Chapter 10. Hardware Assurance Best Practices
This chapter covers the following topics related to Objective 2.3 (Explain hardware assurance best practices) of the CompTIA Cybersecurity Analyst (CySA+) CS0-002 certification exam:
• Hardware root of trust: Introduces the Trusted Platform Module (TPM) and hardware security module (HSM)
• eFuse: Covers the dynamic real-time reprogramming of computer chips
• Unified Extensible Firmware Interface (UEFI): Discusses the newer UEFI firmware interface
• Trusted foundry: Describes a program for hardware sourcing assurance
• Secure processing: Covers Trusted Execution, secure enclave, processor security extensions, and atomic execution
• Anti-tamper: Explores methods of preventing physical attacks
• Self-encrypting drive: Covers automatic drive protections
• Trusted firmware updates: Discusses methods for safely acquiring firmware updates
• Measured Boot and attestation: Covers boot file protections
• Bus encryption: Describes the use of encrypted program instructions on a data bus
Organizations acquire hardware and services as part of day-to-day business. The supply chain for tangible property is vital to every organization. An organization should understand all risks for the supply chain and implement a risk management program that is appropriate for it. This chapter discusses best practices for ensuring that all hardware is free of security issues out of the box.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz enables you to assess whether you should read the entire chapter. If you miss no more than one of these ten self-assessment questions, you might want to skip ahead to the “Exam Preparation Tasks” section. Table 10-1 lists the major headings in this chapter and the “Do I Know This Already?” quiz questions covering the material in those headings so that you can assess your knowledge of these specific areas. The answers to the “Do I Know This Already?” quiz appear in Appendix A.
Table 10-1 “Do I Know This Already?” Foundation Topics Section-to-Question Mapping
1. Which of the following is a draft publication that gives guidelines on hardware-rooted security in mobile devices?
a. NIST SP 800-164
b. IEEE 802.11ac
c. FIPS 120
d. IEC/IOC 270017
2. Which of the following allows for the dynamic real-time reprogramming of computer chips?
a. TAXII
b. eFuse
c. UEFI
d. TPM
3. Which of the following is designed as a replacement for the traditional PC BIOS?
a. TPM
b. Secure boot
c. UEFI
d. NX bit
4. Which of the following ensures that systems have access to leading-edge integrated circuits from secure, domestic sources?
a. DoD
b. FIPS 120
c. OWASP
d. Trusted Foundry
5. Which of the following is a part of an operating system that cannot be compromised even when the operating system kernel is compromised?
a. Secure enclave
b. Processor security extensions
c. Atomic execution
d. XN bit
6. Which of the following technologies can zero out sensitive data if it detects penetration of its security and may even do this with no power ?
a. TPM
b. Anti-tamper
c. Secure enclave
d. Measured boot
7. Which of the following is used to provide transparent encryption on self-encrypting drives?
a. DEK
b. TPM
c. UEFI
d. ENISA
8. Which of the following is the key to trusted firmware updates?
a. Obtain firmware updates only from the vendor directly
b. Use a third-party facilitator to obtain updates
c. Disable Secure Boot
d. Follow the specific directions with the update
9. Windows Secure Boot is an example of what technology?
a. Security extensions
b. Secure enclave
c. UEFI
d. Measured boot
10. What is used by newer Microsoft operating systems to protect certificates, BIOS, passwords, and program authenticity?
a. Security extensions
b. Bus encryption
c. UEFI
d. Secure enclaves
Foundation Topics
Hardware Root of Trust
NIST SP 800-164 is a draft Special Publication that gives guidelines on hardware-rooted security in mobile devices. It defines three required security components for mobile devices: Roots of Trust (RoTs), an application programming interface (API) to expose the RoTs to the platform, and a Policy Enforcement Engine (PEnE).
Roots of Trust are the foundation of assurance of the trustworthiness of a mobile device. RoTs must always behave in an expected manner because their misbehavior cannot be detected. Hardware RoTs are preferred over software RoTs due to their immutability, smaller attack surfaces, and more reliable behavior. They can provide a higher degree of assurance that they can be relied upon to perform their trusted function or functions. Software RoTs could provide the benefit of quick deployment to different platforms. To support device integrity, isolation, and protected storage, devices should implement the following RoTs:

• Root of Trust for Storage (RTS)
• Root of Trust for Verification (RTV)
• Root of Trust for Integrity (RTI)
• Root of Trust for Reporting (RTR)
• Root of Trust for Measurement (RTM)
The RoTs need to be exposed by the operating system to applications through an open API. This provides application developers a set of security services and capabilities they can use to secure their applications and protect the data they process. By providing an abstracted layer of security services and capabilities, these APIs can reduce the burden on application developers to implement low-level security features, and instead allow them to reuse trusted components provided in the RoTs and the OS. The APIs should be standardized within a given mobile platform and, to the extent possible, across platforms. Applications can use the APIs, and the associated RoTs, to request device integrity reports, protect data through encryption services provided by the RTS, and store and retrieve authentication credentials and other sensitive data.
