1 Introduction
Computer attacks happen each and every day. Simply connect an innocuous computer to the Internet, and someone will try to pry into the machine three, five, or a dozen times every 24 hours. Even without any advertisements or links bringing attention to it, attackers looking for vulnerable prey will constantly scan your machine or pummel you with e-mail trying to trick you into opening an innocuous-appearing attachment. If the computer is used for actual business purposes, such as a commercial, educational, not-for-profit, or even military system, it will get even more attention from the bad guys.
Many of these attacks are mere scans looking for particularly weak prey. Others are really sophisticated computer break-ins, which occur with increasing frequency as any glimpse of recent headlines demonstrates. In just a year’s time, various government agencies around the world have publicly admitted they were targeted with a customized Trojan horse designed to pilfer very sensitive government secrets. Attackers have stolen untold millions of credit card numbers from e-commerce sites, banks, and credit card processors, sometimes turning to extortion of the victim company to get paid not to release customers’ credit card information. Numerous online retailers have been temporarily shut down due to major packet floods. A major U.S.-based high-tech manufacturer disclosed that attackers had broken into its network and stolen the source code for future releases of its popular networking product. The stories go on and on.
The purpose of this book is to illustrate how many of these attacks are conducted so that you can defend your computers against cyber siege. By exploring in detail the techniques used by the bad guys, we can learn how to defend our systems and turn the tables on the attackers.
The Computer World and the Golden Age of Hacking
Over the last several decades, our society has rapidly become very dependent on computer technology. We’ve taken the controls for our whole civilization and loaded them onto digital machines. Our computer systems are responsible for storing sensitive medical information, guiding aircraft around the world, conducting nearly all financial transactions, planning food distribution, and even transmitting love letters. When I was a kid (not all that long ago, mind you), computers were primarily for nerds, something avoided by most people who had a choice in the matter. Only 15 years ago, the Internet was the refuge of researchers and academics. Now, as a major component of our population stares into computer screens and talks on cell phones all day long for both business and personal use, these technologies dominate our headlines and economy.
I’m sure you’ve noticed that the underlying technologies behind computers and networks have many flaws. Sure, there are counterintuitive user interfaces and frequent computer crashes. Beyond these easily observed bugs, however, there are some fundamental flaws in the design and implementation of the underlying operating systems, applications, and protocols. By taking advantage of these flaws, an attacker can steal data, take over systems, or otherwise wreak havoc.
Indeed, we have created a world that is inherently hackable. With our great reliance on computers and the numerous flaws found in most systems, this is the Golden Age of Hacking. New flaws in computer technology are being discovered every day and widely shared throughout a burgeoning computer underground. By setting up a lab in the comfort of their own homes, attackers and security researchers alike can create a scaled-down copy of the computer platforms used by giant corporations, government agencies, or even military operations, using the same operating systems, routers, and other gadgetry as their ultimate target. By scouring these systems looking for new vulnerabilities, attackers can hone their skills and discover new vulnerabilities to exploit.
And computer technology is continuing its advance into every nook and cranny of our lives. We’ve seen an explosion in Personal Video Recorders (PVRs), wonderful tools that sit on your television and observe your TV viewing habits. When your PVR decides that you are a major fan of The Simpsons or Star Trek, it starts recording those shows on its built-in hard drive. The latest PVRs even include Ethernet jacks so you can connect them to your home network and the Internet itself, sharing their stored TV content on other screens. So, there’s a box on your TV, watching what you watch, connected to the Internet. Imagine hacking that! An attacker could use some of that PVR hard drive space to store nefarious information, including stolen software, attack plans, or pornography. Attackers could even customize your TV viewing sessions, injecting their own content into the next episode of The Simpsons that you watch. In addition to PVRs, many stereo systems are now geared toward MP3 playback and can interface with a home computer, creating a media center built on underlying technologies full of security holes. In the very near future, your car will have a wireless network connection supporting map downloads, remote troubleshooting, and—Heaven help us—e-mail reading while you drive.
Beyond these consumer-centric applications, medical devices are being computerized and networked like never before. Some new heart pacemakers include magnetic induction interfaces so a doctor can read the settings on the device simply by holding a magnetic coupler over the patient’s chest. Some versions even support such readings over the phone, so the doctor and patient don’t have to be together. Future versions might even support the update of the pacemaker’s configuration over the Internet!
What underlies all of these rapidly approaching technologies? Computers and the networks that link them together.
With these advances, our current Golden Age of Hacking could get even more golden for the attackers. Think about it: Today, an attacker tries to break into your computer by scanning through your Internet connection, tricking you into surfing to an evil Web site, or duping you into running an e-mail attachment. In the near future, someone might try to hack into your network-enabled automobile while you are driving down the street. You’ve heard of carjacking? Get ready for the world of car hacking.
Why This Book?
If you know the enemy and know yourself,
you need not fear the result of a hundred battles.
