Appendix A. Memory Tables
This appendix contains the tables and lists that are part of the Exam Preparation Tasks in each chapter. The following tables and lists cover key topics but are incomplete. Fill them in and check your answers against the complete tables and lists in Appendix B, “Memory Tables Answer Key,” on the DVD. The complete tables and lists also appear in the book’s chapters.
Chapter 2
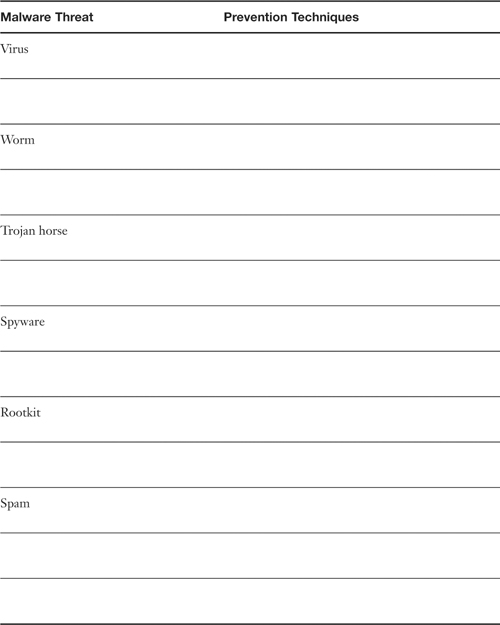
Table 2-1. Summary of Malware Threats
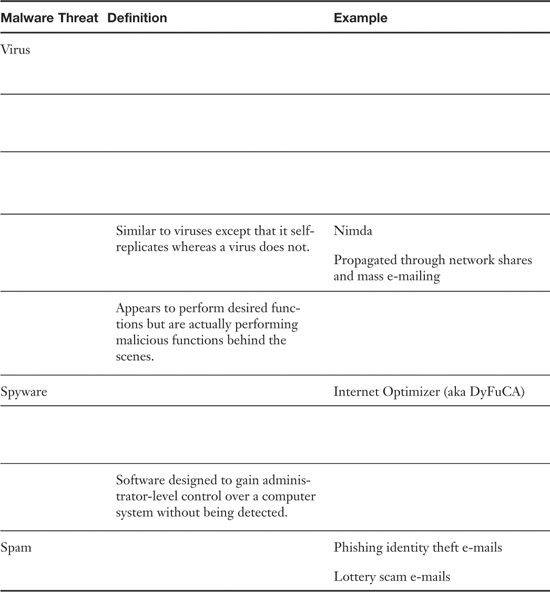
Table 2-2. Summary of Malware Prevention Techniques
Chapter 3
Patch Management
Fill-in the second and fourth phases of patch management, as well as descriptions of each.
• Planning—Before actually doing anything, a plan should be set into motion. The first thing that needs to be decided is whether the patch is necessary and if it will be compatible with other systems. Microsoft Baseline Security Analyzer (MBSA) is one example of a program that can identify security misconfigurations on the computers in your network, letting you know if patching is needed. If the patch is deemed necessary, the plan should consist of a way to test the patch in a “clean” network on clean systems, how and when the patch will be implemented, and how the patch will be checked after it is installed.
• ______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
• Implementing—If the test is successful, the patch should be deployed to all the necessary systems. In many cases, this will be done in the evening or over the weekend for larger updates. Patches can be deployed automatically using software such as Microsoft’s Systems Management Server (SMS).
• ______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
Keeping a Well-Maintained Computer
Fill in the fourth and sixth steps for keeping a well-maintained computer, as well as descriptions of each.
Step 1. Use a surge protector or UPS—Make sure the computer and other equipment connect to a surge protector, or better yet a UPS if you are concerned about power loss.
Step 2. Update the BIOS—Flashing the BIOS isn’t always necessary; check the manufacturer’s website for your motherboard to see if an update is needed.
Step 3. Update Windows—This includes the latest SPs and any Windows updates beyond that and setting Windows to alert if there are any new updates.
