Chapter Seven
Wireless Networking
Introduction
One of the bigger changes in the networking world since the release of the previous Network+ exam is in wireless networking. Networks of all shapes and sizes incorporate wireless segments. Home wireless networking has also grown significantly in the past few years.
As you know, wireless networking enables users to connect to a network using radio waves instead of wires. Network users within range of a wireless transceiver (transmitter/receiver), known as an access point (AP), can move around an office freely without needing to plug in to a wired infrastructure. The benefits of wireless networking clearly have led to its growth.
Today, wireless local area networks (WLAN) provide a flexible and secure data communications system used to augment an ethernet LAN or in some cases to replace it altogether. This chapter explores the many facets of wireless networking starting with some of the devices and technologies that make wireless networking possible.
Understanding Wireless Devices
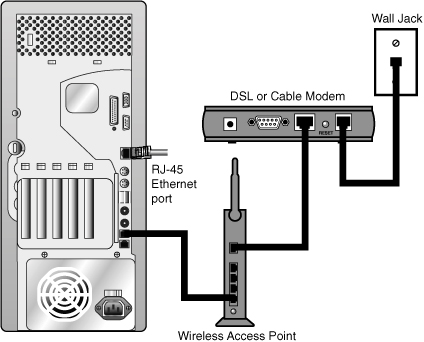
In a common wireless implementation, an AP connects to the wired network from a fixed location using standard cabling. The wireless AP receives and then transmits data between the wireless LAN and the wired network infrastructure.
Client systems communicate with a wireless AP using wireless LAN adapters. Such adapters are built in to, or added to, devices such as PC cards in laptops, PDAs, or desktop computers. Wireless LAN adapters provide the communication point between the client system and the airwaves via an antenna.
This section describes the role of APs and antennas in a wireless network.
Wireless Access Point
Wireless APs are both a transmitter and receiver (transceiver) device used for wireless LAN (WLAN) radio signals. An AP is typically a separate network device with a built-in antenna, transmitter, and adapter. APs use the wireless infrastructure network mode to provide a connection point between WLANs and a wired ethernet LAN. Recall from Chapter 1, “Introduction to Networking,” that wireless networks use the ad-hoc network topology and the infrastructure topology. The ad hoc is a peer-to-peer network design, and the infrastructure topology uses an AP. APs also typically have several ports allowing a way to expand the network to support additional clients.
Depending on the size of the network, one or more APs may be required. Additional APs are used to allow access to more wireless clients and to expand the range of the wireless network. Each AP is limited by a transmissions range, which is the distance a client can be from an AP and still get a useable signal. The actual distance depends on the wireless standard being used and the obstructions and environmental conditions between the client and the AP. Factors affecting wireless transmission ranges are covered later in this chapter. Figure 7.1 shows an example of an AP in a network configuration.
Figure 7.1 APs connect WLANs and a wired ethernet LAN.
Note
Wireless Access Points An AP can also operate as a bridge connecting a standard wired network to wireless devices or as a router passing data transmissions from one access point to another.
Tip
AP range If you are using a wireless device that loses its connection, it may be that you are too far away from the AP.
As mentioned, an AP is used in an infrastructure wireless network design. Used in the infrastructure mode, the AP receives transmissions from wireless devices within a specific range and transmits those signals to the network beyond. This network may be a private ethernet network or the Internet. In infrastructure wireless networking, there may be multiple access points to cover a large area or only a single access point for a small area such as a single home or small building.
Note
An AP for all seasons Because wireless networks are sometimes deployed in environments other than inside a warm, dry building, some manufacturers offer rugged versions of APs. These devices are sealed against the elements, making them suitable for placement in locations where nonrugged devices would not survive. If you are implementing a wireless network, consider whether using these rugged devices may be warranted.
When working with wireless APs, there are many terms and acronyms you need to understand. In this section we define some of the more common wireless acronyms you will see both on the exam and in any wireless networking documentation.
Exam Alert
Know the acronyms Several of the acronyms provided in the following bulleted list are sure to be on the Network+ exam. Be sure you can identify the function of each before writing the exam.
• Service Set Identifier (SSID)—The SSID is a network name needed to connect to a wireless AP. It is like a workgroup name used with Windows networking. 802.11 wireless networks use the SSID to identify all systems belonging to the same network. Client stations must be configured with the SSID to be authenticated to the AP. The AP may broadcast the SSID, allowing all wireless clients in the area to see the SSID of the AP. For security reasons, IPs can be configured to not broadcast the SSID or to cloak them. This means that client systems need to be given the SSID name by an administrator instead of it automatically being discovered by the client system.
Exam Alert
SSIDs One element of wireless security involves configuring the AP not to broadcast the SSID name. This configuration is done on the AP.
• Basic Service Set (BSS)—Refers to a wireless network that uses a single AP and one or more wireless clients connecting to the AP. Many home offices are an example of a BSS design. The BSS is an example of the infrastructure wireless topology. Wireless topologies were discussed with other network topologies in Chapter 1.
• Extended Service Set (ESS)—The ESS refers to two or more BSS sets connected, therefore using multiple APs. The ESS is used to create WLANs or larger wireless networks and is a collection of APs and clients. Connecting BSS systems allows clients to roam between areas and maintain the wireless connection without having to reconfigure between BSSs.
• Extended Service Set Identifier (ESSID)—The ESSID and the SSID are used interchangeably, but there is a difference between the two. The SSID is the name used with BSS networks, and the ESSID is the network name used with an ESS wireless network design. With an ESS, not all APs necessarily use the same name.
• Basic Service Set Identifier (BSSID)—The BSSID refers to the MAC address of the BSS AP. The BSSID is not to be confused with the SSID, which is the name of the wireless network.
• Basic Service Area (BSA)—When troubleshooting or designing wireless networks, the BSA is an important consideration. The BSA refers to the coverage area of the AP. The BSA for an AP depends on many factors, including the strength of the AP antenna, interference in the area, and whether an omnidirectional or directional antenna is being used.
Wireless Antennas
A wireless antenna is an integral part of overall wireless communication. Antennas come in many shapes and sizes, with each one designed for a specific purpose. Selecting the right antenna for a particular network implementation is a critical consideration and one that could ultimately decide how successful a wireless network will be. In addition, using the right antennas can save money on networking costs because you’ll need fewer antennas and access points.
Many small home network adapters and access points come with a nonupgradeable antenna, but higher-grade wireless devices require that you decide which antenna to use. Selecting an antenna takes careful planning and requires an understanding of what range and speed you need for a network. The antenna is designed to help wireless networks do the following:
• Work around obstacles
• Minimize the effects of interference
• Increase signal strength
• Focus the transmission, which can increase signal speed
The following sections explore some of the characteristics of wireless antennas.
Antenna Ratings
When a wirelesssignal is low and being influenced by heavy interference, it may be possible to upgrade the antennas to create a more solid wireless connection. To determine the strength of an antenna, we refer to its gain value. But how do we determine the gain value?
Consider a huge wireless tower emanating circular waves in all directions. If you could see these waves, you would see the data waves forming a sphere around the tower. The signals around the antenna flow equally in all directions (including up and down). An antenna that does this has a 0dbi gain value and is referred to as an isotropic antenna. The isotropic antenna rating provides a base point for measuring actual antenna strength.
An antenna’s gain value represents the difference between the 0dbi isotropic and the power of the antenna. For example, a wireless antenna advertised as a 15dbi antenna is 15 times stronger than the hypothetical isotropic antenna. The higher the decibel figure, the higher the gain.
Note
dbi The db in the designation stands for decibels, and the i references the hypothetical isotropic antenna.
When looking at wireless antennas, remember that a higher gain value means stronger send and receive signals. In terms of performance, the general rule is that every 3dB of gain added doubles the effective power output of an antenna.
Types of Wireless Antennas
When selecting an antenna for a particular wireless implementation, you must determine the type of coverage used by an antenna. In a typical configuration, a wireless antenna can be either omnidirectional or directional. The choice between the two depends on the wireless environment.
