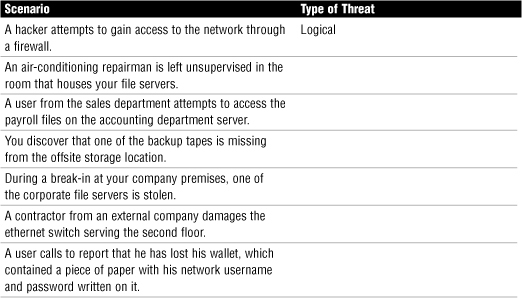
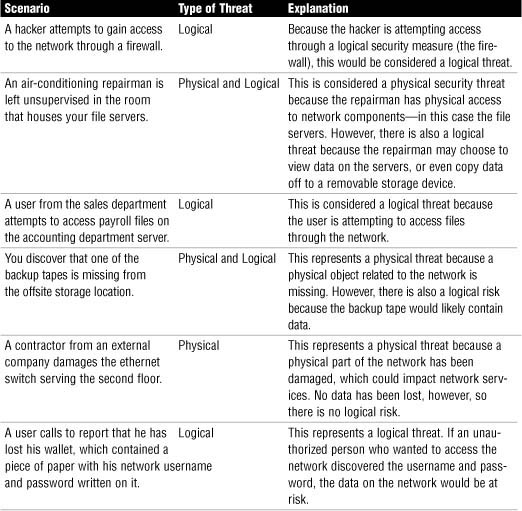
Chapter Fourteen
Network Access Security
Introduction
Today, more than ever, the security of networks is a major consideration for network administrators. Security risks come from seemingly everywhere, both from outside of the network from remote attackers and from malicious users from inside the network. Administrators have several tools to help mitigate the risks from attackers. This includes everything from protocols to firewalls.
To fully understand the security risks associated with the network, a network administrator must take a holistic view and consider every aspect, threat, and possible weakness. The network administrator must assume that someone will attempt to gain unauthorized access to the network or the systems attached to it at some point. This might sound a little dramatic, but plenty of network administrators can attest to the fact that it is a reality.
There are, of course, certain environments in which security is more of a concern than in others. If you work for, say, a bank or a branch of the government, security is likely to be a high priority. For a chain of florists in Fresno, network security is likely to be less of an issue, but it must still be considered.
Security today is not just about stopping corporate espionage or preventing theft of equipment. It’s about protecting the physical assets and, perhaps more important, the data of the organization. The cracker coming in through your firewall and entering 50 bogus orders for gift hampers might think it’s funny. Your boss is likely to find it less amusing.
Note
Hacker or cracker? The terms hacker and cracker are tossed about freely when it comes to network security, but the two terms describe very different individuals. A hacker is someone who attempts to disassemble or delve into a computer program with the intention of understanding how it works, normally to make it better. A cracker, on the other hand, is someone who attempts to gain access to a computer system or application without authorization, with the intention of using the application illegally or viewing the data. Crackers, not hackers, are the people network administrators need to be concerned with. However, over time, the term hacker has become synonymous with people who attempt to gain access to systems without permission, and the term cracker has fallen out of use.
In essence, security is about ensuring the privacy, integrity, and quality of a network’s data and the systems that hold it, with the purpose of ensuring business continuity. Determining what measures are required to ensure this security is the concern of the network administrator.
Understanding Network Security Threats
Before we look at the measures you can take to secure your network, let’s first look at what you are trying to protect against. The following are some possible threats to a network’s security:
• Internal threats—It is a sad fact that the most common source of security problems in an organization is from the employees of that organization. For example, a user might decide to “borrow” the apparently unused hub from the equipment cupboard on the third floor, or he might really want to know just how much money the president of the company earns. In more extreme cases, a user might attempt to pass valuable corporate information to an outside party. Sound far fetched? It’s not; it happens every day.
• Deliberate data damage—To most people, the idea of deliberately damaging someone else’s property is, to say the least, distasteful. Unfortunately, not everyone operates with the same values. Whether “just for fun” or with more shady intent, some people might delight in corrupting data or deleting it completely. Either way, business continuity will almost certainly be affected.
• Industrial espionage—This dramatic sounding security threat involves the process of a person retrieving data from a server for a purpose. The intruder might want to get her hands on the latest blueprints of your new widget, or she might want financial information for a buyout bid. Either way, the integrity (and in some cases, the future viability) of the business can be affected by such events.
• Physical equipment theft—Although it is normally less of an issue than theft of data, theft of physical equipment can still affect business continuity. If an important piece of equipment is stolen (for example, the server or a backup tape), the intruder will have access to your data. Insurance normally takes care of replacing the actual equipment, but data is generally not insured, unless specified, so the cost of restructuring the data is not provided for.
You might be fortunate enough not to suffer from any of these threats. Certainly, in a small organization that performs a seemingly uninteresting (to outsiders) business, there might not be any occurrences of security threats. But as an organization grows, so too do the amount of information, the number of methods that can be used to access it, and the number of people interested in finding out about the business. Also, as the number of employees grows, the chance that a “bad apple” will find its way into the cart increases as well.
Security Responsibilities of a Network Administrator
To combat possible security threats, what is expected of you, as a network administrator? The exact network security responsibilities you have depend on the kind of environment in which you are working. In large companies, an individual or a group might be responsible specifically for security issues. You might be part of that group or be under its direction. In small companies, the entire onus of network security might be placed on your—the network administrator’s—shoulders. This chapter assumes that as a network administrator you are primarily responsible for network security. Assume that you need to do the following to ensure network security in your organization:
• Ensure that a security policy is in place—A security policy defines the security measures, how they function, what is involved in their operation, and how problems are dealt with. The security policy should be created with the support of management.
• Ensure that the security policy is enforced—There is no point in having a policy if it is not enforced. As the network administrator, you need to make sure that the security policy works and is implemented as described.
• Ensure that any infractions of the security policy are dealt with—Perhaps the most undesirable part of a network administrator’s security responsibilities involves dealing with infractions of the security policy. Because the majority of security-related incidents occur with people inside the company, this can often be an unpleasant task.
• Ensure that the security situation is continually evaluated, revised, and updated—Networks change, as does the company structure. The security needs of an organization should be evaluated constantly. Any changes deemed necessary should be incorporated into the security policy, again with the cooperation of management.
This is a brief look at the responsibilities a network administrator has in implementing security on a network. Depending on the environment you work in, you might have to consider more or fewer security-related responsibilities. Now that you have an idea of some of the basic security responsibilities, let’s look at the two types of network security: physical and logical.
Physical and Logical Security
Security can be broken into two distinct areas: physical security and logical security. Physical security refers to the issues related to the physical security of the equipment that composes or is connected to the network. Physical security measures include controlling access to equipment, supervising visitors, controlling physical access to areas that contain networking equipment, and ensuring that removable media such as backup tapes are transported and stored securely.
Logical security is concerned with security of data held on devices connected to the network. Logical security involves controlling passwords and password policies, controlling access to data on servers through file system security, controlling access to backup tapes, and perhaps most important, preventing sources outside the network from gaining access to the network through a connection from another network, such as the Internet. Because logical security is a large and complex topic, this chapter covers only topics related to the Network+ exam and some supporting information.
Physical Security
Physical security is concerned with the prevention of unauthorized access to the physical equipment that makes up the network or the systems attached to it.
Perhaps the biggest consideration related to physical security is restricting access to networking equipment and servers. Most commonly, the people you are trying to protect against in this respect are the employees of the company rather than malicious outsiders. That said, there is always the chance that a miscreant may decide that it is easier to break in to your premises and steal a server rather than access data through a firewall.
Specific physical security considerations include the following:
• Controlling access to equipment—Networking equipment should be kept in a secure location. For example, you might have a dedicated, environmentally controlled room in which all the network servers and networking equipment are kept. Alternatively, as in many small organizations, networking equipment might be stored in a cupboard or even a rack. Wherever your equipment is located, access control systems (including locks and keys) should be in place to prevent unauthorized access.
