Chapter 5. Network Design Elements and Network Threats
This chapter covers the following subjects:
Network Design—This section discusses network design elements such as hubs, switches, and routers, and how to protect those devices from attack. It also talks about network address translation, private versus public IP addresses, and the private IP ranges. Afterward you learn about network zones and interconnections, for example, intranets and extranets, demilitarized zones, LANs, and WANs. Finally, you learn how to defend against attacks on your virtual local area networks, IP subnets, and telephony devices.
Ports, Protocols, and Malicious Attacks—In this section, you learn the ports and their associated protocols you need to know for the exam and how to secure those ports. The end of the chapter covers the basics about network attacks and how to defend against them.
This chapter covers the CompTIA Security+ SY0-201 objectives 2.1 and 2.2.
Up until now we have focused on the individual computer system. Let’s expand our security perimeter to now include networks. Network design is extremely important in a secure network. The elements that you include in your design can help to defend against many different types of network attacks. Being able to identify these network threats is the next step in securing your network. If you apply the strategies and defense mechanisms included in this chapter, you should be able to stave off most network attacks. This chapter and the following two chapters assume that you have a working knowledge of networks and that you have the CompTIA Network+ certification or commensurate experience. Let’s begin with network design.
Foundation Topics: Network Design
Proper network design is critical for the security of your network, servers, and client computers. You need to protect your network devices so that they and the clients that they connect together will be less subject to attack. Implementing network address translation and having a good understanding of the standard private IP ranges can further protect all the computers in a standard network. A thorough knowledge of network zones, for example local area networks and demilitarized zones, is also important when designing a secure network. Finally, by utilizing subnetting, virtual local area networks, network access control, and secure telephony devices, you can put the final touches on your network design. We start with a relatively easy topic: network devices.
Network Devices
Let’s begin with the network devices that are common on today’s networks. Central connecting devices such as hubs and switches need to be secured and monitored; it makes sense because these devices will connect all the computers on your local area network. Attacks aimed at these devices could bring down the entire LAN. And of course, routers are extremely important when interconnecting local area networks and subnets. Because many routers have visible IP addresses on the Internet, you should expand your line of thinking to include securing these devices from attackers that might come from inside and outside your network. It is more common that attackers will be situated outside your network, but you never know!
Hub
A hub is a central connecting device used in a physical star topology. It is used in Ethernet networks only. A hub is actually a simple device, connecting multiple computers together and amplifying and passing on the electrical signal. Internally, the hub just has one trunk circuit to which all the ports connect. The hub broadcasts information out to all ports. Because of this, it can be easily compromised. A mischievous person could connect a laptop to any port on the hub, or any Ethernet jack that connects to the hub, and access all network traffic with the aid of a protocol analyzer.
Note
Protocol analyzers are also known as network sniffers, or packet sniffers. For more information on protocol analyzers, see Chapter 10, “Vulnerability and Risk Assessment.”
A hub resides on the Physical Layer of the OSI model; therefore, when attempting to secure a hub, you have to think in physical, tangible terms. For example, the hub should be located in a secure area—server room, locked wiring closet, and so on. Further security precautions should be made to monitor traffic, which is covered in Chapter 11, “Monitoring and Auditing.” However, the best way to secure a hub is to remove it! Basic hubs are deprecated devices and should be replaced with a switch or other more current device. Most companies today rely on the switch instead of the hub.
Switch
Ethernet switching was developed in 1996 and quickly took hold as the preferred method of networking, taking the place of deprecated devices such as hubs and bridges. This is due to the switch’s improvement in the areas of data transfer and security. Like a hub, a switch is a central connecting device to which all computers on the network connect. Again, like a hub, a switch will regenerate the signal. That’s where the similarity ends, however. Unlike a hub, a switch sends the signal in a unicast fashion to the correct computer, instead of broadcasting it out to every port. It does this by mapping computers’ MAC addresses to their corresponding physical port. This can effectively make every port an individual entity, thus securing the network, and exponentially increasing data throughput. Switches employ a matrix of copper wiring instead of the standard trunk circuit, and intelligence to pass information to the correct port. Although there are Layer 1 through Layer 4 switches, the type generally covered on the Security+ exam is the Layer 2 switch. This switch sends information to each computer via MAC addresses.
Although the switch is by far the superior solution compared to a hub, there are still some security implications involved with it. These include but are not limited to the following:
• MAC flooding—Switches have memory that is set aside to store the MAC address to the port translation table, known as the Content Addressable Memory table, or CAM table. A MAC flood can send numerous packets to the switch, each of which has a different source MAC address, in an attempt to use up the memory on the switch. If this is successful, the switch changes state to what is known as failopen mode. At this point, the switch broadcasts data on all ports the way a hub does. This means two things: First, that network bandwidth will be dramatically reduced, and second, that a mischievous person could now use a protocol analyzer, running in promiscuous mode, to capture data from any other computer on the network. Yikes!
![]()
Some switches are equipped with the capability to shut down a particular port if it receives a certain amount of packets with different source MAC addresses. For example, Cisco switches use port-security. This restricts a port by limiting and identifying MAC addresses of the computers that are permitted to access that port. A Cisco switch defines three categories of secure MAC addresses as part of a policy on the switch. Other providers have like policies that can be implemented. Other ways to secure against MAC flooding and constrain connectivity include using 802.1X-compliant devices, Dynamic VLANs, and network intrusion detection systems (NIDS), and to consistently monitor the network. We speak more to these concepts later in this chapter and in future chapters.
• Physical tampering—Some switches have a dedicated monitoring port. If this is accessible, a person could perpetuate a variety of attacks on the network. Even if a single port of the switch is accessible, a person could attempt the aforementioned MAC flooding attack and move on from there. So remember that the switch needs to be physically secured, most likely in a server room with some type of access control system. It sounds so simple, but it is commonly overlooked by many companies.
Router
A router connects two or more networks to form an internetwork. They are used in LANs, in WANs, and on the Internet. This device routes data from one location to another, usually by way of the IP address and IP network numbers. Routers function on the Network Layer of the OSI model.
Note
For a primer about the OSI Model and its layers, see the following link: www.davidlprowse.com/forums/showthread.php?t=1556.
Routers come in several forms including SOHO routers, those four port devices used in homes and small offices to connect to the Internet; servers, which can be configured for routing if they have multiple network adapters and the proper software; and most commonly, black box devices such as Cisco routers. Routers are intelligent and even have their own operating system, for example Cisco routers use an IOS (Internetwork Operating System). Quite often, a DMZ will be set up within a router, especially SOHO router devices; we speak more about the DMZ later in this chapter.
Routers can be the victim of denial-of-service attacks, malware intrusions, and other attacks that we cover in more depth later in this chapter and can spread these attacks and malware to other sections of the network. Routers can be protected from these attacks in the following ways:
• Firewalls—Firewalls protect against and filter out unwanted traffic. A firewall can be an individual device or can be added to a router. For example, most SOHO routers have a firewall built in, and Cisco Integrated Services Routers include the Cisco IOS Firewall. You can find more information on firewalls in Chapter 6, “Network Perimeter Security.”
• Intrusion prevention systems (IPS)—An IPS will not only detect, but will also prevent directed attacks, botnet attacks, malware, and other forms of attacks. An IPS can be installed as a network-based solution or on a particular computer and some routers. More information on network-based IPS (and IDS) solutions can be found in Chapter 6.
• Secure VPN connectivity—Instead of connecting directly to a router, virtual private networks enable for secure connections utilizing IPSec and SSL. Secure VPN connectivity can be used on SOHO routers, advanced routers like ones offered by Cisco, or implemented with Windows server. You can find more information about VPNs in Chapter 8, “Physical Security and Authentication Models.”
• Content filtering—Content filtering blocks or restricts access to certain websites. This provides protection from malicious websites. Content filtering can be installed as a server, as an appliance or on some routers. You can find more information about content filters in Chapter 6.
• Access control lists (ACLs)—Access control lists enable or deny traffic. These can be implemented on a router and within firewalls; in some cases the two will be the same physical device. For example, an ACL can be configured to deny any connections by computers that have IP addresses outside of the network number. You can find more information about access control lists in Chapter 9, “Access Control Methods and Models.”
Network Address Translation, and Private Versus Public IP
Network address translation (NAT) is the process of changing an IP address while it is in transit across a router. This is usually so one larger address space (private) can be remapped to another address space, or single IP address (public). In this case it is known as network masquerading, or IP masquerading, and was originally implemented to alleviate the problem of IPv4 address exhaustion. Today, NAT provides protection by hiding a person’s private internal IP address. Basic routers only allow for basic NAT, which is IP address-translation-only. But more advanced routers allow for PAT, or port address translation, which translates both IP addresses and port numbers. A NAT implementation on a firewall hides an entire private network of IP addresses (for example, the 192.168.1.0 network), behind a single publicly displayed IP address. Many SOHO routers, servers, and more advanced routers offer this technology to protect a company’s computers on the LAN. Generally, when an individual computer attempts to communicate through the router, static NAT is employed, meaning that the single private IP address will translate to a single public IP address. This is also called one-to-one mapping.