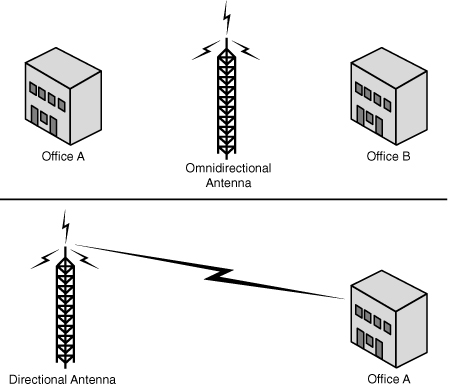
An omnidirectional antenna is designed to provide a 360-degree dispersed wave pattern. This type of antenna is used when coverage in all directions from the antenna is required. Omnidirectional antennas are good to use when a broad-based signal is required. For example, by providing an even signal in all directions, clients can access the antenna and associated access point from various locations. Because of the dispersed nature of omnidirectional antennas, the signal is weaker overall and therefore accommodates shorter signal distances. Omnidirectional antennas are great in an environment where there is a clear line of sight between the senders and receivers. The power is evenly spread to all points, making omnidirectional antennas well suited for home and small office applications.
Exam Alert
Directional differences Omnidirectional antennas provide wide coverage but weaker signal strength in any one direction than a directional antenna.
Directional antennas are designed to focus the signal in a particular direction. This focused signal allows for greater distances and a stronger signal between two points. The greater distances enabled by directional antennas allow a viable alternative for connecting locations, such as two offices, in a point-to-point configuration.
Directional antennas are also used when you need to tunnel or thread a signal through a series of obstacles. This concentrates the signal power in a specific direction and allows you to use less power for a greater distance than an omnidirectional antenna. Figure 7.2 shows an example of a directional and an omnidirectional antenna beam.
Figure 7.2 Directional antenna signal.
Note
Polarization In the wireless world, polarization refers to the direction that the antenna radiates wavelengths. This direction can either be vertical, horizontal, or circular. Today, vertical antennas are perhaps the most common. As far as configuration is concerned, both the sending and receiving antennas should be set to the same polarization.
Data Rate Versus Throughput
When talking about wireless transmissions, it is important to distinguish between throughput and data rate. From time to time these terms are used interchangeably, but technically speaking, they are different. As shown later in this chapter, each wireless standard has an associated data rate. For instance, the 802.11g wireless standard lists a data rate of up to 54Mbps. This represents the potential maximum data rate at which devices using this standard can send and receive data. However, in network data transmissions, many factors prevent the data rate from reaching this end-to-end theoretical maximum. For instance, data packets include overhead such as routing information, checksums, and error recovery data. Although this may all be necessary, it can impact overall data rate.
The number of clients on the network can also impact the data rate; the more clients, the more collisions. Depending on the network layout, collisions can have a significant impact on end-to-end transmission. Wireless network signals degrade as they pass through obstructions such as walls or doors; the signal speed deteriorates with each obstruction.
All these factors leave us with the actual throughput of wireless data transmissions. Throughput represents the actual transfer rate to expect from wireless transmissions. In practical application, wireless transmissions will be approximately one-half or less of the listed data rate. This means that we could hope for about 20–25Mbps for 802.11g and not the listed rate of 54Mbps. Depending on the wireless setup, the transmission rate could be much less.
802.11 Wireless Standards
802.11 represents the IEEE designation for wireless networking. Several wireless networking specifications exist under the 802.11 banner. The Network+ objectives focus on 802.11, 802.11a, 802.11b, 802.11g, and 802.11n. All these standards use the ethernet protocol and the CSMA/CA access method.
Note
CSMA/CA CSMA/CA defines a media access method for wireless networking. CSMA/CA was discussed in Chapter 6, “Ethernet Networking Standards.”
The 802.11 wireless standards can differ in terms of speed, transmission ranges, and frequency used, but are similar in terms of actual implementation. All standards can use either an infrastructure or ad-hoc network design, and each can use the same security protocols. The ad-hoc and infrastructure wireless topologies were discussed in Chapter 1.
The IEEE 8082.11 standards include
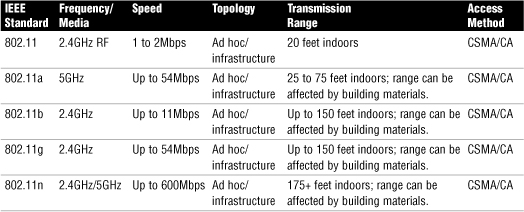
• IEEE 802.11—There were two variations on the initial 802.11 wireless standard. Both offered 1 or 2Mbps transmission speeds and the same radio frequency (RF) of 2.4GHz. The difference between the two was in the way in which data traveled through the RF media. One used frequency hopping spread spectrum (FHSS), and the other used direct sequence spread spectrum (DSSS). These technologies are discussed in the next section. The original 802.11 standards are far too slow for modern networking needs and are now no longer deployed.
• IEEE 802.11a—In terms of data rate, the 802.11a standard is far ahead of the original 802.11 standards. 802.11a specifies data rates of up to 54Mbps, but communications typically take place at 6Mbps, 12Mbps, or 24Mbps. 802.11a is not compatible with other wireless standards 802.11b and 802.11g.
• IEEE 802.11b—The 802.11b standard provides for a maximum transmission data rate of 11Mbps. However, devices are designed to be backward compatible with previous standards that provided for speeds of 1, 2, and 5.5Mbps. 802.11b offers a transmission range of up to 100ft with 11Mbps data rate and 300ft operating a 1Mbps data rate. 802.11b uses a 2.4GHz RF range and is compatible with 802.11g.
• IEEE 802.11g—802.11g is a popular wireless standard today. On average, 802.11g offers wireless transmission over distances of 150 feet and a data rate of 54Mbps compared with the 11Mbps of the 802.11b standard. Like 802.11b, 802.11g operates in the 2.4GHz range and is therefore compatible with it.
• IEEE 802.11n—The newest of the wireless standards listed in the Network+ objectives is 802.11n. The goal of the 802.11n standard is to significantly increase throughput in both the 2.4 GHz and the 5 GHz frequency range. The baseline goal of the standard is to reach speeds of 100 Mbps but given the right conditions, it is estimated that the 802.11n data rates might reach a staggering 600 Mbps. In practical operation, 802.11n speeds will be much less.
Exam Alert
Wireless standards Be prepared to answer questions on the specific characteristics of wireless standards on the Network+ exam.
Table 7.1 highlights the characteristics of the various 802.11 wireless standards.
Table 7.1 802.11 Wireless Standards
The Magic Behind 802.11n
802.11n is poised to bring about the next big change in wireless networking, promising greater distances and staggering speeds. But how is this done? 802.11n takes the best from the 802.11 standards and mixes in some new features to take wireless to the next level. First among these new technologies is multiple input multiple output (MIMO).
MIMO is unquestionably the biggest development for 802.11n and the key to the new speeds. Essentially, MIMO uses multiplexing to increase range and speed of wireless networking. Multiplexing is a technique that combines multiple signals for transmission over a single line or media. MIMO enables the transmission of multiple data streams traveling on different antennas in the same channel at the same time. A receiver reconstructs the streams which has multiple antennas as well. By using multiple paths, MIMO provides a significant capacity gain over conventional single antenna systems, along with more reliable communication.
In addition to all these improvements, 802.11n allows channel bonding that will essentially double the data rate again. The 802.11b and 802.11g wireless standards use a single channel to send and receive information. With channel bonding, it is possible to use two channels at the same time. As you might guess, the capability to use two channels at once increases performance. It is expected that bonding will help increase wireless transmission rates from the 54Mbps offered with the 802.11g standards to a theoretical maximum of 600Mbps.
Note
Channel surfing In wireless networking a single channel is 20MHz in width. When two channels are bonded they are a total of 40MHz. 802.11n systems can use either the 20MHz channels or the 40MHz channel.
Wireless Radio Channels
Radio frequency (RF) channels are important parts of wireless communications. A channel is the band of RF used for the wireless communication. Each IEEE wireless standard specifies the channels that can be used. The 802.11a standard specifies radio frequency ranges between 5.15 and 5.875GHz. In contrast, 802.11b and 802.11g standards operate between the 2.4 to 2.4835GHz range.
Note
That Hertz Hertz (Hz) is the standard of measurement for radio frequency. Hertz is used to measure the frequency of vibrations and waves, such as sound waves and electromagnetic waves. One hertz is equal to one cycle per second (1Hz). Radio frequency is measured in kilohertz (one thousand cycles per second), megahertz (one million cycles per second), or gigahertz (one billion cycles per second).
As far as channels are concerned, 802.11a has a wider frequency band, allowing more channels and therefore more data throughput. As a result of the wider band, 802.11a supports up to eight nonoverlapping channels. 802.11b/g standards use the smaller band and support only up to three nonoverlapping channels.
