Chapter 9. Access Control Methods and Models
This chapter covers the following subjects:
Access Control Models Defined—This section gets into access control models, such as MAC, DAC, and RBAC, plus methodologies such as implicit deny and job rotation. Before creating and enforcing policies, a plan of action has to be developed, and the access control model to be used should be at the core of that plan.
Rights, Permissions, and Policies—Here, we delve into users, groups, permissions, rights, and policies that can be created on a computer network. By configuring users, templates, and groups in a smart fashion, you can ease administration and increase security at the same time. Policies can control just about anything a user does on the network or on an individual computer. And security templates make it easier than ever to implement a secure set of policies.
This chapter covers the CompTIA Security+ SY0-201 objectives 3.6, 3.7, 3.8, and 3.9.
Controlling user access is of paramount importance. You don’t want just any Tom, Dick, or Harry to gain admittance to your computer network! The first step in controlling user access is to define who needs to have access and what they need to have access to. After this is done, an access control plan must be developed. This primarily consists of choosing an access control model. The model you choose will depend on your organization’s procedures and written policies, and on the level of security you need, and the amount of IT resources at your disposal. After a model has been selected, you should implement as many safe practices as possible to bolster the model’s effectiveness. Then, you can actually implement security on the computers and network. This includes creating and organizing secure users, groups, and other network objects such as organizational units. More important, it incorporates the use of policies and group policy objects. By configuring computer-based policies for your users, groups, and computers, you are forcing them to abide by your organization’s rules.
Foundation Topics: Access Control Models Defined
Access control models are methodologies in which admission to physical areas, and more important, computer systems, is managed and organized. Access control, also known as an access policy, is extremely important when it comes to users accessing secure or confidential data. Some organizations also practice concepts such as separation of duties, job rotation, and least privilege. By combining these best practices along with an access control model, a robust plan can be developed concerning how users will access confidential data and secure areas of a building.
There are several models for access control, each with its own special characteristics that you should know for the exam. The three most commonly recognized models are discretionary access control (DAC), mandatory access control (MAC), and role-based access control (RBAC). Let’s discuss these now.
Discretionary Access Control
Discretionary access control (DAC) is an access control policy generally determined by the owner. Objects such as files and printers can be created and accessed by the owner. Also, the owner decides what users are allowed to have access to the objects, and what level of access they may have. The levels of access, or permissions, are stored in access control lists (ACLs).
Originally, DAC was described in The Orange Book as the Discretionary Security Policy and was meant to enforce a consistent set of rules governing limited access to identified individuals. The Orange Book’s proper name is the Trusted Computer System Evaluation Criteria, or TCSEC, and was developed by the DoD; however, The Orange Book is old (they refer to it in the movie Hackers in the ’90s!), the standard was superseded by new policies in 2002. But the DAC methodology lives on in most of today’s personal computers and client-server networks.
Note
An entire set of security standards was published by the DoD in the ’80s and ’90s known as the “Rainbow Series.” Although The Orange Book is the centerpiece of the series (maybe not in the color spectrum, but as far as security content), there are other ones you might come into contact with such as The Red Book, which is the Trusted Network Interpretation standard. Some of the standards have been superseded, but they contain the basis for many of today’s security procedures.
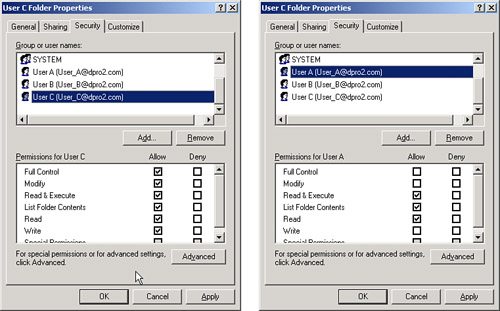
An example of DAC would be a typical Windows computer with two users. User A can log on to the computer, create a folder, stock it with data, and then finally configure permissions so that only she can access the folder. User B can log on to the computer, but cannot access User A’s folder by default, unless User A says so, and configures it as so! However, User B can create his own folder and lock down permissions in the same way. Let’s say that there was a third user, User C, who wanted both User A and User B to have limited access to a folder of their creation. That is also possible by setting specific permission levels, as shown in Figure 9-1. The first Properties window shows that User C (the owner) has full control permissions. This is normal because User C created the folder. But in the second Properties window, you see that User A has limited permissions, which were set by User C.
Figure 9-1. Example of Discretionary Access in Windows
![]()
Note
The owner of a resource controls the permissions to that resource! This is the core of the DAC model.
Windows networks/domains work in the same fashion. Access to objects is based on what user created them and what permissions they assign to those objects. However, in Windows networks we can group users together and assign permissions by way of roles as well. More on that in the role-based access control (RBAC) section.
In a way, DAC, when implemented in client-server networks is sort of a decentralized administration model. Even though an administrator will still have control over most, or all, resources, (depending on company policy) the owners will retain a certain amount of power over their own resources. But, many companies will take away the ability for users to configure permissions. They may create folders, and save data to them, but the permissions list is often generated on a parent folder by someone else and is inherited by the subfolder.
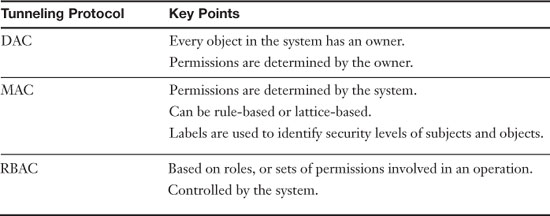
There are two important points to remember when talking about the DAC model: First, that every object in the system has an owner and that the owner has control over its access policy; and second, access rights, or permissions, can be assigned by the owner to users to specifically control object access.
Mandatory Access Control
Mandatory access control (MAC) is an access control policy determined by a computer system, not by a user or owner, as it is in DAC. Permissions are predefined in the MAC model. Historically, it has been used in highly classified government and military multilevel systems, but you will find lesser implementations of it in today’s more common operating systems as well. The MAC model defines sensitivity labels that are assigned to subjects (users) and objects (files and folders). A subject’s label dictates its security level, or level of trust. An object’s label dictates what level of clearance is needed to access it, also known as a trust level. Also, in the MAC model data import and export is controlled. MAC is the strictest of the access control models.
