Chapter 4. Application Security
This chapter covers the following subjects:
Securing the Browser—What is a client computer without a web browser? Some might answer “worthless.” Well, a compromised browser is worse than no browser at all. The web browser must be secured to have a productive and enjoyable web experience. In this section, we concentrate on Internet Explorer and Firefox, and show various ways to secure them.
Securing Other Applications—Organizations use many applications, and they each have their own group of security vulnerabilities. In this section, we spend a little time on common applications such as Microsoft Office and demonstrate how to make those applications safe.
This chapter covers the CompTIA Security+ SY0-201 objective 1.4.
This is a shorter chapter, but another important one. Browser security should be at the top of any network security administrator’s list. It’s another example of inherently insecure software “out of the box”. Browsers are becoming more secure as time goes on, but malware and especially adware are presenting more of a challenge—as we mentioned in Chapter 1, “Introduction to Security,” the scales are always tipping back and forth.
Most browsers have plenty of built-in options that you can enable to make them more secure, and third-party programs can help in this endeavor as well. This chapter concentrates on Internet Explorer and Firefox, but the concepts we cover can be applied to most other browsers. However, users don’t just work with web browsers. They use office applications frequently as well, so these should be secured, too. Also, other applications, such as the command-line, though a great tool, can also be a target. Be sure to secure any application used on your network. It takes only one vulnerable application to compromise the security of your network.
Let’s start with discussing how to secure web browsers.
Foundation Topics: Securing the Browser
There is a great debate as to which web browser to use. The two front runners are Internet Explorer and Firefox. Personally, it doesn’t matter too much to me, because as a security guy, I am going to spend a decent amount of time securing either one. However, each does have advantages, and one might work better than the other depending on the environment. So if you are also in charge of implementing a browser solution, be sure to plan for performance and security right from the start. As to planning for, and configuring security, I do make some standard recommendations to customers, students, and readers. Let’s discuss a few of those now.
The first recommendation is to not use the latest browser. (Same advice I always give for any application it seems). Let the people at the top of the marketing pyramid, the innovators, mess around with the “latest and greatest;” let those people find out about the issues, back doors, and whatever other problems a new application might have; at worst, let their computer crash! For the average user, and especially for a fast-paced organization, the browser needs to be rock-solid; these organizations will not tolerate any downtime. As an example, as of the writing of this book, Internet Explorer 8 has been released (Windows 7 comes with it standard), but I still don’t recommend it to customers running other Windows operating systems. Of course, that will change over time, but I always allow for some time to pass before fully embracing and recommending software. (My lead time for new software is between 6 and 12 months depending on what it is.) The reason I bring this up is because most companies share the same view.
The next recommendation is to consider what type of computer, or computers, will be running the browser. Generally, Linux computers run Firefox or another browser besides IE; however, you can run a type of IE on Linux, but WINE must be installed first. IE dominates the Windows market, but Firefox works well on Windows PCs, too. And many other applications such as Microsoft Office are linked to IE, so it is wise to consider other applications that are in use when deciding on a browser. Another important point is whether you will be centrally managing multiple client computers’ browsers. IE can be centrally managed through the use of Group Policy Objects (GPOs) on a domain; I’ll show a quick demonstration of this later in the chapter.
You might also want to consider how the two browser companies fix vulnerabilities. If vulnerability is found in Firefox, it generally becomes common knowledge quickly, which could lead to rapid exploits of the vulnerability before the folks at Mozilla have a chance to fix it. However, an advantage of Firefox is that vulnerabilities appear to be fixed faster than IE vulnerabilities the majority of the time. On the flipside, Microsoft will find out about vulnerabilities but will keep them secret, which pretty much eliminates any possible exploits born from company-presented information. But...Microsoft might take longer to fix the vulnerability. When it comes to functionality, they both work very well. Personally, I use Internet Explorer for sites that I frequent often such as banking websites and my personal website. But I use Firefox for researching of data. It should be noted that some sites do not allow connections by any browser except IE. This is a “security feature” of those websites and should be investigated before implementing other browsers in your organization. If your company makes connections to those types of sites, no other browser will be appropriate. As far as security in general, IE received a poor reputation during older versions. However, Microsoft has worked on this in recent years, resulting in a much more secure version 7 and higher. Firefox has been known all along for its security, but it would seem that the two are quite evenly matched at this point. If you were to research the total number of discovered vulnerabilities for each browser, it would probably be close to the same number. Anyway, I think that’s enough yappin’ about the two for now—we’ll cover some security techniques for each in just a little bit.
General Browser Security Procedures
First, some general procedures should be implemented regardless of the browser your organization uses:
• Use a proxy and content filter.
• Secure against malicious code.
Each of these is discussed in more detail in the following sections.
Implement Policies
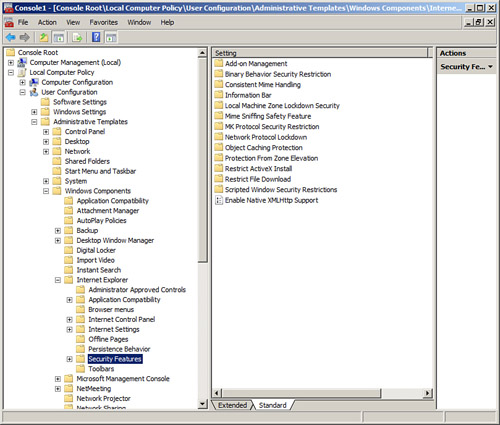
The policy could be written, configured at the browser, implemented within the computer operating system, or better yet, configured on a server centrally. Policies can be configured to manage add-ons, and disallow access to websites known to be malicious, have Flash content, or use a lot of bandwidth. As an example, Figure 4-1 displays Internet Explorer Security Features within the Local Group Policy of a Windows Vista computer. You can access it by opening the computer’s Local Computer Policy (in the figure it was added as a snap-in to an MMC) and navigating to User Configuration > Administrative Templates > Windows Components > Internet Explorer > Security Features. Of course, there are literally hundreds of settings that can be changed for Internet Explorer. You can also modify Internet Explorer Maintenance Security by navigating to User Configuration > Windows Settings > Internet Explorer Maintenance > Security, as shown in Figure 4-2. The Security Zones and Content Ratings object was double-clicked to show the dialog box of the same name. Some versions of Windows will not enable you to access to the Local Computer Policy; however, most security features can be configured directly within the browser.
