Chapter 17. Analyzing Potential Indicators of Compromise
This chapter covers the following topics related to Objective 4.3 (Given an incident, analyze potential indicators of compromise) of the CompTIA Cybersecurity Analyst (CySA+) CS0-002 certification exam:
• Network-related indicators of compromise: Includes bandwidth consumption, beaconing, irregular peer-to-peer communication, rogue device on the network, scan/sweep, unusual traffic spike, and common protocol over non-standard port
• Host-related indicators of compromise: Covers processor consumption, memory consumption, drive capacity consumption, unauthorized software, malicious process, unauthorized change, unauthorized privilege, data exfiltration, abnormal OS process behavior, file system change or anomaly, registry change or anomaly, and unauthorized scheduled task
• Application-related indicators of compromise: Includes anomalous activity, introduction of new accounts, unexpected output, unexpected outbound communication, service interruption, and application log
Indicators of compromise (IOCs) are somewhat like clues left at the scene of a crime except they also include clues that preceded the crime. IOCs help us to anticipate security issues and also to reconstruct the process that was taken to cause the security issue or breach. This chapter examines some common IOCs and what they might indicate.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz enables you to assess whether you should read the entire chapter. If you miss no more than one of these nine self-assessment questions, you might want to skip ahead to the “Exam Preparation Tasks” section. Table 17-1 lists the major headings in this chapter and the “Do I Know This Already?” quiz questions covering the material in those headings so that you can assess your knowledge of these specific areas. The answers to the “Do I Know This Already?” quiz appear in Appendix A.
Table 17-1 “Do I Know This Already?” Foundation Topics Section-to-Question Mapping

1. Which of the following IoCs is most likely from a DoS attack?
a. Beaconing
b. Irregular peer-to-peer communication
c. Bandwidth consumption
d. Rogue device on the network
2. Which of the following IoCs is most likely an indication of a botnet?
a. Beaconing
b. Irregular peer-to-peer communication
c. Bandwidth consumption
d. Rogue device on the network
3. Which of the following is used to locate live devices?
a. Ping sweep
b. Port scan
c. Pen test
d. Vulnerability test
4. Which of the following metrics cannot be found in Windows Task Manager?
a. Memory consumption
b. Drive capacity consumption
c. Processor consumption
d. Unauthorized software
5. Which of the following utilities is a freeware task manager that offers more functionality than Windows Task Manager?
a. System Information
b. Process Explorer
c. Control Panel
d. Performance
6. Which of the following is a utility built into the Windows 10 operating system that checks for system file corruption?
a. TripWire
b. System File Checker
c. sigver
d. SIEM
7. Which of the following might be an indication of a backdoor?
a. Introduction of new accounts
b. Unexpected output
c. Unexpected outbound communication
d. Anomalous activity
8. Within which of the following tools is the Application log found?
a. Event Viewer
b. Performance
c. System Information
d. App Locker
9. Which of the following is not an application-related IoC?
a. Introduction of new accounts
b. Unexpected output
c. Unexpected outbound communication
d. Beaconing
Foundation Topics
Network-Related Indicators of Compromise
Security analysts, regardless of whether they are operating in the role of first responder or in a supporting role analyzing issues, should be aware of common indicators of compromise. Moreover, they should be aware of the types of incidents implied by each IOC. This can lead to a quicker and correct choice of action when time is of the essence. It is helpful to examine these IOCs in relation to the component that is displaying the IOC.
Certain types of network activity are potential indicators of security issues. The following sections describe the most common of the many network-related symptoms.
Bandwidth Consumption
Whenever bandwidth usage is above normal and there is no known legitimate activity generating the traffic, you should suspect security issues that generate unusual amounts of traffic, such as denial-of-service (DoS) or distributed denial-of-service (DDoS) attacks. For this reason, benchmarks should be created for normal bandwidth usage at various times during the day. Then alerts can be set when activity rises by a specified percentage at those various times. Many free network bandwidth monitoring tools are available. Among them are BitMeter OS, FreeMeter Bandwidth Monitor, BandwidthD, and PRTG Network Monitor. Anomaly-based intrusion detection systems can also “learn” normal traffic patterns and can set off alerts when unusual traffic is detected. Figure 17-1 shows an example of setting an alert in BitMeter.