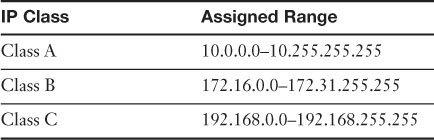
It is also important to know the difference between private and public addresses. A private address is one not displayed directly to the Internet and is normally behind a firewall (or NAT-enabled device). Typically these are addresses that a SOHO router or DHCP server would assign automatically to clients. A list of reserved private IP ranges is shown in Table 5-1. Public addresses are addresses displayed directly to the Internet; they are addresses that anyone can possibly connect to around the world. Most addresses besides the private ones listed in Table 5-1 are considered public addresses. Figure 5-1 shows an example of a router/firewall implementing NAT. The router’s public address is 207.172.15.50, and its private address is 10.0.0.1. Computers to the left of the router are on the LAN, and all their IP addresses are private, protected by NAT, which occurs at the router. Servers outside the Internet cloud have public IP addresses (for example, 208.96.234.193) so that they can be accessed by anyone on the Internet.
Table 5-1. Private IP Ranges (as Assigned by the IANA)
![]()
Figure 5-1. Example of Public and Private IP Addresses
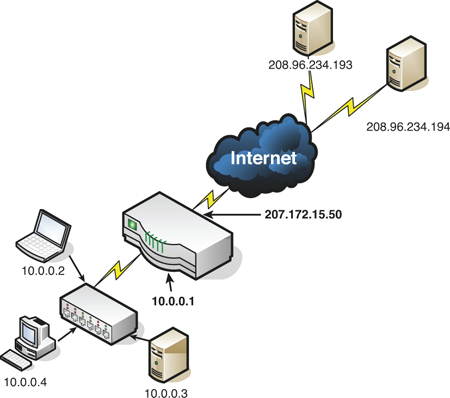
![]()
Network Zones and Interconnections
When designing your network, think about all the pieces of the network and all the connections your network might make to other networks. Are you in charge of a local area network, or more than one local area network that perhaps form a wide area network? What kind of, and how many Internet connections do you have? Will you have servers that need to be accessed by users on the Internet? And will you need to share information with company employees that work from home or with other organizations, while securing that information from the average user on the Internet? The more interconnections and network zones that you have, the more security risk you are taking on. Keep this in mind as you read through the section.
LAN Versus WAN
A local area network, or LAN, is a group of networked computers contained in a small space like a small office, a school, or one or two close-knit buildings. Generally, the computers in the LAN are all assigned private IP addresses and are behind a firewall. Although computers on a LAN do not have to connect to the Internet, they usually will, but will do so via a router that acts as an IP proxy and employs NAT. It is important to secure computers on the LAN by placing them behind the router, assigning private IPs, and verifying that antimalware programs are installed.
A wide area network, or WAN, is one or more LANs connected together. The big difference between a LAN and a WAN is that a WAN covers a larger geographic area. This implies that the services of a telecommunications or data communications provider is necessary. The security implications of a WAN are great; the more connections your network has, the more likely attacks will become. All connections should be monitored and firewalled if possible. Consider that there might be connections to other states or countries...and, to the biggest WAN of them all—the Internet.
Internet
The Internet is the worldwide interconnection of individual computers and computer networks. Because it is a public arena, anyone on the Internet can possibly be a target, or an attacker. All types of sessions on the Internet should be protected at all times. For example, voice calls should be done within a protected VoIP system; data sessions should be protected by being run within a virtual private network; and so on. Individual computers should be protected by firewalls and antimalware programs. Networks should be protected by firewalls as well. But what about systems that need to access the LAN and also need to be accessed by clients on the Internet? Well, one option is to create an area that is not quite the LAN, and not quite the Internet; this is a demilitarized zone, or DMZ.
Demilitarized Zone (DMZ)
When talking about computer security, a Demilitarized Zone (DMZ) is a special area of the network (sometimes referred to as a subnetwork) that houses servers which host information accessed by clients or other networks on the Internet. Some of these servers might include web, FTP, mail, and database computers. These servers might also be accessible to clients on the LAN. There are several ways to set up a DMZ; a common way is the 3-leg perimeter DMZ, as shown in Figure 5-2. Notice the third “leg” that branches off the firewall to the right. This leads to a special switch that has WWW and FTP servers connected to it. Also note that the DMZ is on a different IP network than the LAN, although both the LAN and DMZ are private IP network numbers. The firewall can (and usually will) be configured in a secure fashion on the DMZ connection (172.29.250.200) and an even more secure fashion on the LAN connection (192.168.100.200). The DMZ connection in Figure 5-2 needs to have only inbound ports 80 (WWW) and 21 (FTP) open; all other ports can be closed, thus filtering inbound traffic. The LAN connection can be completely shielded on the inbound side. Although DMZs can be created logically, they are most often found as physical implementations. There are several other implementations of a DMZ. For example, a DMZ can be set up with two firewalls that surround it, also known as a back-to-back perimeter network configuration; in this case the DMZ would be located between the LAN and the Internet. A DMZ might also be set up within a router, especially in small organizations that use basic SOHO router devices. It all depends on the network architecture and security concerns of the organization.
Figure 5-2. 3-Leg Perimeter DMZ
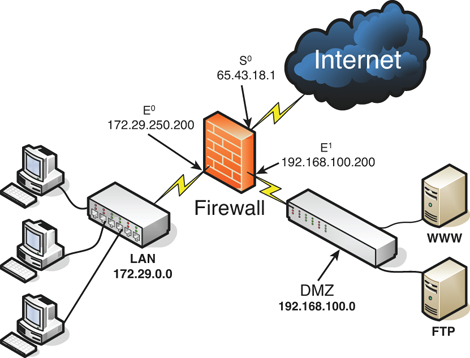
![]()
Intranets and Extranets
Intranets and extranets are implemented so that a company (or companies) can share its data using all the features and benefits of the Internet, while keeping that data secure within the organization, select organizations, and specific users. In the case of an intranet, only one company is involved; it could be as simple as an internal company website, or a more advanced architecture of servers, operational systems, and networks that deploy tools, applications, and of course data. In the case of an extranet, multiple companies can be involved, or an organization can opt to share its data and resources with users that are not part of the organization(s). This sharing is done via the Internet, but again, is secured so that only particular people and organizations can connect. Whether you have an intranet or an extranet, security is a major concern. Proper authentication schemes should be implemented to ensure that only the appropriate users can access data and resources. Only certain types of information should be stored on an intranet or extranet. Confidential, secret, and top secret information should not be hosted within an intranet or extranet. Finally, the deployment of a firewall(s) should be thoroughly planned out in advance. An example of a company that hosts an intranet and an extranet is shown in Figure 5-3. Note that data commuters from Company A can access the intranet because they work for the company. Also note that Company B can access the extranet, but not the intranet. In this example, the company (Company A) has created two DMZs, one for its intranet and one for its extranet. Of course, it is possible to set this up using only one DMZ, but the access control lists on the firewall and other devices would have to be planned and monitored more carefully. If possible, separating the data into two distinct physical locations will have several benefits, namely being more secure; although, it will cost more money to do so. This will all depend on the acceptable risk level of the organization and its budget!
Figure 5-3. Example of an Intranet and Extranet
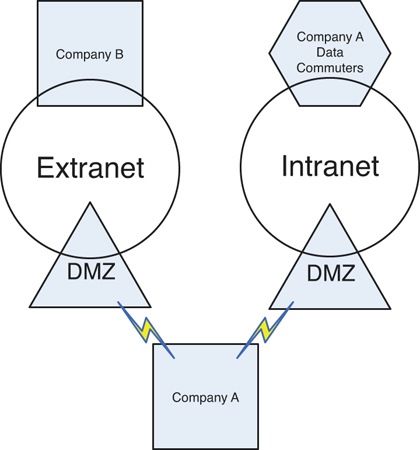
Network Access Control (NAC)
In this chapter, we have mentioned several types of networking technologies and design elements. But whichever you choose to use, they need to be controlled in a secure fashion. Network Access Control (NAC) does this by setting the rules by which connections to a network are governed. Computers attempting to connect to a network are denied access unless they comply with rules including levels of antivirus protection, system updates, and so on...effectively weeding out those who would perpetuate malicious attacks. The client computer will continue to be denied until it has been properly updated, which in some cases can be taken care of by the NAC solution automatically. This would often require some kind of pre-installed software (an agent) on the client computer, or the computer would be scanned by the NAC solution remotely.
Some companies offer hardware-based NAC solutions, for example the Nortel Secure Network Access Switch, whereas other organizations offer software-based NAC solutions such as FreeNAC (http://freenac.net/) or PacketFence (www.packetfence.org), which are both open source.
The IEEE 802.1X standard, known as port-based Network Access Control, or PNAC, is a basic form of NAC that enables the establishment of authenticated point-to-point connections, but NAC has grown to include software; 802.1X is now considered a subset of NAC. See the section “Authentication Models and Components” in Chapter 8 for more information about IEEE 802.1X.