• Creating and enforcing visitor policies—Even if you have a dedicated server room, it’s highly likely that other equipment will be in the room, such as telephone systems, air-conditioning units, and fire-protection systems. Each of these systems will have a scheduled maintenance program, which will periodically require visitors to be in the server room. Procedures should be in place so that the identities of visitors are verified, and that they are supervised when in the equipment room.
• Securing the area—The physical security of the network environment should be examined from a big-picture perspective. If a dedicated room is used for the server, determine the security of the room. Are there windows in the room that might represent a security risk? Are there windows that could facilitate someone outside the building seeing in? All these aspects and more must be factored in when considering physical security.
Exam Alert
Physical security The Network+ exam focuses much more on logical security than on physical security. For this reason, the discussion of physical security is confined to just the basics.
Network Hardware and Server Room Access
Access to the server room should be tightly controlled, and all access doors must be secured by some method, whether it is a lock and key or a retinal scanning system. Each method of server-room access control has certain characteristics. Whatever the method of server-room access, it should follow one common principle: control. Some access control methods provide more control than others.
Lock and Key
If access is controlled by lock and key, the number of people with a key should be restricted to only those people who need access. Spare keys should be stored in a safe location, and access to spare keys should be controlled.
Here are some of the characteristics of lock and key security:
• Inexpensive—Even a very good lock system will cost only a few hundred dollars.
• Easy to maintain—With no back-end systems and no configuration, using a lock and key is the easiest access control method.
• Less control than other methods—Keys can be lost, copied, and loaned to other people. There is no record of access to the server room and no way of proving that the key holder is entitled to enter.
Tip
Do not copy If you are using a lock and key for security, make sure that all copies of the original key are stamped “DO NOT COPY.” That way, it is more difficult for someone to get a copy because reputable key cutters will not make copies of such keys.
Swipe Card and PIN Access
If budgets and policies permit, swipe card and PIN (personal identification number) entry systems are good choices for managing physical access to a server room. Swipe card systems use a credit-card-sized plastic card that is read by a reader on the outside of the door. To enter the server room, you must swipe the card (run it through the reader), at which point it is read by the reader, which validates it. Usually, the swipe card’s use to enter the room is logged by the card system, making it possible for the logs to be checked. In higher-security installations, it is common to have a swipe card reader on the inside of the room as well so that a person’s exit can be recorded.
Although relatively few disadvantages exist to swipe card systems, they do need specialized equipment so that the cards can be coded with users’ information. They also have the same drawbacks as keys in that they can be lost or loaned to other people. Of course, the advantage that swipe cards have over key systems is that swipe cards are very hard to copy.
PIN pads can be used alone or with a swipe card system. PIN pads have the advantage of not needing any kind of card or key that can be lost. For the budget conscious, PIN pad systems that do not have any logging or monitoring capability can be purchased for a reasonable price. Here are some of the characteristics of swipe card and PIN pad systems:
• Moderately expensive—Some systems, particularly those with management capabilities, are quite expensive.
• Enhanced controls and logging—Each time a person enters the server room, he or she must key in a number or use a swipe card. This process enables systems to log who enters and when.
• Some additional knowledge required—Swipe card systems need special software and hardware that can configure the cards. Someone has to learn how to do this.
Biometrics
Although they may still seem like the realms of James Bond, biometric security systems are becoming far more common. Biometric systems work by utilizing some unique characteristic of a person’s identity—such as a fingerprint, a palm print, or even a retina scan—to validate that person’s identity.
Although the price of biometric systems has been falling over recent years, they are not widely deployed in small to mid-sized networks. Not only are the systems themselves expensive, but the installation, configuration, and maintenance of the systems must be considered. However, biometric solutions are becoming more common; for example, newer laptops can be bought with finger scanners built in. Following are some of the characteristics of biometric access control systems:
• Very effective—With biometrics, each person entering the server room must supply proof-of-person evidence. This can be harder to fake than getting a swipe card or stealing a password. Combing these methods can make it even harder to gain unauthorized access.
• Nothing to lose—Because there are no cards or keys, there is nothing that can be lost.
• Expensive—Biometric security systems and their attendant scanners and software are still relatively expensive and are affordable only by organizations with a larger budget, although prices are sure to drop as more people turn to this method of access control.
Hardware Room Best Practices
Apart from the physical and environmental considerations, server rooms or other areas containing equipment must be managed on a policy and procedural level. In view of this, it is important that procedures, a monitoring schedule, and server-room documentation be in place.
Tip
No-snack zone It may sound obvious, but server rooms should be “No food or drink” zones. To go to some of the lengths described here and then fall prey to a can of Cherry Coke or to nacho crumbs would be a little ironic. So, the rule is no food, no drinks, no exceptions. Post signs to remind server-room users of this rule. If you want to be really creative, you can add a shelf outside the server room so that those entering the server room can save their coffee or snack for later.
As with anything else relating to servers, the server environment should be well documented, and detailed procedures should be in place to cover all possible situations. Anyone working near the server should be made aware of the server environment procedures, and development and enforcement of the procedures should have the backing of management.
Server-room procedures should define the following:
• Visitor policies—As discussed earlier, the server environment might not be used exclusively for server hardware, and people other than server administrators might need access to the area. In addition, outside contractors might need to access the server environment. Procedures should state such things as whether outside contractors must be escorted at all times and what identification should be verified before outsiders are granted access to the server area. You would not let engineers from the local utility company come into your home without identification, so why would you let them into your server room without seeing ID?
• Fire-drill procedures—Procedures should include guidelines for handling inert gas systems. Different procedures might be needed for a test drill. Procedures should also detail at what intervals fire detection systems are tested and at what intervals they are serviced. Although the companies that service such systems are normally very good at reminding you when the system is due for service, it should be noted who is responsible for checking this fact.
• Flood actions—As with fire, the procedures should provide information on what actions to take in case of flood detection. If appropriate, the procedures should include the location of valves that can be turned off to limit the flooding, as well as details of whom should be contacted in the event of flooding. Procedures should also define at what point equipment should be removed from the affected area.
• Staff turnover—Providing access control mechanisms means that procedures must be in place to cope with employees leaving the organization. The related procedures should define what steps should be taken. These steps may include the changing of network passwords, removal of user IDs, and, in exceptional cases, the changing of door locks.
• Detailed contact charts—The procedures should also include information on any internal and external contacts who may need to be notified in case of an incident.
Logical Security
Logical security is a much more involved subject than physical security. Not only are there more ways in which data can be threatened logically than physically, but the measures available to secure data are equally diverse. Logical security focuses on the security protocols and procedures to protect data from both internal and remote network users. Logical security measures include authentication (such as username/password), determining access rights (authorization), tracking security logs (accountability). Logical security measures such as authentication, authorization and accountability are discussed in Chapter 15, “Security Technologies and Malicious Software.”
Firewalls
A firewall is considered a logical security measure and one of the cornerstone concepts for network security.
A firewall is a either a hardware device or a software application that sits at the edge of the network controlling the flow of traffic between two or more networks. Through configured settings, the firewall controls the type of traffic that is allowed to flow between networks. The most common use of a firewall is to protect a private network from a public network such as the Internet. However, firewalls are also used as a means to separate a sensitive area of a private network from other, less-sensitive, areas of the private network.
At its most basic, a firewall is a device (it could be a computer system or a dedicated hardware device) that has more than one network interface and manages the flow of network traffic between those interfaces. How it manages the flow and what it does with certain types of traffic depend on its configuration. Figure 14.1 shows the most basic firewall configuration.
Figure 14.1 A basic firewall implementation.
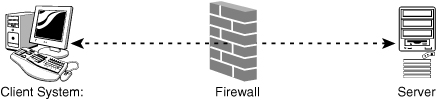
Strictly speaking, a firewall performs no action on the packets it receives besides the basic functions just described. However, in a real-world implementation, a firewall is likely to offer other functionality, such as Network Address Translation (NAT) and proxy server services. The additional features used with firewalls are discussed in the following section.