The PEnE enforces policies on the device with the help of other device components and enables the processing, maintenance, and management of policies on both the device and in the information owners’ environments. The PEnE provides information owners with the ability to express the control they require over their information. The PEnE needs to be trusted to implement the information owner’s requirements correctly and to prevent one information owner’s requirements from adversely affecting another’s. To perform key functions, the PEnE needs to be able to query the device’s configuration and state.
Mobile devices should implement the following three mobile security capabilities to address the challenges with mobile device security:
• Device integrity: Device integrity is the absence of corruption in the hardware, firmware, and software of a device. A mobile device can provide evidence that it has maintained device integrity if its software, firmware, and hardware configurations can be shown to be in a state that is trusted by a relying party.
• Isolation: Isolation prevents unintended interaction between applications and information contexts on the same device.
• Protected storage: Protected storage preserves the confidentiality and integrity of data on the device while at rest, while in use (in the event an unauthorized application attempts to access an item in protected storage), and upon revocation of access.
Trusted Platform Module (TPM)
Controlling network access to devices is helpful, but in many cases, devices such as laptops, tablets, and smartphones leave your network, leaving behind all the measures you have taken to protect the network. There is also a risk of these devices being stolen or lost. For these situations, the best measure to take is full disk encryption.
The best implementation of full disk encryption requires and makes use of a Trusted Platform Module (TPM) chip. A TPM chip is a security chip installed on a computer’s motherboard that is responsible for protecting symmetric and asymmetric keys, hashes, and digital certificates. This chip provides services to protect passwords and encrypt drives and digital rights, making it much harder for attackers to gain access to the computers that have TPM chips enabled.
Two particularly popular uses of TPM are binding and sealing. Binding actually “binds” the hard drive through encryption to a particular computer. Because the decryption key is stored in the TPM chip, the hard drive’s contents are available only when the drive is connected to the original computer. But keep in mind that all the contents are at risk if the TPM chip fails and a backup of the key does not exist.
Sealing, on the other hand, “seals” the system state to a particular hardware and software configuration. This prevents attackers from making any changes to the system. However, it can also make installing a new piece of hardware or a new operating system much harder. The system can only boot after the TPM chip verifies system integrity by comparing the original computed hash value of the system’s configuration to the hash value of its configuration at boot time.
A TPM chip consists of both static memory and versatile memory that is used to retain the important information when the computer is turned off:

• Endorsement key (EK): The EK is persistent memory installed by the manufacturer that contains a public/private key pair.
• Storage root key (SRK): The SRK is persistent memory that secures the keys stored in the TPM.
• Attestation identity key (AIK): The AIK is versatile memory that ensures the integrity of the EK.
• Platform configuration register (PCR) hash: A PCR hash is versatile memory that stores data hashes for the sealing function.
• Storage keys: A storage key is versatile memory that contains the keys used to encrypt the computer’s storage, including hard drives, USB flash drives, and so on.
BitLocker and BitLocker to Go by Microsoft are well-known full disk encryption products. The former is used to encrypt hard drives, including operating system drives, and the latter is used to encrypt information on portable devices such as USB devices. However, there are other options. Additional whole disk encryption products include
• PGP Whole Disk Encryption
• SecurStar DriveCrypt
• Sophos SafeGuard
• Trend Micro Maximum Security
Virtual TPM
A virtual TPM (VTPM) chip is a software object that performs the functions of a TPM chip. It is a system that enables trusted computing for an unlimited number of virtual machines on a single hardware platform. A VTPM makes secure storage and cryptographic functions available to operating systems and applications running in virtual machines.
Figure 10-1 shows one possible implementation of VTPM by IBM. The TPM chip in the host system is replaced by a more powerful VTPM (PCIXCC-vTPM). The virtual machine (VM) named Dom-TPM is a VM whose only purpose is to proxy for the PCIXCC-vTPM and make TPM instances available to all other VMs running on the system.