Step 4. ______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
Step 5. Update the firewall—Be sure to have some kind of firewall installed and enabled; then update it. If it is the Windows Firewall, updates should happen automatically through Windows Update. However, if you have a SOHO router with a built-in firewall, or other firewall device, you need to update the device’s ROM by downloading the latest image from the manufacturer’s website.
Step 6. ______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
Chapter 4
Table 4-1. Common Applications and Safeguards
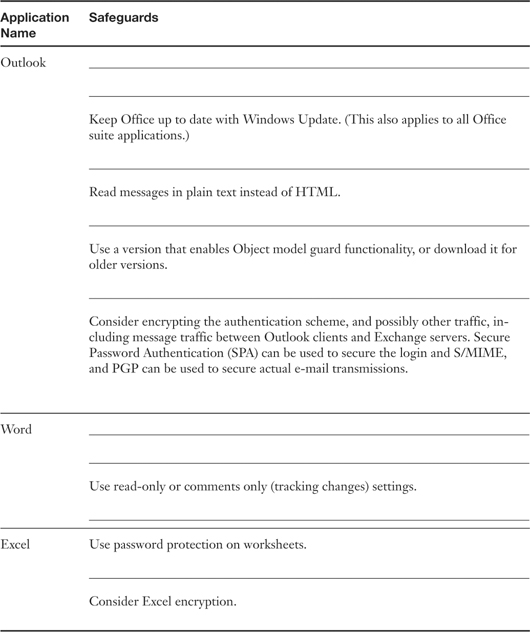
Table 4-2. Summary of Programming Vulnerabilities
Chapter 5
Table 5-1. Private IP Ranges (as Assigned by the IANA)
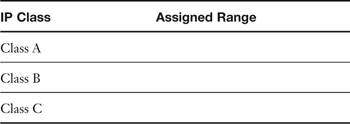
Table 5-3. Port Ranges
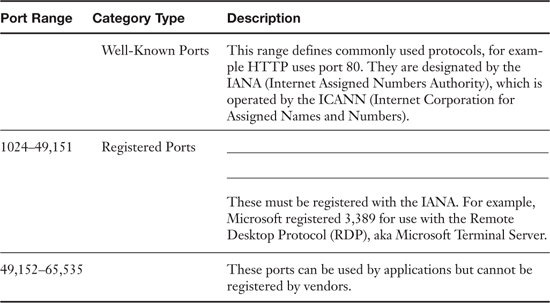
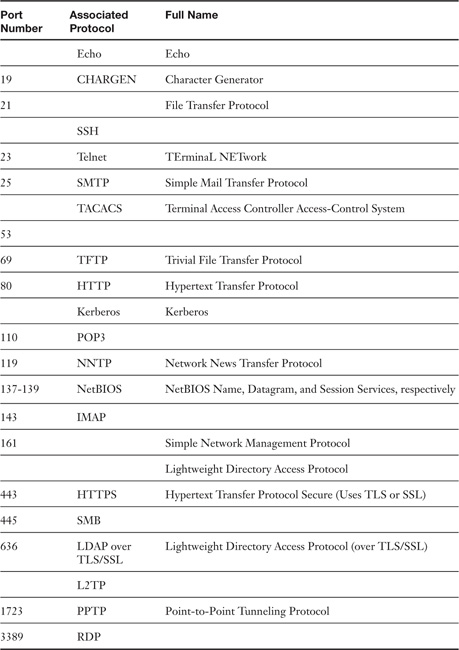
Table 5-4. 23 Ports and Their Associated Protocols
Chapter 6
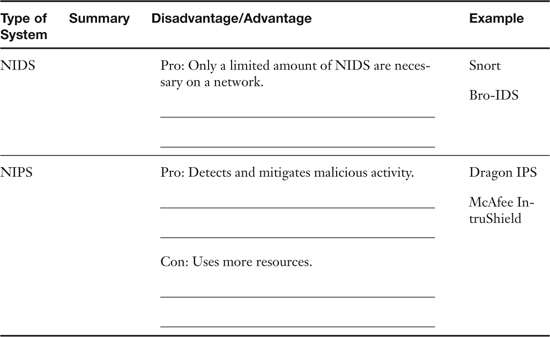
Table 6-1. Summary of NIDS Versus NIPS
Chapter 7
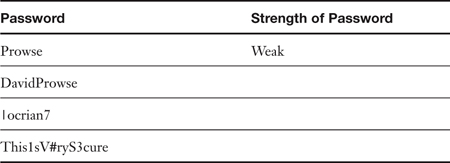
Table 7-1. Weak, Strong, and Stronger Passwords
Privilege Escalation
Describe the following terms:
• Vertical privilege escalation
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
• Horizontal privilege escalation
______________________________________________________________
______________________________________________________________
______________________________________________________________
This can be done through hacking or by a person walking over to other people’s computers and simply reading their e-mail! Always have your users lock their computer (or log off) when they are not physically at their desk!