Subnetting
Subnetting is the act of creating subnetworks logically through the manipulation of IP addresses. These subnetworks are distinct portions of a single IP network.
Subnetting is implemented for a few reasons:
• It increases security by compartmentalizing the network.
• It is a more efficient use of IP address space.
• It reduces broadcast traffic and collisions.
To illustrate the first bullet point, examine Figure 5-4. This shows a simple diagram of two subnets within the 192.168.50.0 network using the subnet mask 255.255.255.240; this would also be known as 192.168.50.0/28 in CIDR notation. You can see that the subnets are divided; this implies that traffic is isolated—it can not travel from one subnet to another without a route set up specifically for that purpose. So, computers within Subnet ID 2 can communicate with each other by default, and computers within Subnet ID 8 can communicate with each other, but computers on Subnet 2 cannot communicate with computer on Subnet 8, and vice versa.
Figure 5-4. Example of a Subnetted Network
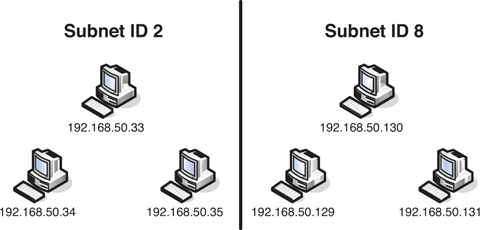
As a security precaution, using subnet zero is discouraged, and instead a network administrator should start with subnet 1, which in the preceding example would be 192.168.50.16. This avoids any possible confusion regarding the actual network number (192.168.50.0) and its subnets. If a network administrator were to use the first subnet and then inadvertently use a default subnet mask (such as 255.255.255.0) the hosts on that subnet would have access to more of the network than they should. This kind of mistake is common when using the first subnet and is the main reason it is discouraged.
When compartmentalizing the network through subnetting, an organization’s departments can be assigned to individual subnets, and varying degrees of security policies can be associated with each subnet. Incidents and attacks are normally isolated to the subnet that they occur on. Any router that makes the logical connections for subnets should have its firmware updated regularly, and traffic should be occasionally monitored to verify that it is isolated.
Note
The CompTIA Security+ objectives speak to securing subnetted IP networks and expect the examinee to be well versed with how to set up subnetworks; the “how” portion is covered in the Network+ exam. For more information about how to subnet as it applies to the CompTIA Network+ exam, purchase the CompTIA Network+ Video Mentor (by yours truly) and access my website:
Virtual Local Area Network (VLAN)
A VLAN is implemented to segment the network, reduce collisions, organize the network, boost performance, and hopefully, increase security. A device such as a switch can control the VLAN. Like subnetting, a VLAN compartmentalizes the network and can isolate traffic. But unlike subnetting, a VLAN can be set up in a physical manner; an example of this would be the port-based VLAN, as shown in Figure 5-5. In this example, each group of computers such as Classroom 1 have its own VLAN; however, computers in the VLAN can be located anywhere on the physical network. For example, Staff computers could be located in several physical areas in the building, but regardless of where they are located, they are associated with the Staff VLAN because of the physical port they connect to. Due to this, it is important to place physical network jacks in secure locations for VLANs that have access to confidential data.
Figure 5-5. Example of a VLAN
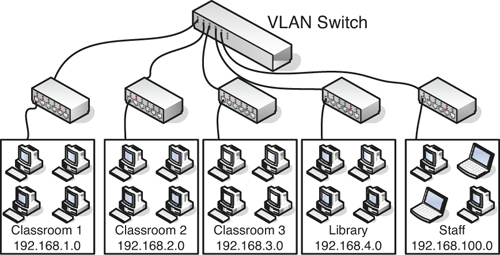
There are also logical types of VLANs, such as the protocol-based VLAN and the MAC address-based VLAN, that have a whole separate set of security precautions, but those precautions go beyond the scope of the CompTIA Security+ exam.
The most common standard associated with VLANs is IEEE 802.1Q; which modifies Ethernet frames by “tagging” them with the appropriate VLAN information, based on which VLAN the Ethernet frame should be directed to.
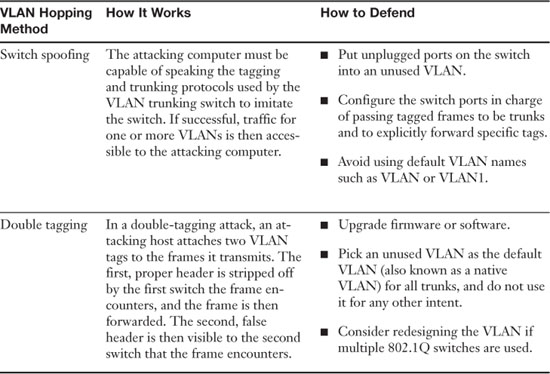
VLANs restrict access to network resources, but this can be bypassed through the use of VLAN hopping. VLAN hopping can be divided into two categories, as shown in Table 5-2.
Table 5-2. Types of VLAN Hopping
![]()
MAC flooding attacks can also be perpetuated on a VLAN, but because the flood of packets will be constrained to an individual VLAN, VLAN hopping will not be possible as a result of a MAC flood.
VLANs can also be the victims of ARP attacks, brute force attacks, spanning-tree attacks, and more of which we discuss in later chapters.
Telephony Devices
Telephony aims at providing voice communication for your users and requires various equipment to accomplish this goal. Older devices such as modems can be the victim of an attack, but nowadays computers are also heavily involved in telephony; this is known as computer telephony integration or CTI. What does this mean for you, the network security administrator? Well, for one thing, special telephones and servers require particular security, for a whole new level of attacks and ways of targeting this equipment. The telephone, regardless of what type, is still one of the primary communication methods and therefore needs to be up and running all the time.
Modems
In networking environments such as a network operations center (NOC) or server room, modems are still used by network administrators to connect to servers and networking equipment via dial-up lines. Often, this is a redundant, worst-case scenario implementation—sometimes, it is the default way for an admins to access and configure their networking equipment. In some cases, this is done without any authentication, and to make matters worse, sometimes admins use Telnet to configure their equipment. Of course, this is insecure, to say the least. A modem can be the victim of wardialing, which is the act of scanning telephone numbers by dialing them one at a time. Computers will usually pick up on the first ring, and the wardialing system will make a note of that and add that number to the list. Besides the obvious social annoyance this could create, a hacker would then use the list to attempt to access computer networks. Now think back to the system that has no authentication scheme in place!
So to protect modem connections, a network admin should 1) use the callback feature in the modem software and set it to call the person back at a preset phone number; 2) use some type of username/password authentication scheme and select only strong passwords because wardialers will most likely try at password guessing; and 3) use dial-up modems sparingly, only in secure locations, and try to keep the modem’s phone number secret. And by the way, a quick word on Telnet; it is not secure and should be substituted with SSH or another more secure way of configuring a remote device.
For the typical user who still uses a modem on a client computer, set the modem to not answer incoming calls, and be sure not to use any remote control software on the system that houses the modem. Finally, consider upgrading to a faster and more secure Internet access solution!
PBX Equipment
A private branch exchange (PBX) makes all of an organization’s internal phone connections and also provides connectivity to the PSTN. Originally, they were simple devices, but as time progressed they incorporated many new features and along the way became more of a security concern. For example, a hacker might attempt to exploit a PBX to obtain free long distance service or to employ social engineering to obtain information from people at the organization that owns the PBX. To secure a standard PBX, make sure it is in a secure room (server room, locked wiring closet, and so on); usually they should be mounted to the wall but could be fixed to the floor as well. Also, change passwords regularly, and only allow authorized maintenance; log any authorized maintenance done as well. PBX computers will often have a remote port (basically a built-in modem or other device) for monitoring and maintenance; ensure that this port is not exploited and that only authorized personnel know how to access it. Today’s PBX devices might act as servers on the network and might incorporate VoIP, which is also known as an IP-PBX.
VoIP
Voice over Internet Protocol (VoIP) is a broad term that deals with the transmission of voice data over IP networks such as the Internet. It is used by organizations and in homes. In an organization, IP phones can be the victim of attacks much like individual computers can. In addition, VoIP servers can be exploited the same way that other servers can; for example, by way of denial-of-service attacks. When securing a VoIP server, a network security administrator should implement many of the same precautions that they would make for more traditional servers, such as file servers and FTP servers. Some VoIP solutions, especially for home use, use the Session Initiation Protocol (SIP), which can be exploited by man-in-the-middle attacks. To help reduce risk, VoIP systems should be updated regularly and use encryption and an authentication scheme. We could talk about VoIP for days, but luckily for you, the exam requires that you have only a basic understanding of what VoIP is and how to protect it in a general sense. Most of the ways that you will mitigate risk on a VoIP system are the same as you would for other server systems, and these are covered in the following section.