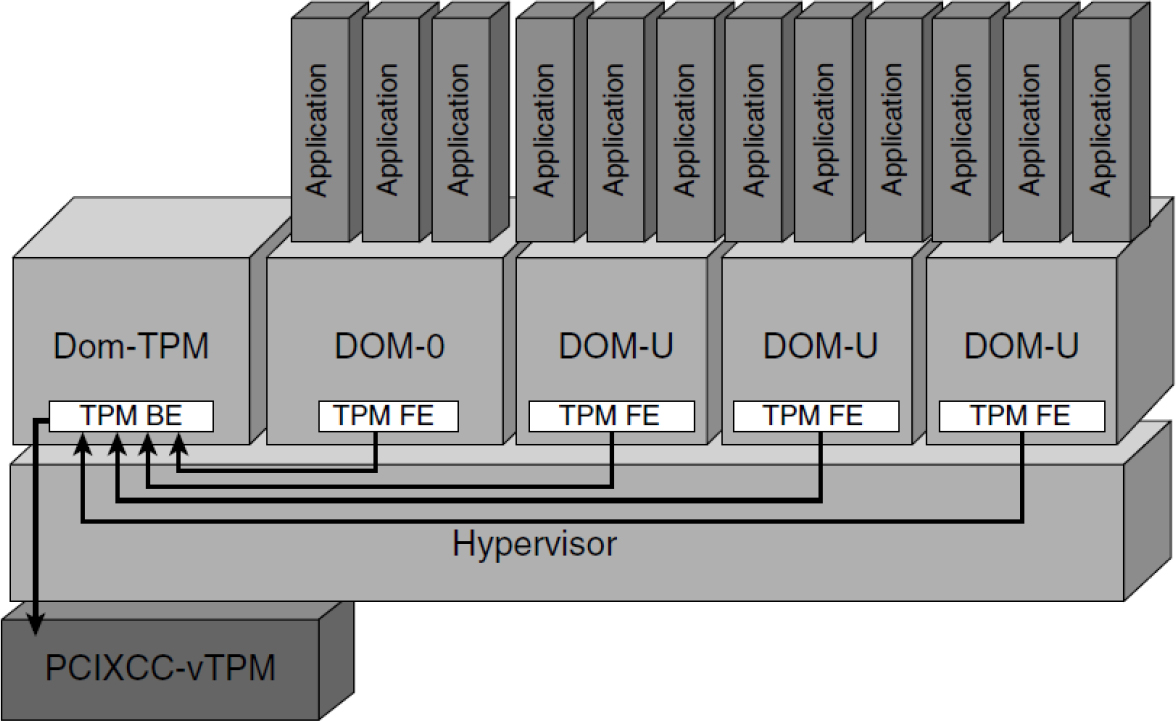
Figure 10-1 vTPM Possible Solution 1
Another possible approach suggested by IBM is to run VTPMs on each VM, as shown in Figure 10-2. In this case, the VM named Dom-TPM talks to the physical TPM chip in the host and maintains separate TPM instances for each VM.

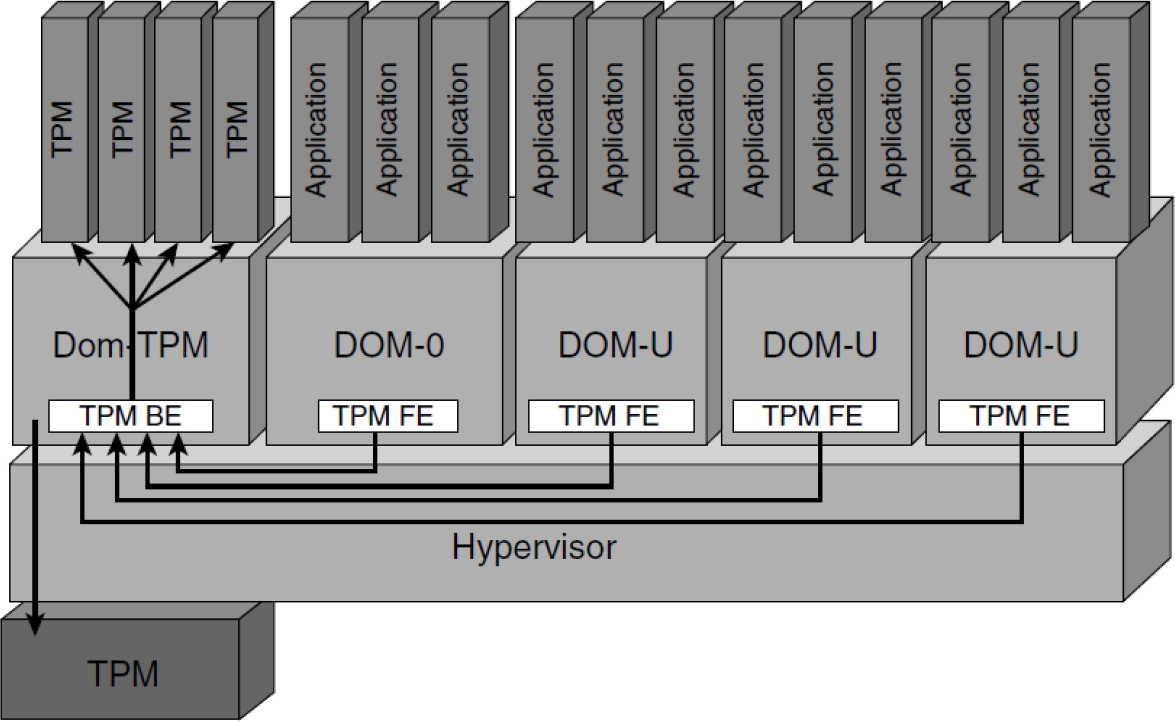
Figure 10-2 VTPM Possible Solution 2
Hardware Security Module (HSM)
A hardware security module (HSM) is an appliance that safeguards and manages digital keys used with strong authentication and provides crypto processing. It attaches directly to a computer or server. Among the functions of an HSM are

• Onboard secure cryptographic key generation
• Onboard secure cryptographic key storage and management
• Use of cryptographic and sensitive data material
• Offloading of application servers for complete asymmetric and symmetric cryptography
HSM devices can be used in a variety of scenarios, including the following:
• In a PKI environment to generate, store, and manage key pairs
• In card payment systems to encrypt PINs and to load keys into protected memory
• To perform the processing for applications that use TLS/SSL
• In Domain Name System Security Extensions (DNSSEC; a secure form of DNS that protects the integrity of zone files) to store the keys used to sign the zone file
There are some drawbacks to an HSM, including the following:

• High cost
• Lack of a standard for the strength of the random number generator
• Difficulty in upgrading
When selecting an HSM product, you must ensure that it provides the services needed, based on its application. Remember that each HSM has different features and different encryption technologies, and some HSM devices might not support a strong enough encryption level to meet an enterprise’s needs. Moreover, you should keep in mind the portable nature of these devices and protect the physical security of the area where they are connected.
MicroSD HSM
A microSD HSM is an HSM that connects to the microSD port on a device that has such a port. The card is specifically suited for mobile apps written for Android and is supported by most Android phones and tablets with a microSD card slot.
Moreover, some microSD cards can be made to support various cryptographic algorithms, such as AES, RSA, SHA-1, SHA-256, and Triple DES, as well as the Diffie-Hellman key exchange. This is an advantage over microSD cards that do not support this, which enables them to provide the same protections as microSD HSM.

eFuse
Computer logic is generally hard-coded onto a chip and cannot be changed after the chip is manufactured. An eFuse allows for the dynamic real-time reprogramming of computer chips. Utilizing a set of eFuses, a chip manufacturer can allow for the circuits on a chip to change while it is in operation.
