Chapter 6. Network Perimeter Security
This chapter covers the following subjects:
Firewalls and Network Security—In this section, you will find out about one of the most important strategic pieces in your network security design—the firewall. Then we discuss other network security concepts such as packet filtering, access control lists, proxy servers, and honeypots.
NIDS Versus NIPS—This section delves into the characteristics, advantages, disadvantages, and differences of network intrusion detection systems and network intrusion prevention systems.
This chapter covers the CompTIA Security+ SY0-201 objectives 2.3 and 2.4.
This chapter is all about the network border, also known as the network perimeter. This should be a network administrator’s primary focus when it comes to securing the network because it contains the entrances that attackers attempt to use.
Allow me to analogize for a few moments. I’ve said it before; as you read this book, you are building yourself an impenetrable castle of knowledge, culminating in hands-on familiarity and the know-how to pass the exam. But we can use the castle analogy for your network as well. Imagine a big stone castle with tall walls, an expanse of clear land around the castle, or perhaps a moat surrounding it (with alligators, of course), and one or more drawbridges. The tall walls are meant to keep the average person out, sort of like a firewall in a computer network, not perfect, but necessary. The open area around the castle makes it difficult for people to sneak up on your castle; they would quickly be detected, just like malicious packets detected by a network intrusion detection system. Or better yet, if you had a moat, people trying to cross it would have a difficult time, would be easy targets for your bowmen, and would probably be gobbled up by your pet alligators. This would represent a network intrusion prevention system, which not only detects threats, but also eliminates those threats to the network. The drawbridge, or drawbridges, could be seen as network ports open to the network. As drawbridges are part of the castle wall, so network ports are part of the firewall. You, as the network administrator, have the ability and the right to close these ports at any time. At the risk of taking this analogy even further, you might decide to set traps for people; like a pool of quicksand that has a bag of pyrite suspended above it, or maybe a false entry to the castle that, after a long corridor, is walled off on the inside, ultimately trapping the unwary. In a network environment, these would be known as honeypots. Of course, every once in a while, legitimate traffic needs to enter and exit your network, too! To do this in a more secure fashion, you can set up proxy servers to act as go-betweens for the computers inside your network, and the servers they talk to on the Internet. Kind of like a sentry in the tower of the castle that would relay an outsider’s messages to someone inside the castle.
The network perimeter is less tangible in an actual network environment. Most networking devices will commonly be located in one single server room! To better envision your network, one of the best tips I can give you is to map out your network on paper, or create network documentation using programs such as Microsoft Visio and by utilizing network mapping tools (more on these tools in Chapter 10, “Vulnerability and Risk Assessment”).
So before we end up playing Dungeons & Dragons, let’s talk about one of the most important parts of your strategic defense—the firewall.
Foundation Topics: Firewalls and Network Security
Nowadays, firewalls are everywhere. Businesses large and small use them, and many households have simpler versions of these protective devices as well. You need to be aware of several types of firewalls, and you definitely want to spend some time configuring a firewall, which we do in the “Work-Through Hands-On Scenarios” section. The firewall is there to protect the entire network, but other tools are often implemented as well; for example proxy servers that help protect users and computers by keeping them anonymous, and honeypots meant to attract hackers, crackers, and other types of attackers into a false computer or network. But by far, the most important element in your network will be the firewall, so let’s begin with that.
Firewalls
In Chapter 2, “Computer Systems Security,” we discussed personal firewalls—you remember, the kind installed to an individual computer. Now let’s broaden the scope of your knowledge with network-based firewalls. Network-based firewalls are primarily used to section off and protect one network from another. They are a primary line of defense and are extremely important in network security. There are several types of firewalls; some run as software on server computers, some as a standalone dedicated appliances, and some that work as just one function of many on a single device. They are commonly represented as a sort of “brick wall” between a LAN and the Internet, as shown in Figure 6-1.
