CHAPTER 15
Tool Sets
In this chapter you will learn:
• The major cybersecurity tools and technologies for analysts
• When and how you might use different tools and technologies
• How to choose among similar tools and technologies
We shape our tools and thereafter our tools shape us.
—Marshall McLuhan
The purpose of this chapter is to introduce you to (or perhaps reacquaint you with) the tools with which you will need to be familiar for the CySA+ exam. We are not trying to provide a full review of each tool or even cover all the features. Instead, we give you enough information to understand the purpose of each tool and when you may want to use one over the other. For convenience, we group these tools into five categories: preventative, collective, analytical, exploitative, and forensic. If you read about a tool for the first time in this chapter, you may want to spend more time familiarizing yourself with it before you take the exam.
Each of the five tool categories may be further subdivided into classes of tools. For example, the preventative category has a class of tools called “firewalls.” All tools within a class do pretty much the same thing, albeit in different ways. For each tool class, we provide an overview before comparing notable products in that class. We then provide an illustrative scenario that offers a more detailed description of each tool and how it fits in that scenario.
Preventative Tools
The first class of tools we’ll discuss includes all those that help us prevent incidents. They allow us to create defensive perimeters around an application, host, or network. For best results, we employ these tools to create concentric perimeters that, generally speaking, provide a number of defensive layers proportional to the value of the assets they protect.
Firewalls
Firewalls are systems that restrict the flow of network data according to specific sets of rules, which in turn enforce an organization’s security policies. An organizational security policy provides high-level directives on acceptable and unacceptable actions as they pertain to protecting critical assets. The firewall has a more detailed security policy that dictates, among other things, what IP addresses and ranges are allowed as well as what ports can be accessed. A firewall policy or rule set is commonly called an access control list (ACL). A simple rule, such as the one shown here, could be used to allow SMTP traffic to travel from system 10.1.1.2 to system 172.16.1.1:
permit tcp any host 10.1.1.2 host 172.16.1.1 eq smtp
The parameters of this rule are the protocols (TCP and “any” version of IP), the hosts’ IP addresses, and the port number (SMTP = 25). This is an example of stateless packet filtering because the firewall only looks at the listed parameters. A stateful packet inspection (SPI) firewall could use that same rule but would also keep track of the state of the connection between the endpoints. If a legitimate connection doesn’t exist (that is, one that starts with a TCP three-way handshake and ends with a four-way handshake), then the packet is not allowed even if it matches this rule. If we wanted to be even more intrusive, we could use an application-level firewall, which also understands the protocols used by specific applications and allows only packets that “make sense” for that application.
Entire books have been written on firewalls, so we’ll focus our discussion on the specific type of firewalls with which you will have to be familiar for the CySA+ exam. A Next-Generation Firewall (NGFW) incorporates the attributes of the previously discussed firewalls but adds a number of important improvements. Most significantly, it incorporates an intrusion prevention system (IPS) engine. This means that, in addition to ensuring that the traffic is behaving in accordance with the rules of the applicable protocols, the firewall can look for specific indicators of attack even in otherwise well-behaved traffic. NGFWs oftentimes include features that allow them to share signatures with a cloud-based aggregator so that once a new attack is detected by one, all other firewalls manufactured by that vendor become aware of the attack signature. Another characteristic of an NGFW is its ability to connect to external data sources such as Active Directory, whitelists, blacklists, and policy servers. This feature allows controls to be defined in one place and pulled by every NGFW on the network, which reduces the chances of inconsistent settings on the various firewalls that typically exist in large networks.
Tools
The NGFW market is consistently led by three companies: Check Point, Cisco, and Palo Alto Networks. There are many companies, but these three set the tone as well as command the largest shares. It is difficult to do a comprehensive comparison of their products in a few pages because they are exceptionally feature rich and are constantly evolving. Instead, Table 15-1 highlights some key features and describes when one vendor’s product might be a better fit than the others.
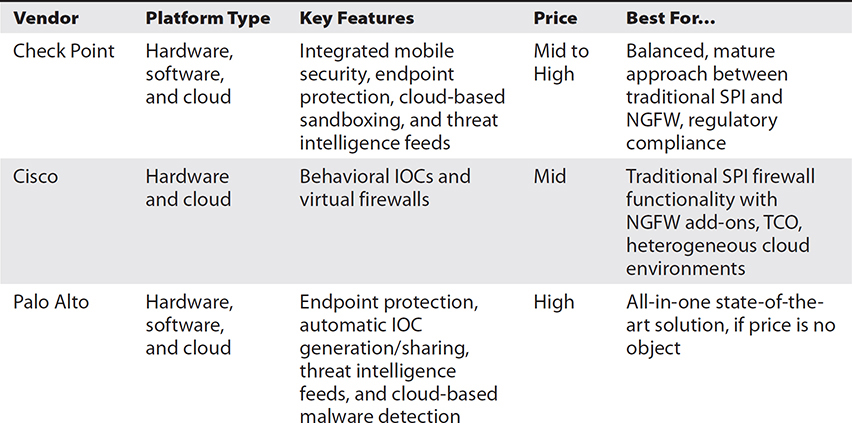
Table 15-1 Comparison of Next-Generation Firewall Offerings
Scenario
You work at a large organization that just recently finished recovering from a major incident involving a sophisticated adversary. This experience resulted in the allocation of new funding for security infrastructure upgrades. A key finding in the lessons-learned report was the fact that the indicators of compromise (IOCs) associated with this threat actor were known in the threat intelligence community, of which you are not a part. As a senior analyst, you are part of the team charged with improving security. You have a significant investment in Cisco products, but want to consider the best fit regardless of brand. As you consider your hardware options, you remember that some NGFWs are able to automatically exchange IOCs with similar devices around the world. If only you’d had that capability a month ago!
Check Point This company’s claim to fame is having pioneered the stateful packet inspection (SPI) firewall. Check Point is not always “first to market” with innovative features, but when it does implement them, they tend to be very well done. Still, Check Point has a very robust research and development arm and is considered among the market leaders. Check Point also has a very good reputation when it comes to complex deployments in very large organizations as well as in some niche use cases (for example, ruggedized ICS/SCADA protection) and with regard to regulatory compliance. Because your organization is large and the upgrades could be complicated, Check Point might help you make the transition easier.
Cisco Cisco’s NGFW solutions are common in Cisco-only (or Cisco-mostly) deployments. Its solutions are marketed as Cisco ASA with FirePOWER Services, and they represent a (subscription-based) FirePOWER service on a traditional ASA firewall. When it comes to traditional firewall features and protection, Cisco leads compared to the other manufacturers. That said, its NGFW features compare well with the other two, though they tend to not be as robust or innovative. If total cost of ownership (TCO) is a principal concern, Cisco NGFWs compete very well. This is particularly relevant in the scenario because you already have a significant investment in Cisco devices.
Palo Alto Palo Alto Networks is widely regarded as the industry leader in NGFW innovation, frequently rolling out new features ahead of its competitors. An example of this is the introduction of cloud-based malware detection into the market with its Wildfire subscription service, which is integrated with its threat intelligence cloud. Integration is a major theme within Palo Alto’s product line, which can result in faster detection and better protection, particularly against previously unknown threats. This innovation comes at a cost, however, because Palo Alto’s solutions tend to be more expensive than its competitors’. If ever there was a time to jump on the Palo Alto bandwagon, this might be it since you are better resourced.
IDS and IPS
An intrusion detection system (IDS) is a system that captures network traffic, compares it to a set of rules or heuristics, and generates some sort of notification if there is any evidence of unauthorized activity. An intrusion prevention system (IPS) is simply an IDS that attempts to stop the intrusions it detects, and not simply generate alerts. It follows that an IPS is a special class of IDS that retains all the latter’s features and adds responsive capabilities. Although both can be network or host based, we will focus our attention on the network version.
Tools
We already discussed two of these systems (Snort and Bro) in Chapter 2 when we looked at their IDS capabilities. We’ll now circle back and explore how these systems can be used to detect and prevent intrusions. Table 15-2 provides a comparison of three IDS/IPS tools.
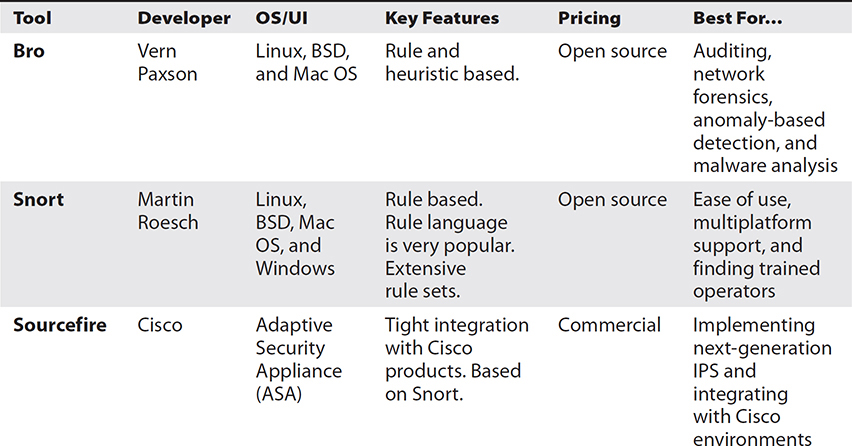
Table 15-2 Comparison of IDS/IPS Tools
Scenario
You recently joined a small business as its only cybersecurity analyst. The company has a reasonable security architecture using some older Cisco routers and firewalls, but it doesn’t have an IPS. You quickly realize that this a critical area for improvement, but also know that money is tight. You have written some basic Snort rules but are not really proficient with it or any other system. A scheduled meeting with the Director of IT next week might be an opportunity to propose some improvements in this area.
Bro Bro is not really meant to be used as an IPS, but its powerful scripting language certainly allows for this. At its core, this IDS does two things: it captures all sorts of events (labeling them neither good nor bad) and then runs scripts that analyze the events looking for signatures or anomalies that might indicate a security incident. These scripts can take actions ranging from sending a warning message to changing configurations on systems in order to thwart a threat. What might make Bro a particularly good fit for the scenario is that it records everything, even as you are getting familiarized with it and building a library of scripts. This means that you would be able to run new scripts on already-acquired data to detect things that happened before you were fully up to speed. The fact that it is free also fits your limited budget.
Snort Snort, though also an IDS, is more frequently used as an IPS than Bro. Its scripting language is not as powerful as Bro’s, but it is plenty to stop any network threat for which you can develop a signature. This is a key difference between Snort and Bro, in that the latter can look for both signatures and anomalous behaviors. Unlike Bro, Snort does not automatically log everything it sees on the network, which may be attractive if you have limited means to store large amounts of event data. Like Bro, however, Snort is free and open source, which means you should be able to afford it. Because you have some Snort experience (in this scenario), you already have a leg up on deploying it in your new organization.
Sourcefire Sourcefire started its life as the commercial version of Snort. It quickly grew in capabilities and was later expanded into a set of offerings under the Firepower line of security products. The Sourcefire company was acquired by Cisco in 2013, and the Firepower IPS was integrated into Cisco products even as it was further improved. This system is offered as a time-limited (typically annual) license in Cisco’s Adaptive Security Appliance (ASA) line of products. The licensing model is one that increases with the number of hosts being supported, so a small organization like the one in the scenario would probably be able to afford it, particularly if the Cisco firewalls you already have can support Sourcefire Firepower. Unlike Bro and Snort, this IPS comes with commercial support, which could make things easier for you as you settle into your new role.
Host-Based Intrusion Prevention Systems
As the name implies, a host-based intrusion prevention system (HIPS) is an IPS that only inspects and responds to the traffic in and out of a host’s network interfaces. Unlike its network-based brethren, the protection is afforded only to one device. Although this may seem like a limitation, it actually enhances the overall security posture by allowing the HIPS to become finely tuned to the traffic and pattern at one specific host. This is doubly true of an HIPS that doesn’t just rely on signatures but also incorporates behavioral or heuristic approaches.
The only reason why you wouldn’t want to have HIPSs deployed across your organization is if you don’t have the resources (for example, time, money, or personnel) to properly install and maintain them. Apart from the direct costs for the licenses, it is important to note that an anomaly-based HIPS can require a significant amount of human supervision during the training period (that is, the period of time it takes the system to learn what “right” looks like). During this period, you may also have to deal with loss of productivity as the HIPS incorrectly classifies benign traffic as malicious. Some of these costs can be mitigated by ensuring your solution includes centralized management and monitoring capabilities.
Antimalware
Antimalware (sometimes called antivirus) software is designed to detect and neutralize malicious software, including viruses, worms, and Trojan horses. The vast majority of commercially available antimalware software is rule based, with new malware definition files getting downloaded from the vendor on a weekly (or shorter) basis. This software works by identifying a distinctive attribute of the malware, extracting that as its signature, and then updating all software systems with it. Antimalware identifies malware that is already known to the vendor, which means that it might not detect new malware (or “old” malware that has been modified).
At least 16 major antimalware products are on the market at the time of this writing. Although none offers 100 percent protection against malicious software, multiple independent reports put them in the range of 96 to 99.9 percent effectiveness against known malware, according to independent testing. This makes antimalware products some of the most cost-effective protections around. Still, it is not difficult to develop malware that is specifically designed to be invisible to any one product. This means that if a sophisticated adversary knows which antimalware product you use, it is not at all difficult to bypass it.
Enhanced Mitigation Experience Toolkit
The Enhanced Mitigation Experience Toolkit (EMET) is a free Microsoft product designed to enhance the protection of Windows systems against a variety of threats, particularly unknown (or zero-day) ones. Among the key features in EMET that improve the security posture are the following:
• Data Execution Prevention (DEP) When a process calls a function, it causes the allocation of memory space for (executable) code and (presumably non-executable) data. Buffer overflow exploits overrun the data space and cause “data” to overwrite the memory space, allowing arbitrary code execution. DEP prevents this situation by marking the data space as non-executable and preventing data from being written to code space.
• Address Space Layout Randomization (ASLR) Buffer overflows and other forms of attack require the attacker to know (or be able to guess) the location in memory of specific data (typically code). ASLR, when properly implemented, makes it infeasible (or at least very difficult) to determine the location of a specific instruction or data item.
• Control Flow Guard (CFG) Return-oriented programming (ROP) is an attack technique in which the adversary hijacks the normal flow of a process and causes it to perform malicious actions. CFG mitigates the risk of ROP by creating a virtual map of the allowable flows within the program and preventing any flows that are not mapped.
It is important to note that these features are typically part of the Windows systems without EMET. However, in order to be useful, every program needs to be compiled by the developer to take advantage of them. Unfortunately, many programs are not compiled in this manner, making them vulnerable to multiple classes of attack. EMET works by compensating these shortcomings when the programs are not built to leverage these features and by allowing the user control over which features are enabled for which programs, as shown in Figure 15-1.
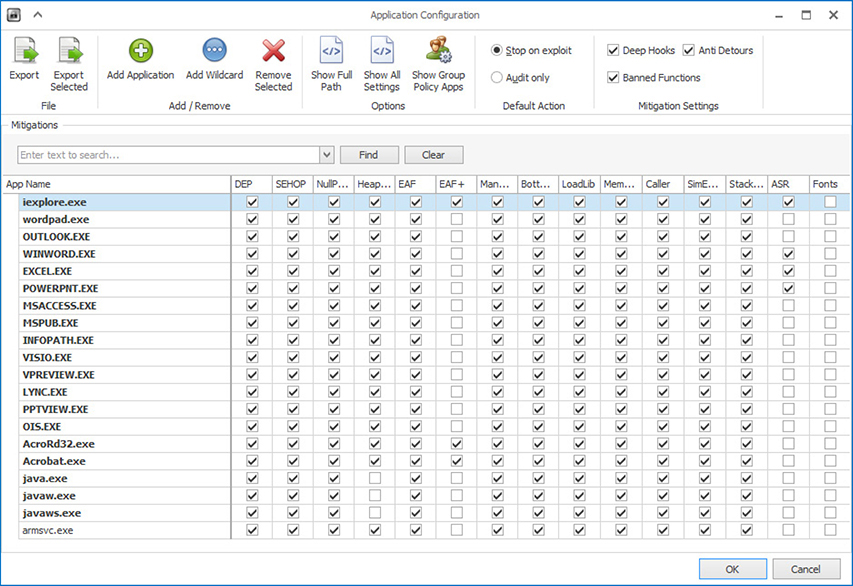
Figure 15-1 EMET mapping security features to programs
Web Proxies
A web proxy is a system that intercepts and then forwards web traffic between clients and servers. Such proxies are commonly used to carry out content filtering to ensure that Internet use conforms to the organization’s acceptable-use policy. They can block unacceptable web traffic, provide logs with detailed information pertaining to the sites specific users visited, monitor bandwidth-usage statistics, block restricted website usage, and screen traffic for specific keywords (such as porn, confidential, or Social Security numbers). The proxy servers can be configured to act as caching servers, which keep local copies of frequently requested resources, allowing organizations to significantly reduce their upstream bandwidth usage and costs while significantly increasing performance.
It is worth noting that although most web proxies support HTTPS traffic, doing so effectively requires additional steps. For starters, you will be examining the contents of a “conversation” that is encrypted and can therefore be reasonably expected (by the user) to be private. It is essential that your organizational policies make it clear to the users that this can happen, or else you could find yourself in legal trouble.
The next step is to ensure that all clients in your organization trust the Certificate Authority (CA) with which you will be signing the internal certificates. At issue is the fact that, when using HTTPS, a client requests from the server a certificate that is issued by a trusted CA and matches the domain of the requested resource. When a web proxy is mediating this conversation, it will present its own certificate to the client to secure the internal connection and use the server’s certificate to secure the external half of the connection. If the proxy’s CA is not trusted by the client, the browser will generate a certificate warning every time, which is something we really don’t want our users to get used to clicking through.
Web Application Firewalls
Whereas web proxies control what is done by and to web clients, we also need similar protections for our servers so that we have assurance that external clients won’t be able to easily attack them. A web application firewall (WAF) is a system that mediates external traffic to a protected server. The WAF is configured for the specific web apps (or classes of web apps) that it is intended to protect. In other words, the WAF “speaks the language” of the web app so as to identify unusual or disallowed requests to it. It is able to determine which URLs, directories, and parameters are acceptable and which are suspicious. This is something that traditional firewalls cannot do.
Tools
The three most popular WAFs are detailed in Table 15-3.
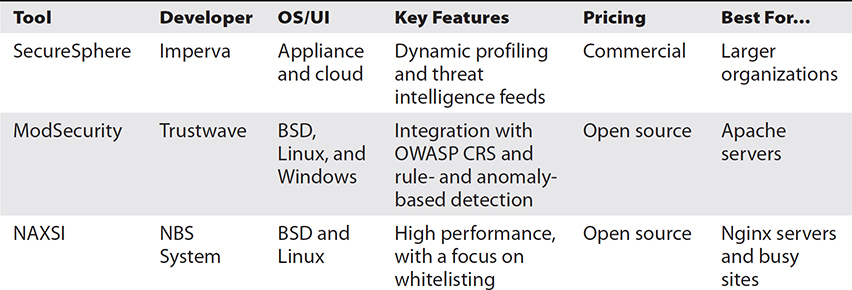
Table 15-3 Comparison of Monitoring Tools
Scenario
Your friend is starting an online business and, having heard you just aced your CySA+ exam, approaches you for advice on how to protect his web storefront and comply with the PCI DSS requirements. The venture capitalists backing the startup expect the business to grow rapidly and have invested a significant amount of first-round funding. The web infrastructure is yet to be developed, so there are no legacy issues to consider. The one system admin who has been hired is proficient with Apache, but is somewhat familiar with Nginx.
SecureSphere Imperva’s SecureSphere is one of the market-leading WAFs. One of its distinctive features is dynamic profiling, which automatically learns protected applications’ legitimate structure and behaviors, as well as the normal behaviors of their users. Taking a page from NGFWs, SecureSphere is able to exchange known threat sources and indicators of new attacks with a threat intelligence system in the cloud, which reduces the vulnerability to attacks and actors that have already been seen elsewhere. With an extensive feature set, the ability to learn normal and abnormal patterns, and a connection to threat intelligence resources, SecureSphere is arguably one of the most powerful WAFs in the market. This, however, comes with a price in the tens of thousands of dollars per appliance, which puts SecureSphere out of the reach of many smaller organizations.
Because the startup is well funded and the infrastructure is yet to be developed, this may be the right time to think long-term and make the investment in SecureSphere. Although it may be overkill in the early days of the company, it would support very rapid growth.
ModSecurity ModSecurity is an open source toolkit for web application monitoring, logging, and control. It was originally developed as an Apache server module (hence the “Mod” part of the name), but has since been adapted to work with Microsoft Internet Information Server (IIS) as well as Nginx (though there are some issues and limitations). ModSecurity is able to leverage the Open Web Application Security Project (OWASP) Core Rule Set (CRS), which is a set of detection rules for the most common web application attacks. The CRS is specifically developed by OWASP for ModSecurity, though it also works with compatible WAFs. In addition to this traditional rule-based detection, ModSecurity is also able to aggregate multiple (less-critical) rule matches so that, collectively, they trigger a higher-level alert. This anomaly-based approach is meant to catch adversaries who go for small, incremental attacks that would otherwise not show up on an analyst’s screen.
Because the system admin in the scenario is proficient with Apache, ModSecurity would provide a very low-cost solution that would not require specialized hardware, licenses, or additional hires. Apache with ModSecurity, however, may not be the best choice among the three systems we discuss in terms of performance for a rapidly growing business.
NAXSI NAXSI stands for Nginx Anti XSS and SQL Injection, and XSS stands for cross-site scripting. As a related aside, Nginx is an open source web server developed specifically to outperform Apache in high-use environments. It follows that NAXSI also focuses on performance and does so by zeroing in on a relatively small rule set that reportedly identifies the features of 99 percent of known web application attacks. By taking some fairly draconian measures with these rules, NAXSI implements a “deny by default” policy. It is then up to the system administrator to create whitelists that will allow legitimate traffic through, while letting NAXSI drop everything else. Obviously, tuning a NAXSI implementation is critical, but this is facilitated by a semi-supervised self-learning feature that this WAF can use to automatically generate whitelists.
The system admin in the scenario would probably have a lot of learning to do in order to get a NAXSI solution up and running. Still, if funds are limited and performance during a rapid growth phase is important, this may be the best fit. It would probably be a bit more expensive than the Apache ModSecurity option, but it may also be able to better support a large customer base in the future.
Collective Tools
Even if our preventative tools are very effective at blocking the vast majority of the threats against our systems, we would still need to keep an eye on them (and the system at large) to ensure they were still effective in an ever-changing threat environment. In reality, our tools and other controls will fail more often than we’d like to admit. This underscores the importance of collecting information for point or historical analyses. Collective tools run the gamut from very focused command-line tools like the perennial ping to exceptionally complex security information and event management (SIEM) solutions.
Security Information and Event Management
Security information and event management (SIEM) systems are at least as much analytical as they are collective tools. All tools in this category perform four basic functions: collect, store, analyze, and report. Most of the collected information comes from various systems’ logs, which are exported and sent to the SIEM system. The SIEM will then typically normalize the format of the data from these disparate sources so that they can be compared with each other. It then stores everything in a system that is optimized for quick retrieval, which is needed to analyze vast amounts of information. Whether the analysis is the result of a simple user query or the end product of sophisticated processes of correlation, SIEMs also have to produce a variety of reports for different purposes that range from internal lessons learned to regulatory compliance.
Tools
There are dozens of players in the SIEM marketplace, but for the purposes of the CySA+ exam, we focus on only six. These are highlighted in Table 15-4 and further described in the context of the scenario presented next.
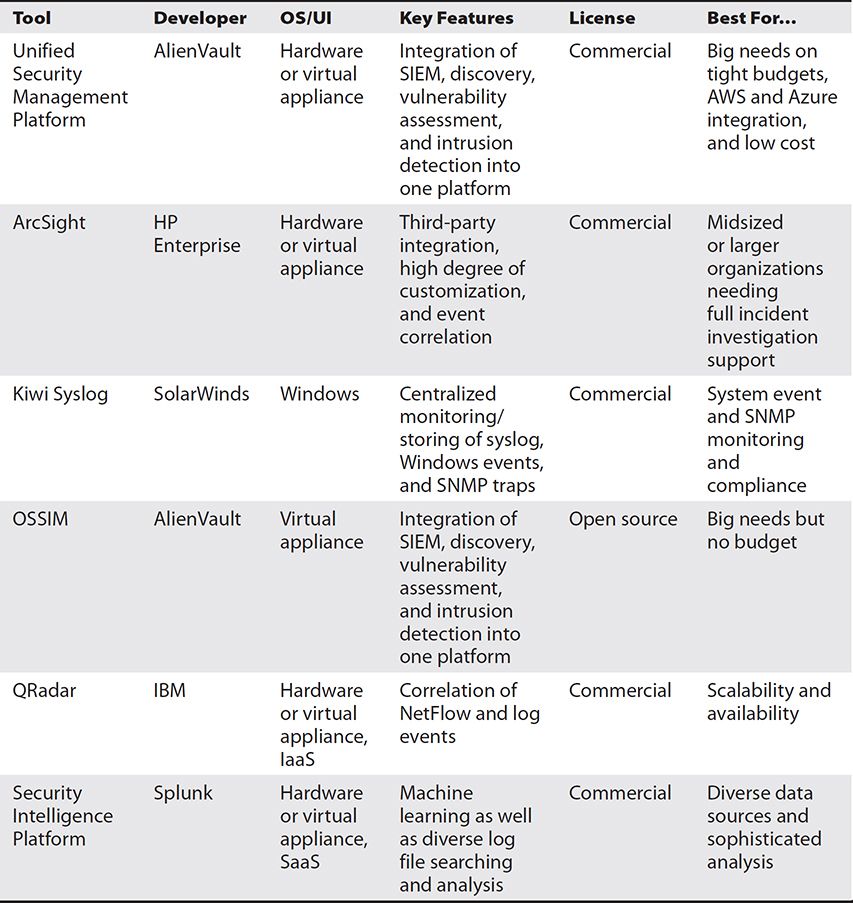
Table 15-4 Comparison of SIEM Offerings
Scenario
After a couple of (fairly) small security incidents, your mid-sized firm is ready to make an investment in more robust event management capabilities. As the senior cybersecurity analyst on staff, you are assigned the task of identifying and acquiring the best solution. You are not given a blank check but still have a reasonable amount of funds, so you don’t have to go for a free solution. The timing is critical, since your forecasts call for significant growth in the next 18 months involving both new hires and a couple of small acquisitions. You do a lot of government work, so you don’t have a big cloud presence (choosing to keep the data on premises instead), but this clientele also makes you a likely target for advanced persistent threats.
Unified Security Management Platform The AlienVault Unified Security Management (USM) system is a proprietary extension of the Open Source Security Information Manager (OSSIM), which we discuss later. In addition to the OSSIM capabilities, USM includes data analytics and visualizations, log management, phone and e-mail support, documentation, a knowledgebase, and a full day of training. AlienVault also offers a subscription threat intelligence service in addition to the crowd-sourced Threat Exchange, which supports OSSIM and USM. All this is available as a virtual or hardware appliance either on premises or tightly integrated into Amazon Web Services (AWS), with well-regarded customer service.
Because the scenario specifies that you don’t have much in the way of SIEM capabilities, a product like USM would allow you to pack a lot of punch for a fairly small amount of money. The threat intelligence service subscription could also help mitigate the threat from APTs, particularly with the sophisticated analysis and reporting features in this product.
ArcSight With three distinct but related platforms, ArcSight has something for medium- to large-sized organizations. Among its distinctive features is the maturity of its correlation and analytics engine. Multiple optional modules for specialized feature sets such as user behavior analytics (UBA) and DNS malware analytics provide additional functionality only for those who want it. One of the features that differentiates ArcSight from other SIEMs (as of this writing) is an open architecture that facilitates its integration with most other security solutions. This is evident in the way it can either do its own data analytics or interface with other systems such as Hadoop and Kafka to feed third-party big data platforms.
ArcSight is one of the most respected platforms on the market, so you couldn’t go wrong in selecting it in this scenario. The optional modules would provide you a nice growth path, even though the base product provides a robust set of features. Additionally, if your organization grows to the point of being able to leverage big data analytics, ArcSight would integrate very well with the most common solutions in that space.
Kiwi Syslog Kiwi Syslog is a tool developed by SolarWinds to monitor, archive, and alert on syslog events. Technically, it is not a SIEM, though it does share some basic features with this class of tools (for example, prioritizing and alerting on messages). Kiwi is really meant to help monitor performance and for regulatory compliance issues, but these can also help identify compromises, which is the reason CompTIA lumped it in with the SIEMs. Realistically, though, Kiwi would be insufficient as a standalone SIEM.
There is nothing in the scenario that specifically calls out Kiwi Syslog as a good solution. Still, if your main challenge were the integration of log files from both Linux and Windows systems, this could be part of the solution.
OSSIM The Open Source Security Information Manager (OSSIM) is an integrated collection of components rather than a monolithic product. OSSIM was started in 2003, and five years later became the basis for the commercial product AlienVault, described previously. It includes the Open Vulnerability Assessment System (OpenVAS) for vulnerability assessment, Suricata for network-based intrusion detection, OSSEC for host-based intrusion detection, as well as file integrity monitoring and more. The multitude of open source tools are coherently integrated into a unified web-based interface with wizards to walk you through common setups, as shown in Figure 15-2. OSSIM is distributed as an ISO that can be installed on a virtual or physical host. These hosts can participate in the Open Threat Exchange, which is a crowd-sourced IP reputation service that allows OSSIM systems to share information about known or suspected malicious addresses.
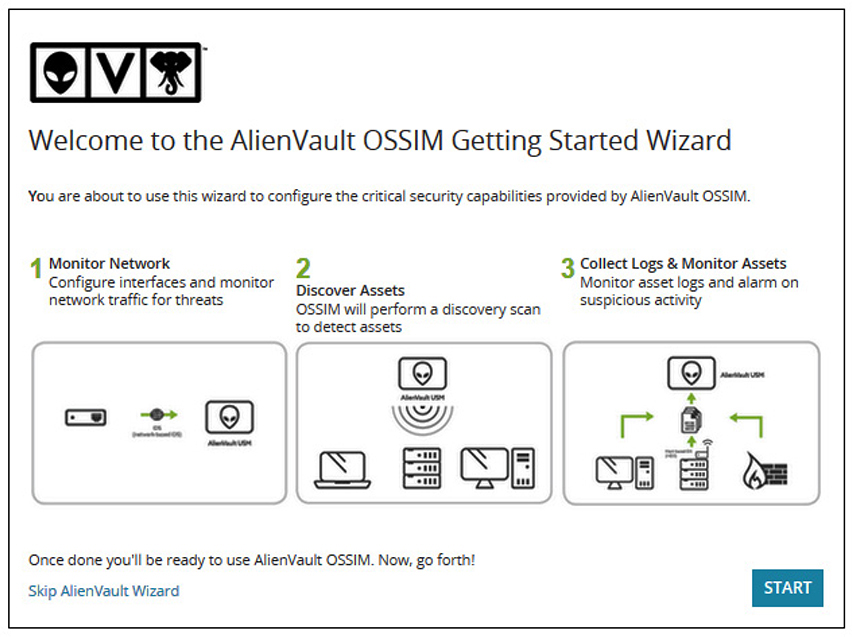
Figure 15-2 OSSIM configuration wizard
You already saw how AlienVault’s USM would be a good fit for the scenario. If your budget was limited, or if you preferred to invest in workforce development in addition to platform acquisition, then OSSIM could be a good fit. The money you save by choosing this free platform could be invested in training for your staff, which could give you a better fit, depending on the specific requirements.
QRadar IBM’s QRadar stands out from other SIEMs in its ability to integrate NetFlows, packet captures, and event logs in support of incident response. Rather than only tracking events (which could become incidents), this system tracks “offenses,” which are correlated events that are more likely to be indicative of a security compromise. Analysts examining an offense can then see all the network and log data supporting it, all the affected hosts, and all relevant vulnerabilities. Another distinctive feature of QRadar is its ability to automatically start acquiring forensic data and/or start an event ticket.
QRadar would be a good fit in the scenario if you needed tight integration between your SIEM and your response processes. In particular, if your responses typically involve network captures or NetFlow data that had to be correlated with event logs, then this would likely be your best choice provided you could afford it. Because the scenario doesn’t spell out this requirement, you would have to dig a bit deeper before making the decision.
Security Intelligence Platform Splunk is probably the best-known name in the SIEM market. Its Security Intelligence Platform (SIP) comprises two products: Splunk Enterprise and Splunk Enterprise Security. The former provides event and log collection, indexing, and analysis, whereas the latter has the traditional SIEM features that make that data actionable. Splunk started off as a log file analysis engine that grew up into a SIEM, which explains why it shines in the first role but faces stiff competition in the second role. In fact, if you are looking for advanced event correlation, other platforms may provide better products and require less effort. Like ArcSight, SIP is also able to provide user behavior analysis (UBA), which is very useful for advanced threat monitoring.
There is nothing in the scenario that makes SIP stand out as an obvious choice, so it would boil down to the best cost for the basic capabilities you need. Splunk is very competitive with other solutions, so you would have to specify your requirements and get quotes from multiple vendors. You could then compare the features and costs and choose the right platform based on those criteria.
Network Scanning
Network scanning is the interrogation of a set of hosts for specific information. A horizontal network scan, for instance, sends messages to a set of host addresses asking the question, “Are you there?” Its goal is to determine which addresses correspond to active (responding) systems. A vertical scan, on the other hand, sends messages to a set of protocol/port combinations (for example, UDP 53 or TCP 25) asking the same question, with the goal of determining which ports are listening for client connection attempts. It is also possible to combine both horizontal and vertical scans, as shown in Figure 15-3. The point of a network scan of any flavor is to find out who is listening (and responding) on a network. This is useful in finding systems that are not behaving as they ought to.

