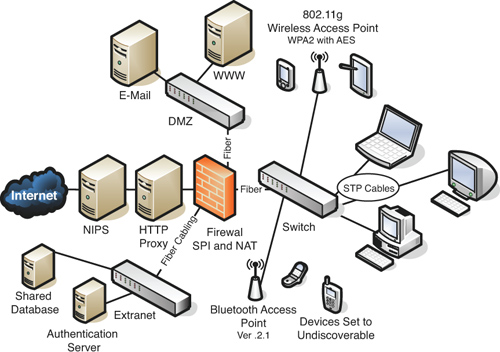
Chapter 7. Securing Network Media and Devices
This chapter covers the following subjects:
Securing Wired Networks and Devices—In this section, you learn about how to reduce the risk of attack to your wired networks and the central connecting devices that control access to those networks. Concepts covered include security for common network devices such as SOHO routers and firewalls, and how to secure twisted-pair, fiber-optic, and coaxial cables.
Securing Wireless Networks—Here, we delve into wireless networks, how you can secure your wireless access points and protect your wireless network from intruders, inside or outside the building. Wireless concepts covered include Wi-Fi security and Bluetooth security.
This chapter covers the CompTIA Security+ SY0-201 objectives 2.5, 2.6, and 2.7.
Imagine if you will that you are in charge of securing your organization’s wired and wireless networks, and all of the devices associated with them. There are several questions you should ask yourself: What kind of cables does your network use, what are the vulnerabilities of those cables, and how can they be secured? What are your future cabling plans? Do you have wireless networks, and if so, how can you protect data that is flinging through the air? How many devices can be accessed either from users on the network or remotely? And are there any older devices that need to be updated, or simply removed?
Verifying that all network devices, cables, and other mediums are secure might sound like a daunting task at first, but let’s take it step by step and discuss how this can be done. We’ll begin with wired networks, cables, and the devices you might find on a wired network; then we’ll move onto wireless transmissions. At the end of the chapter, we will show a final piece of network documentation that sums up a lot of the security precautions that we’ve implemented in Chapters 5 through 7.
Foundation Topics: Securing Wired Networks and Devices
Implementing a security plan for your wired network is critical. In Chapter 5, “Network Design Elements and Network Threats,” we talked about the design elements of your network and the possible threats to those design elements and to the computers and servers on the network. In Chapter 6, “Network Perimeter Security,” we talked about some of the security tools such as firewalls that could be used to protect the network. But what connects it altogether?—Usually the wired network. Now let’s get into the nitty-gritty of the wired network. Not only are the devices wired to the network targets for attack, but the wires could be targets as well. Some attacks could come from inside the network, whereas other attacks could be external. Let’s start with some of the common vulnerabilities to network devices.
Network Device Vulnerabilities
Devices that reside on your network might include hubs, switches, routers, firewalls, NIDS/NIPS appliances, and more. Each of these devices can be vulnerable in their default state. Most devices are sold with simple default accounts and blank or weak passwords. In some cases, it’s easy for users to escalate their privileges to gain access to resources that they normally would not have access to. Some devices and computers can be the victim of backdoors that programmers did not remove, or forgot to remove, which enable access for attackers. And of course, a good network administrator will protect against network attacks such as denial of service. Let’s go through each of these one by one and show how to protect against these vulnerabilities to help mitigate risk.
Default Accounts
A lot of the networking devices available to organizations are initially installed with a default set of user credentials; this is the default account. The default account might be called administrator, or admin, or something else similar. If possible, this default account should be changed to a new name, because attackers are aware of default account names. This also applies to computers and servers, as we mentioned in Chapter 3, “OS Hardening and Virtualization.” By renaming the default account, or by removing it altogether, you add a layer of security that makes it more difficult for an attacker to figure out which account has administrative access to the device. One example of this is the D-Link DIR-655 SOHO router we have mentioned in previous chapters. It is common knowledge that these devices (and many other SOHO routers) are set up by default with the username admin and a blank password. This is one of the first things you should change before you connect it to the Internet. Although the DIR-655 does not enable you to change the username, it certainly enables you to change the password. And a lot of these devices allow a separate user account as well, which might have varying levels of access depending on the device. This should either be set with a complex password or disabled altogether.
If any guest accounts exist, it is recommended that you disable these accounts. And again, this applies to network devices and computers. The guest account will usually not be enabled, but you should always check this just in case. Of course, more important than the account name or the username is the password. If you have to use a guest account, set a complex password! More on passwords in just a little bit.
Weak Passwords
Passwords should be as complex as possible. A weak password can be cracked by an attacker in a short time. Many network devices come stock with no password at all; so, your first order of business should be to create a complex password. It is common knowledge that a strong password is important for protecting a user account, whether the account is with a bank, at work, or elsewhere. The same goes for network devices. But what is a strong password? Many organizations define a strong password as a password with at least 8 characters, including at least one uppercase letter, one number, and one special character. The best passwords have the same requirements but are 14 characters or more. Many password checker programs are available on the Internet, for example Microsoft’s password checker at www.microsoft.com/protect/yourself/password/checker.mspx.
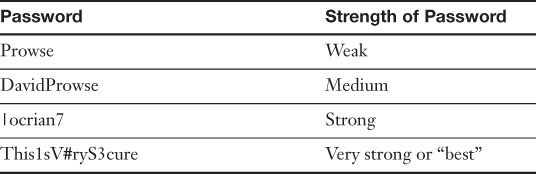
Let’s look at Table 7-1. This table gives some examples of weak passwords and strong passwords.
