Chapter 3. The Building Blocks in an Identity Services Engine Design
This chapter covers the following topics:
![]() ISE solution components
ISE solution components
![]() ISE personas
ISE personas
![]() ISE licensing, requirements, and performance
ISE licensing, requirements, and performance
![]() ISE policy-based structure
ISE policy-based structure
Knowing how to properly design security solutions is what separates the professional from the amateur. Without a proper design, the eventual implementation will most likely be a disaster. One of the keys to success when designing a security solution is to first understand all of the pieces, or building blocks, you have to work with. After you understand the building blocks, you need to become skilled at manipulating them in ways that best fit your environment. This chapter focuses on the building blocks that are available with the ISE for Secure Unified Access solution. The purpose and function of each building block are covered in this chapter. Chapter 4, “Making Sense of All the ISE Design Options,” discusses your options for manipulating these building blocks.
ISE Solution Components Explained
At a high level, the following are the three product component groups that make up the ISE solution:
![]() Infrastructure components
Infrastructure components
![]() Policy components
Policy components
![]() Endpoint components
Endpoint components
Each group has a distinct role to play in the ISE solution. Let’s examine the roles and functions of these groups in more detail.
Infrastructure Components
Infrastructure components supported by Cisco ISE are numerous, with more added regularly. These network infrastructure devices include both Cisco-branded devices and non-Cisco devices. However, the Cisco-branded devices, predictably, provide more functionality with better integration into the ISE solution.
Note
Certain advanced use cases, such as those that involve posture assessment, profiling, and web authentication, are not consistently available with non-Cisco devices or may provide limited functionality, and are therefore not supported with non-Cisco devices. In addition, certain other advanced functions, such as Centralized Web Authentication (CWA), Change of Authorization (CoA), Security Group Access, and downloadable Access Control Lists (dACL), are supported only on Cisco devices.
Note
For the latest support list of infrastructure components, refer to the most recent release of Cisco Identity Services Engine Network Component Compatibility at http://www.cisco.com/en/US/products/ps11640/products_device_support_tables_list.html.
Table 3-1 provides a partial list of the core infrastructure components that are most likely to be used in an ISE deployment. The table shows each device’s capabilities for the following features:
![]() MAC Authentication Bypass (MAB): Using the MAC Address of an endpoint that cannot authenticate itself to the network.
MAC Authentication Bypass (MAB): Using the MAC Address of an endpoint that cannot authenticate itself to the network.
![]() 802.1X: The IEEE standard for communicating identity credentials using Extensible Authentication Protocol (EAP) over LAN.
802.1X: The IEEE standard for communicating identity credentials using Extensible Authentication Protocol (EAP) over LAN.
![]() Web Authentication: Authenticating users attempting network access via a web page. Web Authentication has two deployment modes:
Web Authentication: Authenticating users attempting network access via a web page. Web Authentication has two deployment modes:
![]() Central Web Authentication (CWA): The most popular option, controlled by ISE.
Central Web Authentication (CWA): The most popular option, controlled by ISE.
![]() Local Web Authentication (LWA): Performed by the switch or Wireless LAN Controller (WLC) and cannot perform CoA (described next), modify the port VLAN, or support session ID.
Local Web Authentication (LWA): Performed by the switch or Wireless LAN Controller (WLC) and cannot perform CoA (described next), modify the port VLAN, or support session ID.
![]() Change of Authorization (CoA): RADIUS attribute that ISE issues to an access device in order to force the session to be reauthenticated. CoA forms the backbone of the 802.1X ISE solution.
Change of Authorization (CoA): RADIUS attribute that ISE issues to an access device in order to force the session to be reauthenticated. CoA forms the backbone of the 802.1X ISE solution.
![]() VLAN: Virtual LAN. The layer-2 broadcast domain that might be assigned to incoming devices.
VLAN: Virtual LAN. The layer-2 broadcast domain that might be assigned to incoming devices.
![]() Downloadable ACL (dACL): An access control list that is sent from ISE to the access device to restrict the session.
Downloadable ACL (dACL): An access control list that is sent from ISE to the access device to restrict the session.
