Chapter Fifteen
Security Technologies and Malicious Software
Introduction
Keeping a network secure is not always an easy task for administrators. When securing a network, administrators must considered certain areas. Chapter 14, “Network Access Security,” reviewed network security concepts such as access control lists, firewalls, and security protocols. This chapter continues the discussion of network security, focusing on security elements such as authentication methods and protocols, physical and logical security, secure protocols, and one security concept that is always a threat, malware.
We start this chapter with a review of the relationship between three security concepts: authentication, authorization, and accountability.
Authentication, Authorization, and Accountability (AAA)
Before it is possible to establish strong network security, it is essential to understand some of the key security concepts. This includes authentication, authorization, and accountability (AAA). AAA defines a spectrum of security measures, policies, and procedures that are combined to create a secure network.
Authentication
Authentication refers to the mechanisms used to verify the identity of the computer or user attempting to access a particular resource. Several forms of authentication are used on today’s networks. A password username combination is typically the most common form of authentication. Other types of authentication include
• Smart cards
• Biometrics (fingerprints, retina scan)
• Voice recognition
Authentication is a significant consideration for network and system security, and maintaining strong authentication is a primary concern for network administrators.
Although biometrics and smartcards are becoming more common, they still have a very long way to go before they attain the level of popularity that username and password combinations enjoy. Apart from the fact that usernames and passwords do not require any additional equipment, which practically every other method of authentication does, the username and password process is familiar to users, easy to implement, and relatively secure. For that reason, they are worthy of more detailed coverage than the other authentication systems previously listed.
Exam Alert
Accessing the network For the Network+ exam, remember that in a Windows environment, two pieces of information are required to access the network: a valid username and a valid password. Both are required to gain access.
Password Policies
Passwords are a relatively simple form of authentication in that only a string of characters can be used to authenticate the user. However, how the string of characters is used and which policies you can put in place to govern them make usernames and passwords an excellent form of authentication.
All popular network operating systems include password policy systems that allow the network administrator to control how passwords are used on the system. The exact capabilities vary between network operating systems. However, generally they allow the following:
• Minimum length of password—Shorter passwords are easier to guess than longer ones. Setting a minimum password length does not prevent a user from creating a longer password than the minimum, although each network operating system has a limit on how long a password can be.
• Password expiration—Also known as the maximum password age, password expiration defines how long the user can use the same password before having to change it. A general practice is that a password is changed every month or every 30 days. In high-security environments, you might want to make this value shorter, but you should generally not make it any longer. Having passwords expire periodically is an important feature because it means that if a password is compromised, the unauthorized user will not have access indefinitely.
• Prevention of password reuse—Although a system might be able to cause a password to expire and prompt the user to change it, many users are tempted to simply use the same password again. A process by which the system remembers the last 10 passwords, for instance, is most secure because it forces the user to create completely new passwords. This feature is sometimes called enforcing password history.
• Password complexity—Some systems have the capability to evaluate the password provided by a user to determine whether it meets a required level of complexity. This prevents users from having passwords such as password or 12345678.
Exam Alert
Password policy On the Network+ exam, you may need to identify an effective password policy. For example, a robust password policy would include forcing users to change their passwords on a regular basis.
Password Strength
No matter how good a company’s password policy, it is only as effective as the passwords that are created within it. A password that is hard to guess, or strong, is more likely to protect the data on a system than one that is easy to guess, or weak.
To understand the difference between a strong password and a weak one, consider this: A password of six characters that uses only numbers and letters and is not case sensitive has over 2 billion possible combinations. That might seem like a lot, but to a password-cracking program, it’s really not much security. A password that uses eight case-sensitive characters, with letters, numbers, and special characters has so many possible combinations that a standard calculator is not capable of displaying the actual number.
There has always been debate over how long a password should be. It should be sufficiently long that it is hard to break but sufficiently short that the user is able to easily remember it (and type it). In a normal working environment, passwords of 8 characters are sufficient. Certainly, they should be no fewer than 6 characters. In environments where security is a concern, passwords should be 12 characters or more.
Tip
Password testing Want to see how strong your passwords are? Microsoft has a password checker available at http://www.microsoft.com/protect/yourself/password/checker.mspx.
Users should be encouraged to use a password that is considered strong. A strong password has at least eight characters; has a combination of letters, numbers, and special characters; uses mixed case; and does not form a proper word. Examples might include 3E$cc5T0h and e1oXPn$3r. Such passwords might be secure, but users are likely to have problems remembering them. For that reason, a popular strategy is to use a combination of letters and numbers to form phrases or long words. Examples include d1eTc0La and tAb1eT0p. These passwords might not be quite as secure as the preceding examples, but they are still very strong and a whole lot better than the name of the user’s household pet.
Multifactor Authentication
In many environments a username and password combination is an adequate level of authentication security. However, traditional passwords have well-documented problems. Users forget passwords, choose passwords that are easy to guess, and reuse the same password over and over.
Because of such issues, organizations are looking at other more convenient and secure forms of authentication. Airports, banks, government agencies, and many high-profile companies are spending large amounts of time and resources to create more secure environments. An integral part of this effort is the authentication strategy.
Three strategies that may be used to tighten authentication security are tokens, biometrics, and multifactor authentication schemes.
Authentication Tokens
Authentication tokens typically refer to physical hardware devices carried by users for authentication. For example, workers in airports, hospitals, or other organizations may wear cards on neck chains or on belt loops. These tokens are used to authenticate with a computer terminal.
Such tokens can take the form of smart cards or embedded in a commonly used object such as a USB key device. Security tokens provide an extra level of assurance through a method known as two-factor authentication: the user has a personal identification number (PIN), which authorizes them as the owner of that particular device; the device then displays a number that uniquely identifies the user to the service, allowing the user to log in.
Exam Alert
Two-factor authentication Two-factor authentication refers to strategies that combine authentication types. Typically two-factor authentication refers to combining something you know (a password) with something you have (a token).
Biometrics
Biometric systems work by utilizing some unique characteristic of a person’s identity—such as a fingerprint, a palm print, voice recognition, or even a retina scan—to validate that person’s identity.
Exam Alert
Biometrics For the Network+ exam, remember that biometric authentication has a distinct advantage over swipe card and PIN access. Swipe cards can be loaned to people, and PINs can be discovered, but unique physical characteristics cannot be duplicated.
The price of biometric systems has been decreasing in recent years and is now in the budget for most organizations. Because each person attempting to authenticate must supply proof-of-person evidence, verification of the person is very reliable. Also, because there are no cards or keys, there is nothing that can be lost.
Multifactor Authentication/Two-Factor Authentication
To authenticate a user, there are three primary categories of authentication:
• Something the user knows (passwords, PIN numbers)
• Something the user has (tokens, smart cards, USB key devices)
• Characteristics of a user (fingerprints, retinal scans, voice recognition)
Each of these approaches provides some level of authentication security. Multifactor authentication involves the combination of two of these authentication categories. This approach can be difficult and costly to implement and is often restricted to environments that require the highest level of authentication security.
Multifactor authentication is also known as two-factor authentication previously discussed in the token section.
Although multifactor authentication provides an increased level of security, users like the convenience of reusable passwords and do not like the inconvenience of carrying an object around just to log in to a computer system. Aside from user resistance, the added expense of cards, tokens, and readers coupled with the logistics of distribution makes it difficult to justify moving away from a traditional password-based system. The question is whether and when security is preferable to convenience.
Authorization
Authorization is the method used to determine whether an authenticated user has access to a particular resource. This is commonly determined through group association; that is, a particular group may have a specific level of security clearance.
Figure 15.1 shows an example of authentication and authorization. Marge is authenticated to the network but is not authorized to use the backup server or the scanner. She is, however, authorized to use other network resources after she has been authenticated.
Figure 15.1 The relationship between authentication and authorization.
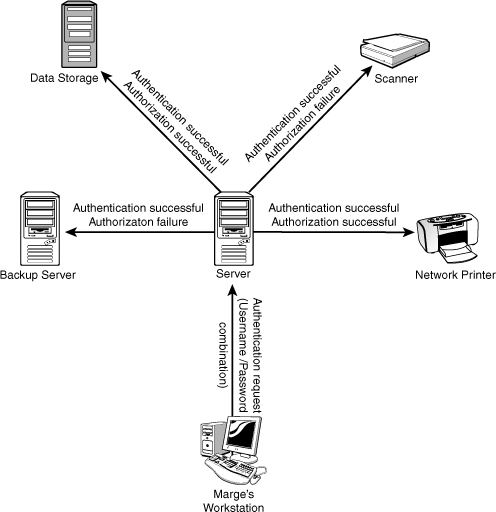
A bank transaction at an ATM is another good example of authentication and authorization. When a bank card is placed in the ATM, the magnetic strip is read, making it apparent that someone is trying to access a particular account. If the process ended there and access was granted, it would be a significant security problem because anyone holding the card could gain immediate access. To authenticate the client, after the card is placed in the bank machine, a secret code or PIN is required. This authentication ensures that the PIN number and card match.
With the correct code, the client is verified and authenticated, and access is granted. Authorization addresses the specifics of which accounts or features the user is allowed to access once authenticated, such as a checking or savings account.