Table 7-1. Weak, Strong, and Stronger Passwords
![]()
The first password in Table 7-1 is weak; even though it has an uppercase P, it is only 6 characters in length. The second password is only medium strength; it has 11 characters but only two uppercase characters, and nothing else is special about it. However, notice the third password is using the pipe symbol instead of the letter L. This is a special character that shares the backslash key on the keyboard. Because it has a special character, and a number, and that it has 8 characters in total, it is considered to be a strong password. In the last password, we have 16 characters, including 3 uppercase letters, 2 numbers, and 1 special character. These methods make for an extremely strong password that would take a super-computer many years to crack.
Privilege Escalation
Privilege escalation is the act of exploiting a bug or design flaw in a software or firmware application to gain access to resources that normally would be protected from an application or user. This results in a user gaining additional privileges, more than were originally intended by the developer of the application. For example, if a particular user can read another user’s e-mail without authorization. Other programs, such as Cisco Call Manager, have also been the victim of privilege escalations, although patches are regularly released if issues like these are discovered. Buffer overflows are used on Windows computers to elevate privileges as well. To bypass digital rights management (DRM), attackers use a method known as a jail break, another type of privilege escalation. Malware will also attempt to exploit privilege escalation vulnerabilities, if any exist on the system. Privilege escalation can also be attempted on network devices. Generally, the fix for this is simply to update the device and to check on a regular basis if any updates are available. For example, our D-Link DIR-655 mentioned previously has a user account and an admin account. If a device like this isn’t properly updated, an attacker can take advantage of a bug in the firmware to elevate the privileges of the user account. Couple this with the fact that a person forgot to put a password on the user account (or disable it) and your network could be in for some “fun.” It is also possible on some devices to encrypt the firmware component. Following are a couple different types of privilege escalation:
![]()
• Vertical privilege escalation—When a lower privileged user accesses functions reserved for higher privilege users, for example, if a standard user can access functions of an administrator. This is also known as privilege elevation and is the most common description.
• Horizontal privilege escalation—When a normal user accesses functions or content reserved for other normal users, for example, if one user reads another’s e-mail. This can be done through hacking or by a person walking over to other people’s computers and simply reading their e-mail! Always have your users lock their computer (or log off) when they are not physically at their desk!
There is also privilege de-escalation, when high privileged but segregated users can downgrade their access level to access normal users’ functions. Sneaky admins can attempt this to glean confidential information from an organization. It’s a two-way street when it comes to security; you should think three-dimensionally when securing your network!
Back Doors
Backdoors are used in computer programs to bypass normal authentication and other security mechanisms in place. Originally backdoors were used by developers as a legitimate way of accessing an application, but soon after they were implemented, attackers would use backdoors to either make changes on network devices, or the attacker would create a completely new application that would act as a backdoor, for example Back Orifice, which enables a user to control a Windows computer from a remote location. Often, it is installed via a Trojan horse; this particular one is known as a remote access Trojan or RAT. Some worms install backdoors on computers so that remote spammers can send junk e-mail from the infected computers, or so an attacker can attempt privilege escalation. Unfortunately, there isn’t much that can be done about backdoors aside from updating or patching the infected system and keeping on top of updates. However, if network administrators were to find out about a new backdoor, they should inform the manufacturer of the device or the application as soon as possible. Backdoors are less common nowadays, because their practice is usually discouraged by software manufacturers and by makers of network devices.
Network Attacks
Denial of service and many other network attacks can cause havoc on your network devices. It is important to keep abreast of these latest attacks and to verify that all systems and network devices are updated accordingly. Use smart network intrusion prevention systems (NIPS) to identify new attacks and prevent them from causing trouble on your networks. For more information on denial of service attacks and other types of network attacks, see the section titled “Ports, Protocols, and Malicious Attacks” in Chapter 5.
Other Network Device Considerations
Some network administrators use remote ports on their network devices to remotely administer that device. These ports can be used maliciously as well. If the remote port is not to be used, it should be disabled. If it is to be used, a strong authentication system should be employed, and data encryption should be considered. This applies to routers, switches, servers, and PBX equipment. For more specific ways to protect your network devices, see the section “Network Design” in Chapter 5.
In some cases a network administrator uses the Telnet program to access network equipment remotely from another site or from within the local area network. This practice should be shunned because Telnet by default is not secure; it does not encrypt data, including passwords, and default implementations of Telnet have no authentication scheme that ensures that communications will not be intercepted. In addition most Telnet programs have other vulnerabilities and risk associated with them. Instead of using Telnet, administrators should opt for another protocol such as Secure Shell (SSH).
Cable Media Vulnerabilities
The most commonly overlooked item in a network is the cabling. The entire cabling infrastructure (or cabling plant) includes the cables themselves, network jacks, patch panels, punch blocks, and so on. You need to think about what types of cabling you are using, what vulnerabilities they have, and how to combat those vulnerabilities in an attempt to reduce risk. Following are three types of cabling that you might have implemented in your network:
• Twisted-pair—A copper-based cable with four pairs of wires (for a total of eight wires), each of which is twisted together along the length of the cable. It is the most common type of network cable; it sends electrical signals to transfer data and uses RJ45 plugs to connect to ports on hosts. The most common security problem with twisted-pair cable is crosstalk, which we discuss later.
![]()
• Fiber-optic—A glass/plastic-based cable that sends light (photons) instead of electricity. It is composed of one or more thin strands known as fibers that transfer the data. Generally, this is the most secure type of cable that can be used in a network. It is not susceptible to EMI, RFI, or data emanations and is the least susceptible cable to wiretapping.