When working with firewalls, you may hear the terms host-based and network-based firewalls. Network-based firewall systems are those that monitor traffic on the entire network segment. Typically, a firewall server monitors and controls traffic to the entire network. An administrator monitors and controls the firewall services from a central location. A host-based firewall is installed on an individual system and monitors and controls inbound and outbound traffic for just that system. In general terms, this is how they operate, but which is better? It all depends; they each have their pros and cons. Table 14.1 compares the characteristics of a host-based and network-based firewall system.
Table 14.1 Comparing Host-Based and Network-Based Firewalls
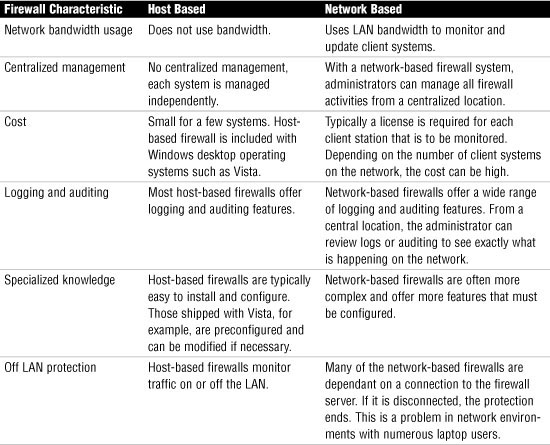
So which do you choose? It may boil down to whether you are an administrator or network user. In a LAN or WAN, you are likely to see network-based firewall systems. Network-based firewalls are centralized, making it possible for the administrator to update, manage, and monitor the firewall from a single location. All this would be virtually invisible to the end user. Many network administrators opt for the control and ease that a network-based solution holds.
Remote users, with laptops that leave the LAN or WAN, may want a host-based firewall solution that stays active whether they are connected to the LAN or not. Host-based firewalls are versatile for movement and ensure that the system stays protected. However, it is much more difficult for administrators to track and review log files and updates on systems on a one-to-one basis.
The Purpose and Function of a Firewall
Although the fundamental purpose of a firewall is to protect one network from another, you need to configure the firewall to allow some traffic through. If you don’t need to allow traffic to pass through a firewall, you can dispense with it entirely and completely separate your network from other networks.
A firewall can employ a variety of methods to ensure security. In addition to the role just described, modern firewall applications can perform a range of other functions, often through the addition of add-on modules. These functions can include the following:
• Content filtering—Most firewalls can be configured to provide some level of content filtering. This can be done for both inbound and outbound content. For instance, the firewall can be configured to monitor inbound content restricting certain locations or particular websites. Firewalls can also limit outbound traffic by prohibiting access to certain websites by maintaining a list of URLs and IP addresses. This is often done when organizations want to control employees’ access to Internet sites.
• Signature identification—A signature refers to a unique identifier for a particular application. In the antivirus world, a signature is an algorithm that uniquely identifies a specific virus. Firewalls can be configured to detect certain signatures that are associated with malware or other undesirable applications and block them before they enter the network.
• Virus scanning services—As web pages are downloaded, firewalls can check content within the pages for viruses. This feature is becoming increasingly attractive to companies that are concerned about the potential threats from Internet-based sources.
• Network address translation (NAT)—To protect the identity of machines on the internal network, and to allow more flexibility in internal TCP/IP addressing structures, many firewalls (and proxy servers—see the next section) translate the originating address of data into a different address, which is then used on the Internet. Network address translation is a popular function because it works around the limited availability of TCP/IP addresses.
• URL filtering—By using a variety of methods, the firewall can choose to block certain websites from being accessed by clients within the organization. This blocking allows companies to control what pages can be viewed and by whom.
• Bandwidth management—Although required only in certain situations, bandwidth management can prevent a certain user or system from hogging the network connection. The most common approach to bandwidth management is to divide the available bandwidth into sections and then make just a certain section available to a user or system.
These functions are not strictly firewalling activities. However, the flexibility offered by a firewall, coupled with its placement at the edge of a network, make a firewall the ideal base for controlling access to external resources.
The following sections describe stateful and stateless firewalls, firewall methods, and the purpose and configuration of a demilitarized zone.
Stateful and Stateless Firewalls
When talking about firewalls, two terms will often come up: stateful and stateless firewalls. These two terms differentiate how firewalls operate. A stateless firewall, sometimes called a packet-filtering firewall, monitors specific data packets and restricts or allows access to the network based on certain criteria. Stateless firewalls look at each data packet in isolation and as such are not aware whether that particular data packet is part of a larger data stream. Essentially, stateless firewalls do not see the big picture or “state” of data flow, only at the individual packets.
Today, we are more likely to use stateful firewalls. Stateful firewalls monitor data traffic streams from one end to the other. A stateful firewall will refuse unsolicited incoming traffic that does not comply with dynamic or preconfigured firewall exception rules. A stateful firewall tracks the state of network connections watching data traffic, including monitoring source and destination addresses and TCP and UDP port numbers.
Exam Alert
Stateless firewall For the Network+ exam, remember that a stateless firewall examines the information within a data packet and rejects or accepts the packet based on the source or destination address or port number listed within the packet header.
Firewall Methods
This section discusses the various firewall methods commonly used: packet-filtering firewalls, circuit-level firewalls, and application-layer firewalls.
Tip
Three firewall methods The three firewall methods described in this chapter are often combined into a single firewall application. Packet filtering is the basic firewall function. Circuit-level functionality provides NAT, and an application gateway firewall provides proxy functionality.
Network Layer Firewalls
A network layer (also known as a packet-filtering firewall) firewall examines each packet that passes through it and determines what to do with it, based on the configuration. A network layer firewall deals with packets at the network layer of the Open Systems Interconnect (OSI) model. The following are some of the criteria by which packet filtering can be implemented:
• IP address—By using the IP address as a parameter, the firewall can allow or deny traffic, based on the source or destination IP address. For example, you can configure the firewall so that only certain hosts on the internal network are able to access hosts on the Internet. Alternatively, you can configure it so that only certain hosts on the Internet are able to gain access to a system on the internal network.
• Port number—TCP/IP suite uses port numbers to identify which service a certain packet is destined for. By configuring the firewall to allow certain types of traffic, you can control the flow. You might, for example, open port 80 on the firewall to allow Hypertext Transfer Protocol (HTTP) requests from users on the Internet to reach the corporate web server. You might also, depending on the application, open the HTTP Secure (HTTPS) port, port 443, to allow access to a secure web server application.
• Protocol ID—Because each packet transmitted with IP has a protocol identifier in it, a firewall can read this value and then determine what kind of packet it is. If you are filtering based on protocol ID, you specify which protocols you will and will not allow to pass through the firewall.
• MAC address—This is perhaps the least used of the packet-filtering methods discussed, but it is possible to configure a firewall to use the hardware-configured MAC address as the determining factor in whether access to the network is granted. This is not a particularly flexible method, and it is therefore suitable only in environments in which you can closely control who uses which MAC address. The Internet is not such an environment.
Circuit-Level Firewalls
Circuit-level firewalls, also called session-layer firewalls, are similar in operation to packet-filtering firewalls, but they operate at the transport and session layers of the OSI model. The biggest difference between a packet-filtering firewall and a circuit-level firewall is that a circuit-level firewall validates TCP and UDP sessions before opening a connection, or circuit, through the firewall. When the session is established, the firewall maintains a table of valid connections and lets data pass through when session information matches an entry in the table. The table entry is removed, and the circuit is closed when the session is terminated. Circuit level firewalls that operate at the session layer, or Layer 5 of the OSI model, provided enough protection in terms of firewalls in their day. As attacks become more sophisticated and included application-layer attacks, they no longer provided sufficient protection.
