Chapter 14. Automation Concepts and Technologies
This chapter covers the following topics related to Objective 3.4 (Compare and contrast automation concepts and technologies) of the CompTIA Cybersecurity Analyst (CySA+) CS0-002 certification exam:
• Workflow orchestration: Describes the process of Security Orchestration, Automation, and Response (SOAR) and its role in security
• Scripting: Reviews the scripting process and its role in automation
• Application programming interface (API) integration: Describes how this process reduces access to an application’s internal functions through an API
• Automated malware signature creation: Identifies an automated process of malware identification
• Data enrichment: Discusses processes used to enhance, refine, or otherwise improve raw data
• Threat feed combination: Defines a process for making use of data from multiple intelligence feeds
• Machine learning: Describes the role machine learning plays in automated security
• Use of automation protocols and standards: Identifies various protocols and standards, including Security Content Automation Protocol (SCAP), and their application
• Continuous integration: Covers the process of ongoing integration of software components during development
• Continuous deployment/delivery: Covers the process of ongoing review and upgrade of software
Traditionally, network operations and threat intelligence activities were performed manually by technicians. Increasingly in today’s environments, these processes are being automated through the use of scripting and other automation tools. This chapter explores how workflows can be automated.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz enables you to assess whether you should read the entire chapter. If you miss no more than one of these ten self-assessment questions, you might want to skip ahead to the “Exam Preparation Tasks” section. Table 14-1 lists the major headings in this chapter and the “Do I Know This Already?” quiz questions covering the material in those headings so that you can assess your knowledge of these specific areas. The answers to the “Do I Know This Already?” quiz appear in Appendix A.
Table 14-1 “Do I Know This Already?” Foundation Topics Section-to-Question Mapping

1. Which of the following enables you to automate the response to a security issue? (Choose the best answer.)
a. Orchestration
b. Piping
c. Scripting
d. Virtualization
2. Which scripting language is used to work in the Linux interface?
a. Python
b. Bash
c. Ruby
d. Perl
3. Which of the following is used to provide integration between your website and a payment gateway?
a. Perl
b. Orchestration
c. API
d. Scripting
4. Which of the following is an additional method of identifying malware?
a. DHCP snooping
b. DAI
c. Automated malware signature creation
d. Piping
5. When you receive bulk e-mail from a vendor and it refers to you by first name, what technique is in use?
a. Scripting
b. Orchestration
c. Heuristics
d. Data enrichment
6. Threat feeds inform the recipient about all but which of the following?
a. Presence of malware on the recipient
b. Suspicious domains
c. Lists of known malware hashes
d. IP addresses associated with malicious activity
7. Which of the following is an example of machine learning?
a. NAC
b. AEG
c. EDR
d. DLP
8. Which of the following is a standard that the security automation community uses to enumerate software flaws and configuration issues?
a. NAC
b. DAC
c. SCAP
d. DLP
9. Which of the following is a software development practice whereby the work of multiple individuals is combined a number of times a day?
a. Sinkholing
b. Continuous integration
c. Aggregation
d. Inference
10. Which of the following is considered the next generation of DevOps and attempts to make sure that software developers can release new product changes to customers quickly in a sustainable way?
a. Agile
b. DevSecOps
c. Continuous deployment/delivery
d. Scrum
Foundation Topics
Workflow Orchestration
Workflow orchestration is the sequencing of events based on certain parameters by using scripting and scripting tools. Over time orchestration has been increasingly used to automate processes that were formerly carried out manually by humans.
In virtualization, it is quite common to use orchestration. For example, in the VMware world, technicians can create what are called apps, groups of virtual machines that are managed and orchestrated as a unit to provide a service to users. Using orchestration tools, you can set one device to always boot before another device. For example, in an Windows Active Directory environment, you may need the domain controller (DC) to boot up before the database server so that the database server can property authenticate to the DC and function correctly.
Figure 14-1 shows another, more complex automated workflow orchestration using VMware vCloud Automation Center (vCAC).