It is recommended that the nonoverlapping channels be used for communication. In the United States, 802.11b/g use 11 channels for data communication; three of these—channels 1, 6, and 11—are nonoverlapping channels. Most manufacturers set their default channel to one of the nonoverlapping channels to avoid transmission conflicts. With wireless devices, you have the option of selecting which channel your WLAN operates on to avoid interference from other wireless devices that operate in the 2.4GHz frequency range.
When troubleshooting a wireless network, be aware that overlapping channels can disrupt the wireless communications. For example, in many environments, APs are inadvertently placed close together—perhaps two access points in separate offices located next door to each other or between floors. Signal disruption will result if channel overlap exists between the access points. The solution is to try to move the access point to avoid the problem with the overlap, or change channels to one of the other nonoverlapping channels—for example, switch from channel 6 to channel 11.
You would typically change the channel of a wireless device only if a channel overlap occurs with another device. If a channel must be changed, it must be changed to another nonoverlapping channel.
Note
Troubleshooting utilities When troubleshooting a wireless problem in Windows, you can use the ipconfig command to see the status of IP configuration. Similarly, you can use the ifconfig command in Linux. In addition, Linux users can use the iwconfig command to view the state of your wireless network adapter. Using iwconfig, you can view such important information as the link quality, AP MAC address, data rate, and encryption keys, which can be helpful in ensuring that the parameters within the network are consistent.
Exam Alert
Channel separation IEEE 802.11g/b wireless systems communicate with each other using radio frequency signals in the band between 2.4GHz and 2.5GHz. Neighboring channels are 5MHz apart. Applying two channels that allow the maximum channel separation will decrease the amount of channel cross talk and provide a noticeable performance increase over networks with minimal channel separation.
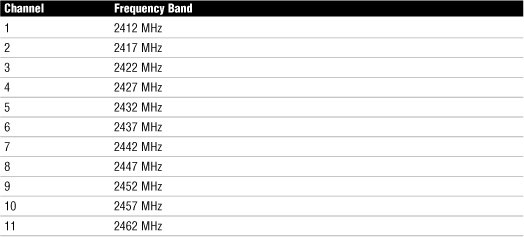
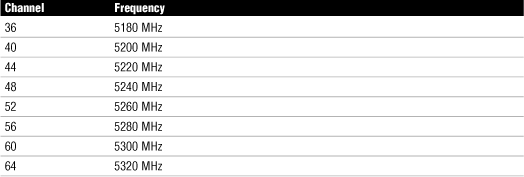
Table 7.2 outlines the available wireless channels. When deploying a wireless network, it is recommended that you use channel 1, grow to use channel 6, and add channel 11 when necessary, because these three channels do not overlap.
Table 7.2 RF Channels for 802.11b/g
Note
Why do they overlap? When looking at Table 7.2, remember that the RF channels listed (2412 for channel 1, 2417 for 2, and so on) are actually the center frequency that the transceiver within the radio and access point uses. There is only 5MHz separation between the center frequencies, and an 802.11b signal occupies approximately 30MHz of the frequency spectrum. As a result, data signals fall within about 15MHz of each side of the center frequency and overlap with several adjacent channel frequencies. This leaves you with only three channels (channels 1, 6, and 11 for the U.S.) that you can use without causing interference between access points.
Table 7.3 shows the channel ranges for 802.11a. 802.11n has the option of using both channels used by 802.11a and b/g.
Table 7.3 RF Channels for 802.11a
Note
War driving The advent of wireless networking has led to a new phenomenon: war driving. Armed with a laptop with an 802.11b/g wireless NIC, it is possible to drive around metropolitan areas seeking out wireless networks. When one is found, users can attempt to gain access to the network over the wireless connection. Such practices are illegal, although little can be done to prevent them other than using the built-in security features of 802.11. The problem is, not many installations use these features. If you are responsible for a network that has a wireless element, be sure to implement all the security features available. Not doing so is tantamount to letting anyone into your building and letting him use one of your PCs to access the server.
Spread Spectrum Technology
Spread spectrum refers to the manner in which data signals travel through a radio frequency. With spread spectrum, data does not travel straight through a single RF band; this type of transmission is known as narrowband transmission. Spread spectrum requires that data signals either alternate between carrier frequencies or constantly change their data pattern. Although the shortest distance between two points is a straight line (narrowband), spread spectrum is designed to trade off bandwidth efficiency for reliability, integrity, and security. Spread spectrum signal strategies use more bandwidth than in the case of narrowband transmission, but the trade-off is a data signal that is clearer and easier to detect. This chapter reviews three types of spread spectrum technologies: frequency hopping, direct sequence, and Orthogonal Frequency Division Multiplexing.
Frequency-Hopping Spread Spectrum (FHSS) Technology
Frequency-Hopping Spread Spectrum (FHSS) requires the use of narrowband signals that change frequencies in a predictable pattern. The term frequency hopping refers to hopping of data signals between narrow channels. For example, consider the 2.4GHz frequency band used by 802.11b. This range is divided into 70 narrow channels of 1MHz each. Somewhere between 20 and several hundred milliseconds, the signal hops to a new channel following a predetermined cyclical pattern.
Because data signals using FHSS switch between RF bands, they have a strong resistance to interference and environmental factors. The FHSS signal strategy makes it well suited for installations designed to cover a large geographical area and where the use of directional antennas to minimize the influence of environmental factors is not possible.
FHSS is not the preferred spread spectrum technology for today’s wireless standards. However, FHSS is used for some lesser-used standards and for cellular deployments for fixed Broadband Wireless Access (BWA), where the use of DSSS is virtually impossible because of its limitations.
Direct-Sequence Spread Spectrum (DSSS) Technology
With Direct-Sequence Spread Spectrum (DSSS) transmissions, the signal is spread over a full transmission frequency spectrum. For every bit of data that is sent, a redundant bit pattern is also sent. This 32-bit pattern is called a chip. These redundant bits of data provide for both security and delivery assurance. Transmissions are safe and reliable because the system sends so many redundant copies of the data, and only a single copy is required to have complete transmission of the data or information. DSSS can minimize the effects of interference and background noise.
As for a comparison between the two, DSSS has the advantage of providing higher security and signal delivery than FHSS, but it is a sensitive technology, affected by many environmental factors.
Orthogonal Frequency Division Multiplexing
Orthogonal Frequency Division Multiplexing (OFDM) is a transmission technique that transfers large amounts of data over 52 separate, evenly spaced frequencies. OFDM splits the radio signal into these separate frequencies and simultaneously transmits them to the receiver. By splitting the signal and transferring over different frequencies, the amount of cross talk interference is reduced. OFDM is associated with 802.11a, 802.11g amendments, and 802.11n wireless standards.
FHSS, DSSS, OFDM, and 802.11 Standards
The original 802.11 standard had two variations, both offering the same speeds but differing in the RF spread spectrum used. One of the original 802.11 standards used FHSS. This 802.11 variant used the 2.4GHz radio frequency band and operated with a 1 or 2Mbps data rate. Since this original standard, wireless implementations have favored DSSS.
The second 802.11 variation uses DSSS and specifies a 2Mbps peak data rate with optional fallback to 1Mbps in very noisy environments. 802.11, 802.11b, and 802.11g use the DSSS spread spectrum. This means that the underlying modulation scheme is similar between each standard, allowing all DSSS systems to coexist with 2, 11, and 54Mbps 802.11 standards. As a comparison, it is like the migration from the older 10Mbps ethernet networking to the more commonly implemented 100Mbps standard. The speed was different, but the underlying technologies were similar, allowing for an easier upgrade.
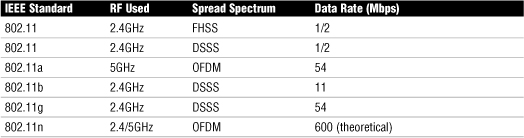
Table 7.4 provides a comparison of wireless standards and spread spectrum used.
Table 7.4 Comparison of IEEE 802.11 Standards
Establishing Communications Between Wireless Devices
To work with wireless networks, it is important to have a basic understanding of the communication that occurs between wireless devices. If using an infrastructure wireless network design, there are two key parts to the network: the wireless client, also known as the station (STA), and the AP. The AP acts as a bridge between the STA and the wired network.
As with other forms of network communication, before transmissions between devices can occur, the wireless AP and the client must first begin to talk to each other. In the wireless world, this is a two-step process involving association and authentication.