Figure 15-3 Nmap performing both horizontal and vertical scans
Consider the case in which a software development team sets up a test web server to ensure the web app on which the team members are working is functioning properly. There is no malice, but not knowing that this server is running (and how) could seriously compromise the integrity of the defenses. On the other hand, we can sometimes find evidence that a host has been compromised and is now running a malicious service. Though these situations should be rare in a well-managed network, scanning is one of the quintessential skills of any security professional because it is one of very few ways to really know and map what is on our networks.
Nmap
Nmap is a tool that is synonymous with network scanning. The name is shorthand for “network mapper,” which is an apt description of what it does. Nmap works by sending specially crafted messages to the target hosts and then examining the responses. This not only can tell which hosts are active on the network and which of their ports are listening, but it can also help us determine the operating system, hostname, and even patch level of some systems. Though it is a command-line interface (CLI) tool, a number of front ends provide a graphical user interface (GUI), including Zenmap (Windows), NmapFE (Linux), and XNmap (Mac OS).
Packet Capture
The original commercial tool for capturing packets was the Network General Sniffer developed in the late 1980s, which forever changed the way we observe and analyze our networks by allowing us to capture real-time data. We introduced packet capture in Chapters 1 and 2, but we return to the topic here to address when and how you might want to use the various tools available. Apart from their usefulness for troubleshooting and incident response, sniffers are commonly used for logging and auditing purposes. Some organizations with particularly sensitive data (for example, financial and military) perform full packet captures of all traffic in some of their networks. We will not get into this big data analytics use case and will instead focus on more common uses for network packet captures (see Table 15-5).
Tools
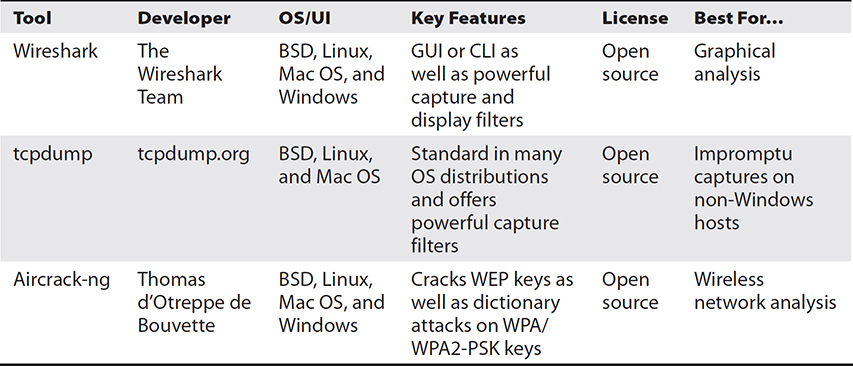
Table 15-5 Comparison of Packet Capture Offerings
Scenario
You are investigating suspicious NetFlow data involving your Domain Name System (DNS) server. Neither your firewalls nor your SIEM are set up to capture full packets, which you think will be needed in order to get to the bottom of this. By connecting to the switch port analyzer (SPAN) port on the right switch and capturing only port 53 traffic to/from your DNS server, you estimate that the amount of packets will not be too large for manual analysis. You do, however, want to save the packet captures for future reference, analysis, or evidentiary use.
Wireshark Wireshark is probably the most widely used, GUI-based packet analyzer. Despite the many advantages of using its graphical front end, it is important to note that it includes a CLI capability called TShark, which is useful when you can’t get to a GUI (for example, when connecting over SSH) or when you want to script a packet capture. Whether you capture the traffic through the GUI or CLI, you can save it and view it on GUI later. You can similarly view captures from other tools (such as tcpdump) provided they were saved in the packet capture (PCAP) file format. Figure 15-4 shows a typical capture, whereas Figure 15-5 shows how you can drill into a specific packet to get a detailed view that includes the payload.