• Coaxial—A less used copper-based cable that has a single copper core. Although not used for connections to hosts anymore, you might see it used with special connections, perhaps for the Internet or for video. In smaller companies’ networks, it is common to see an RG-6 cable used for the Internet connection. The most common security risk with coaxial cable is data emanation, which we discuss later.
Each of these cables has its own inherent vulnerabilities; let’s talk about a few of these now.
Interference
Interference is anything that disrupts or modifies a signal traveling along a wire. There are many types of interference but you should know about only a few for the exam, including the following:
• Electromagnetic interference (EMI)—A disturbance that can affect electrical circuits, devices, and cables due to electromagnetic conduction or radiation. Just about any type of electrical device can cause EMI: TVs, microwaves, air conditioning units, motors, unshielded electrical lines, and so on. Copper-based cables and network devices should be kept away from these electrical devices if at all possible. If not possible, shielded cables can be used, for example shielded twisted pair (STP). Or the device that is emanating EMI can be shielded. For example, an air conditioning unit could be boxed in with aluminum shielding in an attempt to keep the EMI generated by the AC unit’s motor to a minimum. In addition, electrical cables should be BX (encased in metal), and not Romex (not encased in metal); most municipalities require this to meet industrial and office space building code. EMI can also be used in a mischievous manner, known as radio jamming. But the methods listed here can help defend against this as well.
![]()
• Radio frequency interference (RFI)—Interference that can come from AM/FM transmissions and cell towers. It is often considered to be part of the EMI family and will sometimes be referred to as EMI. The closer a business is to one of these towers, the greater the chance of interference. The methods mentioned for EMI can be employed to help defend against RFI. In addition, filters can be installed on the network to eliminate the signal frequency broadcast by a radio tower, though this usually does not affect standard-wired Ethernet networks. Wireless signals from wireless networks and cell phones can interfere with speakers and other devices; try to keep speakers and monitors away from cell phones and wireless network adapters. Try to keep wireless access points away from computers, printers, monitors, and speakers, ands switches, routers, and other network equipment.
Another common type of interference is crosstalk that we discuss in next.
Crosstalk
Crosstalk is when a signal transmitted on one copper wire creates an undesired effect on another wire; the signal “bleeds” over, so to speak. This first occurred when telephone lines were placed in close proximity to each other. Because the phone lines were so close, the signal could jump from one line to the next intermittently. If you have ever heard another conversation while talking on your home phone (not cell phones mind you) you have been the victim of crosstalk. This can happen with connections made by a modem as well, causing considerable havoc on the data transfer.
Note
With cell phones, crosstalk is also known as co-channel interference or CCI, a different type not covered on the 2008 Security+ objectives.
To combat crosstalk, you can use twisted-pair cable. This helps when regular analog signals are sent across the wires and applies only to standard POTS connections and computer modems that use POTS connections. The beauty of the twists in twisted-pair cabling is that the signal has less chance of leaking to other wires, in comparison to straight wires next to each other and bundled together. If the signals are digital, for example, Ethernet data transfers or voice over IP, you already have an environment less susceptible to crosstalk, in comparison to an analog environment. Data can still bleed over to other wires, but it is less common, because the twists of the wires have been precisely calculated by the manufacturer. Sometimes this occurs due to bunches of cables bundled too tightly, which could also cause crimping or other damage to the cable. If this is the case, a trusty continuity tester will let you know which cable has failed; normally this would have to be replaced. When it comes to twisted-pair cabling, crosstalk is broken down into two categories: near end crosstalk (NEXT) and far end crosstalk (FEXT). NEXT is when measured interference occurs between two pairs in a single cable, measured on the cable end nearest the transmitter. FEXT is when like interference occurs but is measured at the cable end farthest from the transmitter.
If crosstalk is still a problem, even though twisted-pair cable has been employed, and digital data transmissions have been implemented, shielded twisted pair (STP) could be used. Although twisting individual pairs can minimize crosstalk between wire pairs within a cable, shielding an entire cable will minimize crosstalk between cables. Normally, companies opt for regular twisted-pair cabling, which is unshielded (also known as UTP), but sometimes, too much interference exists in the environment to send data effectively, and STP must be utilized.
Data Emanation
Data emanation (or signal emanation) is the electromagnetic (EM) field generated by a network cable or network device, which can be manipulated to eavesdrop on conversations or to steal data. Data emanation is sometimes also referred to as eavesdropping, although this is not accurate.
Data emanation is the most commonly seen security risk when using coaxial cable, depending on the type of coaxial cable but can also be a security risk for other copper-based cables. There are various ways to tap into these (EM) fields to get unauthorized access to confidential data. To alleviate the situation, there are several solutions. For example, you could use shielded cabling or run the cabling through metal conduits. Secondly, you could use electromagnetic shielding on devices that might be emanating an electromagnetic field. This could be done on a small scale by shielding the single device or on a larger scale shielding an entire room, perhaps a server room; this would be an example of a Faraday cage. If an entire room is shielded, electromagnetic energy cannot pass through the walls in either direction. So, if a person attempts to use a cell phone inside the cage, it will not function properly, because the signal cannot go beyond the cage walls. More important, devices such as cell phones, motors, and wireless access points that create electromagnetic fields and are outside the cage cannot disrupt electromagnetic-sensitive devices that reside inside the cage. Server rooms and cabling should be protected in some way, especially if the data that travels through them is confidential. Studies are constantly done about signal emanations and how to contain them. A group of standards known as TEMPEST refers to the investigations of conducted emissions from electrical and mechanical devices, which could be compromising to an organization.