If you know yourself but not the enemy,
for every victory gained you will also suffer a defeat.
If you know neither the enemy nor yourself,
you will succumb in every battle.
—Sun Tzu, Art of War
Translation and commentary by Lionel Giles (part of Project Gutenberg)
“Golly Gee!” you might be thinking. “Why write a book on hacking? You’ll just encourage them to attack more!” I respect your concern, but unfortunately there are some flaws behind this logic. Let’s face it—the malicious attackers have all the information they need to do all kinds of nasty things. If they don’t have the information now, they can get it easily enough on the Internet through a variety of Web sites, mailing lists, and newsgroups devoted to hacking, using a variety of the Web sites we discuss in Chapter 13, The Future, References, and Conclusions. Experienced attackers often selectively share information with new attackers to get them started in the craft. Indeed, the communication channels in the computer underground among attackers are often far better than the communication among computer professionals like you and me. This book is one way to help make things more even.
My purpose here is not to create an army of barbarian hackers mercilessly bent on world domination. The focus of this book is on defense, but to create an effective defense, we must understand the offensive tools used by our adversaries. By seeing how the tools truly work and understanding what they can do, not only can we better see the needs for good defenses, but also we can better understand how the defensive techniques work.
This book is designed for system administrators, security personnel, and network administrators whose jobs require them to defend their systems from attack. Additionally, other curious folks who want to learn how attackers work and techniques for defending their own systems against attacks can benefit. The book includes practical recommendations for people who have to deal with the care and feeding of systems, keeping them running and keeping the bad guys out, ranging from home users to operators of corporate and government environments. With this understanding, we can work to create an environment where effective defensive techniques are commonplace, and not the exception. As good ol’ Sun Tzu said, you must understand your enemy’s capabilities and your own. For each offensive technique described in this book, we’ll also describe real-world defenses. You can measure your own security capabilities against these defenses to see how you stack up. Where your policies, procedures, and technologies fall short, you can implement appropriate defenses to protect against the enemy. And that’s what this book is all about: Learning what the attackers do so we can defend ourselves.
Why Cover These Specific Tools and Techniques?
There are thousands of different computer and network attack tools available today, and tens of thousands of different exploit techniques. To address this flood of possible attacks, this book focuses on particular genres of attack tools and techniques, examining the most widely used and most damaging tools from each category. By learning in depth how to defend against the nastiest tools and techniques in each category, we will be defending against all related tools in the category. For example, there are hundreds of methods available that let an attacker hide on a machine by transforming the operating system itself, using tools called rootkits. Rather than describing each and every individual rootkit available today, we analyze in a greater level of detail some of the most powerful and widely used rootkit tools in Chapter 10, Phase 4: Maintaining Access. By learning about and properly defending against these specimens, you will go a long way in securing your systems against other related rootkit attacks. In the same way, by learning about the most powerful tools in other categories, we can design and implement the most effective defenses.
How This Book Differs
In recent years, several books have been released covering the topic of attackers and their techniques. Some of these books are well written and quite useful in helping readers understand how attacks work and highlighting defenses. Why add another book to the shelf addressing these topics? I’m glad you asked. This book is focused on being different in several ways, including these:
- Being more like an encyclopedia instead of a dictionary. Other books in this genre cover thousands of tools, with a paragraph or page on each tool. As described in the previous section, this book focuses on understanding each category of tool in much more depth. Therefore, whereas other books act like fantastic dictionaries of attack tools and defenses, this book aims to be more of an encyclopedia, describing the attack process in more detail and providing the overall architecture of attacks. By covering each category of attack tool and the overall attack architecture in more detail, we can better understand the appropriate defenses. But, the book isn’t designed to be just an encyclopedia. We don’t want this book to be merely a giant tome on your shelf gathering dust, occasionally used as a reference. Instead, we aim to provide the material in an interesting and educational manner, helping bring readers up to speed with the myriad of attacks we face and real-world methods for handling them in an effective manner.
- Presenting a phased view of attacks. Other books present a view of how attackers gain access to systems, focusing on the penetration portion of an attack. Although gaining access is an incredibly important element of most attacks, our adversaries do much more than simply gain access. Once access is gained, most attackers manipulate the system to maintain access and work hard to cover their tracks. This book covers the attack sequence end-to-end by presenting a phased approach to attacking, so we can cover defenses at each stage of a siege. Most attacks follow a general outline that includes reconnaissance, scanning, gaining access, maintaining access, and covering the tracks. This book describes each phase in detail.
- Covering scenarios for how the tools are used together. The tools used by attackers are a little like building blocks; each one fills a specific (but limited) purpose. Only by seeing how attackers build complete attacks out of the little blocks can we understand how to best defend ourselves. Sophisticated attackers take individual building blocks of tools and combine them in creative ways to devise very elegant attacks. This book describes how the tools are used together with its phased view of an attack. Additionally, Chapter 12, Putting It All Together: Anatomy of an Attack, presents several scenarios describing how these tools are used together in the wild to undermine systems.