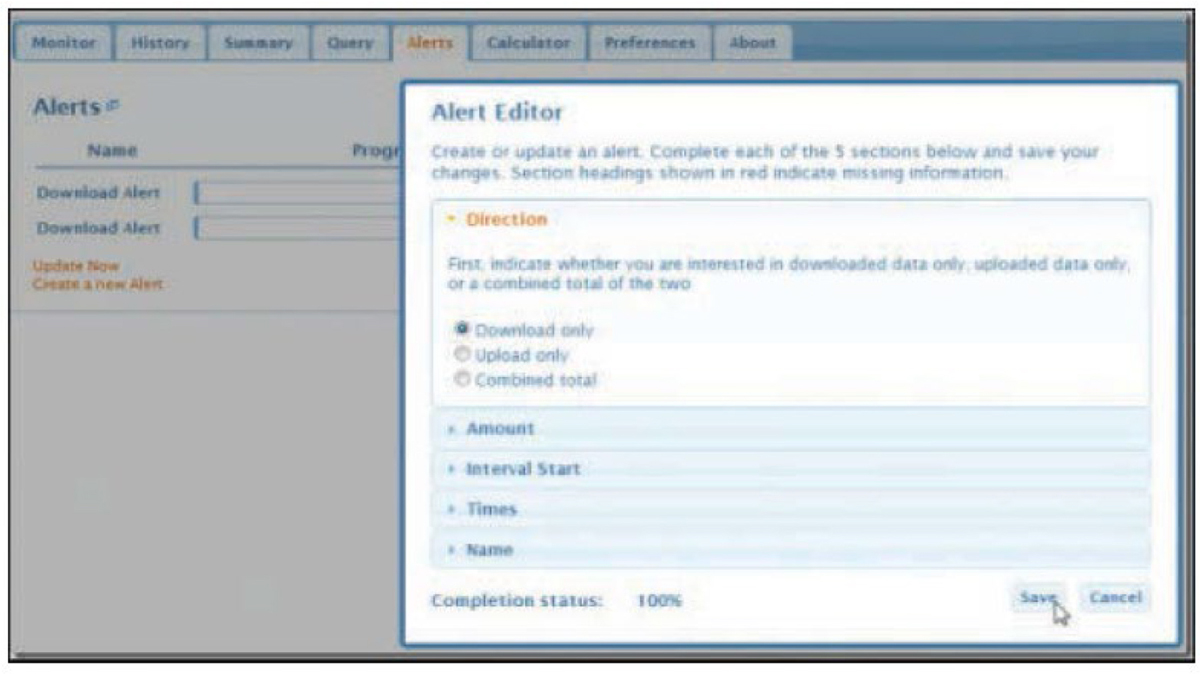
Figure 17-1 Setting an Alert in BitMeter
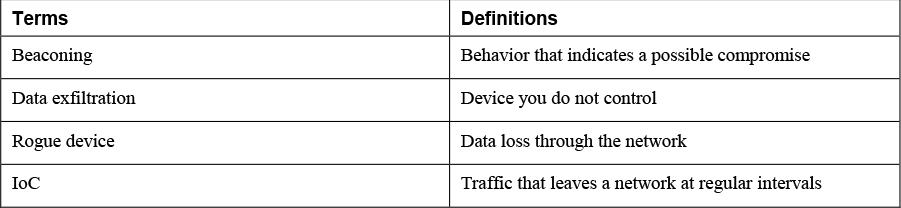
Beaconing
Beaconing refers to traffic that leaves a network at regular intervals. This type of traffic could be generated by compromised hosts that are attempting to communicate with (or call home) the malicious party that compromised the host. While there are security products that can identify beacons, including firewalls, intrusion detection systems, web proxies, and SIEM systems, creating and maintaining baselines of activity will help you identify beacons that are occurring during times of no activity (for example, at night). When this type of traffic is detected, you should search the local source device for scripts that may be generating these calls home.