Figure 15-4 Typical Wireshark packet capture
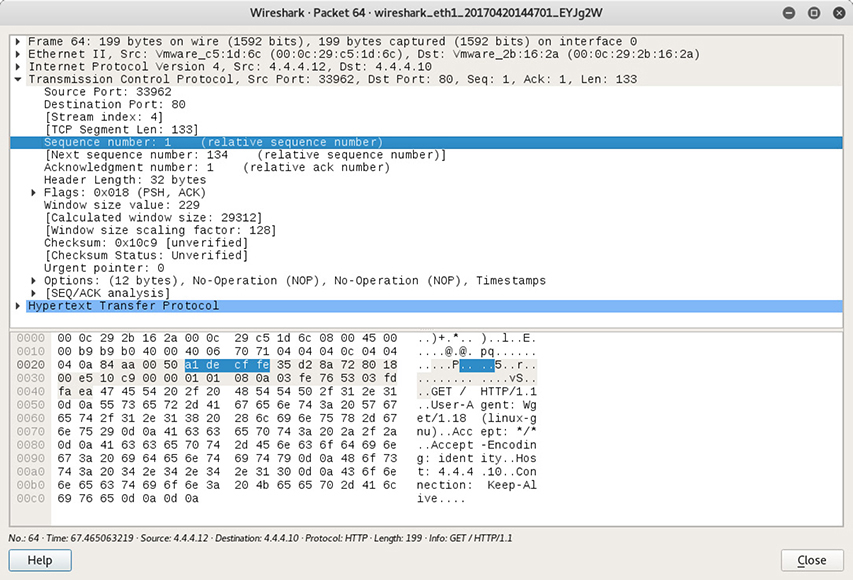
Figure 15-5 Wireshark showing packet details
Because the scenario is not specific as to the interface you’d be using, this ability to do deep analysis of the packets on a graphical front end would make Wireshark a good choice. The scenario is also generic concerning the platform you’d be using to capture packets, but because Wireshark runs on BSD, Linux, Mac OS, and Windows, it would be a feasible choice regardless of the operating system.
Tcpdump Tcpdump is a CLI tool that comes standard in many distributions of BSD, Linux, and Mac OS, which means you typically don’t have to worry about installing it on the platform from which you’d like to capture traffic. As long as you can SSH into a host and run as a privileged user (such as root), you can capture packets on most non-Windows systems. As shown on Figure 15-6, the display is not as easy to read as Wireshark’s, but the information captured can be the same. There is also a Windows version called windump, which is typically not installed by default. Unless you were planning to use a Windows computer for the capture in the scenario, tcpdump would be a good choice, particularly if you couple it with a more robust analysis engine.
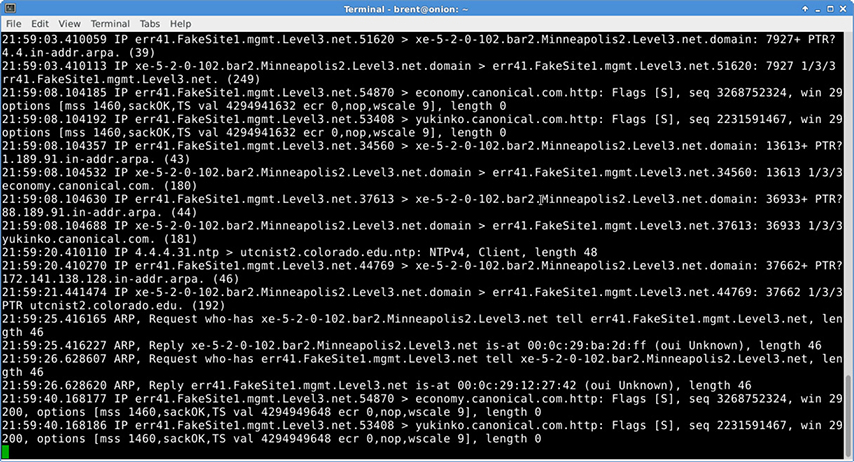
Figure 15-6 Typical tcpdump packet capture
Aircrack-ng Aircrack-ng is the most popular open source wireless network security tool. It’s mostly used for its ability to audit the security of WLANs through attacks on WPA keys, replay attacks, deauthentication, and the creation of fake access points. It does, however, include packet capture functionality. Also, it could be coerced into capturing wired network traffic, as specified in the scenario. It would not be a very good choice, particularly considering the power of the other two tools we discussed here. If the scenario required wireless capture, however, this would be the tool of choice.
Command-line Utilities
This section is a catch-all for some of the myriad CLI tools that every cybersecurity analyst must know how to use. They are all very narrowly focused, but absolutely essential under the right situations. If you are unfamiliar with any of these, you really should spend some time working with them not just for the CySA+ exam, but more importantly in order to do your job well.
Netstat The netstat utility provides a wealth of information on the status of network connections and listening sockets. This is probably the most common use of this tool. It can also show interface statistics. Both of these features are shown in Figure 15-7. It can also provide protocol statistics such as for IP and ICMP, as you can see in Figure 15-8. Netstat is part of the default installation of almost every Linux, Mac OS, and Windows system, though some specific options are slightly different in Windows.