- Using analogies to illustrate the underlying computer concepts. Throughout the book, I have used analogies to highlight how various technologies work. Although some of the analogies are certainly cheesy, I hope they make the material more interesting and accessible to readers.
The Threat: Never Underestimate Your Adversary
So who are these attackers that we must defend against? So often, when we speak of computer attackers, people get visions of a pimply-faced teenager messing around with his computer from his bedroom in his parents’ house, sucking down a bunch of high-caffeine energy drinks in the process. This image lulls some people into lowering their defenses, thinking, “What kind of damage could a mere kid do?” This thinking is wrong on at least three accounts.
First, in my experience, many of the youthful attackers have remarkably clear skin, with not a pimple to be found. Second, and far more important, many of the kids are amazingly good at what they do, with sophisticated skills and a huge degree of determination. Sure, some of the youthful masses don’t have a great deal of skill, but if your organization falls into the crosshairs of highly skilled youthful attackers, they can do some significant damage to your computing systems. Don’t let your defenses down just because you think your only threat is younger than 20 years old.
A third reason not to let your defenses down with visions of teenage attackers is perhaps the most important. Most organizations are faced with threats far beyond mischievous youth. You should never underestimate your adversary. Different organizations have different exposure to potential threats. In reality, attackers come from all walks of life and have a variety of motives for their actions. Beyond the youthful offender, some of the outside threats that we encounter launching attacks include the following:
- Organized crime. If your organization handles money (which most organizations do at some level), your computing infrastructure could be the target of organized crime. Similarly, if you are an individual (which most people are), your sensitive information could be very useful to criminals. These attackers might be looking for sensitive data for identity theft or other fraud, a convenient way to launder money, information useful in their criminal business endeavors, or system access for other nefarious purposes. One of the most important stories of the past couple of years has been the rush of organized crime into the computer attacking business. The bad guys have honed their business models to optimize how they make money in computer attacks. This type of crime can be highly lucrative for the bad guys, who might steal and sell credit card numbers, commit identity theft, or even extort money from a target under threat of denial-of-service flood. Further, if the attackers cover their tracks carefully, the possibilities of going to jail (as well as the likelihood of getting shot) are far lower for computer crimes than for many types of physical crimes. Finally, by operating from an overseas base from a country with little or no legal framework regarding computer crime prosecution and no extradition treaties, attackers can operate with virtual impunity.
- Terrorists. If your organization is considered part of the critical infrastructure of your country or the world, you face potential cyber attacks from terrorists. They could plant malicious programs throughout your enterprise to shut down all critical systems during sensitive times, destroy systems or data to cause economic upheaval, or otherwise cause potentially life-threatening problems.
- Governments. Most governments have active interest in the activities of a huge variety of organizations operating on their soil. Some have turned to cyber attacks to gain access to and information about local organizations to support law enforcement, to gain information to help homegrown companies compete against foreign companies, and even to repress dissidents. Going further, some governments have reached outside of their own territory in subtle computer probing and outright attacks against businesses and other governments, for military or business advantage.
- The competition. Sometimes, an organization’s competition will turn to computer attacks to try to gain the upper hand. These attacks could include low-level reconnaissance for gathering interesting tidbits about the business, in-depth penetration into sensitive systems to gain details of future strategies, or even massive denial-of-service attacks to prevent customers from reaching the victim. We’ve personally handled incidents in which e-commerce sites were targeting their competition to knock them offline for a while in an effort to drive customers toward their own Web sites and increase revenue.
- Hacktivists. If your organization does something politically sensitive, you might be the target of hacktivists. This class of attackers tries to break into your systems to make a political point or demonstrate regarding social issues. Hacktivists might alter your Web site to display their messages and embarrass your organization, or cripple your processing capabilities to slow down your business.
- “Hired guns.” This type of attacker is looking to make money by stealing information or gaining access to computer systems on behalf of a client, which could be one of the other external threats included in this list.
Beyond these outsiders, keep in mind that a majority of attacks come from insiders, folks who have direct access to your computer systems as part of their job function or a business relationship. Insider threats include the following:
- Disgruntled employees. Because they have a great degree of access to, exposure on, and training in an organization’s own systems, an organization’s own employees are often the most frequent and damaging attackers of computer systems.
- Clueless employees. Beyond the employees who are out to get you (that is, the disgruntled ones), other employees might inadvertently compromise your organization’s security. By disabling antivirus tools, surfing to sites that try to attack their browsers, or countless other improper security practices, these users represent a real risk, even though they aren’t trying to hurt anyone.
- Customers. Unfortunately, customers sometimes turn on their suppliers, attacking their computing systems in an attempt to gain sensitive information about other customers, alter prices, or otherwise mess up an organization’s data.