Ports, Protocols, and Malicious Attacks
I can’t stress enough how important it is to secure a host’s ports and protocols. They are the doorways into an operating system. Think about it, an open doorway is a plain and simple invitation for disaster. And that disaster could be caused by one of many different types of malicious network attacks. The network security administrator must be ever vigilant in monitoring, auditing, and implementing updated defense mechanisms to combat malicious attacks. Understanding ports and protocols is the first step in this endeavor.
Ports and Protocols
Although many readers of this book are familiar with ports used by the network adapter and operating system, a review of them is necessary because they play a big role in securing hosts and will most definitely appear on the exam in some way, shape, or form.
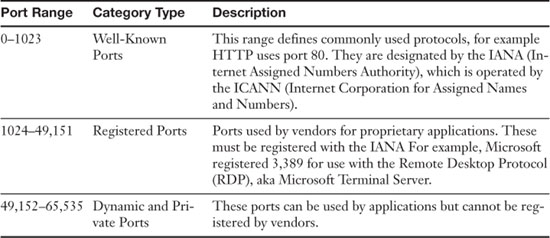
Ports act as logical communications endpoints for computers and are used on the Transport Layer of the OSI model by protocols such as the Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). There are 65,536 ports altogether, numbering between 0 and 65,535. The ports are divided into categories, as shown in Table 5-3.
Table 5-3. Port Ranges
You need to understand the difference between inbound and outbound ports as described in the following two bullets and as illustrated in Figure 5-6.
Figure 5-6. Inbound Versus Outbound Ports
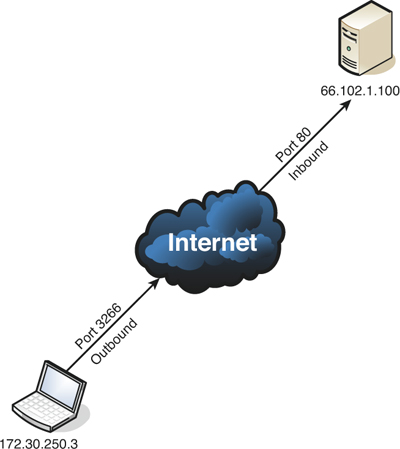
• Inbound ports—Used when another computer wants to connect to a service or application running on your computer. Servers primarily use inbound ports so that they can accept incoming connections and serve data. For example, in Figure 5-6, the server with the IP address 66.102.1.100 has inbound port 80 open to accept incoming web page requests.
• Outbound ports—Used when your computer wants to connect to a service or application running on another computer. Client computers primarily use outbound ports that are assigned dynamically by the operating system. For example, in Figure 5-6, the client computer with the IP address 172.30.250.3 has outbound port 3266 open to make a web page request to the server.
Note
For a refresher about TCP, UDP, and ports, see the short 5-minute video at the following link:
It’s the inbound ports that a network security administrator should be most concerned with. Web servers, FTP servers, database servers, and so on have specific inbound ports opened to the public. Any other unnecessary ports should be closed, and any open ports should be protected and monitored carefully. Although there are 1,024 well-known ports, for the exam you need to know only a handful of them, as shown in Table 5-4. Remember that these inbound port numbers relate to the applications, services, and protocols that run on a server.
Table 5-4. 23 Ports and Their Associated Protocols
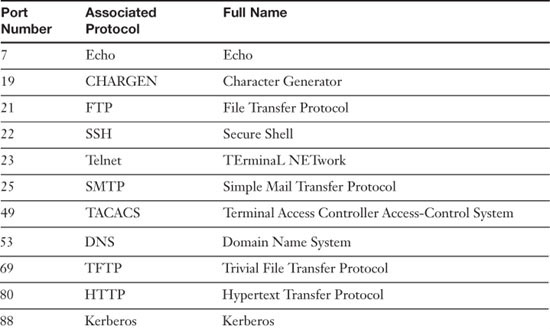
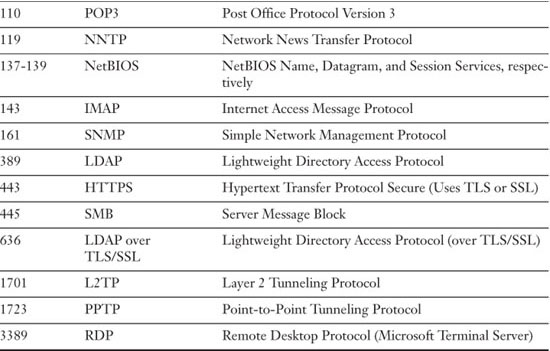
![]()
Note
You can find a complete list of ports and their corresponding protocols at the following link: www.iana.org/assignments/port-numbers.
The IP address of a computer and the port number it is sending or receiving on are combined together to form a network socket address. An example of this would be 66.102.1.100:80. That illustrates the IP address of the server in Figure 5-6 and the inbound port number accepting a connection from the client computer. Notice that the two are separated by a colon.
Figure 5-7 illustrates a few more examples of this within a Windows Vista client computer. It shows some of the results of a netstat –an command after FTP, WWW, and mail connections were made by the client to two separate servers. Examine the following figure and then read on.
Figure 5-7. IP Addresses and Ports
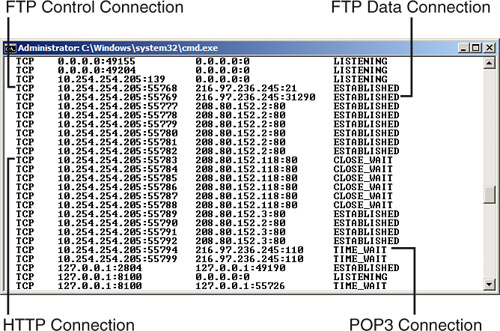
![]()
The first callout in the figure is FTP Control Connection. This happens when a user first connects to an FTP server with FTP client software. Notice that the local computer has the IP address 10.254.254.205 and uses the dynamically assigned outbound port 55768 to connect to the FTP server. The remote computer on the other hand has the IP address 216.97.236.245 and uses inbound port 21 to accept the connection. Keep in mind that this is only the initial connection and login to the FTP server. Subsequent data connections are normally done on the server side via dynamically assigned ports. For example, the second callout, FTP Data Connection, occurred when the client downloaded a file. It is a separate session in which the client used the dynamically assigned port number 55769. In reality, this isn’t quite dynamic anymore; the client operating system is simply selecting the next port number available; afterward, a subsequent and concurrent download would probably use port 55770. The server, on the other hand used the dynamically assigned port number 31290. Many FTP servers randomly select a different inbound port to use for each data connection to increase security. However, some FTP connections still use the original port 20 for data connections, which is not as secure, not only because it is well known, but also because it is static. To secure FTP communications, consider using software that enables dynamically assigned ports during data transfers; for example, Pure-FTPd (www.pureftpd.org) on the server-side and FileZilla (http://filezilla-project.org/) on the client-side. If your FTP server enables it, you can also consider IPv6 connections, and as always, be sure to use strong, complex passwords. (I don’t mean to sound like a broken record!) The third callout shows an HTTP connection. Note that this is being made to a different server (208.80.152.118) and uses port 80. And finally, a POP3 connection that was previously made to the same server IP enabled the FTP connection, but note that the port number reflects POP3—it shows port number 110. These are just a few examples of many that occur between clients and servers all the time. Try making some connections to various servers from your client computer and view those sessions in the command-line.
Aside from servers, ports also become particularly important on router/firewall devices. These devices operate on the implicit deny concept, which means they will deny all traffic unless a rule is made to open the port associated with the type of traffic desired to be let through. We talk more about firewalls in Chapter 6.
You need to scan your servers, routers, and firewall devices to discern which ports are open. This can be done with the aforementioned netstat command or with an application such as Nmap (http://nmap.org/) or with an online scanner from a website such as GRC’s ShieldsUP! (www.grc.com). The most effective way is with an actual scanning application which we show in depth in Chapter 10. However, there is a basic lab on port scanning referenced at the end of this chapter in the “Work Through Hands-On Scenarios” section.
Afterward, unnecessary ports should be closed. This can be done in a few ways:
• Within the operating system GUI—For example, in Windows, open the Computer Management console. Then go to Services and Applications > Services. Right-click the appropriate service and select Properties. From here the service can be stopped and disabled.
• Within the CLI—For example, a service can be stopped in Windows by using the net stop service command. A service can be disabled with the SC command. In Red Hat Linux a service can be stopped with the command # service httpd stop for example, and the same service can be disabled with the command # chkconfig httpd off. (Different versions of Linux have varying commands.)
• Within a firewall—Simply setting up a firewall normally closes and shields all ports by default. But you might have a service that was used previously on a server, and therefore a rule might have been created on the firewall to enable traffic through on that port. Within the firewall software, the rule can be deleted, disabled, or modified as needed.
Unnecessary ports also include ports associated with nonessential protocols. For example, TFTP (port 69) is usually considered a nonessential protocol, as is Finger (port 79). Telnet (port 23) is insecure and as such is also considered nonessential. However, the list of nonessential protocols will differ from one organization to the next. Always rescan the host to make sure that the ports are indeed closed. Then, make the necessary changes in documentation. Depending on company policy, you might need to follow change management procedures before making modifications to ports and services. For more information on this type of documentation and procedures, see Chapter 15, “Policies, Procedures, and People.”