The association process occurs when a wireless adapter is first turned on. The client adapter immediately begins to scan across the wireless frequencies for wireless APs, or if using ad-hoc mode, other wireless devices. When the wireless client is configured to operate in infrastructure mode, the user can choose a wireless AP to connect with. This process may also be automatic with the AP selection based on the SSID, signal strength, and frame error rate. Finally, the wireless adapter switches to the assigned channel of the selected wireless AP and negotiates the use of a port.
If at any point, the signal between the devices drops below an acceptable level, or if the signal becomes unavailable for any reason, the wireless adapter initiates another scan looking for an AP with stronger signals. When the new AP is located, the wireless adapter selects the new AP and associates with it. This is known as reassociation.
Note
Roaming around The 802.11 standards allows a wireless client to roam between multiple APs. An AP transmits a beacon signal every so many milliseconds and includes a time stamp for client synchronization and an indication of supported data rates. A client system uses the beacon message to identify the strength of the existing connection to an AP. If the connection is too weak, the roaming client attempts to associate itself with a new AP. This allows the client system to roam between distances and APs.
With the association process complete, the authentication process begins. After the devices associate, keyed security measures are applied before communication can take place. On many APs, authentication can be set to either shared key authentication or open authentication. The default setting is typically open authentication. Open authentication enables access with only the SSID and/or the correct WEP key for the AP. The problem with open authentication is that if you don’t have other protection or authentication mechanisms in place, your wireless network is totally open to intruders. When set to shared-key mode, the client must meet security requirements before communication with the AP can occur.
After security requirements are met, you have established IP-level communication. This means that wireless standard requirements have been met, and ethernet networking takes over. Basically, a switch occurs between 802.11 to 802.3 standards. The wireless standards create the physical link to the network, allowing regular networking standards and protocols to use the link. This is how the physical cable is replaced, but to the networking technologies there is no difference between regular cable media or wireless media.
Several components combine to enable wireless communications between devices. Each of these must be configured on both the client and the AP:
• (Extended)Service Set Identifier (SSID/ESSID)—Whether your wireless network is using infrastructure mode or ad-hoc mode, an SSID is required. The SSID is a configurable client identification that allows clients to communicate to a particular base station. Only client systems configured with the same SSID as the AP can communicate with it. SSIDs provide a simple password arrangement between base stations and clients.
• Wireless channel—RF channels are important parts of wireless communications. A channel refers to the band of frequency used for the wireless communication. Each standard specifies the channels that can be used. The 802.11a standard specifies radio frequency ranges between 5.15 and 5.875GHz. In contrast, 802.11b and 802.11g standards operate between the 2.4 to 2.4835GHz ranges. Fourteen channels are defined in the IEEE 802.11b/g channel set, 11 of which are available in North America.
• Security features—IEEE 802.11 provides for security using two methods, authentication and encryption. Authentication refers to the verification of the client system. In the infrastructure mode, authentication is established between an AP and each station. Wireless encryption services must be the same on the client and the AP for communication to occur.
Note
Default settings Wireless devices ship with default SSIDs, security settings, channels, passwords, and usernames. To protect yourself, it is strongly recommended that you change these default settings. Today, many Internet sites list the default settings used by manufacturers with their wireless devices. This information is used by people who want to gain unauthorized access to your wireless devices.
Beacon Management Frame
Within wireless networking is a frame type known as the beacon management frame (beacon). Beacons are an important part of the wireless network because it is their job to advertise the presence of the access point so systems can locate it. Wireless clients automatically detect the beacons and attempt to establish a wireless connection to the access point.
The beacon frame is sent out by the AP in an infrastructure network design. Client stations will only send out beacons if connected in an ad-hoc network design. There are several parts of the beacon frame, all of which are used by the client system to learn about the AP before attempting to join the network. This information includes the following:
• Channel information—The channel used by the AP.
• Supported data rates—The data transfer rates identified by the AP configuration.
• SSID—The name of the wireless network name.
• Time stamp—Synchronization information. The time stamp is used by the client system to synchronize its clock with the AP.
These beacons are transmitted from the AP about every 10 seconds. The beacon frames themselves add overhead to the network; therefore, some APs let you reduce the amount of beacons that are sent. With home networks, constant beacon information is not necessary.
Before a client system can attempt to connect to an AP, it must first be able to locate it. There are two methods for AP discovery: passive and active. In passive detection, the client system listens for the beacon frames to discover the AP. After it is detected, the beacon frame provides the information necessary for the system to access the AP.
With active scanning, the client station transmits another type of management frame known as a probe request. The probe request goes out from the client system looking for a specific SSID or any SSID within its area. After the probe request is sent, all APs in the area with the same SSID will reply with another frame, the probe response. The information contained in the probe response is the same information included with the beacon frame. This information enables the client to access the system.
Exam Alert
Beacon Be prepared to identify the role of wireless beacons on the Network+ exam.
Configuring and Troubleshooting the Wireless Connection
Now that we have reviewed key wireless settings, let’s take a look at an actual wireless connection configuration. Figure 7.3 shows the configuration screen of a wireless access point.
Figure 7.3 Wireless configuration information.
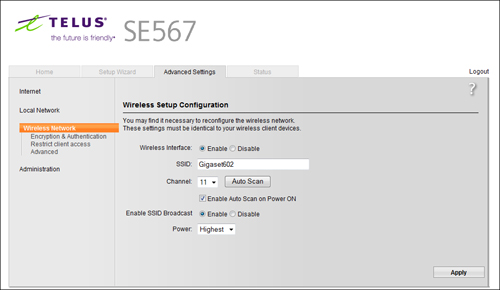
As you can see from the screen capture, the settings for this wireless router are clearly laid out. For instance, you can see that the wireless connection uses an SSID password of Gigaset602 and wireless channel 11. Each wireless access point may differ in the layout, but all have similar configuration options.
The configuration screen on a wireless AP allows you to adjust many settings for troubleshooting or security reasons. This section identifies some of the common settings and terms used on an AP.
• SSID—This configuration uses an SSID of Gigaset602. The SSID may be changed in large network to help identify its location or network segment.
As far as troubleshooting is concerned, if a client is not able to access a base station, make sure that they are both using the same SSID. Incompatible SSIDs are sometimes found when clients move computers, such as laptops, between different wireless networks. They obtain an SSID from one network, and, if the system is not rebooted, the old SSID won’t allow communication to a different base station.
• Channel—This connection is set to use channel 11. To access this network, all systems must use this channel. If needed, the channel can be changed using the drop-down menu. The menu lists channels 1 through 11.
• SSID Broadcast—In their default configuration, wireless access points typically broadcast the SSID name into the air at regular intervals. This feature of SSID broadcast is intended to allow clients to easily discover the network and roaming between WLANs. The problem with SSID broadcasting is that it makes it a little easier to get around security. SSIDs are not encrypted or protected in any way. Anyone can snoop and get a look at the SSID and attempt to join the network.
• Authentication—Typically, you can set three options for the authentication to be used:
• WEP-open—WEP-open is the simplest of the three authentications methods because it does not perform any type of client verification. It is a very weak form of authentication because there is no proof of identity.
• WEP-shared—WEP-shared requires that a WEP key be configured on both the client system and the access point. This makes authentication with WEP-shared mandatory and therefore more secure for wireless transmission.
• WPA-PSK—Wi-Fi Protected Access with Pre-Shared Key (WPA-PSK) is a stronger form of encryption where keys are automatically changed and authenticated between devices after a specified period of time or after a specified number of packets has been transmitted.
• Wireless Mode—To access the network, the client must use the same wireless mode as the AP. Today most users will configure the network for 802.11g for the faster speeds or a combination of 802.11b/g because they are compatible.
• DTIM Period—Wireless transmissions can broadcast to all systems, that is they can send messages to all clients on the wireless network. Multiple broadcast messages are known as multicast or broadcast traffic. Delivery traffic indication message (DTIM) is a feature used to ensure that when the multicast or broadcast traffic is sent, all systems are awake to hear the message. The DTIM setting specifies how often the DTIM message is sent within the beacon frame. The DTIM setting by default is 1. This means that the DTIM message will be sent with every beacon. If the DTIM is set to 3, then every third beacon will include a wake up call.
• Maximum Connection Rate—The transfer rate is typically set to Auto by default. This allows the maximum connection speed. However, it is possible to drop the speed down to increase the distance that the signal travels and boost signal strength due to poor environmental conditions.