- Suppliers. Suppliers sometimes attack customers. A malicious employee on a supplier’s network could attack systems in a variety of ways.
- Vendors. Vendors are often given full access to systems for remote diagnostics, system upgrades, and administration. With this access, they could not only attack the systems to which they are given access, but potentially systems throughout the network. What’s more, whether you like it or not, the software running on your systems acts as a massively trusted insider, with access to very sensitive information. The people who wrote that software might or might not have your best interests at heart. A renegade developer at a software company could have planted a backdoor or deliberately inserted a security flaw so that he or she could gain access to your systems. With recent trends toward outsourcing software development around the globe, very few organizations even know where the guts of their own vital software was developed, let alone the names and motivations of the people on the development team.
- Business partners. Joint ventures, shared projects, and other business relationships often involve linking networks together and sharing highly sensitive information. An attacker located on any one of the networks connected together could launch an attack on one of the other business partners. Also, security is often like the proverbial chain with the weakest link. If one of your business partners succumbs to an external attacker because they have a lower security stance than you do, that attacker could gain access to your network through a business partner connection.
- Contractors, temps, and consultants. Having worked as a consultant myself for more than a decade, I feel confident in saying that these breeds of insiders can be particularly insidious. Many organizations do not conduct thorough background checks on these temporary employees as they do on their own permanent employees. These short-term workers often have a great deal of access to systems and data. Compounding the problem, some organizations cannot remove account access by short-term workers as quickly or thoroughly as they can for terminated employees. I’ve seen situations where terminated employees’ accounts will be closed out the morning of separation, whereas a temp’s account might linger for months.
Of course, the threats in this list are not mutually exclusive. For example, a determined terrorist group could place people within your organization as temps in an effort to gain access and plant malicious software on your systems from the inside. Likewise, a competitor could employ highly skilled youthful offenders as hired guns to steal particular information from an organization’s systems. The combinations and permutations are endless.
However, just as you don’t want to underestimate the threats you face, neither do you want to overestimate them. You don’t want to gold plate your security, protecting against phantoms that would have no interest in your computers or information. No one installs expensive car alarms on a beaten up 1992 Chevy station wagon. However, in certain neighborhoods, you certainly lock the doors on such a car to keep people from taking a joyride at your expense. You must sit down and carefully evaluate which threats would be motivated to go after your organization, tally the tangible and intangible value of the assets you have to protect, and then deploy security commensurate with the threat and the value of your systems and information.
Attacker Skill Levels: From Script Kiddies to the Elite
Among the numerous types of computer attackers, skill levels vary greatly. Some attackers have only rudimentary skills, not understanding how their tools really work and instead relying on prepackaged attack tools written by others. Such attackers are often derisively referred to as “script kiddies,” as their skills are based on running scripts and other software written by more sophisticated attackers and they tend to be rather immature. Script kiddies often indiscriminately scan large swaths of the Internet looking for easy prey to take over, or send a bazillion e-mail messages with evil attachments, hoping that some small fraction of their targets take the bait. By compromising this low-hanging fruit, script kiddies get bragging rights and a base from which to launch further attacks. Because so many hosts are so poorly protected on the Internet today, even attackers with very low skill levels can compromise hundreds or thousands of systems around the world. There are a huge number of script kiddies on the Internet today, and their growth is truly international in scope.
Beyond the simple script kiddies, we often observe moderately skilled attackers, who are very sharp in one type of operating system. With the right degree of determination, these medium-level attackers can cause a great deal of damage to a target organization. Furthermore, a major trend in the computer underground involves moderately or highly skilled attackers and security researchers discovering vulnerabilities in computer systems and creating simple-to-use exploit tools to demonstrate the discovered vulnerability. Many of the moderately skilled attackers release these tools in a public forum, such as a newsgroup or on a Web site. Some of these exploits are quite sophisticated, yet are very easy to use. In fact, many of the tools have point-and-click graphical interfaces or simple command-line options. The script kiddies adopt these tools written by more skilled attackers and use them in their attacks without understanding the underlying vulnerabilities that they are exploiting.
At the top end of the skill chart, we find truly elite attackers. These individuals tend to have in-depth skills covering a wide range of platforms. Unlike the script kiddie masses, these elite attackers seldom want publicity. When they take over a system, the elite tend to lurk silently in the background, carefully covering their tracks and gathering sensitive information for future use. This elite community also conducts detailed security research, looking for holes in applications, operating systems, and other programs that can be used to take over systems. Based on this research, they develop their own specialized tools for taking over systems. Many of the elite attackers keep their newly discovered vulnerabilities and custom attack tools to themselves, not sharing them publicly. By not sharing tools and techniques, these more secretive attackers attempt to prevent development and deployment of effective defenses against their tools.