Accountability
Accountability refers to the tracking mechanisms used to keep a record of events on a system. One tool often used for this purpose is known as auditing. Auditing refers to the process of monitoring events on a system and keeping a log of what has occurred. A system administrator determines the events that should be audited. Tracking events and attempts to access the system helps prevent unauthorized access and provides a record that administrators can analyze to make security changes as necessary. It also provides administrators with solid evidence for looking into improper user conduct.
The first step in auditing is to identify what system events to monitor. After the system events are identified, in a Windows environment, the administrator can choose to monitor the success or failure of a system event. For instance, if “logon” is the event being audited, the administrator may choose to log all unsuccessful logon attempts, which may indicate that someone is attempting to gain unauthorized access. Conversely, the administrator can choose to audit all successful attempts to monitor who and when a particular user or user groups are logging on. Some administrators prefer to log both events. However, overly ambitious audit policies can reduce overall system performance. In general, the common types of events that are monitored include the following:
• Access to objects, such as files and folders.
• Management of user accounts and group accounts.
• Users logging on to and logging off from the system.
Auditing is an important part of system security and a large part of accountability. It provides a means to track events that occur on a system.
A network administrator might need to audit many events on a system, such as failed/successful logons, printer access, file and directory access, and remote access. Reviewing the log files generated by auditing allows an administrator to better gauge the potential threats to the network.
RADIUS and TACACS+
RADIUS and TACACS+ are designed to provide for AAA service. RADIUS and TACACS+ are protocols that enable a single server to become responsible for all remote access authentication, authorization, and auditing (or accounting) services. Although they both provide a function, they do so in a slightly different fashion. This section discusses both protocols and how they are used.
RADIUS
Among the potential issues network administrators face when implementing remote access are utilization and the load on the remote access server. As a network’s remote access implementation grows, reliance on a single remote access server might be impossible, and additional servers might be required. RADIUS can help in this scenario.
RADIUS functions as a client/server system. The remote user dials in to the remote access server, which acts as a RADIUS client, or network access server (NAS), and connects to a RADIUS server. The RADIUS server performs authentication, authorization, and auditing (or accounting) functions and returns the information to the RADIUS client (which is a remote access server running RADIUS client software); the connection is either established or rejected based on the information received.
When RADIUS is being used, a client system sends a request to a NAS to gain access to a network or network resource. A NAS can be a wireless access point, VPN server, or even a 802.1x switch. A NAS acts as a gateway between the network and the RAIDUS server. The following outlines the steps in RADIUS authentication:
1. The client system sends its credentials and access request to the NAS system. For instance, attempting to log on to the wireless access point.
2. The NAS forwards this access request message to the RADIUS server. The request message is accompanied with the client credentials (typically username and password combination).
3. The RADIUS server looks over the client request and verifies the credentials using authentication protocols such as PAP, CHAP and EAP (discussed later in this chapter in the section “Remote Authentication Protocols”).
4. Reviewing the user’s credentials, RADIUS performs one of the following actions:
• Deny the request—If the user’s credentials cannot be authorized, the request for access will be denied.
• Seek more information—The RADIUS server may request additional information, such as a secondary password or some other means to verify the user’s authentication credentials.
• Accept the client request—The client system is granted access. The next step is authorization.
Figure 15.2 shows a RADIUS server in action.
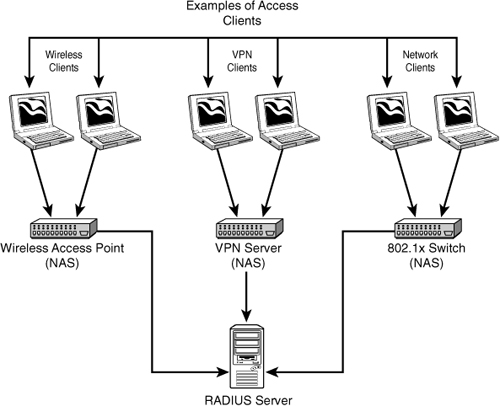
With the authentication complete and accepted, the process of authorization and accounting begins. As previously mentioned, authorization refers to the process of granting or denying client access to network resources after authentication. The type and availability of various network resources depends on the user’s authorization level.
Exam Alert
RADIUS authorization Remember for the Network+ exam that the function of authorization is to establish what a user may do on the network after authentication has been completed.
TACACS+
Terminal Access Controller Access Control System+ (TACACS+) is a security protocol designed to provide centralized validation of users who are attempting to gain access to a router or NAS. Like RADIUS, TACACS+ is a set of security protocols designed to provide authentication, authorization, and accounting (AAA) of remote users. TACACS uses TCP port 49 by default.
Although both RADIUS and TACACS+ offer AAA services for remote users, some noticeable differences exist:
• TACACS+ relies on TCP for connection-oriented delivery, whereas RADIUS uses connectionless UDP for data delivery.
• RADIUS combines authentication and authorization, whereas TACACS+ can separate their functions.
Exam Alert
RADIUS versus TACACS+ For the Network+ exam, remember that TACACS+ relies on the connection-oriented TCP protocol, whereas RADIUS uses the connectionless UDP protocol.
Understanding Cryptography Keys
Before we can continue a discussion of authentication protocols in the following sections, it is important to first understand how cryptography keys work. Cryptography is used to ensure that a client can prove its identity to a server (and vice versa) across an insecure network connection. The term key is used for very good reason—public and private keys are used to lock (encrypt) and unlock (decrypt) data. These keys are actually long numbers, making it next to impossible for someone to access a particular key. When keys are used to secure data transmissions, the computer generates two types of keys: a public key and a private key. The distinction between the two is as follows:
• Public key—A nonsecret key that forms half of a cryptographic key pair that is used with a public key algorithm. The public key is freely given out to all potential receivers.
• Private key—The secret half of a cryptographic key pair that is used with a public key algorithm. The private part of the public key cryptography system is never transmitted over a network.
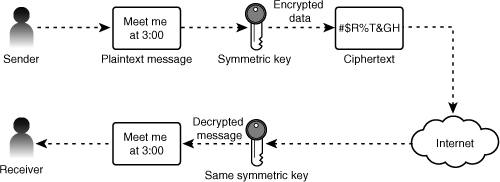
Keys can be used in two ways to secure data communications: public key encryption (asymmetric) and private (symmetric) key encryption. Private (symmetric) key encryption uses a single key for both encryption and decryption. If a person possesses the key, he or she can both encrypt and decrypt messages. Unlike public keys, this single secret key cannot be shared with anyone except people who should be permitted to decrypt and encrypt messages.
In secret key cryptography, a plain-text message can be converted into ciphertext (encrypted data) and then converted back to plain text using one key. Thus, two devices share a secret key to encrypt and decrypt their communications. Figure 15.3 shows the symmetric key process.
Figure 15.3 Symmetric key process.
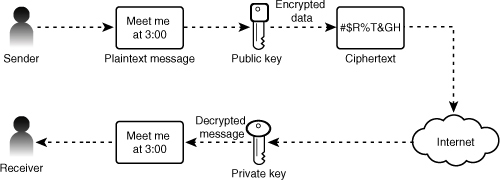
Public (asymmetric) key encryption uses both a private and public key to encrypt and decrypt messages. The public key is used to encrypt a message or verify a signature, and the private key is used to decrypt the message or sign a document. Figure 15.4 shows a public (asymmetric) key encryption.
Figure 15.4 Public (asymmetric) key encryption.
With an understanding of cryptography keys, we can now look at some of the technologies that use them. First up is the Kerberos protocol.
Kerberos Authentication
Kerberos is an authentication protocol that provides authentication, which is an integral part of network security. Networks, including the Internet, are able to connect people from all over the world. When data travels from one point to another across a network, it can be lost, stolen, corrupted, or misused. Much of the data sent over networks is sensitive, whether it is medical data, financial, or otherwise, and a key consideration for those responsible for the network is maintaining the confidentiality of the data. In the networking world, Kerberos plays a significant role in data confidentiality.
In a traditional authentication strategy, a username and password is used to access network resources. In a secure environment, it may be necessary to provide a username and password combination to access each network service or resource. For example, a user may be prompted to type in her username and password when accessing a database, and again for the printer and again for Internet access. This is a very time-consuming process, and it can also present a security risk. Each time the password is typed in, there is a chance it can be seen when being typed or, if sent over the network without encryption, it may be viewed by malicious eavesdroppers.
Kerberos was designed to fix such problems by using a method requiring only a single sign-on. This single sign-on allows a user to log in to a system and access multiple systems or resources without the need to reenter the username and password repeatedly. Additionally, Kerberos is designed to have entities authenticate themselves by demonstrating possession of secret information.
Kerberos is one part of a strategic security solution that provides secure authentication services to users, applications, and network devices, by eliminating the insecurities caused by passwords being stored or transmitted across the network. Kerberos is used primarily to eliminate the possibility of a network “eavesdropper” from tapping into data over the network, and particularly usernames and passwords. Kerberos ensures data integrity and blocks tampering on the network. It employs message privacy (encryption) to ensure messages are not visible to eavesdroppers on the network.
For the network user, Kerberos eliminates the need to repeatedly demonstrate possession of private or secret information.
Exam Alert
Kerberos authentication For the Network+ exam, remember that Kerberos is a non-proprietary protocol and is used for cross-platform authentication.
Kerberos is designed to provide strong authentication for client/server applications by using secret-key cryptography. After a client and server have used Kerberos to prove their identity, they can also encrypt all their communications to ensure privacy and data integrity.
Exam Alert
Kerberos security Remember for the exam, Kerberos allows secure authentication over an insecure network such as the Internet.