• Network Type—This is where the network can be set to use the ad-hoc or infrastructure network design.
Exam Alert
AP settings For the Network+ exam, ensure you can identify the various settings used to establish connection between a client and an AP.
Troubleshooting Wireless Signals
Because wireless signals travel through the atmosphere, they are susceptible to different types of interference than standard wire networks. Interference weakens wireless signals and is therefore an important consideration when working with wireless networking.
Interference is unfortunately inevitable, but the trick is to minimize the levels of interference. Wireless LAN communications are typically based on radio frequency signals that require a clear and unobstructed transmission path.
The following are some factors that cause interference:
• Physical objects—Trees, masonry, buildings, and other physical structures are some of the most common sources of interference. The density of the materials used in a building’s construction determines the number of walls the RF signal can pass through and still maintain adequate coverage. Concrete and steel walls are particularly difficult for a signal to pass through. These structures will weaken or at times completely prevent wireless signals.
• Radio frequency interference—Wireless technologies such as 802.11b/g use an RF range of 2.4GHz, and so do many other devices, such as cordless phones, microwaves, and so on. Devices that share the channel can cause noise and weaken the signals.
• Electrical interference—Electrical interference comes from devices such as computers, refrigerators, fans, lighting fixtures, or any other motorized devices. The impact that electrical interference has on the signal depends on the proximity of the electrical device to the wireless access point. Advances in wireless technologies and in electrical devices have reduced the impact these types of devices have on wireless transmissions.
• Environmental factors—Weather conditions can have a huge impact on wireless signal integrity. Lightning, for example, can cause electrical interference, and fog can weaken signals as they pass through.
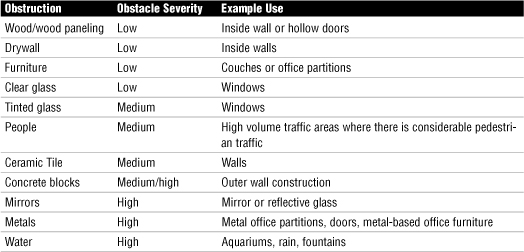
Many wireless implementations are found in the office or at home. Even when outside interference such as weather is not a problem, plenty of wireless obstacles exist around the office. Table 7.5 highlights a few examples to be aware of when implementing a wireless network indoors.
Table 7.5 Wireless Obstacles Found Indoors
Note
Wireless and water Water is a major interference factor for 2.4GHz wireless networks because water molecules resonate at the frequency in the 2.4GHz band. Interestingly, microwaves cause water molecules to resonate during cooking, which interferes with 2.4GHz RF.
Note
Signal strength Wireless signals degrade depending on the construction material used. Signals passing through concrete and steel are particularly weakened.
Troubleshooting Access Point Coverage
Like any other network media, APs have a limited transmission distance. This limitation is an important consideration when deciding where an AP should be placed on the network. When troubleshooting a wireless network, pay close attention to the distance client systems are from the AP.
When faced with a problem where client systems cannot consistently access the AP, you could try moving the access point to better cover the area, but then you may disrupt access for users in other areas. So what can be done to troubleshoot AP coverage?
Depending on the network environment, the quick solution may be to throw money at the problem and purchase another access point, cabling, and other hardware to expand the transmission area. However, you can try a few options before installing another wireless access point. The following list starts with the least expensive solution and progresses to the most expensive:
• Increase transmission power—Some access points have a setting to adjust the transmission power output. By default, most of these settings will be set to the maximum output; however, it is worth verifying just in case. As a side note, the transmission power can be decreased if you’re trying to reduce the dispersion of radio waves beyond the immediate network. Increasing the power provides clients stronger data signals and greater transmission distances.
• Relocate the AP—When wireless client systems suffer from connectivity problems, the solution may be as simple as relocating the AP to another location. It may be that it is relocated across the room, a few feet away, or across the hall. Finding the right location will likely take a little trial and error.
• Adjust or replace antennas—If the access point distance is not sufficient for some network clients, it may be necessary to replace the default antenna used with both the AP and the client with higher-end antennas. Upgrading an antenna can make a big difference in terms of transmission range. Unfortunately, not all APs have replaceable antennas.
• Signal amplification—RF amplifiers add significant distance to wireless signals. An RF amplifier increases the strength and readability of the data transmission. The amplifier provides improvement of both the received and transmitted signals, resulting in an increase in wireless network performance.
• Use a repeater—Before installing a new AP, you may first want to think about a wireless repeater. When set to the same channel as the AP, the repeater takes the transmission and repeats it. So, the AP transmission gets to the repeater and then the repeater duplicates the signal and passes it forward. It is an effective strategy to increase wireless transmission distances.
Note
Signal strength Wireless signals degrade depending on the construction material used. Signals passing through concrete and steel are particularly weakened.
Review Break
Wireless Troubleshooting Checklist
Poor communication between wireless devices has many potential causes. The following is a review checklist of wireless troubleshooting presented in this chapter:
• Auto transfer rate—By default, wireless devices are configured to use the strongest, fastest signal. If you’re experiencing connectivity problems between wireless devices, try using the lower transfer rate in a fixed mode to achieve a more stable connection. For example, you can manually choose the wireless transfer rate and instead of using 11Mbps, the highest rate for 802.11b, try 5.5Mbps, 2Mbps, or 1Mbps. The higher the transfer rate, the shorter the connection distance.
• AP placement—If signal strength is low, try moving the access point to a new location. Moving it just a few feet can make the difference.
• Antenna—The default antenna shipped with wireless devices may not be powerful enough for a particular client system. Better quality antennas can be purchased for some APs, which will boost the distance the signal can go.
• Building obstructions—Wireless RF communications are weakened if they have to travel through obstructions such as metal and concrete.
• Conflicting devices—Any device that uses the same frequency range as the wireless device can cause interference. For example, 2.4GHz phones can cause interference with devices using the 802.11g standard.
• Wireless channels—If connections are inconsistent, try changing the channel to another nonoverlapping channel.
• Protocol issues—If an IP address is not assigned to the wireless client, an incorrect SSID or incorrect WEP settings can prevent a system from obtaining IP information.
• SSID—The SSID number used on the client system must match the one used on the AP. Typically, the default SSID assigned is sufficient but may need to be changed if switching a laptop between different WLANs.
• WEP—If WEP is enabled, the encryption type must match what is set up in the AP.
Exam Alert
Troubleshooting The Network+ exam will likely test knowledge on basic wireless troubleshooting. Be sure to review this section before taking the Network+ exam.
Securing Wireless Networks
Many strategies and protocols are used to secure LAN and WAN transmissions. What about those network transmissions that travel over the airwaves? In the past few years wireless networking has changed the look of modern networks, bringing with it an unparalleled level of mobility and a host of new security concerns.
Wireless LANs (WLANs) require new protocols and standards to handle security for radio communications. As it stands today, wireless communications represent a significant security concern. When working with wireless, you need to be aware of a few wireless security standards, including Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA), and 802.1X. Before we get to describing each, let’s define a few terms.
Defining Access Control, Authentication, Authorization, and Encryption
Wireless security, like all computer security, is about controlling access to data and resources. It is important to understand the difference between authentication, authorization, and access control. Though these terms are sometimes used interchangeably, they refer to distinct steps that must be negotiated successfully to determine whether a particular request for a resource will result in that resource actually being returned. This is true for both a wired and wireless network.
Access control refers to any mechanism, software or hardware, used to restrict availability to network resources. To secure a network, it is necessary to determine which users will be granted access to various resources. Access control provides the design strategies necessary to ensure that only permitted users have access to such resources. It is a fundamental concept and forms the basis of a strong and secure network environment.
Although the concept of access control is easily understood, implementing it can be complex. Access to every network resource, including files, folders, hard disks and Internet access, must be controlled. This is a difficult task in large network environments.
Exam Alert
Access control The primary objective of access control is to preserve and protect the confidentiality, integrity, and availability of information, systems, and resources.
Authentication verifies the identity of the computer or user attempting to access a particular resource. Authentication is most commonly done with the presentation of credentials such as a username and a password. More sophisticated identification methods can include the use of the following:
• Smart cards
• Biometrics
• Voice recognition
• Fingerprints
Authorization determines whether the person, previously identified and authenticated, is allowed access to a particular resource. This is commonly determined through group association; that is, a particular group may have a specific level of security clearance. For instance, a group security policy may allow the school secretaries access to some data while locking students out.