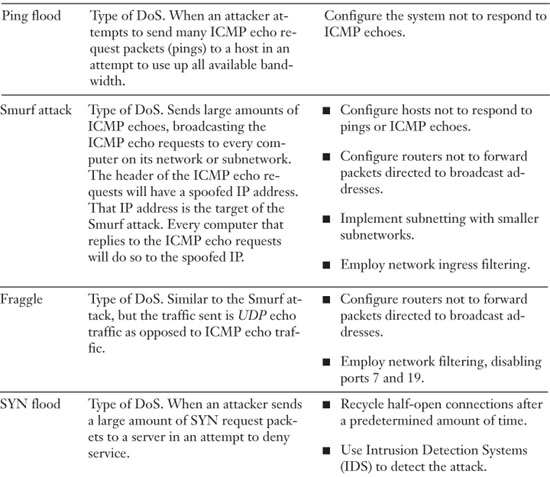
Malicious Network Attacks
There are many types of network attacks. Some are similar to others, making it difficult to differentiate between them. Because of this, I’ve listed simple definitions and examples of each, plus mitigating techniques, and summarized them at the end of this section.
DoS
Denial of Service (DoS) is a broad term given to many different types of network attacks that attempt to make computer resources unavailable. Generally this will be done to servers but could also be perpetuated against routers and other hosts. DoS attacks can be implemented in several ways as listed here.
• Flood attacks—Deals with sending many packets to a single server or other host in an attempt to disable it. There are a few ways to accomplish this including:
• Ping flood—Also known as an ICMP flood attack, is when an attacker attempts to send many ICMP echo request packets (pings) to a host in an attempt to use up all available bandwidth. This will work only if the attacker has more bandwidth available than the target. To deter this attack, configure the system not to respond to ICMP echoes. You might have noticed that several years ago, you could ping large companies’ websites and get replies. But after Ping floods became prevalent, a lot of these companies disabled ICMP echo replies. For example, try opening the command prompt and typing pingmicrosoft.com (Internet connection required). It should result in Request Timed Out, which tells you that Microsoft has disabled this.
• Smurf attack—Also sends large amounts of ICMP echoes, but this particular attack goes a bit further. The attacking computer broadcasts the ICMP echo requests to every computer on its network or subnetwork. In addition, in the header of the ICMP echo requests will have a spoofed IP address. That IP address is the target of the Smurf attack. Every computer that replies to the ICMP echo requests will do so to the spoofed IP. Don’t forget that the original attack was broadcast, so, the more systems on the network (or subnetwork), the more echo replies that are sent to the target computer. There are several defenses for this attack, including configuring hosts not to respond to pings or ICMP echoes, configuring routers not to forward packets directed to broadcast addresses, implement subnetting with smaller subnetworks, and employing network ingress filtering in an attempt to drop packets that contain forged or spoofed IP addresses (especially addresses on other networks). These defenses have enabled most network administrators to make their networks immune to Smurf and other ICMP-based attacks. The attack can be automated and modified using the exploit code known as Smurf.c.
• Fraggle—Similar to the Smurf attack, but the traffic sent is UDP echoes. The traffic is directed to port 7 (Echo) and port 19 (CHARGEN). To protect against this attack, again, configure routers not to forward packets directed to broadcast addresses, employ network filtering, and disable ports 7 and 19. These ports are not normally used in most networks. The attack can be automated and modified using the exploit code known as Fraggle.c.
Note
A similar attack is known as a UDP flood attack, which also uses the connectionless User Datagram Protocol. It is enticing to attackers because it does not require a synchronization process.
• SYN flood—Occurs when an attacker sends a large amount of SYN request packets to a server in an attempt to deny service. Remember that in the TCP three-way handshake, a synchronization (SYN) packet is sent from the client to the server, then a SYN/ACK packet is sent from the server to the client, and finally, an acknowledgment (ACK) packet is sent from the client to the server. Attackers attempting a SYN flood will either simply skip sending the ACK or will spoof the source IP address in the original SYN. Either way, the server will never receive the final ACK packet. This ends up being a half-open connection. By doing this multiple times, an attacker seeks to use up all connection-oriented resources so that no real connections can be made. A couple ways to defend against this are to recycle half-open connections after a predetermined amount of time and use Intrusion Detection Systems (IDS) to detect the attack. You can find more information about IDS in Chapter 6 and more information about SYN flood attacks and mitigation techniques at the following link:
http://tools.ietf.org/html/rfc4987
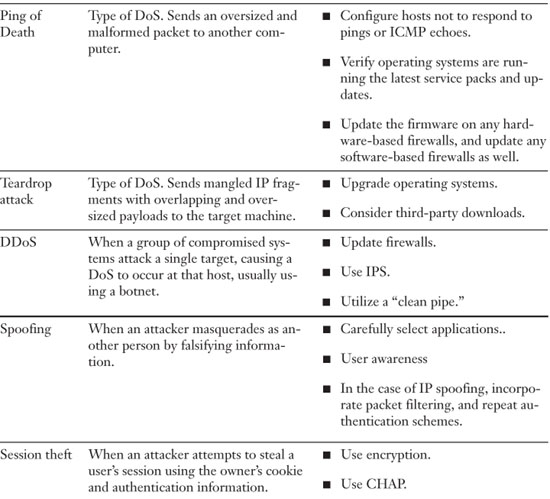
• Ping of Death—POD is an attack that sends an oversized and malformed packet to another computer. It is an older attack; most computer operating systems today will not be affected by it, and most firewalls will block it before it enters a network. It entails sending a packet that is larger than 65,535 bytes in length, which according to RFC 791 is the largest size packet that can be used on a TCP/IP network without fragmentation. If a packet is sent that is larger than 65,535 bytes, it might overflow the target system’s memory buffers, which can cause several types of problems including system crashes. Windows computers do not allow ping sizes beyond 65,500 bytes. For example, ping destination –l 65500 will work, but ping destination –l 66000 will not work. However, on some systems, this maximum limitation can be hacked in the Registry, and there are also third-party applications that can send these “larger than life” packets. To protect against this type of attack, configure hosts not to respond to pings or ICMP echoes, make sure that operating systems run the latest service packs and updates, update the firmware on any hardware-based firewalls, and update any software-based firewalls as well. POD can be combined with a ping flood, but because most firewalls will block one or more PODs, it doesn’t make much sense to attempt the attack, so most hackers will opt for some other sort of packet flooding nowadays. This was one of the first DoS attacks. It and other attacks such as Nuke and WinNuke are considered to be deprecated.
• Teardrop attack—Sends mangled IP fragments with overlapping and over-sized payloads to the target machine. This can crash and reboot various operating systems due to a bug in their TCP/IP fragmentation re-assembly code. For example, Windows 7 and Vista are particularly susceptible to Teardrop attacks. Linux and Windows systems should be upgraded to protect from this attack. There are also software downloads available on the Internet for Teardrop detection.
• Permanent DoS attack—Generally consists of an attacker exploiting security flaws in routers and other networking hardware by flashing the firmware of the device and replacing it with a modified image. This is also known as Phlashing, or PDoS.
• Fork bomb—Works by quickly creating a large number of processes to saturate the available processing space in the computer’s operating system. Running processes can be “forked” to create other running processes, and so on. They are not considered viruses or worms but are known as “wabbits” or “bacteria” because they might self-replicate but do not infect programs or use the network to spread.
There are other types of DoS attacks, but that should suffice for now. Keep in mind that new DoS attacks are always being dreamed up (and implemented), so as a network security administrator, you need to be ready for new attacks and prepared to exercise new mitigation techniques.
DDoS
A distributed denial-of-service (DDoS) attack is when a group of compromised systems attack a single target, causing a DoS to occur at that host. A DDoS attack often utilizes a botnet. The unsuspecting computers in the botnet that act as attackers are known as zombies. A hacker starts the DDoS attack by exploiting a single vulnerability in a computer system and making that computer the zombie master, or DDoS master. The master system communicates with the other systems in the botnet. The attacker often loads malicious software on many computers (zombies). The attacker can launch a flood of attacks by all zombies in the botnet with a single command.
DoS and DDoS attacks are difficult to defend against. Other than the methods mentioned previously in the DoS section, these attacks can be prevented to some extent by updated stateful firewalls, switches, and routers with access control lists, intrusion-prevention systems (IPS), and proactive testing. Several companies offer products that simulate DoS and DDoS attacks. By creating a test server and assessing its vulnerabilities with simulated DoS tests, you can find holes in the security of your server before you take it live. A quick search for DoS testing shows a few of these simulation test companies. An organization could also opt for a “clean pipe,” which attempts to weed out DDoS attacks, among other attacks. This solution is offered as a service by Verisign and other companies. Finally, if you do realize that a DDoS attack is being carried out on your network, call your ISP and request that this traffic be redirected.