The key to understanding Kerberos is to understand the secret key cryptography it uses. Kerberos uses symmetric key cryptography, which was discussed in the previous section. Refer to Figure 15.3 to see how the symmetric key cryptography works.
Exam Alert
Kerberos keys For the Network+ exam, remember that Kerberos uses a symmetric key cryptography method.
Kerberos authentication works by assigning a unique key (called a ticket), to each client that successfully authenticates to a server. The ticket is encrypted and contains the password of the user, which is used to verify the user’s identity when a particular network service is requested. Kerberos works in the same way that you go to a ballgame or a movie. First, you go to a ticket counter, tell the person what game you want to see, and get your ticket. After that, you go to a turnstile and hand the ticket to someone else, and then you’re “in.” In very simplistic terms, that’s Kerberos.
Exam Alert
Tickets For the Network+ exam, you should know that the security tokens used in Kerberos are known as tickets.
Public Key Infrastructure
A public key infrastructure (PKI) is a collection of software, standards, and policies that are combined to allow users from the Internet, or other unsecured public networks, to securely exchange data. PKI is used in a variety of environments and for a range of purposes, including the following:
• Web security—As we all know, the Internet is an unsecured network. PKI increases web security by offering server authentication that enables client systems to validate that the server they are communicating with is indeed the intended server. Without this information, it is possible for people to place themselves between the client and the server and intercept client data by pretending to be the server. PKI also offers client authentication, which validates the client’s identity.
• Confidentiality—PKI provides secure data transmissions using encryption strategies between the client and the server. In application, PKI works with the Secure Sockets Layer (SSL) protocol and the Transport Layer Security (TLS) protocol to provide secure HTTP transfers, referred to as Hypertext Transport Protocol Secure (HTTPS) protocol. To take advantage of the SSL and TLS protocols, both the client system and the server require certificates issued by a mutually trusted certificate authority (CA).
• Digital signatures—Digital signatures are the electronic equivalent of a sealed envelope and are intended to ensure that a file has not been altered in transit. Any file with a digital signature is used to verify not only the publishers of the content or file, but also to verify the content integrity at the time of download. On the network, PKI allows you to issue certificates to internal developers/contractors and allows any employee to verify the origin and integrity of downloaded applications.
• Secure email—Today’s organizations rely heavily on email to provide external and internal communications. Some of the information sent via email is not sensitive and does not need security, but for those communications that contain sensitive data, a method is needed to secure email content. PKI can be deployed as a method for securing email transactions. In application, a private key is used to digitally sign outgoing emails and the sender’s certificate is sent with the email so the recipient of the email can verify the sender’s signature.
The following sections review the important components of the PKI and how they are combined to provide the services discussed previously.
Components of a PKI
There are services and components working together to develop the PKI. Some of the key components of a PKI include the following:
• Certificates—A form of electronic credentials that validates users, computers or devices on the network. A certificate is a digitally signed statement that associates the credentials of a public key to the identity of the person, device, or service that holds the corresponding private key.
• Certificate authorities (CAs)—Entities that validate the identity of a network device or user requesting data. CAs issue and manage certificates. CAs can be either independent third parties, known as a public CA, or they can be organizations running their own certificate-issuing server software, known as private CAs.
• Certificate templates—Templates used to customize certificates issued by a certificate server. This customization includes a set of rules and settings created on the CA and used for incoming certificate requests.
• Certification Revocation List (CRL)—A list of certificates that have been revoked before they have reached the certificate expiration date. Certificates are often revoked because of security concerns, such as a compromised certificate.
Exam Alert
PKI keys PKI uses a public key cryptography method. In public key cryptography, both a private and a public key encrypt and decrypt messages.
Certificates
Certificates are the cornerstones of PKI. A certificate is essentially a form of electronic credentials that validates users, computers, or devices on the network. A certificate is a digitally signed statement that associates the credentials of a public key to the identity of the person, device, or service that holds the corresponding private key. Certificates can provide a number of security services, including the following:
• Authentication—An important part of a security strategy. For authentication to happen, users are required to prove their identity to the network device or server to which they are trying to communicate. Certificates provide the means to ensure that this communication is secure and that the parties involved in the communication are who they say they are.
• Encryption—The process of converting something that is in a plain-text form into an unreadable form. This prevents unwanted eyes from viewing potentially sensitive data. Decryption is the process of taking the unreadable data and converting it to something that can be read. This can be thought of as locking something valuable into a strong box with a key. Using certificates, we have the ability to protect email messages, files on a disk, and files being transmitted across the network.
• Digital signature—A way to ensure the integrity and origin of data. Integrity involves ensuring that the data being received has not been altered since it was signed. Digital signatures also provide a method of verifying the identity of the person or entity who signed the data. This enables the important security features of integrity and nonrepudiation, which are essential for secure electronic commerce transactions.
Discussions of certificates can be quite involved. The following section highlights some of the key concepts surrounding certificates, including certificate stores, trusts, and certificate authorities.
Exam Alert
Certificates For the Network+ exam remember that a certificate is a form of electronic credentials that validates users, computers, or devices on the network.
Certificate Stores
Certificate stores are essentially a container for certificates and their associated properties. PKI uses five types of certificates stores:
• Personal—Stores a user’s or a computer’s certificates for which the related private key is available.
• CA stores—The issuing and intermediate CA certificates to use in the CA hierarchy.
• Enterprise trust—Contains certificate trust lists. These are an alternative mechanism that allows an administrator to specify a collection of trusted CAs that must verify to a self-signed CA certificate in the trusted root store.
• Trusted root—Contains only self-signed CA certificates that are trust points in the PKI.
• UserDS—Stores a logical view of the certificate container that is located in the Active Directory and is used to simplify access to certificate stores.
Trusts
The issue of trust is an important consideration when looking at PKI. For instance, in a private key encryption method, the two parties exchanging data trust their shared private key. It is assumed that the private key is stored securely, and therefore, message integrity exists between the sender and receiver. The trust is built on the security of the private key.
A trust built in a public key encryption method is another story altogether. Both parties each secure their own private key, and at the same time, they have to share each other’s public key. This means that when we receive a digitally signed message, we need to be able to trust that the digital signature is from whoever claimed to make it. Trusting this public key is a critical consideration for the public key infrastructure to work. The problem is, how can a public key be implicitly trusted?
There are two steps in forming this trust. The first is confirming the validity of the signature using the known public key. Using this key, it is possible to determine the integrity of the signature and ensure that the signature is mathematically valid. The problem is, even if you know the signature is mathematically valid, how do you know you used the right public key? That is, is it the public key from the other end of the communication that made the signature in the first place? It may not be.
To complete the trust in a public key encryption, it is necessary to locate a certificate for the public key that can verify that the key belongs to the right entity. To do this, the certificate must be issued by a CA)that is implicitly trusted by the receiver. If the receiver trusts a particular CA, all certificates issued by that CA are, in turn, trusted.
After a certificate has verified the public key by a trusted CA, the signature is trusted.
Certificate Authorities (CAs)
CAs are entities that validate user identities and that issue and manage certificates. As outlined previously, the CA provides security certificates that ensure that people are who they say they are. CAs can be either independent third parties, known as a public CA, or they can be organizations running their own certificate-issuing server software, known as private CAs.
Public CAs
Public CAs are organizations such as Verisign or Entrust, which issue publicly accessible certificates. On the Internet, many of the e-commerce sites use these types of third-party CAs for their secured websites. Such a strategy is designed to increase consumer confidence in ensuring that the communication is secure. Public CAs are often used in the following circumstances:
• If you are buying or selling products over the Internet, you can use third-party certificates to verify the transaction.
• If the resources or trained personnel are not available to deploy a PKI strategy into an internal network, a public CA can be used.
• If certification use is limited, public CAs have the infrastructure in place to accommodate limited use.
• Third-party CAs can be used for interorganization communication because the certificates are acquired from a common third-party root authority.
Private CAs
Public CAs have found considerable success when conducting transactions over the Internet; however, some organizations choose to create and manage an internal CA. Although it may take more effort to create an internal CA, it also provides an organization with control over all client-issued certificates and as a side benefit, decreases the cost of obtaining certificates from third-party CAs. Private CAs are often deployed under the following conditions:
• An organization requires increased control over client-issued certificates.
• Current infrastructure and expertise are in place to support the PKI.
• An organization wants to reduce the costs associated with obtaining third-party certificates.
Network Access Control
When we talk about network access control, we are talking about the mechanisms used to filter network traffic to determine who is and who is not allowed to access the network and network resources. Firewalls, proxy servers, routers, and individual computers all have the capability to maintain access control to some degree. By limiting who can and cannot access the network and its resources, it is easy to understand why access control plays an important role in security strategy. There are a few types of access control:
• Mandatory Access Control (MAC)
• Discretionary Access Control (DAC)
• Rule-Based Access Control (RBAC)
• Role-Based Access Control (RBAC)
The following sections describe each of these access control types.
Mandatory Access Control (MAC)
MAC is the most secure form of access control. In systems configured to use MAC, administrators dictate who can access and modify data, systems, and resources. MAC systems are commonly used in military installations, financial institutions, and because of new privacy laws, medical institutions.
Note
MAC x 2 With so many acronyms in the IT world, it only makes sense that some of them would overlap. MAC can refer to either the media access control, which is a hexadecimal address that uniquely identifies network cards, and mandatory access control. Both may be referenced on the exam; however, the tests makes clear which one is referred to.