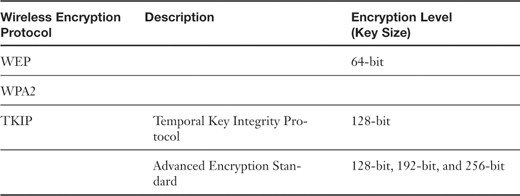
Table 7-2. Wireless Encryption Methods
Chapter 8
Table 8-1. VPN Tunneling Protocols
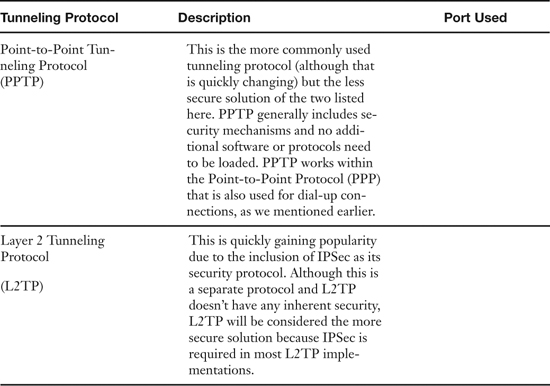
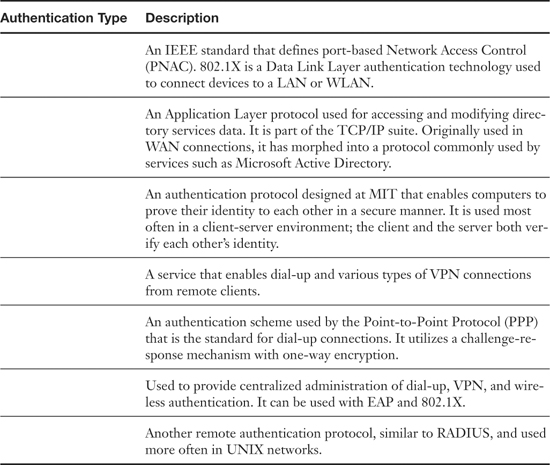
Table 8-2. Summary of Authentication Technologies
Chapter 9
Mandatory Access Control
Describe the following terms:
• Rule-based access control
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
• Lattice-based access control
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
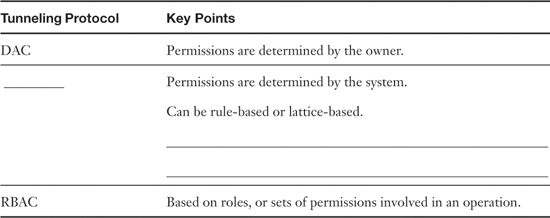
Table 9-1. Summary of Access Control Models
Here are a couple more tips when it comes to user accounts, passwords, and logons. Fill in the title for each description.
• ________________________________________________________________—It’s nice that Windows has incorporated a separate administrator account: The problem is that by default the account has no password. To configure this account, navigate to Computer Management > System Tools > Local Users and Groups > Users and locate the Administrator account. In a domain this would be in ADUC > Domain name > Users. By right-clicking the account, you see a drop-down menu in which you can rename it and/or give it a password. (Just remember the new username and password!) Now it’s great to have this additional administrator account on the shelf just in case the primary account fails; however, some OSs such as Vista disable the account by default. To enable it, right-click the account and select Properties. In the General tab, deselect the Account Is Disabled check box. Alternatively, open the command line and type net user administrator /active:yes. The way that the administrator account behaves by default will depend on the version of Windows. The Linux/UNIX counterpart is the root account. The same types of measures should be employed when dealing with this account.
