contain the SSID of the specific WLAN that the client station is looking for or can look for any SSID. A client station that is looking for any SSID sends a probe request with the SSID field set to null. A probe request with the specific SSID information is known as a directed probe request. A probe request without the SSID information is known as a null probe request.
If a directed probe request is sent, all APs that support that specific SSID and hear the request should reply by sending a probe response. The information that is contained inside the body of a probe response frame is the same information that can be found in a beacon frame, with the exception of the traffic indication map (TIM). Just like the beacon frame, the probe response frame contains all of the necessary information for a client station to learn about the parameters of the basic service set before joining the BSS.
If a null probe request is sent, all APs that hear the request should reply by sending a probe response, as shown in Figure 9.5.
FIGURE 9.5 Active scanning
One drawback to passive scanning is that beacon management frames are broadcast only on the same channel as the AP. In contrast, active scanning uses probe request frames that are sent out across all available channels by the client station. If a client station receives probe responses from multiple APs, signal strength and quality characteristics are typically used by the client station to determine which AP has the best signal and thus which AP to connect to. The client station will sequentially send probe requests on each of the supported channels. In fact, it is common for a client station that is already associated to an AP and transmitting data to go off-channel and continue to send probe requests every few seconds across other channels. By continuing to actively scan, a client station can maintain and update a list of known APs, and if the client station needs to roam, it can typically do so faster and more efficiently.
How often a client station goes off-channel for active scanning purposes is proprietary. For example, an 802.11 radio in a mobile device such as a smartphone or tablet will probably send probe requests across all channels more frequently than an 802.11 radio in a laptop. By performing Exercise 9.2, you will be able to look at probe request and probe response frames.
Understanding Probe Requests and Probe Responses
- To perform this exercise, you need to first download the CWNA-CH9.PCAP file from the book's online resource area, which can be accessed at www.sybex.com/go/cwna4e.
- After the file is downloaded, you will need packet analysis software to open the file. If you do not already have a packet analyzer installed on your computer, you can download Wireshark from www.wireshark.org.
- Using the packet analyzer, open the CWNA-CH9.PCAP file. Most packet analyzers display a list of capture frames in the upper section of the screen, with each frame numbered sequentially in the first column.
- Scroll down the list of frames and click on frame #416, which is a probe request.
- In the lower section of the screen, look at the SSID field in the frame body and notice that this is a directed probe request.
- Click on frame #417, which is a probe response.
- In the lower section of the screen, browse through the information found inside the frame body and notice that the information is similar to a beacon frame.
- Click on frame #253, which is a probe request. Look at the SSID field in the frame body and notice that this is a null probe request, since it does not contain an SSID value.
- Click on frames #254, #255, and #256. Notice that there are three probe responses to the null probe request. Each probe response has a different SSID.
Authentication
Authentication is the first of two steps required to connect to the 802.11 basic service set. Both authentication and association must occur, in that order, before an 802.11 client can pass traffic through the AP to another device on the network.
Authentication is a process that is often misunderstood. When many people think of authentication, they think of what is commonly referred to as network authentication—entering a username and password in order to get access to the network. In this chapter, we are referring to 802.11 authentication. When an 802.3 device needs to communicate with other devices, the first step is to plug the Ethernet cable into the wall jack. When this cable is plugged in, the client creates a physical link to the wired switch and is now able to start transmitting frames. When an 802.11 device needs to communicate, it must first authenticate with the AP or with the other stations if it is configured for Ad Hoc mode. This authentication is not much more of a task than plugging the Ethernet cable into the wall jack. The 802.11 authentication merely establishes an initial connection between the client and the AP. Think of this as authenticating that both of the devices are valid 802.11 devices.
The original 802.11 standard defined two different methods of authentication: Open System authentication and Shared Key authentication. Shared Key authentication is simply not used anymore; however, Open System authentication is still used for backward compatibility reasons. The following two sections describe these two original authentication methods.
Open System Authentication
Open System authentication is the simpler of the two authentication methods. It provides authentication without performing any type of client verification. It is essentially an exchange of hellos between the client and the AP. It is considered a null authentication because no exchange or verification of identity takes place between the devices. Open System authentication occurs with an exchange of frames between the client and the AP, as shown in Exercise 9.3.
Wired Equivalent Privacy (WEP) security can be used with Open System authentication; however, WEP is used only to encrypt the upper-layer information of data frames and only after the client station is 802.11 authenticated and associated. Because of its simplicity, Open System authentication is also used in conjunction with more advanced network security authentication methods such as PSK authentication and 802.1X/EAP.
Using Open System Authentication
- To perform this exercise, you need to first download the CWNA-CH9.PCAP file from the book's online resource area, which can be accessed at www.sybex.com/go/cwna4e.
- After the file is downloaded, you will need packet analysis software to open the file. If you do not already have a packet analyzer installed on your computer, you can download Wireshark from www.wireshark.org.
- Using the packet analyzer, open the CWNA-CH9.PCAP file. Most packet analyzers display a list of capture frames in the upper section of the screen, with each frame numbered sequentially in the first column.
- Scroll down the list of frames and click on frame #418, which is an authentication request.
- In the lower section of the screen, look at the 802.11 MAC header and note the source address and destination address.
- Click on frame #419, which is an authentication response. Look at the 802.11 MAC header and note that the source address is the AP's BSSID and that the destination address is the MAC address of the client that sent the authentication request. Look at the frame body and note that authentication was successful.
Shared Key Authentication
Shared Key authentication uses WEP when authenticating client stations and requires that a static WEP key be configured on both the station and the AP. In addition to WEP being mandatory, authentication will not work if the static WEP keys do not match. The authentication process is similar to Open System authentication but includes a challenge and response between the AP and client station.
Shared Key authentication is a four-way authentication frame exchange:
- The client station sends an authentication request to the AP.
- The AP sends a cleartext challenge to the client station in an authentication response.
- The client station then encrypts the cleartext challenge and sends it back to the AP in the body of another authentication request frame.
- The AP then decrypts the station's response and compares it to the challenge text. If they match, the AP will respond by sending a fourth and final authentication frame the station, confirming the success. If they do not match, the AP will respond negatively. If the AP cannot decrypt the challenge, it will also respond negatively.
If Shared Key authentication is successful, the same static WEP key that was used during the Shared Key authentication process will also be used to encrypt the 802.11 data frames.
Although it might seem that Shared Key authentication is a more secure solution than Open System authentication, in reality Shared Key could be the bigger security risk. Anyone who captures the cleartext challenge phrase and then captures the encrypted challenge phrase in the response frame could potentially derive the static WEP key. If the static WEP key is compromised, a whole new can of worms has been opened because now all the data frames can be decrypted. Neither of the legacy authentication methods is considered strong enough for enterprise security and WEP is essentially a legacy encryption method that has been cracked. The more secure PSK and 802.1X/EAP authentication methods are discussed in Chapter 13, “802.11 Network Security Architecture.”
Association
After the station has authenticated with the AP, the next step is for it to associate with the AP. When a client station associates, it becomes a member of a basic service set (BSS). Association means that the client station can send data through the AP and on to the distribution system medium. The client station sends an association request to the AP, seeking permission to join the BSS. The AP sends an association response to the client, either granting or denying permission to join the BSS. In the body of the association response frame is an association identifier (AID), a unique association number given to every associated client. You will learn later in this chapter that the AID is used during power management.