An example of MAC can be seen in FreeBSD version 5.0 and higher. In this OS, access control modules can be installed that allow for security policies which label subjects and objects. The enforcement of the policies is done by administrators or by the OS; this is what makes it mandatory and sets it apart from DAC.
MAC was also originally defined in the Orange Book, but as the Mandatory Security Policy—a policy that enforces access control based on a user’s clearance, and by the confidentiality levels of the data. Even though The Orange Book is deprecated, the concept of MAC lives on in today’s systems and is implemented in two ways:
• Rule-based access control—Also known as label-based access control, this defines whether access should be granted or denied to objects by comparing the object label and the subject label.
• Lattice-based access control—Used for more complex determinations of object access by subjects. Somewhat advanced mathematics are used to create sets of objects and subjects and define how the two interact.
Note
Rule-based access control uses labels, is part of mandatory access control, and should not be confused with role-based access control.
Note
Other related access control models include Bell-La Padula, Biba, and Clark-Wilson. Bell-La Padula is a state machine model used for enforcing access control in government applications. It is a less common multilevel security derivative of mandatory access control. This model focuses on data confidentiality and controlled access to classified information. The Biba Integrity Model describes rules for the protection of data integrity. Clark-Wilson is another integrity model that provides a foundation for specifying and analyzing an integrity policy for computing system.
Role-Based Access Control (RBAC)
Role-based access control (RBAC) is an access model that, like MAC, is controlled by the system, and unlike DAC, not by the owner of a resource. However, RBAC is different than MAC in the way that permissions are configured. RBAC works with sets of permissions, instead of individual permissions that are label-based. A set of permissions will constitute a role. When users are assigned to roles, they can then gain access to resources. A role might be the ability to complete a specific operation in an organization as opposed to accessing a single data file. For example, a person in a bank who wants to check a prospective client’s credit score would be attempting to perform a transaction that is allowed only if that person holds the proper role. So roles are created for various job functions in an organization. Roles might have overlapping privileges and responsibilities. Also, some general operations can be completed by all the employees of an organization. Because there is overlap, an administrator can develop role hierarchies; these define roles that can contain other roles, or have exclusive attributes.
Think about it. Did you ever notice that an administrator or root user is extremely powerful? Perhaps too powerful? And standard users are quite often not powerful enough to respond to their own needs or fix their own problems. Some operating systems counter this problem by creating mid-level accounts such as Power Users (Microsoft) or Operators (Solaris), but for large organizations, this is not flexible enough. Currently, more levels of roles and special groups of users are implemented in newer operating systems. RBAC is used in database access as well and is becoming more common in the healthcare industry and government.
Table 9-1 summarizes the access control models we discussed in the last three sections: DAC, MAC, and RBAC.
Table 9-1. Summary of Access Control Models
![]()
Note
Another type of access control method is known as anonymous access control, for example access to a FTP server. This method uses attributes before access is granted to an object. Authentication is usually not required.
Access Control Wise Practices
After you decide on an access control model that fits your needs, you should consider employing some other concepts. Some of these are used in operating systems automatically to some extent:
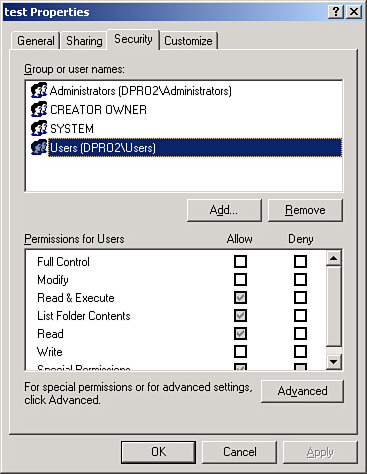
• Implicit deny—This concept denies all traffic to a resource unless the users generating that traffic are specifically granted access to the resource. Even if permissions haven’t been configured for the user in question, that person will still be denied access. This is a default setting for access control lists on a Cisco router. It is also used by default on Microsoft computers to a certain extent. Figure 9-2 shows an example of this. In the folder’s permissions, you can see that the Users group has the Read & Execute, List Folder Contents, and Read permissions set to Allow. But other permissions such as Modify are not configured at all—not set to Allow or Deny. Therefore, the users in the Users group cannot modify data inside the folder because that permission is implicitly denied. Likewise, they can’t take full control of the folder.
Figure 9-2. Example of Implicit Deny on a Windows Folder
![]()
Note
Implicit deny will deny users access to a resource unless they are specifically allowed access.
• Least privilege—This is when users are given only the amount of privileges needed to do their job and not one iota more. A basic example of this would be the Guest account in a Windows computer. This account (when enabled) can surf the web, and use other basic applications, but cannot make any modifications to the computer system. However, least privilege as a principle goes much further. One of the ideas behind the principle is to run the user session with only the processes necessary, thus reducing the amount of CPU power needed. This hopefully leads to better system stability and system security. Have you ever noticed that many crashed systems are due to users trying to do more than they really should be allowed? Or more than the computer can handle? The concept of least privilege tends to be absolute, where an absolute solution isn’t quite possible in the real world. It is difficult to gauge exactly what the “least” amount of privileges and processes would be. Instead, a security administrator should practice the implementation of minimal privilege, reducing what a user has access to as much as possible. Programmers will also practice this when developing applications and operating systems, making sure that the app has only the least privilege necessary to accomplish what it needs to do. This concept is also known as “the principle of least privilege.”
• Separation of Duties (SoD)—This is when more than one person is required to complete a particular task or operation. If one person has too much control, and completes too many portions of a task, it can become a security risk. The more people involved, the less the chance that a job can be compromised. Checks and balances are employed to make sure that the proper equilibrium of users is maintained. One example of this would be the securing of a new network. There might be one or more security administrators in charge of doing the actual planning, and a couple more doing the actual implementation, and finally another group for testing; or perhaps, a third-party company will do the testing, keeping everything on the up and up. It all depends on the size of the organization and the internal trust level (and the IT budget!).
SoD can also be applied to a single user. For example, if a typical user on a Windows 7 computer has a specific set of privileges. But if they want to do something on the system that requires administrative access, User Account Control (UAC) will kick in and ask for the proper credentials to perform the actions of that role. If the credentials cannot be supplied, UAC will block the action, keeping the various duties separate.