MAC secures information and resources by assigning sensitivity labels to objects and users. When a user requests access to an object, his sensitivity level is compared to the objects. A label is a feature that is applied to files, directories, and other resources in the system. It is similar to a confidentiality stamp. When a label is placed on a file, it describes the level of security for that specific file and will permit access only by files, users, programs, and so on with a similar or higher security setting.
Discretionary Access Control (DAC)
Unlike MAC, DAC is not forced from the administrator or the operating system. Instead, access is controlled by an object’s owner. For example, if a secretary creates a folder, she decides who will have access to that folder. This access is configured using the permissions dialog box.
DAC uses an ACL to determine access. The ACL is a table that informs the operating system of the rights each user has to a particular system object, such as a file, a directory, or a printer. Each object has a security attribute that identifies its ACL. The list has an entry for each system user with access privileges. The most common privileges include the ability to read a file (or all the files in a directory), to write to the file or files, and to execute the file (if it is an executable file or program).
Microsoft Windows servers/XP/Vista, Linux, UNIX, and MAC OSX are among the operating systems that use ACLs. The list is implemented differently by each operating system.
In Windows server products, an ACL is associated with each system object. Each ACL has one or more access control entries (ACE) consisting of the name of a user or group of users. The user can also be a role name, such as “secretary,” or “research.” For each of these users, groups, or roles, the access privileges are stated in a string of bits called an access mask. Generally, the system administrator or the object owner creates the ACL for an object.
Rule-Based Access Control (RBAC)
Rule-based access control controls access to objects according to established rules. The configuration and security settings established on a router or a firewall are good examples.
When a firewall is configured, rules are set up that control access to the network. Requests are reviewed to see if the requestor meets the criteria to be allowed access through the firewall. For instance, if a firewall is configured to reject all addresses in the 192.168.x.x range of IP addresses, and the requestor’s IP is in that range, the request would be denied.
In a practical application, rule-based access control is a variation of MAC. Administrators typically configure the firewall or other device to allow or deny access. The owner or another user does not specify the conditions of acceptance, and safeguards ensure that an average user cannot change settings on the devices.
Role-Based Access Control (RBAC)
In role-based access control, access decisions are determined by the roles that individual users have within the organization. Role-based access requires the administrator to have a thorough understanding of how a particular organization operates, the number of users, and each user’s exact function in that organization.
Because access rights are grouped by role name, the use of resources is restricted to individuals authorized to assume the associated role. For example, within a school system, the role of teacher can include access to certain data, including test banks, research material, and memos. School administrators may have access to employee records, financial data, planning projects, and more.
The use of roles to control access can be an effective means for developing and enforcing enterprise-specific security policies, and for streamlining the security management process.
Roles should receive just the privilege level necessary to do the job associated with that role. This general security principal is known as the least privilege concept. When someone is hired in an organization, the employee’s role is clearly defined. A network administrator creates a user account for the new employee and places that user account in a group with those with the same role in the organization.
Least privilege is often too restrictive to be practical in business. For instance, using teachers as an example, some more experienced teachers may have more responsibility than others and may require increased access to a particular network object. Customizing access to each individual is a time-consuming process.
Note
Where’s 802.1x? 802.1x is a standard that specifies port-based network access control. 802.1x is often associated with wireless networks. Information on 802.1x was covered in Chapter 7, “Wireless Networking.”
Remote Authentication Protocols
One of the most important decisions an administrator needs to make when designing a remote access strategy is the method by which remote users will be authenticated. Authentication refers to the mechanisms used to verify the identity of the computer or user attempting to access a particular resource. The exact protocol used by an organization will depend on its security policies. The authentication methods may include the following:
• Microsoft Challenge Handshake Protocol (Microsoft-CHAP or MS-CHAP)—MS-CHAP is used to authenticate remote Windows workstations, providing the functionality to which LAN-based users are accustomed while integrating the hashing algorithms used on Windows networks. MS-CHAP works with PPP, PPTP, and L2TP network connections. MS-CHAP uses a challenge/response mechanism to keep the password from being sent during the authentication process. MS-CHAP uses the Message Digest 5 (MD5) hashing algorithm and the Data Encryption Standard (DES) encryption algorithm to generate the challenge and response and provides mechanisms for reporting connection errors and for changing the user’s password.
• Microsoft Challenge Handshake Authentication Protocol version 2 (MS-CHAP v2)—The second version of MS-CHAP brings with it enhancements over its predecessor. These enhancements include support for two-way authentication and a few changes in how the cryptographic key is analyzed. As far as authentication methods are concerned, MS-CHAP version 2 is the most secure. MS-CHAP works with PPP, PPTP, and L2TP network connections.
• Challenge Handshake Authentication Protocol (CHAP)—CHAP is a widely supported authentication method and works much the same way as MS-CHAP. A key difference between the two is that CHAP supports non-Microsoft remote access clients. CHAP allows for authentication without actually having users send their passwords over the network, and because it’s an industry standard, it allows Windows Server 2003 to behave as a remote client to almost any third-party PPP server.
• Extensible Authentication Protocol (EAP)—EAP is an extension of PPP that supports authentication methods that go beyond the simple submission of a username and password. EAP was developed in response to an increasing demand for authentication methods that use other types of security devices such as token cards, smart cards, and digital certificates.
• Password Authentication Protocol (PAP)—Use PAP only if necessary. PAP is a simple authentication protocol in which the username and password are sent to the remote access server in unencrypted text, making it possible for anyone listening to network traffic to steal both. PAP is typically used only when connecting to older UNIX-based remote access servers that do not support any additional authentication protocols.
• Unauthenticated Access—Users are allowed to log on without authentication.
Choosing the correct authentication protocol for remote clients is an important part of designing a secure remote access strategy. After they are authenticated, users have access to the network and servers. It is recommended for administrators to start with the most secure protocol, MS-CHAP v2.
Exam Alert
Authentication protocols Before taking the Network+ exam, you should be familiar with the different remote access authentication methods and know where and when they may be used.
Using Secure Protocols
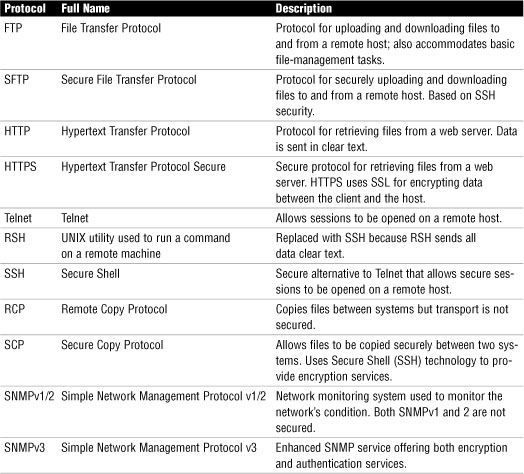
We use many protocols to move information throughout networks. Some of these protocols are secure, whereas others offer little and sometimes no security at all. When administering a network, it is important to be able to choose the right protocol for the job. TCP/IP protocols were discussed in Chapter 4, “Understanding the TCP/IP Protocol Suite.” However, Table 15.1 compares some unsecured protocols with the secure counterpart.
Table 15.1 Comparing Protocols
Malicious Software
Malicious software, or malware, is a serious problem in today’s computing environments. It is often assumed that malware is composed of viruses. Although this is typically true, many other forms of malware exist that by definition are not viruses but are equally undesirable.
The term malware is a general term that includes a variety of software threats, including the following:
• Viruses—By now, we have all heard of computer viruses. These are the dreaded software programs or code that can unknowingly operate on our computers and cause a range of problems. Often, viruses get blamed for more than they actually do, but as we know, they can cause significant problems.
• Macro viruses—One variant of the regular virus is a macro virus. These are the viruses that are targeted directly at documents. Given that often the data on our systems is the most hard to replace, losing documents or corrupting documents can be a huge loss.
• Worms—Worms are programs that are designed to propagate automatically and silently without modifying software or alerting the user. Inside a system, they can carry out their intended harm, whether it is to damage data or relay sensitive information.
• Trojan horses—Trojan horses are particularly tricky and require users to be keenly aware of the programs they install on a computer system. Essentially, Trojan horses appear as helpful or harmless programs but, when installed, carry and deliver a malicious payload. For example, harmless online games may be installed on a system, but they actually may be installing harmful code at the same time.
• Spyware—Spyware covertly gathers system information through the user’s Internet connection without his or her knowledge, usually for advertising purposes. Spyware applications are typically bundled as a hidden component of freeware or shareware programs that can be downloaded from the Internet.
Each of these viruses pose a threat to the systems on a network. But how does this malicious software propagate? As a network administrator, you need to be aware of how the various types of malware are distributed.
Malware Distribution
To be effective, malware requires a method to get from one computer to another. Those administering networks or individual systems should know how malware is transported because it helps to determine the strategies used to fight the viruses. Following are some of the common malware delivery types:
• Removable media—In the past, floppy disks were the most common mechanism for delivering malware. Today we have many forms of removable media, MP3 players, USB storage devices, and more. All these devices may carry viruses into a network if they go unchecked. Policies, such as checking such devices before using them in a network and restricting access to removable media, are common. USB and FireWire devices can transport both legitimate files and malware because they are commonly used to carry files or applications between computers.