Association occurs after Shared Key or Open System authentication, as you will see in Exercise 9.4. After a client station becomes a member of the BSS by completing association, the client will begin communications at upper layers and establish IP connectivity.
Understanding Association
- To perform this exercise, you need to first download the CWNA-CH9.PCAP file from the book's online resource area, which can be accessed at www.sybex.com/go/cwna4e.
- After the file is downloaded, you will need packet analysis software to open the file. If you do not already have a packet analyzer installed on your computer, you can download Wireshark from www.wireshark.org.
- Using the packet analyzer, open the CWNA-CH9.PCAP file. Most packet analyzers display a list of capture frames in the upper section of the screen, with each frame numbered sequentially in the first column.
- Scroll down the list of frames and click on frame #420, which is an association request. Look at the frame body.
- Click on frame #421, which is the association response. Look at the frame body and note that the association was successful and that the client received an AID number.
Authentication and Association States
The 802.11 station keeps two variables for tracking the authentication state and the association state. The states that are tracked are as follows:
- Authentication state: unauthenticated or authenticated
- Association state: unassociated or associated
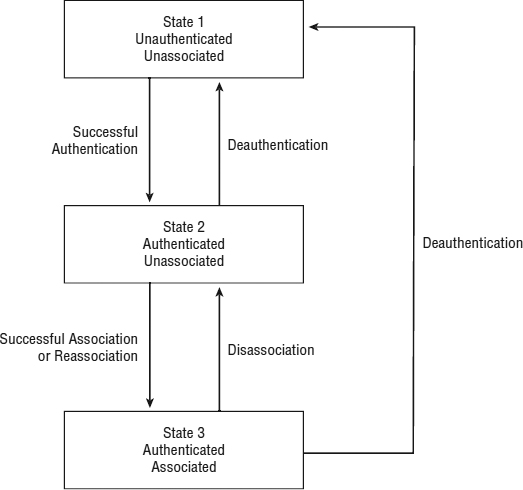
Together, these two variables create three possible states for the stations, as shown in Figure 9.6.
FIGURE 9.6 Authentication and association states
- State 1: initial start state, unauthenticated and unassociated
- State 2: authenticated and unassociated
- State 3: authenticated and associated (pending security mechanisms)
Because a station must authenticate before it can associate, it can never be unauthenticated and associated. Since the introduction of 802.11i security mechanisms, the IEEE 802.11-2012 standard now considers there to a forth state in the connection state machine (State 4: authenticated and associated - PSK or 802.1X security mechanisms completed.)
Basic and Supported Rates
As you have learned in earlier chapters, the 802.11-2012 standard defines supported rates for various RF technologies. For example, HR-DSSS (802.11b) radios are capable of supporting data rates of 1, 2, 5.5, and 11 Mbps. ERP (802.11g) radios are capable of supporting the HR-DSSS data rates but are also capable of supporting ERP-OFDM rates of 6, 9, 12, 18, 24, 36, 48, and 54 Mbps.
Specific data rates can be configured for any AP as required rates. The 802.11-2012 standard defines required rates as basic rates. In order for a client station to successfully associate with an AP, the station must be capable of communicating by using the configured basic rates that the AP requires. If the client station is not capable of communicating with all of the basic rates, the client station will not be able to associate with the AP and will not be allowed to join the BSS.
In addition to the basic rates, the AP defines a set of supported rates. This set of supported rates is advertised by the AP in the beacon frame and is also in some of the other management frames. The supported rates are data rates that the AP offers to a client station, but the client station does not have to support all of them.
Roaming
As wireless LANs grew to multiple APs, the 802.11 standard provided the ability for the client stations to transition from one AP to another while maintaining network connectivity for the upper-layer applications. This ability is known as roaming, although the 802.11 standard does not specifically define what roaming is.
The decision to roam is currently made by the client station. What actually causes the client station to roam is a set of proprietary rules specified by the manufacturer of the wireless radio, usually determined by the signal strength, noise level, and bit-error rate. As the client station communicates on the network, it continues to look for other APs and will authenticate to those that are within range. Remember, a station can be authenticated to multiple APs but associated to only one AP. As the client station moves away from the AP that it is associated with and the signal drops below a predetermined threshold, the client station will attempt to connect to another AP and roam from its current BSS to a new BSS. Some WLAN vendors attempt to encourage or discourage roaming by manipulating the client station with the use of management frames. However, it should be understood that ultimately the roaming decision is made by the client station.
As the client station roams, the original AP and the new AP should communicate with each other across the distribution system medium and help provide a clean transition between the two. Many manufacturers provide this handoff, but it is not officially part of the 802.11 standard, so each vendor does it using its own method. In WLAN controller–based solutions, the roaming handoff mechanisms usually occur within the WLAN controller. The roaming handoff mechanisms occur at the edge of the network when the conversation is between cooperative APs that do not require a WLAN controller.
Reassociation
When a client station decides to roam to a new AP, it will send a reassociation request frame to the new AP. It is called a reassociation not because you are reassociating to the AP but because you are reassociating to the SSID of the wireless network.
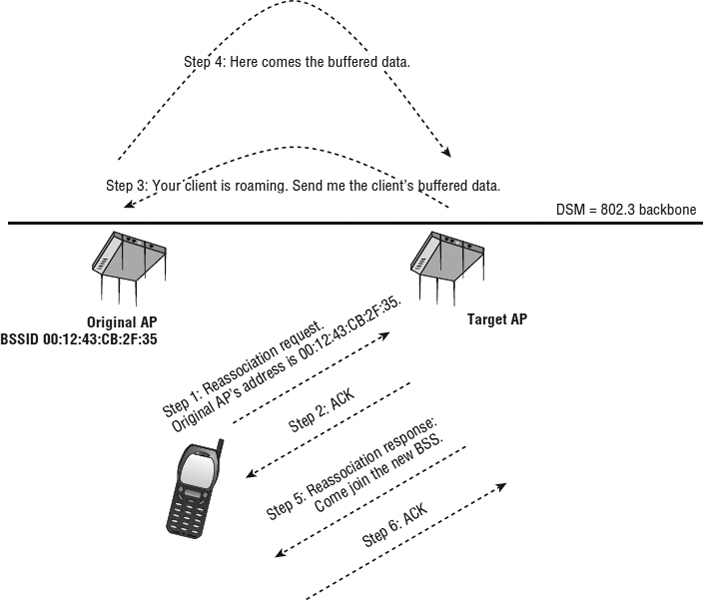
Reassociation occurs after the client and the AP move through a serious of steps, as described here:
- In the first step, the client station sends a reassociation request frame to the new AP.
As shown in Figure 9.7, the reassociation request frame includes the BSSID (MAC address) of the AP it is currently connected to (we will refer to this as the original AP).
FIGURE 9.7 Reassociation process
- The new AP then replies to the station with an ACK.
- The new AP attempts to communicate with the original AP by using the distribution system medium (DSM).
The new AP attempts to notify the original AP about the roaming client and requests that the original AP forward any buffered data. Please remember that any communications between APs via the DSM are not defined by the 802.11-2012 standard and are proprietary. In a controller-based WLAN solution, the inter-AP communications might occur within the controller. Cooperative APs which do not require a controller will communicate with each other at the edge of the network.
- If this communication is successful, the original AP will use the distribution system medium to forward any buffered data to the new AP.