Tapping into Data and Conversations
This is a huge subject, and we could talk about it for days without scratching the surface. One item of note: ANY system can be tapped or hacked. It’s just the lengths you must go to that can vary; it depends on the network, cabling, and security precautions already in place.
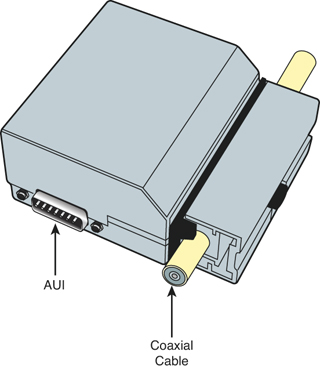
One of the items on the Security+ exam is “vampire taps”; this is number 2.6 in the 2008 Security+ objectives. This type of tap deals with coaxial cable, namely 10BASE5 or “thicknet,” which uses a bus topology. Although this is a deprecated network type, the vampire tap is nevertheless still on the objectives, so you should know it for the exam. The vampire tap works by piercing into the 10BASE5 cable. The device surrounds the cable and actually taps into the copper core. It has an Attachment User Interface (AUI) that enables a new connection to be made to a PC, as shown in Figure 7-1; some have RG-58 coaxial connections as well. The point of the device is to enable an administrator to tap into the network and add a PC to it, without having to bring the entire network down. Without the device, a network admin would have to cut the cable and attach a T-connector, which would indeed require stopping the network until the job is done. Now, it stands to reason that the vampire tap could be used for more insidious purposes by attackers, but only if they have physical access to the coaxial cable. When attackers have access by using a vampire tap, they can monitor the network in a transparent fashion; meaning, the network admin won’t even know that the monitoring is taking place. Again, this is an older type of technology, and an older way of hacking in to a system, but it should make you realize that any network can be tapped.
Figure 7-1. Illustration of a Vampire Tap
![]()
“Tapping” today takes on a whole new meaning. Instead of tapping directly onto a coaxial cable, tapping can mean any one of the following and more:
• Connecting to a punch block, or RJ11 jack with a butt set—A butt set (or lineman’s handset) is a device that looks similar to a phone but has alligator clips that can connect to the various terminals used by phone equipment enabling a person to test a new line or listen in to a conversation. The device is used primarily by telecommunications technicians but can obviously be used for malicious purposes as well. There are analog versions of this device (for POTS systems) and digital versions (for digital systems such as VoIP and so on) that act as packet capturing devices (sniffers). To protect against this, keep all punch blocks and other phone equipment in a locked server room or wiring closet. Although expensive, there are also lockable RJ11 jacks, but it would probably be less costly to install a network of cameras in the building, especially if your organization wants them for other purposes as well.
• Plugging into an open port of a twisted-pair network—This could be either at a RJ45 wall plate or in the server room (not as easy) at an open port of a hub or switch. Unused ports, whether on a hub or switch, or at a computer station’s RJ45 jack, should be disabled. Also, central connecting devices such as hubs and switches should be locked in the server room, and only properly authenticated individuals should have access.
• Splitting the wires of a twisted-pair connection—This can be done anywhere along a cable but would disrupt communications for that individual computer or segment while it is being done. By cutting the twisted-pair cable and soldering a second twisted-pair cable to the appropriate wires (for example, Ethernet 568B networks use the orange and green pairs of wires by default), a person could eavesdrop on all communications on that segment. Cables should not be exposed if at all possible. Cable runs should be above the drop ceiling and inside the walls, perhaps run in conduit. It is understandable that computers need to connect to RJ45 jacks by way of patch cables; if a computer suddenly loses its connection to the network, an alert can be sent to junior administrators, prompting them to investigate why it occurred.
• Using a spectral analyzer to access data emanations—Spectral analyzers can measure the composition of electrical waveforms at specific frequencies (for example 100 MHz on a 100BASE-T twisted-pair network). These can also decode encrypted transmissions. These types of devices should not be allowed in the building (unless used by authorized personnel). A metal detector could be used at the entrance of the building, and again, video cameras can help detect this, and perhaps even prevent mischievous people from attempting to do so, just because they think they might be under surveillance.
• Using a passive optical splitter for fiber-optic networks—This is a more expensive device and would need access to a cable. Plus the process of getting it to work is difficult. (And again, this would disrupt communications for a time.) The preceding listed methods apply to defending against this as well. Because it is difficult to implement an optical splitter properly, this could cause chromatic dispersion on the particular fiber segment. Chromatic dispersion (and subsequent loss of data) could also occur if the fiber optic cable is too long. Administrators could monitor the network for dispersion and have alerts sent to them in the case that it occurs. The most common example of chromatic dispersion is the rainbow. For example, if light is sent through a prism, the light will be refracted (dispersed) into the rainbow of colors. Although not exactly how it would occur on a fiber optic cable, if this were to happen, data transmissions would fail.
Keep in mind that the Security+ exam does not go too far in depth for this subject, but realize that you might get a question on wire tapping, and remember that any network can be hacked! It is more common to attempt hacking into wireless networks. So let’s delve into the basics of that immense subject next.
Securing Wireless Networks
Wireless networks pose a whole new set of problems for a network administrator. Wireless access points and wireless network adapters need to be secure from attackers that could be just about anywhere as long as they’re within range of the wireless network. There are several points we cover that can help you secure your wireless access point, wireless network adapters, and any other wireless devices. In this section, you learn how to watch out for wireless transmission vulnerabilities and some of the Bluetooth vulnerabilities that you should be aware of.