Figure 6-1. Diagram of a Basic Firewall Implementation
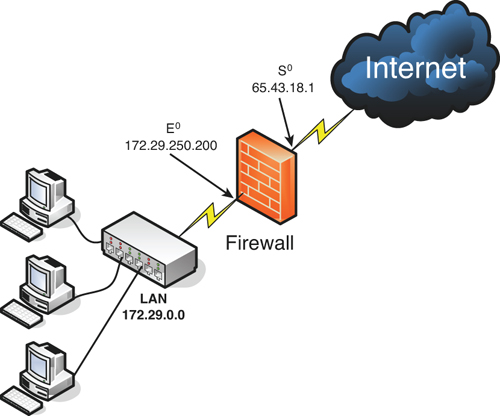
Just as a firewall in a physical building is there to slow the spread of a fire and contain it until the fire department arrives, a firewall in a computer network is there to keep fire at bay in the form of malicious attacks. Quite often, a firewall (or the device the firewall resides on) will have NAT in operation as well. In Figure 6-1, note that the firewall has a local address of 172.29.250.200; this connects it to the LAN. It also has an Internet address of 65.43.18.1, enabling connectivity for the entire LAN to the Internet, while hiding the LAN IP addresses. By default, the IP address 65.43.18.1 is completely shielded. This means that all inbound ports are effectively closed and will not enable incoming traffic, unless a LAN computer initiates a session with another system on the Internet. However, a good network security administrator always checks this to make sure; first, by accessing the firewall’s firmware (or software application as the case may be) and verifying that the firewall is on, and next by scanning the firewall with a third-party application such as Nmap (www.nmap.org) or with a web-based port scanning utility such as ShieldsUP! (www.grc.com), as was shown in the Chapter 5 lab, “Port Scanning Basics.” If any ports are open, or unshielded, they should be dealt with immediately. Then the firewall should be rescanned for vulnerabilities. You can find more information on port scanning and vulnerability assessments in Chapter 10. Firewalls should be used only as they were intended. The company firewall should not be handling any other extraneous services, for example acting as a web server or SMTP server. By using a firewall as it was intended, its vulnerability is reduced.
Generally, a firewall inspects traffic that passes through it and permits or denies that traffic based on rules set by an administrator. For example, this can be done through the use of port forwarding and virtual servers, or it can be based on the IP address of the external computer.
Note
For a quick tutorial on setting up virtual servers and port forwarding on a typical SOHO router/firewall, see the following link:
A lot of today’s firewalls have two types of firewall technologies built-in to them: SPI and NAT. However, there are a couple other types of firewall methodologies that you should be aware of; all these are covered in the following list.
• Packet filtering—Inspects each packet passing through the firewall and accepts or rejects it based on rules. However, there are two types: stateless packet inspection, and stateful packet inspection (also known as SPI or a stateful firewall). A stateless packet filter, also known as pure packet filtering, does not retain memory of packets that have passed through the firewall; due to this, a stateless packet filter can be vulnerable to IP spoofing attacks. But a firewall running stateful packet inspection is normally not vulnerable to this because it keeps track of the state of network connections by examining the header in each packet. It can distinguish between legitimate and illegitimate packets. This function operates at the Network Layer of the OSI model.
![]()
• NAT filtering—Also known as NAT endpoint filtering, filters traffic according to ports (TCP or UDP). This can be done in three ways: by way of basic endpoint connections, by matching incoming traffic to the corresponding outbound IP address connection, or by matching incoming traffic to the corresponding IP address and port.
• Application-level gateway (ALG)—Applies security mechanisms to specific applications, such as FTP and or BitTorrent. It supports address and port translation and checks whether the type of application traffic is allowed. For example, your company might allow FTP traffic through the firewall, but might decide to disable Telnet traffic (probably a wise choice). The ALG will check each type of packet coming in and discard those that are Telnet packets. Although this adds a powerful layer of security, the price is that it is resource-intensive, which could lead to performance degradation.
• Circuit-level gateway—Works at the Session Layer of the OSI model, and applies security mechanisms when a TCP or UDP connection is established; they act as a go between for the Transport and Application Layers in TCP/IP. After the connection has been made, packets can flow between the hosts without further checking. Circuit-level gateways hide information about the private network, but they do not filter individual packets.
A firewall can be set up in several different physical configurations. For example, in Chapter 5, “Network Design Elements and Network Threats,” we discussed implementing a DMZ. This could be done in a back-to-back configuration (two firewalls surrounding the DMZ), as shown in Figure 6-2, or as a 3-leg perimeter configuration.
Figure 6-2. Back-to-Back Firewall/DMZ Configuration
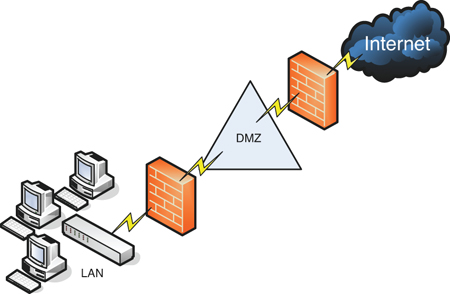
![]()
Note
For a quick tutorial on setting up a 3-leg perimeter firewall/DMZ configuration with ISA, see the following link:
Generally, there will be one firewall with the network and all devices and computers residing “behind” it. By the way, if a device is “behind” the firewall, it is also considered to be “after” the firewall, and if the device is “in front of” the firewall, it is also known as being “before” the firewall. Think of the firewall as the drawbridge of a castle. When you are trying to gain admittance to the castle, the drawbridge will probably be closed. You would be in front of the drawbridge, and the people inside the castle would be behind the drawbridge. This is a basic analogy, but should help to understand the whole “in front of” and “behind” business as it relates to data attempting to enter the network and devices that reside on your network.