- The new AP sends a reassociation response frame to the roaming client via the wireless medium.
- The client sends an ACK to the new AP, confirming that it received the forwarded data.
If the reassociation is not successful, the client will retain its connection to the original AP and either continue to communicate with it or attempt to roam to another AP. In Exercise 9.5, you can look at the reassociation request and reassociation response frames.
Understanding Reassociation
- To perform this exercise, you need to first download the CWNA-CH9.PCAP file from the book's online resource area, which can be accessed at www.sybex.com/go/cwna4e.
- After the file is downloaded, you will need packet analysis software to open the file. If you do not already have a packet analyzer installed on your computer, you can download Wireshark from www.wireshark.org.
- Using the packet analyzer, open the CWNA-CH9.PCAP file. Most packet analyzers display a list of capture frames in the upper section of the screen, with each frame numbered sequentially in the first column.
- Scroll down the list of frames and click on frame #658, which is a reassociation request. Look at the frame body.
- Click on frame #659, which is the reassociation response. Look at the frame body and note that the reassociation was successful and that the client received an AID number.
Disassociation
Disassociation is a notification, not a request. If a station wants to disassociate from an AP, or an AP wants to disassociate from stations, either device can send a disassociation frame. This is a polite way of terminating the association. A client will do so when you shut down the operating system. An AP might do so if it is being disconnected from the network for maintenance. Disassociation cannot be refused by either party, except when management frame protection (defined in 802.11w) is negotiated and the message integrity check (MIC) fails. If the disassociation frame is not heard by the other party, MAC management is designed to accommodate loss of communications.
Deauthentication
Like disassociation, a deauthentication frame is a notification and not a request. If a station wants to deauthenticate from an AP, or an AP wants to deauthenticate from stations, either device can send a deauthentication frame. Because authentication is a prerequisite for association, a deauthentication frame will automatically cause a disassociation to occur. Deauthentication cannot be refused by either party, except when management frame protection (defined in 802.11w) is negotiated and the message integrity check (MIC) fails.
ACK Frame
The ACK frame is one of the nine control frames and one of the key components of the 802.11 CSMA/CA medium access control method. Since 802.11 is a wireless medium that cannot guarantee successful data transmission, the only way for a station to know that a frame it transmitted was properly received is for the receiving station to notify the transmitting station. This notification is performed using an ACK.
The ACK is a simple frame consisting of 14 octets of information, as depicted in Figure 9.8. When a station receives data, it waits for a short period of time known as a short interframe space (SIFS). The receiving station copies the MAC address of the transmitting station from the data frame and places it in the Receiver Address (RA) field of the ACK frame. As you will see in Exercise 9.6, the receiving station then replies by transmitting the ACK. If all goes well, the station that sent the data frame receives the ACK with its MAC address in the RA field and now knows that the frame was received and was not corrupted. The delivery of every unicast frame must be verified, or a retransmission must take place. The ACK frame is used for delivery verification.
FIGURE 9.8 ACK control frame
 Every unicast frame must be followed by an ACK frame. If for any reason the unicast frame is corrupted, the 32-bit CRC known as the frame check sequence (FCS) fails and the receiving station will not send an ACK. If a unicast frame is not followed by an ACK, it is retransmitted. With a few rare exceptions, broadcast and multicast frames do not require acknowledgment.
Every unicast frame must be followed by an ACK frame. If for any reason the unicast frame is corrupted, the 32-bit CRC known as the frame check sequence (FCS) fails and the receiving station will not send an ACK. If a unicast frame is not followed by an ACK, it is retransmitted. With a few rare exceptions, broadcast and multicast frames do not require acknowledgment.
Understanding Acknowledgment
- To perform this exercise, you need to first download the CWNA-CH9.PCAP file from the book's online resource area, which can be accessed at www.sybex.com/go/cwna4e.
- After the file is downloaded, you will need packet analysis software to open the file. If you do not already have a packet analyzer installed on your computer, you can download Wireshark from www.wireshark.org.
- Using the packet analyzer, open the CWNA-CH9.PCAP file. Most packet analyzers display a list of capture frames in the upper section of the screen, with each frame numbered sequentially in the first column.
- Scroll down the list of frames and click on frame #1499, which is a data frame.
- Observe the frame exchanges between frame #1500 and frame #11178. Notice that all the unicast frames are being acknowledged by the receiving station.
Fragmentation
The 802.11-2012 standard allows for fragmentation of frames. Fragmentation breaks an 802.11 frame into smaller pieces known as fragments, adds header information to each fragment, and transmits each fragment individually. Although the same amount of actual data is being transmitted, each fragment requires its own header, and the transmission of each fragment is followed by a SIFS and an ACK. In a properly functioning 802.11 network, smaller fragments will actually decrease data throughput because of the MAC sublayer overhead of the additional header, SIFS, and ACK of each fragment. On the other hand, if the network is experiencing a large amount of data corruption, lowering the 802.11 fragmentation setting may improve data throughput. Fragmentation was sometimes used in legacy 802.11b/g networks but is no longer needed with 802.11n/ac networks that support frame aggregation.
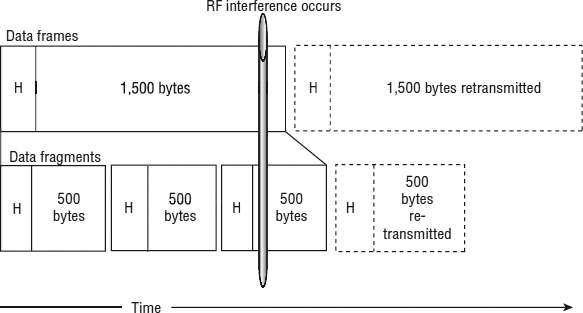
If an 802.11 frame is corrupted and needs to be retransmitted, the entire frame must be sent again. When the 802.11 frame is broken into multiple fragments, each fragment is smaller and transmits for a shorter period of time. If interference occurs, instead of an entire large frame becoming corrupted, it is likely that only one of the small fragments will become corrupted and only this one fragment will need to be retransmitted. Retransmitting the small fragment will take much less time than retransmitting the larger frame. If fragmentation is implemented, retransmission overhead may be reduced.
Figure 9.9 illustrates how smaller fragments reduce retransmission overhead. (Please note that this is a representation and not drawn to scale. Additionally, to simplify the illustration, ACKs were not included.) This illustration shows the transmission and retransmission of a large 1,500-byte frame above and the transmission and retransmission of smaller 500-byte fragments below. If there was no RF interference, only the solid-lined rectangles would need to be transmitted. Because of the additional headers (H) and the time between the fragments for each SIFS and ACK, the smaller fragments would take longer to transmit. However, if RF interference occurred, it would take less time to retransmit the smaller fragment than it would to retransmit the larger frame.
FIGURE 9.9 Frame fragmentation
 The transmission of a fragment is treated the same way as the transmission of a frame. Therefore, every fragment must participate in the CSMA/CA medium access and must be followed by an ACK. If a fragment is not followed by an ACK, it will be retransmitted.
The transmission of a fragment is treated the same way as the transmission of a frame. Therefore, every fragment must participate in the CSMA/CA medium access and must be followed by an ACK. If a fragment is not followed by an ACK, it will be retransmitted.
