Chapter 18. Utilizing Basic Digital Forensics Techniques
This chapter covers the following topics related to Objective 4.4 (Given a scenario, utilize basic digital forensics techniques) of the CompTIA Cybersecurity Analyst (CySA+) CS0-002 certification exam:
• Network: Covers network protocol analyzing tools including Wireshark and tcpdump
• Endpoint: Discusses disk and memory digital forensics
• Mobile: Covers mobile forensics techniques
• Cloud: Includes forensic techniques in the cloud
• Virtualization: Covers issues and forensics unique to virtualization
• Legal hold: Describes the legal concept of retaining information for legal purposes
• Procedures: Covers forensic procedures
• Hashing: Describes forensic verification, including changes to binaries
• Carving: Describes the process of carving that allows the recovery of files
• Data acquisition: Covers data acquisition processes
Over time, techniques have been developed to perform a forensic examination of a compromised system or network. Security professionals should use these time-tested processes to guide the approach to gathering digital evidence. This chapter explores many of these basic techniques.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz enables you to assess whether you should read the entire chapter. If you miss no more than one of these nine self-assessment questions, you might want to skip ahead to the “Exam Preparation Tasks” section. Table 18-1 lists the major headings in this chapter and the “Do I Know This Already?” quiz questions covering the material in those headings so that you can assess your knowledge of these specific areas. The answers to the “Do I Know This Already?” quiz appear in Appendix A.
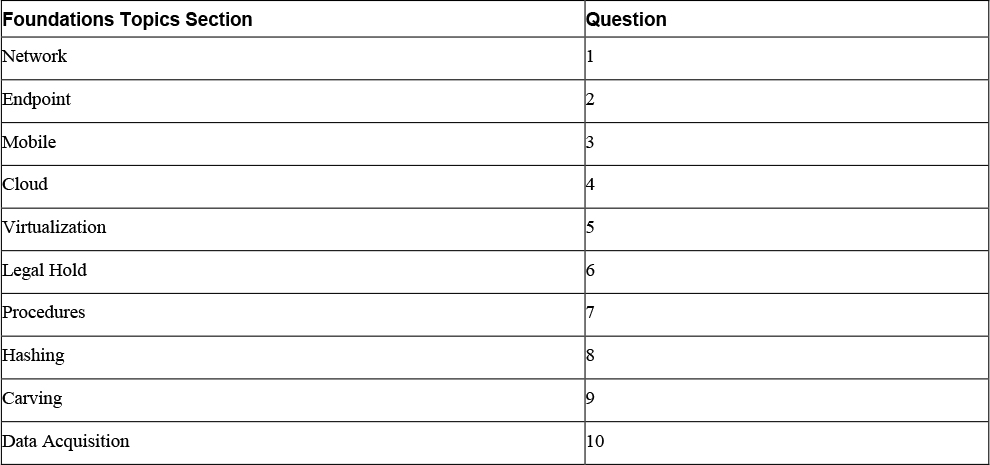
Table 18-1 “Do I Know This Already?” Foundation Topics Section-to-Question Mapping
1. Which of the following is a packet analyzer?
a. Wireshark
b. FTK
c. Helix
d. Cain and Abel
2. Which of the following groups is a password cracking tool?
a. Wireshark
b. FTK
c. Helix
d. Cain and Abel
3. Which of the following is a data acquisition tool?
a. MD5
b. EnCase
c. Cellebrite
d. dd
4. Which of the following is not true of the cloud-based approach to vulnerability scanning?
a. Installation costs are lower than with a premises-based solutions.
b. Maintenance costs are higher than with a premises-based solutions.
c. Upgrades are included in a subscription.
d. It does not require the client to provide onsite equipment.
5. Which of the following is false with respect to using forensic tools for the virtual environment?
a. The same tools can be used as in a physical environment.
b. Knowledge of the files that make up a VM is critical.
c. Requires deep knowledge of the log files created by the various components.
d. Requires access to the hypervisor code.
6. Which of the following often requires that organizations maintain archived data for longer periods?
a. Chain of custody
b. Lawful intercept
c. Legal hold
d. Discovery
7. Which if the following items in a digital forensic investigation suite is used to make copies of a hard drive?
a. Imaging utilities
b. Analysis utilities
c. Hashing utilities
d. Password crackers
8. Which of the following is the strongest hashing utility?
a. MD5
b. MD6
c. SHA-1
d. SHA-3
9. Which of the following types of file carving is not supported by Forensic Explorer?
a. Cluster-based file carving
b. Sector-based file carving
c. Byte-based file carving
d. Partition-based file carving
10. Which of the following is a data acquisition tool for smartphones?
a. MD5
b. EnCase
c. Cellebrite
d. dd
Foundation Topics
Network
During both environmental reconnaissance testing and when performing forensic investigations, security analysts have a number of tools at their disposal, and it’s no coincidence that many of them are the same tools that hackers use. The following sections cover the most common network tools and describe the types of information you can determine about the security of the environment by using each tool.