Another group with an elite degree of attacking skills has exactly the opposite intention. They have more noble purposes, wanting to discover vulnerabilities before the malicious attackers do in an effort to defend systems. These more noble elites sometimes become security professionals, offering their skills to companies or governments looking to improve their security stance or vendors who want to improve their products. Some provide this information for free, just trying to make the world a better, more secure place. Others hang a shingle outside their door and go into business as security researchers or consultants.
A Note on Terminology and Iconography
Hackers, Crackers, and Hats of Many Colors: Let’s Just Use “Attackers” and “Bad Guys”
Just as Eskimos have a large number of words to represent the idea of snow, so too are there a variety of words used to refer to people who attack computer systems. Unlike snow, though, there is some degree of controversy over these computer attacker terms. The media and, by extension, the general public refer to people who attack computer systems as “hackers.” However, many people in the computer underground point out that the term “hacker” has historically referred to a person who was gifted at extending the function of computers beyond their original design. According to this definition, hackers are good, acting as noble explorers making computers do new and cool things. Using the term hacker to label a computer vandal or thief denigrates not only the term, but the historic hacking concept.
For folks who use the term hacker in a positive sense, people who maliciously attack computer systems trying to wreak havoc are sometimes called “crackers.” So, in this vernacular, hackers are good, and crackers are bad. Of course, because the worldwide media labels both categories of people as hackers, the cracker terminology hasn’t caught on.
To address this problem of terminology, you sometimes see the words “black hat” and “white hat” used for different kinds of attackers. Just like in old cowboy movies, black hats are the malicious attackers, whereas white hats are the computer security experts who try to protect systems. A black hat tries to break into systems, whereas a white hat conducts research and does penetration testing to find and fix vulnerabilities. Predictably, people who work on both sides of the divide (sometimes attacking systems, sometimes defending them) are “gray hats.”
Because the hacker, cracker, and multicolored hat terminology can get rather muddled and controversial, throughout this book we will use the simple term “attacker” to refer to someone who attacks computers. The attacker could be a hacker, cracker, white hat, black hat, gray hat, super elite, security researcher, or even a penetration tester. Whatever the skill level, motivation, and the nomenclature, these are the people attacking computers. Therefore, we use the term attacker. Additionally, we use the term bad guy to refer to those specific attackers with evil intent.
Another important point to keep in mind is that attackers (or bad guys) are not necessarily human. No, they aren’t extraterrestrials ... I’m referring to malicious code. Sometimes your attacker has fingers on a keyboard and a heartbeat, whereas other times, the bad guy is really software, a worm rampaging through the Internet or a bot installed on a system. Sure, any given worm or bot was created by a human at some point in the past, but, once released, the original developer usually has little or no control over how it propagates. Thus, whenever we use the terms attacker and bad guy in this book, remember that we can be referring to a person or malicious software going after a target.
Pictures and Scenarios
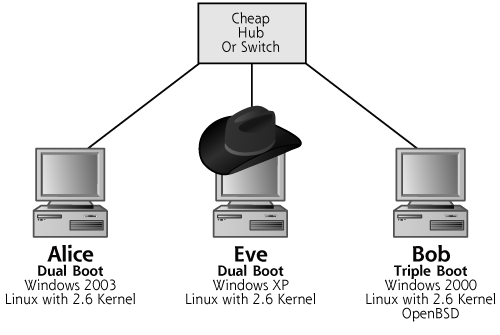
Although the terms attacker and bad guy are used throughout the book, we do need to show pictorially which machine belongs to an attacker in our figures. To do so, we borrow the imagery of the black hat. In pictures throughout the book, the attacker’s machines are always shown wearing a black hat so they can easily be spotted, as shown in Figure 1.1.
Figure 1.1 Throughout the book, an attacker’s machine is shown wearing a black hat.

Additionally, the book includes numerous scenarios to highlight various attack techniques. In many of these scenarios, we use a recurring cast of characters named Alice, Bob, and Eve. Alice and Bob are innocent machines trying to get some work done. Eve is the attacker, trying to undermine Alice and Bob to gain access, steal information, corrupt data, or otherwise disrupt Alice’s and Bob’s happy lives. Please note that the names Alice, Bob, and Eve are frequently used in the cryptography and security communities and we intend no slight of any gender whatsoever in calling the attacker Eve. Of course, there are certainly tremendous gender and theological implications to calling the attacker Eve. However, for our purposes, Eve is genderless, referred to as he, she, or it. And discussions of the theology of calling the bad guy Eve are often best had over several drinks, so we won’t dwell on them here. In the cryptography and security community, the attacker Eve was given this name based on its phonetic similarity to the word “eavesdropper.” Others call the bad guy Mallory, which again raises those gender issues we won’t discuss here.