• Peer-to-peer (P2P) sharing networks—P2P networks that offer free applications, music, and other software are often ripe with viruses, worms, Trojan horses, and spyware. Many of these malware types can replicate quickly and be tricky to handle. Many network administrators have created policies restricting access to such sites. These policies limit what can be installed on a local computer system.
• Network shares—A network share is a file, folder, or resource that is made available to the network. Malware can use the network shares to propagate itself from system to system over the network. Poorly implemented security on network shares produces an environment where malware can replicate to a large number of computers connected to the network.
• Email—Email has traditionally been a hot spot for virus propagation. Many networks have email monitoring software to help determine the presence of viruses in email. Preventing email viruses is important because with the click of a button, malware can be sent to hundreds of thousands of users. Most malware attacks through email require the recipient to activate the attack either by opening an email or downloading something from the email after assuming it is from a trusted source.
These examples show how malware can be transported from system to system. Because the individuals who write and export malware are always designing new programs, they are also continually finding new ways to transport their software. Administrators need to keep abreast of new and existing transport mechanisms.
Malware Payloads
When we talk about a malware payload, we are referring to the way in which it impacts the computer system or the description of its intended purpose. To help detect malware, knowing what it is designed to do will help administrators be aware of potential threats. Some of the more common payloads include the following:
• Attacks on data—Many of the malicious programs are designed to attack data by corrupting, deleting, or stealing it. These attacks are particularly dangerous because data is the most valuable resource on the network.
• Backdoor attacks—If backdoor access to a system is found, an intruder may be able to take complete or partial control over a system. The user may not even know that the takeover is occurring. The intruder can then use that system as a launching point to stage other attacks or steal personal information or data.
• Overwhelm system resources—Some malware is specifically designed to overload and ultimately prevent a service form running or to crash the entire system. This is a denial-of-service attack.
• Applications—Many malware programs corrupt or take over applications. Applications include everything from the word processor to the firewall software.
More About Viruses
Viruses and their effects are well documented and are feared by users and administrators alike. The damage from viruses varies greatly from disabling an entire network to damaging applications on a single system. Regardless of the impact, viruses can be destructive, causing irreplaceable data loss and consuming hours of productivity.
As mentioned, not all the malware we encounter is by definition a virus. To be considered a virus, the malware must possess the following characteristics:
• It must be able to replicate itself.
• It requires a host program as a carrier.
• It must be activated or executed in order to run.
Exam Alert
Virus or not? For the Network+ exam, remember that a virus must be able to replicate itself.
There are many types of viruses and many terms to describe them, such as the following:
• Resident virus—A resident virus installs itself into the operating system and stays there. It typically places itself into memory and from there infects and does damage. The resident will load with the operating system on boot.
• Variant virus—Like any other applications, from time to time viruses are enhanced to make them harder to detect and modify the damage that they do. Modifications to existing viruses are referred to as variants because they are rereleased versions of known viruses.
• Polymorphic virus—One particularly hard to handle type of virus is the polymorphic one. These have the ability to change their characteristics to avoid detection. Polymorphic viruses are some of the most difficult types to detect and remove.
• Overwriting/non-overwriting virus—Viruses can be designed to overwrite files or code and replace them with modified data. In many cases the application may function as normal so the user will not know the program has been modified. Non-overwriting viruses amend an application by adding files or code.
• Stealth virus—A stealth virus is one that is able to hide itself to avoid detection. Such viruses will often fool detection programs by appearing as legitimate programs or hiding within legitimate programs.
• Macro virus—Macro viruses are specifically designed to infect and corrupt documents. Because documents are commonly shared, these viruses can spread at an alarming rate.
More About Trojan Horses and Worms
Trojan horses, as the name implies, are about hiding. Trojan horses come hidden in other programs. For example, a Trojan horse can be hidden in a shareware game. The game looks harmless but when downloaded and executed, the Trojan is operating in the background, corrupting and damaging the system.
Trojan horses are different from viruses because a Trojan horse does not replicate itself and does not require a host program to run. They are commonly found on P2P sharing networks where interesting and helpful looking programs are actually disguised Trojan horses. Trojan horses are also spread when programs are shared using email communications or removable media. In the past, many of the executable jokes sent through email, such as cartoons and amusing games were in fact the front end of a Trojan horse.
Worms are different and have the potential to spread faster than any other form of malware. Worms can be differentiated from viruses. Although they can replicate, they do not require a host and do not require user intervention to propagate. Worms can spread at an alarming rate because they often exploit security holes in applications or operating systems. After a security hole is found, worms automatically begin to replicate, looking for new hosts with the same vulnerability. Worms look for an Internet connection and then use that connection to replicate without any user intervention.
Review Break
Comparing Malware Types
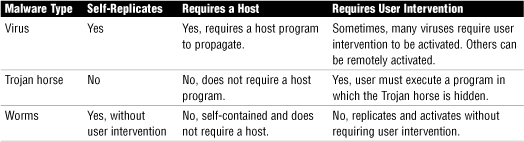
Table 15.2 identifies the distinctions between worms, Trojan horses, and viruses.
Table 15.2 Comparing Malware Types
Types of Attacks
Life would be easier for network administrators if fewer types of attacks were launched against networks. Unfortunately, numerous attacks exist that administrators must be aware of, with new ones always being discovered. In this section we review some of the more common attacks.
Denial of Service and Distributed Denial of Service Attacks
Denial of service (DoS) attacks are designed to tie up network bandwidth and resources and eventually bring the entire network to a halt. This type of attack is done by flooding a network with more traffic than it can handle. A DoS attack is not designed to steal data but to cripple a network and in doing so may have a significant financial impact on companies.
The effects of DoS attacks include the following:
• Saturating network resources, which then render those services unusable.
• Flooding the network media, preventing communication between computers on the network.
• User downtime because of an inability to access required services.
• Potentially huge financial losses for an organization because of network and service downtime.
Whereas a DoS attack focuses on a single system or a few systems, a distributed denial of service (DDoS) attack takes out entire networks. In a DDoS attack, an influx of traffic is used to halt network functionality. DDoS attacks can also be aimed at specific server types within a network. For example, DDoS attacks can be launched against a network’s mail servers, DNS servers, or web servers.
Exam Alert
DDoS For the Network+ exam, remember that DoS and DDoS attacks are attempts by attackers to prevent use of a system or service from using that service.
There are several types of DoS and DDoS attacks, and each targets a different area. For instance, they may target bandwidth, memory, CPU, and hard drive space. When a server or other system is overrun by malicious requests, one or more of these core resources breaks down, causing the system to crash or stop responding.
• Fraggle—In a Fraggle attack, spoofed UDP packets are sent to a network’s broadcast address. These packets are directed to specific ports such as port 7 (ICMP) or port 19 (chargen); after they are connected, they can flood the system.
• Smurf—The Smurf attack is similar to a Fraggle attack, except a Ping request is sent to a broadcast network address with the sending address spoofed so that many Ping replies will come back to the victim and overload the ability of the victim to process the replies.
• Ping of Death—With this attack, an oversized ICMP datagram is used to crash IP devices that were manufactured before 1996.
Exam Alert
ICMP floods For the Network+ exam, remember that attacks that focus on port 7 (ICMP) and use ping are known as ICMP flood attacks. Ping of death, fraggle, and smurf are all forms of ICMP flood attacks.
• SYN flood—In a typical TCP session, communication between two computers is initially established by a three-way handshake referred to a SYN, SYN/ACK, ACK. At the start of a session, the client sends a SYN message to the server. The server acknowledges the request by sending a SYN/ACK message back to the client. The connection is established when the client responds with an ACK message.
In a SYN attack, the victim is overwhelmed with a flood of SYN packets. Every SYN packet forces the targeted server to produce a SYN-ACK response and then wait for the ACK acknowledgment. However, the attacker won’t respond with an ACK or will spoof its destination IP address with a non-existent address so that there is no ACK response. The result is that the server will begin filling up with half-open connections. When all the server’s available resources are tied up on half-open connections, it stops acknowledging new incoming SYN requests, including legitimate ones.
Other Common Attacks
Malware and DoS attacks are not the only threats facing network administrators. Other threats include the following:
• Password attacks—Password attacks are one of the most common types of attacks. Typically, usernames are easy to obtain, and matching the username with the password allows the intruder to gain system access to the level associated with that particular user. This access is why it is vital to protect administrator passwords. Obtaining a password with administrator privileges provides the intruder with total unrestricted access to the system or network.
• Social engineering—Social engineering is a common form of cracking. It can be used both by outsiders and by people within an organization. Social engineering is a hacker term for tricking people into revealing their password or some form of security information. It may include trying to get users to send passwords or other information over email, shoulder surfing, or any other method that tricks users into divulging information. Social engineering is an attack that attempts to take advantage of human behavior.
• Eavesdropping—As the name implies, eavesdropping involves an intruder who obtains sensitive information such as passwords, data, and procedures for performing functions by intercepting, listening, and analyzing network communications. It is possible for an intruder to eavesdrop by wiretapping, using radio, or auxiliary ports on terminals. It is also possible to eavesdrop using software that monitors packets sent over the network. In most cases, it is difficult to detect eavesdropping, making it important to ensure that sensitive data is not sent over the network in clear text.
• Man-in-the-middle attack—In a man–in-the-middle attack, the intruder places himself between the sending and receiving devices and captures the communication as it passes by. The interception of the data is invisible to those actually sending and receiving the data. The intruder is able to capture the network data and manipulate it, change it, examine it, and then send it on. Wireless communications are particularly susceptible to this type of attack. A rogue access point can be an example of a man-in-the-middle attack.