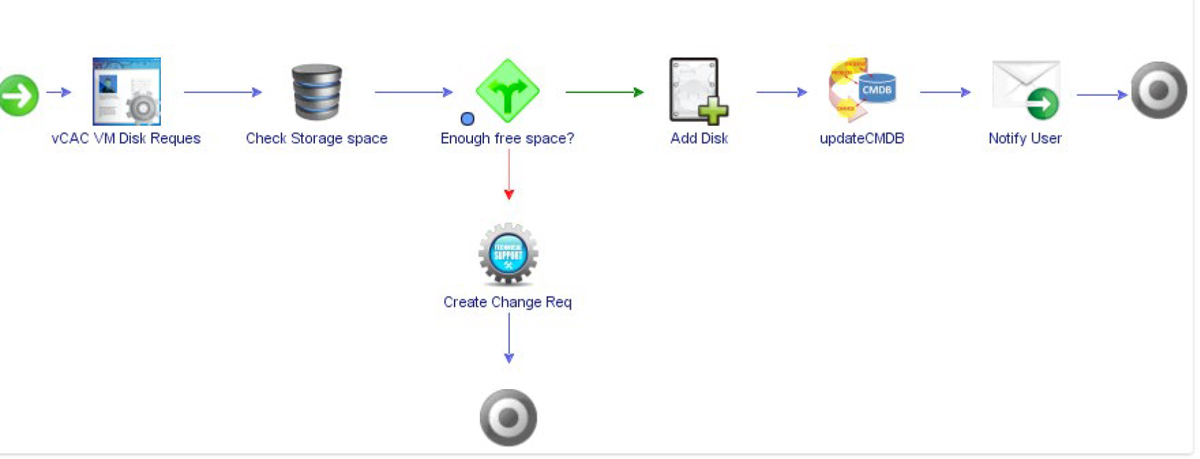
Figure 14-1 Workflow Orchestration
The workflow is sequenced to occur in the following fashion:
1. A request comes in to write to the disk.
2. The disk space is checked.
3. Insufficient space is found.
4. A change request is generated for more space.
5. A disk is added.
6. The configuration database is updated.
7. The user is notified.
While this is one use of workflow orchestration, it can also be used in the security world. Examples include
• Dynamic incident response plans that adapt in real time
• Automated workflows to empower analysts and enable faster response
Scripting
Scripting languages and scripting tools are used to automate a process. Common scripting languages include

• bash: Used to work in the Linux interface
• Node js: Framework to write network applications using JavaScript
• Ruby: Great for web development
• Python: Supports procedure-oriented programming and object-oriented programming
• Perl: Found on all Linux servers, helps in text manipulation tasks
• Windows PowerShell: Found on all Windows servers
Scripting tools that require less knowledge of the actual syntax of the language can also be used, such as

• Puppet
• Chef
• Ansible
For example, Figure 14-2 shows Puppet being used to automate the update of Apache servers.

Figure 14-2 Puppet Orchestration
Application Programming Interface (API) Integration
As a review, an API is a set of clearly defined methods of communication between various software components. As such, you should think of an API as a connection point that requires security consideration. For example, an API between your e-commerce site and a payment gateway must be secure. So, what is API integration and why is it important?
API integration means that the applications on either end of the API are synchronized and protecting the integrity of the information that passes across the API. It also enables the proper updating and versioning required in many environments. The term also describes the relationship between a website and an API when the API is integrated into the website.
Automated Malware Signature Creation
Automated malware signature creation is an additional method of identifying It might not be malware. The antivirus software monitors incoming unknown files for the presence of malware and analyzes each file based on both classifiers of file behavior and classifiers of file content. The file is then classified as having a particular malware classification. Subsequently, a malware signature is generated for the incoming unknown file based on the particular malware classification. This malware signature can be used by an antivirus program as a part of the antivirus program’s virus identification processes.
Data Enrichment
Data enrichment is a technique that allows one process to gather information from another process or source and then customize a response to a third source using the data from the second process or source. When you receive bulk e-mail from a vendor and it refers to you by first name, that is an example of data enrichment in use. In that case a file of email address is consult (second process) and added to the response to you. Another common data enrichment process would, for example, correct likely misspellings or typographical errors in a database by using precision algorithms designed for that purpose. Another way in which data enrichment can work is by extrapolating data.
This can create a privacy issue that has been raised by the EU General Data Protection Regulation (GDPR), leading to some privacy regulations by the EU that limit data enrichment for this very reason. Users typically have a reasonable idea about which information they have provided to a specific organization, but if the organization adds information from other databases, this picture will be skewed. The organization will have information about them of which they are not aware.
Figure 14-3 shows another security-related example of the data enrichment process. This is an example of an automated process used by a security analytics platform called Blue Coat. The data enrichment part of the process occurs at Steps 4 and 5 when information from an external source is analyzed and used to enrich the alert message that is generated from the file detected.