Not all wireless LAN adapters allow you to adjust the fragmentation settings. If you do set your wireless LAN adapter to use a smaller fragment size, you must realize that as you roam between APs and as you move between networks, all of your 802.11 frames will be fragmented using the setting you have configured. This means that if you roam to a location where there is no interference, your station will still be using the smaller frame fragments and will actually perform worse than if you had left the fragmentation value at its largest setting.
Protection Mechanism
The 802.11-2012 standard mandates support for both DSSS and OFDM technologies for ERP radios (802.11g). When HR-DSSS (802.11b) client stations need to communicate in a basic service set with an ERP (802.11g) AP and ERP (802.11g) client stations, the 802.11g devices have to provide compatibility for the slower 802.11b devices. ERP APs must also be backward compatible with legacy DSSS (802.11) client stations. This environment is often referred to as mixed mode. Contrary to what some people believe, the 802.11g devices do not simply switch to 802.11b mode and communicate using 802.11b data rates. In order for 802.11g, 802.11b, and legacy 802.11 stations to coexist within the same BSS, the 802.11g devices enable what is referred to as the protection mechanism, also known as 802.11g Protected mode. In Chapter 5, “IEEE 802.11 Standards,” you learned that vendors often offer three configuration modes for 802.11g APs:
802.11b-Only Mode When an 802.11g AP is running in this operational mode, support for DSSS and HR-DSSS technology is solely enabled. Effectively, the AP has been configured to be an 802.11b AP. Legacy 802.11 DSSS clients, 802.11b HR-DSSS clients, 802.11g clients using ERP-DSSS, and 802.11n clients using one of these three methods will all be able to communicate with the AP at data rates of 1, 2, 5.5, and 11 Mbps. Aggregate throughput will be the same as achieved in an 802.11b network.
802.11g-Only Mode APs configured as g-only will communicate with only 802.11g client stations using ERP-OFDM technology. Support for 802.11 DSSS and 802.11b HR-DSSS is disabled; therefore, 802.11b HR-DSSS clients and legacy 802.11 DSSS clients will not be able to associate with the AP. Since 802.11n devices are backward compatible, they will be able to connect, but only using ERP-OFDM technology. Aggregate throughput will be equivalent to what can be achieved in an 802.11a network. For example, the aggregate throughput of an AP with a data rate of 54 Mbps might be about 19 Mbps to 20 Mbps. G-only wireless LANs are sometimes referred to as Pure G networks.
802.11b/g Mode This is the default operational mode of most 802.11g APs and is often called mixed mode. Support for DSSS, HR-DSSS, and OFDM is enabled. Legacy 802.11 DSSS clients and 802.11b HR-DSSS clients will be able to communicate with the AP at data rates of 1, 2, 5.5, and 11 Mbps. The ERP (802.11g) clients will communicate with the AP by using the ERP-OFDM data rates of 6, 9, 12, 18, 24, 36, 48, and 54 Mbps. 802.11n clients will also be able to communicate with the AP, although they will have to use ERP also.
You need to understand that these vendor configurations are not part of the 802.11-2012 standard. Although most vendors do indeed support these configurations, the standard mandates support for 802.11 Clause 16 devices, 802.11b Clause 17 devices, and 802.11g Clause 19 devices within the ERP basic service set.
In Chapter 8, you learned that one of the ways of preventing collisions is for the stations to set a countdown timer known as the network allocation vector (NAV). This notification is known as NAV distribution. NAV distribution is done through the Duration/ID field that is part of the data frame. When a data frame is transmitted by a station, the Duration/ID field is used by the listening stations to set their NAV timers. Unfortunately, this is not inherently possible in a mixed-mode environment. If an 802.11g device were to transmit a data frame, 802.11b devices would not be able to interpret the data frame or the Duration/ID value because the 802.11b HR-DSSS devices are not capable of understanding 802.11g ERP-OFDM transmissions. The 802.11b devices would not set their NAV timers and could incorrectly believe that the medium is available. To prevent this from happening, the 802.11g ERP stations switch into what is known as Protected mode.
In a mixed-mode environment, when an 802.11g device wants to transmit data, it will first perform a NAV distribution by transmitting a request to send/clear to send (RTS/CTS) exchange with the AP or by transmitting a CTS-to-Self using a data rate and modulation method that the 802.11b HR-DSSS stations can understand. The RTS/CTS or CTS-to-Self will hopefully be heard and understood by all of the 802.11b and 802.11g stations. The RTS/CTS or CTS-to-Self will contain a Duration/ID value that will be used by all of the listening stations to set their NAV timers. To put it simply, using a slow transmission that all stations can understand, the ERP (802.11g) device notifies all the stations to reset their NAV values. After the RTS/CTS or CTS-to-Self has been used to reserve the medium, the 802.11g station can transmit a data frame by using OFDM modulation without worrying about collisions with 802.11b HR-DSSS or legacy 802.11 DSSS stations.
Within an ERP basic service set, the HR-DSSS (802.11b) and legacy 802.11 DSSS stations are known as non-ERP stations. The purpose of the protection mechanism is that ERP stations (802.11g) can coexist with non-ERP stations (802.11b and 802.11 legacy) within the same BSS. This allows the ERP stations to use the higher ERP-OFDM data rates to transmit and receive data yet still maintain backward compatibility with the older legacy non-ERP stations.
So what exactly triggers the protection mechanism? When an ERP (802.11g) AP decides to enable the use of a protection mechanism, it needs to notify all of the ERP (802.11g) stations in the BSS that protection is required. It accomplishes this by setting the NonERP Present bit, and the ERP stations will know that Protected mode is required. There are an assortment of reasons why Protected mode may be enabled. The following are three scenarios that can trigger protection in an ERP basic service set:
- If a non-ERP STA associates with an ERP AP, the ERP AP will enable the NonERP_Present bit in its own beacons, enabling protection mechanisms in its BSS. In other words, an HR-DSSS (802.11b) client association will trigger protection.
- If an ERP AP hears a beacon from an AP where the supported data rates contain only 802.11b or 802.11 DSSS rates, it will enable the NonERP_Present bit in its own beacons, enabling protection mechanisms in its BSS. In simpler terms, if an 802.11g AP hears a beacon frame from an 802.11 or 802.11b AP or ad hoc client, the protection mechanism will be triggered.
- If an ERP AP hears a management frame (other than a probe request) where the supported rate includes only 802.11 or 802.11b rates, the NonERP_Present bit may be set to 1.
How Does 802.11b Affect 802.11g Throughput?
A common misconception is that 802.11g radios revert to 802.11b data rates when the protection mechanism is used. In reality, ERP (802.11g) radios still transmit data at the higher ERP-OFDM rates. However, when an HR-DSSS (802.11b) station causes an ERP (802.11g) BSS to enable the protection mechanism, a large amount of RTS/CTS or CTS-to-Self overhead is added prior to every ERP-OFDM data transmission. The aggregate data throughput loss is caused by the extra overhead and not by using slower 802.11b rates. A data rate of 54 Mbps usually will provide about 18 Mbps to 20 Mbps of aggregate throughput when protection is not enabled. After protection is enabled, the overhead will reduce the aggregate data throughput to below 13 Mbps—and possibly as low as 9 Mbps.