• Spoofing—Spoofing is a technique in which the real source of a transmission, file, or email is concealed or replaced with a fake source. This technique enables an attacker, for example, to misrepresent the original source of a file available for download in order to trick users into accepting a file from an untrusted source, believing it is coming from a trusted source.
• Rogue access points—A rogue access point describes a situation where a wireless access point has been placed on a network without knowledge of the administrator. The result is that it is possible to remotely access the rogue access point because it likely does not adhere to company security policies. So all security can be compromised by a cheap wireless router placed on the corporate network.
• Phishing—Often, users receive a variety of emails offering products, services, information, or opportunities. Unsolicited email of this type is referred to as phishing (fishing). The technique involves a bogus offer that is sent to hundreds of thousands or even millions of email addresses. The strategy plays the odds; for every 1,000 emails sent perhaps 1 person replies. Phishing can be dangerous because users may be tricked into divulging personal information such as credit card numbers or bank account information.
Exam Alert
Attack types The Network+ exam is sure to have questions requiring you to identify the types of attacks used. Be sure you can identify the attacks described in the preceding list before taking the exam.
An Ounce of Prevention
The threat from malicious code is a very real concern. It is important to take the steps to protect our systems, and although it may not be possible to eliminate the threat, it is possible to significantly reduce that threat.
One of the primary tools used in the fight against malicious software is antivirus software. Antivirus software is available from a number of companies, and each offers similar features and capabilities. The following is a list of the common features and characteristics of antivirus software:
• Real-time protection—An installed antivirus program should continuously monitor the system, looking for viruses. If a program is downloaded, an application opened, or a suspicious email received, the real-time virus monitor detects and removes the threat. The virus application sits in the background largely unnoticed to the user.
• Virus scanning—An antivirus program must be capable of scanning selected drives and disks either locally or remotely. Scanning can either be run manually or be scheduled to run at a particular time.
• Scheduling—It is a best practice to schedule virus scanning to occur automatically at a predetermined time. In a network environment, this would typically occur during off hours when the overhead of the scanning process won’t impact users.
• Live updates—New viruses and malicious software are released with alarming frequency. It is recommended that the antivirus software be configured to receive virus updates regularly.
• Email vetting—Emails represent one of the primary sources for virus delivery. It is essential to use antivirus software that provides email scanning for both inbound and outbound email.
• Centralized management—In a network environment, it is a good idea to use software that supports managing the antivirus program from the server. Antivirus updates and configurations need to be made only on the server and not on each individual client station.
Managing the threat from viruses is considered a proactive measure, with antivirus software being only part of the solution. A complete virus protection strategy requires many aspects to help limit the risk of viruses, including the following:
• Develop in-house policies and rules—In a corporate environment, or even a small office, it is important to establish what information can be placed onto a system. For example, should users be able to download programs from the Internet? Can users bring in their own flash drives or other storage media?
• Monitoring virus threats—With new viruses coming out all the time, it is important to check whether new viruses have been released and what they are designed to do.
• Educate users—One of the keys to a complete antivirus solution is to train users in virus prevention and recognition techniques. If users know what they are looking for, it can prevent a virus from entering the system or the network. Back up copies of important documents. Be aware that no solution is absolute and care should be taken to ensure the data is backed up. In the event of a malicious attack, redundant information is available in a secure location.
• Automate virus scanning and updates—Today’s antivirus software can be configured to scan and update itself automatically. Because such tasks can be forgotten and overlooked, it is recommended to have these processes scheduled to run at predetermined times.
• Patches and updates—All applications, antivirus programs, and operating systems release patches and updates often; they are designed to address potential security weaknesses. Administrators must keep an eye out for these patches and install them when needed.
The preceding list describes common strategies used to help prevent and manage malware on networks and computer systems. There are also several strategies required to mitigate and manage the threats from attacks such as DoS and DDoS, such as the following:
• Installing an intrusion detection or intrusion prevention system on the network or computer system.
• Use up-to-date antivirus software to help locate possible zombie agents.
• To prevent exploitation of security flaws, ensure your applications and operating systems patches are current.
• Use monitoring software that can identify slow down or unusual behavior on a network or computer system.
• Disable any unused network services.
• Ensure that firewalls are used and properly configured.
Maintaining Operating System Software
One of the key components to keeping systems safe is maintaining the operating system. This includes keeping the network operating software up to date with patches and service used to address security issues.
Operating systems are complex systems having to accommodate a dynamic environment while providing services to clients and applications software. This complexity makes it very hard to produce products that operate at 100 percent capacity on every level, making it necessary to apply periodic updates to the software. This operation can be one of the more time consuming and complex server maintenance tasks.
Operating systems are generally updated through the use of patches and service packs. Windows operating systems, for instance, periodically introduce service packs starting with, as most do, service pack 1; they keep producing service packs as issues and security flaws are detected. Each of these service packs provides fixes, updates, and enhanced features for the operating system. However, many servers using Windows do not have the latest service packs installed, leaving them at potential risk of being hacked. To be as secure as possible, you need to know when, why, and how service packs should be used on a server.
Note
Get packed Service packs are not restricted to operating systems, but can include all application software running on the computer. This abundance of service packs can represent an interesting challenge to server administrators because an update for one product will sometimes necessitate an update for a different product.
Reasons to Use a Service Pack
If you use an operating system right from the box and expect it to provide all the functionality it advertised, you might be out of luck. Before they are released, operating systems are run through a rigorous testing period, including being released in a Beta version to get further testing, with real-world applications, before going live. However, there is no way to cover all real-world applications in a test environment, so when the operating system comes out, its shortcomings are soon discovered. Service packs are released to address problems with the operating system’s functionality.
Traditionally, updates to software were distributed individually, with each separate problem necessitating a specific fix. In recent years, the complexity of the software and the need to streamline the application of fixes has led to the use of service packs, which are essentially complete programs designed to easily correct a large number of problems in a single exercise. Even so, software companies still issue specific patches for certain situations.
Although service packs are commonly applied to fix errors or shortcomings of an operating system, some applications will install and run only if the latest service pack is installed. Your server may be functioning well, but when you’re trying to install a new proxy server program, the installation can shut down with a message stating that a newer service pack is required for the installation of the product. These messages are not normally given for the amusement of the software developers; generally, these messages indicate that an unstable situation may arise if the new software is installed on a platform that doesn’t have the required service pack installed.
A less-obvious reason for installing services packs is that if you call an operating system manufacturer’s technical support line, one of the first questions you will be asked is whether you have the latest service pack installed. The support representative’s first recommendation will probably be to upgrade to the latest service pack, and if that doesn’t fix the problem, call back. Software manufacturers do not make this stipulation unnecessarily. When someone is attempting to troubleshoot a problem, knowing that the underlying operating system is at a given level is an important step in the resolution process.
When to Use a Service Pack
There are some clear guidelines to follow when you’re considering installing a service pack on a server. Keep in mind that any change to a server—whether it’s a software or a hardware change—has the potential for disaster. Therefore, service pack updates are installed only when they’re needed to address a known bug with the operating system or when they include a new feature that you need. If you apply a service pack without knowing the reason why, you are guilty of a techno sin—that of blind patching.
Blind patching is the term given to describe the practice of upgrading without knowing the issues you are trying to address. It is a dangerous practice. You must know the specific reasons that a service pack needs to be installed and what it promises to address.
How to Apply a Service Pack
Unfortunately, applying a service pack is not always as easy as simply downloading it and installing it. The installation of service packs is generally well documented by the operating system manufacturer, and the instructions given must be closely followed. The exact instructions for applying service packs can generally be found on the manufacturers’ websites (on their support and knowledge base pages).
When you’re installing a service pack, follow these guidelines:
1. Review the documentation—Before even downloading the service pack, review the documentation to ensure that there are no last-minute changes and that you are sure that the service pack addresses the problems you have.
2. Verify free space—Service packs can be very large, so before downloading them, make sure that the server has enough hard disk space for you to apply the patch. If the drive doesn’t have the space, you’ll need to free some up.
3. Test the service pack—Although it is not always possible, it is recommended that you download and install the service pack on another computer to discover any hidden problems. If you can’t do this, check newsgroups for valuable information from other server administrators who have used the service pack. A lot can be gained from the experience of others.
4. Back up the server—Make sure that a current backup is done on the system before you apply the service pack. This backup should include the data drives and the main operating system drive. Things can sometimes go wrong, and it’s essential to ensure that you can get the server back to the state it was in before you applied the service pack.
5. Get a baseline—If the service pack is being applied to address a particular problem, it is a good idea to get “before” and “after” pictures. Baselines are often the only means to measure if the service pack has actually addressed the issue it was intended to. If it has, that’s good, but if it hasn’t, a different fix will need to be applied.
6. Install the service pack—As we mentioned, installing a service pack is not always as easy as running an executable file. For instance, is the service pack applied after all of the major protocols and services have been installed, or is the service pack applied only after all other server software applications, services, and protocols have been installed and configured? The only way to know how and in what order the service pack is to be installed is to follow the manufacturer’s recommendations.
7. Reinstall and configure as necessary—Some service packs require some post-installation maintenance and configuration with the operating system. You might need to restart services, reinstall protocols, or update other software.