Figure 15-7 Netstat showing TCP connections, listening ports, and interface statistics
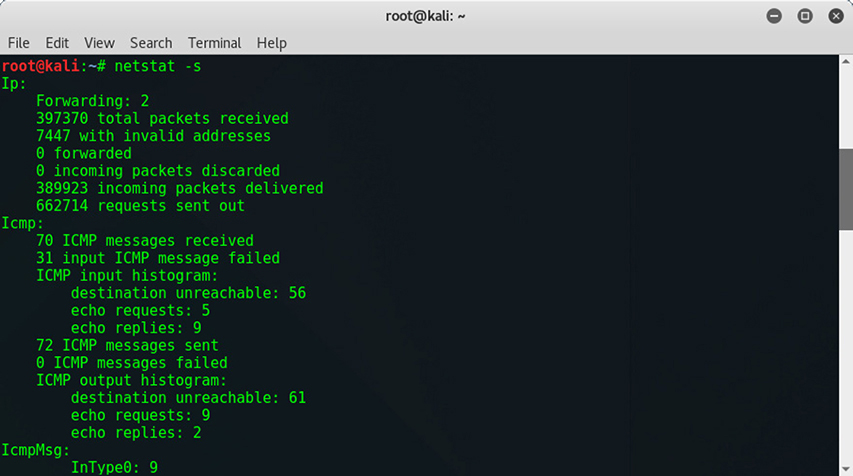
Figure 15-8 Protocol statistics provided by netstat
Ping The ping utility simply sends four (Windows) or continuous (other OS’s) Internet Control Message Protocol (ICMP) echo requests to whichever host you indicate. If the target host is configured to respond to these, it will send back an ICMP echo reply message for each message received. Ping will compare the time at which it sent the request with the time at which it received the response and then provide a total (round-trip) time for the exchange. These round-trip times can provide indicators of latency and jitter to/from that target.
Traceroute The traceroute utility (for BSD, Linux, and Mac OS) and its Windows sibling tracert take advantage of the time to live (TTL) field in an IP packet on which an ICMP echo request is transmitted. Traceroute works by incrementing the TTL (starting with 1) in a sequence of messages to the same host. The way IP works, a receiving host will first decrement the TTL of an arriving packet. If that new value is greater than zero, the host will process the packet normally. Otherwise, it will send an ICMP “time exceeded” message to the source address. By incrementing the TTL, traceroute forces each consecutive host between the source and the ultimate destination to reveal its IP address. It is worth noting that IP packets are not guaranteed to follow the same route every time, so traceroute can return inconsistent results.
Ifconfig One of the basic parameters we oftentimes need is the IP address of whichever host we are examining. The ifconfig utility (for BSD, Linux, and Mac OS) and ipconfig command (Windows) provide that information together with other IP parameters such as netmask, default gateway, and MAC address. The major difference between the two is that ifconfig allows you to configure the interfaces rather than just seeing what their parameters are. Still, most of the time we don’t reconfigure interfaces during cybersecurity analysis or incident response, so they serve the same purpose in the context of the CySA+ exam.
Nslookup The name server lookup, or nslookup, utility can be thought of as the user interface of the DNS. It allows us to resolve the IP address corresponding to a fully qualified domain name (FQDN) of a host. Depending on the situation, it is also possible to do the inverse (that is, resolve the IP address of an FQDN). The tool allows for the specification of a DNS server to be used, or it can use the system default. Lastly, it is possible to fully interrogate the target server and obtain other record data, such as MX (e-mail) and CNAME (canonical name).
OpenSSL OpenSSL is an open source software library that allows software systems to communicate securely. Despite its name, it includes both Secure Sockets Layer (SSL) and Transport Layer Security (TLS) functionality. This library includes a command-line interface that provides the following functionality.
• Generate and validate certificates.
• Generate, sign, and verify MD5 and SHA hashes.
• Encrypt and decrypt data.
• Establish secure connections to remote servers.
Analytical Tools
The next class of tools is focused on comparing observations with reference information in order to analyze the performance of a system. Although it could be argued that SIEMs and other tools belong in this class, CompTIA tried to classify tools by their principal set of features. As tools develop, the lines frequently blur, making this effort much more difficult. You should not be too concerned about the name of the class to which a tool is assigned, but rather about the situations under which that tool would best be used.
Vulnerability Scanning
Knowing what your network looks like from the adversary’s point of view is the first step in defense. Vulnerability scanning provides insight into what your network looks like and identifies weaknesses of these systems. Modern vulnerability scanners can identify software flaws and misconfigurations as well as suggest countermeasures or compensating controls. To demonstrate the features of some of the more popular vulnerability scanning tools, we’ll consider a few scenarios and explore what each of these tools provides to solve our challenge. Note that while many of these tools are free for personal use, some require licenses for enterprise or business use.
Tools
The tools we discuss in this section range from cloud-based solutions for large enterprise networks to open source utilities for web app scanning. Table 15-6 provides a comparison of these tools.
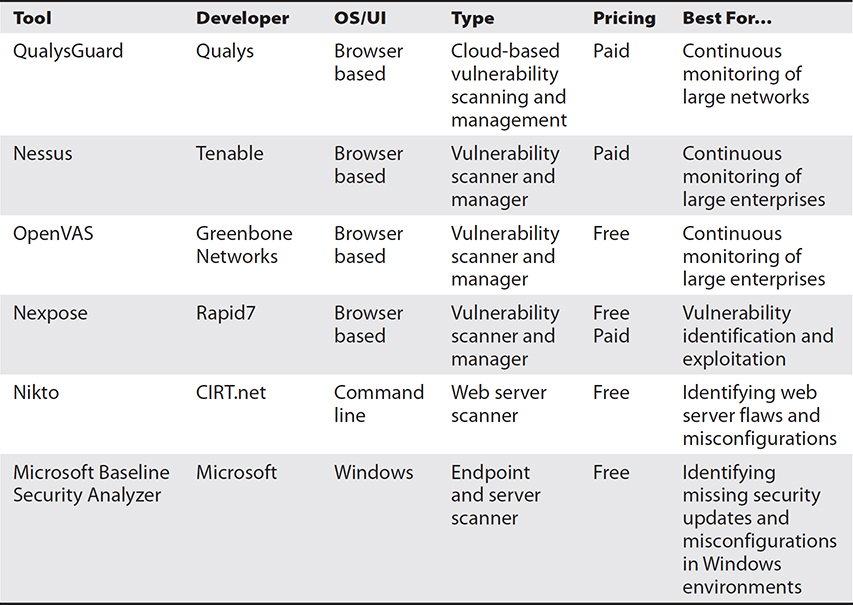
Table 15-6 Comparison of Vulnerability Scanning Tools
Scenario
Your organization has experienced significant growth over the past few months and has recently hired its first chief information security officer (CISO). As she prepares suggestions for changes to the organization’s information security policy, she wants to provide the rest of the leadership with a snapshot of the organization’s network assets, including public-facing servers, endpoints, and data stores. She’s interested in providing a short report for the company leadership, but wants a detailed follow-up plan for herself with technical details about each vulnerability and a plan for remediation. She notifies you that she wants this assessment conducted at least every two weeks, and would like the results automatically delivered to her inbox.
QualysGuard QualysGuard is a product of the California-based security company Qualys, an early player in the vulnerability management market. The company currently provides several cloud-based vulnerability assessment and management products through a Software as a Service (SaaS) model. For internal scans, a local virtual machine conducts the assessment and reports to the Qualys server. Figure 15-9 is a sample dashboard that shows various options under the vulnerability management module.