Encryption is the process of encoding the data sent over remote connections, and it involves scrambling the usernames and passwords used to gain access to the remote network. Encryption is the process of encoding data using a mathematical algorithm that makes it difficult for unauthorized users to read the data if they are able to intercept it. The algorithm is actually a mathematical value known as a key. The key is required to read the encrypted data. Encryption techniques use public and private keys; public keys can be shared, and private keys cannot.
A key is a binary number that has a large number of bits. As you might imagine, the bigger the number or key, the more difficult it is to guess. Today, simple encryption strategies use 40 to 56 bits. On a 40-bit encryption, there are 240 possible keys; 56-bit encryption has 256 possible keys. That’s a lot of keys. Remember that without the correct key, the data cannot be accessed. Although the number of keys associated with lower-grade encryption may seem amazing, they have been cracked by some very high-end, specialized systems. That makes necessary higher-grade encryption: Many online transactions require 128-bit encryption, and other applications support encryption as high as 1,024 bits. (If you have time, try to calculate the key combinations for these higher-grade encryption strategies.)
Wireless Authentication and Encryption Methods
Now that we have a better idea of what authorization, authentication, and encryption are, we can look at the protocols and methods used to achieve wireless security. As an administrator for a wireless network, you will certainly be using these security features, and you will certainly be asked questions about them on the Network+ exam.
Exam Alert
Wireless security The Network+ exam will have questions about wireless security, including WEP and WPA. Be sure you can identify wireless security protocols before taking the exam.
Wired Equivalent Privacy (WEP)
Wired equivalent privacy (WEP) was the first attempt to keep wireless networks safe. WEP was designed to be easy to configure and implement, and originally it was hoped that WEP would provide the same level of security to wireless networks as was available to wired networks. For a time it was the best and only option for securing wireless networks.
WEP is an IEEE standard introduced in 1997 designed for securing 802.11 networks. With WEP enabled, each data packet transmitted over the wireless connection would be encrypted. Originally, the data packet was combined with a secret 40-bit number key as it passed through an encryption algorithm known as RC4. The packet was scrambled and sent across the airwaves. On the receiving end, the data packet passed through the RC4 backward, and the host received the data as it was intended. WEP originally used a 40-bit number key, but later specified 128-bit encryption, making WEP that much more robust.
WEP was designed to provide security by encrypting data from the sending and receiving devices. In a short period of time, however, it was discovered that WEP encryption was not nearly as secure as hoped. Part of the problem was that when the 802.11 standards were being written, security was not the major concern it is today. As a result, WEP security was easy to crack with freely available hacking tools. From this point, wireless communication was regarded as a potentially insecure transmission media.
There are two types of WEP security: static and dynamic WEP. Dynamic and static WEP differ in that dynamic WEP changes security keys periodically, or dynamically, making it more secure. Static WEP uses the same security key ongoing. The primary security risks are associated with static WEP, which uses a shared password to protect communications. Security weaknesses discovered in static WEP means that WLANs protected by it are vulnerable to several types of threats. Freely available hacking tools make breaking into static WEP-protected wireless networks a trivial task. Unsecured WLANs are obviously exposed to these same threats as well; the difference being that less expertise, time, and resources are required to carry out the attacks.
Wi-Fi Protected Access (WPA)
Security weaknesses associated with WEP provided administrators with a valid reason to be concerned with wireless security. The need for increased wireless security was important for wireless networking to reach its potential and to bring a sense of confidence for those with sensitive data to use wireless communications. In response, the Wi-Fi Protected Access (WPA) was created. WPA was designed to improve the security weaknesses of WEP and to be backward compatible with older devices using the WEP standard. WPA addressed two main security concerns:
• Enhanced data encryption—WPA uses a temporal key integrity protocol (TKIP), which scrambles encryption keys using a hashing algorithm. Then the keys are issued an integrity check to verify that they have not been modified or tampered with during transit.
• Authentication—Using the Extensible Authentication Protocol (EAP). WEP regulates access to a wireless network based on a computer’s hardware-specific MAC address, which is relatively simple to be sniffed out and stolen. EAP is built on a more secure public-key encryption system to ensure that only authorized network users can access the network.
Temporal Key Integrity Protocol (TKIP)
As mentioned previously, WEP lacked security. The Temporal Key Integrity Protocol (TKIP) was designed to address the shortcomings of the WEP security protocol. TKIP is an encryption protocol defined in IEEE 802.11i. TKIP was not only designed to increase security but also to use existing hardware, making it easy to upgrade to TKIP encryption.
TKIP is built on the original WEP security standard but enhances it by “wrapping” additional code both at the end and the beginning of the data packet. This additional code modifies the original code for additional security. Because TKIP is based on WEP, it too uses the RC4 stream encryption method but unlike WEP, TKIP encrypts each data packet with a stronger encryption key than available with regular WEP.
TKIP provides increased security for data communications, but it is far from the final solution. TKIP provides strong encryption for home user and nonsensitive data, but it may not provide a level of security necessary to protect corporate or more sensitive data while in transmission.
802.1X
802.1X is an IEEE standard specifying port-based network access control. 802.1X was not specifically designed for wireless networks; rather, it provides authenticated access for both wired and wireless networks. Port-based network access control uses the physical characteristics of a switched local area network (LAN) infrastructure to authenticate devices attached to a LAN port and to prevent access to that port in cases where the authentication process fails. There are three main components to the 802.1X framework:
• Supplicant—The system or node requesting access and authentication to a network resource.
• Authenticator—A control mechanism that allows or denies traffic to pass though a port.
• Authentication server—The authentication server validates the credentials of the supplicant that is trying to access the network or resource.
During a port-based network access control interaction, a LAN port adopts one of two roles: authenticator or supplicant. In the role of authenticator, a LAN port enforces authentication before it allows user access to the services that can be accessed through that port. In the role of supplicant, a LAN port requests access to the services that can be accessed through the authenticator’s port. An authentication server, which can be either a separate entity or co-located with the authenticator, checks the supplicant’s credentials on behalf of the authenticator. The authentication server then responds to the authenticator, indicating whether the supplicant is authorized to access the authenticator’s services.
The authenticator’s port-based network access control defines two logical access points to the LAN through one physical LAN port. The first logical access point, the uncontrolled port, allows data exchange between the authenticator and other computers on the LAN, regardless of the computer’s authorization state. The second logical access point, the controlled port, allows data exchange between an authenticated LAN user and the authenticator.
In a wireless network environment, the supplicant would typically be a network host, the authenticator could be the wireless network switch or AP, and the role of authentication server would be played by a Remote Authentication Dial-In User Service (RADIUS).
RADIUS is a protocol that allows a single server to become responsible for all remote access authentication, authorization, and auditing (or accounting) services. RADIUS functions as a client/server system. The remote user dials in to the remote access server, which acts as a RADIUS client, or network access server (NAS), and connects to a RADIUS server. The RADIUS server performs authentication, authorization, and auditing (or accounting) functions and returns the information to the RADIUS client (which is a remote-access server running RADIUS client software); the connection is either established or rejected based on the information received.
Summary
Several wireless standards fall under the 802.11 banner, including 802.11a, 802.11b, 802.11g, and 802.11n. Each of these standards has different characteristics, including speed, range, and RF used. Wireless networks are typically implemented using ad-hoc or infrastructure network design. Many types of interference can weaken the wireless signals, including weather, obstructions such as trees or walls, and RF interference.
Three types of spread spectrum technologies are reviewed in this chapter: frequency hopping, direct sequence, and Orthogonal Frequency Division Multiplexing. Each is associated with a particular wireless networking standard.
Many strategies and protocols are used to secure wireless transmissions, including Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA), and 802.1X. WEP was proven to be insecure but is still widely used. AP uses TKIP to encrypt potentially sensitive data. RADIUS is also used to increase security and acts as an authentication server.
When configuring a wireless network, the client and the AP must be configured with the same characteristics. If the AP uses 802.11a, so must the client. The same holds true for the SSID and the security settings.
Key Terms
• AP
• Channels
• WPA
• WEP
• RADIUS
• TKIP
• SSID
• BSS
• ESSID
Apply Your Knowledge
Exercises
7.1 Configuring infrared networking in Windows XP
You want to manage infrared communications on your Windows XP systems. On one computer you need to prevent other computers from sending files to your computer, and on the other computer, you need to verify that infrared is available on the system.
This exercise assumes that you are using Windows XP and have infrared networking capability.