Because 802.11b/g networks are now considered legacy technology, the degradation of throughput caused by the ERP protection mechanism is usually no longer an issue because of the high data rates defined by 802.11n and 802.11ac. The 802.11n and 802.11ac amendments introduced additional transmission technologies that must also be backward compatible with 802.11a/b/g technology. Therefore, 802.11n and 802.11ac also use protection mechanisms. 802.11n/ac protection mechanisms also create MAC-layer overhead; however, the effective decrease in throughput is rarely noticed due to the higher data rates used by 802.11n and 802.11ac radios.
RTS/CTS
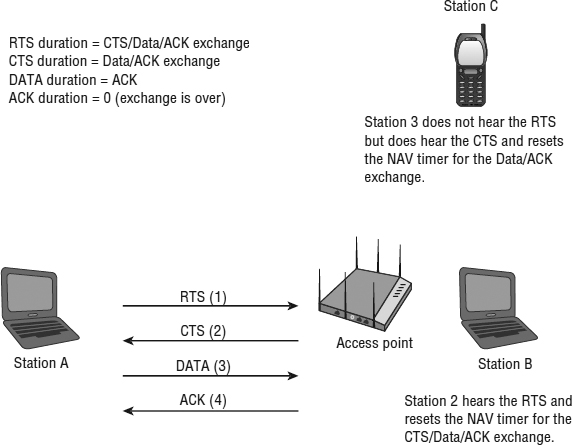
In order for a client station to participate in a BSS, it must be able to communicate with the AP. This is straightforward and logical; however, it is possible for the client station to be able to communicate with the AP but not be able to hear or be heard by any of the other client stations. This can be a problem because, as you may recall, a station performs collision avoidance by setting its NAV when it hears another station transmitting (virtual carrier sense) and by listening for RF (physical carrier sense). If a station cannot hear the other stations, or cannot be heard by the other stations, there is a greater likelihood that a collision can occur. Request to send/clear to send (RTS/CTS) is a mechanism that performs a NAV distribution and helps prevent collisions from occurring. This NAV distribution reserves the medium prior to the transmission of the data frame.
Now, let's look at the RTS/CTS from a slightly more technical perspective. This will be a basic explanation, because an in-depth explanation is beyond the scope of the exam. When RTS/CTS is enabled on a station, every time the station wants to transmit a frame it must perform an RTS/CTS exchange prior to the normal data transmissions. When the transmitting station goes to transmit data, it first sends an RTS frame. The duration value of the RTS frame resets the NAV timers of all listening stations so that they must wait until the CTS, DATA, and ACK have been transmitted. The receiving station, the AP, then sends a CTS, which is also used for NAV distribution. The duration value of the CTS frame resets the NAV timer of all listening stations so that they must wait until the DATA and ACK have been transmitted.
As you can see in Figure 9.10, the duration value of the RTS frame represents the time, in microseconds, that is required to transmit the CTS/DATA/ACK exchange plus three SIFS intervals. The duration value of the CTS frame represents the time, in microseconds, that is required to transmit the DATA/ACK exchange plus two SIFS intervals. If any station did not hear the RTS, it should hear the CTS. When a station hears either the RTS or the CTS, it will set its NAV to the value provided. At this point, all stations in the BSS should have their NAV set, and the stations should wait until the entire data exchange is complete. Figure 9.11 depicts an RTS/CTS exchange between a client station and an AP.
FIGURE 9.10 RTS/CTS duration values
RTS/CTS is used primarily in two situations. It can be used when a hidden node exists (this is covered in Chapter 12), or it can be used automatically as a protection mechanism when different technologies such as 802.11b/g/n coexist in the same basic service set. Figure 9.11 depicts the RTS/CTS frame exchange.
CTS-to-Self
CTS-to-Self is used strictly as a protection mechanism for mixed-mode environments. One of the benefits of using CTS-to-Self over RTS/CTS as a protection mechanism is that the throughput will be higher because fewer frames are being sent.
When a station using CTS-to-Self wants to transmit data, it performs a NAV distribution by sending a CTS frame. This CTS notifies all other stations that they must wait until the DATA and ACK have been transmitted. Any station that hears the CTS will set their NAV to the value provided.
Since CTS-to-Self is used as a protection mechanism for mixed-mode environments, the ERP (802.11g) station will transmit the CTS by using DSSS technology that all stations can understand. Then the DATA and the ACK will be transmitted at a faster 802.11g speed by using ERP-OFDM data rates.
FIGURE 9.11 RTS/CTS frame exchange
 CTS-to-Self is better suited for use by an AP. It is important to make sure that all stations hear the CTS to reserve the medium, and this is most likely to occur if it is being sent by an AP. If a client station were to use CTS-to-Self, there is a chance that another client station on the opposite side of the BSS might be too far away from the CTS-to-Self and would not realize that the medium is busy. Even though this is true, from our experience, it appears that most use CTS-to-Self on client stations to reserve the medium instead of RTS/CTS. CTS-to-Self is used because of the decreased overhead when compared with RTS/CTS. Some vendors allow the user to select whether the client station uses RTS/CTS or CTS-to-Self when in Protected mode.
CTS-to-Self is better suited for use by an AP. It is important to make sure that all stations hear the CTS to reserve the medium, and this is most likely to occur if it is being sent by an AP. If a client station were to use CTS-to-Self, there is a chance that another client station on the opposite side of the BSS might be too far away from the CTS-to-Self and would not realize that the medium is busy. Even though this is true, from our experience, it appears that most use CTS-to-Self on client stations to reserve the medium instead of RTS/CTS. CTS-to-Self is used because of the decreased overhead when compared with RTS/CTS. Some vendors allow the user to select whether the client station uses RTS/CTS or CTS-to-Self when in Protected mode.
Data Frames
As mentioned earlier, there are 15 subtypes of data frames. The most common data frame is the simple data frame, which has MSDU upper-layer information encapsulated in the frame body. The integration service that resides in APs and WLAN controllers takes the MSDU payload of a simple data frame and transfers the MSDU into 802.3 Ethernet frames. For data privacy reasons, the MSDU data payload should usually be encrypted.
The null function frame is used by client stations to inform the AP of changes in Power Save status by changing the Power Management bit. When a client station decides to go off-channel for active scanning purposes, the client station will send a null function frame to the AP with the Power Management bit set to 1. As demonstrated in Exercise 9.7, when the Power Management bit is set to 1, the AP buffers all of that client's 802.11 frames. When the client station returns to the AP's channel, the station sends another null function frame with the Power Management bit set to 0. The AP then transmits the client's buffered frames. Some vendors also use the null function frame to implement proprietary power-management methods.
Using Data Frames
- To perform this exercise, you need to first download the CWNA-CH9.PCAP file from the book's online resource area, which can be accessed at www.sybex.com/go/cwna4e.
- After the file is downloaded, you will need packet analysis software to open the file. If you do not already have a packet analyzer installed on your computer, you can download Wireshark from www.wireshark.org.
- Using the packet analyzer, open the CWNA-CH9.PCAP file. Most packet analyzers display a list of capture frames in the upper section of the screen, with each frame numbered sequentially in the first column.
- Scroll down the list of frames and click on frame #2001, which is an unencrypted simple data frame. Look at the frame body and notice the upper-layer information such as IP addresses and UDP port. This information is visible because no encryption is being used.
- Click on frame #689, which is a null function frame. Look at the 802.11 MAC header. Look in the Frame Control field and note that the Power Management bit is set to 1. The AP will now buffer the client's traffic.