Figure 14-3 Data Enrichment Process Example
Threat Feed Combination
A threat feed is a constantly updating stream of intelligence about threat indicators and artifacts that is delivered by a third-party security organization. Threat feeds are used to inform the organization as quickly as possible about new threats that have been identified. Threat feeds contain information including
• Suspicious domains
• Lists of known malware hashes
• IP addresses associated with malicious activity
Chapter 11, “Analyzing Data as Part of Security Monitoring Activities,” described how a SIEM aggregates the logs from various security devices into a single log for analysis. By analyzing the single aggregated log, inferences can be made about potential issues or attacks that would not be possible if the logs were analyzed separately.
Using SIEM (or other aggregation tools) to aggregate threat feeds can also be beneficial, and tools and services such as the following offer this type of threat feed combination:

• Combine: Gathers threat intelligence feeds from publicly available sources
• Palo Alto Networks AutoFocus: Provides intelligence, correlation, added context, and automated prevention workflows
• Anomali ThreatStream: Helps deduplicate data, removes false positives, and feeds intelligence to security tools
• ThreatQuotient: Helps accelerate security operations with an integrated threat library and shared contextual intelligence
• ThreatConnect: Combines external threat data from trusted sources with in-house data
Machine Learning
Artificial intelligence (AI) and machine learning have fascinated humans for decades. Artificial intelligence (AI) is the capability of a computer system to make decisions using human-like intelligence. Machine learning is a way to make that possible by creating algorithms that enable the system to learn from what it sets and apply it. Since the first time we conceived of the idea of talking to a computer and getting an answer like characters did in comic books years ago, we have waited for the day to come when smart robots would not just do the dirty work but also learn just as humans do.
Today, robots are taking on increasingly more and more detailed work. One of the exciting areas where AI and machine learning is yielding dividends is in intelligent network security—or the intelligent network. These networks seek out their own vulnerabilities before attackers do, learn from past errors, and work on a predictive model to prevent attacks.
For example, automatic exploit generation (AEG) is the “first end-to-end system for fully automatic exploit generation,” according to the Carnegie Mellon Institute’s own description of its AI named Mayhem. Developed for off-the-shelf as well as the enterprise software being increasingly used in smart devices and appliances, AEG can find a bug and determine whether it is exploitable.
Use of Automation Protocols and Standards
As in almost every other area of IT, standards and protocols for automation have emerged to help support the development and sharing of threat information. As with all standards, the goal is to arrive at common methods of sharing threat data.
Security Content Automation Protocol (SCAP)
Chapter 2, “Utilizing Threat Intelligence to Support Organizational Security,” introduced the Common Vulnerability Scoring System (CVSS), a common system for describing the characteristics of a threat in a standard format. The ranking of vulnerabilities that are discovered is based on predefined metrics that also are used by the Security Content Automation Protocol (SCAP). This is a standard that the security automation community uses to enumerate software flaws and configuration issues. It standardized the nomenclature and formats used. A vendor of security automation products can obtain a validation against SCAP, demonstrating that it will interoperate with other scanners and express the scan results in a standardized way.
Understanding the operation of SCAP requires an understanding of its identification schemes, one of which you learned about, CVE. Let’s review it.