Application-Layer Firewalls
As the name suggests, application-layer firewalls operate at the application layer of the OSI model. In operation, application-layer firewalls can inspect data packets traveling to or from an application. This allows the firewall to inspect, modify, block, and even redirect data traffic as it sees fit. Application-layer firewalls are sometimes referred to as a proxy firewall because they have the capability to proxy in each direction. This means that the source and destination systems do not come in direct contact with each other; rather, the firewall proxy serves as a middle point.
Exam Alert
Proxy service For the Network+ exam, remember that application-layer firewalls offer a proxy service between the sending and receiving devices. Using proxy services, the firewall is able to filter the content to and from the object or subject.
Demilitarized Zones
An important firewall-related concept is demilitarized zones (DMZs). A DMZ is part of a network on which you place servers that must be accessible by sources both outside and inside your network. However, the DMZ is not connected directly to either network, and it must always be accessed through the firewall. The military term DMZ is used because it describes an area in which there is little or no enforcement or policing.
Using DMZs provides an extra level of flexibility, protection, and complexity to your firewall configuration. Figure 14.2 shows an example of a DMZ configuration.
Figure 14.2 A DMZ configuration.

By using a DMZ, you can create an additional step that makes it more difficult for an intruder to gain access to the internal network. In Figure 14.2, for example, an intruder who tried to come in through Interface 1 would have to spoof a request from either the web server or proxy server into Interface 2 before it could be forwarded to the internal network. Although it is not impossible for an intruder to gain access to the internal network through a DMZ, it is difficult.
Firewalls have become a necessity for organizations of all sizes. As the Internet becomes an ever more hostile place, firewalls and the individuals who understand them are likely to become an essential part of the IT landscape.
Intrusion Detection and Intrusion Prevention Systems
Two other strategies we use to help secure the network are intrusion detection systems (IDS) and intrusion prevention systems (IPS). The IDS device is passive; it monitors the network, watching packets of data travel the network. The IDS compares the traffic it monitors to predefined parameters and rules. Traffic in violation of these rules is flagged as potentially dangerous. The IDSs can detect malware or other dangerous traffic that may pass undetected by the firewall. Most IDSs can detect potentially dangerous content by its signature.
A typical IDS will log incidents and store these in a database for review. The IDS can be configured to generate alerts that are sent to the system administrator. The administrator can then take the appropriate action to secure the holes in the network. For those wanting a secure network, IDS and their discovery of potential threats can be an important part. If there is a downside of an IDS, it may be that they can generate false threat reports. The IDS can sometimes erroneously detect and flag harmless traffic. This can be reduced if the administrators carefully configure the IDS rules. As with anything else technology related, IDSs have progressed and the false detection errors will and have decreased.
The IPS has all the features of the IDS but also has the capability to prevent dangerous traffic from getting to the network. The IPS is not a passive system; rather, it actively monitors the network traffic and may attempt to block potentially harmful traffic rather than just flag it. The IPS can prevent attacks in a variety of ways; it can block access from a particular user account, IP address, port, or even a specific application.
An IPS is a network device that continually scans the network looking for inappropriate activity and shuts down any potential threats. The IPS scans look for any known signatures of common attacks and automatically tries to prevent those attacks. An IPS is considered a reactive security measure because it actively monitors and can take steps to correct a potential security threat.
Network Access Security
Network access security includes the mechanisms used to filter network traffic to determine who is and who is not allowed to access the network and network resources. Firewalls, proxy servers, routers, and individual computers all have the capability to maintain access control to some degree. By limiting who can and cannot access the network and its resources, it is easy to understand why access control plays an important role in security strategy. This section reviews some network access security concepts, including access control lists and port blocking.
Access Control Lists
As far as security is concerned, an access control list (ACL) typically refers to specific access permissions assigned to an object or device on the network. For example, wireless routers can be configured to restrict who can and who cannot access the router based on MAC address. Another form of access control may be the permissions set on a network printer. The permissions may allow printer access only to a certain network group, whereas another can’t access the printer. TCP/IP can also be used as a filtering strategy. TCP/IP filtering involves restricting network traffic based on its IP address.
Access Control and MAC Filtering
Filtering network traffic using the MAC address of a system is typically done using an ACL. The ACL keeps track of all MAC addresses and is configured to allow or deny access to certain systems based on the list. As an example, let’s look at the MAC ACL from a router. Figure 14.3 shows the MAC ACL screen.
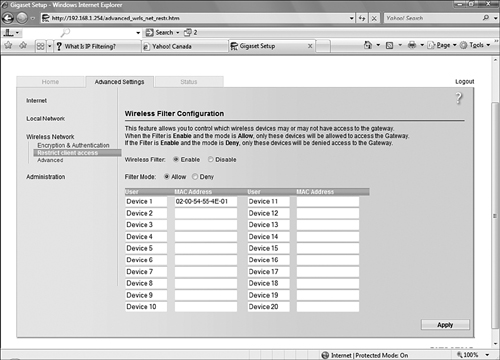
Notice from Figure 14.3 that specific wireless MAC addresses can either be denied or allowed depending on the configuration. In this example, only the system with the MAC address of 02-00-54-55-4E-01 may authenticate to this router.
TCP/IP Filtering
TCP/IP filtering also may use an ACL. The ACL will determine what types of IP traffic will be let through the router. The IP traffic that is not permitted according to the ACL will be blocked. Depending on the type of IP filtering used, the ACL can be configured to allow or deny several types of IP traffic, including the following:
• Protocol type: TCP, UDP, ICMP, SNMP, IP, and so on
• Port number used by protocols (for TCP/UPD)
• Message source address
• Message destination address
Port Blocking/Filtering
Port blocking or filtering is one of the most widely used security methods on networks. Port blocking is associated with firewalls and proxy servers, although in fact it can be implemented on any system that provides a means to manage network data flow, according to data type.
Essentially, when you block a port, you disable the capability for traffic to pass through that port, thereby filtering that traffic. Port blocking is typically implemented to prevent users on a public network from accessing systems on a private network, although it is equally possible to block internal users from external services, and internal users from other internal users, by using the same procedure.
Depending on the type of firewall system in use on a network, you might find that all the ports are disabled (blocked) and that the ones you need traffic to flow through must be opened. The benefit of this strategy is that it forces the administrator to choose the ports that should be unblocked rather than specify those that need to be blocked. This ensures that you allow only those services that are absolutely necessary into the network.
What ports remain open largely depends on the needs of the organization. For example, the ports associated with the services listed in Table 14.2 are commonly left open.
Table 14.2 Commonly Opened Port Numbers and Their Associated Uses
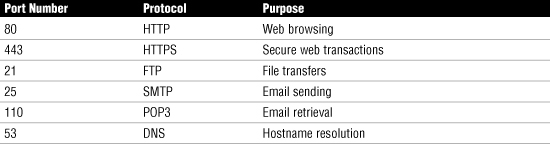
These are, of course, only a few of the services you might need on a network, and allowing traffic from other services to traverse a firewall is as easy as opening the port. Keep in mind, though, that the more ports that are open, the more vulnerable you become to outside attacks. Never open a port on a firewall unless you are absolutely sure that you need to.
Note
A complete list of ports You can obtain a complete list of port numbers and their associated protocols from the Internet Assigned Numbers Authority (IANA), at www.iana.org/assignments/port-numbers.
Before you implement port blocking, you should have a good idea of what the port is used for. Although it is true that blocking unused ports does not have any impact on internal network users, if the wrong port is blocked, you can create connectivity issues for users on the network.
For instance, a network administrator was given the task of reducing the amount of spam emails received by his company. He decided to block port 25, the port used by the Simple Mail Transfer Protocol (SMTP). He succeeded in blocking the spam email, but in the process, he also prevented users from sending email.
Remote Access Protocols and Services
Today, there are many ways to establish remote access into networks, including virtual private networks (VPNs) or plain old modem dial-up access. Regardless of the technique used for remote access or the speed at which access is achieved, certain technologies need to be in place for the magic to happen. These technologies include the protocols to allow the access to the server and to secure the data transfer after the connection is established. Also necessary are methods of access control that make sure only authorized users are using the remote access features.