Figure 15-9 The QualysGuard dashboard for managing its cloud-based vulnerability assessment and management tasks
All network discovery, mapping, asset prioritization, scheduling, vulnerability assessment reporting, and remediation tracking tasks can be accessed via the web-based UI. The platform can generate detailed reports using several templates. Included in the default installation is a template called “Executive Report,” which provides just the type of data the CISO needs for her discussion. A portion of results of this report can be seen in Figure 15-10.

Figure 15-10 A portion of the QualysGuard report generated from the “Executive Report” template
Nessus As we covered in Chapter 6, Nessus is one of the most popular vulnerability scanners on the market. It boasts a large library of over 80,000 plug-ins, which the platform uses to scan for vulnerabilities on the network on an ad-hoc or scheduled basis. Like QualysGuard, Nessus provides an easy way to configure assessments and view the results through your favorite web browser. When Nessus discovers a vulnerability, it assigns a severity level to it in the scan results, as shown in Figure 15-11.

Figure 15-11 Listing of discovered vulnerabilities in the Nessus web interface
Technical details for each vulnerability, the method used in identifying it, and any database references can be found here. Nessus is particularly strong at assessing compliance using its library of “compliance checks.” These compliance checks, or any other type of scan, can be scheduled to occur as desired, fulfilling the CISO’s desire to automatically conduct periodic scans. As for reports, Nessus offers several export options, as shown in Figure 15-12.

Figure 15-12 Nessus export options for report generation after vulnerability scan
Nessus can generate reports that only list vulnerabilities with an associated exploit alongside suggested remediation steps. For an audience such as company leaders, explaining in plain language the concrete steps that may be taken to improve organizational security is key. Nessus provides these suggestions for individual hosts as well as for the network at large.
OpenVAS OpenVAS, a fork of the initial Nessus project, is a widely used vulnerability scanner whose major benefit is its cost. OpenVAS uses a similar structure as Nessus to conduct its scans: the OpenVAS Manager is used to configure and access the OpenVAS Scanner, which schedules and runs the vulnerability scans. Figure 15-13 is an example of the OpenVAS dashboard, which an analyst accesses to manage vulnerability scans.
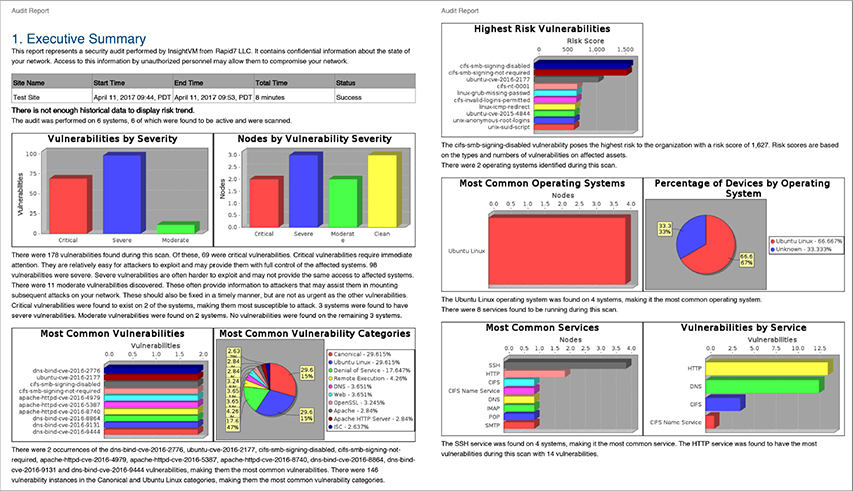
Figure 15-13 OpenVAS main screen providing access to the OpenVAS Manager
As free and open source software, OpenVAS relies heavily on community support in maintaining its library of nearly 50,000 network vulnerability tests (NVTs). Although the software is free, it doesn’t offer the same level of support its paid alternatives do. For a large enterprise network, the price of on-demand customer support might justify the increased cost.
Nexpose Nexpose is a vulnerability scanner from Rapid7, the developers of Metasploit. It places more emphasis on the entire vulnerability management lifecycle rather than just scanning for and cataloging vulnerabilities. It’s also designed to integrate directly into Metasploit for exploitation of discovered vulnerabilities. Once the scan is started, network-connected devices, referred to as “assets,” will populate the dashboard, shown in Figure 15-14.

Figure 15-14 Nexpose Scan Progress screen
An analyst may choose to view the details of the vulnerabilities discovered either by clicking a particular host listed or by viewing all vulnerabilities across the site to look for trends. Figure 15-15 shows the site-wide vulnerability charts, breaking all discoveries down by CVSS score.
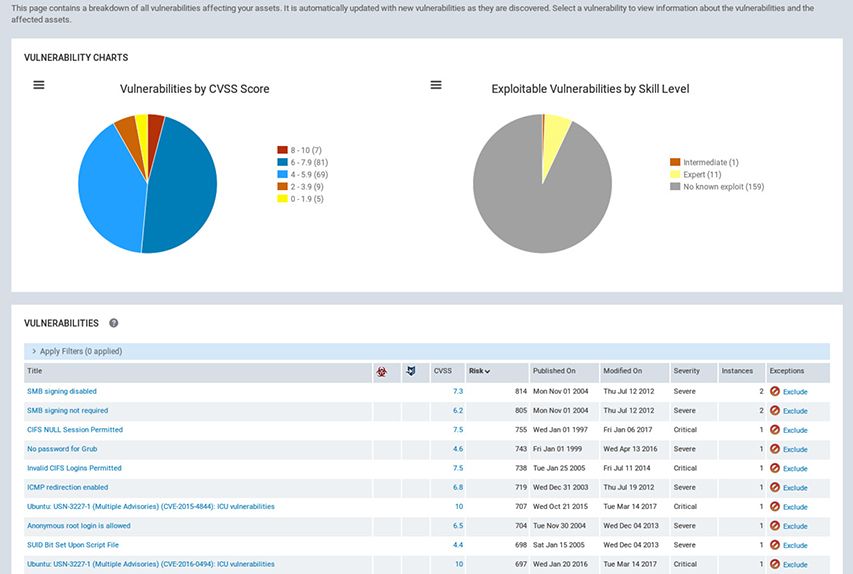
Figure 15-15 Nexpose discovered vulnerability overview and details screen
This system provides context to rate each vulnerability by how exploitable it might be. This is important because not every vulnerability has an associated exploit, nor does every vulnerability have a risk. For example, a resource that has no value cannot have a risk, so it doesn’t necessarily make sense to devote energy to hardening that resource. This point must be considered when conducting risk assessments, especially in resource-constrained environments.
This platform allows for any of the previous screens to be exported, or a report may be generated. Each report contains a summary of the network, complete with an overview of both devices and vulnerabilities. The “Executive Summary” generated by Nexpose can be tailored to share with leadership to help inform their decisions about security policy and resourcing.
Nikto Nikto, as you may remember from Chapter 6, is a command-line-based web server vulnerability scanner. Although its utility is limited to web servers, Nikto’s strength is its speed in assessing the software vulnerabilities and configuration. As a command-line tool, it’s also not as user friendly as other tools. Nikto requires at least a target host to be specified, with any additional options, such as nonstandard ports, added in the command line. In Figure 15-16, we see the command issued to perform a scan against the web team’s new site, which operates on port 3780.
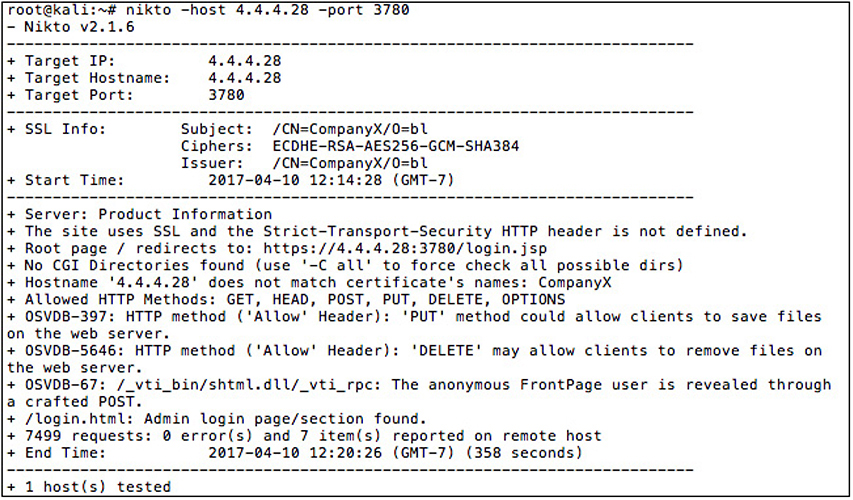
Figure 15-16 Nikto command-line output for a test against a web server located at IP 4.4.4.28
Nikto allows reports to be saved in a variety of ways, including HTML. An example of the HTML files can be found in Figure 15-17.
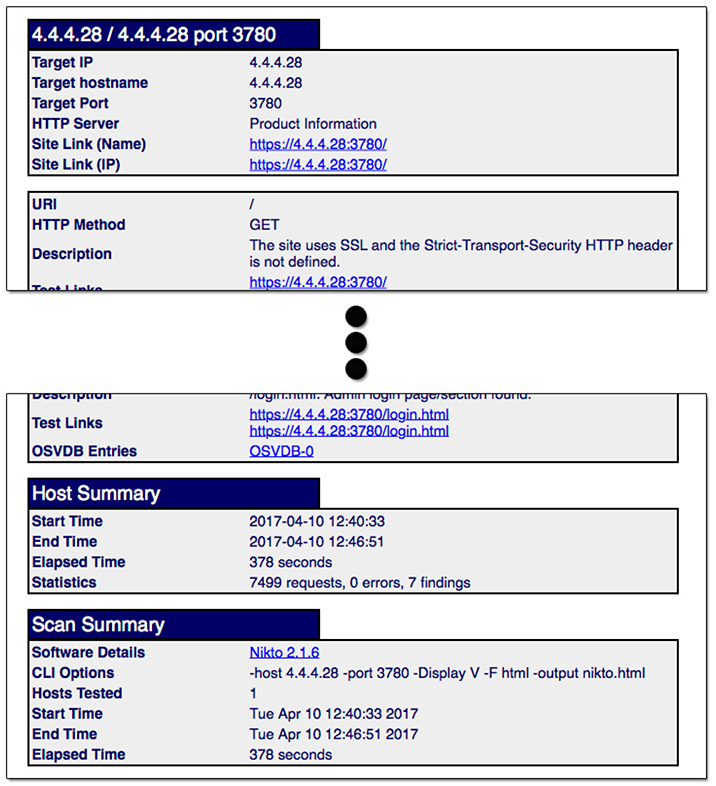
Figure 15-17 Nikto HTML output from a test against a web server located at IP 4.4.4.28
This report includes a summary of the command issued, information about the servers tested, and hyperlinks to the relevant resources and their vulnerability data. Although this is good for technical teams to act on, it may not be as useful for nontechnical decision-makers.
Microsoft Baseline Security Analyzer Microsoft provides a tool called the Baseline Security Analyzer to quickly identify missing security patches or software misconfigurations in Windows operating systems. Designed for use with Windows Vista, Windows XP, Windows 7, Windows 8, Windows Server 2003, Windows Server 2008, and Windows Server 2012, Baseline Security Analyzer is available as a small download directly from Microsoft. This tool is only useful for assessing Windows endpoints and servers, so if the organization is running anything else, this tool won’t work on those platforms. Figure 15-18 shows the various options for starting a scan with this tool. You can scan for vulnerabilities related to passwords, server and database misconfigurations, and missing security updates. The output of the resulting report can also be modified to suit your organization’s naming conventions.

Figure 15-18 Microsoft Baseline Security Analyzer scan configuration screen
The reports generated by the analyzer provide information about what was tested on the system and the results from each test. For some entries, a link to possible solutions is provided. The full report of our local scan is show in Figure 15-19. You can see that the vulnerabilities are grouped by type, and there is an option to sort the result by impact.