Naming Names
Another standard we’ll observe throughout the book is to mention the name or handle of the people who have created each of the tools that we discuss. Some might feel that giving any publicity to folks who have created these tools should be avoided. I disagree. Some of the tools can be used for both good and malicious purposes. A well-written packet-capturing tool (a “sniffer”), for example, can be used to troubleshoot a network (a beneficial use) or to capture other users’ passwords (often leading to a malicious attack). Likewise, a vulnerability scanner can find holes so a system owner can fix them, or so an attacker can pinpoint areas to attack. Other tools, although entirely malicious, illustrate the importance of utilizing a particular defensive technique, and therefore have value.
Although we might disagree with some of their motives, you have to respect the great skill, time, and effort that went into developing many of these tools. Therefore, as a form of respect to the many folks who have worked countless hours to develop some of the attack tools described in this book and the associated defensive techniques, we provide the name of the tool’s author and links so you can download the tools themselves.
Caveat: These Tools Could Hurt You
We have indeed included specific links where you can download each tool described in this book on the World Wide Web. It is incredibly important that you realize that you use these tools at your own risk! Although some of the tools we discuss are written by software vendors, security consultants, and open-source aficionados, other tools covered in the book were written by people with more sinister motives. As with all software, you must be careful about what you download and run on your production systems.
Many of the tools discussed in this book are designed to have some sort of malicious capability, and they can harm your system in the way advertised. It is also possible for an attacker to create a tool that is not only harmful in the advertised way, but also includes hidden features that exploit your systems. You think the handy tool you just downloaded will scan your network for vulnerabilities. Unfortunately, the tool may also send a copy of your vulnerability report to the attacker or load a nasty worm on your machine. Making matters worse, perhaps the tool itself was developed with the noblest intentions, and was released with no hidden nefarious functionality. But then, a bad guy compromised the Web site used to distribute the erstwhile safe tool. The attacker could add a backdoor to the tool and place it on the now-compromised Web site. Anyone who downloads the new version of the tool and installs it unwittingly cedes control of his or her own machines to the attacker. This type of attack does happen, and has been used by bad guys for over a decade. It’s a tough world out there, and you’ve got to be careful.
How should you face these concerns? Should you just avoid running the tools discussed in this book altogether? You need to make that decision yourself, but I do recommend that you experiment with these tools in a controlled environment so you can get a good understanding for how the attacks work and can better defend yourself.
Setting Up a Lab for Experimentation
By a controlled environment, what I mean is that I recommend that you experiment with these attack tools on systems completely separated from your production network. The tools described in this book do not require much computing horsepower; you can use some old 700-MHz Pentium III machines with 256 MB of RAM and 10-GB hard drives to experiment with these tools. You can buy used machines with such specs at a very reasonable price at your favorite auction site. Set up two or three machines on an isolated LAN segment, with completely fresh operating systems. Make sure there is absolutely no sensitive information on the hard drives. Link the systems together with an inexpensive hub or switch, which you can purchase for less than $50 at most computer stores.
To maximize the flexibility of your lab, I recommend that you create dual-boot systems, installing operating systems such as Linux, Microsoft Windows 2000/XP/2003, OpenBSD, or Solaris x86. Most attack tools run on Linux and Windows, the two favorite platforms of the computer underground, so make sure you include them. Figure 1.2 shows one possible network configuration, the one I use in my own lab at home.
Figure 1.2 An experimental lab for analyzing attack tools.
If you have a little more money to spend, you might want to take the architecture of Figure 1.2 and virtualize the whole thing. Get a virtual machine environment tool, such as the commercial VMware (www.vmware.com) or VirtualPC (www.microsoft.com/windows/virtualpc) or the free Bochs (http://bochs.sourceforge.net), Plex86 (http://plex86.sourceforge.net), or Qemu (http://fabrice.bellard.free.fr/qemu). These tools let you run multiple operating systems on a single hardware machine. Get a laptop or desktop with a lot of RAM (say, 1 GB or more), and install a host operating system. Then, inside your virtual machine environment, install several guest operating systems, which you could then run all at the same time. That way, you’ll be able to test tools and practice your attack, defense, and analysis skills on a single handy machine.
Additional Concerns
Although most of the Web sites distributing software described in this book are run by consulting firms or computer professionals, a few of the Web sites referred to in this book are run by somewhat shady characters. When you access these Web sites, you leave your computer’s network address in their logs, and could invite an attack. Although most of these site operators are far too busy to start attacking you just because you’ve accessed their site, I do recommend some discretion. Whenever you surf the Internet looking for attack tools and techniques, I strongly recommend that you use a browser on a machine dedicated to that purpose, without any sensitive data stored on the system. Also, use an account with a different Internet Service Provider (ISP) from the one that your organization relies on for Internet service. There’s no sense in leaving your organization’s network addresses or other information in the logs of the Web sites you are searching for attack tools.
Additionally, when you download attack tools, you might want to review the source code. Most of the tools include source code, some with reasonably good comments. Although code review can be a painstaking process, you can learn a lot from it. Additionally, you might be able to spot additional, malicious functionality not documented by the tool’s author.