Wireless Access Point Vulnerabilities
The wireless access point is the central connecting device for wireless network adapters that might exist in PCs, laptops, handheld computers, PDAs, and other similar devices. You need to secure any broadcasts that the wireless access point might make and verify that transmissions are encrypted with a strong encryption technique. It’s also important to watch out for rogue access points and round up any nomads on your network.
Secure the Administration Interface
The first thing you should look at when it comes to wireless access points is the administration interface, or console. The act of accessing the administration interface is sometimes referred to as “romming” into the access point. By default, most access points have a blank password or a simple and weak password, for example “password.” The first step you want to take is to access the administration interface and modify the password; change it to a complex password. Next, consider disabling remote administration if it is not necessary. Your organization might require it, but it depends on several factors. If you are dead set on leaving it enabled, be completely sure that the remote administration password is complex.
SSID Broadcast
The service set identifier (SSID) is one of several broadcasts that a wireless access point makes. It identifies the network and is the name of the access point used by clients to connect to the wireless network. It is on by default. After all your clients have been connected to the wireless network, consider disabling the SSID broadcast. Though there will still be ways for hackers to get into your access point, this at least provides a preliminary level of security. The average user cannot see the SSID and cannot connect to the wireless network. In the future if you need to add clients, simply enable the SSID temporarily, connect the client, and then disable the SSID. This might not be a factor if you are in a large building. But if you are in a smaller structure, the wireless access point’s broadcast range may leak out beyond your organization’s property. You can also try reducing the transmitter power of the wireless access point. Although not all access points have this function, some do and it can help to fine-tune the area that the access point serves.
Rogue Access Points
Sometimes companies lose track of the wireless access points on their network. Keep track of all your devices with network documentation. Use network mapping programs and Microsoft Visio to detect and document any rogue access points. Older access points, especially ones with weak encryption, should be updated, disabled, or simply disconnected from the network. Some companies may have a dozen wireless access points and additional wireless devices such as repeaters, and it may be difficult to keep track of these. In this case, a network mapping program can be one of your best friends. In addition, you can search for rogue access points with a laptop or handheld computer with Microsoft’s Wireless Zero Configuration tool, the wireless network adapter’s built-in software, or third-party applications such as AirMagnet or NetStumbler.
Weak Encryption
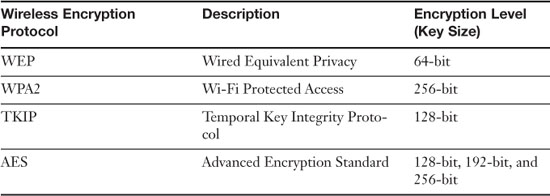
Weak encryption or no encryption can be a couple of the worst things that can happen to a wireless network. This can occur for several reasons, for example if someone wanted to connect an older device or a device that hasn’t been updated, and that device can run only a weaker, older type of encryption. It’s important to have strong encryption in your network; as of the writing of this book, WPA2 is the strongest encryption you can use. It can be used with TKIP or AES. Remember that the encryption level of the wireless access point and the network adapters that connect to it need to be the same. Table 7-2 defines some of the available wireless encryption types.
Table 7-2. Wireless Encryption Methods
![]()
WEP is the weakest type of encryption; WPA is stronger, and WPA2 is the strongest of the three. However, it is better to have WEP as opposed to nothing. If this is the case, use encryption keys that are difficult to guess, and consider changing those keys often. Some devices can be updated to support WPA, whether it is through a firmware upgrade or through the use of a software add-on. Figure 7-2 shows a typical wireless access point with WPA2 and AES configured; AES is the cipher type. The preshared key used to enable connectivity between wireless clients and the access point is a complex pass-phrase.
Figure 7-2. Wireless Security Configuration on a Typical Access Point

Other Wireless Access Point Security Strategies
Strategic placement of a WAP is vital. Usually, the best place for a WAP is in the center of the building. This way, equal access can be given to everyone on the perimeter of the organization’s property, and there is the least chance of the signal bleeding over to other organizations. If needed, attempt to reduce the transmission power of the antenna; which can reduce the broadcast range of the WAP. Also, to avoid interference in the form of EMI or RFI, keep wireless access points away from any electrical panels, cables, devices, motors, or other pieces of equipment that might give off an electromagnetic field. If necessary, shield the device creating the EM field, or shield the access point itself. Sheesh, I am starting to sound bossy!
Many wireless access points come with a built-in firewall. If the firewall is utilized, the stateful packet inspection (SPI) option and NAT filtering should be enabled. The wireless access point might also have the capability to be configured for MAC filtering, which can filter out which computers can access the wireless network. The WAP does this by consulting a list of MAC addresses that have been previously entered. Only the network adapters with those corresponding MAC addresses can connect; everyone else cannot join the wireless network. In some cases, a device might broadcast this MAC table. If this is the case, look for an update for the firmware of the access point, and again, attempt to fine-tune the broadcast range of the device so that it does not leak out to other organizations.
It is also possible to include the IEEE 802.1x standard for port-based network access control that can provide for strong authentication. For a wireless access point to incorporate this kind of technology, it must also act as a router, which adds the duty of wireless gateway to the access point.
Another option is to consider encryption technologies on the Application Layer, such as SSL, SSH, or PGP; these and others can help to secure data transmissions from attackers that have already gained access to the wireless network. For more information on encryption types see the section “Security Protocols” in Chapter 13, “Encryption Protocols, Keys, and Certificates,” When it comes down to it, authentication and a strong encryption protocol such as WPA (or WPA2) are the two security precautions that will best help to protect against network attacks.
