Chapter 5. Threats and Vulnerabilities Associated with Specialized Technology
This chapter covers the following topics related to Objective 1.5 (Explain the threats and vulnerabilities associated with specialized technology) of the CompTIA Cybersecurity Analyst (CySA+) CS0-002 certification exam:
• Mobile: Discusses threats specific to the mobile environment
• Internet of Things (IoT): Covers threats specific to the IoT
• Embedded: Describes threats specific to embedded systems
• Real-time operating system (RTOS): Covers threats specific to an RTOS
• System-on-Chip (SoC): Investigates threats specific to an SoC
• Field programmable gate array (FPGA): Covers threats specific to FPGAs
• Physical access control: Discusses threats specific to physical access control systems
• Building automation systems: Covers threats specific to building automation systems
• Vehicles and drones: Describes threats specific to vehicles and drones
• Workflow and process automation systems: Covers threats specific to workflow and process automation systems
• Incident Command System (ICS): Discusses the use of ICS
• Supervisory control and data acquisition (SCADA): Covers systems that operate with coded signals over communication channels to provide control of remote equipment
In some cases, the technologies that we create and develop to enhance our ability to control the environment and to automate processes create security issues. As we add functionality, we almost always increase the attack surface. This chapter describes specific issues that are unique to certain scenarios and technologies.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz enables you to assess whether you should read the entire chapter. If you miss no more than one of these 12 self-assessment questions, you might want to skip ahead to the “Exam Preparation Tasks” section. Table 5-1 lists the major headings in this chapter and the “Do I Know This Already?” quiz questions covering the material in those headings so that you can assess your knowledge of these specific areas. The answers to the “Do I Know This Already?” quiz appear in Appendix A.
Table 5-1 “Do I Know This Already?” Foundation Topics Section-to-Question Mapping
1. Which of the following is a specification first used in late 2001 that allows USB devices, such as tablets and smartphones, to act as either a USB host or a USB device?
a. USB pass-through
b. USB-OTG
c. Ready Boost
d. Lo Jack
2. Which of the following is not one of the five categories of IoT deployments?
a. LAN base
b. Smart home
c. Wearables
d. Connected cars
3. Which of the following describes a piece of software that is built into a larger piece of software and is in charge of performing some specific function on behalf of the larger system?
a. Proprietary
b. Legacy
c. Embedded
d. Linked
4. VxWorks 6.5 is an example of a(n) _______________ system?
a. Modbus
b. embedded
c. RTOS
d. legacy
5. Which of the following is an example of a SoC that manages all the radio functions in a network interface?
a. Dual-core processor
b. Broadband processor
c. Baseband processor
d. Hyper-processor
6. An FPGA is an example of which of the following?
a. SoC
b. PLD
c. PGA
d. Hypervisor
7. Which of the following is a series of two doors with a small room between them?
a. Turnstile
b. Bollard
c. Mantrap
d. Moat
8. Which of the following is an application, network, and media access control (MAC) layer communications service used in HVAC systems?
a. BACnet
b. Modbus
c. CAN bus
d. BAP
9. Which of the following is designed to allow vehicle microcontrollers and devices to communicate with each other’s applications without a host computer?
a. CAN bus
b. ZigBee
c. Modbus
d. BAP
10. Which of the following is a tool used to automate network functions?
a. DMVPN
b. Puppet
c. Net DNA
d. Modbus
11. Which of the following provides guidance for how to organize assets to respond to an incident (system description) and processes to manage the response through its successive stages (concept of operations)?
a. ICS
b. DMVPN
c. IEE
d. IoT
12. Which of the following industrial control system components connect to the sensors and convert sensor data to digital data, including telemetry hardware?
a. PLCs
b. RTUs
c. BUS link
d. Modbus
Foundation Topics
Mobile
In today’s world, seemingly everyone in the workplace has at least one mobile device. But with the popularity of mobile devices has come increasing security issues for security professionals. The increasing use of mobile devices combined with the fact that many of these devices connect using public networks with little or no security provides security professionals with unique challenges.
Educating users on the risks related to mobile devices and ensuring that they implement appropriate security measures can help protect against threats involved with these devices. Some of the guidelines that should be provided to mobile device users include implementing a device-locking PIN, using device encryption, implementing GPS location, and implementing remote wipe. Also, users should be cautioned on downloading apps without ensuring that they are coming from a reputable source. In recent years, mobile device management (MDM) and mobile application management (MAM) systems have become popular in enterprises. They are implemented to ensure that an organization can control mobile device settings, applications, and other parameters when those devices are attached to the enterprise network.
The threats presented by the introduction of personal mobile devices (smartphones and tablets) to an organization’s network include the following:

• Insecure web browsing
• Insecure Wi-Fi connectivity
• Lost or stolen devices holding company data
• Corrupt application downloads and installations
• Missing security patches
• Constant upgrading of personal devices
• Use of location services
While the most common types of corporate information stored on personal devices are corporate emails and company contact information, it is alarming to note that some surveys show almost half of these devices also contain customer data, network login credentials, and corporate data accessed through business applications.
To address these issues and to meet the rising demand by employees to bring personal devices into the workplace and use them for both work and personal purposes, many organizations are creating bring your own device (BYOD) policies. As a security professional, when supporting a BYOD initiative, you should take into consideration that you probably have more to fear from the carelessness of the users than you do from hackers. Not only are they less than diligent in maintaining security updates and patches on devices, they buy new devices frequently to get the latest features. These factors make it difficult to maintain control over the security of the networks in which these devices are allowed to operate.
Centralized mobile device management tools are becoming the fastest-growing solution for both organization-issued and personal mobile devices. Some solutions leverage the messaging server’s management capabilities, and others are third-party tools that can manage multiple brands of devices. One example is Systems Manager by Cisco that integrates with its Cisco Meraki cloud services. Another example is the Apple Configurator for iOS devices. One of the challenges with implementing such a system is that not all personal devices may support native encryption and/or the management process.
Typically, centralized MDM tools handle organization-issued and personal mobile devices differently. For organization-issued devices, a client application typically manages the configuration and security of the entire device. If the device is a personal device allowed through a BYOD initiative, the application typically manages the configuration and security of itself and its data only. The application and its data are sandboxed from the other applications and data. The result is that the organization’s data is protected if the device is stolen, while the privacy of the user’s data is also preserved.
In Chapter 9, “Software Assurance Best Practices,” you will learn about best practices surrounding the use of mobile devices. The sections that follow look at some additional security challenges posed by mobile devices.
Unsigned Apps/System Apps
Unsigned applications represent code that cannot be verified to be what it purports to be or to be free of malware. While many unsigned applications present absolutely no security issues, most enterprises wisely chose to forbid their installation. MDM software and security settings in the devices themselves can be used to prevent this.
System apps are those that come preinstalled on the device. While these apps probably present no security issue, some of them run all the time, so it might be beneficial to remove them to save space and to improve performance. The organization also might decide that removing some system apps is necessary to prevent features in these apps that can disclose information about the user or the device that could lead to a social engineering attack. By following the instructions on the vendor site, these apps can be removed.
Security Implications/Privacy Concerns
Security issues are inherent in mobile devices. Many of these vulnerabilities revolve around storage devices. Let’s look at a few.
Data Storage
While protecting data on a mobile device is always a good idea, in many cases an organization must comply with an external standard regarding the minimum protection provided to the data on the storage device. For example, the Payment Card Industry Data Security Standard (PCI DSS) enumerates requirements that payment card industry players must meet to secure and monitor their networks, protect cardholder data, manage vulnerabilities, implement strong access controls, and maintain security policies. Various storage types share certain issues and present issues unique to the type.
Nonremovable Storage
The storage that is built into the device might not suffer all the vulnerabilities shared by other forms but is still data at risk. One tool at our disposal with this form of storage that is not available with others is the ability to remotely wipe the data if the device is stolen. At any rate, the data should be encrypted with AES 128/256-bit encryption. Also, be sure to have a backup copy of the data stored in a secure location.
Removable Storage
While removable storage may be desirable in that it may not be stolen if the device is stolen, it still can be lost and stolen itself. Removable storage of any type represents one of the primary ways data exfiltration occurs. If removable storage is in use, the data should be encrypted with AES 128/256-bit encryption.
Transfer/Back Up Data to Uncontrolled Storage
In some cases users store sensitive data in cloud storage that is outside the control of the organization, using sites such as Dropbox. These storage providers have had their share of data loss issues as well. Policies should address and forbid this type of storage of data from mobile devices.
USB OTG
USB On-The-Go (USB OTG) is a specification first used in late 2001 that allows USB devices, such as tablets and smartphones, to act as either a USB host or a USB device. With respect to smartphones, USB OTG has been used to hack around an iPhone security feature that requires a valid iPhone username and password to use a device after a factory reset. This feature is supplied to prevent the use of a stolen smartphone that has been reset to factory defaults, but it can be defeated with a hack using USB OTG.
Device Loss/Theft
Of course, one the biggest threats to organizations is a lost or stolen device containing irreplaceable or sensitive data. Organizations should ensure that they can remotely wipe the device when this occurs. Moreover, polices should require that corporate data be backed up to a server so that a remote wipe does not delete data that only resides in the device.
Rooting/Jailbreaking
While rooting or jailbreaking a device enables the user to remove some of the restrictions of the device, it also presents security issues. Jailbreaking removes the security restrictions on your iPhone or iPad. This means apps are given access to the core functions of the device, which normally requires the user consent. It also allows the installation of apps not found in the Apple Store. One of the reasons those apps are not in the Apple Store is that they are either insecure or malware masquerading as a legitimate app. Finally, a rooted or jailbroken device receives no security updates, making it even more vulnerable.
Push Notification Services
Push notification services allow unsolicited messages to be sent by an application to a mobile device even when the application is not open on the device. Although these services can be handy, there are some security best practices when developing these services for your organization:

• Do not send company confidential data or intellectual property in the message payload.
• Do not store your SSL certificate and list of device tokens in your web-root.
• Be careful not to inadvertently expose APN (Apple) certificates or device tokens.
Geotagging
Geotagging is the process of adding geographical identification metadata to various media and is enabled by default on many smartphones (to the surprise of some users). In many cases, this location information can be used to locate where images, video, websites, and SMS messages originate. At the very least, this information can be used to assemble a social engineering attack. This information has been used in the past to reveal the location of high-valued goods. In an extreme case, four U.S. Army Apache helicopters were destroyed (on the ground) by the enemy after they were able to pinpoint the helicopters’ location through geotagged photos taken by U.S. soldiers and posted on the Internet.
OEM/Carrier Android Fragmentation
Android fragmentation refers to the overwhelming number of versions of Android that have been sold. The primary issue is that many users are still running an older version for which security patches are no longer available. The fault is typically that of the phone manufacturer for either maintaining use of an operating system when a new one is available or by customizing the OS (remember, Android is open source) so much that the security patches are incompatible. Organizations should consider these issues when choosing a phone manufacturer.

Mobile Payment
One of the latest features of smartphones is the ability to pay for items using the smartphone instead of a credit card. There are various technologies used to make this possible and they have attendant security issues. Let’s look at how these technologies work.
NFC Enabled
A new security issue facing both merchants and customers is the security of payment cards that use near field communication (NFC), such Apple Pay and Google Pay. NFC is a short-range type of wireless transmission and is therefore difficult to capture. Moreover, these transmissions are typically encrypted. However, interception is still possible. In any case, some steps can be taken to secure these payment mechanisms:

• Lock the mobile device. Devices must be turned on or unlocked before they can read any NFC tags.
• Turn off NFC when not in use.
• For passive tags, use an RFID/NFC-blocking device.
• Scan mobile devices for unwanted apps, spyware, and other threats that may siphon information from your payment apps.
Inductance Enabled
Inductance is the process used in NFC to transmit the information from the smartphone to the reader. Coils made of ferrite material uses electromagnetic induction to transmit information. Therefore, an inductance-enabled device would be one that supports a mobile payment system. While capturing these transmissions is possible, the attacker must be very close.
Mobile Wallet
An alternative technology used in mobile payment systems is the Mobile Wallet used by online companies like PayPal, Amazon Payments, and Google Payt. In this system, the user registers his card number and is issued a PIN, which he uses to authorize payments. The PIN identifies the user and the card and charges the card.
Peripheral-Enabled Payments (Credit Card Reader)
Credit card readers that can read from a mobile phone at close range are also becoming ubiquitous, especially with merchants that operate in remote locations such as cabs, food trucks, and flea markets. Figure 5-1 shows one such device reading a card.