Logging is also important when it comes to a firewall. Firewall logs should be the first thing you check when an intrusion has been detected. You should know how to access the logs, and how to read them. For example, Figure 6-3 shows two screen captures: The first displays the Internet sessions on a basic D-Link router/firewall, and the second shows log events such as blocked packets. Look at the blocked Gnutella packet that is pointed out. I know it is a Gnutella packet because the inbound port on my firewall that the external computer is trying to connect to shows as port 6346; this associates with Gnutella. Gnutella is a P2P file-sharing network. None of the computers on this particular network use or are in any way connected to the Gnutella service. These external computers are just random clients of the Gnutella P2P network trying to connect to every one possible. It’s good that these packets have been blocked, but maybe you don’t want the IP address shown (24.253.3.20) to have any capability to connect to your network at all. To eliminate that IP, you could add it to an inbound filter (which you will do in the “Work-Through Hands-On Scenarios” section) or to an access control list (ACL). When dealing with firewalls, an ACL is a set of rules that apply to a list of network names, IP addresses, and port numbers. These rules can be configured to control inbound and outbound traffic. This is a bit different than ACLs with respect to operating systems, which we cover in Chapter 9, “Access Control Methods and Models,” but the same basic principles apply: Basically, one entity is granted or denied permission to another entity.
Figure 6-3. D-Link Router/Firewall Internet Sessions
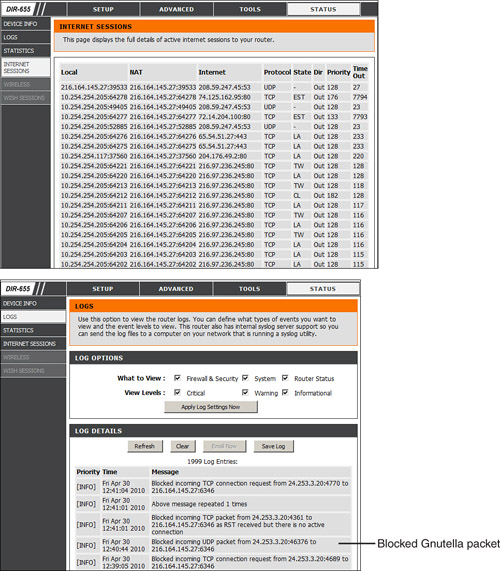
Examples of network firewalls include basic devices such as the D-Link DIR-655 SOHO router/firewall, as shown in Figure 6-3, and more advanced appliances such as Cisco PIX/ASA Security Appliances and Juniper NetScreens. A firewall could also be incorporated into a server, for instance Microsoft’s Internet Security & Acceleration Server (ISA). A firewall will usually have more than one network adapter so that it can connect to more than one network; this is known as a multihomed connection. An ISA server needs to be dual-homed at minimum (two adapters), and it is recommended that the server has three network adapters, in the case that you want to implement a DMZ or another perimeter security technique.
Firewalls are often considered to be all-in-one devices, but actually they provide specific functionality as we have discussed in this section. Still, it is common to hear people refer to a firewall when they are really talking about another technology, or even another device. For example, many home users and small office users will have an all-in-one multifunction network device. This device will have four ports for wired connections, plus a wireless antenna; it will connect all the computers to the Internet, and finally will have a firewall built-in. Because some users consider this to be simply a firewall, you should teach them about the benefits of disabling SSID broadcasting, and enabling MAC filtering. By disabling Service Set Identifier (SSID) broadcasting, the average user cannot connect wirelessly to the device. An attacker will know how to bypass this, but it is an important element of security that you should implement, after all trusted computers have been connected wirelessly. MAC filtering denies access to any computer that does not have one of the MAC addresses you list, another powerful tool. See Lab 3, “Enabling MAC Filtering” in the “Work Through Hands-On Scenarios” on the DVD for more information.
To make matters a bit more confusing, a firewall can also act as, or in combination with, a proxy server, which we discuss in the following section.
Proxy Servers
A proxy server acts as an intermediary for clients usually located on a LAN, and the servers that they want to access that are usually located on the Internet. By definition, proxy means go-between, or mediator, acting as such a mediator in between a private and a public network. The proxy server will evaluate requests from clients, and if they meet certain criteria, forward them to the appropriate server. There are several types of proxies, including a couple you should know for the exam:
• IP proxy—Secures a network by keeping machines behind it anonymous; it does this through the use of NAT. For example, a basic four-port router can act as an IP proxy for the clients on the LAN it protects. An IP proxy can be the victim of many of the network attacks mentioned in Chapter 5, especially DoS attacks. Regardless of whether the IP proxy is an appliance, or a computer, it should be updated regularly, and its log files should be monitored periodically and audited according to organization policies.