One use is to prevent downgrading the firmware of a device. Systems equipped with an eFuse will check the number of burnt fuses before attempting to install new firmware. If too many fuses are burnt (meaning the firmware to be installed is older than the current firmware), then the bootloader will prevent installation of the older firmware.
An eFuse can also be used to help secure a stolen device. For example, the Samsung eFuse uses an eFuse to indicate when an untrusted (non-Samsung) path is discovered. Once the eFuse is set (when the path is discovered), the device cannot read the data previously stored.
Unified Extensible Firmware Interface (UEFI)
A computer’s BIOS contains the basic instruction that a computer needs to boot and load the operating system from a drive. The process of updating the BIOS with the latest software is referred to as flashing the BIOS. Security professionals should ensure that any BIOS updates are obtained from the BIOS vendor and have not been tampered with in any way.
The traditional BIOS has been replaced with the Unified Extensible Firmware Interface (UEFI). UEFI maintains support for legacy BIOS devices, but is considered a more advanced interface than traditional BIOS. BIOS uses the master boot record (MBR) to save information about the hard drive data, while UEFI uses the GUID partition table (GPT). BIOS partitions were a maximum of 4 partitions, each being only 2 terabytes (TB). UEFI allows up to 128 partitions, with the total disk limit being 9.4 zettabytes (ZB) or 9.4 billion terabytes. UEFI is also faster and more secure than traditional BIOS. UEFI Secure Boot requires boot loaders to have a digital signature.
UEFI is an open standard interface layer between the firmware and the operating system that requires firmware updates to be digitally signed. Security professionals should understand the following points regarding UEFI:
• Designed as a replacement for traditional PC BIOS.
• Additional functionality includes support for Secure Boot, network authentication, and universal graphics drivers.
• Protects against BIOS malware attacks including rootkits.
Secure Boot requires that all boot loader components (e.g., OS kernel, drivers) attest to their identity (digital signature) and the attestation is compared to the trusted list. More on Secure/Measured Boot and attestation will be covered later in the “Measured Boot and Attestation” section.
• When a computer is manufactured, a list of keys that identify trusted hardware, firmware, and operating system loader code (and in some instances, known malware) is embedded in the UEFI.
• Ensures the integrity and security of the firmware.
• Prevents malicious files from being loaded.
• Can be disabled for backward compatibility.
UEFI operates between the OS layer and the firmware layer, as shown in Figure 10-3.