• Job rotation—This is one of the checks and balances that might be employed to enforce the proper separation of duties. Job rotation is when users are cycled through various assignments to
• Increase user insight as to overall operations
• Reduce employee boredom
• Enhance employee skill level
• Increase operation security
Job rotation creates a pool of people that can do an individual job and discourages hoarding of information. It also helps to protect the purity of an operation. By cross-training people in each department, you defend against fraud and increase awareness making it easier to detect if it does happen.
By incorporating the implicit deny, least privilege, separation of duties, and job rotation concepts, your total access control plan can be improved greatly.
Rights, Permissions, and Policies
Now that we have a plan for access control, we need to implement it in a tangible way. By strategically setting up organizational units, users, and groups, and by assigning permissions according to our chosen access control model, we can create a safe, guarded working area for all employees. In so doing, we can protect the data on the network.
Users, Groups, and Permissions
User accounts can be added to individual computers or to networks. For example, a Windows client, Linux computer, or Mac can have multiple users. And larger networks that have a controlling server, for example a Windows domain controller, enable user accounts that can access one or more computers on the domain. In a Microsoft domain, users are added in Active Directory Users and Computers (ADUC), as shown in Figure 9-3.
Figure 9-3. The Users Folder Within ADUC on a Windows Server 2003
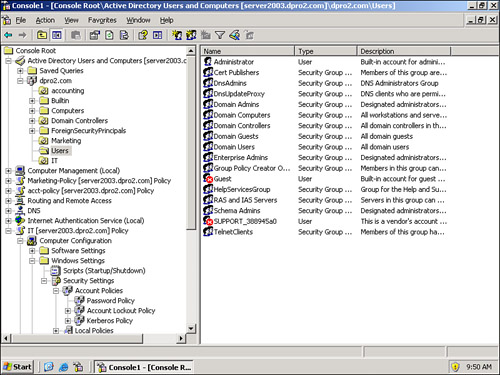
ADUC can be accessed from Administrative Tools or added as a snap-in to an MMC. Users can be added in one of two places:
• In the Users folder—This is located inside the domain name within ADUC.
• In an OU—Organizational units can be created within the domain. These are often made to mimic the departments of a company. In the figure, there are accounting and marketing OUs; users can be created within these OUs.
User rights can be modified within the particular user’s Properties window. There are many more rights associated with a user account that is stored on a Windows Server domain controller than there are on an individual Windows client computer.
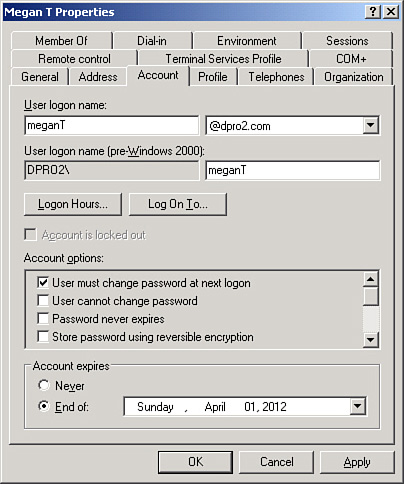
For example, the Account tab can be configured so that the user account has an expiration date. You can see this in Figure 9-4 where at the bottom of the Properties window, we have configured Megan’s account to expire on April 1, 2012—and that’s no April Fools! Immediately after expiration, the user cannot log on to the domain unless her account is reconfigured or she logs on as someone else.
Figure 9-4. User Account Expiration Date
![]()
Note
Users cannot log on to a network after their account has expired. The Account Expiration date in Windows controls this.
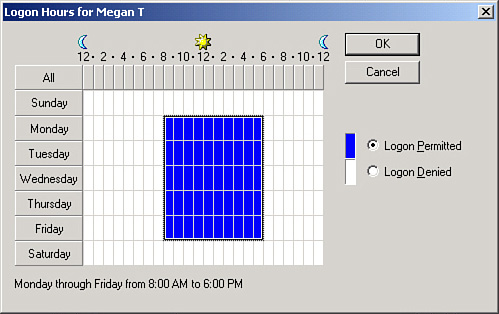
By clicking the Logon Hours button, time-of-day restrictions can be configured so that a user can only log on at certain times throughout the week. An example of this is shown in Figure 9-5. In the figure, Megan’s user account has been configured in such a way that she can only log on to the domain between 8 a.m. and 6 p.m. Monday–Friday. If she attempts to log on at any other time, the system will deny access. These kinds of access rights are available on domain controllers.
Figure 9-5. Time-of-Day Restrictions for a Standard User
![]()
Groups can be created to classify users and to ease administration when assigning permissions. If you refer to Figure 9-3, you see that a group is displayed with a two-headed icon, for example the Domain Admins group. Single users are displayed with a single head, as is the case with the Administrator. By grouping users together, you can save a lot of time when assigning permissions to files and other resources; instead of assigning permissions to one user at a time, it can be done to the entire group in one shot.
Permissions such as file and printer access can be assigned to individual users or to groups. These permissions are examples of access control lists (ACLs). An ACL is a list of permissions attached to an object. ACLs reside on firewalls, routers, and on computers. Permissions in an ACL might allow access or deny access. It all depends on who is required to have access; then, the configuration is up to you.
In Windows there are two types of permissions. Sharing permissions are basic permissions including Full Control, Change, and Read, which are applied to folders only. These are often ignored in favor of the more powerful (and superseding) NTFS permissions, also called security permissions, which can secure folders and individual files. In a standard Windows folder on a domain, the types of NTFS permissions include the following:
• Full Control
• Modify
• Read & Execute
• List Folder Contents
• Read
• Write
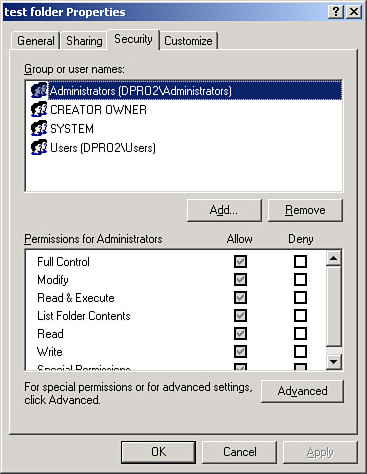
These are shown in Figure 9-6 on a Window Server 2003 in the Properties dialog box of a folder named “test folder.” Note that the Administrators group has full control of the folder. Also note that you can allow particular permissions, or specifically deny those permissions. If a permission is not set to Allow, it will be implicitly denied.