Power Management
One of the main uses of wireless networking is to provide mobility for the client station. Client mobility goes hand in hand with battery-operated client stations. When battery-operated devices are used, one of the biggest concerns is how long the battery will last until it needs to be recharged. To increase the battery time, a bigger, longer-lasting battery can be used or power consumption can be decreased. The 802.11 standard includes a power-management feature that can be enabled to help increase battery life. Battery life is extremely important for smartphones, tablets, handheld scanners, and VoWiFi phones. The battery life of mobile devices usually needs to last at least one 8-hour work shift. The two legacy power-management modes supported by the 802.11 standard are Active mode and Power Save mode. 802.11 power-management methods have also been enhanced by both the ratified 802.11e amendment and the ratified 802.11n-2009 amendment.
Active Mode
Active mode is a legacy power-management mode used by very old 802.11 stations. When a station is set for Active mode, the wireless station is always ready to transmit or receive data. Active mode is sometimes referred to as Continuous Aware mode, and it provides no battery conservation. In the MAC header of an 802.11 frame, the Power Management field is 1 bit in length and is used to indicate the power-management mode of the station. A value of 0 indicates that the station is in Active mode. Stations running in Active mode will achieve higher throughput than stations running in Power Save mode, but the battery life will typically be much shorter.
 Stations that are always connected to a power source should be configured to use Active mode.
Stations that are always connected to a power source should be configured to use Active mode.
Power Save Mode
Power Save mode is an optional mode for 802.11 stations. When a client station is set for Power Save mode, it will shut down some of the transceiver components for a period of time to conserve power. The wireless radio basically takes a short nap. The station indicates that it is using Power Save mode by changing the value of the Power Management bit to 1. When the Power Management bit is set to 1, the AP is informed that the client station is using power management, and the AP buffers all of that client's 802.11 frames.
Traffic Indication Map
If a station is part of a basic service set, it will notify the AP that it is enabling Power Save mode by changing the Power Management field to 1. When the AP receives a frame from a station with this bit set to 1, the AP knows that the station is in Power Save mode. If the AP then receives any data that is destined for the station in Power Save mode, the AP will store the information in a buffer. Any time a station associates to an AP, the station receives an association identifier (AID). The AP uses this AID to keep track of the stations that are associated and the members of the BSS. If the AP is buffering data for a station in Power Save mode, when the AP transmits its next beacon, the AID of the station will be seen in a field of the beacon frame known as the traffic indication map (TIM). The TIM field is a list of all stations that have undelivered data buffered on the AP, waiting to be delivered. Every beacon will include the AID of the station until the data is delivered.
After the station notifies the AP that it is in Power Save mode, the station shuts down part of its transceiver to conserve energy. A station can be in one of two states, either awake or doze:
- During the awake state, the client station can receive frames and transmit frames.
- During the doze state, the client station cannot receive or transmit any frames and operates in a very low power state to conserve power.
Because beacons are transmitted at a consistent predetermined interval known as the target beacon transmission time (TBTT), all stations know when beacons will occur. The station will remain asleep for a short period of time and awaken in time to hear a beacon frame. The station does not have to awaken for every beacon. To conserve more power, the station can sleep for a longer period of time and then awaken in time to hear an upcoming beacon. How often the client station awakens is based on a client variable called the listen interval and is usually vendor specific.
When the station receives the beacon, it checks to see whether its AID is set in the TIM, indicating that a buffered unicast frame waits. If so, the station will remain awake and will send a PS-Poll frame to the AP. When the AP receives the PS-Poll frame, it will send the buffered unicast frame to the station. The station will stay awake while the AP transmits the buffered unicast frame. When the AP sends the data to the station, the station needs to know when all of the buffered unicast data has been received so that it can go back to sleep. Each unicast frame contains a 1-bit field called the More Data field. When the station receives a buffered unicast frame with the More Data field set to 1, the station knows that it cannot go back to sleep yet because there is some more buffered data that it has not yet received. When the More Data field is set to 1, the station knows that it needs to send another PS-Poll frame and wait to receive the next buffered unicast frame.
After all of the buffered unicast frames have been sent, the More Data field in the last buffered frame will be set to 0, indicating that there is currently no more buffered data, and the station will go back to sleep. The AP will set the value of the station's AID bit to 0, and when the next TBTT arrives, the AP will send a beacon. The station will remain asleep for a short period of time and again awaken in time to hear a beacon frame. When the station receives the beacon, it will again check to see whether its AID is set in the TIM. Assuming that there are no buffered unicast frames awaiting this station, the station's AID will not be set to 1 in the TIM and the station can simply go back to sleep until it is time to wake up and check again.
Delivery Traffic Indication Message
In addition to unicast traffic, network traffic includes multicast and broadcast traffic. Because multicast and broadcast traffic is directed to all stations, the BSS needs to provide a way to make sure that all stations are awake to receive these frames. A delivery traffic indication map (DTIM) is used to ensure that all stations using power management are awake when multicast or broadcast traffic is sent. DTIM is a special type of TIM. A TIM or DTIM is transmitted as part of every beacon.
A configurable setting on the AP called the DTIM interval determines how often a DTIM beacon is transmitted. A DTIM interval of 3 means that every third beacon is a DTIM beacon, whereas a DTIM interval of 1 means that every beacon is a DTIM beacon. Every beacon contains DTIM information that informs the stations when the next DTIM will occur. A DTIM value of 0 indicates that the current TIM is a DTIM. All stations will wake up in time to receive the beacon with the DTIM. If the AP has multicast or broadcast traffic to be sent, it will transmit the beacon with the DTIM and then immediately send the multicast or broadcast data.
After the multicast or broadcast data is transmitted, if a station's AID was in the DTIM, the station will remain awake and will send a PS-Poll frame and proceed with retrieving its buffered unicast traffic from the AP. If a station did not see its AID in the DTIM, or if its AID was set to 0, the station can go back to sleep.
The DTIM interval is important for any application that uses multicasting. For example, many VoWiFi vendors support push-to-talk capabilities that send VoIP traffic to a multicast address. A misconfigured DTIM interval would cause performance issues during a push-to-talk multicast.
Announcement Traffic Indication Message
If a station is part of an IBSS, there is no central AP to buffer data while the stations are in Power Save mode. A station will notify the other stations that it is enabling Power Save mode by changing the Power Management field to 1. When the station transmits a frame with this field set to 1, the other stations know to buffer any data that they may have for this station because this station is now in Power Save mode.
Periodically, all stations must wake up and notify each other if any station has buffered data that needs to be delivered to another station. This recurring period of time when all devices must be awake to exchange this information is known as the announcement traffic indication message (ATIM) window. During the ATIM window, if a station has buffered data for another station, it will send a unicast frame known as an ATIM frame to the other station. This unicast frame informs the station that it must stay awake until the next ATIM window so that it can receive the buffered data. Any station that either has buffered data for another station or has received an ATIM will stay awake so that the buffered data can be exchanged. All of the other stations can go to sleep and wait until the next ATIM window to go through this process again.
When the ATIM window expires, the nodes that have stayed awake go through the usual CSMA/CA process to exchange the unsent data. If a station is unable to transmit the data during this time, it will simply send another ATIM frame during the next ATIM window and then attempt to send the data during the following CSMA/CA period.