![]()
• Caching proxy—Attempts to serve client requests without actually contacting the remote server. Although there are FTP and SMTP proxies among others, the most common caching proxy is the HTTP proxy, also known as a web proxy, which caches web pages from servers on the Internet for a set amount of time. Examples of caching proxies include Microsoft ISA Server and Privoxy. An example of a caching proxy is illustrated in Figure 6-4. For example, let’s say a coworker of yours (Client A) accessed www.google.com, and that she was the first person to do so on the network. This client request will go through the HTTP proxy and be redirected to Google’s web server. As the data for Google’s home page comes in, the HTTP proxy will store or cache that information. When another person on your network (Client B) makes a subsequent request for www.google.com, the bulk of that information will come from the HTTP proxy instead of from Google’s web server. This is done to save bandwidth on the company’s Internet connection and to increase the speed at which client requests are carried out. Most HTTP proxies check websites to verify that nothing has changed since the last request. Because information changes quickly on the Internet, a time limit of 24 hours is common for storing cached information before it is deleted.
Figure 6-4. Illustration of an HTTP Proxy in Action
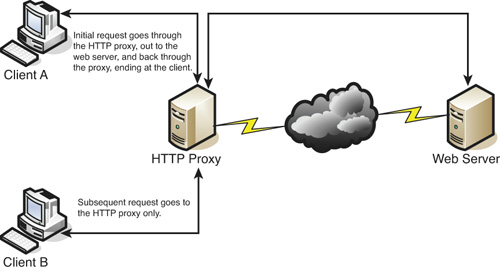
![]()
Other types of proxies are available to apply policies, block undesirable websites, audit employee usage, and scan for malware. One device or computer might do all these things or just one or two. It depends on the software used or appliance installed. Reverse proxies can also be implemented to protect a DMZ server’s identity or to provide authentication and other secure tasks. This is done when users on the Internet are accessing server resources on your network. Generally, a proxy server will have more than one network adapter so that it can connect to the various networks it is acting as a mediator for. Each of the network adapters in a proxy should be periodically monitored for improper traffic and for possible network attacks and other vulnerabilities. A proxy server might be the same device as a firewall, or it could be separate. Because of this, there are a multitude of network configurations possible. Proxy servers, especially HTTP proxies, can be used maliciously to record traffic sent through them; because most of the traffic is sent in unencrypted form, this could be a security risk. A possible mitigation for this is to chain multiple proxies together in an attempt to confuse any onlookers and potential attackers.
Another example of a proxy in action is Internet content filtering. An Internet content filter, or simply a content filter, is usually applied as software at the Application Layer and can filter out various types of Internet activities such as websites accessed, e-mail, instant messaging, and more. It is used most often to disallow access to inappropriate web material (estimated to be a big percentage of the Internet!) or websites that take up far too much of an organization’s Internet bandwidth. Internet content filters can be installed on individual clients, but by far the more efficient implementation is as an individual proxy that acts as a mediator between all the clients and the Internet. These proxy versions of content filters secure the network in two ways: one, by forbidding access to potentially malicious websites, and two, by blocking access to objectionable material that employees might feel is offensive. Even if employees inadvertently type an incorrect URL, they can rest assured that any objectionable material will not show up on their display. Internet filtering appliances will analyze just about all the data that comes through it including Internet content, URLs, and security certificates such as the kind you would automatically receive when going to a secure site that starts with https.
Honeypots and Honeynets
Honeypots and honeynets attract and trap potential attackers to counteract any attempts at unauthorized access of the network. This isolates the potential attacker in a monitored area and contains dummy resources that look to be of value to the perpetrator. While an attacker is trapped in one of these, their methods can be studied and analyzed, and the results of those analyses can be applied to the general security of the functional network.
A honeypot is generally a single computer but could also be a file, group of files, or an area of unused IP address space, whereas a honeynet is one or more computers, servers, or an area of a network; these are used when a single honeypot is not sufficient. Either way, the individual computer, or group of servers, will usually not house any important company information. Various analysis tools are implemented to study the attacker; these tools, along with a centralized group of honeypots (or a honeynet), are known collectively as a honeyfarm.
One example of a honeypot in action is the spam honeypot. Spam e-mail is one of the worst banes known to a network administrator; a spam honeypot can lure spammers in enabling the network administrators to study the spammer’s techniques and habits, thus allowing the network admins to better protect their actual e-mail servers, SMTP relays, SMTP proxies, and so on, over the long term. It might ultimately keep the spammers away from the real e-mail addresses, because the spammers are occupied elsewhere. Some of the information gained by studying spammers is often shared with other network admins or organizations’ websites dedicated to reducing spam. A spam honeypot could be as simple as a single e-mail address or as complex as an entire e-mail domain with multiple SMTP servers.
Of course, as with any technology that will study attackers, honeypots also bear risks to the legitimate network. The honeypot or honeynet should be carefully firewalled off from the legitimate network to ensure that the attacker can’t break through.
Quite often, honeypots and honeynets are used as part of a more complex solution known as a network intrusion detection system.