• Common Configuration Enumeration (CCE): These are configuration best practice statements maintained by the National Institute of Standards and Technology (NIST).
• Common Platform Enumeration (CPE): These are methods for describing and classifying operating systems, applications, and hardware devices.
• Common Weakness Enumeration (CWE): These are design flaws in the development of software that can lead to vulnerabilities.
• Common Vulnerabilities and Exposures (CVE): These are vulnerabilities in published operating systems and applications software.
A good example of the implementation of this is the Window System Center Configuration Manager Extensions for SCAP. It allows for the conversion of SCAP data files to Desired Configuration Management (DCM) Configuration Packs and converts DCM reports into SCAP format.
Continuous Integration
Continuous integration is a software development practice whereby the work of multiple individuals is combined a number of times a day. The idea behind this is to identity bugs as early as possible in the development process. As it relates to security, the goal of continuous integration is to locate security issues as soon as possible. Continuous integration security testing improves code integrity, leads to more secure software systems, and reduces the time it takes to release new updates. Usually, merging all development versions of the code base occurs multiple times throughout a day. Figure 14-4 illustrates this process.


Figure 14-4 Continuous Integration
Continuous Deployment/Delivery
Taking continuous integration one step further is the concept of continuous deployment/delivery. It is considered the next gen of DevOps and attempts to make sure that software developers can release new changes to customers quickly in a sustainable way. Continuous deployment goes one step further with every change that passes all stages of your production pipeline being released to your customers. This helps to improve the feedback loop. Figure 14-5 illustrates the relationship between the three concepts.


Figure 14-5 Continuous Integration, Continuous Delivery, and Continuous Deployment
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have several choices for exam preparation: the exercises here, Chapter 22, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep Software Online.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 14-2 lists a reference of these key topics and the page numbers on which each is found.

Table 14-2 Key Topics in Chapter 14

Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
application programming interface (API) integration
automated malware signature creation
Security Content Automation Protocol (SCAP)
Common Configuration Enumeration (CCE)
Common Platform Enumeration (CPE)
Common Weakness Enumeration (CWE)
Common Vulnerabilities and Exposures (CVE)
continuous deployment/delivery
Review Questions
1. _______________ is the sequencing of events based on certain parameters by using scripting and scripting tools.
2. List at least one use of workflow orchestration in the security world.
3. Match the following terms with their definitions.

4. __________________ is a scripting tool found in Windows servers.
5. List at least two of the components of SCAP.
6. Puppet is a ________________________ tool.
7. List at least two types of information available from threat feeds.
8. Match the following SCAP terms with their definitions.

9. _________________________ is a software development practice where by the work of multiple individuals is combined a number of times a day
10. List at least two threat feed aggregation tools.
11. Match the following terms with their definitions.
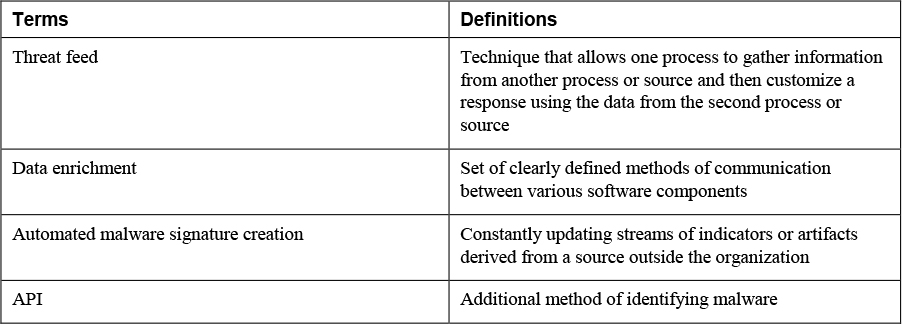
12. ______________________ are groups of VMware virtual machines that are managed and orchestrated as a unit to provide a service to users.