Figure 4-1. Internet Explorer Security Features in the Local Computer Policy
![]()
Figure 4-2. Internet Explorer Maintenance Security in the Local Computer Policy
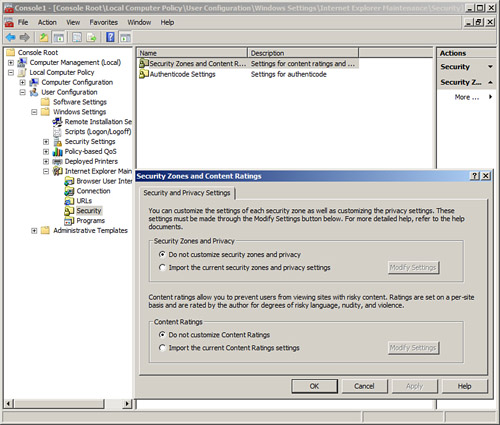
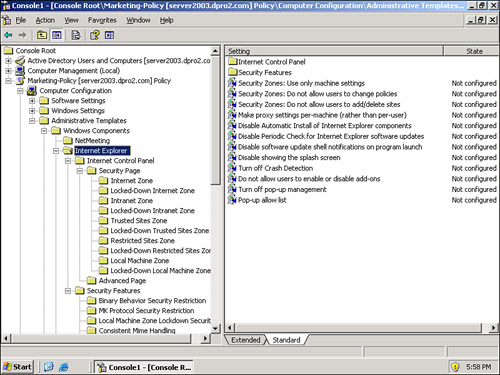
Now, you wouldn’t want to configure these policy settings on many more than a few computers individually. If you have multiple computers that need their IE security policies updated, consider using a template (described in Chapter 3, “OS Hardening and Virtualization”), or if you have a domain controller, consider making the changes from that central location. From there, much more in-depth security can be configured and deployed to the IE browsers within multiple computers. An example of the IE policies, as managed from a domain controller, is shown in Figure 4-3. For this, I set up a Windows Server 2003 as a domain controller (controlling the domain dpro2.com), created an organizational unit named Marketing, and then created a Group Policy Object named Marketing-Policy that I added to the MMC. From that policy the Internet Explorer settings, which can affect all computers within the Marketing organizational unit (OU), can be accessed by navigating to Computer Configuration > Administrative Templates > Windows Components > Internet Explorer. From here we can configure trusted and nontrusted sites, zones, and advanced security features in one shot for all the computers in the OU. A real time-saver!
Figure 4-3. Internet Explorer Policies in the Marketing-Policy GPO
![]()
Train Your Users
User training is important to determine what websites to access, how to use search engines, and what to do if pop-ups appear on the screen. The more users you can reach with your wisdom, the better! On-site training classes, webinars, and downloadable screencasts all work great. Or if your organization doesn’t have those kinds of resources, consider writing a web article to this effect, make it engaging and interesting, yet educational.
For example, explain to users the value of pressing Alt+F4 to close pop-up windows instead of clicking No or an X. Pop-ups could be coded in such a way where No actually means Yes, and the close-out X actually means “take me to more annoying websites!” Alt+F4 is a hard-coded shortcut key that closes applications.
Another example is to show users how to know if their communications are secure on the web. Just typing HTTPS in the address bar isn’t enough. Today, Internet Explorer and Firefox show a green background in the address bar if the website uses a proper encryption certificate. Some browsers use a padlock in the locked position to show it is secure. One website that shows these security notifications in action is https://www.paypal.com.
Use a Proxy and Content Filter
HTTP proxies (known as proxy servers) act as a go-between for the clients on the network and the Internet. Simply stated, they cache website information for the clients, reducing the amount of requests that need to be forwarded to the actual corresponding web server on the Internet. This is done to save time, make more efficient use of bandwidth, and help to secure the client connections. By using a content filter in combination with this, specific websites can be filtered out, especially ones that can potentially be malicious, or ones that can be a waste of man hours, for example P2P websites/servers. I know—I’m such a buzzkill. But these filtering devices are common in today’s networks; we talk more about them in Chapter 6, “Network Perimeter Security.” For now, it is important to know how to connect to them with a browser. We use Internet Explorer as an example. Remember that the proxy server is a mediator between the client and the Internet. So the client’s web browser must be configured to connect to them. You can either have the browser automatically detect a proxy server or (and this is more common) configure it statically. Here’s how:
Step 1. Open Internet Explorer. (For this exercise I used IE 7, but other versions will be similar.)
Step 2. On the menu bar go to Tools. If the menu bar is not visible, press Alt+T on the keyboard to bring up the menu.
Step 3. Select Internet Options. This should display the Internet Options dialog box.
Step 4. Click the Connections tab.
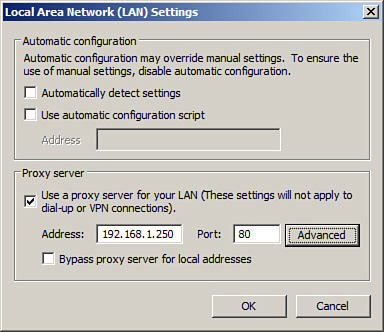
Step 5. Click the LAN Settings button. This displays the Local Area Network (LAN) Settings window, as shown in Figure 4-4.