Figure 15-19 Microsoft Baseline Security Analyzer report detailing the completed scan
To get more information about any of the issues, you click the appropriate link. The description is written in nontechnical language and often provides a note about the potential impact of the vulnerability.
Monitoring Tools
Network monitoring is a critical task toward understanding what’s happening on the network. Whether through direct inspection of packet captures, watching for surges in traffic, or examining for unusual connections, monitoring give us the visibility on our network required to thwart attackers and improve usability.
Tools
In this section, we focus on software-based tools that gather network data to generate statistics and charts about the network. Table 15-7 provides a comparison of these monitoring tools.
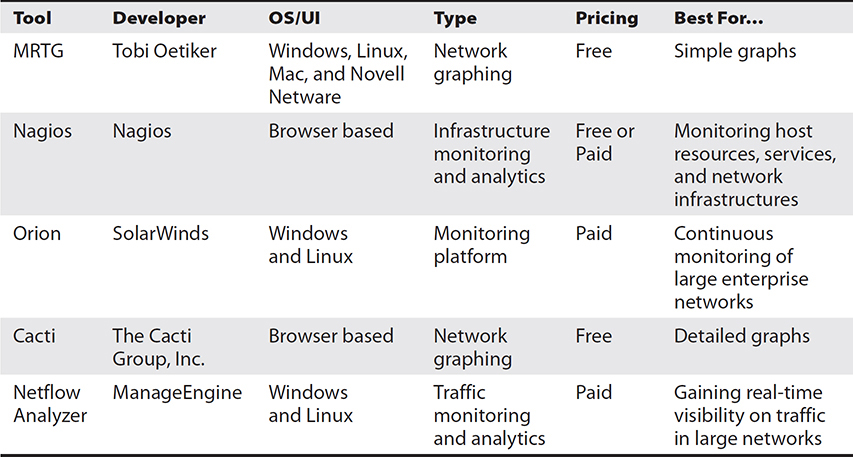
Table 15-7 Comparison of Monitoring Tools
Scenario
You receive a call from a member of the research and development group in your organization reporting of intermittent connectivity. The problem, he explains, seems to be getting worse and is particularly concerning because the company is scheduled to make a new product announcement in the coming months. You send a tech over to investigate and he immediately notices that one of the file servers is running hot. When he uses netstat on the server, he receives the output shown on Figure 15-20.
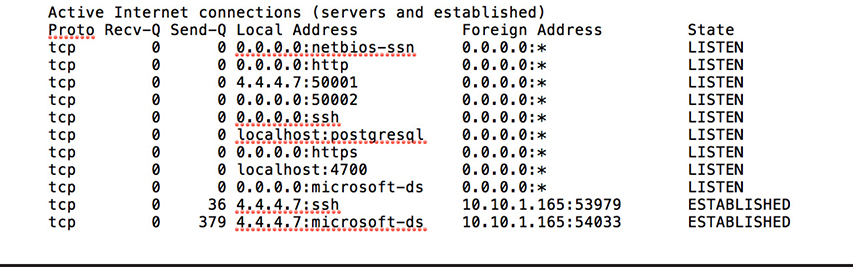
Figure 15-20 Netstat output from fileserver during troubleshooting
You notice a connection made from a foreign address that doesn’t belong to the R&D subnet. You want to get more information about the types of connections made with this server and the total bandwidth consumed as part of your investigation and troubleshooting.
MRTG The Multi Router Traffic Grapher (MRTG) is a cross-platform, network measuring tool that relies on Simple Network Management Protocol (SNMP) exchanges to produce graphs and statistics. Developed to be lightweight, the tool is written in Perl and offered as free software under the GNU General Public License. A sample graph is shown in Figure 15-21 of network traffic over several weeks.

Figure 15-21 MRTG output graph of network traffic
MRTG is very fast and capable of storing traffic logs for years without appreciable increase in log storage requirements. Although the HTML output is convenient, it lacks the polished interface and correlation features offered by other network monitoring solutions.
Nagios Nagios is a very popular monitoring and alerting platform that comes in two flavors: Nagios Core and Nagios XI. While both solutions provide monitoring and analytics capabilities for network infrastructure, Nagios Core is offered as an open source and no-cost solution. Nagios XI, on the other hand, requires an annual standard or enterprise license. Aside from the cost, the primary differences between the two options are in the reporting and interface options. Nagios XI allows for advanced configuration of the dashboards, graphs, and reports. Figure 15-22 is an example of a dashboard that provides quick access to network assets.
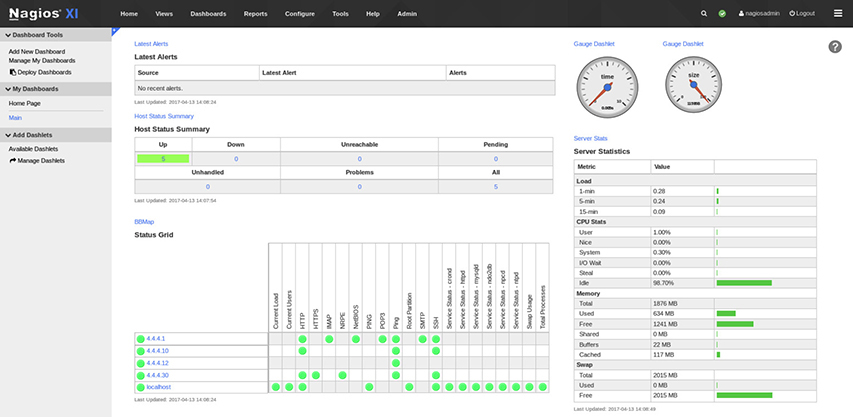
Figure 15-22 Nagios XI dashboard view of the network status
Details on each device are hyperlinked directly from the dashboard, so all historical information about the server in question is just a click away. Each host details screen, as shown in Figure 15-23, can be configured in the same manner as the dashboard to show the graphs and screens most relevant to your security team’s needs.
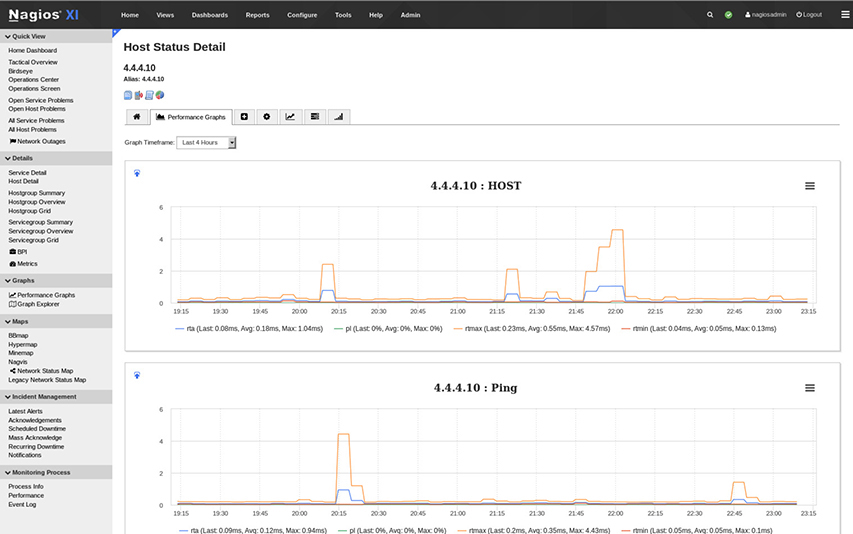
Figure 15-23 Nagios XI host status details
Orion SolarWinds is a provider of several IT and network monitoring tools. The company began in 1999 as a developer of network performance monitoring software and has expanded to flow analysis, virtualization management, and server monitoring, each with advanced reporting options. Its main platform, Orion, provides the foundation for the entire SolarWinds suite of products. Performing protocol analysis to determine what kind of data is moving from nodes, for example, can be performed by the NetFlow Traffic Analyzer tool, which rides on the Orion framework.
Cacti Cacti is a free front end for the RRDTool, a network logging and graphing tool based on MRTG. Like MRTG, Cacti’s strength is its speed in ingesting and visualizing logging data. Due to its low resource requirements, Cacti is a popular choice for web administrators who want to create quick graphs and statistics. Figure 15-24 is a display provided by the developers to highlight the precise control over graph timespans using the web interface.

Figure 15-24 Cacti web interface showing the custom controls over timespans
NetFlow Analyzer ManageEngine’s NetFlow Analyzer is an analysis tool for network traffic that relies on NetFlow data to give administrators a complete view of their network. In addition to performing basic bandwidth monitoring and service identification, NetFlow Analyzer also provides traffic-shaping features, which might be useful to identify and curb bandwidth abuse. Additionally, NetFlow Analyzer provides some network forensics and security-specific capabilities through an add-in module. In our scenario, you could use NetFlow Analyzer to quickly identify the server in question and whether other devices are exhibiting the same type of behavior.
Interception Proxy
For the propose of analysis, interception proxies provide extraordinary insight into user behavior because they sit in between the user and the requested resource. As an intermediary device, an interception proxy can be used in several ways to collect, modify, or block certain types of data.
Tools
Interception proxies are extremely flexible tools, capable of acting as proxies, scanners, fuzzers, and web crawlers. Table 15-8 details three of the more popular interception proxies in use today.
Table 15-8 Comparison of Interception Proxy Tools
Scenario
Your accounting team recently set up a new internal website to assist managers with their budgets. The website will provide managers with a snapshot of their current spending and feedback to help them plan future operations. The members of the accounting team are concerned about exposure of sensitive team financial data, so they’ve asked your help with letting them know what, if any, data might be visible to others and ways to correct it.
Burp Suite Burp Suite is an integration web application testing platform. Often used to map and analyze a web application’s vulnerabilities, Burp allows seamless use of automated and manual functions when finding and exploiting vulnerabilities. In proxy mode, Burp will allow the user to manually inspect every request passing through from the user to the server. The option to forward or drop the request is shown in Figure 15-25.

Figure 15-25 Burp Suite intercept screen and options in proxy mode
Although Burp is designed for a human to be in the decision loop, it does offer a point-and-click web-scanning feature in the paid version that might be useful for this scenario.
ZAP The OWASP Zed Attack Proxy (ZAP) is one of OWASP’s flagship projects due to its powerful features and popularity. ZAP uses its position between the user’s browser and the web application to intercept and inspect user requests, modify the contents if required, and then forward them to a web server. This is exactly the same process that occurs during a man-in-the-middle attack. ZAP is also designed to be used by security practitioners at all levels. Figure 15-26 shows the results of an attack conducted with nothing more than a target specified.
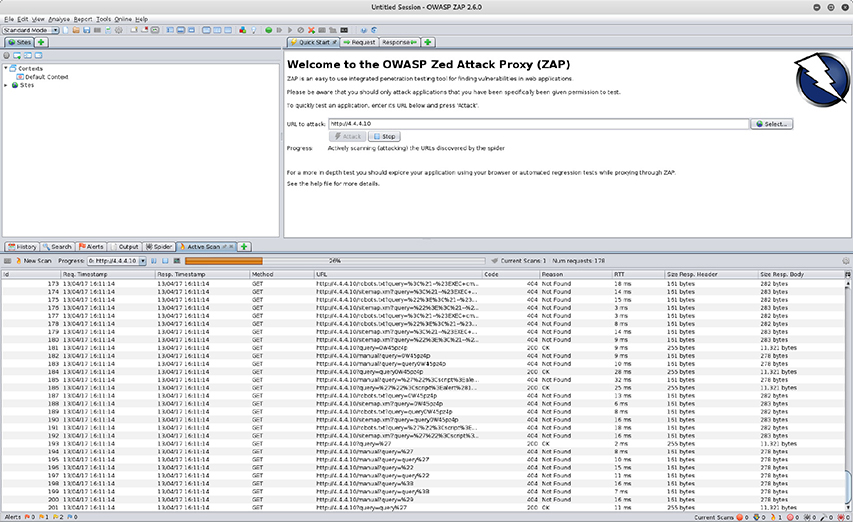
Figure 15-26 ZAP screen showing progress in active scanning attack
In this example, ZAP rapidly fabricates a list of GET request using known directories and files to test the site. These locations should not be publically viewable, so the results here will inform an administrator of misconfigurations in the server and unexpected data exposure.
Vega Vega is another cross-platform interception proxy written in Java. It provides automated scanning, injection discovery, and cross-site scripting vulnerability discovery through its user interface or via an API. Usage is similar to ZAP in that a user can launch a quick attack by identifying a target. As with ZAP, the list of results will include a short description of the discovery, why it’s important, and how best to remediate. An example of the information provided is shown in Figure 15-27.