Do not confuse the ATIM frame with the TIM field. The ATIM is a frame used for power management by ad hoc clients not communicating through an AP. The TIM is a field in the beacon frame that tells client stations in Power Management mode that the AP has buffered unicast frames for the clients.
WMM Power Save and U-APSD
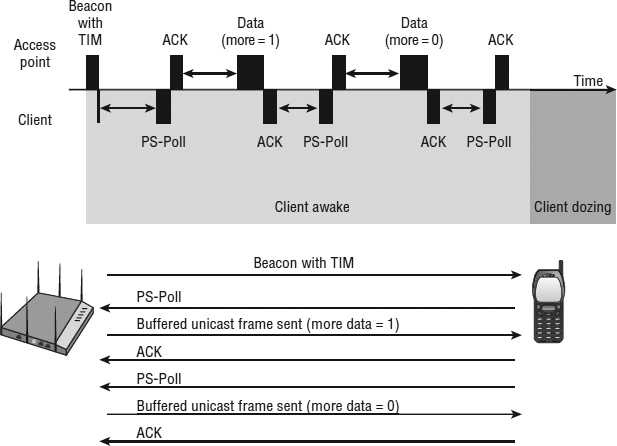
The main focus of the 802.11e amendment, which is now part of the 802.11-2012 standard, is quality of service. However, the IEEE 802.11e amendment also introduced an enhanced power-management method called automatic power save delivery (APSD). The two APSD methods that are defined are scheduled automatic power save delivery (S-APSD) and unscheduled automatic power save delivery (U-APSD). The S-APSD power-management method is beyond the scope of this book. The Wi-Fi Alliance's WMM Power Save (WMM-PS) certification is based on U-APSD. WMM-PS is an enhancement over the legacy power saving mechanisms already discussed. The goal of WMM-PS is to have client devices spend more time in a doze state and consume less power. WMM-PS is also designed to minimize latency for time-sensitive applications such as voice during the power-management process.
The legacy power-management methods have several limitations. As shown in Figure 9.12, a client using legacy power management must first wait for a beacon with a TIM before the client can request buffered unicast frames. The client must also send a unique PS-Poll frame to the AP to request every single buffered unicast frame. This ping-pong power-management method increases the latency of time-sensitive applications such as voice. The clients must also stay awake during the ping-pong process, which results in reduced battery life. In addition, the amount of time that the clients spend dozing is determined by the vendor's driver and not by the application traffic.
FIGURE 9.12 Legacy power management
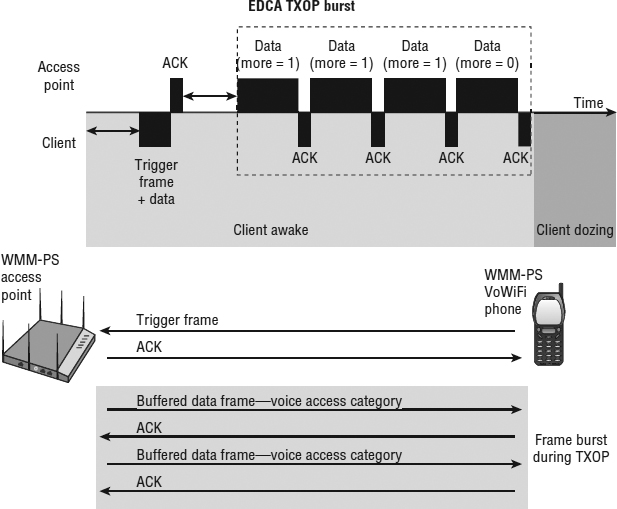
WMM-PS uses a trigger mechanism to receive buffered unicast traffic based on WMM access categories. You learned in Chapter 8 that 802.1D priority tags from the Ethernet side are used to direct traffic to four different WMM access-category priority queues. The access-category queues are voice, video, best effort, and background. As shown in Figure 9.13, the client station sends a trigger frame related to a WMM access category to inform the AP that the client is awake and ready to download any frames that the AP may have buffered for that access category. The trigger frame can also be an 802.11 data frame, thus eliminating the need for a separate PS-Poll frame. The AP will then send an ACK to the client and proceed to send a frame burst of buffered application traffic during a transmit opportunity (TXOP).
FIGURE 9.13 WMM-PS
The advantages of this enhanced power-management method include the following:
- Applications now control the power-save behavior by setting doze periods and sending trigger frames. VoWiFi phones will obviously send triggers to the AP frequently during voice calls, whereas a laptop radio using a data application will have a longer doze period.
- The trigger and delivery method eliminates the need for PS-Poll frames.
- The client can request to download buffered traffic and does not have to wait for a beacon frame.
- All the downlink application traffic is sent in a faster frame burst during the AP's TXOP.
A couple of conditions have to be met for a Wi-Fi client to use the enhanced WMM-PS mechanisms:
- The client is Wi-Fi CERTIFIED for WMM-PS.
- The AP is Wi-Fi CERTIFIED for WMM-PS.
It should be noted that applications that do not support WMM-PS can still coexist with WMM Power Save–enabled applications. The data from the other applications will be delivered with legacy power-save methods.
 A white paper from the Wi-Fi Alliance called “Wi-Fi CERTIFIED for WMM®-Power Save: Support for Advanced Power Save for Mobile and Portable Devices in Wi-Fi® Networks (2005)” is available for download at
A white paper from the Wi-Fi Alliance called “Wi-Fi CERTIFIED for WMM®-Power Save: Support for Advanced Power Save for Mobile and Portable Devices in Wi-Fi® Networks (2005)” is available for download at
www.wi-fi.org/discover-wi-fi/wi-fi-certified-wmm-programs.
This white paper is highly recommended extra reading for the CWNA exam.
802.11n Power Management
The ratified 802.11n-2009 amendment also defines two new power-management methods. The first method is called spatial multiplexing power save (SM power save). The purpose of SM power save is to enable a MIMO 802.11n device to power down all but one of its radio chains. The second new power-management method, power save multi-poll (PSMP), has also been defined for use for HT (802.11n) radios. PSMP is an extension of automatic power save delivery (APSD), which was defined by the 802.11e amendment. A more detailed discussion about these two power-management methods is presented in Chapter 18.
Summary
This chapter covered key areas of the MAC architecture:
- 802.11 frame format
- Major 802.11 frame types
- 802.11 frame subtypes
- Fragmentation
- ERP protection mechanism
- Power management
It is important to understand the makeup of the three major 802.11 frame types and the purpose of each individual 802.11 frame and how they are used in scanning, authentication, association, and other MAC processes. You should understand the need for an ERP protection mechanism. Without one, mixed-mode networks would not be able to function. Both RTS/CTS and CTS-to-Self provide ERP (802.11g) protection mechanisms.
To help manage battery life, power management can be configured on a wireless station. Active mode provides no battery conservation of any kind, whereas Power Save mode can be invaluable for increasing the battery life of laptop and handheld computing devices. WMM and 802.11n have also enhanced power-management capabilities. We discussed the following power-management pieces in this chapter:
- Traffic indication map (TIM)
- Delivery traffic indication message (DTIM)
- Announcement traffic indication message (ATIM)
- WMM Power Save (WMM-PS)
Exam Essentials
Explain the differences between a PPDU, PSDU, MPDU, and MSDU. Understand at which layer of the OSI model each data unit operates and what each data unit comprises.
Understand the similarities and differences of 802.11 frames and 802.3 frames. The IEEE created both of these frame types. 802.11 and 802.3 frames share similar and different properties. Know how they compare to each other.