• ____________________________________________________________________—This can be done by right-clicking the account in question, selecting Properties and then selecting the checkbox named Account Is Disabled. It is also possible to delete accounts (aside from built-in accounts such as the Guest account): however, companies usually opt to have them disabled instead so that the company can retain information linking to the account.
• _______________________—Pressing Ctrl+Alt+Del before the logon adds a layer of security to the logon process. This can be added as a policy on individual Windows computers. It is implemented by default with computers that are members of a domain.
• _______________________—Policies governing user accounts, passwords, and so on can help you to enforce your rules, as discussed in the next section. Large organizations with a lot of users will usually implement a self-service password management system. This means that users reset their own passwords after a given amount of time (set in a group policy); the administrator does not create passwords for users.
Chapter 10
Table 10-2. Summary of Risk Assessment Types
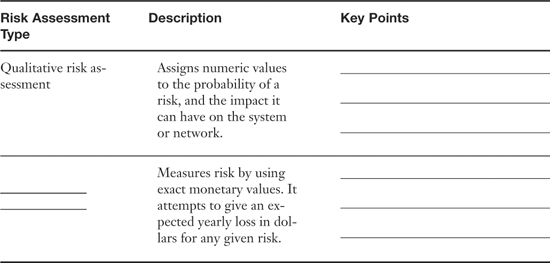
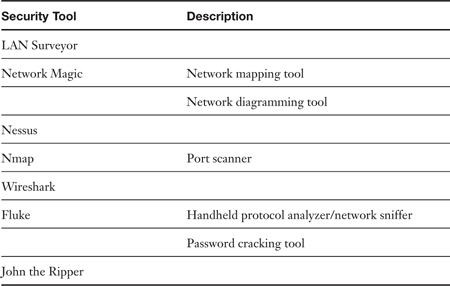
Table 10-3. Summary of Chapter 10 Security Tools
Chapter 11
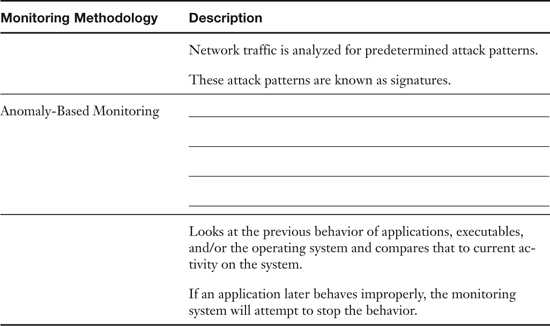
Table 11-1. Summary of Monitoring Methodologies
Network adapters can work in one of two different modes: promiscuous and non-promiscuous. Define each.