![]() Security Group Access (SGA): SGA architecture builds secure networks by establishing a domain of trusted network devices. SGA also uses the device and user identity information acquired during authentication to classify the packets as they enter the network. This packet classification is maintained by tagging packets on ingress to the SGA-based network. The tag, called the Security Group Tag (SGT), allows the network to enforce the access control policy by enabling the network device to act upon the SGT to control/restrict traffic.
Security Group Access (SGA): SGA architecture builds secure networks by establishing a domain of trusted network devices. SGA also uses the device and user identity information acquired during authentication to classify the packets as they enter the network. This packet classification is maintained by tagging packets on ingress to the SGA-based network. The tag, called the Security Group Tag (SGT), allows the network to enforce the access control policy by enabling the network device to act upon the SGT to control/restrict traffic.
![]() Cisco IOS Device Sensor: Enables profiling functionality built into the Cisco IOS Catalyst switch or Cisco WLC hardware. This allows profiling to occur locally at the access device instead of centrally at an ISE node.
Cisco IOS Device Sensor: Enables profiling functionality built into the Cisco IOS Catalyst switch or Cisco WLC hardware. This allows profiling to occur locally at the access device instead of centrally at an ISE node.
Table 3-2 lists the most capable and recommended infrastructure components for each category (at the time of writing).
Policy Components
The Cisco Identity Services Engine comprises the one and only policy component in the ISE solution. Having a single centralized policy engine signifies the power inherent in the ISE solution. Cisco ISE provides a highly powerful and flexible attribute-based access control solution that combines on a single platform authentication, authorization, and accounting (AAA); posture; profiling; and guest management services. Administrators can centrally create and manage access control policies for users and endpoints in a consistent fashion, and gain end-to-end visibility into everything that is connected to the network. Cisco ISE automatically discovers and classifies endpoints, provides the right level of access based on identity, and provides the ability to enforce endpoint compliance by checking a device’s posture. Cisco ISE also provides advanced enforcement capabilities, including SGA through the use of Security Group Tags (SGT), Security Group Firewalls such as the Cisco ASA, and Security Group ACLs (SGACL).
Endpoint Components
The network endpoints play an integral role in the total ISE solution. It is the endpoint that provides authentication using 802.1X, MAB, or web authentication. It is also the endpoint that provides posture information to ISE to ensure it is in compliance with security policies. Here are the recommended endpoint components (these are recommended, not required):
![]() 802.1X Supplicant/Agent: A supplicant is basically just software that understands how to communicate via Extensible Authentication Protocol over LAN (EAPoL). There are many supplicants available for use. A supplicant is built into Windows and Mac OS-X. Also available via Cisco AnyConnect and other, third-party supplicant software agents. Cisco IP Phones, video equipment, printers, and many other devices now come with built-in supplicants. Nearly any device that is able to use WiFi will have a native supplicant.
802.1X Supplicant/Agent: A supplicant is basically just software that understands how to communicate via Extensible Authentication Protocol over LAN (EAPoL). There are many supplicants available for use. A supplicant is built into Windows and Mac OS-X. Also available via Cisco AnyConnect and other, third-party supplicant software agents. Cisco IP Phones, video equipment, printers, and many other devices now come with built-in supplicants. Nearly any device that is able to use WiFi will have a native supplicant.
![]() Cisco NAC Agent: For Windows, Mac OS X, and Linux. Provides host posture information to ISE.
Cisco NAC Agent: For Windows, Mac OS X, and Linux. Provides host posture information to ISE.
In many cases, you will not have the option of adding the recommended endpoint components. This is typically the case with printers, IP-Phones, badge readers, HVAC, and other industrial or biomedical endpoints. It is for this reason that ISE has a profiler service that can automate the process of properly identifying and categorizing devices that can’t do it by themselves.