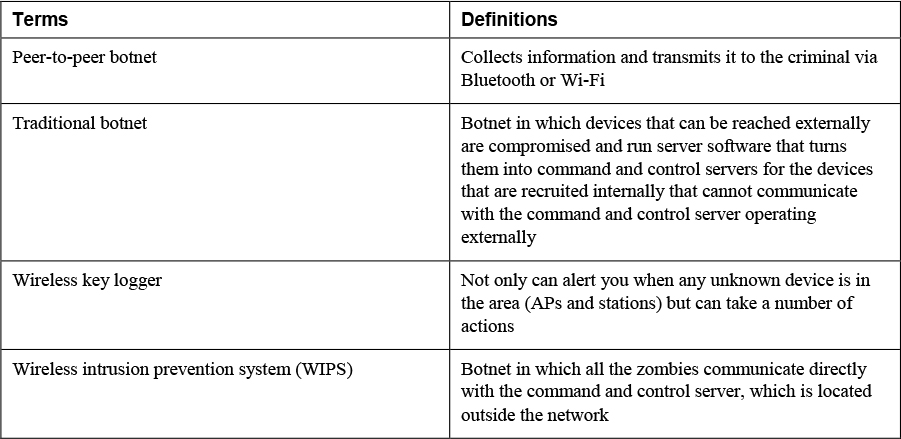
Irregular Peer-to-Peer Communication
If traffic occurring between peers within a network is normal but communications are irregular, this may be an indication of a security issue. At the very least, illegal file sharing could be occurring, and at the worst, this peer-to-peer (P2P) communication could be the result of a botnet. Peer-to-peer botnets differ from normal botnets in their structure and operation. Figure 17-2 shows the structure of a traditional botnet. In this scenario, all the zombies communicate directly with the command and control server, which is located outside the network. The limitation of this arrangement and the issue that gives rise to peer-to-peer botnets is that devices that are behind a NAT server or proxy server cannot participate. Only devices that can be reached externally can do so.
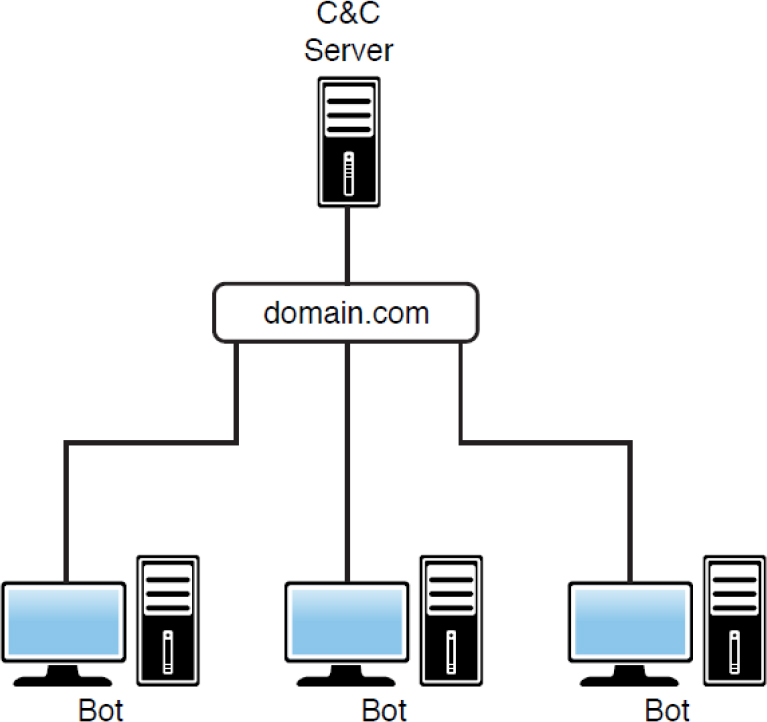
Figure 17-2 Traditional Botnet
In a peer-to-peer botnet, devices that can be reached externally are compromised and run server software that turns them into command and control servers for the devices that are recruited internally that cannot communicate with the command and control server operating externally. Figure 17-3 shows this arrangement.