Wireshark
A packet (or protocol) analyzer can be a standalone device or software running on a laptop computer. One of the most widely used software-based protocol analyzers is Wireshark. It captures raw packets off the interface on which it is configured and allows you to examine each packet. If the data is unencrypted, you can read the data. Figure 18-1 shows an example of Wireshark in use. You can use a protocol analyzer to capture traffic flowing through a network switch by using the port mirroring feature of a switch. You can then examine the captured packets to discern the details of communication flows.
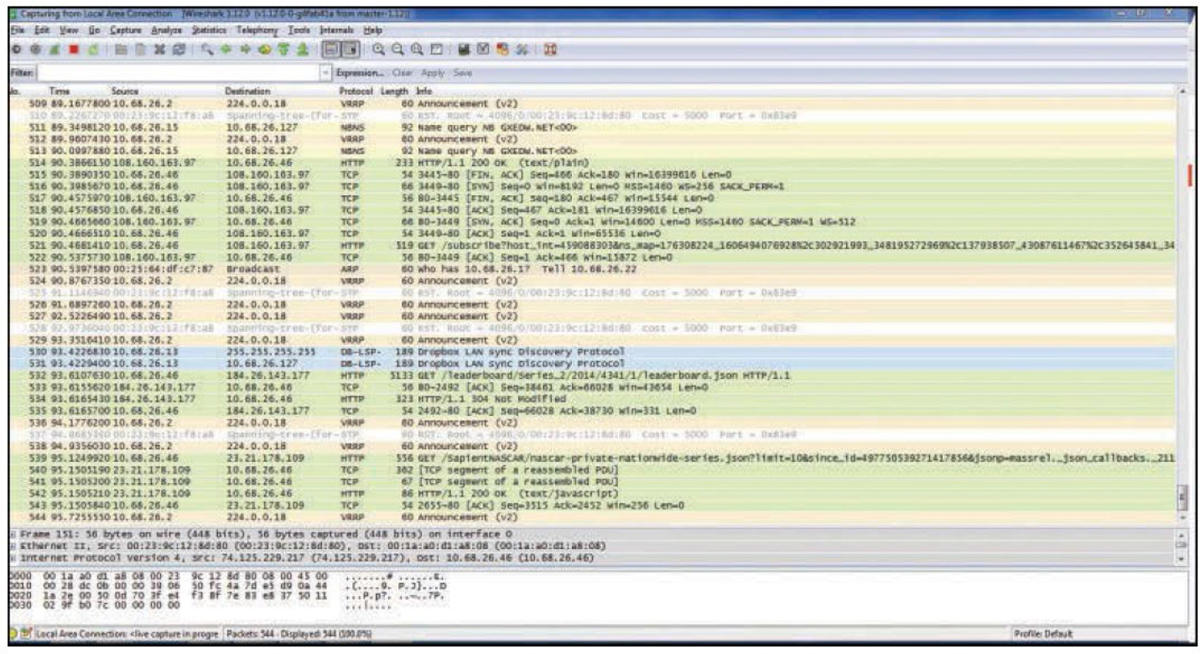
Figure 18-1 Wireshark
In the output shown in Figure 18-1, each line represents a packet captured on the network. You can see the source IP address, the destination IP address, the protocol in use, and the information in the packet. For example, line 511 shows a packet from 10.68.26.15 to 10.68.16.127, which is a NetBIOS name resolution query. Line 521 shows an HTTP packet from 10.68.26.46 to a server at 108.160.163.97. Just after that, you can see the server sending an acknowledgment back. To read a packet, you click the single packet. If the data is cleartext, you can read and analyze it. So you can see how an attacker could use Wireshark to acquire credentials and other sensitive information. Protocol analyzers can be of help whenever you need to see what is really happening on your network. For example, say you have a security policy that mandates certain types of traffic should be encrypted, but you are not sure that everyone is complying with this policy. By capturing and viewing the raw packets on the network, you can determine whether users are compliant.
Figure 18-2 shows additional output from Wireshark. The top panel shows packets that have been captured. The line numbered 384 has been chosen, and the parts of the packet are shown in the middle pane. In this case, the packet is a response from a DNS server to a device that queried for a resolution. The bottom pane shows the actual data in the packet and, because this packet is not encrypted, you can see that the user was requesting the IP address for www.cnn.com. Any packet not encrypted can be read in this pane.