Figure 15-27 Vega reporting a possible vulnerability in an Apache web service
Exploitative Tools
Not all vulnerabilities have exploits, but these software flaws open up the opportunity for clever programmers to bend the rules to gain unauthorized entry. Exploit code is code designed to take advantage of a software vulnerability to gain control over a system, access data, or prevent legitimate access to services through denial of service.
Exploitation Frameworks
Exploitation frameworks aim to provide security teams with the tools necessary to replicate attacks and validate vulnerabilities in order to prioritize security resources. Some of the more popular frameworks offer a range of penetration-testing options by providing easy access to well-known vulnerabilities, exploits, and security tools in an intuitive manner. Table 15-9 details two such frameworks: Metasploit and Nexpose.
Tools

Table 15-9 Comparison of Exploitation Frameworks
Scenario
After reading the vulnerability report you prepared a few weeks ago, your organization’s CISO has a much better sense of the assets on the network and their associated vulnerabilities. She presented your findings to company leadership, which then provided feedback and additional requests for information. She calls you back into the office to discuss the next step. She believes that the best thing to do is to identify the most serious vulnerabilities and apply either the appropriate patches or compensating controls. Before beginning this process, however, you want to make sure the vulnerabilities actually exist and are actually able to be exploited.
Metasploit Like many popular security tools, the Metasploit Framework began as an open source project and was later acquired and expanded to include paid options for commercial use. Initially developed under the larger Metasploit Project to develop and execute exploits against remote targets, the framework provides an easy way for security professionals to assess system vulnerabilities and determine exploitability. Although the Metasploit Framework itself is still free, Rapid7 offers several interfaces and professional options with a paid license. Every version ships with hundreds of exploits and payloads, referred to collectively as modules, which contain the relevant code and reference data. Figure 15-28 is a screenshot of the Metasploit command-line interface.
Figure 15-28 Metasploit welcome screen
Metasploit’s main strength is the versatility it provides by way of its modular design. Exploits can be combined with payloads to take advantage of flaws and execute code in a single effort. Figure 15-29 shows an example in which a user selects the PSExec Exploit for use against a Windows operating system, along with the various options presented for its usage.

Figure 15-29 Exploit selection command and options available for the module
Nexpose At its core, Nexpose is a vulnerability discovery and management tool. Because it integrates extremely well with Metasploit, it’s a natural choice for security analysts wanting to pivot quickly from analysis to exploitation without leaving the interface. Using one of the commercial options of Metasploit, called Metasploit Pro, it’s possible to connect to the Nexpose scan engine directly. Figure 15-30 shows a listing of vulnerabilities found during a routine scan, along with an indication of whether an exploit exists for that vulnerability. The Metasploit integration into Nexpose is useful in determining and prioritizing exploitable vulnerabilities on the network, while also reducing the burden of managing reports across the two systems.
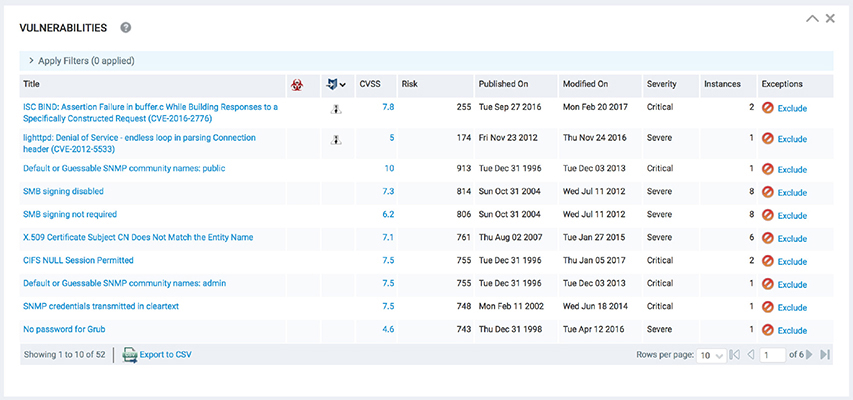
Figure 15-30 Nexpose vulnerabilities listing sorted by known exploits
Fuzzers
Software fuzzing is a technique used to discover software flaws by inputting random data into software to force instability or crashes. The resulting errors can often be traced back to the root cause by the fuzzing software for remediation and patching. Fuzzing is useful because programmers cannot always predict how their software will react given unexpected or malformed input. See Table 15-10 for a comparison of some fuzzers.
Tools
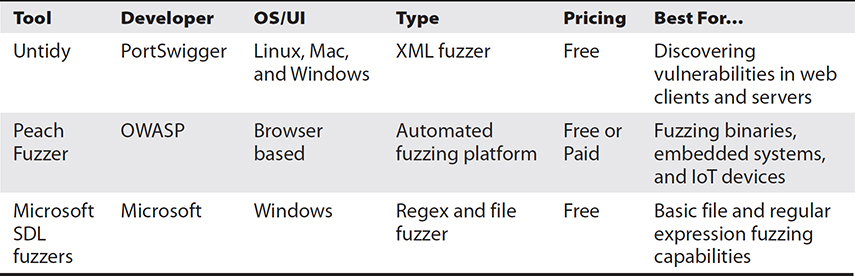
Table 15-10 Comparison of Fuzzers
Scenario
Your human resources team recently developed a public-facing online feedback submission system and reached out to your team for suggestions on how to test it before going live. Because the app relies heavily on user input, the developers have taken steps to ensure that user input is sanitized before being executed and stored. However, they want an extra bit of assurance and want to fuzz-test the application, including URLs, forms, and any user-generated content.
Untidy Untidy is a popular Extensible Markup Language (XML) fuzzer. Used to test web application clients and servers, untidy takes valid XML and modifies it before inputting it into the application. The untidy fuzzer is now part of the Peach Fuzzer project.
Peach Fuzzer The Peach Fuzzer is a powerful fuzzing suite that’s capable of testing a wide range of targets. Peach uses XML-based modules, called pits, to provide all the information needed to run the fuzz. These modules are configurable based on the testing needs. Before conducting a fuzz test, the user must specify the type of test, the target, and any monitoring settings desired. Figure 15-31 is a short listing of the pits available for image file and network protocol fuzzing.
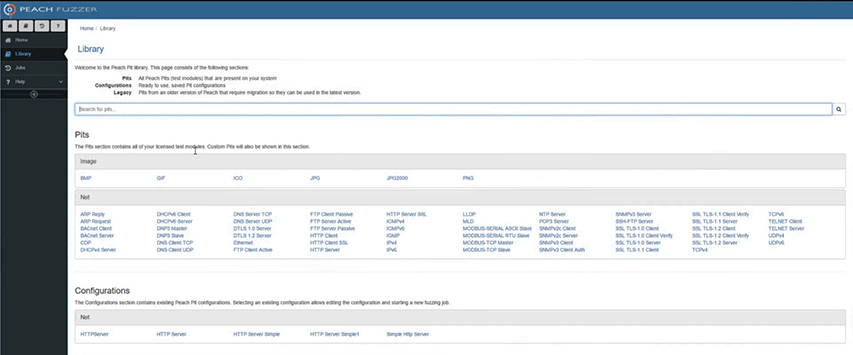
Figure 15-31 Peach library of fuzz testing modules available for use during a test
Microsoft SDL Fuzzers As part of its Security Development Lifecycle (SDL) toolset, Microsoft released two types of standalone fuzzers designed to be used in the verification phase of the SDL: the Minifuzz file fuzzer and the Regex Fuzzer. However, Microsoft has dropped support and no longer provides these applications for download. Figure 15-32 shows the setup screen for the SDL Regex Fuzzer.
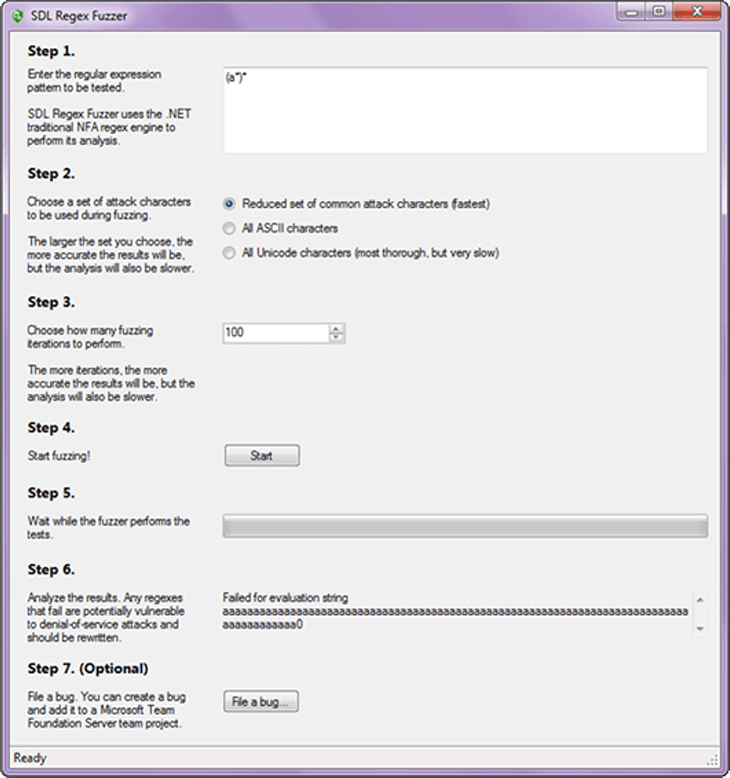
Figure 15-32 Setup screen for the Microsoft Security Development Lifecycle (SDL) Regex Fuzzer
Forensic Tools
Forensics in the real world is all about the application of the scientific method to investigate the circumstances of a crime. It relies heavily on the collection, preservation, and analysis of evidence such as fingerprints, DNA, and other artifacts to build the best picture possible of what happened. Digital forensics, as a branch of forensic science, relies on the same principles of discovery to build a timeline of what happened on our systems during a suspected attack.
Forensic Suites
Reconstructing what happened after the fact is inherently a difficult task, but we have many tools at our disposal to assist with this process. Forensic suites include a range of tools to uncover data thought to be lost, or data that might be lost easily, such as in the case of volatile memory. Because documentation is an important part of forensics, particularly in criminal investigations, some suites automatically document the evidence analysis progression. Table 15-11 details some of the most popular forensic suites available today.
Tools
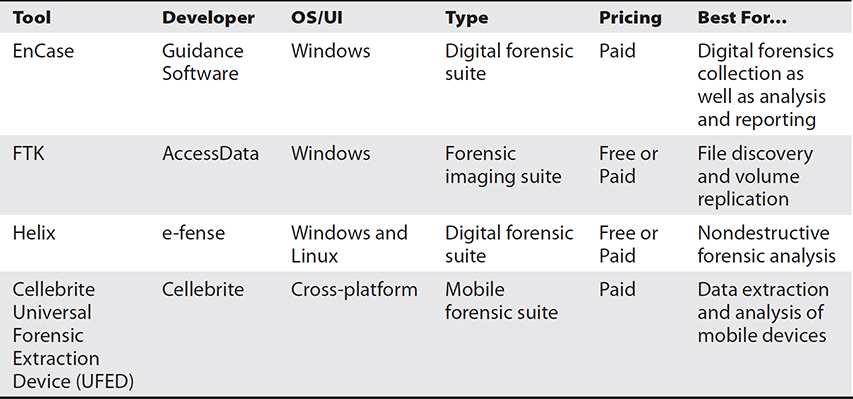
Table 15-11 Comparison of Forensic Suites
Scenario
You receive a tip from a friend of yours who leads a security team at another company. He tells you of a new type of ransomware affecting certain types of older systems and shares the pertinent details with you. You pass this information on to your team members and, fortunately, they were able to isolate a single machine that showed signs of compromise before more damage could be done on the network. Your security chief is concerned, however, because none of your detection systems were able to identify the malware before it infected that machine. He wants to learn more about how it happened, so he sends you to investigate the quarantined machine.
EnCase EnCase’s suite of tools is very popular with law enforcement and government for forensics missions because of its easy-to-use GUI and chain-of-custody features. The EnCase suite include tools for forensic acquisition, analysis, and report generation. EnCase’s Evidence File format is among the most common types of forensic imaging formats, due in part to its high portability. The imaged volume’s data, metadata, and hashes are all included in a single file.
FTK AccessData’s Forensic Toolkit, or FTK, is a popular choice for investigators needing to create forensic images of hard drives. FTK is a favorite for forensics analysis because of its built-in logging features, making the process of documentation easier for investigators looking to preserve details of the analysis itself. One of the more popular tools included in the FTK suite is the FTK Imager, a data preview and volume imaging tool.
Helix Helix3 Pro is the latest multiplatform forensic suite offered by e-fense. Based on the open source Knoppix live boot utility, Helix allows analysts to fully image all internal devices, including physical memory and hard disks. The program also includes utilities for mobile device analysis, offering the same nondestructive imaging features.
Cellebrite Cellebrite is a company that developed data transfer solutions for mobile carriers and has since moved into the mobile forensics market. Its flagship product, the Universal Forensic Extraction Device (UFED), is a handheld hardware device primarily marketed to law enforcement and military communities. With the UFED, a user can extract encrypted, deleted, or hidden data from select mobile phones. Cellebrite also provides evidence preservation using techniques such as write blocking during the data extraction procedure.
Hashing
Hashing is a common technique used to verify the integrity of files by creating a small unique value of fixed size, regardless of the size of the original file. Much like placing tamper-evident tape before sending out a shipment, a hash value aims to make it obvious if the contents of a file are changed. Hashing functions rely on the concept that no two files should have the same message digest, also referred to as fingerprints.
Tools
There are really only two cryptographic hashing algorithms in widespread use today: MD5 and the various flavors of SHA. Of these, MD5 and SHA-1 are known to be vulnerable to attacks. Still, they remain (for now) popular. The two tools with which you need to be familiar as a cybersecurity analyst are md5sum and shasum (see Table 15-12).
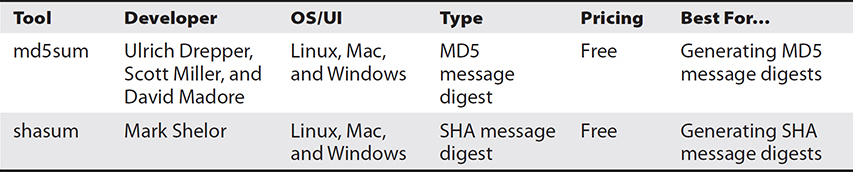
Table 15-12 Comparison of Hashing Tools
Scenario
One of your junior database analysts recently completed a rollout of new database software. Every night, he backs up the entire database to an offsite location and wants to know if there is a quick way to verify the integrity of the backup files. Ideally, he wants to perform the computation immediately after completing the backup and to do so directly from the command line.
md5sum Included with nearly every variant of Linux is the md5sum program, a simple utility that computes the 128-bit MD5 hash for a file specified. Although an MD5 is more reliable than a simple cyclic redundancy check (CDC) for verifying file integrity, its usage is no longer recommended because researchers have discovered methods to modify file content without resulting in a change to the MD5 hash. Taking a look at Figure 15-33, we can see that the md5sum utility is invoked from the command line, with the file location specified immediately after the command. The resulting output is the 128-bit MD5 fingerprint of the file.
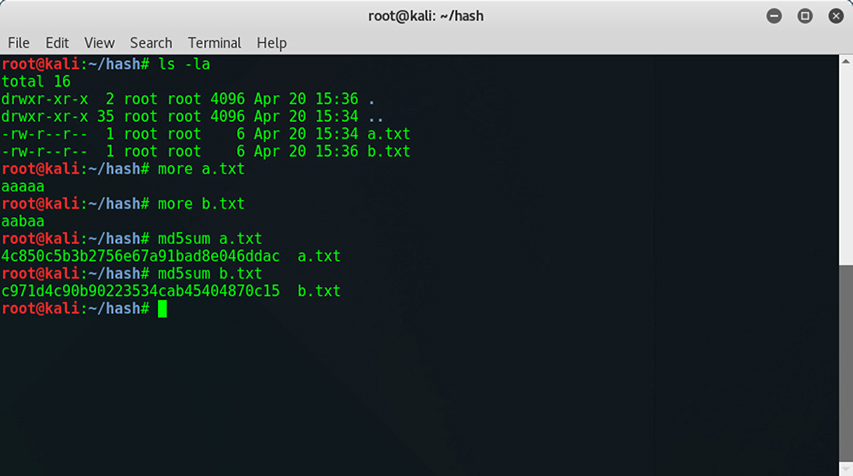
Figure 15-33 The md5sum utility in the command line
shasum The shasum utility was created as a quick way to generate SHA hashes from files. Like md5sum, the utility calculates message digests directly from the command line and inputs them to the standard output. Figure 15-34 shows two files, a.txt and b.txt, and their associated hashes as the output of each command. Using no options, the program will calculate the 160-bit SHA-1 message digest. Using the -a option, we can specify a different algorithm altogether.