ISE Personas
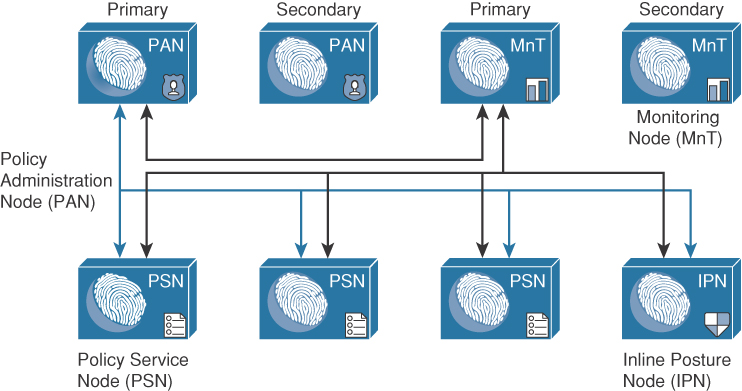
The ISE architecture has many personas to help it scale to large networks and large numbers of users and devices. Cisco ISE has a highly available and scalable architecture that supports standalone and distributed deployments. ISE has three main personas. The persona or personas of an ISE node determine the services it will provide. An ISE node can assume any or all of the following personas:
![]() Administration: Allows you to perform all administrative operations in a standalone or distributed Cisco ISE deployment. The Administration node provides a single pane of glass for management. It handles all system-related and policy-based configuration. In a distributed ISE deployment, you can have only one, or a high-availability (HA) pair, of nodes running the Administration persona. An ISE node dedicated to the administration persona is known as a Policy Administration Node (PAN).
Administration: Allows you to perform all administrative operations in a standalone or distributed Cisco ISE deployment. The Administration node provides a single pane of glass for management. It handles all system-related and policy-based configuration. In a distributed ISE deployment, you can have only one, or a high-availability (HA) pair, of nodes running the Administration persona. An ISE node dedicated to the administration persona is known as a Policy Administration Node (PAN).
![]() Policy Service: Provides network access, posture, guest access, client provisioning, web portals, and profiling services. This persona evaluates the policies and makes all the decisions. You can have more than one node assume this persona. When a node is dedicated to the Policy Service persona, it is referred to as a Policy Service Node (PSN). Typically, a distributed deployment would have more than one PSN.
Policy Service: Provides network access, posture, guest access, client provisioning, web portals, and profiling services. This persona evaluates the policies and makes all the decisions. You can have more than one node assume this persona. When a node is dedicated to the Policy Service persona, it is referred to as a Policy Service Node (PSN). Typically, a distributed deployment would have more than one PSN.
![]() Monitoring: Enables Cisco ISE to function as the log collector and store log messages from all the Administration and Policy Service Nodes in your network. This persona provides advanced monitoring and troubleshooting tools that you can use to manage your network and resources effectively. A node with this persona aggregates and correlates the data that it collects to provide you with meaningful information in the form of reports. Cisco ISE allows you to have a maximum of two nodes with this persona, both of which can take on primary or secondary roles for high availability. Both the primary and secondary Monitoring nodes collect log messages. If the primary Monitoring node goes down, the secondary Monitoring node automatically becomes the primary Monitoring node. When an ISE node is dedicated to the Monitoring persona, it is referred to as a Monitoring & Troubleshooting Node (MnT).
Monitoring: Enables Cisco ISE to function as the log collector and store log messages from all the Administration and Policy Service Nodes in your network. This persona provides advanced monitoring and troubleshooting tools that you can use to manage your network and resources effectively. A node with this persona aggregates and correlates the data that it collects to provide you with meaningful information in the form of reports. Cisco ISE allows you to have a maximum of two nodes with this persona, both of which can take on primary or secondary roles for high availability. Both the primary and secondary Monitoring nodes collect log messages. If the primary Monitoring node goes down, the secondary Monitoring node automatically becomes the primary Monitoring node. When an ISE node is dedicated to the Monitoring persona, it is referred to as a Monitoring & Troubleshooting Node (MnT).
Note
Due to the high performance requirements of the Monitoring persona, in midsize to large deployments, it is recommended that you dedicate a node to specifically run this persona.
ISE also has two node types that determine the node’s functions:
![]() ISE node
ISE node
![]() Inline Posture Node (IPN)
Inline Posture Node (IPN)
Only the ISE node type can be configured with one or more of the previously discussed personas. The inline posture node must be a dedicated node and cannot assume any of the personas. As an inline posture node, it is logically or physically inline in the network. Typically, this means it is behind a VPN headend device or behind a non-Cisco WLC that cannot support CoA or another required feature. While inline, this node type can block traffic and apply other network policies as per the ISE policy rule table.
Figure 3-1 provides an idea of how these personas and node types look logically. Only the primary connections are shown, for simplicity.
ISE Licensing, Requirements, and Performance
This section discusses the centralized ISE licensing model, hardware and virtual machine requirements, and the published performance of an ISE node.