NIDS Versus NIPS
It’s not a battle royale, but you should be able to differentiate between a network intrusion detection system (NIDS) and a network intrusion prevention system (NIPS) for the exam. Previously, in Chapter 3, “OS Hardening and Virtualization,” we discussed host-based intrusion detection systems (or HIDS). Although a great many attacks can hamper an individual computer, there are just as many network attacks that could possibly take down a server, switch, router, or even an entire network. Network-based IDSs were developed to detect these malicious network attacks, and network-based IPSs were developed in an attempt to prevent them.
NIDS
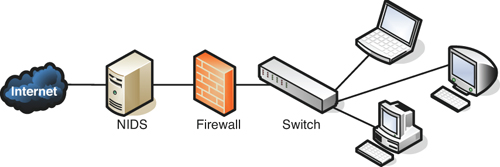
A network intrusion detection system (NIDS) by definition is a type of IDS that attempts to detect malicious network activities, for example port scans and DoS attacks, by constantly monitoring network traffic. Examples of NIDS include open source instances such as Snort (www.snort.org/), Bro (www.bro-ids.org/), and products from Enterasys (www.enterasys.com). A NIDS should be situated at the entrance or gateway to your network. It is not a firewall but should be used with a firewall. Because the NIDS will be inspecting every packet that traverses through your network, it needs to be fast; basically the slower the NIDS, the slower the network. So the solution itself, the computer/device it is installed on and the network connections of that computer/device all need to be planned out accordingly, to ensure that the NIDS does not cause network performance degradation. Figure 6-5 illustrates how a NIDS might be implemented on a network. Quite often it will be placed in front of a firewall. The NIDS will detect attacks and anomalies and alert the administrator if they occur, whereas the firewall will do its best to prevent those attacks from entering the network. However, a NIDS could be placed behind the firewall, or you might have multiple NIDS points strategically placed around the network. If the NIDS is placed in front of the firewall, it will generate a lot more administrator alerts, but these can usually be whittled down within the firmware or software of the device running the NIDS. Regardless of where the NIDS is located, a network administrator should monitor traffic from time to time; to do so, the computer, server, or appliance that has the NIDS installed should have a network adapter configured to work in promiscuous mode. This passes all traffic to the CPU, not just the frames addressed to it.
Figure 6-5. Illustration of NIDS Placement in a Network
![]()
The beauty of a NIDS is that you might get away with one or two NIDS points on the network, and do away with some or all the HIDS installed on individual computers, effectively lowering the bottom line while still doing a decent job of mitigating risk. A couple of the disadvantage of a NIDS, aside from possible network performance issues, is that it might not be able to read encrypted packets of information and will not detect problems that occur on an individual computer. Therefore, to secure a network and its hosts, many organizations will implement a mixture of NIDS and HIDS. If a NIDS is placed in front of the firewall, it is subject to attack; therefore it should be monitored and updated regularly. Some NIDS solutions will auto-update. Finally, the biggest disadvantage of a NIDS is that it detects only attacks; to protect against, or prevent, these attacks, you would need a NIPS.
NIPS
A network intrusion prevention system (NIPS) is designed to inspect traffic, and based on its configuration or security policy, it can remove, detain, or redirect malicious traffic. More and more companies are offering NIPS solutions in addition to, or instead of, NIDS solutions. Examples of NIPS include Enterasys Intrusion Prevention System (also known as Dragon IPS), Check Point Security Appliances (www.checkpoint.com), McAfee IntruShield (www.mcafee.com), and the aforementioned Snort, which is actually an NIDS/NIPS software package that should be installed on a dual or multihomed server. Not only can a NIPS go above and beyond a NIDS by removing or redirecting malicious traffic, it can also redirect a recognized attacker to a single computer known as a padded cell, which contains no information of value, and has no way out.
Like a NIDS, a NIPS should sit inline on the network, often in front of the firewall, although it could be placed elsewhere, depending on the network segment it protects and the network architecture. Whereas many NIPS solutions have two connections only and are known as perimeter solutions, other NIPS appliances will have up to 16 ports enabling many points of detection on the network—these would be known as network “core” devices. Regardless of the solution you select, as packets pass through the device, they are inspected for possible attacks. These devices need to be accurate and updated often (hopefully automatically) to avoid the misidentification of legitimate traffic, or worse, the misidentification of attacks. If the NIPS blocks legitimate traffic, it would be known as a false positive, and effectively could deny service to legitimate customers, creating a self-inflicted denial of service of sorts. If the IPS does not have a particular attack’s signature in its database, and lets that attack through thinking it is legitimate traffic, it is known as a false negative, also bad for obvious reasons! Many IPS systems can monitor for attack signatures and anomalies. More information about false positives and false negatives can be found in Chapter 8, “Physical Security and Authentication Models.” More information on signatures can be found in Chapter 3 and Chapter 11, “Monitoring and Auditing.” Another type of error that can occur with NIDS and NIPS is a subversion error; this is when the NIDS/NIPS has been altered by an attacker to allow for false negatives, ultimately leading to attacks creeping into the network. This can be deadly because the NIDS/NIPS will often be the first point of resistance in the network. To protect against this, some devices will have the capability to hide or mask their IP address. They might also come with an internal firewall. It is also important to select an IPS solution that has a secure channel for the management console interface.