Figure 18-2 Analyzing Wireshark Output
During environmental reconnaissance testing, you can use packet analyzers to identify traffic that is unencrypted but should be encrypted (as previously mentioned), protocols that should not be in use on the network, and other abnormalities. You can also use these tools to recognize certain types of attacks. Figure 18-3 shows Wireshark output which indicates that a SYN flood attack is underway. Notice the lines highlighted in gray. These are all SYN packets sent to 10.1.0.2, and they are part of a SYN flood. Notice that the target device is answering with RST/ACK packets, which indicates that the port is closed (lines highlighted in red). One of the SYN packets (highlighted in blue) is open, so you can view its details in the bottom pane. You can expand this pane and read the information from all four layers of the TCP model. Currently the transport layer is expanded.
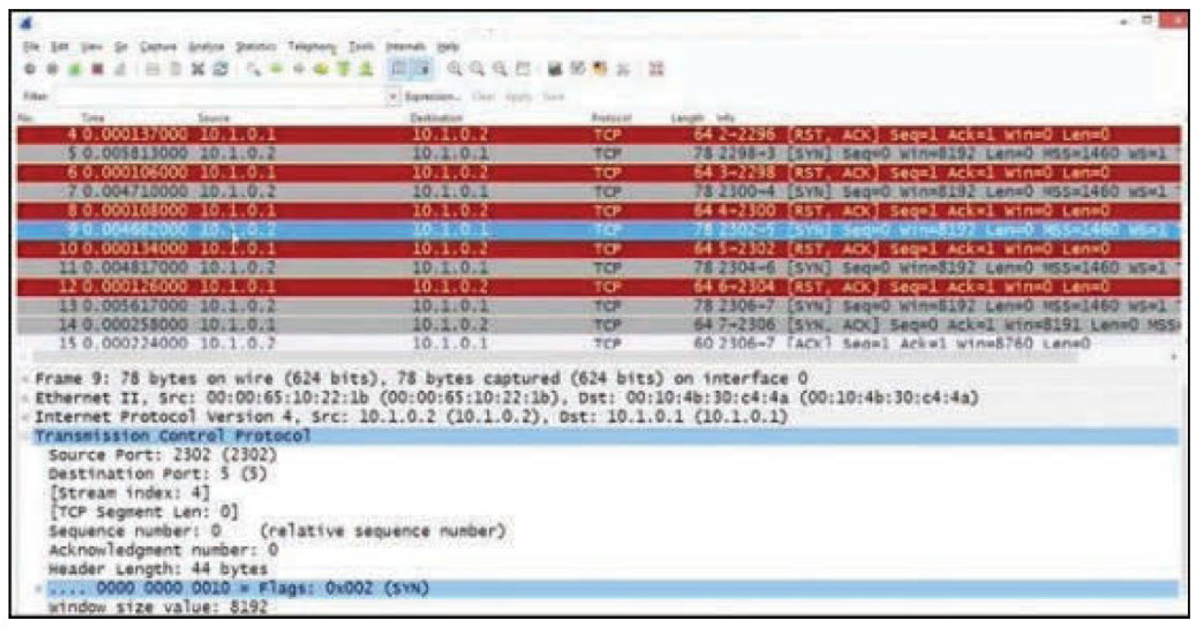
Figure 18-3 SYN Flood Displayed in Wireshark
tcpdump
tcpdump is a command-line tool that can capture packets on Linux and Unix platforms. A version for Windows, windump, is available as well. Using it is a matter of selecting the correct parameter to go with the tcpdump command. For example, the following command enables a capture (-i) on the Ethernet 0 interface.
tcpdump -i eth0
To explore the many other switches that are available for tcpdump, see www.tcpdump.org/tcpdump_man.html.
Endpoint
Forensic tools are used in the process of collecting evidence during a cyber investigation. Many of these tools are used to obtain evidence from endpoints. Included in this category are forensic investigation suites, hashing utilities, password cracking tools, and imaging tools.
Disk
Many tools are dedicated to retrieving evidence from a hard drive. Others are used to work with the data found on the hard drive. The following tools are all related in some form or fashion to obtaining evidence from a hard drive.
FTK
Forensic Toolkit (FTK) is a commercial toolkit that can scan a hard drive for all sorts of information. This kit also includes an imaging tool and an MD5 hashing utility. It can locate relevant evidence, such as deleted e-mails. It also includes a password cracker and the ability to work with rainbow tables.
For more information on FTK, see https://accessdata.com/products-services/forensic-toolkit-ftk.
Helix3
Helix3 comes as a live CD that can be mounted on a host without affecting the data on the host. From the live CD you can acquire evidence and make drive images. This product is sold on a subscription basis by e-fense.
For more information on Helix, see www.e-fense.com/products.php.
Password Cracking
In the process of executing a forensic investigation, it may be necessary to crack passwords. Often files have been encrypted or password protected by malicious individuals, and you need to attempt to recover the password. There are many, many password cracking utilities out there; the following are two of the most popular ones:
• John the Ripper: John the Ripper is a password cracker that can work in Unix/Linux as well as macOS systems. It detects weak Unix passwords, though it supports hashes for many other platforms as well. John the Ripper is available in three versions: an official free version, a community-enhanced version (with many contributed patches but not as much quality assurance), and an inexpensive pro version. One mitigation for this attack is the Hash Suite for Windows.