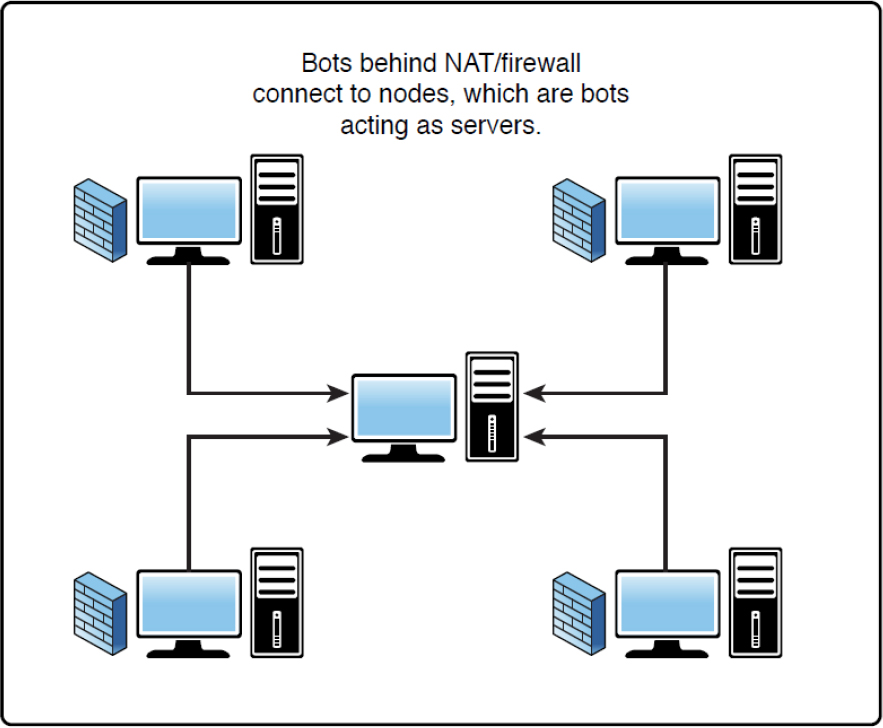
Figure 17-3 Peer-to-Peer Botnet
Regardless of whether peer-to-peer traffic is used as part of a botnet or simply as a method of file sharing, it presents the following security issues:

• The spread of malicious code that may be shared along with the file
• Inadvertent exposure of sensitive material located in unsecured directories
• Actions taken by the P2P application that make a device more prone to attack, such as opening ports
• Network DoS attacks created by large downloads
• Potential liability from pirated intellectual property
Because of the dangers, many organizations choose to prohibit the use of P2P applications and block common port numbers used by these applications at the firewall. Another helpful remediation is to keep all anti-malware software up to date in case malware is transmitted by the use of P2P applications.
Rogue Device on the Network
Any time new devices appear on a network, there should be cause for suspicion. While it is possible that users may be introducing these devices innocently, there are also a number of bad reasons for these devices to be on the network. The following types of illegitimate devices may be found on a network:

• Wireless key loggers: These collect information and transmit it to the criminal via Bluetooth or Wi-Fi.
• Wi-Fi and Bluetooth hacking gear: This gear is designed to capture both Bluetooth and Wi-Fi transmissions.
• Rogue access points: Rogue APs are designed to lure your hosts into a connection for a peer-to-peer attack.
• Rogue switches: These switches can attempt to create a trunk link with a legitimate switch, thus providing access to all VLANs.
• Mobile hacking gear: This gear allows a malicious individual to use software along with software-defined radios to trick cell phone users into routing connections through a fake cell tower.
The actions required to detect or prevent rogue devices depend on the type of device. With respect to rogue switches, ensure that all ports that are required to be trunks are “hard coded” as trunks and that Dynamic Trunking Protocol (DTP) is disabled on all switch ports.