Figure 4-4. Configuring the Proxy Server Connection in Internet Explorer
![]()
Step 6. Check the Use a proxy server for your LAN checkbox. This enables the Proxy server field.
Step 7. In the Address field, type in the IP address or name of the proxy server, for example 192.168.1.250.
Step 8. Select a port; by default 80 is selected because it corresponds with HTTP and most web requests. However, your proxy might use a different port. Consult your network documentation for details.
Step 9. If your proxy server also acts as a go-between for other services such as FTP or secure web transactions, configure these by clicking the Advanced button.
Step 10. Click OK for the Local Area Network (LAN) Settings dialog box.
Step 11. Click OK for the Internet Options dialog box. The client should now be configured to use a proxy server for all its HTTP transactions. To remove the proxy server at any time, simply deselect the Use a proxy server for your LAN checkbox.
Note
This setting can also be configured within an organizational unit’s Group Policy Object on the domain controller. This way, it can be configured one time but will affect all the computers within the particular OU.
Secure Against Malicious Code
Depending on your company’s policies and procedures, you might need to configure a higher level of security concerning ActiveX controls, Java, JavaScript, Flash media, Phishing, and much more. We show a few of these configurations in the subsequent sections.
Securing Internet Explorer
There are lots of ways to make Internet Explorer more secure. Be warned, though, that the more a browser is secured, the less functional it becomes. Generally, the best solution is to find a happy medium between functionality and security.
The first thing that should be done is to update the browser. Internet Explorer can be updated directly through the Windows Update feature; however, watch for completely new versions as well. Whenever updating, always check the list of updates before installing them.
Next, install pop-up blocking and other ad-blocking solutions. Many antivirus suites have pop-up blocking tools. There is also the Google Toolbar and other tools like it. And of course, newer versions of web browsers will block some pop-ups on their own.
Now we move on to configuring security within the browser itself. By adjusting Internet Explorer settings, you can add a layer of defense that helps to prevent spyware and other malicious attacks.
First we configure security zones. This and many other security configurations can be completed in the Internet Options dialog box, which can be accessed by going to Tools on the menu bar and selecting Internet Options. (If the menu bar is not visible, press Alt+T on the keyboard to bring up the Tools menu.) Then click the Security tab to show the Internet Explorer security zones. Remember, just because they are called security zones doesn’t necessarily make them secure. Adjust the security level for the zone named Internet. Many organizations set this to High, as shown in Figure 4-5.
Figure 4-5. Internet Options Dialog Box—Security Zones
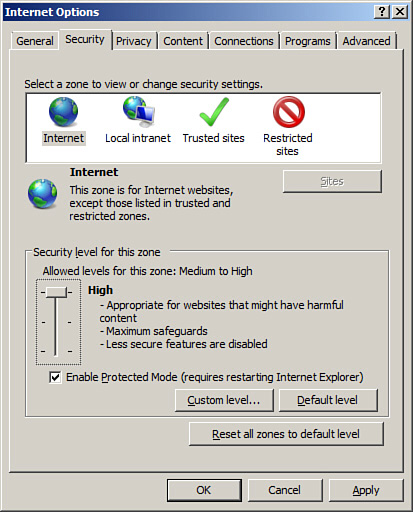
![]()
You can set the security level in the same manner for the Local intranet zone, Trusted sites zone, and Restricted sites zone. In addition, you can set custom levels by clicking the Custom Level button. Here you can disable ActiveX controls and plug-ins, turn the scripting of Java applets on and off, and much more. The Security tab is also where you can add trusted sites to the computer. For example, if you have a high security level, and IE always asks if a particular website is okay to visit, and it’s a site you visit everyday that you know to be legitimate, you can add it to the trusted sites by clicking the Trusted sites zone, clicking the Sites button, and adding the URL of the site in question. Conversely, you can restrict sites by clicking the Restricted sites zone and again clicking the Sites button.
Cookies can also pose a security threat. The next tab in the Internet Options window is the Privacy tab. This is where you can select how cookies will be handled. Cookies are text files placed on the client computer that store information about it, which could include your computer’s browsing habits and possibly user credentials. By adjusting the slider, you can either accept all cookies, deny all cookies, or select one of several options in between. Figure 4-6 displays this slider set to High, which blocks cookies that save information that can be used to contact the user or do not have a compact privacy policy.
Figure 4-6. Internet Options Dialog Box—Privacy Tab
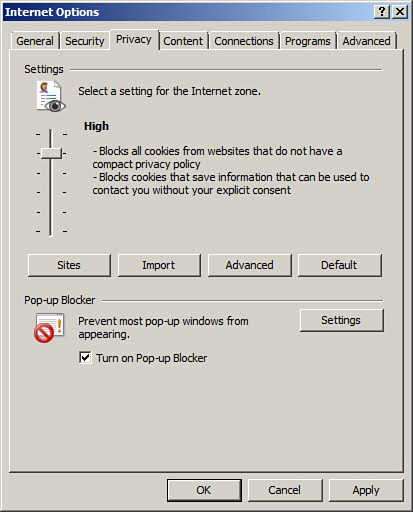
![]()
You can also override any automatic cookie handling that might occur by clicking the Advanced button (this displays the Advanced Privacy Settings dialog box), check marking the box and selecting Prompt for example. This way, a user will be prompted when a website attempts to create a cookie. With this setting in place, IE will display a window similar to Figure 4-7. In this example, my website www.davidlprowse.com was accessed. My site automatically tries to create a cookie due to the bulletin board system code. IE sees this, stops it before it occurs, and verifies with the user whether to accept it. This particular cookie is harmless, so in this case I would accept it. There is a learning curve for users when it comes to knowing which cookies to accept. I guarantee that once or twice they will block a cookie that subsequently blocks functionality of the website. In some cases, an organization deals with too many websites that have too many cookies, so this particular security configuration is not an option.