8. Test the system—Before users are allowed back onto the system, it should be thoroughly tested to ensure correct operation. Nothing is likely to annoy users more than being allowed to log back on to the server and then having to log off five minutes later because of an unforeseen problem with the service pack.
9. Perform a comparison baseline—Whether or not you expect the update to affect the performance of the server, the baseline must be retaken to ensure that the system has not been detrimentally affected. As we have already discussed, a service pack installation can have far-reaching effects and can, in exceptional cases, affect other system components. A comparison baseline is used to compare performance before and after the installation of the service pack.
Server Patches
Service packs are released infrequently and are usually used to address numerous issues within an operating system. Patches, on the other hand, provide quick fixes for a program or feature and are more commonplace. Patches are designed to address a very specific problem. For instance, you would download a patch to fix a security hole in the operating system when downloading and installing an entire service pack may not be necessary.
Note
Hotfix Patches are sometimes referred to as hotfixes.
The frequency with which patches are released and the relative lack of fanfare that they bring make it difficult to keep ahead of new developments. Maintaining a server involves being aware of the patches that are introduced for both the operating system and other software on the server. Even when the server is running smoothly, hidden problems may exist, such as security holes that patches are designed to fix. Frequently visiting the software manufacturer’s website to review the latest patches is not just a good idea, it is an essential part of proactive maintenance.
Another good way of staying up-to-date with the latest patches and packs is to read related newsgroups and check Internet sites.
Before you even download any patch for the server, first check out the operating system’s knowledge base for the specific instructions. Some patches, for instance, will work only if applied from within specific directories, some need extra files installed, or some need specific server services shut down. In addition to knowing exactly what the patch is intended to do, you need to know how it must be installed.
Whatever the purpose of the patch, you need to do a full backup because patches invariably change system files. For patches directed toward applications on the server, it may be tempting to skip a backup, but this is not advised. If something goes wrong with the patch, it is important to be able to get back to the point you started from before the patch.
Exam Alert
Same rule The same rule applies to software patches and service packs: no blind patching is allowed. Know what the patch you are downloading is intended to do, and implement the patch only if it is needed.
Summary
A cornerstone concept of network security is that of authorization, authentication, and accountability (AAA). Authentication refers to the mechanisms used to verify the identity of the computer or user attempting to access a particular resource. Authorization refers to the ability of the user to access a service or network resource after authentication, and accountability is the tracking of users on the network.
Several types of authentication are used on a network, including biometrics and smart cards. The most common is a username and password combination. To be strong, passwords should mix uppercase and lowercase letters with numbers and symbols. In network environments where security is a major concern, passwords should be no shorter than 10 characters.
RADIUS and TACACS+ are designed to provide used to provide authentication, authorization, and accountability. RADIUS and TACACS+ are protocols that enable a single server to become responsible for all remote access authentication, authorization, and auditing (or accounting) services. RADIUS uses UDP as a transport protocol whereas TACACS+ uses TCP.
PKI and Kerberos are both used for authentication purposes. Kerberos uses tickets for authentication, whereas PKI uses certificates. PKI uses cryptography keys to secure the communication between the client and the server. Private (symmetric) key encryption uses a single key for both encryption and decryption. PKI uses asymmetric keys that use a public key and a private key for encryption and decryption.
When accessing a network remotely, authentication protocols are used to verify the client. These protocols include CHAP, MS-CHAP, MS-CHAPv2, EAP, and PAP.
Several forms of network access control are used, including mandatory access control, discretionary access control, and rule-based and role-based access control. Mandatory access control is dictated by the network administrator, discretionary is dictated by the owner of an object or resource, role-based is assigned according to the role a user has in a network environment, and rule-based access control is dictated according to settings and policies, such as the settings used to control access in a network router.
Administrators need to be aware of many types of malware. This includes viruses, Trojan horses, and worms. A key part in the strategy for managing malware is to ensure that the firewall is set correctly, that the operating system and other applications are patched, and that the antivirus software is up to date.
Key Terms
• 802.1x
• CHAP
• DAC
• DoS
• DDoS
• EAP
• Kerberos
• MAC
• MS-CHAP
• PAP
• PKI
• RADIUS
• RBAC
• SSL
• TACACS+
• Virus
• Worm
Apply Your Knowledge
Exercises
15.1 Choosing how Windows applies updates in Windows Vista
Windows Vista can be configured to automatically or manually download and install updates. In most cases the automatic setting will do for desktop systems such as Vista. But as previously mentioned, the server system will not necessarily want live updates occurring. In this exercise we look at the different update options in Windows Vista, but comparable options can be found in most desktop and server operating systems today.
Estimated time: 15 minutes
1. Select Start, Control Panel, and click the Security link. This opens the Windows Vista Security options dialog screen. This screen is shown in Figure 15.5.
Figure 15.5 Windows Vista Security screen.
2. With the Security window visible, click the Windows Update option. This will open the Windows Update screen as shown in Figure 15.6. The center of the Windows Update screen lists the current status of the system updates. Notice from Figure 15.6 that there is one pending update and some information on the most recent updates.
Figure 15.6 Windows Update dialog screen.
To continue, click the Change Settings link located on the left of the Windows Update Windows screen.
3. In the Change Settings Windows screen, you can configure all the Windows Update features. Windows Vista provides four options for configuring the updates.
• Install Updates Automatically (Recommended)—This option lets you set the time of day when you want the automatic updates to occur.
• Download Updates but Let Me Choose Whether to Install Them—In this option, the updates will be downloaded but not installed until the administrator chooses to install them. This is often done if the update is going to require too many system resources. The update can then easily be applied in the off hours.
• Check for Updates but Let Me Choose Whether to Download and Install Them—Unlike the previous option, in this configuration the update is not downloaded, just flagged as a pending update. This gives the administrator time to review its purpose before deciding to download the update.
• Never Check for Updates—This is not the advised option for most configurations. This means that the administrator is responsible to find and download updates if needed.
4. Select the option to Download Updates but Let Me Choose Whether to Install Them. Click OK to continue. You will be returned to the main Windows Update screen.
15.2 Testing Password Strength
Network administrators are required to set strong passwords and ensure that users also set strong passwords. In this exercise, you test password strength.
Estimated time: 10 minutes
1. Open a web browser and go to the Security Stats website (www.securitystats.com/tools/password.php).
2. In the Enter a Password field, enter a sample password and click Submit.
3. The password strength is displayed in a bar graph, ranging from Weak Passwords to Strong Passwords. After getting the results on the password strength, try to increase the password’s strength by using the table offered under the To Increase the Strength of Your Password, Consider One or More of the Following area of the screen. Write down on a piece of paper what passwords you try so that you can see the progression from a weak to a strong password.
4. Continue experimenting until you get the message “Congratulations! You’ve supplied a sample password that is difficult to guess and hard to crack. It is recommended that you use passwords of this type.”
Exam Questions
1. Which of the following protocols provides AAA functionality and uses TCP as a transport mechanism?
![]() A. TACACS+
A. TACACS+
![]() B. RADIUS
B. RADIUS
![]() C. HTTPS
C. HTTPS
![]() D. 802.1x
D. 802.1x
2. Which of the following terms describes the mechanisms used to verify the identity of the computer or user attempting to access a particular resource?
![]() A. Authorization
A. Authorization
![]() B. Authentication
B. Authentication
![]() C. Accountability
C. Accountability
![]() D. Accounting
D. Accounting
3. Which of the following protocols is used to secure the HTTP protocol?
![]() A. SSP
A. SSP
![]() B. PPP
B. PPP
![]() C. SSL
C. SSL
![]() D. SFTP
D. SFTP
4. What is the function of RADIUS?
![]() A. RADIUS provides AAA services and uses the UDP protocol
A. RADIUS provides AAA services and uses the UDP protocol
![]() B. RADIUS provides AAA services and uses the TCP protocol
B. RADIUS provides AAA services and uses the TCP protocol
![]() C. RADIUS provides AAA services and uses the FTP protocol
C. RADIUS provides AAA services and uses the FTP protocol
![]() D. RADIUS provides AAA services and uses the HTTP protocol
D. RADIUS provides AAA services and uses the HTTP protocol
5. Which of the following malware types does not replicate itself?
![]() A. Worm
A. Worm
![]() B. Trojan horse
B. Trojan horse
![]() C. Virus
C. Virus
![]() D. Macro-virus
D. Macro-virus
6. Which of the following is the strongest password?
![]() A. password
A. password
![]() B. WE300GO
B. WE300GO
![]() C. l00#Ka1ivE
C. l00#Ka1ivE
![]() D. lovethemusic
D. lovethemusic
7. Which of the following are PPP authentication methods? (Choose the two best answers.)
![]() A. SLAP
A. SLAP
![]() B. CHAP
B. CHAP
![]() C. MS-CHAP
C. MS-CHAP
![]() D. POP
D. POP
8. You are the network administrator for a large network. You have just received an email warning of a potential security flaw in your network operating system. Which of the following should you do first?
![]() A. Install a service pack to mitigate the threat.
A. Install a service pack to mitigate the threat.
![]() B. Back up the server and take a baseline.
B. Back up the server and take a baseline.
![]() C. Review the documentation for the service pack or hotfix.
C. Review the documentation for the service pack or hotfix.
![]() D. Back up the server, take a baseline, and apply the fix.