• Cain and Abel: One of the most well-known password cracking programs, Cain and Abel can recover passwords by sniffing the network; crack encrypted passwords using dictionary, brute-force, and cryptanalysis attacks; record VoIP conversations; decode scrambled passwords; reveal password boxes; uncover cached passwords; and analyze routing protocols. Figure 18-4 shows sample output from this tool. As you can see, an array of attacks can be performed on each located account. This example shows a scan of the local machine for user accounts in which the program has located three accounts: Admin, Sharpy, and JSmith. By right-clicking the Admin account, you can use the program to perform a brute-force attack—or a number of other attacks—on that account.

Figure 18-4 Cain and Abel
Imaging
Before you perform any analysis on a target disk in an investigation, you should make a bit-level image of the disk so that you can conduct the analysis on that copy. Therefore, a forensic imaging utility should be part of your toolkit. There are many forensic imaging utilities, and many of the forensic investigation suites contain them. Moreover, many commercial forensic workstations have these utilities already loaded.
The dd command is a Linux command that is used is to convert and copy files. The U.S. Department of Defense created a fork (a variation) of this command called dcfldd that adds additional forensic functionality. By simply using dd with the proper parameters and the correct syntax, you can make an image of a disk, but dcfldd enables you to also generate a hash of the source disk at the same time. For example, the following command reads 5 GB from the source drive and writes that to a file called mymage.dd.aa:
dcfldd if=/dev/sourcedrive hash=md5,sha256 hashwindow=10G md5log=hashmd5.txt sha256log=hashsha.txt hashconv=after bs=512 conv=noerror,sync split=5G splitformat=aa of=myimage.dd
This example also calculates the MD5 hash and the SHA-256 hash of the 5-GB chunk. It then reads the next 5 GB and names that myimage.dd.ab. The MD5 hashes are stored in a file called hashmd5.txt, and the SHA-256 hashes are stored in a file called hashsha.txt. The block size for transferring has been set to 512 bytes, and in the event of read errors, dcfldd writes zeros.
Memory
Many penetration testing tools perform an operation called a core dump or memory dump. Applications store information in memory, and this information can include sensitive data, passwords, usernames, and encryption keys. Hackers can use memory-reading tools to analyze the entire memory content used by an application. Any vulnerability testing should take this into consideration and utilize the same tools to identify any issues in the memory of an application. The following are some examples of memory-reading tools:

• Memdump: This free tool runs on Windows, Linux, and Solaris. It simply creates a bit-by-bit copy of the volatile memory on a system.
• KnTTools: This memory acquisition and analysis tool used with Windows systems captures physical memory and stores it to a removable drive or sends it over the network to be archived on a separate machine.
• FATKit: This popular memory forensic tool automates the process of extracting interesting data from volatile memory. FATKit helps an analyst visualize the objects it finds to help in understanding the data that the tool was able to find.
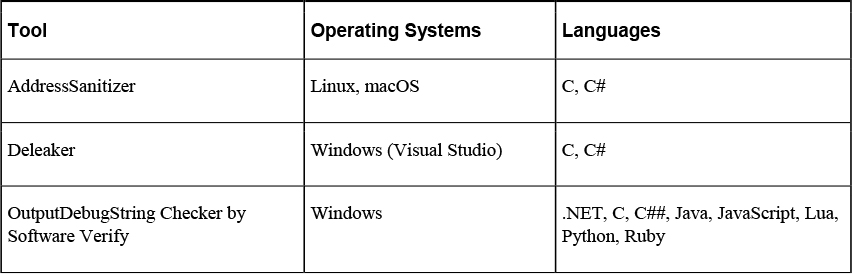
Runtime debugging, on the other hand, is the process of using a programming tool to not only identify syntactic problems in code but also discover weaknesses that can lead to memory leaks and buffer overflows. Runtime debugging tools operate by examining and monitoring the use of memory. These tools are specific to the language in which the code was written. Table 18-2 shows examples of runtime debugging tools and the operating systems and languages for which they can be used.
Table 18-2 Runtime Debugging Tools
Memory dumping can help determine what a hacker might be able to learn if she were able to cause a memory dump. Runtime debugging would be the correct approach for discovering syntactic problems in an application’s code or to identify other issues, such as memory leaks or potential buffer overflows.