Figure 4-7. IE Cookie Privacy Alert
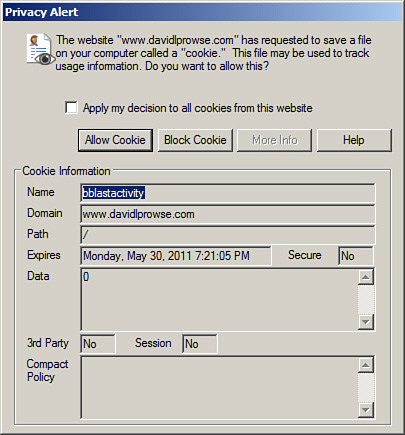
Tracking cookies are used by spyware to collect information about a web user’s activities. Cookies can also be the target for various attacks; namely, session cookies are used when an attacker attempts to hijack a session. There are various types of session hijacking including Cross-site scripting (also known as XSS), which is when the attacker manipulates a client computer into executing code considered trusted as if it came from the server the client was connected to. In this way, the hacker can acquire the client computer’s session cookie (allowing them to steal sensitive information) or exploit the computer in other ways. We cover more about session hijacking in Chapter 5, “Network Design Elements and Network Threats.”
Pop-ups are the bane of any web surfer. There is a pop-up blocker in the Privacy tab of Internet Explorer, this is on by default, but is worth checking if a user is getting a lot of pop-ups.
The Content tab allows for parental controls and a content advisor, both of which can help secure the browser. This tab is also where you can find encryption certificates. You can find more information on certificates in Chapter 13, “PKI and Encryption Protocols.”
The Connections tab enables a user to make secure connections through a VPN and also connect to the Internet via a proxy server as mentioned earlier. You can find more information on VPNs in Chapter 8, “Physical Security and Authentication Models.”
The Advanced tab has more than a dozen security settings that you can find by scrolling toward the bottom of the Settings box. For example, a hotel that offers Internet access as a service for guests might check mark the Empty Temporary Internet Files folder option. This way, the history of users are erased when they close the browser. On a related note, salespeople, field technicians, and other remote users should be trained to delete temporary files and cookies when they are using computers on the road. From here, you can also configure whether to check if SSL certificates have been revoked. You can also check if the proper version of SSL is used. At the time of this book’s publishing, it is wise to have SSL 3.0 selected and SSL 2.0 deselected. Some organizations also disable third-party browser extensions from this tab in the Browsing section.
You can enable and disable add-on programs in the Programs tab by clicking the Manage add-ons button. (This can also be accessed directly within the Tools menu.) IE will always ask before installing add-ons, but over time a company might decide that certain add-ons (that were already installed) could be vulnerabilities. For example, in Figure 4-8, an audio ActiveX Control is selected. Perhaps this control is causing IE to close or the system to crash; it could be turned off by clicking the Disable radio button in the Settings box. Most add-ons are ActiveX controls, and ActiveX could also be turned off altogether as mentioned previously.
Figure 4-8. Managing Add-Ons
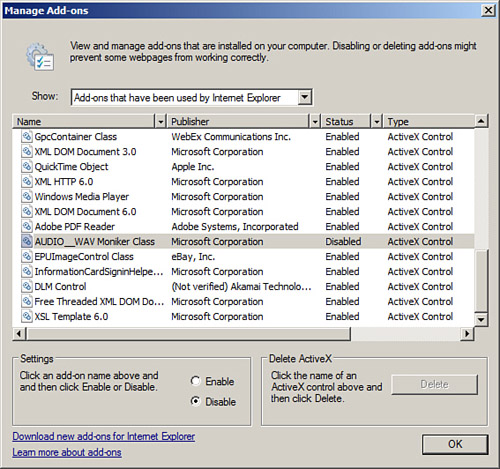
ActiveX controls are small program building blocks used to allow a web browser to execute a program. They are similar to Java applets; however, Java applets can run on any platform, whereas ActiveX can run only on Internet Explorer (and Windows operating systems). You can see how a downloadable, executable ActiveX control or Java applet from a suspect website could possibly contain viruses, spyware, or worse. Flash scripts can also be a security threat. Generally, you can disable undesirable scripts on either the Advanced tab or the Custom level of a security site. If a particular script technology cannot be disabled within the browser, consider using a content filtering solution.
Of course, this only scrapes the surface as you can see, but it gives you an idea of some of the ways to secure Internet Explorer.
In Chapter 3 we mentioned that removing applications that aren’t used is important. But removing web browsers can be difficult, if not downright impossible, and should be voided. Web browsers become one with the operating system, especially so in the case of IE and Windows.
If a computer has multiple browsers, and your organization decides to use Internet Explorer as the default browser, you can make this so by going to the Programs tab and selecting the Make default button. But even if a computer uses Firefox in lieu of IE, it isn’t practical to attempt the removal of IE. The same goes for the converse.
Securing Firefox
If an organization decides to use Mozilla Firefox instead of IE, Firefox can be set as the default by opening the browser, navigating to the Tools menu, clicking Options, clicking Advanced, and on the General tab clicking the Check Now button. This can tell you whether it is default and offer if you want to set it as default. A FYI; we used version 3.6.3 on a Windows Vista platform in the figures. You can also check mark the Always check to see if Firefox is the default browser on startup option, as shown in Figure 4-9, just in case another browser has become the default for some strange reason.
Figure 4-9. Firefox General Tab of the Advanced Options
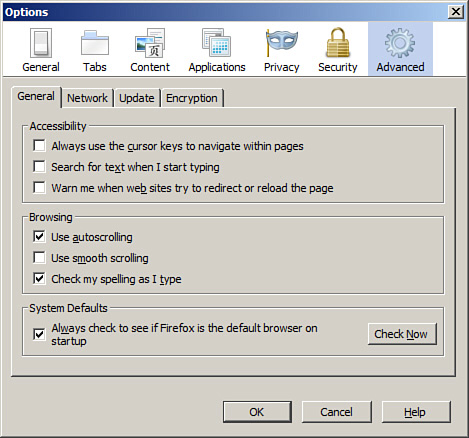
The Options dialog box is where most security configurations appear. Many of the security features we mentioned in the Internet Explorer section can be enabled in Firefox as well, but the navigation to them will be slightly different. Firefox does not offer security zones in the way that IE does and does not offer features that enable the management of ActiveX controls.