Spoofing
A spoofing attack is when an attacker masquerades as another person by falsifying information. There are several types of spoofing attacks. The man-in-the-middle attack is not only a form of session hijacking, but it is also considered spoofing. Internet protocols and their associated applications can also be spoofed, especially if the protocol were poorly programmed in the first place. Web pages can also be spoofed in an attempt to fool users into thinking they are logging into a trusted website; this is known as URL spoofing and is used when attackers are fraudulently phishing for information such as usernames, passwords, credit card information, and identities. Phishing can also be done through a false e-mail that looks like it comes from a valid source. Quite often, this will be combined with e-mail address spoofing, which hides or disguises the sender information. Defending against these types of spoofing attacks is difficult, but by carefully selecting and updating applications that your organization uses, and through user awareness, spoofing can be held down to a minimum and when necessary ignored.
Just about anything can be spoofed if enough work is put into it, and IP addresses are no exception. IP address spoofing is when IP packets are created with a forged source IP address in the header. This conceals where the packets originated from. Packet filtering and sessions that repeat authentication can defend against this type of spoofing. Also, updating OSs and firmware and using newer OSs and network devices helps to mitigate risks involved with IP spoofing. IP spoofing is commonly used in DoS attacks as mentioned earlier and is also common in TCP/IP hijacking, which we discuss more in the next section.
Session Hijacking
Session hijacking is the exploitation of a computer session in an attempt to gain unauthorized access to data, services, or other resources on a computer. A few types of session hijacks can occur:
• Session theft—Can be accomplished by stealing a cookie from the client computer, which authenticates the client computer to a server. This is done at the Application Layer, and the cookies involved are often based off of their corresponding web applications (such as WWW sessions). This can be combated by using encryption and long random numbers for the session key, and regeneration of the session after a successful login. The Challenge Handshake Authentication Protocol (CHAP) can also be employed to require clients to periodically re-authenticate. However, session hijacking can also occur at the Network Layer, for example TCP/IP hijacking.
• TCP/IP hijacking—A common type of session hijacking, due to its popularity among hackers. It is when a hacker takes over a TCP session between two computers without the need of a cookie or any other type of host access. Because most communications’ authentication occurs only at the beginning of a standard TCP session, a hacker can attempt to gain access to a client computer anytime after the session begins. One way would be to spoof the client computer’s IP address, then find out what was the last packet sequence number sent to the server, and then inject data into the session before the client sends another packet of information to the server. Remember the three-way handshake that occurs at the beginning of a session; this is the only authentication that occurs during the session. A synchronization (SYN) packet is sent by the client to the server, then a SYN/ACK packet is sent by the server to the client, and finally, an acknowledgment (ACK) packet is sent by the client to the server. An attacker can jump in any time after this process and attempt to steal the session by injecting data into the data stream. This is the more difficult part; the attacker might need to perform a DoS attack on the client to stop it from sending anymore packets so that the packet sequence number doesn’t increase. In contrast, UDP sessions are easier to hijack because no packet sequence numbers exist. Targets for this type of attack include online games such as Quake and Halo, and also DNS queries.
To mitigate the risk of TCP/IP hijacking, employ encrypted transport protocols such as SSL, IPSec, and SSH. For more information about these encryption protocols, see Chapter 13, “PKI and Encryption Protocols.”
• Blind hijacking—When an attacker blindly injects data into a data stream without being able to see whether the injection was successful. The attacker could be attempting to create a new administrator account or gain access to one.
• Man-in-the-middle (MITM)—Attacks intercept all data between a client and a server. It is a type of active interception. If successful, all communications now go through the MITM attacking computer. The attacking computer can at this point modify the data and send it to the receiving computer. This type of eavesdropping is only successful when the attacker can properly impersonate each endpoint. Cryptographic protocols such as Secure Socket Layer (SSL) and Transport Layer Security (TLS) address MITM attacks by using a mutually trusted third-party certification authority. These public key infrastructures (PKI) should use strong mutual authentication such as secret keys and strong passwords. For more information about PKI, see Chapter 13.
On a semirelated note, cross-site scripting is a type of vulnerability found in web applications that is used with session hijacking. The attacker manipulates a client computer into executing code that is considered trusted as if it came from the server the client was connected to. In this way, the hacker can acquire the client computer’s session cookie (enabling them to steal sensitive information) or exploit the computer in other ways.
Replay
A replay attack is a network attack in which a valid data transmission is maliciously or fraudulently repeated or delayed. An attacker might use a packet sniffer to intercept data and retransmit it later. This differs from session hijacking in that the original session is simply intercepted and analyzed for later use. In this way a hacker can impersonate the entity that originally sent the data. For example, if customers were to log in to a banking website with their credentials while an attacker was watching, the attacker could possibly sniff out the packets that include the usernames and passwords and then possibly connect with those credentials later on. Of course, if the bank uses SSL or TLS to secure login sessions, then the hacker would have to decrypt the data as well, which could prove more difficult. An organization can defend against this attack in several ways. The first is to use session tokens that are transmitted to people the first time they attempt to connect, and identify them subsequently. They are handed out randomly so that attackers cannot guess at token numbers. The second way is to implement timestamping and synchronization as in a Kerberos environment. A third way would be to use a timestamped nonce that is a random number issued by an authentication protocol that can only be used one time. We talk more about SSL, TLS, Kerberos, and other cryptographic solutions in Chapter 13.
Note
A replay attack should not be confused with SMTP relay, which is when one server forwards e-mail to other e-mail servers.
Null Sessions
A null session is a connection to the Windows interprocess communications share (IPC$). The null session attack is a type of exploit that makes unauthenticated NetBIOS connections to a target computer. The attack uses ports 139 and 445, which are the NetBIOS session port and the Server Message Block port respectively. If successful, an attacker could find user IDs, share names, and various settings and could possibly gain access to files, folders, and other resources. An example of the initial code an attacker might use is
net use \IP addressipc$ "" /U: ""
Afterward, the attacker might use a program such as enum.exe or something similar to extract information from the remote computer, such as usernames. Finally, an attacker might use a brute force attack in an attempt at cracking passwords and gaining more access.
To protect against this computers should be updated as soon as possible, for example Windows XP should be upgraded to service pack 3. However, the best way to defend against this attack is to filter out traffic on ports 139 and 445, with a firewall or a host-based intrusion prevention system. When a firewall is enabled, ports 139 and 445 will not appear to exist.
DNS Poisoning and Other DNS Attacks
DNS poisoning or DNS cache poisoning is the modification of name resolution information that should be in a DNS server’s cache. It is done to redirect client computers to incorrect websites. This can happen through improper software design, misconfiguration of name servers, and maliciously designed scenarios exploiting the traditionally open architecture of the DNS system. Let’s say a client wants to go to www.comptia.org. That client’s DNS server will have a cache of information about domain names and their corresponding IP addresses. If CompTIA’s site were visited in the recent past by any client accessing the DNS server, its domain name and IP should be in the DNS server’s cache. If the cache is poisoned, it could be modified in such a way to redirect requests for www.comptia.org to a different IP address and website. This other site could be a phishing site or could be malicious in some other way. This attack can be countered by using Transport Layer Security (TLS) and digital signatures or by using Secure DNS (DNSSEC) that uses encrypted electronic signatures when passing DNS information, and finally, by patching the DNS server.
Unauthorized zone transfers are another bane to DNS servers. Zone transfers replicate the database that contains DNS data. If a zone transfer is initiated, say through a reconnaissance attack, server name and IP address information can be stolen, resulting in the attacker accessing various hosts by IP address. To defend against this, zone transfers should be restricted and audited in an attempt to eliminate unauthorized zone transfers and to identify anyone who tries to exploit the DNS server in this manner. Vigilant logging of the DNS server and the regular checking of DNS records can help detect unauthorized zone transfers.
A Windows computer’s hosts file can also be the victim of attack. The hosts file is used on a local computer to translate or resolve hostnames to IP addresses. This is the predecessor to DNS but can still be used on local computers if DNS or another name service is not available. Attackers may attempt to hijack the hosts file in an attempt to alter or poison it or to try to have the client bypass DNS altogether. The best defense for this is to modify the computer’s hosts file permissions to read-only. It is located at the following path: \%systemroot%System32driversetc.
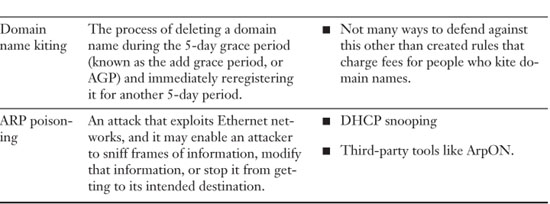
Although it is less of an actual attack, domain name kiting or simply domain kiting is the process of deleting a domain name during the 5-day grace period (known as the add grace period or AGP) and immediately reregistering it for another 5-day period. This process is repeated any number of times with the end result of having the domain registered without ever actually paying for it. It is a malicious attack on the entire domain name system by misusing the domain tasting grace period. The result is that a legitimate company or organization quite often cannot secure the domain name of its choice.