Finally, another option is to not run wireless at all. It’s quite tough to hack into a wireless network that doesn’t exist! Some companies opt for this as strange as it may seem, because they have deduced that the costs of implementation, administration, maintenance, and security outweigh the benefits of having a wireless network. Personally, I don’t run any wireless networks at my home (aside from any testing purposes), my home is cabled up 100%; bedrooms, bathrooms, attic, you name it! J However, if you decide to go down this road, make sure that any devices that enable wireless access have those wireless functions disabled. This includes wireless access points, laptops, and other mobile devices that have wireless adapters, and any Bluetooth, infrared, or other wireless transmitters.
Wireless Transmission Vulnerabilities
Because wireless networks can transmit information through air or space, data emanations are everywhere and can easily be identified by people using the right tools. One deed that can be considered an attack on wireless networks is known as wardriving; this is the act of searching for wireless networks by a person in a vehicle, through the use of a device with a wireless antenna, often times a particularly strong antenna. A basic example of this would be a person in a car with a laptop, utilizing the freely downloadable NetStumbler software. When wardrivers find a network, they can attempt to crack the password or pass-phrase to gain access to the wireless network. This might be done by guessing; you’d be surprised how much this works; it is estimated that more than 40% of wireless networks are unprotected. It could also be done with dictionary or brute force attacks. You can find more information on password cracking in the section “Assessing Vulnerability with Security Tools” in Chapter 10, “Vulnerability and Risk Assessment.”
Note
See the step-by-step lab showing a basic wardriving example and how to protect against this in the “Hands-On Labs” section.
Ways to protect against wardriving include hiding the SSID of the wireless access point, proper positioning of the WAP, using strong encryption, and changing the pass-phrase (encryption key) at regular intervals.
Bluetooth Vulnerabilities
Bluetooth, like any wireless technology, is vulnerable to attack as well. Bluejacking and Bluesnarfing are two types of vulnerabilities to Bluetooth-enabled devices. Bluetooth is also vulnerable to conflicts with other wireless technologies. For example, some WLAN (or Wi-Fi) standards use the 2.4-GHz frequency range, as does Bluetooth, and even though Bluetooth uses frequency hopping, conflicts can occur between 802.11g or 802.11b networks, and Bluetooth personal area networks. To avoid this, use Bluetooth version 1.2 devices or greater, which employ adaptive frequency-hopping, improving resistance to radio interference. Also, consider placing Bluetooth access points (if they are used) and WLAN access points in different areas of the building. Some companies have policies governing Bluetooth usage; in some cases, it is not allowed if 802.11 standards are in place, and in some cases a company will enforce rules that say Bluetooth can be used only outside the building. In other cases, a company will put its 802.11 devices on specific channels or use WLAN standards that use the 5-GHz range.
Bluejacking
Bluejacking is the sending of unsolicited messages to Bluetooth-enabled devices such as mobile phones and PDAs. Bluejacking is usually harmless but may appear that the Bluetooth device is malfunctioning. Originally, bluejackers would send only text messages, but with newer Bluetooth-enabled cell phones and PDAs, it is possible to send images and sounds as well. Bluejacking is used in less-than-reputable marketing campaigns. Bluejacking can be stopped by setting the affected Bluetooth device to “undiscoverable” or by turning off Bluetooth altogether.
Bluesnarfing
I known what you are thinking: The names of these attacks are starting to get a bit ridiculous! I guarantee it will improve as we progress through the rest of this book! Anyways, bluesnarfing is the unauthorized access of information from a wireless device through a Bluetooth connection. Generally, bluesnarfing is the theft of data (calendar information, phonebook contacts, and so on). It is possible to steal other information as well, but to pilfer any of this data, a pairing must be made between the attacking Bluetooth device and the Bluetooth victim. Sony, Nokia, and Ericsson phones are among the most common victims of bluesnarfing. Ways of discouraging bluesnarfing include using a pairing key that is not easy to guess; for example, stay away from 0000 or similar default Bluetooth pairing keys! Otherwise, Bluetooth devices should be set to “undiscoverable” (only after legitimate Bluetooth devices have been set up, of course), or Bluetooth can be turned off altogether, especially in areas that might be bluesnarfing playgrounds, for example, Times Square, NY. Bluesnarfing is considered by some to be a component of bluejacking, but for the exam, try to differentiate between the two.
Exam Preparation Tasks: Review Key Topics
Review the most important topics in the chapter, noted with the Key Topics icon in the outer margin of the page. Table 7-3 lists a reference of these key topics and the page numbers on which each is found.
![]()
Table 7-3. Key Topics for Chapter 7
Complete Tables and Lists from Memory
Print a copy of Appendix A, “Memory Tables,” (found on the DVD), or at least the section for this chapter, and complete the tables and lists from memory. Appendix B, “Memory Tables Answer Key,” also on the DVD, includes completed tables and lists to check your work.
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
electromagnetic interference (EMI),
service set identifier (SSID),
Wired Equivalent Privacy (WEP),
Wi-Fi Protected Access (WPA),
Advanced Encryption Standard (AES),
Temporal Key Integrity Protocol (TKIP),
Hands-On Labs
Complete the following written step-by-step scenarios. After you finish (or if you do not have adequate equipment to complete the scenario), watch the corresponding video solution on the DVD.