All the major operating systems include built-in support for remote access. They provide both the access methods and security protocols necessary to secure the connection and data transfers.
Remote Access Service (RAS)
RAS is a remote access solution included with Windows Server products. RAS is a feature-rich, easy-to-configure, and easy-to-use method of configuring remote access.
Any system that supports the appropriate dial-in protocols, such as PPP, can connect to a RAS server. Most commonly, the clients are Windows systems that use the dial-up networking feature; but any operating system that supports dial-up client software will work. Connection to a RAS server can be made over a standard phone line, using a modem, over a network, or via an ISDN connection.
RAS supports remote connectivity from all the major client operating systems available today, including all newer Windows OSs:
• Windows Server products
• Windows XP/Vista Home–based clients
• Windows XP/Vista Professional–based clients
• UNIX-based/Linux clients
• Macintosh-based clients
Although the system is called RAS, the underlying technologies that enable the RAS process are dial-up protocols such as Serial Line Internet Protocol (SLIP) and Point-to-Point Protocol (PPP).
SLIP
SLIP was designed to allow data to be transmitted via Transmission Control Protocol/Internet Protocol (TCP/IP) over serial connections in a UNIX environment. SLIP did an excellent job, but time proved to be its enemy. SLIP was developed in an atmosphere in which security was not an overriding concern; consequently, SLIP does not support encryption or authentication. It transmits all the data used to establish a connection (username and password) in clear text, which is, of course, dangerous in today’s insecure world.
Note
Clear text—Clear text simply means that the information is sent unencrypted, and anyone can intercept with a packet capture program and read the data with his or her favorite word processor.
In addition to its inadequate security, SLIP also does not provide error checking or packet addressing, so it can be used only in serial communications. It supports only TCP/IP, and log in is accomplished through a terminal window.
Many operating systems still provide at least minimal SLIP support for backward capability to older environments, but SLIP has been replaced by a newer and more secure alternative: PPP. SLIP is still used by some government agencies and large corporations in UNIX remote access applications, so you might come across it from time to time.
PPP
PPP is the standard remote access protocol in use today. PPP is actually a family of protocols that work together to provide connection services.
Because PPP is an industry standard, it offers interoperability between different software vendors in various remote access implementations. PPP provides a number of security enhancements compared to regular SLIP—the most important being the encryption of usernames and passwords during the authentication process. PPP allows remote clients and servers to negotiate data encryption methods, authentication methods, and support new technologies. PPP even gives administrators the ability to choose which particular local area network (LAN) protocol to use over a remote link. For example, administrators can choose among NetBIOS Extended User Interface (NetBEUI), NWLink (Internetwork Packet Exchange/Sequenced Packet Exchange (IPX/SPX)), AppleTalk, or TCP/IP.
During the establishment of a PPP connection between the remote system and the server, the remote server needs to authenticate the remote user and does so by using the PPP authentication protocols. PPP accommodates a number of authentication protocols, and it’s possible on many systems to configure more than one authentication protocol. The protocol used in the authentication process depends on the security configurations established between the remote user and the server. PPP authentication protocols include CHAP, MS-CHAP (2), EAP, SPAP, and PAP. These authentication protocols are reviewed in Chapter 15, “Security Technologies and Malicious Software.”
Exam Alert
Upgrading to PPP If you are working on a network that uses SLIP and you run into connectivity problems, try upgrading to PPP because it is more flexible and secure.
PPPoE
PPPoE (Point-to-Point Protocol over Ethernet) is a protocol used for connecting multiple network users on an ethernet local area network to a remote site through a common device. For example, using PPPoE it is possible to have all users on a network share the same link such as a DSL, cable modem, or a wireless connection to the Internet. PPPoE is a combination of PPP and the ethernet protocol, which supports multiple users in a local area network. Hence the name. The PPP protocol information is encapsulated within an ethernet frame.
With PPPoE, a number of different users can share the same physical connection to the Internet, and in the process, PPPoE provides a way to keep track of individual user Internet access times. Because PPPoE allows for individual authenticated access to high-speed data networks, it is an efficient way to create a separate connection to a remote server for each user. This strategy allows Internet access and billing on a per-user basis rather than a per-site basis.
Users accessing PPPoE connections require the same information as required with standard dial-up phone accounts, including a username and password combination. As with a dial-up PPP service, an Internet service provider (ISP) will most likely automatically assign configuration information such as the IP address, subnet mask, default gateway, and DNS server.
There are two distinct stages in the PPPoE communication process: the discover stage and the PPP session stage. The discovery stage has five steps to complete to establish the PPPoE connection: initiation, offer, request, session confirmation, and termination. These steps represent back and forth communication between the client and the PPPoE server. After these steps have been negotiated, the PPP session can be established using familiar PPP authentication protocols.
Tunneling and Encryption
In the mid-1990s, Microsoft, IBM, and Cisco began working on a technology called tunneling. By 1996, more companies had become interested and involved in the work, and the project soon produced two new virtual private networking solutions: Point to Point Tunneling Protocol (PPTP) and the Layer 2 Tunneling Protocol (L2TP).
From these developments, virtual private networks (VPNs) became one of the most popular methods of remote access. Essentially, a VPN extends a LAN by establishing a remote connection, a connection tunnel, using a public network such as the Internet. A VPN provides a point-to-point dedicated link between two points over a public IP network.
VPN encapsulates encrypted data inside another datagram that contains routing information. The connection between two computers establishes a switched connection dedicated to the two computers. The encrypted data is encapsulated inside PPP, and that connection is used to deliver the data.
A VPN allows anyone with an Internet connection to use the infrastructure of the public network to dial in to the main network and access resources as if the user were logged on to the network locally. It also allows two networks to be connected to each other securely.
Many elements are involved in establishing a VPN connection, including the following:
• A VPN client—The VPN client is the computer that initiates the connection to the VPN server.
• A VPN server—The VPN server authenticates connections from VPN clients.
• An access method—As mentioned, a VPN is most often established over a public network such as the Internet; however, some VPN implementations use a private intranet. The network used must be IP based.
• VPN protocols—Protocols are required to establish, manage, and secure the data over the VPN connection. PPTP and L2TP are commonly associated with VPN connections.
VPNs have become popular because they allow the public Internet to be safely utilized as a wide area network (WAN) connectivity solution. (A complete discussion of VPNs would easily fill another book and goes beyond the scope of the Network+ objectives.)
Caution
VPN connections VPNs support analog modems and ISDN as well as dedicated broadband connections such as cable and DSL. You should remember this for the exam.
SSL VPNs
A VPN creates a virtual link between two end points over the Internet. Because a VPN uses the Internet, security can be a concern. To help alleviate the security issues, VPN transmissions can be secured with the SSL protocol. The SSL VPN functions much the same as a regular VPN but adds the encryption element. An SSL VPN enables encrypted data to travel through the VPN tunnel, making secure communications for such organizations as e-commerce sites, banks, or organizations with sensitive data.
Note
SSL with HTTP Remember that SSL is also used with the HTTP protocol to make it secure for online transactions. HTTPS (HTTP SSL) is used for such transactions as e-commerce and online banking.
SSL VPN does not require any additional software to be installed on the client system, allowing the SSL VPN to be accessed from any computer that has a web browser that supports SSL. The SSL VPN uses the browser as the interface and not other software.
SSL VPN uses something called symmetric encryption. This means that both sides of the communication channel have cryptography keys that are used to encrypt and decrypt the traffic. Symmetric encryption and cryptography keys are covered in Chapter 15. The purpose of the SSL encryption is to help ensure that you are talking to whom you think you are talking.
Exam Alert
SSL port Remember for Network+ exam that SSL uses TCP port 443, which is normally opened by default on system firewalls. This means that SSL should work through firewalls without any special configuration.