Figure 15-34 The shasum utility in the command line
Password Cracking
A common target for attackers is the operating system password file. In Windows, the Security Accounts Manager (SAM) file is the database of user passwords. In modern Linux environments, the user information is stored in the /etc/passwd file, and the password hashes are stored in the /etc/shadow file. As you can imagine, these files are protected by the system using various cryptographic methods. However, it’s still possible to break into these files given the right tools.
Tools
The two most popular password-cracking tools among security professionals are John the Ripper, and Cain and Abel. Though their feature sets are very similar, there are subtle differences with which you may want to become acquainted (see Table 15-13).
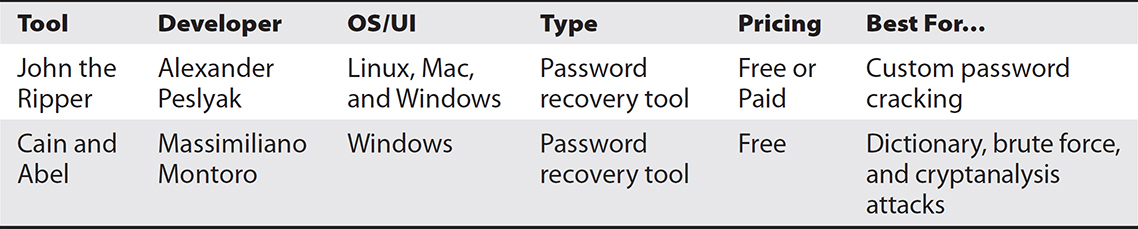
Table 15-13 Comparison of Password Crackers
John the Ripper John the Ripper is an open source password-cracking tool, initially developed for UNIX, that now has variations for many other operating systems. Figure 15-35 shows options for usage with the command-line tool. John runs attacks with wordlists, which reference a precompiled list of possible passwords, or by brute force, which tries many possible combinations in the character space. Additionally, John supports auto-detection of password hash types, the protective measure used by operation systems to prevent unauthorized viewing of the password file. The commercial version of John expands on the already impressive selection of hashes supported.

Figure 15-35 The John the Ripper utility in the command line
Cain and Abel Cain and Abel is a Windows password-cracking tool that can operate on sniffed network traffic or locally acquired password hashes. Note that Cain isn’t officially supported for operating systems newer than Windows Vista, and its use with those modern systems might require workarounds. Like John, Cain supports wordlist and brute-force attacks, but can also use rainbow tables to speed up its analysis. Normally, a password-cracking tool using a wordlist will take the given plaintext, compute the hash, and perform a search for that hash in the password file. Rainbow tables are pre-computed lists of hashes that the program will use to perform a reverse lookup of the possible password. In the case of the rainbow table, only the hash needs to be searched for, so this speeds up the cracking process significantly. The tradeoff is that rainbow tables can be extremely large in size.
Imaging
Imaging tools copy data from a source regardless of the file system that resides on the volume. This means that a hard drive running the Mac OS, Windows, or Linux can be copied in the same way using the same utility. Imaging tools usually allow for the entire contents of the drive to be duplicated to a single file in a remote destination. Unlike a regular file copy, forensic imaging also includes the file system’s slack and free space, where the remnants of deleted files may reside.
dd
Using the dd utility is just about the easiest way to make a bit-for-bit copy of a hard drive. You can find the program in nearly every Linux distribution as well as in the Mac OS. Its primary purpose is to copy or convert files, and accordingly there are several options for block sizes and image conversion during the imaging process that might assist in follow-on analysis. The following command will perform a bit-for-bit copy of hard drive “hda” to a file called case123.img using the options to set the block size to 4096 bytes and fill the rest of the block with null symbols should it encounter an error:
dd if=/dev/hda of=case123.img bs=4k conv=noerror,sync
Chapter Review
Despite being the longest chapter in this book, this could’ve been a lot lengthier. As a CySA+, you really ought to be familiar with every tool we described here. Ideally, you would be proficient with each. Our goal was not to provide you with the depth of knowledge we feel you should possess on them, but rather to give a high-level survey of these essential tools of the trade. We hope that you will use this as a springboard for your own self-study into any products with which you are not familiar. Though the exam will require only a general familiarity with these, your real-world performance will likely be enhanced by a deeper knowledge of the tools of the trade.
Questions
1. You are concerned about your ability to block zero-day exploits before they enter your network. Which of the following tools would best allow you to do this?
A. Wireshark
B. Imperva’s SecureSphere
C. Metasploit
D. Palo Alto Networks NGFW
2. What class of tools is best able to receive information from a variety of platforms, aggregate it into a data store, generate alerts, and allow users to query the data?
A. Interception proxy
B. SIEM
C. Fuzzer
D. HIPS
3. Which of the following is an example of a vulnerability scanner?
A. Bro
B. NAXSI
C. OpenVAS
D. Helix
4. To what class of tools does Metasploit belong?
A. Vulnerability scanners
B. Interception proxies
C. Password crackers
D. Exploitation frameworks
Use the following scenario to answer Questions 5–7:
Your company’s internal development team just developed a new web application for deployment onto the public-facing web server. You are trying to ensure that it conforms to best security practices and does not introduce any vulnerabilities into your systems.
5. Which would be the best tool to use if you want to ensure that the web application is not transmitting passwords in cleartext?
A. Nikto
B. FTK
C. Burp Suite
D. Aircrack-ng
6. Having tested the web application against all the input values you can think of, you decide to try random data to see if you can force instability or crashes. Which is the best tool for this purpose?
A. Untidy
B. Cellebrite
C. Cain and Abel
D. Qualys
7. You discover a vulnerability that causes the application to crash whenever it receives a password of length 256 or greater. This is the only flaw you find, and you are under immense pressure to get the app online. The development team will need a week to fix the issue. Assuming you are already using it, which of the following security tools might allow you to mitigate the risk and allow the app to go online by tomorrow?
A. AlienVault
B. Sourcefire
C. Nessus
D. Metasploit
Use the following scenario to answer Questions 8–10:
You are an analyst at a large organization and are tracking a fairly sophisticated adversary who appears to have compromised some hosts on your network. This actor’s tactics, techniques, and procedures (TTPs), gleaned from a threat intelligence feed, include consolidating files on an internal, compromised host, compressing them onto one file, encrypting them, and then sending them to an external server. The internal aggregator runs a server on TCP port 1337.
8. Using which of the following tools might you best determine if any of your internal hosts are listening on port 1337?
A. Snort
B. Wireshark
C. nmap
D. netstat
9. You find a host running an illicit server on port 1337 and move it to an isolated virtual local area network (VLAN) to prevent further data loss. The next step is to find any other compromised hosts that might be trying to communicate with the rogue server. You quickly provision a new Linux host with the same hostname and IP address and then start a web server on port 1337. Which tool might let you track compromised hosts trying to connect to that socket?
A. tcpdump
B. ifconfig
C. nslookup
D. SHAsum
10. You want to make a forensic image of the isolated server’s hard drive and then ensure the integrity of all the copied data. Which combination of tools is best suited for these tasks? (Choose two.)
A. mv
B. cp
C. md5sum
D. dd
E. shasum
Answers
1. D. Next-Generation Firewalls (NGFWs), such as those made by Palo Alto Networks, can connect to threat intelligence feeds to quickly identify new attacks and share those with others with similar firewalls. They also have the ability to run applications in a sandbox to determine whether they are benign or malicious before allowing them into the network.
2. B. Security information and event management (SIEM) systems are designed to collect, store, analyze, and report security information and events.
3. C. OpenVAS (in addition to Qualys, Nessus, Nexpose, Nikto, and Microsoft Baseline Security Analyzer) is a vulnerability scanner with which you should be familiar.
4. D. Metasploit is the most widely used open source exploitation framework.
5. C. Burp Suite is an integrated web application testing platform often used to map and analyze a web application’s vulnerabilities. It is able to intercept web traffic and allow analysts to examine each request and response.
6. A. The class of tools that tests applications by bombarding them with random values is called fuzzing tools. Untidy, Peach Fuzzer, and Microsoft’s Regex Fuzzer are all examples covered in this chapter.
7. B. Sourcefire is an intrusion prevention system that can be configured to block traffic to your web server containing the problematic password values. None of the other tools listed is an IPS or could reasonably be expected to perform the task at hand.
8. C. Though any of the options listed might work in certain specific conditions, nmap is the best answer because you can use it to quickly and remotely check all hosts on your network. Snort and Wireshark would only be able to identify the server(s) if they captured traffic to/from it. Netstat would require you to remotely log into all hosts and see if port 1337 was listening, which is a very time-consuming way to check a large network.
9. A. Tcpdump can be configured to capture only traffic destined for a given port on the local host, which would over time collect the source IP addresses of any other compromised hosts. Furthermore, tcpdump can capture packets and save them to a remote shared file, which would allow you to monitor it for changes instead of manually checking time and again.
10. D, E. The dd utility is often used to make a bit-for-bit forensic copy of secondary storage devices such as hard disk drives. The cp (copy) command or mv (move) command could conceivably be used to copy or move specific files, respectively, but certainly neither would be able to make a forensic duplicate of a disk or file system. In order to ensure the integrity of the data, you could use either md5sum or shasum, but the latter is preferred, particularly if you use SHA-256 or better.