Cookies can be configured by clicking the Privacy options at the top of the Options dialog box, as shown in Figure 4-10. Exceptions can be configured as to which sites cookies will be allowed. You can also view the list of cookies currently stored on the computer. Allowed cookies are also known as whitelists.
Figure 4-10. Firefox Privacy Options
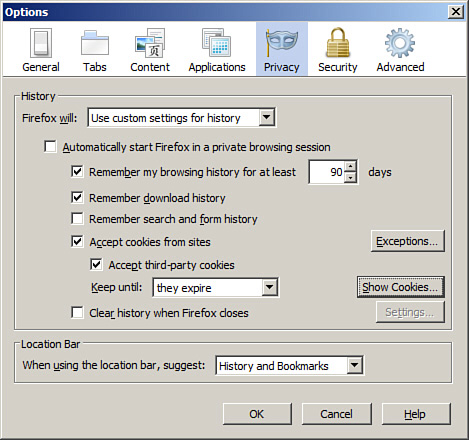
![]()
The Security option houses configurations such as add-on warnings, password remembrance, and other warning messages, as shown in Figure 4-11. Some organizations make it a policy to disable the Remember passwords for sites checkbox. If you do save passwords, it would be wise to enter a master password. This way, when saved passwords are necessary, Firefox will ask for only the master password; and you don’t have to type or remember all the others. A password quality meter tells you how strong the password is. Personally, I don’t recommend allowing any web browser to store passwords. Period.
Figure 4-11. Firefox Security Options
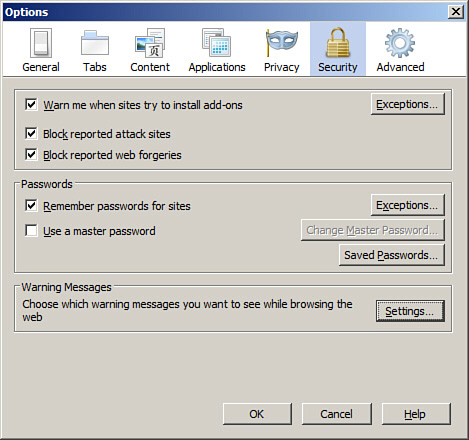
![]()
The Advanced option has several tabs where various portions of Firefox can be configured and include the Encryption tab that includes SSL and TLS versions and certificate information. Also, the Network tab offers the capability to connect to the Internet via a proxy server. This can be done by following these steps:
Step 1. Click the Settings button. This displays the Connection Settings dialog box.
Step 2. Proxies can be auto-detected, but to continue setting up one manually, click the Manual proxy configuration radio button
Step 3. Type in the IP address or name of the proxy server followed by the inbound port it uses
The resulting configuration would look something similar to Figure 4-12. This figure shows a configured HTTP proxy. You can also enable automatic proxy configurations if your proxy server allows for that. A specific URL would be needed that points to the appropriate server and configuration script.
Figure 4-12. Firefox Proxy Connection
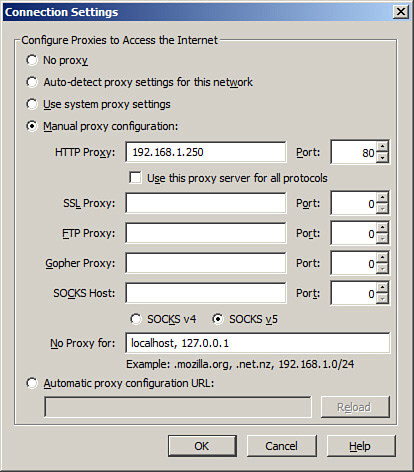
Another way to secure Firefox is to use third-party pop-up blocking software such as Adblock Plus. This is an extension to Firefox, or add-on, so the use of add-ons needs to be enabled. However, programs like this one will automatically update as new types of advertisement pop-ups are released.
Firefox has an entire site dedicated to browser add-ons at https://addons.mozilla.org/en-US/firefox/. One example of a smart add-on is NoScript. You can install this to protect against possible malicious JavaScript, Flash, and XSS code. This helps to ward off hijacking and click-jacking attempts. Check out the site to find more smart add-ons that help to make Firefox more secure and efficient. There are add-ons to get a handhold on the amount of Google ads you encounter, antiphishing tools, and lots more.
Keep in mind that the technology world is changing quickly, especially when it comes to the Internet, browsing, web browsers, and attacks. Be sure to periodically review your security policies for web browsing and keep up to date with the latest browser functionality, security settings, and malicious attacks.
Securing Other Applications
Typical users shouldn’t have access to any applications other than the ones they specifically need. For instance, would you want a typical user to have full control over the Command Prompt in Windows? Doubtful—and protective measures should be put into place to make sure the typical user does not have access.
One way to do this is to use User Account Control or UAC. User Account Control should be used on qualifying Windows operating systems. User Account Control (UAC) is a security component of Windows Vista that keeps every user (besides the actual Administrator account) in standard user mode instead of as an administrator with full administrative rights—even if they are a member of the administrators group. It is meant to prevent unauthorized access and avoid user error in the form of accidental changes. A user attempting to execute commands in the Command Prompt will be blocked, and will be asked for credentials before continuing. This applies to other applications within Windows.
Another way to deny access to applications is to create a policy. For example, on a Windows Server 2003, you can do this in two ways. The first way is to disallow access to specific applications; this policy is called Don’t Run Specified Windows Applications. However, the list could be longer than Florida, so another possibility would be to configure the Run Only Allowed Windows Applications, as shown in Figure 4-13. This and the previously mentioned policy are adjacent to each other and can be found at the following path in Windows Server 2003: Policy (in this case we use the Marketing-Policy again) > User Configuration > Administrative Templates > System.