Figure 9-6. NTFS Permissions
Permissions similar to these are used for individual files and printers, and work in a related fashion on other operating systems such as Linux, Novell, and Mac. Navigation to, and configuration of, permissions in GUI-based OSs is similar to Windows. However, modifying permissions in the command-line, for example in Linux or UNIX is done differently. If a particular file, say test.txt needed to be modified, the command to be used would be chmod. Chmod is short for change mode. The type of mode dictates the “permissions” of the file among other things. For example, in chmod 755 test.txt, the first digit (7) represents the permission associated with the owner of the file. The second digit (5) represents permissions for the group. The third digit (5) represents the permissions for everyone else, also known as the everyone group.
When working with permissions, the “least privilege” or “minimal privilege” concept should be implemented. Give the users only the amount of access that they absolutely need. Also, if a company has a particularly high attrition rate (hiring and terminating of employees), the administrator should periodically review user permissions and access control lists. This will verify that users no longer with the company cannot log on to the network and cannot gain access to resources. It also ensures that new users can gain access to necessary resources.
Permission Inheritance and Propagation
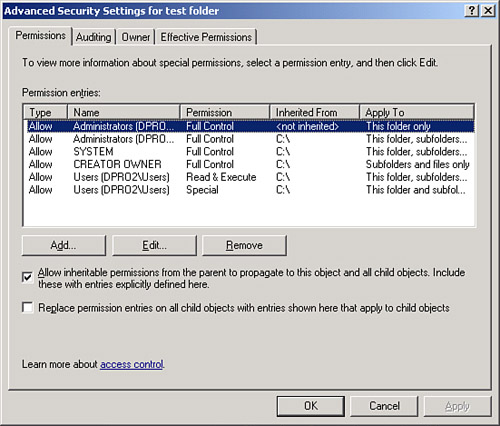
If you create a folder, the default action it takes is to inherit permissions from the parent folder, which ultimately come from the root folder. So any permissions set in the parent will be inherited by the subfolder. To view an example of this, locate any folder within an NTFS volume (besides the root folder), right-click it, and select Properties, access the Security tab, and click the Advanced button. Here, you see an enabled check box named Inherit from Parent the Permission Entries... toward the bottom of the window, as shown in Figure 9-7. This means that any permissions added or removed in the parent folder will also be added or removed in the current folder. In addition, those permissions inherited cannot be modified in the current folder. To make modifications you would have to deselect the Inherit from Parent the Permission Entries... check box. When you do so, you have the option to copy the permissions from the parent to the current folder or remove them entirely. To summarize, by default the parent is automatically propagating permissions to the subfolder, and the subfolder is inheriting its permissions from the parent. You can also propagate permission changes to subfolders not inheriting from the current folder. To do so, select the Replace Permission Entries on All Child Objects... check box. This might all seem a bit confusing, and you will probably not be asked many questions on the subject. Just remember that folders automatically inherit from the parent unless you turn inheriting off—and you can propagate permission entries to subfolders at any time by selecting the Replace option.
Figure 9-7. Inheritable Permissions
Moving and Copying Folders and Files
This subject and the previous one are actually more advanced Microsoft concepts, the type you would be asked on a Microsoft exam, and less likely to be asked on a CompTIA exam, so we’ll try to keep this simple. Moving and copying folders have different results when it comes to permissions. Basically, it breaks down like this:
• If you copy a folder on the same volume or to a different volume, the folder inherits the permissions of the parent folder it was copied to (target directory).
• If you move a folder to a different location on the same volume, the folder retains its original permissions. (You cannot move a folder to a separate volume; if you attempt to do so it will automatically be copied to the other volume.)
Note
Keep in mind that when you move data within a volume, the data isn’t actually relocated; instead the pointer to the file or folder is modified. Accordingly, permissions are not really moved either, so they remain the same.
Usernames and Passwords
The most common type of authentication is the username/password combination. Usernames are usually based on a person’s real name. Large organizations will use the firstname.lastname convention (for example, [email protected]) or first initial and last name ([email protected]). Smaller organizations might use the first name and last initial. The naming convention decided upon should be easy for you to implement without name confusion and have the capability to be utilized for all systems on the network including login, e-mail, database, and file access, and so on.
The password is either set by the user or created automatically for the user by an administrator. Figure 9-8 shows an example of a password that was created by the administrator. However, in this case, the user is not blocked from changing the password (unless a policy was created for that purpose). Note that the second checkbox User Cannot Change Password is not selected. As an administrator, you also have the option to select User Must Change Password at Next Logon. A user would have to pick a password when he first logs on to the domain, one that meets whatever complexity requirements your network calls for. This with the self-service password resetting (when users reset their own passwords at regular intervals) is necessary in larger networks to ease administration and increase security. The only caveat to this is account lockouts. Unlocking accounts that were locked by the system should only be done by an administrator or system operator.
Figure 9-8. Password Phase of User Account Creation
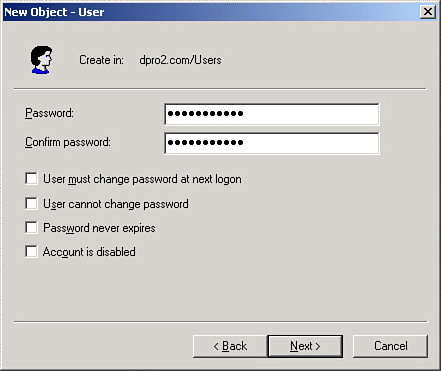
At this point, it is common knowledge that a strong password is important for protecting a user account. Nowadays, a lot of user accounts are compromised because of laziness; laziness on the part of the user for not configuring a strong password, or lethargic complacency on the part of the administrator for not enforcing the use of strong passwords.
But what is a strong password? That will depend on the organization you deal with, but generally it is broken down into a few easy to remember points. Passwords should comply with the following:
![]()
• Contain uppercase letters
• Contain lowercase letters
• Contain numbers
• Contain special characters (symbols)
• Should be 8 characters or more. Some organizations that have extremely sensitive data will require 12 or 14 characters as a minimum.
Many password checker programs are available on the web including:
• Microsoft’s password checker: www.microsoft.com/protect/yourself/password/checker.mspx
• The Password Meter: www.passwordmeter.com/
Try some of your favorite passwords—test them with the checkers. You might be surprised what you find! Your goal is to have a very strong or 100% strong password. Keep in mind that different checkers might have slightly different criteria.