The beauty of a NIPS compared to a host-based IPS is that it can protect noncomputer-based network devices such as switches, routers, and firewalls. However, the NIPS is considered a single point of failure because it sits inline on the network. Due to this, some organizations will opt to install a bypass switch, which also enables the NIPS to be taken offline when maintenance needs to be done.
Another advantage of newer NIPS solutions is that some of them can act as protocol analyzers by reading encrypted traffic and stopping encrypted attacks.
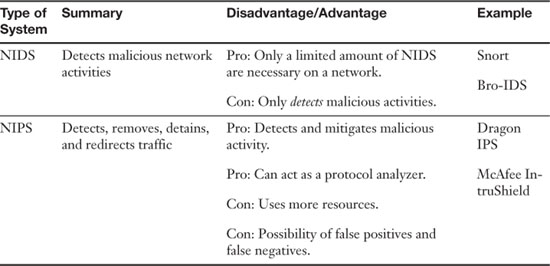
Summary of NIDS Versus NIPS
Table 6-1 summarizes NIDS versus NIPS.
Table 6-1. Summary of NIDS Versus NIPS
![]()
The Protocol Analyzer’s Role in NIDS and NIPS
You might be familiar already with protocol analyzers such as Wireshark (Ethereal) or Network Monitor. These are loaded on a computer and are controlled by the user in a GUI environment; they capture packets enabling the user to analyze them and view their contents. However, some NIDS/NIPS are considered to be full protocol analyzers with no user intervention required. The protocol analyzer is built into the NIDS/NIPS appliance. It decodes Application Layer protocols, such as HTTP, FTP, or SMTP, and forwards the results to the IDS or IPS analysis engine. Then the analysis engine will study the information for anomalous or behavioral exploits. This type of analysis can block many exploits based on a single signature. This is superior to basic signature pattern recognition (without protocol analysis), because with signature-based IDS/IPS solutions, many signatures have to be constantly downloaded and stored in the device’s database, and they don’t enable dynamic understanding of new attacks. However, as with any powerful analysis, like protocol analysis, there is a premium placed on processing power, and the price of these types of IDS/IPS solutions will undoubtedly be higher.
Exam Preparation Tasks: Review Key Topics
Review the most important topics in the chapter, noted with the Key Topics icon in the outer margin of the page. Table 6-2 lists a reference of these key topics and the page numbers on which each is found.
![]()
Table 6-2. Key Topics for Chapter 6
Complete Tables and Lists from Memory
Print a copy of Appendix A, “Memory Tables,” (found on the DVD), or at least the section for this chapter, and complete the tables and lists from memory. Appendix B, “Memory Tables Answer Key,” also on the DVD, includes completed tables and lists to check your work.
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
network intrusion detection system,
network intrusion prevention system,
Hands-On Labs
Complete the following written step-by-step scenarios. After you finish (or if you do not have adequate equipment to complete the scenario), watch the corresponding video solutions on the DVD.
If you have additional questions, feel free to post them at my website: www.davidlprowse.com in the Ask Dave forum. (Free registration is required to post on the website.)
Equipment Needed
• Computer with Internet access.
• Web browser: Internet Explorer version 6 and higher or Firefox are recommended.
• D-Link DIR-655 router:
• If you have access to an actual DIR-655, make sure that it is updated to the latest firmware. Then connect to it by opening a web browser and typing the IP address of the router in the URL field, for example, 192.168.0.1. Next, at the login screen, type the password for the router, and click the Log In button. This should display the Device Information page. Start at this page for each of the three labs.
• If you do not have access to an actual DIR-655, use the D-Link simulator located at http://support.dlink.com/Emulators/dir655/index.html. Then select the 1st option: DIR-655 Device UI. Next, at the login screen, click the Log In button. (No password is necessary.) This should display the Device Information page. Start at this page for each of the three labs.
Lab 6-1: Packet Filtering and NAT Firewalls
In this lab, you view where to turn on stateful packet inspection (SPI) and configure the NAT firewall. The steps are as follows:
Step 1. On the main Device Information page, click the Advanced link near the top of the window. This should bring up the Advanced page.
Step 2. On the left side, click the Firewall Settings link. This should display the Firewall Settings window.
Step 3. Take note of the first setting: Enable SPI. This is stateful packet inspection. It should be selected by default, but if not, select it, and move on to the next step.
Step 4. View the NAT Endpoint Filtering section directly under the Firewall Settings. Increase the security of UDP Endpoint Filtering by clicking the radio button Port and Address Restricted. This is the highest level of security you can select.
Step 5. Next, enable antispoofing by clicking the Enable anti-spoofing checking checkbox.
Step 6. Finally, scroll down and view the Application Level Gateway (ALG) Configuration. PPTP, IPSec (VPN), RTSP, and SIP should all be selected.