Mobile
As the use of mobile devices has increased, so has the involvement of these devices in security incidents. The following tools, among others, have been created to help obtain evidence from mobile devices:
• Cellebrite: Cellebrite has found a niche by focusing on collecting evidence from smartphones. It makes extraction devices that can be used in the field and software that does the same things. These extraction devices collect metadata from memory and attempt to access the file system by bypassing the lock mechanism. They don’t modify any of the data on the devices, which makes this a forensically “clean” solution. The device looks like a tablet, and you simply connect a phone to it via USB. For more information, see https://www.cellebrite.com.
• Susteen Secure View 4: This mobile forensic tool is used by many police departments. It enables users to fully export and report on all information found on the mobile device. It can create evidence reports based only on the information that you find is relevant to your case. This includes deleted data, all files (pictures, videos, documents, etc.), messages, and more. See https://www.secureview/secure_view.html for details.
• MSAB XRY: This digital forensics and mobile device forensics product by the Swedish company MSAB is used to analyze and recover information from mobile devices such as mobile phones, smartphones, GPS navigation tools, and tablet computers. Check out XRY at https://www.msab.com/products/xry/.
Cloud
In Chapter 4, “Analyzing Assessment Output,” you learned about some cloud tools for vulnerability assessments, and in Chapter 8, “Security Solutions for Infrastructure Management,” you learned about cloud anti-malware systems. Let’s look a bit more at cloud vulnerability scanning.
Cloud-based vulnerability scanning is a service performed from the vendor’s cloud and is a good example of Software as a Service (SaaS). The benefits here are the same as the benefits derived from any SaaS offering—that is, no equipment on the part of the subscriber and no footprint in the local network. Figure 18-5 shows a premises-based approach to vulnerability scanning, and Figure 18-6 shows a cloud-based solution. In the premises-based approach, the hardware and/or software vulnerability scanners and associated components are entirely installed on the client premises, while in the cloud-based approach, the vulnerability management platform is in the cloud. Vulnerability scanners for external vulnerability assessments are located at the solution provider’s site, with additional scanners on the premises.

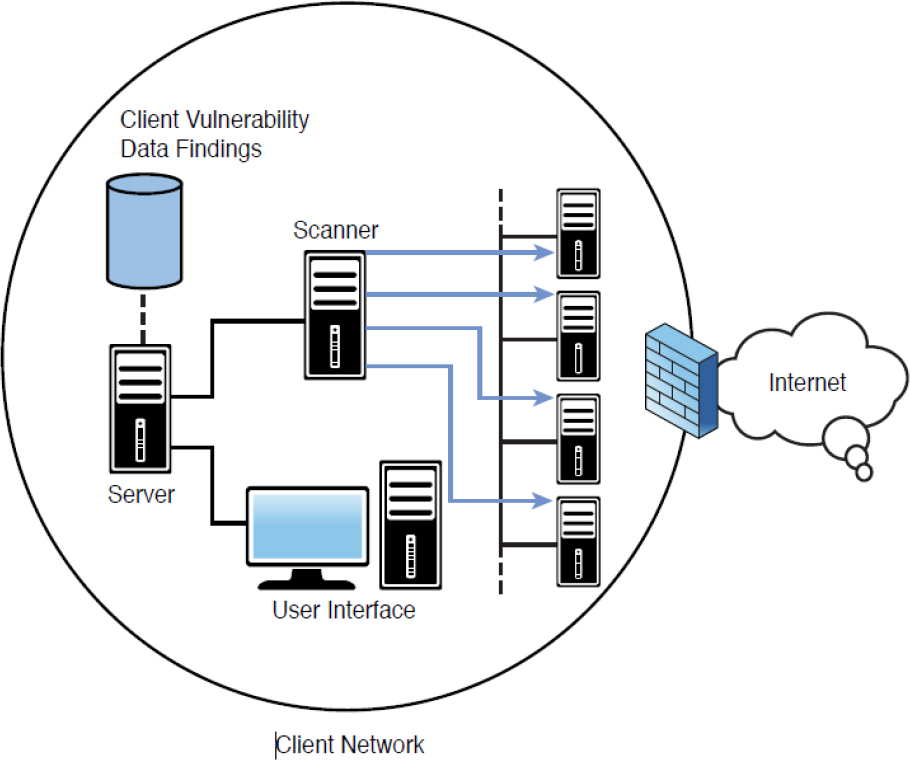
Figure 18-5 Premises-Based Scanning

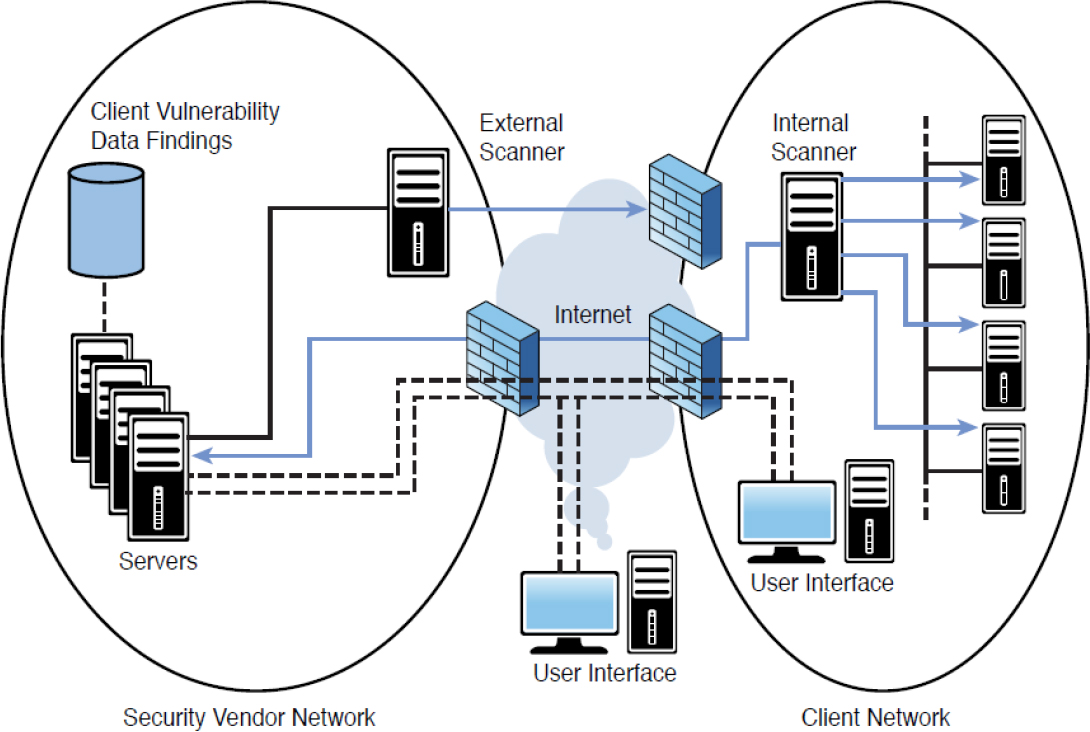
Figure 18-6 Cloud-Based Scanning

The following are the advantages of the cloud-based approach:
• Installation costs are low because there is no installation and configuration for the client to complete.
• Maintenance costs are low because there is only one centralized component to maintain, and it is maintained by the vendor (not the end client).
• Upgrades are included in a subscription.
• Costs are distributed among all customers.
• It does not require the client to provide onsite equipment.