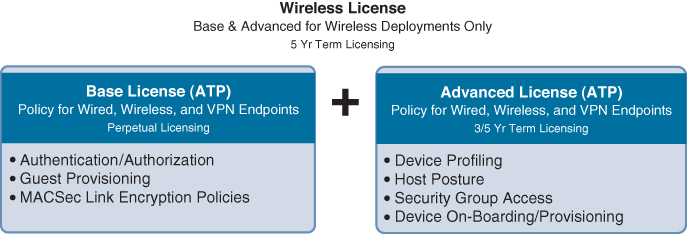
ISE Licensing
Identity Services Engine licensing is fairly straightforward. There are only three licenses, and each license is sized for concurrent authenticated users and devices. Figure 3-2 depicts the three ISE license types: Base, Advanced, and Wireless Only.
The licenses shown in Figure 3-2 would additionally include a user count. For example, L-ISE-ADV3Y-100= means a 100-user advanced license that is valid for 3 years.
Note
The Advanced license requires the purchase of the Base license as well. The Wireless license includes both Base and Advanced licenses.
ISE Requirements
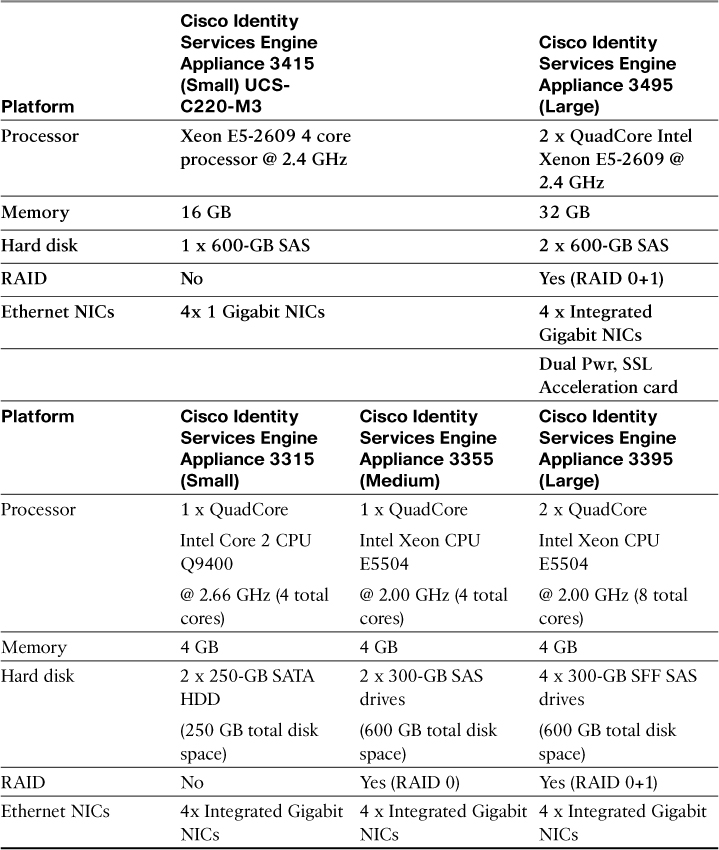
Cisco ISE comes in two form factors: physical appliance and virtual appliance. The physical appliance comes with the server hardware. The virtual appliance comes as a VMware virtual appliance package that you can load onto a VMware ESX server. The physical appliance comes in three form factors: small, medium, and large (as of this writing). Table 3-3 provides the hardware details.
Given that the physical appliances will be upgraded once or twice a year by Cisco, be sure to check Cisco.com for the latest specifications.
For the virtual appliance, the specifications for the virtual machine (VM) host should be sized at or above the specifications for the physical appliance you are trying to match. For example, if you want to have performance similar to that of a Medium physical appliance, then you would build a VM with the specifications of a Medium appliance shown in Table 3-3. Hard drives with 10-KB or higher RPM are highly recommended for ISE VM. VMware VMotion and cloning are only supported in ISE version 1.2 or later. It is possible to decrease the HD requirements in certain situations. Here are the ISE persona minimum disk space requirements for production VM deployments:
![]() Standalone ISE: 600 GB
Standalone ISE: 600 GB
![]() Administration: 200 GB
Administration: 200 GB
![]() Monitoring: 600 GB
Monitoring: 600 GB
![]() Administration and Monitoring: 600 GB
Administration and Monitoring: 600 GB
![]() Administration, Monitoring, and Policy Service: 600 GB
Administration, Monitoring, and Policy Service: 600 GB
![]() Policy Service: 100 GB (200 GB strongly recommended)
Policy Service: 100 GB (200 GB strongly recommended)
Note
Do not use Intel Hyper-Threading Technology for the ISE VM. Ensure that the correct number of Cores are allocated per VM; it is the Cores that matter in the configuration.