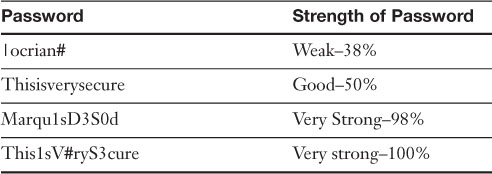
Table 9-2 shows several passwords, each stronger than the last, all of which were checked by The Password Meter.
Table 9-2. Password Strength as Checked by www.passwordmeter.com
![]()
Notice the first password is using the | pipe symbol instead of the letter L. Although the password is 8 characters, and has special characters, it is considered weak; however, this is a stronger password than the majority of passwords used in the United States! To make this password more complex, increasing the size of the password and adding uppercase letters would be the best course of action. The last password has 16 characters, 3 uppercase letters, 2 numbers, and a partridge in a pear tree, um, I mean one special character. Just checking if you are still with me! Of course, a partridge wouldn’t help your password security, but the other methods make for an extremely strong password that would take a super-computer many years to crack. I have placed this password on security testing websites and several persons have attempted to crack it without a positive result. (Actually, it was positive for me because it wasn’t cracked!)
A password that has 12 characters including uppercase, numbers, and special characters is currently considered to be effectively uncrackable. And 72-bit or higher passwords are the standard for networks that contain confidential data. We talk more about password strength and password cracking in Chapter 10, “Vulnerability and Risk Assessment.”
Changing your password at regular intervals is important as well. The general rule of thumb is to change your password as often as you change your toothbrush. However, because this is a subjective concept (to put it nicely!), many organizations have policies concerning your password that we will speak to in the next section. It might need to meet certain requirements, or be changed at regular intervals, and so forth.
Here are a couple more tips when it comes to user accounts, passwords, and logons:
• Rename and password protect the Administrator account—It’s nice that Windows has incorporated a separate administrator account: The problem is that by default the account has no password. To configure this account, navigate to Computer Management > System Tools > Local Users and Groups > Users and locate the Administrator account. In a domain, this would be in ADUC > Domain name > Users. By right-clicking the account, you see a drop-down menu in which you can rename it and/or give it a password. (Just remember the new username and password!) Now it’s great to have this additional administrator account on the shelf just in case the primary account fails; however, some OSs such as Vista disable the account by default. To enable it, right-click the account and select Properties. In the General tab, deselect the Account Is Disabled check box. Alternatively, open the command line and type net user administrator /active:yes. The way that the administrator account behaves by default will depend on the version of Windows. The Linux/UNIX counterpart is the root account. The same types of measures should be employed when dealing with this account.
• Verify that the Guest account (and other unnecessary accounts) are disabled—This can be done by right-clicking the account in question, selecting Properties and then selecting the checkbox named Account Is Disabled. It is also possible to delete accounts (aside from built-in accounts such as the Guest account); however, companies usually opt to have them disabled instead so that the company can retain information linking to the account.
• Use Ctrl+Alt+Del—Pressing Ctrl+Alt+Del before the logon adds a layer of security to the logon process. This can be added as a policy on individual Windows computers. It is implemented by default with computers that are members of a domain.
• Use policies—Policies governing user accounts, passwords, and so on can help you to enforce your rules, as discussed in the next section. Large organizations with a lot of users will usually implement a self-service password management system. This means that users reset their own passwords after a given amount of time (set in a group policy); the administrator does not create passwords for users.
Policies
Policies are rules or guidelines used to guide decisions and achieve outcomes. They can be written or configured on a computer. The former are more difficult to enforce, whereas the latter would have to be hacked to be bypassed. Local computer policies and network policies are what really make an access control model effective.
Password policies can be implemented to enforce the usage of complex passwords and regulate how long passwords last. They can be configured on local computers, such as Windows XP and Vista, by navigating to Start > All Programs > Administrative Tools > Local Security Policy. When in the Local Security Settings window, continue to Security Settings > Account Policies > Password Policy.
More important, they can be configured for an entire network, for example on a Microsoft domain. The policy can affect the entire domain or individual organizational units. This would be known as a group policy and would be configured on a domain controller. For example, a Windows Server 2003 domain controller can be configured by completing the following steps:
Step 1. Access the domain controller.
Step 2. Create an MMC.
Step 3. Add the Default Domain Policy to the MMC. (Done by adding a Group Policy Object Editor snap-in.)
Step 4. In the Default Domain Policy, navigate to Computer Configuration > Windows Settings > Security Settings > Account Policies > Password Policy.
Note
The Default Domain Policy will affect all users. This is okay for small networks, but for larger networks, separate organizational units should be created, each with its own security policy. More information about how to go about this can be found in Lab 9-1 in the “Hands-On Labs” section.
When in the Password Policy, you see the following policies:
• Enforce password history—When this is defined, users cannot use any of the passwords remembered in the history. If you set the history to 3, the last three passwords cannot be used again when it is time to change the password.
• Maximum and minimum password age—This defines exactly how long a password can be used. The maximum is initially set to 42 days but does not affect the default Administrator account. To enforce effective password history, the minimum must be higher than zero.
• Minimum password length—This requires that the password must be at least the specified amount of characters. For a strong password policy, set this to 8 or more.
• Passwords must meet complexity requirements—This means that passwords must meet three of these four criteria: uppercase characters, lowercase characters, digits between 0 and 9, and nonalphabetic characters (special characters).
Remember that these policies, when enabled, affect all users that the policy applies to. If it is the Default Domain Policy (usually not recommended for configuration), it affects all users; if it is an OU policy, it affects all users in the OU.
Note
For more information on password best practices, see the following link: http://technet.microsoft.com/en-us/library/cc784090.aspx.
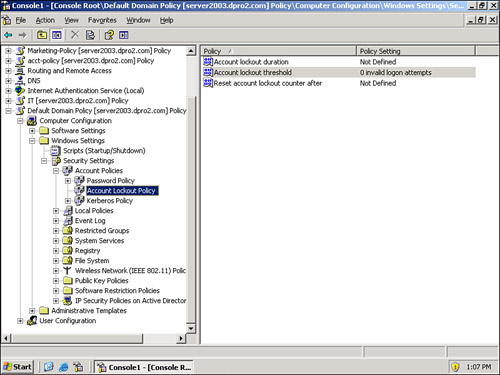
There are plenty of other policies that you can configure. You can pretty much configure any policy on a domain. You can’t configure how a person should shave in the morning, but anything computer-related can be modified and policed. One example is how many attempts a person will be allowed when typing in a password. This is known as the Account lockout threshold, as shown in Figure 9-9. By default, this is set to 5 attempts on a Windows Server 2003, but many companies will adjust this to 3; this is known as the 3 strikes and you’re out rule.