Figure 10-3 UEFI
Trusted Foundry
You must be concerned with the safety and the integrity of the hardware that you purchase. The following are some of the methods used to provide this assurance:

• Trusted Foundry: The Trusted Foundry program can help you exercise care in ensuring the authenticity and integrity of the components of hardware purchased from a vendor. This U.S. Department of Defense (DoD) program identifies “trusted vendors” and ensures a “trusted supply chain.” A trusted supply chain begins with trusted design and continues with trusted mask, foundry, packaging/assembly, and test services. It ensures that systems have access to leading-edge integrated circuits from secure, domestic sources. At the time of this writing, 77 vendors have been certified as trusted.
• Source authenticity of hardware: When purchasing hardware to support any network or security solution, a security professional must ensure that the hardware’s authenticity can be verified. Just as expensive consumer items such as purses and watches can be counterfeited, so can network equipment. While the dangers with counterfeit consumer items are typically confined to a lack of authenticity and potentially lower quality, the dangers presented by counterfeit network gear can extend to the presence of backdoors in the software or firmware. Always purchase equipment directly from the manufacturer when possible, and when purchasing from resellers, use caution and insist on a certificate of authenticity. In any case where the price seems too good to be true, keep in mind that it may be an indication the gear is not authentic.
• OEM documentation: One of the ways you can reduce the likelihood of purchasing counterfeit equipment is to insist on the inclusion of verifiable original equipment manufacturer (OEM) documentation. In many cases, this paperwork includes anti-counterfeiting features. Make sure to use the vendor website to verify all the various identifying numbers in the documentation.
Secure Processing
Secure processing is a concept that encompasses a variety of technologies to prevent to prevent any insecure actions on the part of the CPU or processor. In some cases these technologies involve securing the actions of the processor itself, while other approaches tackle the issue where the data is stored. This section introduces some of these technologies and approaches.
Trusted Execution
Trusted Execution (TE) is a collection of features that is used to verify the integrity of the system and implement security policies, which together can be used to enhance the trust level of the complete system. An example is the Intel Trusted Execution Technology (Intel TXT). This approach is shown in Figure 10-4.
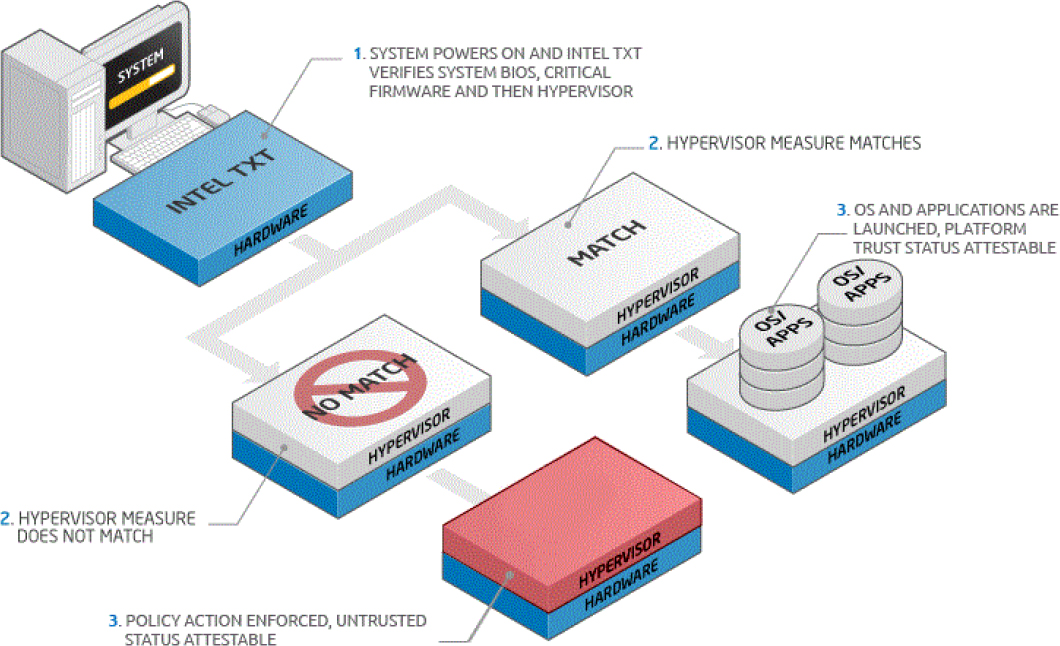
Figure 10-4 Intel Trusted Execution Technology
Secure Enclave
A secure enclave is a part of an operating system that cannot be compromised even when the operating system kernel is compromised, because the enclave has its own CPU and is separated from the rest of the system. This means security functions remain intact even when someone has gained control of the OS. Secure enclaves are a relatively recent technology being developed to provide additional security. Cisco, Microsoft, and Apple all have implementations of secure enclaves that differ in implementation but all share the same goal of creating an area that cannot be compromised even when the OS is.