Estimated time: 10 minutes
To enable or prevent receiving files over infrared links, perform the following steps:
1. From the Start menu, select the Control Panel option and then double-click the Wireless Link applet. (Use the Control Panel in Classic View for this exercise.)
2. To allow your Windows XP system to receive files over an infrared link, select the Allow Others to Send Files to Your Computer Using Infrared Communications option.
3. To prevent your Windows XP system from receiving files, make sure that the Allow Others to Send Files to Your Computer Using Infrared Communications option is cleared.
To verify infrared support on a computer, follow these steps:
1. Verify that the computer has an infrared transceiver. The transceiver is located somewhere on the outside of the computer and looks like a small dark red window.
2. To verify infrared functionality within Windows XP, open the Device Manager and double-click Infrared Devices.
3. If you have located an infrared transceiver on the outside and the infrared device option is not displayed in Device Manager, no infrared devices are recognized by the system.
4. Verify that infrared support is enabled in the BIOS. Enter your system’s BIOS configuration screen to verify whether IrDA devices are enabled. If the infrared device is disabled in BIOS, you might be able to use your computer’s BIOS setup to enable it.
5. If infrared devices are listed in the Device Manager but not enabled, verify that the infrared devices are installed correctly on your computer.
7.2 Configuring a Windows XP system to exclusively use a wireless infrastructure connection
Configuring and managing wireless connections is an increasing part of the network administrator’s role. Windows XP has built-in wizards and features to make working with wireless as easy as possible. In this exercise, we identify the setting used to determine whether a wireless connection is to be configured as an ad-hoc connection or an infrastructure connection.
This exercise assumes that the system has a wireless adapter installed.
Estimated time: 5 minutes
1. In Windows XP, choose Start, Control Panel. (Use the Control Panel in Classic View for this exercise.)
2. From within the Control Panel, double-click the Network Connections Applet to open the Network Connections dialog box.
3. Right-click the wireless connection and select Properties from the menu screen. This Wireless Network Connection Properties dialog box opens.
4. Select the Wireless Networks tab and then click the Advanced button on the lower-right side of the dialog box.
5. This displays a small dialog box with three options:
• Any Available Network (Access Point Preferred)
• Access Point (Infrastructure) Networks Only
• Computer-to-Computer (Ad Hoc) Networks Only
6. To configure the XP system to use only an infrastructure wireless connection, select the option button next to the Access Point (Infrastructure) Networks Only option. You will have to click Close for the window and click OK for the Wireless Network Connection Properties window. If you click Close and then Cancel, the changes will be dropped.
Exam Questions
1. Which of the following wireless protocols operates at 2.4GHz? (Select two.)
![]() A. 802.11a
A. 802.11a
![]() B. 802.11b
B. 802.11b
![]() C. 802.11g
C. 802.11g
![]() D. 802.11t
D. 802.11t
2. Under which of the following circumstances would you change the default channel on an access point?
![]() A. When there is a channel overlap between access points
A. When there is a channel overlap between access points
![]() B. To release and renew the SSID
B. To release and renew the SSID
![]() C. To increase the WEP security settings
C. To increase the WEP security settings
![]() D. To decrease WEP security settings
D. To decrease WEP security settings
3. A client on your network has had no problem accessing the wireless network, but recently the client moved to a new office. Since the move she has been unable to access the network. Which of the following is most likely the cause of the problem?
![]() A. The SSID on the client and the AP are different.
A. The SSID on the client and the AP are different.
![]() B. The SSID has been erased.
B. The SSID has been erased.
![]() C. The client has incorrect WEP settings.
C. The client has incorrect WEP settings.
![]() D. The client system has moved too far away from the access point.
D. The client system has moved too far away from the access point.
4. Which of the following best describes the function of beacons?
![]() A. Beacons monitor for wireless security issues.
A. Beacons monitor for wireless security issues.
![]() B. Beacons advertise the presence of an access point.
B. Beacons advertise the presence of an access point.
![]() C. Beacons prevent unauthorized access into an AP.
C. Beacons prevent unauthorized access into an AP.
![]() D. Beacons prevent unauthenticated access into an AP.
D. Beacons prevent unauthenticated access into an AP.
5. You have just purchased a new wireless access point that uses no WEP security by default. You change the security settings to use 128-bit encryption. How must the client systems be configured?
![]() A. All client systems must be set to 128-bit encryption.
A. All client systems must be set to 128-bit encryption.
![]() B. The client system will inherit security settings from the AP.
B. The client system will inherit security settings from the AP.
![]() C. WEP does not support 128-bit encryption.
C. WEP does not support 128-bit encryption.
![]() D. The client WEP settings have to be set to autodetect.
D. The client WEP settings have to be set to autodetect.
6. You have just been asked to configure the security settings for a new wireless network. You want the setting that offers the greatest level of security. Which of the following would you choose?
![]() A. WEP-open
A. WEP-open
![]() B. WEP-closed
B. WEP-closed
![]() C. WEP-shared
C. WEP-shared
![]() D. WEP-unshared
D. WEP-unshared
7. Which of the following best describes 802.11X?
![]() A. Port-based access control
A. Port-based access control
![]() B. Wireless standard specifying 11Mbps data transfer
B. Wireless standard specifying 11Mbps data transfer
![]() C. Wireless standard specifying 54Mbps data transfer
C. Wireless standard specifying 54Mbps data transfer
![]() D. Integrity-based access control
D. Integrity-based access control
8. You are installing a wireless network solution and require a standard that can operate using either 2.4GHz or 5GHz frequencies. Which of the following standards would you choose?
![]() A. 802.11a
A. 802.11a
![]() B. 802.11b
B. 802.11b
![]() C. 802.11g
C. 802.11g
![]() D. 802.11n
D. 802.11n
9. You are installing a wireless network solution that uses a feature known as MIMO. Which wireless networking standard are you using?
![]() A. 802.11a
A. 802.11a
![]() B. 802.11b
B. 802.11b
![]() C. 802.11g
C. 802.11g
![]() D. 802.11n
D. 802.11n
10. In the 802.1X security framework, which of the following best describes the role of supplicant?
![]() A. To authenticate usernames and passwords
A. To authenticate usernames and passwords
![]() B. To encrypt usernames and passwords
B. To encrypt usernames and passwords
![]() C. The system or node requesting access and authentication to a network resource
C. The system or node requesting access and authentication to a network resource
![]() D. A control mechanism that allows or denies traffic to pass through a port
D. A control mechanism that allows or denies traffic to pass through a port
11. Which of the following 802.11 standards can use the nonoverlapping channels of 1, 6, or 11? (Select two.)
![]() A. 802.11a
A. 802.11a
![]() B. 802.11b
B. 802.11b
![]() C. 802.11g
C. 802.11g
![]() D. 802.11h
D. 802.11h
12. Which of the following wireless security protocols uses TKIP?
![]() A. WEP-open
A. WEP-open
![]() B. WEP-shared
B. WEP-shared
![]() C. WPA
C. WPA
![]() D. WPA-shared
D. WPA-shared
13. Which of the following best describes the role of RADIUS?
![]() A. RADIUS allows a single IP address to become responsible for all remote access authentication.
A. RADIUS allows a single IP address to become responsible for all remote access authentication.
![]() B. RADIUS allows a single server to become responsible for all remote access authentication.
B. RADIUS allows a single server to become responsible for all remote access authentication.
![]() C. RADIUS encrypts all data leaving the AP.
C. RADIUS encrypts all data leaving the AP.
![]() D. RADIUS encrypts all data leaving the remote system.
D. RADIUS encrypts all data leaving the remote system.
14. Which of the following is associated with OFDM?
![]() A. 802.11n
A. 802.11n
![]() B. WEP
B. WEP
![]() C. WPA
C. WPA
![]() D. 802.11b
D. 802.11b
15. A user calls to inform you that she is unable to print. Upon questioning her, you determine that the user has just been moved from the second floor to the third floor. The user connects to the printer via a wireless router on the first floor. You need to allow the user to print but do not want to purchase another AP or disrupt other wireless users. Which of the following might you do?
![]() A. Move the AP to allow the client system to access the network and therefore the printer.
A. Move the AP to allow the client system to access the network and therefore the printer.
![]() B. Search for RF interference on the 2.4GHz range.
B. Search for RF interference on the 2.4GHz range.
![]() C. Change the channel.
C. Change the channel.
![]() D. Configure an RF repeater to forward the wireless communications.