With respect to rogue wireless access points, the best solution is a wireless intrusion prevention system (WIPS). These systems can not only alert you when any unknown device is in the area (APs and stations) but can take a number of actions to prevent security issues, including the following:

• Locate a rogue AP by using triangulation when three or more sensors are present
• Deauthenticate any stations that have connected to an “evil twin”
• Detect denial-of-service attacks
• Detect man-in-the-middle and client-impersonation attacks
Some examples of these tools include Mojo Networks AirTight WIPS, HP RFProtect, Cisco Adaptive Wireless IPS, Fluke Networks AirMagnet Enterprise, HP Mobility Security IDS/IPS, and Zebra Technologies AirDefense.
Scan/Sweep
One of the early steps in a penetration test is to scan or sweep the network. If no known penetration test is under way but a scan or sweep is occurring, it is an indication that a malicious individual may be scanning in preparation for an attack. The following are the most common of these scans:

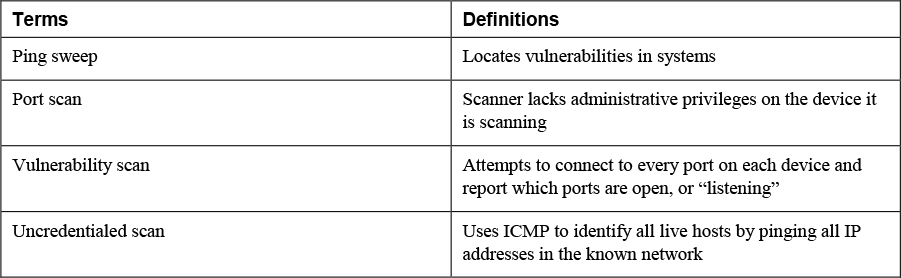
• Ping sweeps: Also known as ICMP sweeps, ping sweeps use ICMP to identify all live hosts by pinging all IP addresses in the known network. All devices that answer are up and running.
• Port scans: Once all live hosts are identified, a port scan attempts to connect to every port on each device and report which ports are open, or “listening.”
• Vulnerability scans: Vulnerability scans are more comprehensive than the other types of scans in that they identify open ports and security weaknesses. The good news is that uncredentialed scans expose less information than credentialed scans. An uncredentialed scan is a scan in which the scanner lacks administrative privileges on the device it is scanning.
Unusual Traffic Spike
Any unusual spikes in traffic that are not expected should be cause for alarm. Just as an increase in bandwidth usage may indicate DoS or DDoS activity, unusual spikes in traffic may also indicate this type of activity. Again, know what your traffic patterns are and create a baseline of this traffic rhythm. With traffic spikes, there are usually accompanying symptoms such as network slowness and, potentially, alarms from any IPSs or IDSs you have deployed.
Keep in mind that there are other legitimate reasons for traffic spikes. The following are some of the normal activities that can cause these spikes:

• Backup traffic in the LAN
• Virus scanner updates
• Operating system updates
• Mail server issues
Common Protocol over Non-standard Port
Common protocols such as FTP, SMTP, and SNMP use default port numbers that have been standardized. However, it is possible to run these protocols over different port numbers. Whenever you discover this being done, you should treat the transmission with suspicion because often there is no reason to use a non-standard port unless you are trying to obscure what you are doing. It also is a way of evading ACLs that prevent traffic on the default standard ports. Be aware, though, that running a common protocol over a non-standard port also is used legitimately to prevent DoS attacks on default standard ports by shifting a well-known service to a non-standard port number. So, it is a technique used by both sides.
Host-Related Indicators of Compromise
While many indicators of compromise are network related, some are indications that something is wrong at the system or host level. These are behaviors of a single system or host rather than network symptoms.
Processor Consumption
When the processor is very busy with very little or nothing running to generate the activity, it could be a sign that the processor is working on behalf of malicious software. Processor consumption was covered in Chapter 13, “The Importance of Proactive Threat Hunting.”
Memory Consumption
Another key indicator of a compromised host is increased memory consumption. Memory consumption was also covered in Chapter 13.
Drive Capacity Consumption
Available disk space on the host decreasing for no apparent reason is cause for concern. It could be that the host is storing information to be transmitted at a later time. Some malware also causes an increase in drive availability due to deleting files. Finally, in some cases, the purpose is to fill the drive as part of a DoS or DDoS attack. One of the difficult aspects of this is that the drive is typically filled with files that cannot be seen or that are hidden. When users report a sudden filling of their hard drive and even a slow buildup over time that cannot be accounted for, you should scan the device for malware in Safe Mode. Scanning with multiple products is advised as well.