Processor Security Extensions
Processor security extensions are sets of security-related instruction codes that are built into some modern CPUs. An example is Intel Software Guard Extensions (Intel SGX). It defines private regions of memory, called enclaves, whose contents are protected and unable to be either read or saved by any process outside the enclave itself, including processes running at higher privilege levels.
Another processor security technique is the use of the NX and XN bits. These bits are related to processors. Their respective meanings are as follows:

• NX (no-execute) bit: Technology used in CPUs to segregate areas of memory for use by either storage of processor instructions (code) or storage of data
• XN (never execute) bit: Method for specifying areas of memory that cannot be used for execution
When these bits are available in the architecture of the system, they can be used to protect sensitive information from memory attacks. By utilizing the capability of the NX bit to segregate memory into areas where storage of processor instructions (code) and storage of data are kept separate, many attacks can be prevented. Also, the capability of the XN bit to mark certain areas of memory that are off-limits to execution of code can prevent other memory attacks as well.
Atomic Execution
Atomic execution in concurrent programming are program operations that run independently of any other processes (threads). Making the operation atomic consists of using synchronization mechanisms to make sure that the operation is seen, from any other thread, as a single, atomic operation. This increases security by preventing one thread from viewing the state of the data when the first thread is still in the middle of the operation. Atomicity also means that the operation of the thread is either completely finished or is rolled back to its initial state (there’s no such thing as partially done).
Anti-Tamper
Anti-tamper technology is designed to prevent access to sensitive information and encryption keys on a device. Anti-tamper processors, for example, store and process private or sensitive information, such as private keys or electronic money credit. The chips are designed so that the information is not accessible through external means and can be accessed only by the embedded software, which should contain the appropriate security measures, such as required authentication credentials. Some of these chips take a different approach and zero out the sensitive data if they detect penetration of their security, and some can even do this with no power.
It also should not be possible for unauthorized persons to access and change the configuration of any devices. This means additional measures should be followed to prevent this. Tampering includes defacing, damaging, or changing the configuration of a device. Integrity verification programs should be used by applications to look for evidence of data tampering, errors, and omissions.
Self-Encrypting Drives
Self-encrypting drives do exactly as the name implies: they encrypt themselves without any user intervention. The process is so transparent to the user that the user may not even be aware the encryption is occurring. It uses a unique and random data encryption key (DEK). When data is written to the drive, it is encrypted, and when the data is read from the drive, it is decrypted, as shown in Figure 10-5.
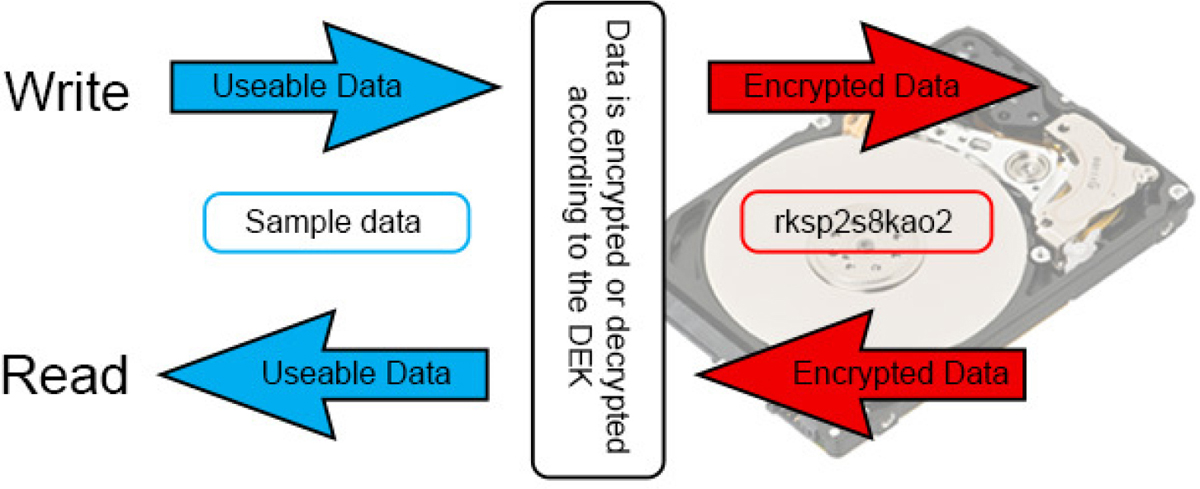
Figure 10-5 Self-encrypting drive
Trusted Firmware Updates
Hardware and firmware vulnerabilities are expected to become an increasing target for sophisticated attackers. While typically only successful when mounted by the skilled hands of a nation-state or advanced persistent threat (APT) group, an attack on hardware and firmware can be devastating because this firmware forms the platform for the entire device.