However, there is a considerable disadvantage to the cloud-based approach: Whereas premises-based deployments store data findings at the organization’s site, in a cloud-based deployment, the data is resident with the provider. This means the customer is dependent on the provider to ensure the security of the vulnerability data.
Qualys is an example of a cloud-based vulnerability scanner. Sensors are placed throughout the network, and they upload data to the cloud for analysis. Sensors can be implemented as dedicated appliances or as software instances on a host. A third option is to deploy sensors as images on virtual machines.
Virtualization
In Chapter 8, you learned the basics of virtualization and how this technology is used in the cloud environment. With respect to forensic tools for the virtual environment, the same tools can be used as in a physical environment. However, the key is knowledge of the files that make up a VM and how to locate these files. Each virtualization system has its own filenames and architecture. Each VM is made up of several files.
Another key aspect of successful forensics in the virtual environment is deep knowledge of the log files created by the various components such as the hypervisor and the guest machine. You need to know not only where these files are located but also the purpose of each and how to read and interpret its entries.
Legal Hold
Legal holds are requirements placed on organizations by legal authorities that require the organization to maintain archived data for longer periods. Data on a legal hold must be properly identified, and the appropriate security controls must be put into place to ensure that the data cannot be tampered with or deleted. An organization should have policies regarding any legal holds that may be in place.
Consider the following scenario: An administrator receives a notification from the legal department that an investigation is being performed on members of the research department, and the legal department has advised a legal hold on all documents for an unspecified period of time. Most likely this legal hold will violate the organization’s data storage policy and data retention policy. If a situation like this arises, the IT staff should take time to document the decision and ensure that the appropriate steps are taken to ensure that the data is retained and stored for a longer period, if needed.
Procedures
In Chapter 16, “Applying the Appropriate Incident Response Procedure,” you learned about the incident response process and its steps. Review those steps as they are important. This section introduces some case management tools that can make the process go smoother.
EnCase Forensic
EnCase Forensic is a case (incident) management tool that offers built-in templates for specific types of investigations. These templates are based on workflows, which are the steps to carry out based on the investigation type. A workflow leads you through the steps of triage, collection, decryption, processing, investigation, and reporting of an incident. For more information, see https://www.guidancesoftware.com/encase-forensic.
Sysinternals
Sysinternals is a Windows command-line tool that contains more than 70 tools that can be used for both troubleshooting and security issues. Among these are forensic tools. For more information, see https://technet.microsoft.com/en-us/sysinternals/.