Note
ISE version 1.2 (and later) moved to a 64-bit OS, thus enabling it to address more than 4 GB of RAM memory. ISE 3495 includes 32 GB of RAM.
ISE Performance
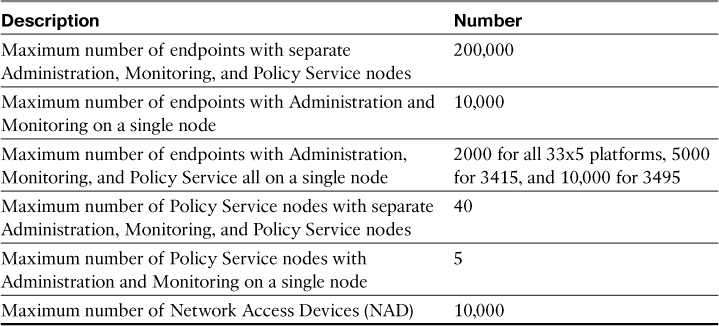
ISE performance is dependent on several factors and, unfortunately, is not a straightforward or precise calculation. It is dependent on the node type, persona(s), policy complexity, bandwidth requirements, and several other variables. Table 3-4 through Table 3-6 dissect the different performance specs for ISE. Use typical design guidance when using performance metrics: never exceed 80 percent of stated capacity, and design for 50 percent or less out of the gate. This allows you to build growth into the architecture and ensures that you have a healthy buffer in case your environment doesn’t mirror the performance metrics tested and documented by Cisco.
Table 3-5 shows the maximum possible performance per ISE deployment, not per ISE node. It assumes Large appliances unless otherwise stated.
When building a distributed ISE deployment, you need to consider the bandwidth requirements that are needed for the ISE personas to exchange information, as outlined in Table 3-6.
ISE Policy-Based Structure Explained
The Identity Services Engine solution relies on a policy-driven rule set to make its decisions. ISE has several different policy types that are all consolidated into a policy set. A policy set is a grouping of several different policy rules from both authentication and authorization policies. You can then have multiple policy sets that are processed in order, top down. Finally, you can have global exception rules across the entire ISE deployment. The following policy rule types can be called within an ISE policy set:
![]() Authentication Policy
Authentication Policy
![]() Authorization Policy
Authorization Policy
![]() Profiling Policy
Profiling Policy
![]() Device Posture Policy
Device Posture Policy
![]() Client Provisioning Policy
Client Provisioning Policy
![]() Security Group Access Policy
Security Group Access Policy
![]() Guest Policy
Guest Policy
Each policy type will be explained in the configuration section of this book. To enable the policy set view, choose Administration > System > Settings > Policy and select Policy set. Given the power of policy sets, it is a best practice to enable this feature.
For now, just realize that, as part of preparing for your ISE deployment, you have these policy types at your disposal. Figure 3-3 shows a simple example of a Policy Set.
In the left pane of Figure 3-3, you can see the Policy Sets. These policy sets are processed from the top down, beginning with the Global Exceptions policy set, followed by the ThirdParty Policy Set, and finally the Default policy set. The Policy Set selected in Figure 3-3, ThirdParty, shows you the Authentication Policies and Authorization Policies that make up this set. These policy rules are also processed from the top down, thus making the ordering of rules very important.
Summary
This chapter provided a baseline to understand all of the building blocks you have to work with inside of ISE. With this knowledge, you can begin to understand your ISE options for the following:
![]() ISE solution components
ISE solution components
![]() ISE personas
ISE personas
![]() ISE licensing, requirements, and performance
ISE licensing, requirements, and performance
![]() ISE policy structure
ISE policy structure
Chapter 4 explores all of the details of the various deployment options for ISE.