Unauthorized Software
The presence of any unauthorized software should be another red flag. If you have invested in a vulnerability scanner, you can use it to create a list of installed software that can be compared to a list of authorized software. Unfortunately, many types of malware do a great job of escaping detection.
One of the ways to prevent unauthorized software is through the use of Windows AppLocker. By using this tool, you can create whitelists, which specify the only applications that are allowed, or you can create a blacklist, specifying which applications cannot be run.
Figure 17-4 shows a Windows AppLocker rule being created. This particular rule is based on the path to the application, but it could also be based on the publisher of the application or on a hash value of the application file. This particular rule is set to allow the application in the path, but it could also be set to deny that application. Once the policy is created, it can be applied as widely as desired in the Active Directory infrastructure.
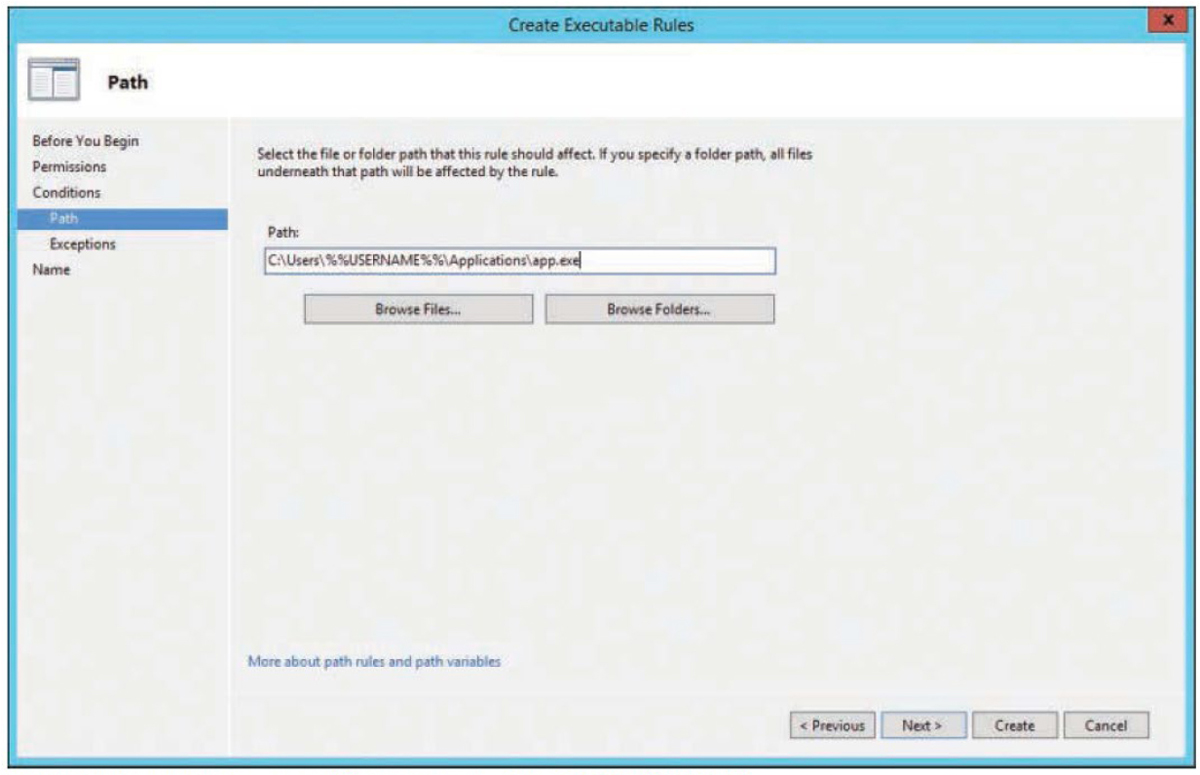
Figure 17-4 Create Executable Rules
The following are additional general guidelines for preventing unwanted software:
• Keep the granting of administrative privileges to a minimum.