VPN Concentrators
A very long time ago now, users used to travel to work, sit at their desktop systems, and work. Now, remote users and telecommuting is part of regular business. VPNs are used to make telecommuting possible, and part of this solution is the VPN concentrator.
The VPN concentrator is a device that is used to create and encrypt a tunnel between the remote user and the network. Traffic is encrypted from the remote user to the VPN concentrator. Figure 14.4 shows a VPN concentrator and encryption range.

Remote access VPN concentrators typically support IPsec or SSL for the VPN. User authentication can be via RADIUS or Kerberos. Authentication strategies including both RADIUS and Kerberos are discussed in Chapter 15. VPN concentrators also help secure the VPN link by using access lists for remote user sessions.
Exam Alert
SSL or IPsec Remember for the Network+ exam that a VPN concentrator can use either IPsec or SSL to encrypt the communication between the remote user and the VPN concentrator.
Point-to-Point Tunneling Protocol (PPTP)
PPTP, which is documented in RFC 2637, is often mentioned with PPP. Although it’s used in dial-up connections as PPP is, PPTP provides different functionality: It creates a secure tunnel between two points on a network, over which other connectivity protocols, such as PPP, can be used. This tunneling functionality is the basis for VPNs.
VPNs are created and managed by using the PPTP protocol, which builds on the functionality of PPP, making it possible to create dedicated point-to-point tunnels through a public network such as the Internet.
To establish a PPTP session between a client and server, a TCP connection known as a PPTP control connection is required to create and maintain the communication tunnel. The PPTP control connection exists between the IP address of the PPTP client and the IP address of the PPTP server, using TCP port 1723 on the server and a dynamic port on the client. It is the function of the PPTP control connection to pass the PPTP control and management messages used to maintain the PPTP communication tunnel between the remote system and the server. PPTP provides authenticated and encrypted communications between two end points, such as a client and a server. PPTP does not use a public key infrastructure but does use a user ID and password.
PPTP uses the same authentication methods as PPP, including MS-CHAP, CHAP, PAP, and EAP, which are discussed in Chapter 15.
Layer Two Tunneling Protocol (L2TP)
L2TP is a combination of PPTP and Cisco’s L2F technology. L2TP, as the name suggests, utilizes tunneling to deliver data. It authenticates the client in a two-phase process: It first authenticates the computer and then the user. By authenticating the computer, it prevents the data from being intercepted, changed, and returned to the user in what is known as a man-in-the-middle attack. L2TP assures both parties that the data they are receiving is exactly the data sent by the originator.
Note
L2TP tunneling without encryption It is possible to create an L2TP tunnel without using encryption, but this is not a true VPN and, obviously, lacks a certain amount of security.
Tip
L2TP and the data-link layer Unlike IPsec, which operates at the network layer of the OSI model, L2TP operates at the data-link layer, making it protocol independent. This means that an L2TP connection can support protocols such as IPX and AppleTalk.
Review Break
Advantages of L2TP and PPTP
L2TP and PPTP are both tunneling protocols, so you might be wondering which you should use. Here is a quick list of some of the advantages of each, starting with PPTP:
• PPTP has been around the longest; it offers more interoperability than L2TP.
• PPTP is an industry standard.
• PPTP is easier to configure than L2TP because L2TP uses digital certificates.
• PPTP has less overhead than L2TP.
The following are some of the advantages of L2TP:
• L2TP offers greater security than PPTP.
• L2TP supports common public key infrastructure technology.
• L2TP provides support for header compression.
Inside IPsec
IPsec is an IP-layer security protocol designed to provide security against internal and external attacks. This consideration is important because the reasons and methods for securing against attacks from outside the network are well documented. IPsec provides a way to protect sensitive data as it travels within the LAN. As we know, firewalls do not provide such security for internal networks, so a complete security solution requires both a firewall solution and internal protection provided by such security mechanisms as IPsec.
To create secure data transmissions, IPsec uses two separate protocols: Authentication Headers (AH) and Encapsulating Security Payloads (ESP). In a nutshell, AH is primarily responsible for the authentication and integrity verification of packets, whereas ESP provides encryption services. Because they are independent protocols, when implementing an IPsec policy, they can be used together or individually. Whether one or both are used depends on the security needs of the network. This section describes AH and ESP as well as IPsec transmission modes.
Authentication Headers
Before using AH, it is important to understand what its function is and what it can and cannot do. AH provides source authentication and integrity for data communication but does not provide any form of encryption. AH is capable of ensuring that network communications cannot be modified during transmission; however, AH cannot protect transmitted data from being read.
AH is often implemented when network communications are restricted to certain computers. In such an instance, AH ensures that mutual authentication must take place between participating computers, which, in turn, prohibits network communications to occur between nonauthenticated computers.
Encapsulating Security Payloads
Encapsulating Security Payloads (ESP) is used to provide encryption services to network data; however, it can also be used for authentication and integrity services. The difference between AH authentication and ESP authentication is that ESP includes only the ESP header, trailer, and payload portions of a data packet. The IP header is not protected as with AH, which protects the entire data packet. Relative to encryption services, ESP provides encryption with the DES or 3DES encryption algorithms.
In IPsec encryption, you will encounter two security protocols: the Data Encryption Standard (DES) and the Triple DES (3DS). The DES encryption method uses a 56-bit encryption key. DES keys are continually regenerated during the communication. This ensures that if one key is compromised, the whole message is not compromised. Unfortunately, DES is not considered secure because 56-bit keys can be cracked with specialized equipment.
Like DES, 3DES used a 56-bit rotating key encryption method; however, as the name suggests, it uses three of them. In total, 3DES is considered a 168-bit encryption method. 3DES is used for environments when communication security is crucial.
IPsec Transmission Modes
IPsec can operate in one of two separate modes: transport mode and tunnel mode. These modes refer to how data is sent throughout the network.
In transport mode, IPsec protection is provided all the way from the issuing client to the destination server. In this way, transport mode is said to provide end-to-end transmission security.
Tunnel mode secures data only between tunnel points or gateways. In this way, tunnel mode provides gateway-to-gateway transmission security. When data is in transmission between the client and the server, it remains unprotected until it reaches the gateway. At the gateway, it is secured with IPsec until it reaches the destination gateway. At this point, data packets are decrypted and verified. The data is then sent to the receiving host unprotected. Tunnel mode is often employed when data must leave the secure confines of a local LAN or WAN and travel between hosts over a public network such as the Internet.
Remote Control Protocols
CompTIA lists three protocols that are associated with remote control access. The first, the remote desktop protocol (RDP) is used in a Windows environment. Terminal Services provides a way for a client system to connect to a server, such as Windows server 2000/2003/2008, and by using the Remote Desktop Protocol operating on the server as if they were local client applications. Such a configuration is known as thin client computing, whereby client systems use the resources of the server instead of their local processing power.
Windows Server products and XP and Vista have built-in support for Remote Desktop Connections. The underlying protocol used to manage the connection is RDP. RDP is a low-bandwidth protocol used to send mouse movements, keystrokes, and bitmap images of the screen on the server to the client computer. RDP does not actually send data over the connection—only screenshots and client keystrokes.
Virtual network computing (VNC) consists of a client, a server, and a communication protocol. It is another system whereby a remote user can access the screen of another computer system. As with the other systems mentioned here, VNC allows remote log-in, where clients can access their own desktop while being physically away from their computer. VNC uses a protocol known as the remote frame buffer (RFB) protocol. RFB is the backbone allowing remote access to another systems graphical interface.
Finally, the Citrix Independent Computing Architecture (ICA) allows clients to access and run applications on a server, using the resources of the server with only the user interface, keystrokes, and mouse movements being transferred between the client system and the server. In effect, even though you are working at the remote computer, the system functions as if you were actually sitting at the computer itself. Like with Terminal Services and RDP, ICA is an example of thin client computing.
Summary
Network security is a complex subject, encompassing many elements and factors. Being able to effectively secure a network involves understanding the risks that can be a threat to the network as well as what the result of a breach in security might entail.