As you can see, the DNS server can be the victim of many attacks due to its visibility on the Internet. It should be closely monitored at all times. Other highly visible servers such as web servers and mail servers should be likewise monitored, audited, and patched as soon as updates are available.
ARP Poisoning
The Address Resolution Protocol (ARP) resolves MAC addresses to IP addresses. Any resolutions that occur over a set amount of time are stored in the ARP table. The ARP table can be poisoned or spoofed. ARP poisoning is an attack that exploits Ethernet networks, and it may enable an attacker to sniff frames of information, modify that information, or stop it from getting to its intended destination. The spoofed frames of data will contain a false source MAC address, which will deceive other devices on the network. The idea behind this is to associate the attackers MAC address with an IP address of another device, such as a default gateway or router so that any traffic that would normally go to the gateway would end up at the attacker’s computer. The attacker could then perpetuate a man-in-the-middle attack, or a denial-of-service attack, in addition to MAC flooding. Some of the defenses for ARP poisoning include DHCP snooping and an open source program called ArpON (http://arpon.sourceforge.net/).
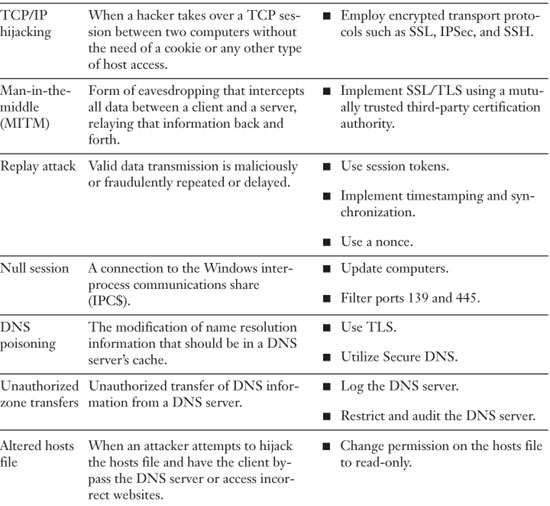
Summary of Network Attacks
Table 5-5 lists important network attacks and mitigation techniques.
Table 5-5. Summary of Important Network Attacks and Mitigation Techniques to Know for the Exam
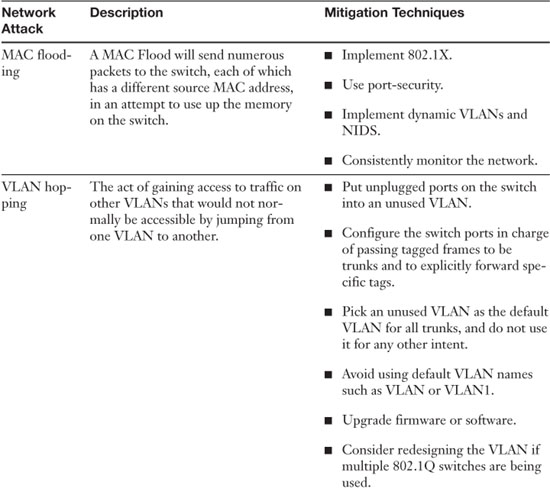
![]()
Exam Preparation Tasks: Review Key Topics
Review the most important topics in the chapter, noted with the Key Topics icon in the outer margin of the page. Table 5-6 lists a reference of these key topics and the page numbers on which each is found.
![]()
Table 5-6. Key Topics for Chapter 5
Complete Tables and Lists from Memory
Print a copy of Appendix A, “Memory Tables,” (found on the DVD), or at least the section for this chapter, and complete the tables and lists from memory. Appendix B, “Memory Tables Answer Key,” also on the DVD, includes completed tables and lists to check your work.
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
Distributed Denial of Service,
Hands-On Labs
Complete the following written step-by-step scenarios. After you finish (or if you do not have adequate equipment to complete the scenario), watch the corresponding video solutions on the DVD.
If you have additional questions, feel free to post them at my website: www.davidlprowse.com in the Ask Dave forum. (Free registration is required to post on the website.)
Equipment Needed
• Two Windows computers, at least one with Internet access.
• Web browser: Internet Explorer version 6 and higher or Firefox are recommended. This will be used to access the ShieldsUP! Program at www.grc.com and to download Nmap.
• Nmap software: This can be downloaded from www.nmap.com.
Lab 5-1: Port Scanning Basics
This lab demonstrates how to scan the ports of a computer with the Nmap program and with the Internet utility ShieldsUP! The steps are as follows:
Step 1. Download and install the command-line version of the Nmap program from http://nmap.org/download.html.
Step 2. Extract the contents to a folder of your choice. In the video, we use the nmap folder.
Step 3. Write down the IP address of a Windows host on your network.
Step 4. Scan the ports of that host with the –sS parameter; for example,
nmap –sS 172.29.250.200
Step 5. If there are nonessential ports open, turn off their corresponding unnecessary services, such as FTP, HTTP, or Telnet. This can be done in a variety of places including Computer Management. If there are no services that you want to turn off, enable one (such as Telnet), then rescan the ports with Nmap (to show that the service is running), turn off the service, and move on to the next step.
Step 6. Scan the ports of that host a second time, again with the –sS parameter. This time you are verifying that the services are turned off by identifying that the corresponding ports are closed.
Step 7. Scan the ports of a 4-port SOHO router/firewall or a computer with a firewall running. Use the –P0 parameter. For example:
nmap –P0 65.43.18.1
This may take up to five minutes. It will verify whether the firewall is running properly by displaying that all the ports are filtered.
Step 8. With a web browser, connect to www.grc.com.
Step 9. Click the ShieldsUP!! Picture.
Step 10. Scroll down and click the ShieldsUP! Link. (This is a necessary second step.)
Step 11. Click the Proceed button.
Step 12. Select the Common Ports scan. This initiates a scan of the computer or device that is displayed to the Internet. If you access the Internet through a router/firewall, this will be the device scanned. If your computer connects directly to the Internet, the computer will be scanned.
Step 13. Make note of the results. It should show the public IP that was scanned. Then it lists the ports that were scanned and their status. The desired result for all ports listed is Stealth, all the way down the line for each of the listed ports. If there are Open or Closed ports, you should check to make sure that the firewall is enabled and operating properly.
Step 14. Try a few other scans, such as All Service Ports, or File Sharing.
Watch the solution video in the “Hands-On Scenarios” section of the DVD.
View Recommended Resources
For readers who wish to brush up on their networking topics:
• Prowse, David L. CompTIA Network+ Video Mentor, First Edition. Que. 2009.
• Harwood, Mike. CompTIA Network+ Cert Guide. 2010.
• Comer, Douglas. Computer Networks and Internets (Fifth Edition). Prentice Hall. 2008.
• Video: OSI Model Primer: www.davidlprowse.com/forums/showthread.php?t=1556
• Internetworking Basics: www.cisco.com/en/US/docs/internetworking/technology/handbook/Intro-to-Internet.html
• Video: TCP, UDP, and Ports Refresher: www.davidlprowse.com/forums/showthread.php?t=1614
Port Numbers: www.iana.org/assignments/port-numbers
FreeNAC: http://freenac.net/
Pure-FTPd: www.pureftpd.org
FileZilla: http://filezilla-project.org/
Nmap: http://nmap.org/
GRC’s ShieldsUP!: www.grc.com
More information on SYN Flood attacks, see tools.ietf.org/html/rfc4987.
Answer Review Questions
Answer the following review questions. You can find the answers at the end of this chapter.
1. Which of the following would you set up in a router?
A. DMZ
B. DOS
C. OSI
D. ARP
2. Which of the following is an example of a nonessential protocol?
A. DNS
B. ARP
C. DMZ
D. TFTP
3. A person attempts to access a server during a zone transfer to get access to a zone file. What type of server are they trying to manipulate?
A. Proxy server
B. DNS server
C. File server
D. Web server
4. Which of the following is a private IP address?
A. 11.16.0.1
B. 127.0.0.1
D. 208.0.0.1
5. Which of these hides an entire network of IP addresses?
A. SPI
B. NAT
C. SSH
D. FTP
6. Which one of the following can monitor and protect a DNS server?
A. Ping the DNS server.
B. Block port 53 on the firewall.
C. Purge PTR records daily.
D. Check DNS records regularly.
7. Which TCP port does LDAP use?
A. 389
B. 80
C. 443
D. 143
8. From the list of ports select two that are used for e-mail. (Select the two best answers.)
A. 110
B. 3389
C. 143
D. 389
9. Which port number does the domain name system use?
A. 53
B. 80
C. 110
D. 88
10. Which of the following statements best describes a static NAT?
A. Static NAT uses a one-to-one mapping.
B. Static NAT uses a many-to-many mapping.
C. Static NAT uses a one-to-many mapping.
D. Static NAT uses a many-to-one mapping.
11. John needs to install a web server that can offer SSL-based encryption. Which of the following ports is required for SSL transactions?