• Audit the presence and use of applications. (AppLocker can do this.)
Malicious Process
Malicious programs use processes to access the CPU, just as normal programs do. This means their processes are considered malicious processes. You can sometimes locate processes that are using either CPU or memory by using Task Manager, but again, many malware programs don’t show up in Task Manager. Either Process Explorer or some other tool may give better results than Task Manager. If you locate an offending process and end that process, don’t forget that the program is still there, and you need to locate it and delete all of its associated files and registry entries.
Unauthorized Change
If an organization has a robust change control process, there should be no unauthorized changes made to devices. Whenever a user reports an unauthorized change in his device, it should be investigated. Many malicious programs make changes that may be apparent to the user. Missing files, modified files, new menu options, strange error messages, and odd system behavior are all indications of unauthorized changes.
Unauthorized Privilege
Unauthorized changes can be the result of privilege escalation. Check all system accounts for changes to the permissions and rights that should be assigned, paying special attention to new accounts with administrative privileges. When assigning permissions, always exercise the concept of least privilege. Also ensure that account reviews take place on a regular basis to identify privileges that have been escalated and accounts that are no longer needed.
Data Exfiltration
Data exfiltration is the theft of data from a device. Any reports of missing or deleted data should be investigated. In some cases, the data may still be present, but it has been copied and transmitted to the attacker. Software tools are available to help track the movement of data in transmissions.
Abnormal OS Process Behavior
When an operating system is behaving strangely and not operating normally, it could be that the operating system needs to be reinstalled or that it has been compromised by malware in some way. While all operating systems occasionally have issues, persistent issues or issues that are typically not seen or have never been seen could indicate a compromised operating system.
File System Change or Anomaly
If file systems change, especially system files (those that are part of the operating system), it is not a good sign. System files should not change from the day the operating system was installed, and if they do, it is an indication of malicious activity. Many systems offer the ability to verify the integrity of system files. For example, the System File Checker (SFC) is a utility built into the Windows 10 operating system that will check for and repair operating system file corruption.
Registry Change or Anomaly
Most registry changes are made through using tools such as Control Panel, and changes are rarely made directly to the registry using the Registry Editor. Changes to registry settings are common when a compromise has occurred. Changes to the registry are not obvious and can remain hidden for long periods of time. You need tools to help identify infected settings in the registry and to identify the last saved settings. Examples include Microsoft’s Sysinternals Autoruns and Silent Runners.vbs.
Unauthorized Scheduled Task
In some cases, malware can generate a task that is scheduled to occur on a regular basis, like communicating back to the hacker at certain intervals or copying file locations at certain intervals. Any scheduled task that was not configured by the local team is a sign of compromise. Access to Scheduled Tasks can be controlled through the use of Group Policy.
Application-Related Indicators of Compromise
In some cases, symptoms are not present on the network or in the activities of the host operating system, but they are present in the behavior displayed by a compromised application. Some of these indicators are covered in the following sections.
Anomalous Activity
When an application is behaving strangely and not operating normally, it could be that the application needs to be reinstalled or that it has been compromised by malware in some way. While all applications occasionally have issues, persistent issues or issues that are typically not seen or have never been seen could indicate a compromised application.
Introduction of New Accounts
Some applications have their own account database. In that case, you may find accounts that didn’t previously exist in the database—and this should be a cause for alarm and investigation. Many application compromises create accounts with administrative access for the use of a malicious individual or for the processes operating on his behalf.
Unexpected Output
When the output from a program is not what is normally expected and when dialog boxes are altered or the order in which the boxes are displayed is not correct, it is an indication that the application has been altered. Reports of strange output should be investigated.
Unexpected Outbound Communication
Any unexpected outbound traffic should be investigated, regardless of whether it was discovered as a result of network monitoring or as a result of monitoring the host or application. With regard to the application, it can mean that data is being transmitted back to the malicious individual.
Service Interruption
When an application stops functioning with no apparent problem, or when an application cannot seem to communicate in the case of a distributed application, it can be a sign of a compromised application. Any such interruptions that cannot be traced to an application, host, or network failure should be investigated.