Figure 9-9. Account Lockout Threshold Policy
Another great tool is previous logon notification. This can be configured in a policy and will show the user the last time the account logged in successfully—generally during the logon process. If users suspects that their account was compromised, they could check the previous logon notification and compare that with when they remember logging in.
It’s important to note that when logging on to a Microsoft network, the logon process is secured by the Kerberos protocol, which is run by the Domain Controller. This adds a layer of protection for the username and password as they are authenticated across the network. When users take a break or go to lunch, they should lock the computer. This can be done by pressing Windows+L. When doing so, the operating system goes into a locked state, and the only way to unlock the computer is to enter the username and password of the person who locked the computer. The difference between this and logging out is that a locked computer keeps all the session’s applications and files open, whereas logging out closes all applications and open files. A policy can also be configured to force locking after a certain amount of time has elapsed. There are literally hundreds of policies that are configurable. You could spend weeks doing it! Microsoft understands this and offers various levels of security templates that can be imported into your OU policy, making your job as an administrator a bit easier. A particular template might be just what you are looking for, or it might need a bit of tweaking. But in most cases it beats starting from scratch!
Policies can be developed on all kinds of software and systems, not just operating systems. For example, many organizations have websites, and a good portion of those organizations now set up bulletin board systems where authorized users can post messages. Bulletin boards are also known as forums or portals. Bulletin boards are often the playground for malicious activity, for example, users or bots who post spam messages. Various policies can be implemented on an interactive bulletin board system to prevent these types of problems. For example, when people first register, they would need to answer a question that requires something they knows such as 2+4 = blank. The user would enter the answer (6) and continue on their merry way. Another viable option is to use CAPTCHA, which can display an image that has letters and numbers in it. The user must type the letters and numbers that they see before they can register, or perhaps to post any messages at all. This is a good deterrent for bots!
User Account Control (UAC)
User Account Control (UAC) is a security component of Windows Server 2008, Windows Vista, and Windows 7 that keeps users (besides the actual Administrator account) in standard user mode instead of as an administrator with full administrative rights—even if they are a member of the administrators group. It is a built-in security policy meant to prevent unauthorized access and avoid user error in the form of accidental changes. With UAC enabled users perform common tasks as nonadministrators, and when necessary, as administrators, without having to switch users, log off, or use Run As.
Basically, UAC was created with two goals in mind: First, to eliminate unnecessary requests for excessive administrative-level access to Windows resources; and second, to reduce the risk of malicious software using the administrator’s access control to infect operating system files. When a standard end user requires administrator privileges to perform certain tasks such as installing an application, a small pop-up UAC window appears notifying the user that an administrator credential is necessary. If users have administrative rights and click Continue, the task will be carried out, but if they do not have sufficient rights, the attempt fails. Note that these pop-up UAC windows do not appear if the person is logged on with the actual Administrator account.
Turning UAC on and off can be done by going to Start > Control Panel > User Accounts and Family Safety. Then select User Accounts and Turn User Account Control On or Off. From there UAC can be turned on and off by checking or unchecking the box. If a change is made to UAC, the system needs to be restarted. Note that if you use the Classic View in the Control Panel, User Accounts and Family Safety is bypassed.
Exam Preparation Tasks: Review Key Topics
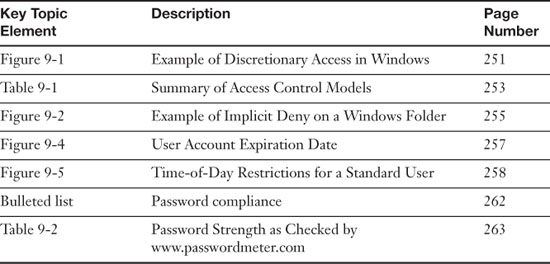
Review the most important topics in the chapter, noted with the Key Topics icon in the outer margin of the page. Table 9-3 lists a reference of these key topics and the page numbers on which each is found.
![]()
Table 9-3. Key Topics for Chapter 9
Complete Tables and Lists from Memory
Print a copy of Appendix A, “Memory Tables,” (found on the DVD), or at least the section for this chapter, and complete the tables and lists from memory. Appendix B, “Memory Tables Answer Key,” also on the DVD, includes completed tables and lists to check your work.
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
discretionary access control (DAC),
Trusted Computer System Evaluation Criteria (TCSEC),
mandatory access control (MAC),
role-based access control (RBAC),
Hands-On Labs
Complete the following written step-by-step scenarios. After you have finished (or if you do not have adequate equipment to complete the scenario), watch the corresponding video solutions on the DVD.
If you have additional questions, feel free to post them at my website: www.davidlprowse.com in the Ask Dave forum. (Free registration is required to post on the website.)
Equipment Needed
• A Windows Server (2003 or 2008 preferred). This server must be promoted to a domain controller.
Lab 9-1: Configuring Password Policies and User Account Restrictions
In this lab, you create an organizational unit and policy within a Windows Server 2003 domain controller. Then, you configure group policy objects and user restrictions. The steps are as follows:
Step 1. Access the Windows Server 2003 MMC. If you don’t have one, create one now, and add the Active Directory Users and Computers (ADUC) snap-in.
Step 2. Create a new organizational unit (OU):
A. Expand the ADUC snap-in.
B. Right-click the domain name and select New > Organizational Unit.
C. Name the OU and click OK. Generally, OUs will be named after departments in a company such as accounting, marketing, and so on.
D. Add a user to the OU by right-clicking the work area and selecting New > User. Call the user Template.
Step 3. Create a policy associated with the OU:
A. Right-click the new OU and select Properties.
B. Click the Group Policy tab.
C. Click the New button.
D. Name the policy. Choose a name that will associate the policy with the OU.
E. Click Close.
Step 4. Add the new policy as a snap-in to the MMC:
A. Click File > Add/Remove Snap-In.
C. Select Group Policy Editor and click Add.
D. Click Browse; then double-click the folder with the name of your new OU.
E. Highlight the new policy and click OK.
F. Click Finish. Close all other dialog boxes. The new policy should now be added to the MMC as a snap-in.
Step 5. Make changes to the policy:
A. Navigate to Computer Configuration > Windows Settings > Security Settings > Account Policies > Password Policy.
B. Modify the password age and length as you want. For example, to change the Maximum password age to 30 days, double-click that policy object, select Define this policy setting, and change the amount to 30.