Firmware includes any type of instructions stored in non-volatile memory devices such as read-only memory (ROM), electrically erasable programmable read-only memory (EPROM), or Flash memory. BIOS and UEFI code are the most common examples for firmware. Computer BIOS doesn’t go bad; however, it can become out of date or contain bugs. In the case of a bug, an upgrade will correct the problem. An upgrade may also be indicated when the BIOS doesn’t support some component that you would like to install, such as a larger hard drive or a different type of processor.
Today’s BIOS is typically written to an EEPROM chip and can be updated through the use of software. Each manufacturer has its own method for accomplishing this. Check out the manufacturer’s documentation for complete details. Regardless of the exact procedure used, the update process is referred to as flashing the BIOS. It means the old instructions are erased from the EEPROM chip, and the new instructions are written to the chip. Firmware can be updated by using an update utility from the motherboard vendor. In many cases, the steps are as follows.

Step 1. Download the update file to a flash drive.
Step 2. Insert the flash drive and reboot the machine.
Step 3. Use the specified key sequence to enter the UEFI/BIOS setup.
Step 4. If necessary, disable Secure Boot.
Step 5. Save the changes and reboot again.
Step 6. Re-enter the CMOS settings.
Step 7. Choose the boot options and boot from the flash drive.
Step 8. Follow the specific directions with the update to locate the upgrade file on the flash drive.
Step 9. Execute the file (usually by typing flash).
Step 10. While the update is completing, ensure that you maintain power to the device.
The key to trusted firmware updates is contained in Step 1. Only obtain firmware updates from the vendor directly. Never use a third-party facilitator for this. Also make sure you verify the hash value that comes along with the update to ensure that it has not been altered since its creation.
Measured Boot and Attestation
Attestation is the process of insuring or attesting to the fact that a piece of software or firmware has integrity or that it has not been altered from its original state. It is used in several boot methods to check all elements used in the boot process to ensure that malware has not altered the files or introduced new files into the process. Let’s look at some of these Secure Boot methods.
Measured Boot, also known as Secure Boot, is a term that applies to several technologies that follow the Secure Boot standard. Its implementations include Windows Secure Boot, measured launch, and Integrity Measurement Architecture (IMA). Figure 10-6 shows the three main actions related to Secure Boot in Windows, which are described in the following list:
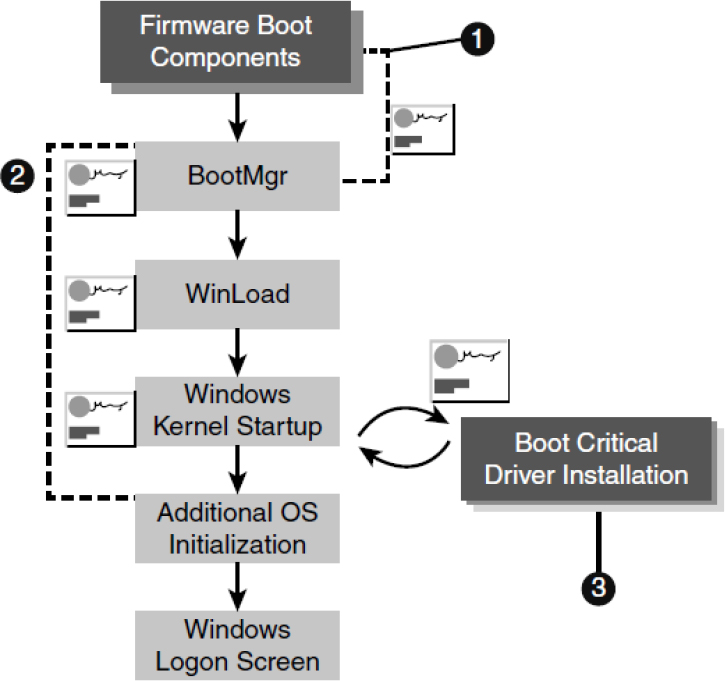

Figure 10-6 Secure Boot
1. The firmware verifies all UEFI executable files and the OS loader to be sure they are trusted.
2. Windows boot components verify the signature on each component to be loaded. Any untrusted components are not loaded and trigger remediation.
3. The signatures on all boot-critical drivers are checked as part of Secure Boot verification in Winload (Windows Boot Loader) and by the Early Launch Anti-Malware driver.
The disadvantage is that systems that ship with UEFI Secure Boot enabled do not allow the installation of any other operating system. This prevents installing any other operating systems or running any live Linux media.
Measured Launch
A measured launch is a launch in which the software and platform components have been identified, or “measured,” using cryptographic techniques. The resulting values are used at each boot to verify trust in those components. A measured launch is designed to prevent attacks on these components (system and BIOS code) or at least to identify when these components have been compromised. It is part of Intel TXT. TXT functionality is leveraged by software vendors including HyTrust, PrivateCore, Citrix, and VMware.
An application of measured launch is Measured Boot by Microsoft in Windows 10 and Windows Server 2019. It creates a detailed log of all components that loaded before the anti-malware. This log can be used to both identify malware on the computer and maintain evidence of boot component tampering. One possible disadvantage of measured launch is potential slowing of the boot process.