Watch the solution video in the “Hands-On Scenarios” section of the DVD.
Lab 6-2: Configuring an Inbound Filter on a SOHO Router/Firewall
In this lab, you view the firewall logs and set up an inbound filter to deny access to a remote computer’s IP address. The steps are as follows:
Step 1. On the main Device Information page, click the Logs link on the left side. This should display the Logs window.
Step 2. View the Log Details. If you are using an actual D-Link DIR-655, you will most likely see blocked packets. If you are using the simulator, you will see only basic entries, for example the wireless link is up, and so on.
Step 3. If there is an IP address that you want to block, write down the number now. Otherwise, write down the IP address: 12.46.14.66 (at one time a known Spam IP address).
Step 4. Click the Advanced link near the top of the window. This should bring up the Advanced page.
Step 5. On the left side, click the Inbound Filter link. This should display the Inbound Filter window.
Step 6. Give a name to your new rule in the Name field; for example, Block IP 12.46.14.66.
Step 7. Leave the Action drop-down box set to Deny. This denies access to the IP address or addresses you select.
Step 8. Click the first checkbox under where it says Remote IP Range.
Step 9. Enter the IP address you want to deny in the Remote IP Start and Remote IP End fields. If you want to block a range of addresses, you could do this as well, for example type: 12.46.14.66 in the Remote IP Start field and 12.46.14.70 in the Remote IP End field.
Step 10. Click the Add button. This should add the filter rule to the list. If you are using the D-Link simulator, you might not see the addition; reference the video solution for this.
Step 11. View the Inbound Filter Rules List. When finished, return the computer to normal. Remove the rule by clicking the garbage can and clicking OK.
Watch the solution video in the “Hands-On Scenarios” section of the DVD.
Lab 6-3: Enabling MAC Filtering
In this lab, you turn on Media Access Control (MAC) filtering at the firewall by allowing only one computer on your network access to the firewall. The steps are as follows:
Step 1. Discover and write down your local computer’s MAC address.
On a Windows computer, open the Command Prompt and type ipconfig/all. The MAC address is a hexadecimal number listed in the Physical Address field. Write this number down. If you have more than one network adapter, write down the MAC address associated with the network adapter you are currently using to access the D-Link DIR-655.
On a Linux computer, open the CLI and type ifconfig. The MAC address is a hexadecimal number listed in the HWaddr field. Write this number down. If you have more than one network adapter, write down the MAC address associated with the network adapter you are currently using to access the D-Link DIR-655.
Step 2. On the main Device Information page of the D-Link DIR-655, click the Advanced link near the top of the window. This should bring up the Advanced page.
Step 3. On the left side, click the Network Filter link. This should display the MAC Address Filter window.
Step 4. Click the drop-down menu for the Configure MAC Filtering below field. Select Turn MAC Filtering ON and ALLOW computers listed to access the network.
Step 5. Type the MAC address you wrote down previously into the first blank field. You can use hyphens or colons to separate the numbers, for example: 00-1C-C0-A1-55-16 or 00:1C:C0:A1:55:16.
Step 6. Click the Save Settings button. The simulator version of the D-Link DIR-655 will usually clear these automatically, but if you want to clear a MAC address that is listed, click the Clear button.
Step 7. Finally, when you finish, click the drop-down menu to turn MAC Filtering off.
Watch the solution video in the “Hands-On Scenarios” section of the DVD.
View Recommended Resources
If you want to brush up on your networking topics:
• Prowse, David L. CompTIA Network+ Video Mentor, First edition. Que. 2009.
• Harwood, Mike. CompTIA Network+ N10-004 Cert Guide, Third edition. Que. 2009.
• Comer, Douglas. Computer Networks and Internets (5th Edition). Prentice Hall. 2008.
Article: Intrusion Detection Overview: www.informit.com/articles/article.aspx?p=174342
Video: Setting up virtual servers and port forwarding on a typical SOHO router/firewall: www.davidlprowse.com/forums/showthread.php?t=1620
Video: Setting up a 3-leg perimeter firewall/DMZ configuration with ISA: www.davidlprowse.com/forums/showthread.php?t=1621
Nmap: http://nmap.org/
GRC’s ShieldsUP!: www.grc.com
Answer Review Questions
Answer the following review questions. You can find the answers at the end of this chapter.