A firewall system provides protection to the network by controlling the traffic that passes between internal and external networks or between two internal networks. Two other forms of network security devices include an IDS and IPS.
Understanding how implementing security features such as port blocking and encryption affect the network and the users on it is another important aspect of network security.
As well as implementing measures that serve to protect the network, you must also be able to detect intrusions to the network and provide procedures that define what steps should be taken when a breach does occur. All these elements must be combined to have an effective network security policy.
A VPN extends a LAN by establishing a remote connection, a connection tunnel, using a public network such as the Internet. A VPN provides a point-to-point dedicated link between two points over a public IP network. VPN can be established using the PPTP or L2TP tunneling protocols.
Key Terms
• Application gateway firewall
• IDS
• IPS
• ACL
• DES
• 3DES
• PPP
• SSL VPN
• VPN
• L2TP
• PPTP
• IPsec
• RAS
• RDP
• PPPoE
• PPP
• VNC
• ICA
Apply Your Knowledge
Exercises
14.1 Configuring Windows Firewall
Whether you are a network administrator working with a network-based firewall or a home user working with a host-based system, configuring your firewall is an important consideration. In this exercise we filter traffic using the Windows Firewall.
Estimated time: 15 minutes
1. Select Start, Control Panel to open the Windows Vista Control Panel. With the Control Panel open, select the Windows Firewall screen. Figure 14.5 shows the Windows Vista dialog screen.
Figure 14.5 Windows Vista Firewall.
2. On the left side of the dialog box, click the Allow a Program Through Windows Firewall option. This opens the Windows Firewall Settings dialog box, shown in Figure 14.6.
Figure 14.6 Windows Firewall Settings dialog screen.
3. Select the Exceptions tab, as shown in Figure 14.7. The Exceptions tab allows you to configure which programs can and cannot pass through the firewall. Additionally you can open certain ports for communications.
Figure 14.7 Windows Firewall Exceptions tab.
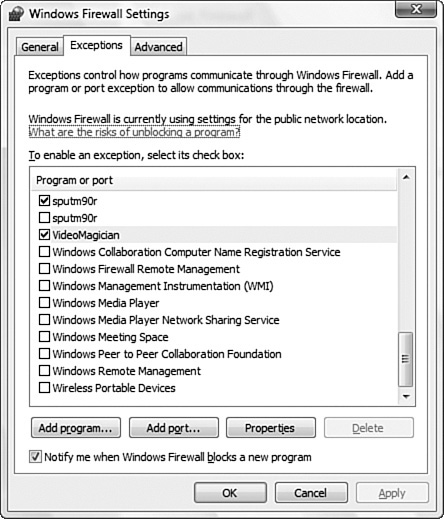
Remember, creating an exception for an application or a port opens an access point into and out of your computer. Each time you do this, the computer becomes a little less secure. The more exceptions or open ports your firewall has, the more your systems can be accessed by malicious users trying to access files or use the exception to spread malicious software.
14.2 Testing Your Ports
Sometimes we lose track of what ports we have opened and whether any open ports are potential security risks. Give your ports a quick a free test.
Estimated time: 15 minutes
1. Navigate to the GRC website: www.grc.com/. Navigate to the ShieldsUP! page from which you can begin to test your firewall settings. Figure 14.8 shows the ShieldsUP! website.
Figure 14.8 ShieldsUP! website.
2. Click the Proceed button to continue.
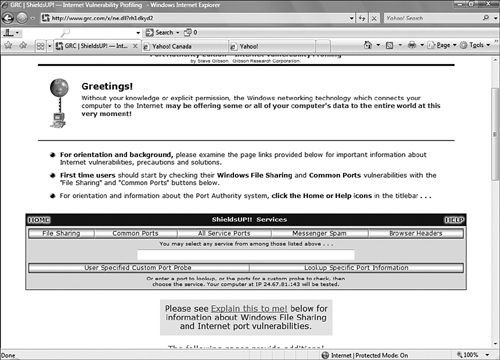
3. Select the options to scan all service ports as shown in Figure 14.9. The scan of your systems security will begin. The results will be color coded; red means your port is open and can be accessed by outside intruders, blue means that the port is closed and cannot be accessed, and green means that the port is running in stealth, meaning that the port returns no information at all. Stealth means that the port status is being blocked somewhere between your computer and the public Internet. This can happen if you are behind a router.
Figure 14.9 ShieldsUP! scanning options screen.
Exam Questions
1. Which of the following is considered a physical security measure?
![]() A. Password policy
A. Password policy
![]() B. Locks on equipment cabinets
B. Locks on equipment cabinets
![]() C. Auditing policy
C. Auditing policy
![]() D. Firewall
D. Firewall
2. On a packet-filtering firewall, which of the following is not used as a criterion for making forwarding decisions?
![]() A. IP address
A. IP address
![]() B. MAC address
B. MAC address
![]() C. TCP/IP port
C. TCP/IP port
![]() D. NetBIOS service name
D. NetBIOS service name
3. What is the basic reason for implementing a firewall?
![]() A. It reduces the costs associated with Internet access.
A. It reduces the costs associated with Internet access.
![]() B. It provides NAT functionality.
B. It provides NAT functionality.
![]() C. It provides a mechanism to protect one network from another.
C. It provides a mechanism to protect one network from another.
![]() D. It allows Internet access to be centralized.
D. It allows Internet access to be centralized.
4. Which of the following protocols is used in thin client computing?
![]() A. RDP
A. RDP
![]() B. PPP
B. PPP
![]() C. PPTP
C. PPTP
![]() D. RAS
D. RAS
5. Your company wants to create a secure link between two networks over the Internet. Which of the following protocols would you use to do this?
![]() A. PPP
A. PPP
![]() B. VPN
B. VPN
![]() C. PPTP
C. PPTP
![]() D. SLIP
D. SLIP
6. In a thin-client scenario, what information is propagated across the communications link between the client and the server?
![]() A. Any data retrieved by the client from websites
A. Any data retrieved by the client from websites
![]() B. Screen updates and keyboard and mouse input
B. Screen updates and keyboard and mouse input
![]() C. Any file opened by the client during the session
C. Any file opened by the client during the session
![]() D. Only the graphics files used to create the user’s desktop, screen updates, and keyboard and mouse input
D. Only the graphics files used to create the user’s desktop, screen updates, and keyboard and mouse input
7. What is the name for an area that is connected to a firewall but is neither in the private network area nor the public network area?
![]() A. Area of no return
A. Area of no return
![]() B. Demilitarized zone
B. Demilitarized zone
![]() C. No man’s land
C. No man’s land
![]() D. Forbidden zone
D. Forbidden zone
8. At which two layers of the OSI model does a packet-filtering firewall operate? (Choose the two best answers.)
![]() A. Network
A. Network
![]() B. Data link
B. Data link
![]() C. Transport
C. Transport
![]() D. Application
D. Application
9. Which of the following protocols does PPTP use to establish connections?
![]() A. DHCP
A. DHCP
![]() B. FTP
B. FTP
![]() C. SSH
C. SSH
![]() D. TCP
D. TCP
10. Which of the following protocols provides authentication and integrity verification for the IPsec protocol?
![]() A. ESP
A. ESP
![]() B. AH
B. AH
![]() C. Kerberos
C. Kerberos
![]() D. MD5
D. MD5
11. After noticing that there have been several attempts to access your network from the Internet, you decide to block port 53. Which of the following services is associated with port 53?
![]() A. NTP
A. NTP
![]() B. DNS
B. DNS
![]() C. SMTP
C. SMTP
![]() D. POP3
D. POP3
12. At which level of the OSI model does a circuit-level firewall operate?
![]() A. Transport
A. Transport
![]() B. Data link
B. Data link
![]() C. Network
C. Network
![]() D. Physical
D. Physical
13. You need to secure your network using IPsec and you want point-to-point security. Which IPsec transmission mode provides this?