• Promiscuous mode
______________________________________________________________
______________________________________________________________
______________________________________________________________
• Non-promiscuous mode
______________________________________________________________
______________________________________________________________
______________________________________________________________
Chapter 12
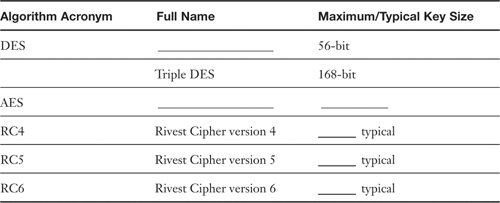
Table 12-3. Summary of Symmetric Algorithms
Chapter 14
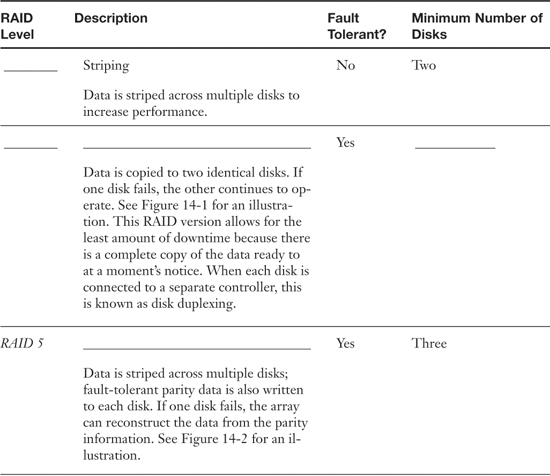
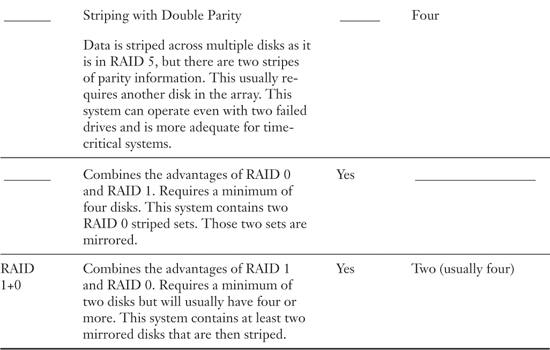
Table 14.1. RAID Descriptions
Redundant Sites
Describe the following types of sites:
• Hot site
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
• Warm site
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
• Cold site
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
Data Backup
Describe the following types of backups:
• Full backup
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
• Incremental backup
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
• Differential backup
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
Other Backup Schemes
Describe the following backup schemes:
• 10 tape rotation
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
• Grandfather-father-son
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
• Towers of Hanoi
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
______________________________________________________________
Chapter 15
Table 15-1. Summary of Social Engineering Types
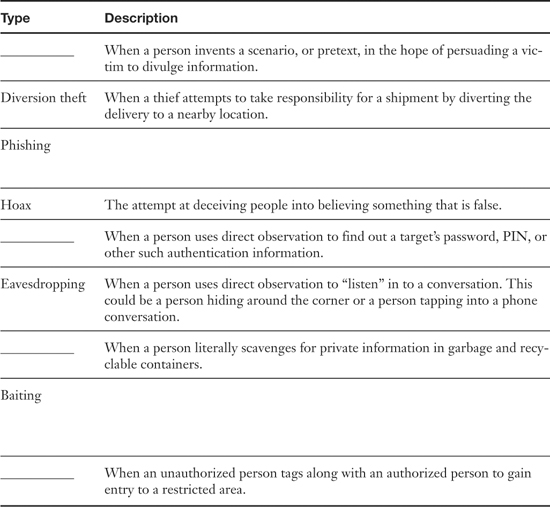
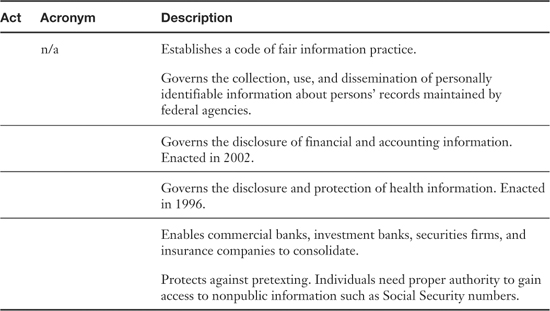
Table 15-4. Acts Passed Concerning the Disclosure of Data and PII
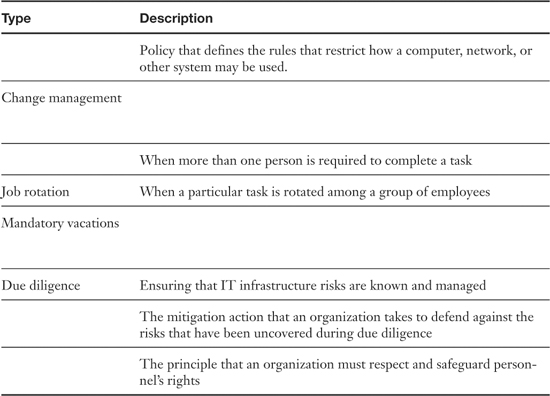
Table 15-5. Summary of Policy Types