Figure 4-13. Run Only Allowed Windows Applications Policy
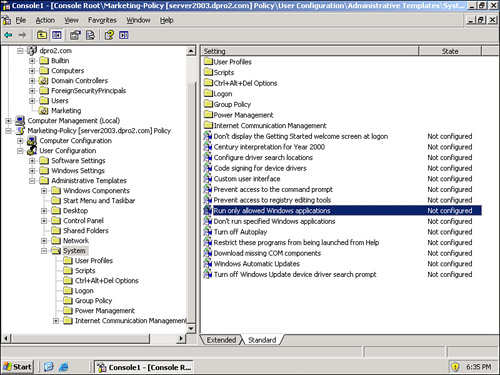
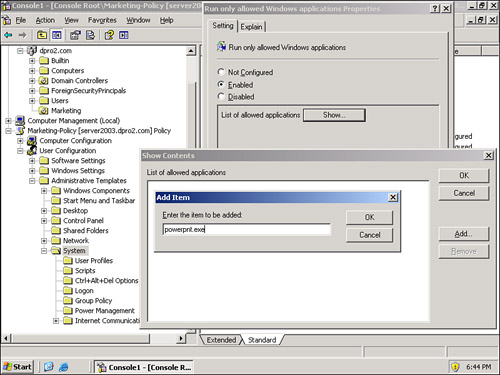
When double-clicked, the policy opens and you can enable it and specify one or more applications that are allowed. All other applications will be denied to the user (if the user is logged onto the domain and is a member of the Marketing organizational unit to which the policy is applied). Maybe you as the systems administrator decide that the marketing people should be using only Microsoft PowerPoint. A rather narrow view, but let’s use that just for the sake of argument. All you need to do is click the Enabled radio button, click the Show button, and in the Show Contents window, add the application—in this case, PowerPoint, which is Powerpnt.exe. An example of this is shown in Figure 4-14.
Figure 4-14. Adding a Single Allowed Application
This is in-depth stuff, and the CompTIA Security+ won’t test you on exact procedures for this, but you should be aware that there are various ways to disallow access to just about anything you can think of. Of course, the more practice you can get on various servers including Windows Server 2003 and 2008, the better.
For those applications that users are allowed to work with, they should be secured accordingly. Table 4-1 shows some common applications and some simple safeguards that can be implemented for them.
Table 4-1. Common Applications and Safeguards
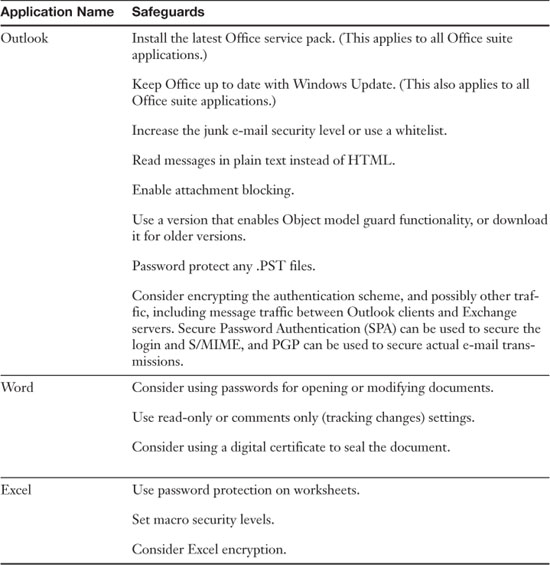
Whatever the application you use, attempt to secure it by updating and configuring it. Access the manufacturer’s website for more information on how to secure the application. Just remember that users still need to work with the program. Don’t make it so secure that a user gets locked out!
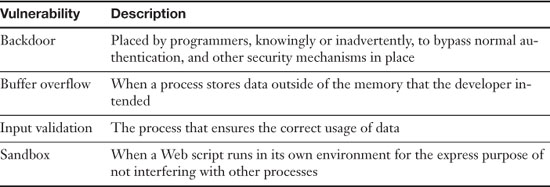
Applications should be analyzed for backdoors, possible buffer overflows, and proper data input validation. Let’s discuss these three briefly.
As mentioned in 2, “Computer Systems Security,” backdoors are used in computer programs to bypass normal authentication and other security mechanisms in place. These can be avoided by updating the operating system and applications and firmware on devices.
Applications in general should be protected from buffer overflows. A buffer overflow is when a process stores data outside of the memory that the developer intended. This could cause erratic behavior in the application, especially if the memory already had other data in it. Stacks and heaps are data structures that can be affected by buffer overflows. Value types are stored in a stack, whereas reference types are stored in a heap. An ethical coder will try to keep these running efficiently. An unethical coder will attempt to use a buffer overflow to affect heaps and stacks that in turn could affect the application in question or the operating system. The buffer overflow might be initiated by certain inputs and can be prevented by bounds checking. It can also be prevented by using correct code and the right programming language for the job in question. Without getting too much into the programming side of things, special values called “canaries” are used to protect against buffer overflows.
Input validation is important for website design and applications development. Input validation or data validation is a process that ensures the correct usage of data. If data is not validated correctly, it can lead to security vulnerabilities and data corruption. You can check data in many ways, from data checks to consistency checks to spelling and grammar checks, and so on. Whatever data is being dealt with, it should be checked to make sure it is being entered correctly and won’t create or take advantage of a security flaw. For example, if an organization has a web page with a contact form, the data entered by the visitor should be checked for errors or vulnerabilities. Sometimes, web developers will run web scripts in a sandbox. A sandbox is when a Web script runs in its own environment for the express purpose of not interfering with other processes, possibly for testing. Table 4-2 summarizes the programming vulnerabilities we have covered in this section.