![]() A. Transport mode
A. Transport mode
![]() B. Tunnel mode
B. Tunnel mode
![]() C. Secure mode
C. Secure mode
![]() D. Point to point mode
D. Point to point mode
14. Which of the following is considered a passive security measure?
![]() A. IPS
A. IPS
![]() B. IDS
B. IDS
![]() C. AH
C. AH
![]() D. ESP
D. ESP
15. To increase security, you decide to block several ports. Afterward, several users complain they are unable to access online banking sites. Which of the following ports needs to be reopened to allow users to access secure sites?
![]() A. 443
A. 443
![]() B. 53
B. 53
![]() C. 80
C. 80
![]() D. 21
D. 21
16. You are sending sensitive data over the network and want a method of encrypting the data. Which of the following would accomplish this?
![]() A. ESP used with IPsec
A. ESP used with IPsec
![]() B. AH used with IPsec
B. AH used with IPsec
![]() C. PPP used with IPsec
C. PPP used with IPsec
![]() D. Kerberos
D. Kerberos
17. Your company is moving from a client-based email system to a web-based solution. After all the users have been successfully moved to the new system, what are you likely to do on the corporate firewall? (Choose the two best answers.)
![]() A. Block port 53
A. Block port 53
![]() B. Block port 110
B. Block port 110
![]() C. Block port 80
C. Block port 80
![]() D. Block port 25
D. Block port 25
18. To increase network security, you have decided that only the company managers need access to a database server. All manager computers range from IP address 192.168.2.15 to 192.168.2.34. Which of the following security measures are you employing? (Select two.)
![]() A. Create an ACL that allows only the managers’ MAC addresses
A. Create an ACL that allows only the managers’ MAC addresses
![]() B. Create a TCP/IP exemptions list in the firewall
B. Create a TCP/IP exemptions list in the firewall
![]() C. TCP/IP port blocking
C. TCP/IP port blocking
![]() D. TCP/IP filtering
D. TCP/IP filtering
19. You have been told to use the PPPoE protocol for establishing connections. Which of the following best describes the function of PPPoE? (Select two.)
![]() A. Multiple users can share a connection to the Internet
A. Multiple users can share a connection to the Internet
![]() B. Secures network wide communications
B. Secures network wide communications
![]() C. Provides a way to keep track of individual users
C. Provides a way to keep track of individual users
![]() D. Provides point to point secure connections
D. Provides point to point secure connections
20. You have configured your wireless router to allow only certain clients according to the MAC address. This is an example of which of the following?
![]() A. IDS
A. IDS
![]() B. IPS
B. IPS
![]() C. ACL
C. ACL
![]() D. CRT
D. CRT
Answers to Exam Questions
1. B. Locks on a cabinet would be considered a physical security measure. Logical security measures have more to do with securing communications with protocols, using firewalls and such. All the other answers are considered logical security measures. For more information, see the section “Physical and Logical Security” in this chapter.
2. D. Firewalls do not make forwarding decisions based on the NetBIOS service name, which is fictitious. All the other answers are valid means by which a firewall can make filtering decisions. For more information, see the section “Firewalls” in this chapter.
3. C. Implementing a firewall allows you to have protection between networks, typically from the Internet to a private network. All the other answers describe functions offered by a proxy server. Note that some firewall systems do offer NAT functionality, but NAT is not a firewall feature; it is an added benefit of these systems. For more information, see the section “Firewalls” in this chapter.
4. A. The RDP protocol is used in thin-client networking, where only screen, keyboard, and mouse inputs are sent across the line. RDP has been used for Windows Terminal Services and now is used with the Remote Desktop feature with Windows XP. PPP is a dial-up protocol used over serial links; PPTP is a technology used in VPNs, and RAS is a remote access service. For more information, see the section “Remote Control Protocols” in this chapter.
5. C. To establish the VPN connection between the two networks, use PPTP. PPP is a protocol used on dial-up links. A VPN is a type of network, not a protocol. VPNs are used to create a virtual tunnel between two end points, such as creating a tunnel through the Internet to create a point-to-point connection. SLIP is a nonsecure dial-up protocol remote access protocol. For more information, see the section “Point-to-Point Tunneling Protocol (PPTP)” in this chapter.
6. B. Only screen, keyboard, and mouse inputs are sent across the communications link in a thin-client scenario. This allows the processing to be handled by the server and with limited information sent, it reduces the amount of bandwidth required for the remote connection. None of the other answers are valid. For more information, see the section “Remote Control Protocols” in this chapter.
7. B. A DMZ is an area of a network where you would place systems that must be accessed by users outside the network. All the other answers are invalid. For more information, see the section “Demilitarized Zones” in this chapter.
8. A, B. Packet-filtering firewalls work at the network layer of the OSI model. They do not operate at the application or transport layers of the OSI model. For more information, see the section “Firewall Methods” in this chapter.
9. D. PPTP uses TCP. None of the other answers are valid. For more information, see the section “Remote Access Protocols and Services” in this chapter.
10. B. To create secure data transmissions, IPsec uses two separate protocols: Authentication Headers (AH) and Encapsulating Security Payloads (ESP). In a nutshell, AH is primarily responsible for the authentication and integrity verification of packets, whereas ESP provides encryption services. For more information, see the section “Inside IPsec” in this chapter.
11. B. DNS uses port 53. NTP uses TCP/IP port 123, SMTP uses port 25, and POP3 uses port 110. For more information, see the section “Port Blocking/Filtering” in this chapter.
12. A. A circuit-level firewall works at the transport layer of the OSI model. The biggest difference between a packet-filtering firewall and a circuit-level firewall is that a circuit-level firewall validates TCP and UDP sessions before opening a connection, or circuit, through the firewall. None of the other answers are valid. For more information, see the section “Firewall Methods” in this chapter.
13. A. IPsec can operate in one of two separate modes: transport mode and tunnel mode. These modes refer to how data is sent throughout the network. In transport mode, IPsec protection is provided all the way from the issuing client to the destination server. In this way, transport mode is said to provide end-to-end transmission security. Tunnel mode provides gateway to gateway security, leaving some areas unprotected by IPsec. For more information, see the section “IPSec Transmission Modes” in this chapter.
14. B. An IDS is considered a passive security measure because it monitors the network looking for potential threats but does not actively seek to correct the threats. An IPS is considered reactive; it can detect threats and take steps to manage those threats. AH and ESP are security protocols used with IPsec. For more information, see the section “Intrusion Detection and Intrusion Prevention Systems” in this chapter.
15. A. Port 443 is used by the HTTPS protocol and is used for secure web transactions. If this port is blocked, users will not be able to perform secure online transactions. Port 53 is used by DNS, port 80 is used by regular HTTP, and port 21 is used by FTP. For more information, see the section “Port Blocking/Filtering” in this chapter.
16. A. Encapsulating Security Payloads (ESP) is used to provide encryption services for IPsec and secure network traffic. AH is used with IPsec to provide authentication services. For more information, see the section “Inside IPsec” in this chapter.
17. B, D. Because users will access their email via a web browser, the firewall will not need to accommodate POP3 (port 110) and SMTP (port 25). Blocking port 53 would disable DNS lookups, and blocking port 80 would disable web browsing (HTTP). For more information, see the section “Port Blocking/Filtering” in this chapter.
18. A, D. Common ACL filters use MAC addresses and TCP/IP addresses. A MAC ACL will allow or deny certain MAC addresses to the network or a network resource. Similarly, a TCP/IP ACL will allow or deny access based on the system’s IP address. For more information, see the section “Access Control Lists” in this chapter.
19. A, B. With PPPoE, a number of users can share the same physical connection to the Internet, and in the process, PPPoE provides a way to keep track of individual user Internet access times. For more information, see the section “PPPoE” in this chapter.
20. C. As far as security is concerned, an ACL typically refers to specific access permissions assigned to an object or device on the network. Restring access to a router by MAC address is an example of an ACL. Only those MAC addresses listed on the list will be able to authenticate to the router. For more information, see the section “Network Access Security” in this chapter.