Know the three major 802.11 frame types. Make sure you know the function of the management, control, and data frames. Know what makes the major frame types different. Data frames contain an MSDU, whereas management and control frames do not. Understand the purpose of each individual frame subtype.
Know the media access control (MAC) process and all of the frames that are used during this process. Understand the function of each of the following: active scanning, passive scanning, beacon, probe request, probe response, authentication, association, reassociation, disassociation, and deauthentication.
Know the importance of the ACK frame for determining that a unicast frame was received and uncorrupted. Understand that after a unicast frame is transmitted, there is a short interframe space (SIFS) and then the receiving station replies by transmitting an ACK. If this process is completed successfully, the transmitting station knows the frame was received and was not corrupted.
Know the benefits and detriments of fragmentation. By default, fragmentation adds overhead, and fragmented frames are inherently slower than unfragmented frames. If RF interference exists, fragmentation can reduce the amount of retransmitted overhead, thus actually increasing the data throughput. If fragmentation does increase throughput, this is a clear indication of a transmission problem such as multipath.
Understand the importance of ERP protection mechanisms and how they function. Protected mode allows ERP (802.11g), HR-DSSS (802.11b), and legacy DSSS devices to coexist within the same BSS. Protected mode can be provided by RTS/CTS or CTS-to-Self. CTS-to-Self is strictly a protection mechanism, but RTS/CTS can also be manually configured and used to identify or prevent hidden nodes.
Understand all of the technologies that make up power management. Power management can be enabled to decrease power usage and increase battery life. Understand how buffered unicast traffic is received in a different way than buffered broadcast and multicast traffic. Understand the power-management enhancements defined by WMM-PS.
Review Questions
- What is the difference between association frames and reassociation frames?
- Association frames are management frames, whereas reassociation frames are control frames.
- Association frames are used exclusively for roaming.
- Reassociation frames contain the BSSID of the original AP.
- Only association frames are used to join a BSS.
- Which of the following contains only LLC data and the IP packet but does not include any 802.11 data?
- MPDU
- PPDU
- PSDU
- MSDU
- MMPDU
- Which of the following are protection mechanisms? (Choose all that apply.)
- NAV back-off
- RTS/CTS
- RTS-to-Self
- CTS-to-Self
- WEP encryption
- The presence of what type of transmissions can trigger the protection mechanism within an ERP basic service set? (Choose all that apply.)
- Association of an HR-DSSS client
- Association of an ERP-OFDM client
- HR-DSSS beacon frame
- ERP beacon frame with the NonERP_Present bit set to 1
- Association of an FHSS client
- Which of the following information is included in a probe response frame? (Choose all that apply.)
- Time stamp
- Supported data rates
- Service set capabilities
- SSID
- Traffic indication map
- Which of the following are true about beacon management frames? (Choose all that apply.)
- Beacons can be disabled to hide the network from intruders.
- Time-stamp information is used by the clients to synchronize their clocks.
- In a BSS, clients share the responsibility of transmitting the beacons.
- Beacons can contain vendor-proprietary information.
- If WMM-PS is not supported, after a station sees its AID set to 1 in the TIM, what typically is the next frame that the station transmits?
- CTS
- PS-Poll
- ATIM
- ACK
- When a station sends an RTS, the Duration/ID field notifies the other stations that they must set their NAV timers to which of the following values?
- 213 microseconds
- The time necessary to transmit the DATA and ACK frames
- The time necessary to transmit the CTS frame
- The time necessary to transmit the CTS, DATA, and ACK frames
- How does a client station indicate that it is using Power Save mode?
- It transmits a frame to the AP with the Sleep field set to 1.
- It transmits a frame to the AP with the Power Management field set to 1.
- Using DTIM, the AP determines when the client station uses Power Save mode.
- It doesn't need to, because Power Save mode is the default.
- What would cause an 802.11 station to retransmit a unicast frame? (Choose all that apply.)
- The transmitted unicast frame was corrupted.
- The ACK frame from the receiver was corrupted.
- The receiver's buffer was full.
- The transmitting station will never attempt to retransmit the data frame.
- The transmitting station will send a retransmit notification.
- If a station is in Power Save mode, how does it know that the AP has buffered unicast frames waiting for it?
- By examining the PS-Poll frame
- By examining the TIM field
- When it receives an ATIM
- When the Power Management bit is set to 1
- From the DTIM interval
- When is an ERP (802.11g) AP required by the IEEE 802.11-2012 standard to respond to probe request frames from nearby HR-DSSS (802.11b) stations? (Choose all that apply.)
- When the probe request frames contain a null SSID value
- When the AP supports only ERP-OFDM data rates
- When the AP supports only HR/DSSS data rates
- When the Power Management bit is set to 1
- When the probe request frames contain the correct SSID value
- Which of the following are true about scanning? (Choose all that apply.)
- There are two types of scanning: passive and active.
- Stations must transmit probe requests in order to learn about local APs.
- The 802.11 standard allows APs to ignore probe requests for security reasons.
- It is common for stations to continue to send probe requests after being associated to an AP.
- Given that an 802.11 MAC header can have as many as four MAC addresses, which type of addresses are not found in an 802.3 MAC header? (Choose all that apply.)
- SA
- BSSID
- DA
- RA
- TA
- When a client station is first powered on, what is the order of frames generated by the client station and AP?
- Probe request/probe response, association request/response, authentication request/response
- Probe request/probe response, authentication request/response, association request/response
- Association request/response, authentication request/response, probe request/probe response
- Authentication request/response, association request/response, probe request/probe response
- WLAN users have recently complained about gaps in audio and problems with the push-to-talk capabilities with the ACME Company's VoWiFi phones. What could be the cause of this problem?
- Misconfigured TIM setting
- Misconfigured DTIM setting
- Misconfigured ATIM setting
- Misconfigured BTIM setting
- The WLAN help desk gets a call that all of the sudden, all of the HR-DSSS (802.11b) VoWiFi phones cannot connect to any of the ERP (802.11g) lightweight APs that are managed by a multiple-channel architecture WLAN controller. All the laptops with ERP (802.11g) radios can still connect. What are the possible causes of this problem? (Choose all that apply.)
- The WLAN admin disabled the 1, 2, 5.5, and 11 Mbps data rates on the controller.
- The WLAN admin disabled the 6 and 9 Mbps data rates on the controller.
- The WLAN admin enabled the 6 and 9 Mbps data rates on the controller as basic rates.
- The WLAN admin configured all the APs on channel 6.
- In a multiple-channel architecture, roaming is controlled by the client station and occurs based on a set of proprietary rules determined by the manufacturer of the wireless radio. Which of the following parameters are often used when making the decision to roam? (Choose all that apply.)
- Received signal level
- Distance
- SNR
- WMM access categories
- What are some of the advantages of using U-APSD and WMM-PS power management over legacy power-management methods? (Choose all that apply.)
- Applications control doze time and trigger frames.
- U-APSD APs transmit all voice and video data immediately.
- The client does not have to wait for a beacon to request data.
- Downlink traffic is sent in a frame burst.
- Data frames are used as trigger frames. PS-Poll frames are not used.
- WMM-PS is based on which 802.11-2012 power-management method?
- S-APSD
- U-APSD
- PSMP
- SM Power Save
- PS-Poll