1. Which tool would you use if you want to view the contents of a packet?
A. TDR
B. Port scanner
C. Protocol analyzer
D. Loopback adapter
2. The honeypot concept is enticing to administrators because
A. It enables them to observe attacks.
B. It traps an attacker in a network.
C. It bounces attacks back at the attacker.
D. It traps a person physically between two locked doors.
3. James has detected an intrusion in his company. What should he check first?
A. DNS Logs
B. Firewall logs
D. Performance logs
4. Which of the following devices should you employ to protect your network? (Select the best answer.)
A. Protocol analyzer
B. Firewall
C. DMZ
D. Proxy server
5. Which device’s log file will show access control lists and who was allowed access and who wasn’t?
A. Firewall
B. PDA
C. Performance monitor
D. IP proxy
6. Where are software firewalls usually located?
A. On routers
B. On servers
C. On clients
D. On every computer
7. Where is the optimal place to have a proxy server?
A. In between two private networks
B. In between a private and a public network
C. In between two public networks
D. On all of the servers
8. A coworker has installed an SMTP server on the company firewall. What security principle does this violate?
A. Chain of custody
B. Use of a device as it was intended
C. Man trap
D. Use of multifunction network devices
9. You are working on a server and are busy implementing a network intrusion detection system on the network. You need to monitor the network traffic from the server. What mode should you configure the network adapter to work in?
A. Half-duplex mode
B. Full-duplex mode
C. Auto configuration mode
D. Promiscuous mode
10. Which of the following displays a single public IP address to the Internet while hiding a group of internal private IP addresses?
A. HTTP proxy
B. Protocol analyzer
C. IP proxy
D. SMTP proxy
11. If your ISP blocks objectionable material, what device would you guess has been implemented?
A. Proxy server
B. Firewall
C. Internet content filter
D. NIDS
12. Of the following, which is a collection of servers that was set up to attract hackers?
A. DMZ
B. Honeypot
C. Honeynet
D. VLAN
13. Which of the following will detect malicious packets and discard them?
A. Proxy server
B. NIDS
C. NIPS
D. PAT
14. Which of the following will an Internet filtering appliance analyze? (Select the three best answers.)
A. Content
B. Certificates
C. Certificate revocation lists
D. URLs certificates were goals
Answers and Explanations
1. C. A protocol analyzer has the capability to “drill” down through a packet and show the contents of that packet as they correspond to the OSI model.
2. A. By creating a honeypot, the administrator can monitor attacks without sustaining damage to a server or other computer. Don’t confuse this with a honeynet (answer B), which is meant to attract and trap malicious attackers in an entire false network. Answer C is not something that an administrator would normally do, and answer D is defining a man trap.
3. B. If there were an intrusion, the first thing you should check are the firewall logs. DNS logs in the event viewer and the performance logs will most likely not show intrusions to the company. The best place to look first is the firewall logs.
4. B. Install a firewall to protect the network. Protocol analyzers will not help to protect a network but are valuable as vulnerability assessment and monitoring tools. Although a DMZ and a proxy server could possibly help to protect a portion of the network to a certain extent, the best answer is firewall.
5. A. A firewall contains one or more access control lists (ACLs) defining who is enabled to access to the network. The firewall can also show attempts at access and whether they succeeded or failed. A personal digital assistant (PDA) might list who called or e-mailed but as of the writing of this book does not use ACLs. Performance Monitor analyzes the performance of a computer, and an IP proxy deals with network address translation, hiding many private IP addresses behind one public address. Although the function of an IP proxy is often built into a firewall, the best answer would be firewall.
6. C. Software-based firewalls, such as the Windows Firewall, are normally running on the client computers. Although a software-based firewall could also be run on a server, it is not as common. Also, a SOHO router might have a built-in firewall, but not all routers will have firewalls.
7. B. Proxy servers should normally be between the private and the public network. This way they can act as a go between for all the computers located on the private network. This applies especially to IP proxy servers but might also include HTTP proxy servers.
8. B. And SMTP servers should not be installed on a company firewall. This is not the intention of a firewall device. The SMTP server should most likely be installed within a DMZ.
9. D. To monitor the implementation of NIDS on the network, you should configure the network adapter to work in promiscuous mode; this forces the network adapter to pass all the traffic it receives to the processor, not just the frames that were addressed to that particular network adapter. The other three answers have to do with duplexing—whether the network adapter can send and receive simultaneously.
10. C. An IP proxy displays a single public IP address to the Internet while hiding a group of internal private IP addresses. It sends data back and forth between the IP addresses by using Network Address Translation (NAT). This functionality is usually built into SOHO routers and is one of the main functions of those routers. HTTP proxies store commonly accessed Internet information. Protocol analyzers enable the capture and viewing of network data. SMTP proxies act as a go between for e-mail.
11. C. An Internet content filter, usually implemented as content-control software can block objectionable material before it ever gets to the user. This is common in schools, government, and many companies.
12. C. A honeynet is a collection of servers set up to attract hackers. A honeypot is usually one computer or one server that has the same purpose. A DMZ is the demilitarized zone that is in between the LAN and the Internet. A VLAN is a virtual LAN.
13. C. NIPS, or a network intrusion prevention system, will detect and discard malicious packets. A NIDS only detects them and alerts the administrator. A proxy server acts as a go-between for clients sending data to systems on the Internet. PAT is port-based address translation.
14. A, B, and D. However, certificate revocation lists will most likely not be analyzed. Remember that CRLs are published only periodically.