If you plan to use the tools, make sure you have permission to run them against your organization’s computer systems. I don’t want you to jeopardize your job by experimenting with these tools! You could easily lose your job or suffer criminal prosecution for doing something you merely thought you had permission to do. Thus, make sure you get written permission from the owner or controller of your targets before running these tools. To help you get that permission, I’ve included a free permission memo on my own Web site, at www.counterhack.net/permission_memo.html. This letter is designed to grant you permission to run computer vulnerability assessment tools against your environment in an effort to improve its security. In the penetration testing business, we refer to such a notice as a “Get Out of Jail Free Card” (GOOJFC). Print this memo on company stationary and take it to the appropriate person in your organization, such as a Chief Information Security Officer (CISO) or your Chief Information Officer (CIO). Don’t take it to the janitor, because he or she cannot give you permission to launch such attacks. Have the appropriate authority read and sign it, and then keep a copy of your GOOJFC on file. It just might save your neck someday.
Also, please do note that particular geographic locations impose limitations on the use of these tools. In some countries, running attack tools across a public network is illegal, even if you target your own computing systems. Therefore, be sure to check with your legal folks before running these attacks across any public network.
Finally, we are certainly not liable if you purposely or accidentally do any damage to yourself or anyone else with these tools. That is an issue between you, your victim, and your local law enforcement authorities.
Organization of Rest of the Book
The remainder of the book is ordered into three main sections: a technology overview, a step-by-step description of attacks, and a final section offering predictions for the future, conclusions, and references. Let’s look at each of these sections in more detail.
Getting Up to Speed with the Technology
To understand how our adversaries attack systems, it is important to have a good grounding in the basic technologies that make up most of our systems and that the attackers use to undermine our machines. The first three chapters of the book provide an overview of several key underlying technologies:
Chapter 2 Networking
Chapter 3 Linux and UNIX
Chapter 4 Windows
These three technologies are in widespread use in all types of organizations today, and they are key components of the Internet itself. Most organizations have built and deployed large numbers of Linux/UNIX and Windows machines for internal use and access on the Internet. Even those organizations that still have pockets of Novell NetWare, mainframes, VMS-based systems, and other platforms often access these systems across a TCP/IP network and use Linux/UNIX or Windows systems as front ends for such access.
The attackers use these same technologies to launch their attacks. Furthermore, even though these tools run on these platforms, many of them are used to target any type of platform. For example, an attacker could use a session hijack tool on a UNIX machine to take over a session between a Windows system and your mainframe. Alternatively, an attacker could launch a denial-of-service attack against your Novell network or IP-enabled wireless Personal Digital Assistant (PDA) using many compromised Windows systems. Keep in mind that even though a specific tool described in this book runs on a given platform, the exact same techniques can be applied to attack other types of platforms. Likewise, the same types of defenses should also be applied to all systems to prevent the attacks.
Common Phases of the Attack
After our initial discussion of common technologies used today, the heart of this book is built around the common phases used in a large majority of attacks. Most attacks follow a general five-phase approach, which includes reconnaissance, scanning, gaining access, maintaining access, and covering the tracks. This book includes one or more chapters describing each attack phase, the tools and techniques used during the phase, and proven defenses for each tool or technique. The chapters on attack phases are organized as follows:
Chapter 5 Phase 1: Reconnaissance
Chapter 6 Phase 2: Scanning
Chapter 7 Phase 3: Gaining Access at the Operating System and Application Level
Chapter 8 Phase 3: Gaining Access at the Network Level
Chapter 9 Phase 3: Gaining Access and Denial-of-Service Attacks
Chapter 10 Phase 4: Maintaining Access
Chapter 11 Phase 5: Covering Tracks
Once the various phases of attacks are covered, we explore how the tools and techniques are used together by addressing several scenarios based on real-world attacks. Three scenarios are presented in Chapter 12, Putting It All Together: Anatomy of an Attack.
Future Predictions, Conclusions, and References
Finally, the book concludes with some predictions for how tools and attacks will evolve in the future, as well as some references so you can keep up to speed with new attack and defense techniques.
Yeah, But What’s NEW?
This is the second edition of Counter Hack, which we’ve chosen to name Counter Hack Reloaded, in a subtle nod to The Matrix movie franchise. Some of you might have read the first edition, and for that I thank you sincerely. But you might be thinking, “Why a new edition? What’s different about this one, and why should I consider it again?” The world of computer attacks has progressed rapidly in the four years since the original Counter Hack. As its name implies, this edition represents a massive update and expansion of Counter Hack. My co-author, Tom Liston, and I went through every last jot and tittle of the book, updating each and every attack to represent the latest methodologies we see used by the bad guys in the real world. What’s more, we’ve expanded several sections to include new attack methodologies and tools that have emerged since the original Counter Hack, so you can learn about the latest attacks and benefit from the best new defensive strategies. In addition to a general update of all of the materials in the book, here are some specific, brand new sections to focus on in each chapter:
Chapter 2: Networking. We’ve updated this chapter generally, and added a specific section on wireless LANs, an immensely popular attack vector today.