Table 4-2. Summary of Programming Vulnerabilities
![]()
Organizations use lots of applications specific to their type of business. Stay on top of the various vendors that supply your organization with updates and new versions of software. Always test what effects one new piece of software will have on the rest of your installed software before implementation.
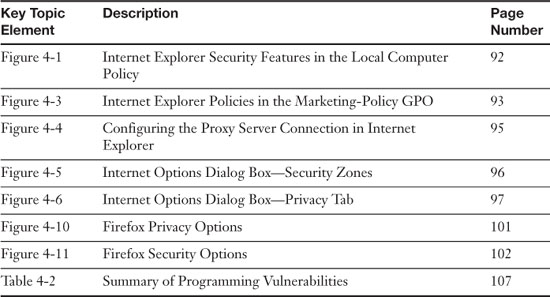
Exam Preparation Tasks: Review Key Topics
Review the most important topics in the chapter, noted with the Key Topics icon in the outer margin of the page. Table 4-3 lists a reference of these key topics and the page numbers on which each is found.
![]()
Table 4-3. Key Topics for Chapter 4
Complete Tables and Lists from Memory
Print a copy of Appendix A, “Memory Tables,” (found on the DVD), or at least the section for this chapter, and complete the tables and lists from memory. Appendix B, “Memory Tables Answer Key,” also on the DVD, includes completed tables and lists to check your work.
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
Hands-On Labs
Complete the following written step-by-step scenarios. After you finish (or if you do not have adequate equipment to complete the scenario), watch the corresponding video solutions on the DVD.
If you have additional questions, feel free to post them at my website at www.davidlprowse.com in the Ask Dave forum. (Free registration is required to post on the website.)
Equipment Needed
• A computer with Internet access and Internet Explorer 7 or higher
• Windows Server 2003 (or Server 2008) that has been promoted to a domain controller
Lab 4-1: Securing the Browser
In this lab, you secure Internet Explorer by turning on the pop-up blocker, enabling the phishing filter, increasing zone and cookies security, and enabling advanced features. The steps are as follows:
Step 1. Open Internet Explorer.
Step 2. Access the Tools menu by pressing ALT+T:
A. Select Pop-up Blocker > Turn on Pop-up Blocker.
B. Next, select Phishing Filter > Turn On Automatic Website Checking.
Step 3. Go back to the Tools menu, and select Internet Options. This displays the Internet Options dialog box.
Step 4. Increase security of the browser’s zones:
A. Click the Security tab.
B. Select the Internet zone.
C. Set the slider to High for maximum security.
Step 5. Increase security for cookies:
A. Click the Privacy tab.
B. Set the slider to High.
Step 6. View other security configurations:
A. Click the Advanced tab.
B. Scroll down to the Security section.
C. Check mark the Empty Temporary Internet Files folder when the browser is closed checkbox.
D. Scroll down further, and verify that SSL 3.0 is enabled and that SSL 2.0 is disabled.
E. Scroll back up to the Browsing section. Deselect the Enable third-party browser extensions* checkbox.
Step 7. Set up websites to be trusted and restricted:
A. Click the Security tab.
B. Click the Restricted sites zone, and then click the Sites button.
C. Add a website to the list. Be sure to remove it when you finish with this lab.
D. Click Close.
E. Click the Trusted sites zone, and click the Sites button.
F. Add a website to the list such as https://www.paypal.com. Be sure to remove it when you finish with this lab.
Watch the solution video in the “Hands-On Scenarios” section of the DVD.
Lab 4-2: Disabling Applications with a Windows Server 2003 Policy
In this lab, you restrict users from applications by configuring a group policy. We use Windows Server 2003 as our example, but Windows Server 2008 will be quite similar. Remember that the server must have been previously promoted to a domain controller so that you can create organization units and the corresponding policies.
Note
For more information about promoting a server to a domain controller, see my video on my website at the following link: www.davidlprowse.com/forums/showthread.php?t=1548.
The steps are as follows:
Step 1. Access the Windows Server.
Step 2. Open your MMC if you have one. If not, create a new one so that you can keep all of your snap-ins organized in one window. Add the Active Directory Users and Computers snap-in.
Step 3. Create a new OU:
A. Navigate to Active Directory Users and Computers > [domain name]. In this example I use the domain name Dpro2.com.
B. Right-click the domain name.
C. Select New > Organization Unit.
D. Name the OU. For example: accounting. Then click OK. This should add the new OU to the domain.
Step 4. Create a new policy based off the OU:
A. Right-click the new OU and select Properties. This displays the accounting Properties dialog box.
B. Click the Group Policy tab.
C. Click the New button. Name the policy, for example acct-policy and press Enter. Then click Close.
Step 5. Add the new policy to the MMC:
A. Go to File > Add/Remove Snap-in.
B. In the Add/Remove Snap-in dialog box, click Add.
C. Select the Group Policy Object Editor and click Add.
D. In the Select Group Policy Object dialog box, click Browse.
E. Double-click the accounting.dpro2.com folder.
F. Highlight the policy (for example acct-policy) and click OK.
G. Click Finish, Close, and OK for the other open dialog boxes. This should add the acct-policy to the MMC.
Step 6. Configure the policy:
A. Expand the acct-policy.
B. Navigate to User Configuration > Administrative Templates > System.
C. Double-click Don’t run specified Windows applications.
D. Click the Enabled radio button.
E. Click Show.
F. Click Add and add an application, for example winword.exe (the executable for Microsoft Word). Then click OK. Be sure to reset this at the end of the lab if it will affect any computers or users.
G. Click OK for the policy’s Properties window. This brings you back to the MMC. The policy will now be enabled.
H. Double-click the Run only allowed Windows applications policy.
I. Enable the policy; then click Show.
J. Add an application by clicking the Add button and typing the name of an application, for example excel.exe (the executable for Microsoft Excel), and clicking OK.