A. Port 80 inbound
B. Port 80 outbound
C. Port 443 inbound
D. Port 443 outbound
12. If a person takes control of a session between a server and a client, it is known as what type of attack?
A. DDoS
B. Smurf
C. Session hijacking
D. Malicious software
13. Making data appear as if it is coming from somewhere other than its original source is known as what?
A. Hacking
B. Phishing
C. Cracking
D. Spoofing
14. Which of the following enables a hacker to float a domain registration for a maximum of 5 days?
A. Kiting
B. DNS poisoning
C. Domain hijacking
D. Spoofing
15. What is the best definition for ARP?
A. Resolves IP addresses to DNS names
B. Resolves IP addresses to host names
C. Resolves IP addresses to MAC addresses
D. Resolves IP addresses to DNS addresses
16. Which of the following should be placed between the LAN and the Internet?
A. DMZ
B. HIDS
C. Domain controller
D. Extranet
17. You have three e-mail servers. What is it called when one server forwards e-mail to another?
A. SMTP relay
B. Buffer overflows
C. POP3
D. Cookies
18. You want to reduce network traffic on a particular network segment to limit the amount of user visibility. Which of the following is the best device to use in this scenario?
A. Switch
B. Hub
C. Router
D. Firewall
19. A coworker goes to a website but notices that the browser brings her to a different website and that the URL has changed. What type of attack is this?
A. DNS poisoning
B. Denial of service
C. Buffer overflow
D. ARP poisoning
20. Which of the following misuses the transmission control protocol handshake process?
A. Man-in-the-middle attack
B. SYN attack
C. WPA attack
D. Replay attack
21. For a remote tech to log in to a user’s computer in another state, what inbound port must be open on the user’s computer?
A. 21
B. 389
C. 3389
D. 8080
22. A DDoS attack can be best defined as what?
A. Privilege escalation
B. Multiple computers attacking a single server
C. A computer placed between a sender and receiver to capture data
D. Overhearing parts of a conversation
23. When users in your company attempt to access a particular website, the attempts are redirected to a spoofed website. What are two possible reasons for this?
A. DoS
B. DNS poisoning
C. Modified hosts file
D. Domain name kiting
24. What kind of attack is it when the packets sent do not require a synchronization process and are not connection-oriented?
A. Man-in-the-middle
B. TCP/IP hijacking
C. UDP attack
D. ICMP flood
25. How many of the TCP/IP ports can be attacked?
A. 1,024 ports
B. 65,535
C. 256
D. 16,777,216
26. Which of the following attacks is a type of DoS attack that sends large amounts of UDP echoes to port 7 and 19?
A. Teardrop
B. IP spoofing
D. Replay
27. Don must configure his firewall to support TACACS. Which port(s) should he open on the firewall?
A. Port 53
B. Port 49
C. Port 161
D. Port 22
28. Which of the following ports is used by Kerberos by default?
A. 21
B. 80
C. 88
D. 443
Answers and Explanations
1. A. A DMZ, or demilitarized zone, can be set up on a router to create a sort of safe haven for servers. It is neither the LAN nor the Internet, but instead, a location in between the two.
2. D. The Trivial File Transfer Protocol (TFTP) is a simpler version of FTP that uses a small amount of memory. It is generally considered to be a nonessential protocol. The Domain Name System service (or DNS service) is required for Internet access and on Microsoft domains. The Address Resolution Protocol (ARP) is necessary in Ethernets that use TCP/IP. And a demilitarized zone (DMZ) is not a protocol but more of a network design element.
3. B. DNS servers are the only types of servers listed that do zone transfers. The purpose of accessing the zone file is to find out what hosts are on the network.
4. C. 172.16.0.1 is the only address listed that is private. The private assigned ranges can be seen in Table 5-1 earlier in the chapter. 11.16.0.1 is a public IP address, as is 208.0.0.1. 127.0.0.1 is the loopback address.
5. B. Network Address Translation hides an entire network of IP Addresses. SPI, or Stateful Packet Inspection, is the other type of firewall that today’s SOHO routers incorporate.
6. D. By checking a DNS server’s records regularly, a security admin can monitor and protect it. Blocking port 53 on a firewall might protect it (it also might make it inaccessible depending on the network configuration) but won’t enable you to monitor it. Pinging the server can simply tell you whether the server is alive. Purging pointer records (PTR) cannot help to secure or monitor the server.
7. A. The Lightweight Directory Access Protocol (LDAP) uses port TCP 389. Port 80 is used by HTTP. Port 443 is used by HTTPS. Port 143 is used by IMAP.
8. A and C. POP3 uses port 110; IMAP uses port 143; 3389 is used by the remote desktop protocol; and 389 is used by LDAP.
9. A. The domain name system or DNS uses port 53. Port 80 is used by HTTP; port 110 is used by POP3; and port 88 is used by Kerberos.
10. A. Static network address translation will normally use a one-to-one mapping when dealing with IP addresses.
11. C. For clients to connect to the server via SSL, the server must have inbound port 443 open. The outbound ports on the server are of little consequence for this concept, and inbound port 80 is used by HTTP.
12. C. Session hijacking (or TCP/IP hijacking) is when an unwanted mediator takes control of the session between a client and a server (for example, an FTP or HTTP session).
13. D. Spoofing is when a malicious user makes data or e-mail appears to be coming from somewhere else.
14. A. Kiting is the practice of monopolizing domain names without paying for them. Newly registered domain names can be canceled with a full refund during an initial 5-day window known as an AGP, or add grace period.
15. C. The address resolution protocol, or ARP, resolves IP addresses to MAC addresses. DNS resolves from IP addresses to hostnames, word domain names, and vice versa. RARP resolves MAC addresses to IP addresses.
16. A. A demilitarized zone, or DMZ, can be placed between the LAN and the Internet; this is known as a back-to-back perimeter configuration. In some cases, it will be part of a 3-leg firewall scheme. Host-based intrusion detection systems are placed on an individual computer, usually within the LAN. Domain controllers should be protected and are normally on the LAN as well. An extranet can include parts of the Internet and parts of one or more LANs; normally it connects two companies utilizing the power of the Internet.
17. A. The SMTP relay is when one server forwards e-mail to other e-mail servers. Buffer overflows are attacks that can be perpetuated on web pages. POP3 is another type of e-mail protocol, and cookies are small text files stored on the client computer that remember information about that computer’s session with a website.
18. A. A switch can reduce network traffic on a particular network segment. It does this by keeping a table of information about computers on that segment. Instead of broadcasting information to all ports of the switch, the switch selectively chooses where the information goes.
19. A. DNS poisoning can occur at a DNS server and can affect all clients on the network. It can also occur at an individual computer. Another possibility is that spyware has compromised the browser. A denial of service is a single attack that attempts to stop a server from functioning. A buffer overflow is an attack that, for example, could be perpetuated on a web page. ARP poisoning is the poisoning of an ARP table, creating confusion when it comes to IP address-to-MAC address resolutions.
20. B. A synchronize (SYN) attack misuses the TCP three-way handshake process. The idea behind this is to overload servers and deny access to users.
21. C. Port 3389 must be open on the inbound side of the user’s computer to enable a remote tech to log in remotely and take control of that computer. Port 21 is the port used by FTP, and 389 is used by LDAP. 8080 is another port used by web browsers that takes the place of port 80.
22. B. When multiple computers attack a single server, it is known as a Distributed Denial of Service attack, or DDoS. Privilege escalation is when a person that is not normally authorized to a server manages to get administrative permissions to resources. If a computer is placed between a sender and receiver, it is known as a man-in-the-middle attack. Overhearing parts of a conversation is known as eavesdropping.
23. B and C. DNS poisoning and a DNS server’s modified hosts files are possible causes for why a person would be redirected to a spoofed website. DoS, or a Denial of Service, is when a computer attempts to attack a server to stop it from functioning. Domain name kiting is when a person renews and cancels domains within 5-day periods.
24. C. User Datagram Protocol (UDP) attacks, or UDP flood attacks, are DoS attacks that use a computer to send a large number of UDP packets to a remote host. The remote host will reply to each of these with an ICMP Destination Unreachable packet, which ultimately, makes it inaccessible to clients.
25. B. The best answer to this question is 65,535. The Internet Assigned Numbers Authority (IANA) list of ports starts at 0 and ends at 65,535. Although this equals 65,536 ports, it should be known that normally port 0 (zero) will forward packets to another port number that is dynamically assigned. So port 0 should not be affected by attacks, because it actually doesn’t act as a normal port.
26. C. A Fraggle attack is a type of DoS attack that sends large amounts of UDP echoes to port 7 and 19. This is similar to the Smurf attack. Teardrop DoS attacks send many IP fragments with over-sized payloads to a target.
27. B. Port 49 is used by TACACS. Port 53 is used by DNS, Port 161 is used by SNMP, and Port 22 is used by SSH.
28. C. Port 88 is used by Kerberos by default. Port 21 is used by FTP. Port 80 is used by HTTP. Port 443 is used by HTTPS (TLS/SSL).