Chapter 3: Linux and UNIX. This chapter’s updates included a more Linux-centric view of the world, given the rising prominence of Linus Torvalds’ offspring.
Chapter 4: Windows. In this chapter, we focused on the rapid evolution of Windows in the post-Windows-2000 world, spending more time discussing Windows XP, Windows 2003, and Active Directory.
Chapter 5: Phase 1: Reconnaissance. This chapter includes some nifty tricks for caller ID spoofing, as well as a very powerful and popular attack technique—using Google to hone an attack and find vulnerable systems.
Chapter 6: Phase 2: Scanning. Here, we extended the discussion to include several war driving techniques used to find potentially vulnerable wireless LANs. Going further, we’ve included new types of port scans, including the very nifty idle scanning options of Nmap, as well as version scanning. We’ve also extended the discussion of how to find active ports on a system and shut down unneeded services, with a raft of tools supporting this capability on both Windows and Linux/UNIX.
Chapter 7: Phase 3: Gaining Access at the Operating System and Application Level. This chapter features some major expansions, with an extended look at stack-based buffer overflows as well as a new section on heap-based overflows. We also look at exploitation framework tools, like Metasploit, some of the slickest attack capabilities we’ve ever seen released publicly. We then discuss one of the most powerful tools around today, the very flexible Cain & Abel suite, a full-featured tool for cracking numerous kinds of passwords and a dozen other attack capabilities. We’ve updated the Web application section in a big way to include some late-breaking attack specifics, as well as a description of the Web Goat environment for developing Web application assessment skills. Finally, we added a section describing one of the most popular attack vectors today: exploiting vulnerable Web browsers.
Chapter 8: Gaining Access at the Network Level. This chapter includes new detailed discussions of passive operating system fingerprinting, port stealing to sniff in a switched environment, and session hijacking with Ettercap. We also address some of the unique problems we face in wireless LAN environments regarding session hijacking. Finally, we’ve extended the Netcat tool discussion to describe how to create persistent listeners on a Linux/UNIX system using a little scripting, a technique very valuable in setting up honeypots.
Chapter 9: Gaining Access and Denial-of-Service Attacks. This chapter has been extended to address some major concerns with TCP Reset attacks, as well as the bot threat in Distributed Denial-of-Service (DDoS) floods. We look at reflected DDoS attacks, as well as the threat of pulsing zombies.
Chapter 10: Phase 4: Maintaining Access. This chapter includes a plethora of nifty new topics, reflecting the computer underground’s major work in this arena. We discuss the rise of bots and spyware. We address the topic of detecting and possibly even escaping virtual machine environments, something that is a rising and very scary threat. We next scrutinize some of the most widespread rootkit tools today, including Hacker Defender and FU, which run on Windows machines, and Adore-ng, a Linux kernel-mode rootkit. The chapter finishes with a discussion of rootkit detection programs for Linux/UNIX and Windows.
Chapter 11: Phase 5: Covering Tracks. In this chapter, we’ve expanded the discussion of Alternate Data Streams and covert channels, showing several tools employing each technique. We also address the notable increase in the use of covert channels by malware and spyware, especially tools that undermine Internet Explorer. Finally, we added a section on passive covert channels with a tool called Nushu that lets the bad guys embed their data inside of normal traffic generated by other activity of a victim machine.
Chapter 12: Putting It All Together. This chapter features a whole new scenario based on the massive credit card thefts we’ve seen in recent headlines, as well as the immense security holes introduced by weak wireless LANs. You’ll read about how these two trends can be related, costing financial institutions serious money, and jeopardizing consumers’ trust.
Summary
As we load more of our lives and society onto networked computers, attacks have become more prevalent and damaging. Because of this, we have entered the Golden Age of Hacking. To keep up with the attackers and defend our systems, we must understand their techniques. This book was written just for that reason—to help system administrators, security personnel, and network administrators defend their computer systems against attack.
Never underestimate your adversary. Attackers come from all walks of life and have a variety of motivations and skill levels. Make sure you accurately assess the threat against your organization and deploy defenses that match the threat and the value of the assets you must protect.
People who attack computers are called many things: hackers, crackers, black hats, and so on. We refer to them throughout this book as attackers or bad guys, and show them in diagrams as computers wearing black hats. We also cover many scenarios showing Alice, Bob, and Eve. Alice and Bob are good, and Eve is the attacker.
If you want to experiment with the tools described in this book, be careful! Run them on systems without any valuable data, physically separated from your production network. Set up a small evaluation lab of two or three machines. Make sure you get written permission from your management and legal counsel before running any tools against your own machines or across a public network.