K. Click OK for the policy’s Properties window. This brings you back to the MMC. The policy will now be enabled.
Step 7. Save your MMC.
Watch the solution video in the “Hands-On Scenarios” section of the DVD.
View Recommended Resources
For readers who want to brush up on their CompTIA A+ topics:
• Prowse, David L. CompTIA A+ Exam Cram, Fourth Edition. Que. 2010.
Firefox add-on links:
• Adblock Plus Firefox add-on: https://addons.mozilla.org/en-US/firefox/addon/1865/
• NoScript Firefox add-on: https://addons.mozilla.org/en-US/firefox/addon/722/
Answer Review Questions
Answer the following review questions. You can find the answers at the end of this chapter.
1. Which of the following is one way of preventing spyware from being downloaded?
A. Use firewall exceptions.
B. Adjust Internet Explorer security settings.
C. Adjust the Internet Explorer home page.
D. Remove the spyware from Add/Remove Programs.
2. What key combination should be used to close a popup window?
A. Windows+R
B. Ctrl+Shift+Esc
C. Ctrl+Alt+Del
D. Alt+F4
3. Which protocol can be used to secure the e-mail login from an Outlook client using POP3 and SMTP?
A. SMTP
B. SPA
C. SAP
D. Exchange
4. What are two ways to secure Internet Explorer? (Select the two best answers.)
A. Set the Internet zone’s security level to High.
B. Disable the pop-up blocker.
C. Disable ActiveX controls.
D. Add malicious sites to the Trusted Sites zone.
5. Heaps and stacks can be affected by which of the following attacks?
A. Buffer overflows
B. Root kits
C. SQL injection
D. Cross-site scripting
6. As part of your user awareness training, you recommend that users remove which of the following when they finish accessing the Internet?
A. Instant messaging
B. Cookies
C. Group policies
D. Temporary files
7. Which statement best applies to the term Java Applet?
A. It decreases the usability of web-enabled systems.
B. It is a programming language.
C. A Web browser must have the capability to run Java applets.
D. It uses digital signatures for authentication.
8. Which of the following concepts can ease administration but can be the victim of malicious attack?
A. Zombies
B. Backdoors
C. Buffer overflow
D. Group policy
9. In an attempt to collect information about a user’s activities, which of the following will be used by spyware?
A. Tracking cookie
B. Session cookie
C. Shopping cart
D. Persistent cookie
10. What is it known as when a Web script runs in its own environment and does not interfere with other processes?
A. Quarantine
B. Honeynet
C. Sandbox
D. VPN
11. How can you train a user to easily determine whether a web page has a valid security certificate? (Select the best answer.)
A. Have the user contact the webmaster.
B. Have the user check for HTTPS://.
C. Have the user click the padlock in the browser and verify the certificate.
D. Have the user called the ISP.
12. To code applications in a secure manner, what is the best practice to use?
A. Cross-site scripting
B. Flash version 3
C. Input validation
D. HTML version 5
Answers and Explanations
1. B. Adjust the Internet Explorer security settings so that security is at a higher level, and add trusted and restricted websites.
2. D. Alt+F4 is the key combination that is used to close an active window. Sometimes it is okay to click the X, but malware creators are getting smarter all the time; the X could be a ruse.
3. B. SPA (Secure Password Authentication) is a Microsoft protocol used to authenticate e-mail clients. S/MIME and PGP can be used to secure the actual e-mail transmissions.
4. A and C. By increasing the Internet zone security level to high, you employ the maximum safeguards for that zone. ActiveX controls can be used for malicious purposes; disabling them makes it so that they do not show up in the browser. Disabling a pop-up blocker and adding malicious sites to the Trusted Sites zone would make Internet Explorer less secure.
5. A. Stacks and heaps are data structures that can be affected by buffer overflows. Value types are stored in a stack, whereas reference types are stored in a heap. An ethical coder will try to keep these running efficiently. An unethical coder will attempt to use a buffer overflow to affect heaps and stacks that in turn could affect the application in question or the operating system. The buffer overflow might be initiated by certain inputs and can be prevented by bounds checking.
6. B. The best answer is cookies, which can be used for authentication and session tracking and can be read as plain text. They can be used by spyware and can track people without their permission. It is also wise to delete temporary Internet files as opposed to temporary files.
7. C. To run Java applets, a Web browser must have that option enabled. Java increases the usability of web-enabled systems, and Java is a programming language. It does not use digital signatures for authentication.
8. B. Backdoors were originally created to ease administration. However, hackers quickly found that they could use these backdoors for a malicious attack.
9. A. A tracking cookie will be used, or misused, by spyware in an attempt to access a user’s activities. Tracking cookies are also known as browser cookies or HTTP cookies, or simply a cookie. Shopping carts take advantage of cookies to keep the shopping cart reliable.
10. C. When a Web script runs in its own environment for the express purpose of not interfering with other processes, it is known as running in a sandbox. Quite often, the sandbox will be used to create sample scripts before they are actually implemented. Quarantining is a method used to isolate viruses. A honeynet is a collection of servers used to attract hackers and isolate them in an area where they can do no damage. VPN is short for virtual private network, which enables the connection of two hosts from remote networks.
11. C. In Internet Explorer, the user should click the padlock in the browser; this will show the certificate information. Quite often, the address bar will have different colors as the background; for example, blue or green means that the certificate is valid, whereas red or pink indicates a problem. In Firefox, click the name of the website listed in the address bar just before where it says HTTPS to find out the validity of the certificate. Contacting the webmaster and calling the ISP are time-consuming, not easily done, and not something that an end user should do. Although HTTPS:// can tell a person that the browser is now using the hypertext transfer protocol secure, it does not necessarily determine whether the certificate is valid.
12. C. Input validation is the best practice to use when coding applications. This is important when creating web applications or web pages that require information to be inputted by the user.