D. Configure an RF repeater to forward the wireless communications.
16. You are deploying a wireless network and decide you need an antenna that provides a 360-degree dispersed wave pattern. Which of the following antennas would you select?
![]() A. Multipoint
A. Multipoint
![]() B. Unidirectional
B. Unidirectional
![]() C. Omnidirectional
C. Omnidirectional
![]() D. Dispersal
D. Dispersal
17. You are working with a wireless network that is using channel 1 (2412MHz). What RF range would be used if you switched to channel 3?
![]() A. 2417
A. 2417
![]() B. 2422
B. 2422
![]() C. 2427
C. 2427
![]() D. 2408
D. 2408
18. You are the network administrator for a small company. Recently you added two remote clients who access the network through an AP. To increase security you decide you need to keep the network name hidden. Which of the following could you do?
![]() A. Enable WEP broadcast
A. Enable WEP broadcast
![]() B. Disable WEP broadcast
B. Disable WEP broadcast
![]() C. Enable secure SSID broadcast
C. Enable secure SSID broadcast
![]() D. Disable SSID broadcast
D. Disable SSID broadcast
19. Which of the following wireless standards specifies an RF of 5GHz?
![]() A. 802.11a
A. 802.11a
![]() B. 802.11b
B. 802.11b
![]() C. 802.11g
C. 802.11g
![]() D. 802.11g
D. 802.11g
20. What is the maximum network speed defined by the 802.11b standard?
![]() A. 100Mbps
A. 100Mbps
![]() B. 5.5Mbps
B. 5.5Mbps
![]() C. 11Mbps
C. 11Mbps
![]() D. 10Mbps
D. 10Mbps
Answers to Exam Questions
1. B, C. Wireless standards specify an RF range on which communications are sent. The 802.11b and 802.11g standards use the 2.4GHz range. 802.11a is incorrect because it uses the 5GHz range, and 802.11t is not a valid standard. For more information, see the section “802.11 Wireless Standards” in this chapter.
2. A. Ordinarily the default channel used with a wireless device is adequate; however, it may be necessary to change the channel if there is overlap with another nearby access point. The channel should be changed to another nonoverlapping channel. Changing the channel would not impact the WEP security settings. For more information, see the section “Wireless Radio Channels” in this chapter.
3. D. An AP has a limited distance that it can send data transmissions. When a client system moves out of range, it won’t be able to access the AP. Many strategies exist to increase transmission distances, including RF repeaters, amplifiers, and buying more powerful antennas. The problem is not likely related to the SSID or WEP settings because the client had access to the network before and no settings were changed. For more information, see the section “Troubleshooting Access Point Coverage” in this chapter.
4. B. Beacons are an important part of the wireless network because they advertise the presence of the access point so systems can locate it. Wireless clients automatically detect the beacons and attempt to establish a wireless connection to the access point. Answers A, C and D are invalid. For more information, see the section “Beacon Management Frame” in this chapter.
5. A. On a wireless connection between an access point and the client, each system must be configured to use the same WEP security settings. In this case, they must both be configured to use 128-bit encryption. For more information, see the section “Wired Equivalent Privacy (WEP)” in this chapter.
6. C. Both WEP-open and WEP-shared are forms of wireless security. WEP-open is the simpler of the two authentications methods because it does not perform any type of client verification. It is a very weak form of authentication because there is no proof of identity. WEP-shared requires that a WEP key be configured on both the client system and the access point. This makes authentication with WEP-shared mandatory and therefore more secure for wireless transmission. For more information, see the section “Wireless Authentication and Encryption Methods” in this chapter.
7. A. 802.1X is an IEEE standard specifying port-based network access control. Port-based network access control uses the physical characteristics of a switched local area network (LAN) infrastructure to authenticate devices attached to a LAN port and to prevent access to that port in cases where the authentication process fails. For more information, see the section “802.1X” in this chapter.
8. D. The IEEE standard 802.11n can use either the 2.4GHz or 5GHz radio frequencies. 802.11a uses 5GHz, 802.11b uses 2.4GHz, as does the 802.11g standard. For more information, see the section “802.11 Wireless Standards” in this chapter.
9. D. MIMO is used by the 802.11n standard and takes advantage of multiplexing to increase range and speed of wireless networking. Multiplexing is a technique that combines multiple signals for transmission over a single line or media. MIMO enables the transmission of multiple data streams traveling on different antennas in the same channel at the same time. A receiver reconstructs the stream that has multiple antennas. For more information, see the section “The Magic Behind 802.11n” in this chapter.
10. C. There are three main components of the 802.1X security framework. The supplicant is the system or node requesting access and authentication to a network resource. The authenticator usually is a switch or AP that acts as a control mechanism allowing or denying traffic to pass though a port. Finally, the authentication server validates the credentials of the supplicant that is trying to the network or resource. For more information, see the section “802.1X” in this chapter.
11. B, C. The 802.11b and 802.11g standards use channels 1–11 in the 2.4GHz frequency range. Of the channels, 1, 6, and 11 are considered nonoverlapping, which means there is less chance for interference. For more information, see the section “802.11 Wireless Standards” in this chapter.
12. C. The WPA wireless security protocol uses TKIP (temporal key integrity protocol), which scrambles encryption keys using a hashing algorithm. Then the keys are issued an integrity check to verify that they have not been modified or tampered with during transit. TKIP encryption is not used with WEP. For more information, see the section “Wi-Fi Protected Access (WPA)” in this chapter.
13. B. RADIUS is a protocol that allows a single server to become responsible for all remote access authentication, authorization, and auditing (or accounting) services. RADIUS functions as a client/server system. For more information, see the section “802.1X” in this chapter.
14. A. Orthogonal Frequency Division Multiplexing (OFDM) is a transmission technique that transfers large amounts of data over 52 separate, even spaced frequencies. OFDM splits the radio signal into these separate frequencies and simultaneously transmits them to the receiver. By splitting the signal and transferring over different frequencies, the amount of cross talk interference is reduced. OFDM is associated with the 802.11n wireless standard. For more information, see the section “Orthogonal Frequency Division Multiplexing” in this chapter.
15. D. By the description, it sounds like the client has moved beyond the reach of the AP. To try to accommodate the client, an RF repeater could be used to duplicate and forward the wireless signal. It would not be wise to move the wireless access point because the move might put it out of reach for other network users. Changing the wireless channel would not help but would prevent the user from accessing the AP altogether. For more information, see the section “Troubleshooting Access Point Coverage” in this chapter.
16. C. An omnidirectional antenna is designed to provide a 360-degree dispersed wave pattern. This type of antenna is used when coverage in all directions from the antenna is required. Omnidirectional antennas are good to use when a broad-based signal is required. This is in contrast to a directional antenna, which works more for a point-to-point connection. For more information, see the section “Types of Wireless Antennas” in this chapter.
17. B. IEEE 802.11g/b wireless systems communicate with each other using radio frequency signals in the band between 2.4GHz and 2.5GHz. Neighboring channels are 5MHz apart. Therefore, channel 3 would use the 2422 RF (2412+5+5). For more information, see the section “Wireless Radio Channels” in this chapter.
18. D. Disabling the SSID broadcast would prevent the SSID name from being displayed on wireless systems. In their default configuration, wireless access points typically broadcast the SSID name into the air at regular intervals. This feature of SSID broadcast is intended to allow clients to easily discover the network and roaming between WLANs. The problem with SSID broadcasting is that it makes it a little easier to get around security. SSIDs are not encrypted or protected in any way. For more information, see the section “Configuring and Troubleshooting the Wireless Connection” in this chapter.
19. A. The 802.11a wireless standard uses the 5GHz frequency range. 802.11b/g use the 2.4GHz range. For more information, see the section “802.11 Wireless Standards” in this chapter.
20. C. The IEEE 802.11b standard for wireless networks defines a maximum speed of 11Mbps. 100Mbps is the defined speed for Fast Ethernet. 5.5Mbps is the speed specified in earlier wireless networking standards. 10Mbps is the maximum speed of standard ethernet. For more information, see the section “802.11 Wireless Standards” in this chapter.
Suggested Readings and Resources
• Perahia, Eldad and Robert Stacey. Next Generation Wireless LANs: Throughput, Robustness, and Reliability in 802.11n. Cambridge University Press, 2008.
• Geier, Jim. Implementing 802.1X Security Solutions for Wired and Wireless Networks. Wiley, 2008.