D. Back up the server, take a baseline, and apply the fix.
9. SSH is a secure alternative to which of the following?
![]() A. Telnet
A. Telnet
![]() B. DHCP
B. DHCP
![]() C. PPTP
C. PPTP
![]() D. Kerberos
D. Kerberos
10. Kerberos is an authentication system that can be used on what operating systems?
![]() A. Windows 2003/Vista
A. Windows 2003/Vista
![]() B. Linux
B. Linux
![]() C. MAC
C. MAC
![]() D. All the options are correct.
D. All the options are correct.
11. What is the purpose of auditing?
![]() A. It allows you to be notified when a security breach is detected.
A. It allows you to be notified when a security breach is detected.
![]() B. It allows you to determine whether a security breach has occurred.
B. It allows you to determine whether a security breach has occurred.
![]() C. It allows you to prevent security breaches.
C. It allows you to prevent security breaches.
![]() D. It allows you to control Internet access from a single point.
D. It allows you to control Internet access from a single point.
12. When defining a password policy for an organization, which of the following would you consider setting? (Choose all the best answers.)
![]() A. Minimum password length
A. Minimum password length
![]() B. Password expiration period
B. Password expiration period
![]() C. Prevention of password reuse
C. Prevention of password reuse
![]() D. Maximum password length
D. Maximum password length
13. Some of the systems on your network contain very sensitive data. Therefore, you have been asked to provide both fingerprint and password authentication. What type of authentication strategy does this represent?
![]() A. Multilayered authentication
A. Multilayered authentication
![]() B. Biometrics
B. Biometrics
![]() C. Multifactor authentication
C. Multifactor authentication
![]() D. Two-phase authentication
D. Two-phase authentication
14. Which of the following are not authentication protocols? (Choose all that apply.)
![]() A. MS-EAP
A. MS-EAP
![]() B. CHAP
B. CHAP
![]() C. SSL
C. SSL
![]() D. EAP
D. EAP
15. You suspect that an employee in the company has been logging on to the system from a remote connection and attempting to look through files that he should not have access to. Which mechanism could you use to discover the identity of the person trying to dial in?
![]() A. Auditing
A. Auditing
![]() B. File permissions
B. File permissions
![]() C. Password policy
C. Password policy
![]() D. Intruder detection
D. Intruder detection
16. Which of the following remote authentication protocols is used with smart card or digital certificates?
![]() A. Chap
A. Chap
![]() B. EAP
B. EAP
![]() C. CHAPv5
C. CHAPv5
![]() D. PAP
D. PAP
17. You are onsite as a consultant. The client’s many remote access users are experiencing connection problems. Basically, when users try to connect, the system is unable to service their authentication requests. What kind of server might you recommend to alleviate this problem?
![]() A. RADIUS server
A. RADIUS server
![]() B. IPsec server
B. IPsec server
![]() C. Proxy server
C. Proxy server
![]() D. Kerberos server
D. Kerberos server
18. You are configuring access control for your network. You decide that you need to implement access control for the network. All access control should be determined by an object’s owner. What form of access control does this represent?
![]() A. DOC
A. DOC
![]() B. RBAC
B. RBAC
![]() C. MAC
C. MAC
![]() D. DAC
D. DAC
19. Which of the following best describes an asymmetric key encryption strategy?
![]() A. Asymmetric key encryption uses both a private and public key to encrypt and decrypt messages.
A. Asymmetric key encryption uses both a private and public key to encrypt and decrypt messages.
![]() B. Asymmetric key encryption uses two private keys to encrypt and decrypt messages.
B. Asymmetric key encryption uses two private keys to encrypt and decrypt messages.
![]() C. Asymmetric key encryption uses a single key for both encryption and decryption.
C. Asymmetric key encryption uses a single key for both encryption and decryption.
![]() D. Asymmetric key encryption uses three separate keys for both encryption and decryption.
D. Asymmetric key encryption uses three separate keys for both encryption and decryption.
20. You have been called in to test the security of a network. You notice that a wireless router has been placed on the network without consent and is being used by remote users to access the network. Which security risk does this represent?
![]() A. Rogue protocol use
A. Rogue protocol use
![]() B. Malware
B. Malware
![]() C. Rogue access point
C. Rogue access point
![]() D. Signal creep
D. Signal creep
Answers to Exam Questions
1. A. Although both RADIUS and TACACS+ offer AAA services for remote users, some noticeable differences exist. TACACS+ relies on TCP for connection-oriented delivery, whereas RADIUS uses connectionless UDP for data delivery. For more information, see the section “RADIUS and TACACS+” in this chapter.
2. B. Authentication refers to the mechanisms used to verify the identity of the computer or user attempting to access a particular resource. Authorization controls who can and who cannot access a resource after authentication. Accountability and accounting are mechanisms used to track who does what on a system or a network. For more information, see the section “Authentication, Authorization, and Accountability (AAA)” in this chapter.
3. C. SSL provides a mechanism for securing data across a network. When used with the unsecured HTTP protocols, HTTP becomes HTTP secured (HTTPS). For more information, see the section “Using Secure Protocols” in this chapter.
4. A. RADIUS is a protocol that enables a single server to become responsible for all remote access authentication, authorization, and auditing (or accounting) services. RADIUS uses the UDP protocol for communication. For more information, see the section “RADIUS and TACACS+” in this chapter.
5. B. A Trojan horse does not replicate itself and does not require a host program to run. This is in contrast to viruses that are able to self-replicate. Worms self-replicate without user intervention. For more information, see the section “Malicious Software” in this chapter.
6. C. Strong passwords include a combination of letters and numbers and upper- and lowercase letters. In this question Answer C is by far the strongest password because it has nine characters—a symbol, numbers, and letters. Answer A is not a strong password because it is a standard word, contains no numbers, and is all in lowercase. Answer B mixes letters and numbers, and it is not a recognized word, so it is a strong password, although it is not as strong as Answer C. Answer D is too easy to guess and contains no numbers. For more information, see the section “Authentication” in this chapter.
7. B, C. Both CHAP and MS-CHAP are PPP authentication methods. The other answers are not valid authentication protocols. For more information, see the section “Remote Authentication Protocols” in this chapter.
8. C. Often overlooked is the need to read the documentation for the service pack or hotfix. The documentation will tell the administrator what the patch is intended to fix and how it should be applied. After the documentation is read and the administrator is sure of the process to apply the patch, a backup and possibly a baseline should be taken before applying the fix. For more information, see the section “How to Apply a Service Pack” in this chapter.
9. A. Many of the protocols used on today’s networks have a secure and a not secure option, meaning that data is sent in clear text. In this instance, SSH is a secure alternative to Telnet. Other examples include HTTPS (HTTP secure) and HTTP. None of the other answers are valid. For more information, see the section “Using Secure Protocols” in this chapter.
10. D. Kerberos is available for all the major operating systems. For more information, see the section “Using Secure Protocols” in this chapter.
11. B. Auditing is a process of reviewing security logs so that breaches can be detected. Answer A describes the function of alerting. The other answers are not valid. For more information, see the section “Accountability,” in this chapter.
12. A, B, C. When creating a password policy, you should set a minimum password length, parameters limiting reusing the old password, and a password expiration period. You may even want to set a maximum password length, though most operating systems have a built in maximum. For more information, see the section “Password Policies” in this chapter.
13. C. In many network environments, two types of authentication are used to help ensure that only those who should gain network access actually do. Combing authentication methods is known as multifactor authentication. It combines, for instance, a username-password combination with a smart card or finger scan. For more information, see the section “Multifactor Authentication” in this chapter.
14. A, C. MS-EAP and SSL are not remote access authentication protocols. Remote authentication protocols such as CHAP and PAP are used by RADIUS or other applications to authenticate remote user credentials. For more information, see the section “Remote Authentication Protocols” in this chapter.
15. A. To determine the user ID of a person trying to log on, you would implement auditing. All major operating systems provide auditing services to record events that occur on a system. This includes tracking logons, logoffs, who accesses certain systems resources, and so on. File permissions, password policies, and intruder detection would not help you to do this. For more information, see the section “Accountability” in this chapter.
16. B. EAP is an extension of PPP that supports authentication methods that go beyond the simple submission of a username and password. EAP was developed in response to an increasing demand for authentication methods that use other types of security devices, such as token cards, smart cards, and digital certificates. For more information, see the section “Remote Authentication Protocols” in this chapter.
17. A. By installing a RADIUS server, it is possible to move the workload associated with authentication to a dedicated server. A proxy server would not improve the dial-up connection’s performance. There is no such thing as a Kerberos server or an IPsec server. For more information, see the section “Using Secure Protocols” in this chapter.
18. D. With discretionary access, control is not forced from the administrator or the operating system. Instead access is controlled by an object’s owner. DAC uses an ACL to determine access. The ACL is a table that informs the operating system of the rights each user has to a particular system object, such as a file, directory, or printer. For more information, see the section “Network Access Control” in this chapter.
19. A. Asymmetric key encryption uses both a private and public key to encrypt and decrypt messages. The public key is used to encrypt a message or verify a signature, and the private key is used to decrypt the message or to sign a document. In a symmetric key encryption strategy, a single key is used for both encryption and decryption. For more information, see the section “Understanding Cryptography Keys” in this chapter.
20. C. A rogue access point describes a situation where a wireless access point has been placed on a network without knowledge of the administrator. The result is that it is possible to remotely access the rogue access point because it likely does not adhere to company security policies. For more information, see the section “Other Common Attacks” in this chapter.