C. Enable password complexity requirements.
Step 6. Make changes to the Account Lockout Policy within Account Policies:
A. Click Account Lockout Policy.
B. Define the account lockout duration as 30 minutes.
C. Define the account lockout threshold to after 3 invalid logon attempts.
Step 7. Examine the importable policies:
A. Right-click Security Settings and select Import Policy.
B. View the policy options. Cancel out when finished.
Step 8. Modify the template user account:
A. Right-click the account and select Properties.
B. Click the Account tab.
C. Click Logon Hours.
D. Modify this setting by clicking and dragging within the days so that the template user can only logon between 9 a.m. and 5 p.m. Monday–Friday.
E. Click OK for the logon hours. Then click OK for the Template account Properties dialog box.
Step 9. Create users by making copies of the template account:
A. Right-click the Template account and select Copy.
B. Name the new user and give is a logon name. For example, someone’s first initial and last name. Then click Next.
C. Give a password for the user that meets your complexity requirements.
D. Deselect User Must Change Password at Logon and click Next.
E. Click Finish. The new account should be listed in the OU.
F. Right-click the new user and select Properties.
G. Review the Logon hours in the Account tab and verify that they are the same as the Template account.
Watch the solution video in the “Hands-On Scenarios” section of the DVD.
Lab 9-2: Configuring User and Group Permissions
In this lab, you configure user and group permissions for a shared resource on a Windows Server 2003 domain controller. This lab is written to be a little more intuitive. The step-by-step is slightly less informative. Use your imagination to fill in the gaps! The steps are as follows:
Step 1. Create two more user accounts in the new OU that you created in the previous lab.
Step 2. Create a group:
A. Right-click the new OU and select New > Group.
B. Name the group, for example: IT1 and click OK.
Step 3. Add members to the group:
A. Right-click the group and select Properties.
B. Click the Members tab.
C. Click Add. Then click Advanced and Find Now. Add the new users you created to the IT group. Select each one at a time or use Ctrl+Click to select all of them at one time. Click OK for all dialog boxes to add them to the group.
Step 4. Apply permissions for a shared folder to the entire group:
A. Create a folder specifically for the new group of users.
B. Share the folder.
C. Click the Security tab.
D. Click the Advanced button. Remove inheritable permissions by deselecting the checkbox and selecting Copy.
E. Click the Add button and add the new group of users to the share.
F. Remove other groups and users besides the Administrators group.
G. Click OK when finished.
Watch the solution video in the “Hands-On Scenarios” section of the DVD.
View Recommended Resources
• TCSEC The Orange Book. http://csrc.ncsl.nist.gov/publications/secpubs/rainbow/std001.txt
• DOD Directive 8500.01E (replacement for The Orange Book) www.dtic.mil/whs/directives/corres/pdf/850001p.pdf
• Role-based access control Introduction http://csrc.nist.gov/groups/SNS/rbac/documents/design_implementation/Intro_role_based_access.htm
Password checking tools:
• Microsoft’s password checker: www.microsoft.com/protect/yourself/password/checker.mspx
• The Password Meter: www.passwordmeter.com/
• Password Best Practices: http://technet.microsoft.com/en-us/library/cc784090.aspx
• User Account Control Step-by-Step Guide: http://technet.microsoft.com/en-us/library/cc709691%28WS.10%29.aspx
Answer Review Questions
Answer the following review questions. You can find the answers at the end of this chapter.
1. Which of the following is the strongest password?
A. | ocrian#
B. Marqu1sD3S0d
C. This1sV#ryS3cure
D. Thisisverysecure
2. Which of these is a security component of Windows Vista?
A. UAC
B. UPS
C. Gadgets
D. Control Panel
3. What key combination helps to secure the logon process?
A. Windows+R
B. Ctrl+Shift+Esc
D. Alt+F4
4. Which of the following is the most common authentication model?
A. Username and password
B. Biometrics
C. Key cards
D. Tokens
5. Which of the following access control methods uses rules to govern whether object access will be allowed? (Select the best answer.)
A. Rule-based access control
B. Role-based access control
C. Discretionary access control
D. Mandatory access control
6. When using the mandatory access control model, what component is needed?
A. Labels
B. Certificates
C. Tokens
D. RBAC
7. Which of the following statements regarding the MAC access control model is true?
A. Mandatory access control is a dynamic model.
B. Mandatory access control enables an owner to establish access privileges to a resource.
C. Mandatory access control is not restrictive.
D. Mandatory access control users cannot share resources dynamically.
8. In the DAC model, how are permissions identified?
A. Role membership.
B. Access control lists.
C. They are predefined.
D. It is automatic.
9. Robert needs to access a resource. In the DAC model, what is used to identify him or other users?
A. Roles
B. ACLs
C. MAC
D. Rules
10. A company has a high attrition rate. What should you ask the network administrator do first? (Select the best answer.)
A. Review user permissions and access control lists.
B. Review group policies.
C. Review Performance logs.
D. Review the Application log.
11. Your company has 1,000 users. Which of the following password management systems will work best for your company?
A. Multiple access methods
B. Synchronize passwords
C. Historical passwords
D. Self-service password resetting
12. In a discretionary access control model, who is in charge of setting permissions to a resource?
A. The owner of the resource
B. The administrator
C. Any user of the computer
D. The administrator and the owner
13. Jason needs to add several users to a group. Which of the following will help him to get the job done faster?
A. Propagation
B. Inheritance
C. Template
D. Access control lists
14. How are permissions defined in the mandatory access control model?
A. Access control lists
B. User roles
C. Defined by the user
D. Predefined access privileges
15. Which of the following would lower the level of password security?
A. After a set number of failed attempts, the server will lock the user out, forcing them to call the administrator to reenable their account.
B. Passwords must be greater than eight characters and contain at least one special character.
C. All passwords are set to expire after 30 days.
D. Complex passwords that users cannot change are randomly generated by the administrator.
16. Of the following access control models, which use object labels? (Select the best answer.)
A. Discretionary access control
B. Role-based access control
C. Rule-based access control
D. Mandatory access control
17. Which of the following methods could identify when an unauthorized access has occurred?
A. Two -factor authentication
B. Session termination
C. Previous logon notification
D. Session lock
18. What would you use to control the traffic that is allowed in or out of a network? (Select the best answer.)
A. Access control lists
B. Firewall
C. Address resolution protocol
D. Discretionary access control
19. In an attempt to detect fraud and defend against it, your company cross-trains people in each department. What is this an example of?