Forensic Investigation Suite
A forensic investigation suite is a collection of tools that are commonly used in digital forensic investigations. A quality forensic investigation suite should include the following items:

• Imaging utilities: One of the tasks you will be performing is making copies of storage devices. For this you need a disk imaging tool. To make system images, you need to use a tool that creates a bit-level copy of the system. In most cases, you must isolate the system and remove it from production to create this bit-level copy. You should ensure that two copies of the image are retained. One copy of the image will be stored to ensure that an undamaged, accurate copy is available as evidence. The other copy will be used during the examination and analysis steps. Message digests (or hashing digests) should be used to ensure data integrity.
• Analysis utilities: You need a tool to analyze the bit-level copy of the system that is created by the imaging utility. Many of these tools are available on the market. Often these tools are included in forensic investigation suites and toolkits, such as the previously introduced EnCase Forensic, FTK, and Helix.
• Chain of custody: While hard copies of chain of custody activities should be kept, some forensic investigation suites contain software to help manage this process. These tools can help you maintain an accurate and legal chain of custody for all evidence, with or without hard copy (paper) backup. Some suites perform a dual electronic signature capture that places both signatures in an Excel spreadsheet as proof of transfer. Those signatures are doubly encrypted so that if the spreadsheet is altered in any way, the signatures disappear.
• Hashing utilities: These utilities are covered in the next section.
• OS and process analysis: These tools focus on the activities of the operating system and the processes that have been executed. While most operating systems have tools of some sort that can report on processes, tools included in a forensic investigation suite have more robust features and capabilities.
• Mobile device forensics: Today, many incidents involve mobile devices. You need different tools to acquire the required information from these devices. A forensic investigation suite should contain tools for this purpose. See the earlier “Mobile” section for examples.
• Password crackers: Many times investigators find passwords standing in the way of obtaining evidence. Password cracking utilities are required in such instances. Most forensic investigation suites include several password cracking utilities for this purpose. Chapter 4, “Analyzing Assessment Output” lists some of these tools.
• Cryptography tools: An investigator uses these tools when they encounter encrypted evidence, which is becoming more common. Some of these tools can attempt to decrypt the most common types of encryption (for example, BitLocker, BitLocker To Go, PGP, TrueCrypt), and they may also be able to locate decryption keys from RAM dumps and hibernation files.
• Log viewers: Finally, because much evidence can be found in the logs located on the device, a robust log reading utility is also valuable. A log viewer should have the ability to read all Windows logs as well as the registry. Moreover, it should also be able to read logs created by other operating systems. See the “Log Review” section of Chapter 11, “Analyzing Data as Part of Security Monitoring Activities.”
Hashing
A hash function takes a message of variable length and produces a fixed-length hash value. Hash values, also referred to as message digests, are calculated using the original message. If the receiver calculates a hash value that is the same, the original message is intact. If the receiver calculates a hash value that is different, then the original message has been altered. Hashing was covered in Chapter 8.
Hashing Utilities
You must be able to prove that certain evidence has not been altered during your possession of it. Hashing utilities use hashing algorithms to create a value that can be used later to verify that the information is unchanged. The two most common algorithms used are Message Digest 5 (MD5) and Secure Hashing Algorithm (SHA).
Changes to Binaries
A binary file is a computer file that is not a text file. The term “binary file” is often used as a term meaning “non-text file.” These files must be interpreted to be read. Executable files are often of this type. These file types can be verified using hashing in the same manner as described in the prior section.

Carving
Data carving is a technique used when only fragments of data are available and when no file system metadata is available. It is a common procedure when performing data recovery, after a storage device failure, for instance. It is also used in forensics.
A file signature is a constant numerical or text value used to identify a file format. The object of carving is to identify the file based on this signature information alone.
Forensic Explorer is a tool for the analysis of electronic evidence and incudes a data carving tool that searches for signatures. It offers carving support for more than 300 file types. It supports
• Cluster-based file carving
• Sector-based file carving
• Byte-based file carving
Figure 18-7 shows the File Carving dialog box in Forensic Explorer.