If you have additional questions, feel free to post them at my website: www.davidlprowse.com in the Ask Dave forum. (Free registration is required to post on the website.)
Equipment Needed
• A computer with Internet access and a wireless network adapter.
• Web browser: Internet Explorer version 6 and higher or Firefox are recommended.
• D-Link DIR-655 or similar router:
• If you have access to an actual DIR-655, make sure that it is updated to the latest firmware. Then connect to it by opening a web browser and typing the IP address of the router in the URL field, for example, 192.168.0.1. Next, at the login screen, type the password for the router, and click the Log In button. This should display the Device Information page. Start at this page for each of the three labs.
• If you do not have access to an actual DIR-655, use the D-Link simulator located at http://support.dlink.com/Emulators/dir655/index.html. Then select the 1st option: DIR-655 Device UI. Next, at the login screen, click the Log In button. (A password is necessary.) This should display the Device Information page. Start at this page for each of the three labs.
• NetStumbler software: www.netstumbler.com/downloads/
Lab 7-1: Securing a Wireless Device: 8 Steps to a Secure Network
In this lab, you secure a wireless access point and make it virtually unhackable. The steps are as follows:
Step 1. Update firmware.
A. On the main Device Information page, click the Tools link near the top of the window. This should bring up the Tools page.
B. On the left side, click the Firmware link. This should display the Firewall Settings window.
C. If you have an actual DIR-655, click the Check Now button. This looks for the latest firmware version. The DIR-655 simulator will be updated to the latest version. If you must download the firmware, note where it is downloaded.
D. Back at the Firmware page of the device, click the Browse button to search for the downloaded firmware. Then click the Upload button to install the new firmware. A restart is required.
Consider checking the Automatically Check Online and Email Notification checkboxes so that the device will look for upgrades and let you know as they become available.
Step 2. Set passwords!
A. Still on the Tools page, click the Admin link to the left.
B. In the Admin Password section, enter a complex password and verify it.
C. In the User Password section, enter a different complex password and verify it.
Step 3. Disable remote administration.
A. On the same Tools > Admin page deselect the Enable Remote Management checkbox. Then, click the Remote Admin Inbound Filter drop-down menu and select Deny All. This eliminates remote management even if the Enable Remote Management checkbox is somehow selected in the future.
Step 4. Disable SSID broadcasting.
A. Click the Setup link in the top banner.
B. Click the Wireless Setting link on the left side.
C. Click the Manual Wireless Network Setup button.
D. Change the Visibility Status by clicking the Invisible radio button. It is also wise to change the default SSID to a different name; dlink is commonly known and should be modified even if you disable the SSID.
Step 5. Enable WPA2 and AES.
A. Still on the Wireless page, click the Security Mode drop-down menu.
B. Select WPA-Personal.
C. Scroll down and in the WPA Mode drop-down menu select WPA2 only.
D. In the Cipher Type drop-down menu select AES.
E. Type a complex preshared key!!! Change this key as often as you change your toothbrush!
F. Click the Save Settings button at the top of the window. A router restart is usually required.
Consider also using Wi-Fi Protected Setup under the Advanced section.
Step 6. Reduce the output transmitting power of the WAP. This is not possible on the DIR-655, but if you have a WAP that incorporates this functionality, you should use it to “shape” your wireless network and prevent leakage to other organizations.
Step 7. Enable MAC filtering.
A. Click the Advanced link in the top banner.
B. Click the Network Filter link on the left side.
C. Add MAC addresses that are either allowed or denied access.
If you haven’t already, check out the Chapter 6, Lab 3: MAC filtering video.
Step 8. Configure other rules and ACLs. This might include inbound filters, access control policies, application rules, and so on, each of which are located in the Advanced page.
Watch the solution video in the “Hands-On Scenarios” section of the DVD.
Lab 7-2: Wardriving...and The Cure
In this lab, you see a basic example of wardriving and how to defend against this. The steps are as follows:
Step 1. Make sure your computer’s wireless adapter is enabled and functioning properly.
Step 2. Attempt to access wireless networks with the Wireless Zero Configuration tool (built in to Microsoft).
Step 3. Attempt to access wireless networks with proprietary software from the network adapter’s manufacturer.
Step 4. Use NetStumbler to view available wireless networks.
A. Download and install the NetStumbler program from www.netstumbler.com/downloads/.
B. Open and run the program to view possible networks.
Step 5. Defend against people attempting to wardrive by
A. Configuring a strong password
B. Configuring strong encryption
C. Disabling SSID
D. Enabling MAC filtering
Watch the solution video in the “Hands-On Scenarios” section of the DVD.
View Recommended Resources
For readers who want to brush up on their networking topics:
• Prowse, David L. CompTIA Network+ Video Mentor, First Edition. Que. 2009.
• Harwood, Mike. CompTIA Exam Prep Network+ N10-004, Third Edition. Que. 2009.
• Comer, Douglas. Computer Networks and Internets (Fifth Edition). Prentice Hall. 2008.
AirMagnet: www.airmagnet.com/
NetStumbler: www.netstumbler.com/
Some decent security websites (there are many more!):
• Security Focus: www.securityfocus.com/
• Cert: www.cert.org/
Answer Review Questions
Answer the following review questions. You can find the answers at the end of this chapter.