A. Separation of duties
B. Chain of custody
C. Job rotation
D. Least privilege
20. What is a definition of implicit deny?
A. Everything is denied by default.
B. All traffic from one network to another is denied.
C. ACLs are used to secure the firewall.
D. Resources that are not given access are denied by default.
21. In an environment where administrators, the accounting department, and the marketing department all have different levels of access, which of the following access control models is being used?
A. Role-based access control (RBAC)
B. Mandatory access control (MAC)
C. Discretionary access control (DAC)
D. Rule-based access control (RBAC)
22. Which security measure should be included when implementing access control?
A. Disabling SSID broadcast
B. Time-of-day restrictions
C. Changing default passwords
D. Password complexity requirements
23. Which password management system best provides for a system with a large number of users?
A. Locally saved passwords management systems
B. Synchronized passwords management systems
C. Multiple access methods management systems
D. Self-service password reset management systems
24. You administer a bulletin board system for a rock and roll band. While reviewing logs for the board, you see one particular IP address posting spam multiple times per day. What is the best way to prevent type of problem?
A. Block the IP address of the user.
B. Ban the user.
C. Disable ActiveX.
D. Implement CAPTCHA.
Answers and Explanations
1. C. Answer C incorporates case-sensitive letters, numbers, and special characters and is 16 characters long. The other answers do not have the complexity of answer C.
2. A. User Account Control (UAC) adds a layer of security to Windows Server 2008, Windows Vista, and Windows 7 to protect against malware and user error and conserve resources. It enforces a type of separation of duties.
3. C. Ctrl+Alt+Del is the key combination used to help secure the logon process. It can be added by configuring the Local Security policy.
4. A. By far the username and password combination is the most common authentication model. Although biometrics, key cards, and tokens are also used, the password is still the most common.
5. A. Rule-based access control uses rules to govern if an object can be accessed. It is a type of mandatory access control.
6. A. Labels are required in the mandatory access control model (MAC).
7. D. In MAC (mandatory access control) users cannot share resources dynamically. MAC is not a dynamic model; it is a static model. Owners cannot establish access privileges to a resource; this would be done by the administrator. MAC is indeed very restrictive, as restrictive as the administrator wants it to be.
8. B. In the discretionary access control model, permissions to files are identified by access control lists or ACLs. Role membership is used in RBAC. The mandatory access control model predefines permissions. Either way, it is not identified automatically.
9. B. Access control lists (ACLs) are used in the Discretionary Access Control model. This is different from role-based, rule-based, and MAC (Mandatory Access Control) models.
10. A. The first thing administrators should do when they notice that the company has a high attrition rate (high turnover of employees) is to conduct a thorough review of user permissions, rights, and access control lists. A review of group policies might also be necessary but is not as imperative. Performance logs and the Application log will probably not pertain to the fact that the company has a lot of employees being hired and leaving the company.
11. D. It would be difficult for administrators to deal with thousands of users passwords; therefore, the best management system for a company with 1,000 users would be self-service password resetting.
12. A. In the discretionary access control model (DAC), the owner of the resource is in charge of setting permissions. In a mandatory access control model, the administrator is in charge.
13. C. By using a template, you can add many users to a group at once simply by applying the template to the users. Propagation and inheritance deal with how permissions are exchanged between parent folders and subfolders. Access control lists show who was allowed access to a particular resource.
14. D. The mandatory access control model uses predefined access privileges to define which users have permission to resources.
15. D. To have a secure password scheme, passwords should be changed by the user. They should not be generated by the administrator. If an administrator were to generate the password for the user, it would have to be submitted in written (and unencrypted) form in some way to the user. This creates a security issue, especially if the user does not memorize the password and leaves a written version of it lying around. All the other answers would increase the level of password security.
16. D. The mandatory access control (MAC) model uses object and subject labels. DAC and RBAC (role-based access control) do not. Rule-based access control is a portion of MAC, and although it might use labels, MAC is the best answer.
17. C. Previous logon notification can identify if unauthorized access has occurred. Two-factor authentication means that person will supply two forms of identity before being authenticated to a network or system. Session termination is a mechanism that can be implemented to end an unauthorized access. Session lock mechanisms can be employed to lock a particular user or IP address out of the system.
18. A. Access control lists can be used to control the traffic that is allowed in or out of a network. They are usually included as part of a firewall, and they are the better answer because they specifically will control the traffic. Address resolution protocol or ARP resolves IP addresses to MAC addresses. In the discretionary access control model, the owner controls permissions of resources.
19. C. When a company cross-trains people, it is known as job rotation. Separation of duties is in a way the opposite; this is when multiple people are needed to complete a single task. Chain of custody has to do with the legal paper trail of a particular occurrence. Least privilege is a mitigation technique to defend against privilege escalation attacks.
20. D. If a resource is not given specific access, it will be implicitly denied by default. Access control lists are used to permit or deny access from one network to another and are often implemented on a firewall.
21. A. Role-based access control is when different groups or roles are assigned different levels of permissions; rights and permissions are based on an ob function. In the mandatory access control model, an administrator centrally controls permissions. In the discretionary access control model, the owner of the user sets permissions. In the rule-based access control model, rules are defined by the administrator and are stored in an ACL.
22. D. By implementing password complexity requirements, users will be forced to select and enter complex passwords, for example, eight characters or more, uppercase characters, special characters, and more. Disabling the SSID deals with wireless networks, time-of-day restrictions is applied only after persons logs in with their username and password, and changing default passwords should be part of a password policy.
23. D. If a network has a large number of users, the administrator should set up a system and policies to enforce the system that will allow for users to reset their own passwords. The passwords should be stored centrally, not locally. Also, it would be best if single sign-on were implemented and not a multiple access method.
24. D. By implementing CAPTCHA, another level of security is added that users have to complete before they can register to and/or post to a bulletin board. Although banning a user or the user’s IP address can help to eliminate that particular person from spamming the site, the best way is to add another level of security, such as CAPTCHA. This applies to all persons who attempt to attack the bulletin board.