Integrity Measurement Architecture
Another approach that attempts to create and measure the runtime environment is an open source trusted computing component called Integrity Measurement Architecture (IMA), mentioned earlier in this chapter. IMA creates a list of components and anchors the list to the TPM chip. It can use the list to attest to the system’s runtime integrity.
Bus Encryption
The CPU is connected to an address bus. Memory and I/O devices recognize this address bus. These devices can then communicate with the CPU, read requested data, and send it to the data bus. Bus encryption protects the data traversing these buses. Bus encryption is used by newer Microsoft operating systems to protect certificates, BIOS, passwords, and program authenticity. Bus encryption is necessary not only to prevent tampering of encrypted instructions that may be easily discovered on a data bus or during data transmission, but also to prevent discovery of decrypted instructions that may reveal security weaknesses that an intruder can exploit.
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have several choices for exam preparation: the exercises here, Chapter 22, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep Software Online.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 10-2 lists a reference of these key topics and the page numbers on which each is found.

Table 10-2 Key Topics in Chapter 10

Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
hardware security module (HSM)
Unified Extensible Firmware Interface (UEFI)
Review Questions
1. RoTs need to be exposed by the operating system to applications through an open ___________.
2. List at least one of the contents of a TPM chip.
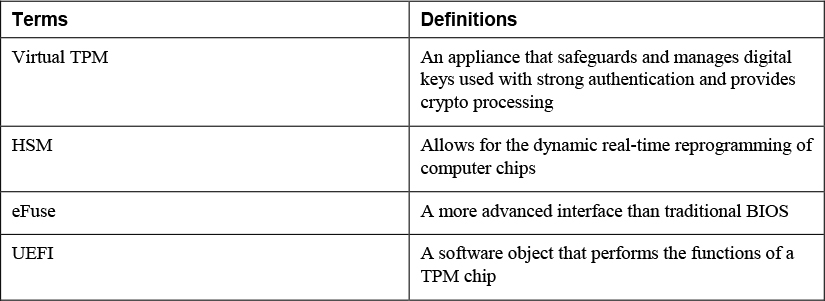
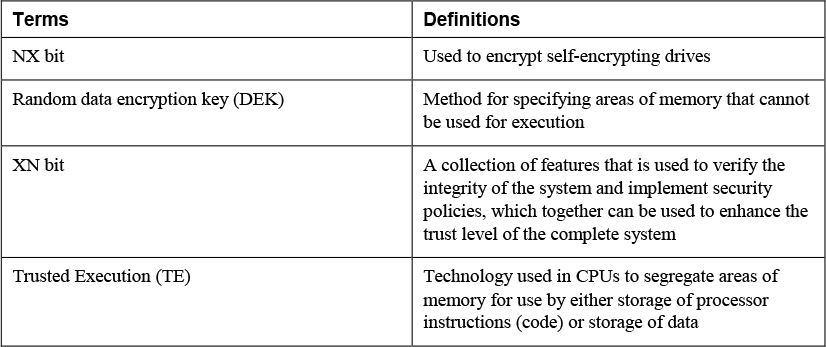
3. Match the following terms with their definitions.
4. _______________ requires that all boot loader components (e.g., OS kernel, drivers) attest to their identity (digital signature) and the attestation is compared to the trusted list.
5. List the Intel example of the implementation of processor security extensions.
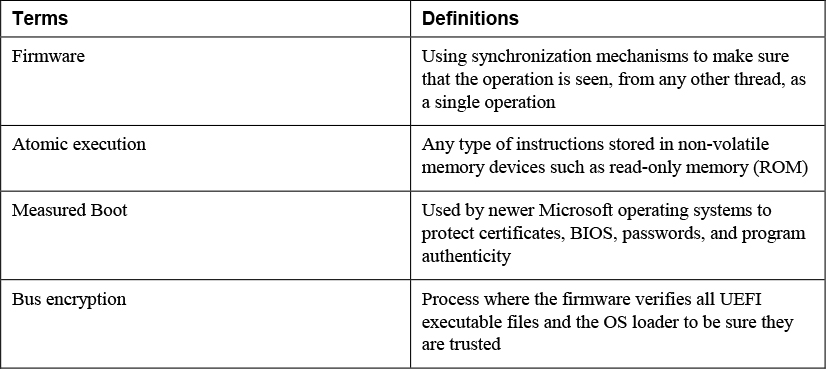
6. Match the following terms with their definitions.
7. _____________ creates a list of components and anchors the list to the TPM chip. It can use the list to attest to the system’s runtime integrity.
8. What is the disadvantage of systems that ship with UEFI Secure Boot enabled?
9. Match the following terms with their definitions.
10. The traditional BIOS has been replaced with the ____________________.