Application Log
Chapter 11, “Analyzing Data as Part of Security Monitoring Activities,” covered the event logs in Windows. One of those event logs is dedicated to errors and issues related to applications, the Application log. This log focuses on the operation of Windows applications. Events in this log are classified as error, warning, or information, depending on the severity of the event. The Application log in Windows 10 is shown in Figure 17-5.
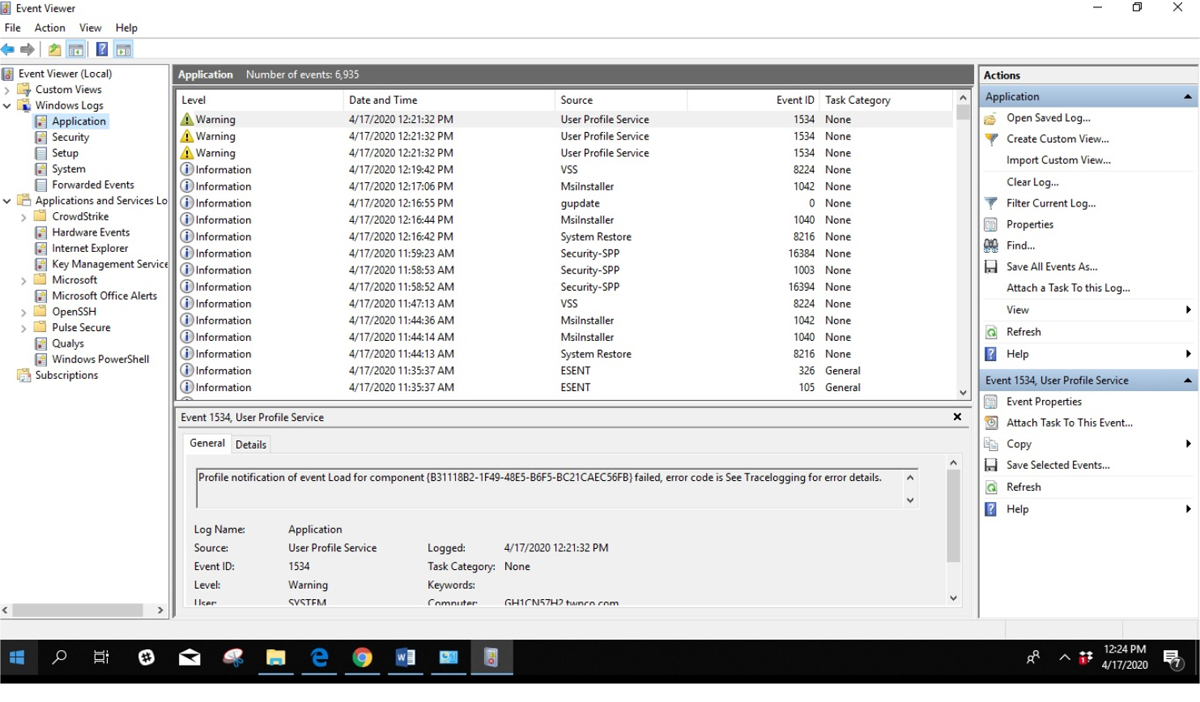
Figure 17-5 Application Log
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have several choices for exam preparation: the exercises here, Chapter 22, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep Software Online.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 17-2 lists a reference of these key topics and the page numbers on which each is found.

Table 17-2 Key Topics for Chapter 17
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
indicators of compromise (IoCs)
wireless intrusion prevention system (WIPS)
Review Questions
1. __________________ refers to traffic that leaves a network at regular intervals.
2. List at least two network-related IoCs.
3. Match the following terms with their definitions.
4. The ____________________ focuses on the operation of Windows applications.
5. List at least two host-related IoCs.
6. Match the following terms with their definitions.
7. _________________ enables you to look at the graphs that are similar to Task Manager and identify what caused spikes in the past, which is not possible with Task Manager alone.
8. List at least two application-related IoCs.
9. Match the following terms with their definitions.
10. A(n) ______________________ is a scan in which the scanner lacks administrative privileges on the device it is scanning.