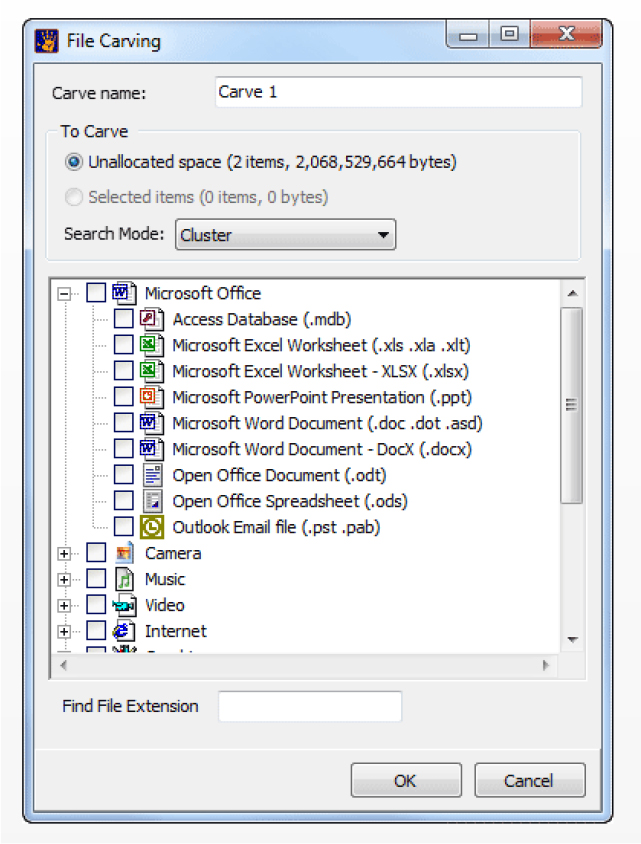
Figure 18-7 Forensic Explorer
Data Acquisition
Earlier in this chapter, in the section “Forensic Investigation Suite,” you learned about data acquisition tools that should be a part of your forensic toolkit. Please review that section and the balance of this chapter with regard to forensic tools.
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have several choices for exam preparation: the exercises here, Chapter 22, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep Software Online.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 18-3 lists a reference of these key topics and the page numbers on which each is found.

Table 18-3 Key Topics in Chapter 18
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
Review Questions
1. ___________________ is a command-line tool that can capture packets on Linux and Unix platforms.
2. List at least one password cracking utility.
3. Match the following terms with their definitions.
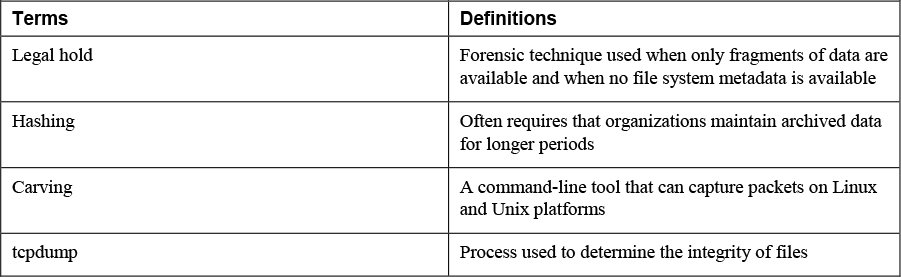
4. The DoD created a fork (a variation) of the dd command called ___________ that adds additional forensic functionality.
5. List at least two memory-reading tools.
6. Match the following terms with their definitions.
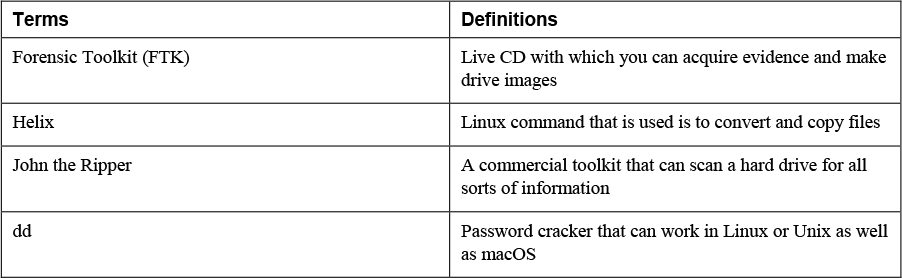
7. Cellebrite found a niche by focusing on collecting evidence from ______________.
8. List at least two advantages of the cloud-based approach to vulnerability scanning.
9. Match the following terms with their definitions.
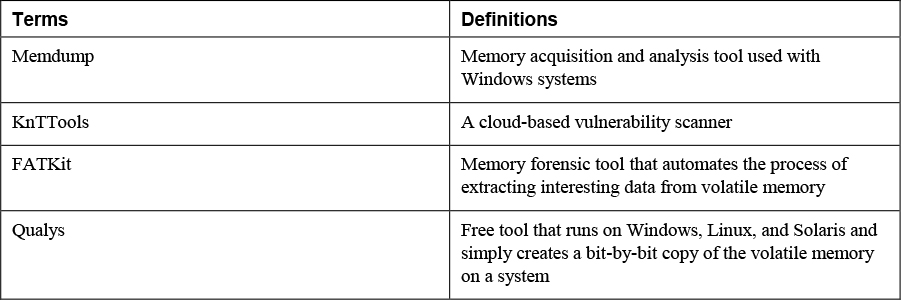
10. _____________ often require that organizations maintain archived data for longer periods.