1. Which of the following is the most secure protocol to use when accessing a wireless network?
A. WEP
B. WPA
C. WPA2
D. WEP2
2. What type of cabling is the most secure for networks?
A. STP
B. UTP
C. Fiber optic
D. Coaxial
3. What should you configure to improve wireless security?
A. Enable the SSID
B. IP spoofing
C. Remove repeaters
D. MAC filtering
4. In a wireless network, why is an SSID used?
A. To secure the wireless access point
B. To identify the network
C. To encrypt data
D. To enforce MAC filtering
5. What is the most commonly seen security risk of using coaxial cable?
A. Data that emanates from the core of the cable
B. Crosstalk between the different wires
C. Chromatic dispersion
D. Time domain reflection
6. Of the following, what is the most common problem associated with UTP cable?
A. Crosstalk
B. Data emanation
C. Chromatic dispersion
D. Vampire tapping
7. What two security precautions can best help to protect against wireless network attacks?
A. Authentication and the WEP
B. Access control lists and WEP
C. Identification and WPA2
D. Authentication and WPA
8. Which of the following cables suffers from chromatic dispersion if the cable is too long?
A. Twisted-pair cable
B. Fiber optic cable
C. Coaxial cable
D. USB cables
9. Which of the following cable media is the least susceptible to a tap?
A. Coaxial cable
B. Twisted-pair cable
C. Fiber optic cable
D. CATV cable
10. Which of the following, when removed, can increase the security of a wireless access point?
A. MAC filtering
B. SSID
C. WPA
D. Firewall
11. A wireless network switch has connectivity issues but only when the air-conditioning system is running. What can be added to fix the problem?
A. Shielding
B. A wireless network
C. A key deflector
D. Redundant air-conditioning systems
12. Which of the following is the most secure type of cabling?
A. Unshielded twisted pair
B. Shielded twisted pair
C. Coaxial
D. Category five
13. Which of the following is the least secure type of wireless encryption?
A. WEP 64-bit
B. WEP 128-bit
C. WPA with TKIP
D. WPA2 with AES
14. Which of the following is the unauthorized access of information from a Bluetooth device?
A. Bluejacking
B. Bluesnarfing
C. Blue privileges
D. The Blues Brothers
15. Which of the following can be described as the act of exploiting a bug or flaw in software to gain access to resources which normally would be protected?
A. Privilege escalation
B. Chain of custody
C. Default account
D. Backdoor
Answers and Explanations
1. C. Wi-Fi Protected Access 2 (WPA2) is the most secure protocol listed for connecting to wireless networks. It is more secure than WPA and WEP. Wired Equivalent Privacy (WEP) is actually a deprecated protocol that should be avoided, as is WEP2. The WEP and WEP2 algorithms are considered deficient for encrypted wireless networks.
2. C. Fiber optic is the most secure because it cannot be tapped like the other three copper-based cables; it does not emit EMI. Although shielded twisted pair (STP) offers a level of security due to it’s shielding, it does not offer a level of security like to that of fiber optic and is not the best answer.
3. D. MAC filtering disallows connections from any wireless clients unless the wireless client’s MAC address is on the MAC filtering list.
4. B. The SSID is used to identify the wireless network. It does not secure the wireless access point; one of the ways to secure a wireless access point is by masking the word disabling the SSID. The SSID does not encrypt data or enforce MAC filtering.
5. A. Some types of coaxial cables suffer from the emanation of data from the core of the cable, which can be accessed. Crosstalk occurs on twisted-pair cable. Chromatic dispersion occurs on fiber-optic cable. Time domain reflection is a concept that is used by a TDR.
6. A. Of the listed answers, crosstalk is the most common problem associated with UTP cable. Older versions of UTP cable (for example Category 3 or 5) are more susceptible to crosstalk than newer versions such as Cat 5e or Cat6. Although data emanation can be a problem with UTP cable, it is more common with coaxial cable, as is vampire tapping. Chromatic dispersion is a problem with fiber-optic cable.
7. D. The best two security precautions are authentication and WPA. Although WPA2 is more secure than WPA, the term identification is not correct. WEP is a deprecated wireless encryption protocol and should be avoided.
8. B. Fiber-optic cable is the only one listed that might suffer from chromatic dispersion, because it is the only cable based on light. All the other answers are based on electricity.
9. C. Fiber-optic cable is the least susceptible to a tap because it operates on the principle of light as opposed to electricity. All the other answers suffer from data emanation because they are all copper-based.
10. B. By removing the security set identifier or SSID, the wireless access point will be more secure and will be tougher for wardrivers to access that network. Of course, no new clients can connect to the wireless access point. MAC filtering, WPA, and firewalls are all components that increase the security of a wireless access point.
11. A. By shielding the network switch, we hope to deflect any interference from the air conditioning system. Another option would be to move the network switch to another location.
12. B. Shielded twisted pair is the most secure type of cabling listed. It adds an aluminum sheath around the wires that can help mitigate data emanation. By far, fiber optic would be the most secure type of cabling because it does not suffer from data emanation because the medium is glass instead of copper.
13. A. WEP 64-bit is the least secure type of wireless encryption listed in the possible answers. The answers are listed in order from least secure to most secure.
14. B. Bluesnarfing is the unauthorized access of information from a Bluetooth device, for example, calendar information, phonebook contacts, and so on. Bluejacking is the sending of unsolicited messages to Bluetooth-enabled devices. Blue privileges is not a valid answer, and if you answered the Blues Brothers, you should reread this entire chapter.
15. A. Privilege escalation is as the act of exploiting a bug or flaw in software to gain access to resources that normally would be protected. Chain of custody is the chronological paper trail used as evidence. A default account is an account such as admin set up by the manufacturer on a device; it usually has a blank or simple password. A backdoor is used in computer programs to bypass normal authentication and other security mechanisms that might be in place.