Figure 5-1 Peripheral-Enabled Payments (Credit Card Reader)
USB
Since this connection uses bounded media, this may be the safest way to make a connection. The only way a malicious individual could make this kind of connection will be to gain physical access to the mobile device. So physical security is the main way to mitigate this.
Malware
Just like laptops and desktops, mobile devices are targets of viruses and malware. Major antivirus vendors such as McAfee and Kaspersky make antivirus and anti-malware products for mobile devices that provide the same real-time protection that the similar products do for desktops. The same guideline that applies to computers applies to mobile devices: keep the antivirus/anti-malware product up to date by setting the device to check for updates whenever connected to the Internet.
Unauthorized Domain Bridging
Most smartphones can act as a wireless hotspot. When a device that has been made a member of the domain and then acts as a hotspot, it allows access to the organizational network to anyone using the hotspot. This is called unauthorized domain bridging and should be forbidden. There is software that can prevent this. In several embodiments, software operative on the network allows activation of only a single communications adapter while inactivating all other communications adapters installed on each computer authorized to access the network.
SMS/MMS/Messaging
Short Message Service (SMS) is a text messaging service component of most telephone, World Wide Web, and mobile telephony systems. Multimedia Messaging Service (MMS) handles messages that include graphics or videos. Both technologies present security challenges. Because messages are sent in clear text, both are susceptible to spoofing and spamming.
Internet of Things (IoT)
The Internet of Things (IoT) refers to a system of interrelated computing devices, mechanical and digital machines, and objects that are provided with unique identifiers and the ability to transfer data over a network without requiring human-to-human or human-to-computer interaction. The IoT has presented attackers with a new medium through which to carry out an attack. Often the developers of the IoT devices add the IoT functionality without thoroughly considering the security implications of such functionality or without building in any security controls to protect the IoT devices.
Note
IoT is a term for all physical objects, or “things,” that are now embedded with electronics, software, and network connectivity. Thanks to the IoT, these objects—including automobiles, kitchen appliances, and heating and air conditioning controllers—can collect and exchange data. Unfortunately, engineers give most of these objects this ability just for convenience and without any real consideration of the security impacts. When these objects are then deployed, consumers do not think of security either. The result is consumer convenience but also risk. As the IoT evolves, security professionals must be increasingly involved in the IoT evolution to help ensure that security controls are designed to protect these objects and the data they collect and transmit.
IoT Examples
IoT deployments include a wide variety of devices, but are broadly categorized into five groups:

• Smart home: Includes products that are used in the home. They range from personal assistance devices, such as Amazon Alexa, to HVAC components, such as Nest thermostats. These devices are designed for home management and automation.
• Wearables: Includes products that are worn by users. They range from watches, such as the Apple Watch, to personal fitness devices, like the Fitbit.
• Smart cities: Includes devices that help resolve traffic congestion issues and reduce noise, crime, and pollution. They include smart energy, smart transportation, smart data, smart infrastructure, and smart mobility devices.
• Connected cars: Includes vehicles that include Internet access and data sharing capabilities. Technologies include GPS devices, OnStar, and AT&T connected cars.
• Business automation: Includes devices that automate HVAC, lighting, access control, and fire detection for organizations.
Methods of Securing IoT Devices
Security professionals must understand the different methods of securing IoT devices. The following are some recommendations:

• Secure and centralize the access logs of IoT devices.
• Use encrypted protocols to secure communication.
• Create secure password policies.
• Implement restrictive network communications policies, and set up virtual LANs.
• Regularly update device firmware based on vendor recommendations.
When selecting IoT devices, particularly those that are implemented at the organizational level, security professionals need to look into the following:

• Does the vendor design explicitly for privacy and security?
• Does the vendor have a bug bounty program and vulnerability reporting system?
• Does the device have manual overrides or special functions for disconnected operations?
Embedded Systems
An embedded system is a piece of software that is built into a larger piece of software and is in charge of performing some specific function on behalf of the larger system. The embedded part of the solution might address specific hardware communications and might require drivers to talk between the larger system and some specific hardware. Embedded systems control many devices in common use today and include systems embedded in cars, HVAC systems, security alarms, and even lighting systems. Machine-to-machine (M2M) communication, the IoT, and remotely controlled industrial systems have increased the number of connected devices and simultaneously made these devices targets.
Because embedded systems are usually placed within another device without input from a security professional, security is not even built into the device. So although allowing the device to communicate over the Internet with a diagnostic system provides a great service to the consumer, oftentimes the manufacturer has not considered that a hacker can then reverse communication and take over the device with the embedded system. As of this writing, reports have surfaced of individuals being able to take control of vehicles using their embedded systems. Manufacturers have released patches that address such issues, but not all vehicle owners have applied or even know about the patches. As M2M and IoT increase in popularity, security professionals can expect to see a rise in incidents like this. A security professional is expected to understand the vulnerabilities these systems present and how to put controls in place to reduce an organization’s risk.
Real-Time Operating System (RTOS)
Real-time operating systems (RTOSs) are designed to process data as it comes in, typically without buffer delays. Like all systems, they have a certain amount of latency in the processing. One of the key issues with these systems is to control the jitter (the variability of such latency).
Many IoT devices use an RTOS. These operating systems were not really designed for security and some issues have surfaced. For example, VxWorks 6.5 and later versions have found to be susceptible to a vulnerability that allows remote attackers full control over targeted devices. The ARMIS security firm discovered and announced 11 vulnerabilities, including six critical vulnerabilities, collectively branded URGENT/11 in the summer of 2019. This is disturbing, because VxWorks is used in mission-critical systems for the enterprise, including SCADA, elevator, and industrial controllers, as well as in healthcare equipment, including patient monitors and MRI scanners.
System-on-Chip (SoC)
System-on-Chip (SoC) have become typical inside cell phone electronics for their reduced energy use. A baseband processor is a chip in a network interface that manages all the radio functions. A baseband processor typically uses its own RAM and firmware. Since the software that runs on baseband processors is usually proprietary, it is impossible to perform an independent code audit. In March 2014, makers of the free Android derivative Replicant announced they had found a backdoor in the baseband software of Samsung Galaxy phones that allows remote access to the user data stored on the phone. Although it has been some time since this happened, it is a reminder that SoCs can be a security issue.
Field Programmable Gate Array (FPGA)
A programmable logic device (PLD) is an integrated circuit with connections or internal logic gates that can be changed through a programming process. A field programmable gate array (FPGA) is a type of PLD that is programmed by blowing fuse connections on the chip or using an antifuse that makes a connection when a high voltage is applied to the junction.
FPGAs are used extensively in IoT implementations and in cloud scenarios. In 2019, scientists discovered a vulnerability in FPGAs. In a side-channel attack, cyber criminals use the energy consumption of the chip to retrieve information that allows them to break its encryption. It is also possible to tamper with the calculations or even to crash the chip altogether, possibly resulting in data losses.
Physical Access Control
Access control is all about using physical or logical controls to control who or what has access to a network, system, or device. It also involves what type of access is given to the information, network, system, device, or facility. Access control is primarily provided using physical and logical controls.
Physical access focuses on controlling access to a network, system, or device. In most cases, physical access involves using access control to prevent users from being able to touch network components (including wiring), systems, or devices. While locks are the most popular physical access control method to preventing access to devices in a data center, other physical controls, such as guards and biometrics, should also be considered, depending on the needs of the organization and the value of the asset being protected.
When installing an access control system, security professionals should understand who needs access to the asset being protected and how those users need to access the asset. When multiple users need access to an asset, the organization should set up a multilayer access control system. For example, users wanting access to the building may only need to sign in with a security guard. However, to access the locked data center within the same building, users would need a smart card. Both of these would be physical access controls. To protect data on a single server within the building (but not in the data center), the organization would need to deploy such mechanisms as authentication, encryption, and access control lists (ACLs) as logical access controls but could also place the server in a locked server room to provide physical access control. When deploying physical and logical access controls, security professionals must understand the access control administration methods and the different assets that must be protected and their possible access controls.
Systems
To fully protect the systems used by the organization, including client and server computers, security professionals may rely on both physical and logical access controls. However, some systems, like client computers, may be deployed in such a manner that only minimal physical controls are used. If a user is granted access to a building, he or she may find client computers being used in nonsecure cubicles throughout the building. For these systems, a security professional must ensure that the appropriate authentication mechanisms are deployed. If confidential information is stored on the client computers, encryption should also be deployed. But only the organization can best determine which controls to deploy on individual client computers. When it comes to servers, determining which access controls to deploy is usually a more complicated process. Security professionals should work with the server owner, whether it is a department head or an IT professional, to determine the value of the asset and the needed protection. Of course, most servers should be placed in a locked room. In many cases, this will be a data center or server room. However, servers can be deployed in regular locked offices if necessary. In addition, other controls should be deployed to ensure that the system is fully protected. The access control needs of a file server are different from those of a web server or database server. It is vital that the organization perform a thorough assessment of the data that is being processed and stored on the system before determining which access controls to deploy. If limited resources are available, security professionals must ensure that their most important systems have more access controls than other systems.
Devices
As with systems, physical access to devices is best provided by placing the devices in a secure room. Logical access to devices is provided by implementing the appropriate ACL or rule list, authentication, and encryption, as well as securing any remote interfaces that are used to manage the device. In addition, security professionals should ensure that the default accounts and passwords are changed or disabled on the device. For any IT professionals that need to access the device, a user account should be configured for the professional with the appropriate level of access needed. If a remote interface is used, make sure to enable encryption, such as SSL, to ensure that communication via the remote interface is not intercepted and read. Security professionals should closely monitor vendor announcements for any devices to ensure that the devices are kept up to date with the latest security patches and firmware updates.
Facilities
With facilities, the primary concern is physical access, which can be provided using locks, fencing, bollards, guards, and closed-circuit television (CCTV). Many organizations think that such measures are enough. But with today’s advanced industrial control systems and the IoT, organizations must also consider any devices involved in facility security. If an organization has an alarm/security system that allows remote viewing access from the Internet, the appropriate logical controls must be in place to prevent a malicious user from accessing the system and changing its settings or from using the system to gain inside information about the facility layout and day-to-day operations. If the organization uses an industrial control system (ICS), logical controls should also be a priority. Security professionals must work with organizations to ensure that physical and logical controls are implemented appropriately to ensure that the entire facility is protected.
Note
There are two “ICSs” covered in this chapter. It can mean either industrial control system (ICS) or Incident Command System (ICS).
Physical access control systems are any systems used to allow or deny physical access to the facility. Examples include the following:

• Mantrap: This is a series of two doors with a small room between them. The user is authenticated at the first door and then allowed into the room. At that point, additional verification occurs (such as a guard visually identifying the person), and then the person is allowed through the second door. Mantraps are typically used only in very high-security situations. They can help prevent tailgating. Figure 5-2 illustrates a mantrap design.
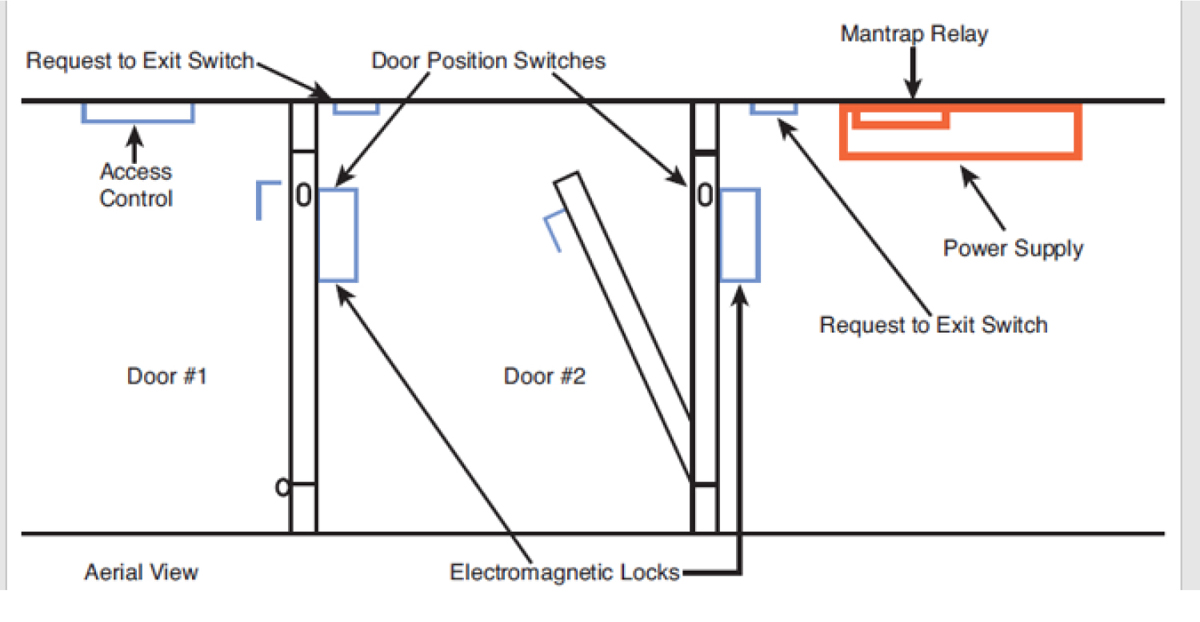
Figure 5-2 Mantrap
• Proximity readers: These readers are door controls that read a proximity card from a short distance and are used to control access to sensitive rooms. These devices can also provide a log of all entries and exits.
• IP-based access control and video systems: When using these systems, a network traffic baseline for each system should be developed so that unusual traffic can be detected.
Some higher-level facilities are starting to incorporate biometrics as well, especially in high-security environments where terrorist attacks are a concern.
Building Automation Systems
The networking of facility systems has enhanced the ability to automate the management of systems, including the following:
• Lighting
• HVAC
• Water systems
• Security alarms
Bringing together the management of these seemingly disparate systems allows for the orchestration of their interaction in ways that were never before possible. When industry leaders discuss the IoT, the success of building automation is often used as a real example of where connecting other devices, such as cars and street signs, to the network can lead. These systems usually can pay for themselves in the long run by managing the entire ecosystem more efficiently in real time than a human could ever do. If a wireless version of such a system is deployed, keep the following issues in mind:

• Interference issues: Construction materials may prevent you from using wireless everywhere.
• Security: Use encryption, separate the building automation systems (BAS) network from the IT network, and prevent routing between the networks.
• Power: When Power over Ethernet (PoE) cannot provide power to controllers and sensors, ensure that battery life supports a reasonable lifetime and that procedures are created to maintain batteries.
IP Video
IP video systems provide a good example of the benefits of networking applications. These systems can be used for both surveillance of a facility and facilitating collaboration. An example of the layout of an IP surveillance system is shown in Figure 5-3.
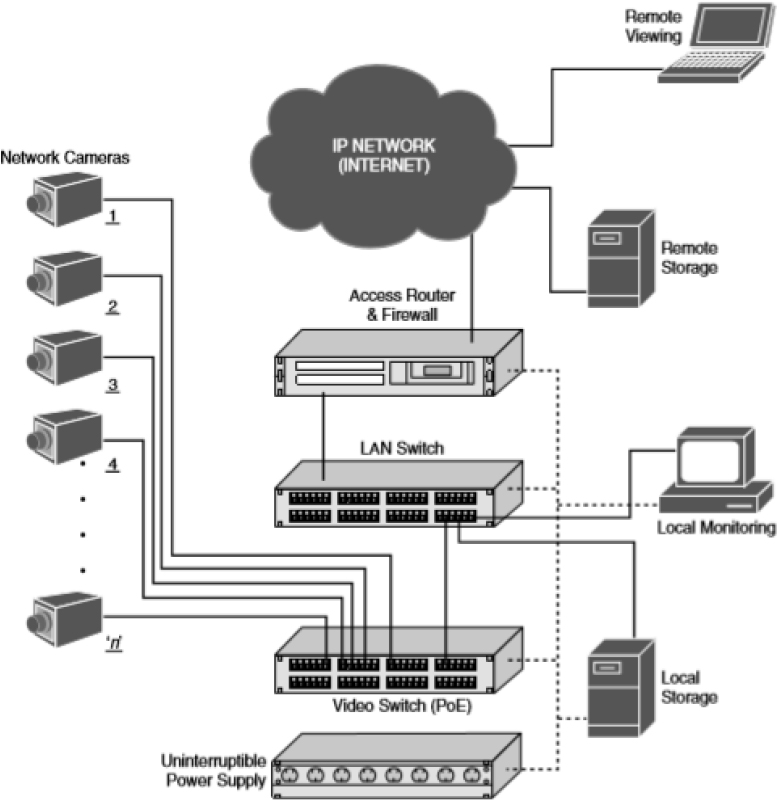
Figure 5-3 IP Surveillance
IP video has also ushered in a new age of remote collaboration. It has saved a great deal of money on travel expenses while at the same time making more efficient use of time.
Issues to consider and plan for when implementing IP video systems include the following:

• Expect a large increase in the need for bandwidth.
• QoS needs to be configured to ensure performance.
• Storage needs to be provisioned for the camera recordings. This could entail cloud storage, if desired.
• The initial cost may be high.
HVAC Controllers
One of the best examples of the marriage of IP networks and a system that formerly operated in a silo is the heating, ventilation, and air conditioning (HVAC) system. HVAC systems usually use a protocol called Building Automation and Control Networks (BACnet), which is an application, network, and media access control (MAC) layer communications service. It can operate over a number of Layer 2 protocols, including Ethernet.
To use the BACnet protocol in an IP world, BACnet/IP (B/IP) was developed. The BACnet standard makes exclusive use of MAC addresses for all data links, including Ethernet. To support IP, IP addresses are needed. BACnet/IP, Annex J, defines an equivalent MAC address composed of a 4-byte IP address followed by a 2-byte UDP port number. A range of 16 UDP port numbers has been registered as hexadecimal BAC0 through BACF.
While putting HVAC systems on an IP network makes them more manageable, it has become apparent that these networks should be separate from the internal network. In the infamous Target breach, hackers broke into the network of a company that managed the company’s HVAC systems. The intruders leveraged the trust and network access granted to the HVAC company by Target and then, from these internal systems, broke into the point-of-sale systems and stole credit and debit card numbers, as well as other personal customer information.
Sensors
Sensors are designed to gather information of some sort and make it available to a larger system, such as an HVAC controller. Sensors and their role in SCADA systems are covered later in this chapter.
Vehicles and Drones
Wireless capabilities added to vehicles and drones have ushered in a new world of features, while at the same time opening the door for all sorts of vulnerabilities common to any network-connected device.
Connected vehicles are not those that drive themselves, although those are coming. A connected vehicle is one that can be reached with a wireless connection of some sort. MacAfee has identified the attack surface that exists in a connected vehicle. Figure 5-4 shows the areas of vulnerability.
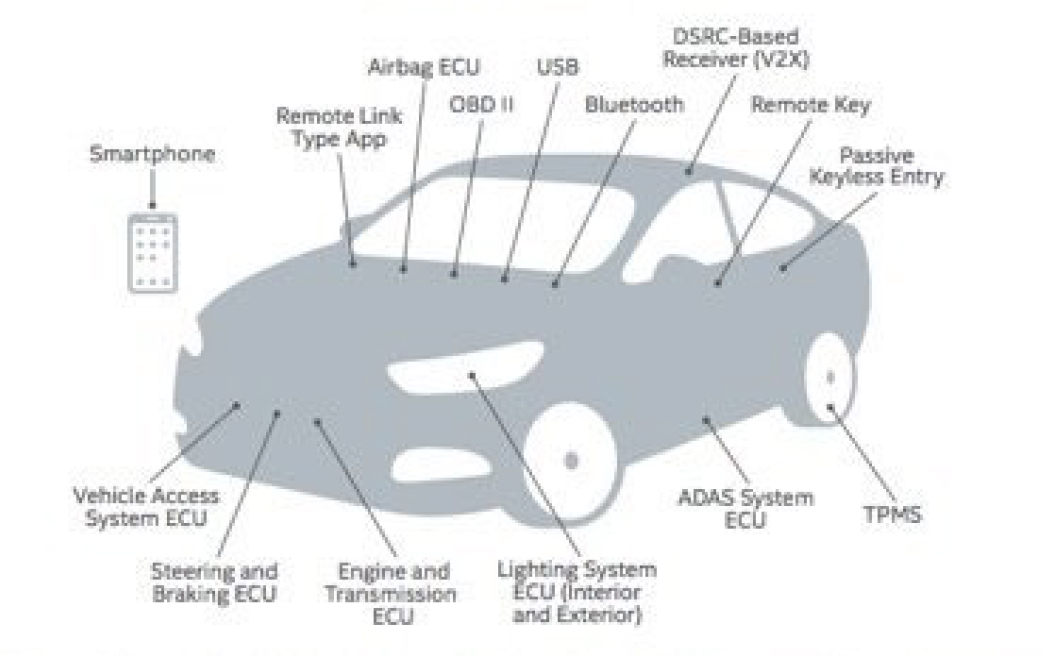
Figure 5-4 Vehicle Attack Surface
As you can see in Figure 5-4, critical vehicle systems may be vulnerable to wireless attacks.
CAN Bus
While autonomous vehicles may still be a few years off, when they arrive they will make use of a new standard for vehicle-to-vehicle and vehicle-to-road communication. Controller Area Network (CAN bus) is designed to allow vehicle microcontrollers and devices to communicate with each other’s applications without a host computer. Sounds great, huh?
It turns out CAN is a low-level protocol and does not support any security features intrinsically. There is also no encryption in standard CAN implementations, which leaves these networks open to data interception.
Failure by vendors to implement their own security measures may result in attacks if attackers manage to insert messages on the bus. While passwords exist for some safety-critical functions, such as modifying firmware, programming keys, or controlling antilock brake actuators, these systems are not implemented universally and have a limited number of seed/key pairs (meaning a brute-force attack is more likely to succeed). Hopefully, an industry security standard for the CAN bus will be developed at some point.
Drones
Drones are managed wirelessly and, as such, offer attackers the same door of entry as found in connected cars. In January 2020, the U.S. Department of the Interior grounded nonemergency drones due to security concerns. Why? The U.S. Department of Defense (DoD) issued warning that Chinese-made drones may be compromised and capable of being used for espionage. This follows a memo from the Navy & Marine Corps Small Tactical Unmanned Aircraft Systems Program Manager that “images, video and flight records could be uploaded to unsecured servers in other countries via live streaming.” Finally, the U.S. Department of Homeland Security previously warned the private sector that their data may be pilfered if they use commercial drone systems made in China.
Beyond the fear of Chinese-made drones that contain backdoors, there is also the risk of a drone being “hacked” and taken over by the attacker in midflight. Since 2016, it has been known that it is possible in some cases to do the following:
• Overwhelm the drone with thousands of connection requests, causing the drone to land
• Send large amounts of data to the drone, exceeding its capacity and causing it to crash
• Convince the drone that orders sent to land the drone were coming from the drone itself rather than attackers, causing the drone to follow orders and land
At the time of writing in 2020, attackers have had four years to probe for additional attack points. It is obvious that drone security has to be made more robust.
Workflow and Process Automation Systems
Automating workflows and processes saves time and human resources. One of the best examples is the automation revolution occurring in network management. Automation tools such as Puppet, Chef, and Ansible and scripting are automating once manual tasks such as log analyses, patch application, and intrusion prevention.
These tools and scripts perform the job they do best, which is manual drudgery, thus freeing up humans to do what they do best, which is deep analysis and planning. Alas, with automation comes vulnerabilities. An example is the cross-site scripting (XSS) vulnerability found in IBM workflow systems, as detailed in CVE-2019-4149, which can allow users to embed arbitrary JavaScript code in the Web UI, thus altering the intended functionality and potentially leading to credentials disclosure within a trusted session. These automation systems also need to be made more secure.
Incident Command System (ICS)
The Incident Command System (ICS) is designed by FEMA to provide a way to enable effective and efficient domestic incident management by integrating a combination of facilities, equipment, personnel, procedures, and communications operating within a common organizational structure.
ICS provides guidance for how to organize assets to respond to an incident (system description) and processes to manage the response through its successive stages (concept of operations). All response assets are organized into five functional areas: Command, Operations, Logistics, Planning, and Administration/Finance. Figure 5-5 highlights the five functional areas of ICS and their primary responsibilities.
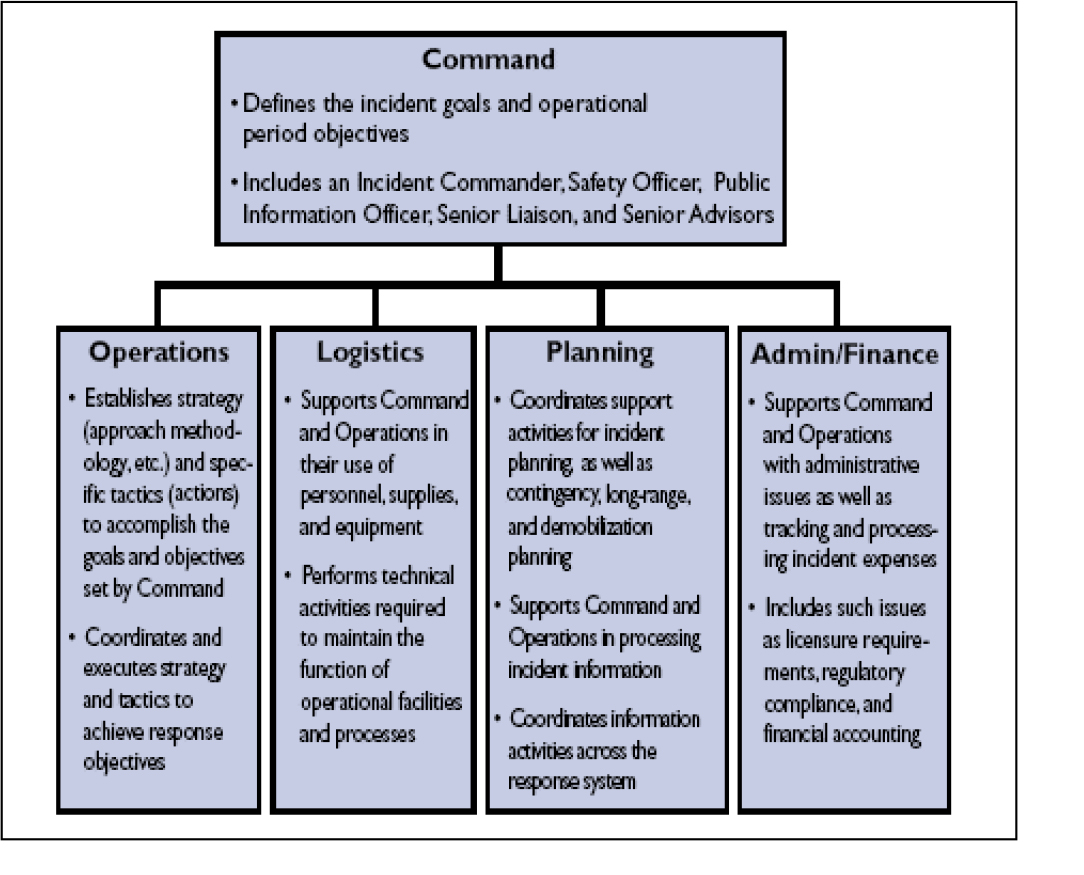
Figure 5-5 Functional Areas of ICS
Supervisory Control and Data Acquisition (SCADA)
Industrial control system (ICS) is a general term that encompasses several types of control systems used in industrial production. The most widespread is supervisory control and data acquisition (SCADA). SCADA is a system that operates with coded signals over communication channels to provide control of remote equipment. ICSs include the following components:

• Sensors: Sensors typically have digital or analog I/O and are not in a form that can be easily communicated over long distances.
• Remote terminal units (RTUs): RTUs connect to the sensors and convert sensor data to digital data, including telemetry hardware.
• Programmable logic controllers (PLCs): PLCs connect to the sensors and convert sensor data to digital data; they do not include telemetry hardware.
• Telemetry system: Such a system connects RTUs and PLCs to control centers and the enterprise.
• Human interface: Such an interface presents data to the operator.
ICSs should be securely segregated from other networks as a security layer. The Stuxnet virus hit the SCADA systems used for the control and monitoring of industrial processes. SCADA components are considered privileged targets for cyberattacks. By using cyber tools, it is possible to destroy an industrial process. This was the idea used on the attack on the nuclear plant in Natanz in order to interfere with the Iranian nuclear program.
Considering the criticality of SCADA-based systems, physical access to these systems must be strictly controlled. Systems that integrate IT security with physical access controls, such as badging systems and video surveillance, should be deployed. In addition, a solution should be integrated with existing information security tools such as log management and IPS/IDS. A helpful publication by NIST, SP 800-82 Rev. 2, recommends the major security objectives for an ICS implementation should include the following:

• Restricting logical access to the ICS network and network activity
• Restricting physical access to the ICS network and devices
• Protecting individual ICS components from exploitation
• Restricting unauthorized modification of data
• Detecting security events and incidents
• Maintaining functionality during adverse conditions
• Restoring the system after an incident
In a typical ICS, this means a defense-in-depth strategy should include the following, according to SP 800-82 Rev. 2:

• Develop security policies, procedures, training, and educational material that applies specifically to the ICS.
• Address security throughout the life cycle of the ICS.
• Implement a network topology for the ICS that has multiple layers, with the most critical communications occurring in the most secure and reliable layer.
• Provide logical separation between the corporate and ICS networks.
• Employ a DMZ network architecture.
• Ensure that critical components are redundant and are on redundant networks.
• Design critical systems for graceful degradation (fault tolerant) to prevent catastrophic cascading events.
• Disable unused ports and services on ICS devices after testing to assure this will not impact ICS operation.
• Restrict physical access to the ICS network and devices.
• Restrict ICS user privileges to only those that are required to perform each person’s job.
• Use separate authentication mechanisms and credentials for users of the ICS network and the corporate network.
• Use modern technology, such as smart cards, for Personal Identity Verification (PIV).
• Implement security controls such as intrusion detection software, antivirus software, and file integrity checking software, where technically feasible, to prevent, deter, detect, and mitigate the introduction, exposure, and propagation of malicious software to, within, and from the ICS.
• Apply security techniques such as encryption and/or cryptographic hashes to ICS data storage and communications where determined appropriate.
• Expeditiously deploy security patches after testing all patches under field conditions on a test system if possible, before installation on the ICS.
• Track and monitor audit trails on critical areas of the ICS.
• Employ reliable and secure network protocols and services where feasible.
SP 800-82 Rev. 2 recommends that security professionals should consider the following when designing security solutions for ICS devices: timeliness and performance requirements, availability requirements, risk management requirements, physical effects, system operation, resource constraints, communications, change management, managed support, component lifetime, and component location.
ICS implementations use a variety of protocols and services, including

• Modbus: A master/slave protocol that uses port 50
• BACnet: A master/slave protocol that uses port 47808 (introduced earlier in this chapter)
• LonWorks/LonTalk: A peer-to-peer protocol that uses port 1679
• Distributed Network Protocol 3 (DNP3): A master/slave protocol that uses port 19999 when using Transport Layer Security (TLS) and port 20000 when not using TLS
ICS implementations can also use IEEE 802.1X, Zigbee, and Bluetooth for communication.
SP 800-82 Rev. 2 outlines the following basic process for developing an ICS security program:

1. Develop a business case for security.
2. Build and train a cross-functional team.
3. Define charter and scope.
4. Define specific ICS policies and procedures.
5. Implement an ICS Security Risk Management Framework.
a. Define and inventory ICS assets.
b. Develop a security plan for ICS systems.
c. Perform a risk assessment.
d. Define the mitigation controls.
6. Provide training and raise security awareness for ICS staff.
The ICS security architecture should include network segregation and segmentation, boundary protection, firewalls, a logically separated control network, and dual network interface cards (NICs) and should focus mainly on suitable isolation between control networks and corporate networks. Security professionals should also understand that many ICS/SCADA systems use weak authentication and outdated operating systems. The inability to patch these systems (and even the lack of available patches) means that the vendor is usually not proactively addressing any identified security issues. Finally, many of these systems allow unauthorized remote access, thereby making it easy for an attacker to breach the system with little effort.
Modbus
As you learned in the previous discussion, Modbus is one of the protocols used in industrial control systems. It is a serial protocol created by Modicon (now Schneider Electric) to be used by its PLCs. It is popular because it is royalty free. It enables communication among many devices connected to the same network; for example, a system that measures water flow and communicates the results to a computer. An example of a Modbus architecture is shown in Figure 5-6.
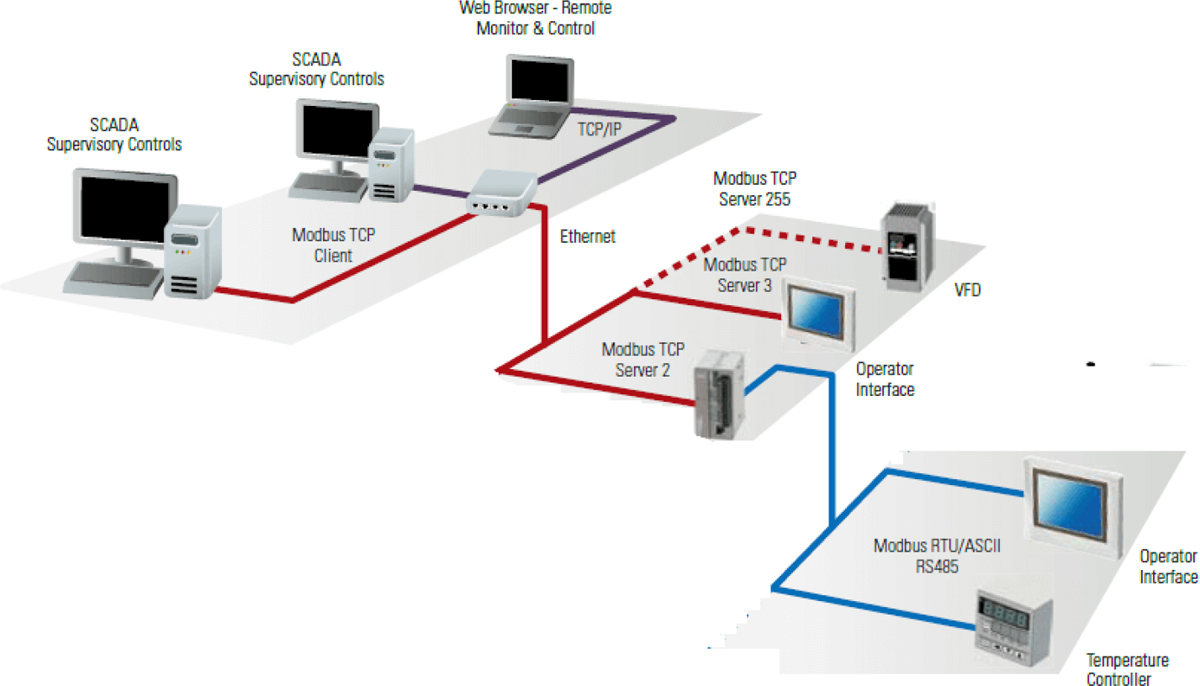
Figure 5-6 Modbus Architecture
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have several choices for exam preparation: the exercises here, Chapter 22, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep Software Online.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 5-2 lists a reference of these key topics and the page numbers on which each is found.

Table 5-2 Key Topics in Chapter 5
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
mobile device management (MDM)
bring your own device (BYOD) policies
Payment Card Industry Data Security Standard (PCI DSS)
near field communication (NFC)
real-time operating system (RTOS)
field programmable gate array (FPGA)
Building Automation and Control Networks (BACnet)
Controller Area Network (CAN bus)
supervisory control and data acquisition (SCADA)
programmable logic controllers (PLCs)
Distributed Network Protocol 3 (DNP3)
Review Questions
1. List at least two threats presented by the introduction of personal mobile devices (smartphones and tablets) into an organization’s network.
2. What is the single biggest threat to mobile devices?
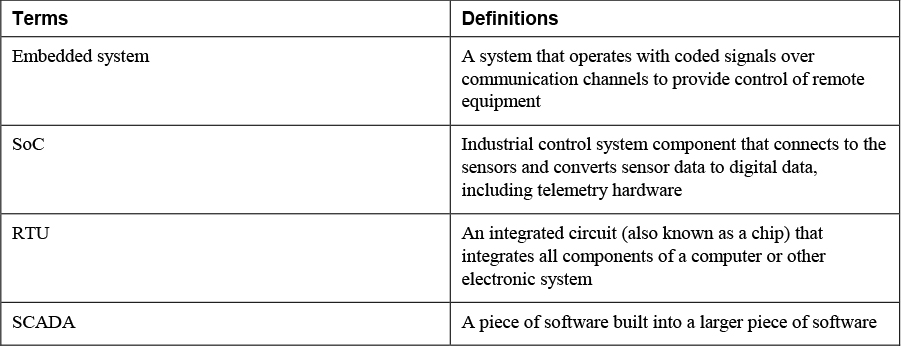
3. Match the term on the left with its definition on the right.
4. ___________________ refers to a system of interrelated computing devices, mechanical and digital machines, and objects that are provided with unique identifiers and the ability to transfer data over a network without requiring human-to-human or human-to-computer interaction.
5. What process enabled the enemy to pinpoint the location of four U.S. Army Apache helicopters on the ground and destroy them?
6. Match the term on the left with its definition on the right.
7. __________________ is a text messaging service component of most telephone, World Wide Web, and mobile telephony systems.
8. List at least one example of an IoT deployment.
9. A(n) __________________ is a series of two doors with a small room between them.
10. To use the BACnet protocol in an IP world, __________________ was developed.
