Chapter 6
Web Camera and Video Tracking
Abstract
This chapter explains how to track user activities through web cameras, mobile phone cameras, security systems, and other forms of camera-based technology. The increased use of mobile devices with cameras, personal computers with webcams, and camera systems installed at homes, businesses, and out in the general public are growing at an alarming rate. In this chapter, we will look at the growing use of this technology, what the technology is capable of, what purposes are served for good and evil, and why we should be concerned. This chapter will cover creepware and other malwares that are used to expose weaknesses in camera technology. We will also look at and discuss how camera systems everywhere are allowing government agencies a view into our private worlds.
Keywords
Creepware
Webcam
Satellite
Nanny cam
Xbox Kinect
Gaming Console
CCTV
DVR
Privacy
Sextortion
Blackshades
Remote Administration Tool (RAT)
Visual malware
PlaceRaider
Digital Forensics
NSA
GCHQ
Optic Nerve
Facial Recognition
Camera tracking
The increased use of mobile devices with cameras, personal computers (PCs) with webcams, and camera systems installed at homes, businesses, and out in the general public are growing at an alarming rate; the threats are also growing to expose security issues with them that violate your privacy. In this chapter, we will look at the growing use of this technology, what the technology is capable of, what purposes are served for good and evil, and why we should be concerned.
As we discuss these topics and how they relate to reconnaissance and surveillance, it will become evident that you are now always on camera. We carry one with us everywhere we go. There tends to be a camera located everywhere. Let’s consider this example: You wake up and get ready for work, while in your home you are on camera as your home has an active internal security surveillance system. You check your e-mail before you leave the house on your laptop configured with a webcam. You pack up to leave and grab your mobile phone and tablet and get into your car. Your drive to work passing roughly 10 traffic lights before pulling in and parking in the parking garage. There is video surveillance feeds in the garage. You enter work and each entrance/exit and floor contains surveillance equipment. You dock your work laptop (with integrated webcam) and get to work briefly checking your mobile devices that are directly sitting next to you. Each time you leave your desk to move within the office, you take your phone with you. You leave for lunch and go to mall to eat in the food court with a few friends. The mall has video surveillance feeds. After work, you drive back home (10 traffic lights) and settle in for the evening. After dinner, you decide to load a game on your Microsoft Xbox and join a few friends online to play games. Later, you check your social media sites online and Skype with a friend.
We can go on and on but I think you get the picture. You are on camera 24 hours a day and this does not include the government’s ability to pinpoint and track your whereabouts via satellite. This does not include military or law enforcement being able to use satellite tracking. In this chapter, we will discuss all of the ways you may or may not know you are being captured on camera and how you protect yourself. Digital surveillance is here to stay and will probably become more invasive over time, so learning how to mitigate threats and being aware of new threats is the key to regaining your privacy.
Tracking examples
In the example given, we covered quite a few things that you may or may not be aware of. Let’s recapitulate.
In the example: You wake up and get ready for work, while in your home you are on camera as your home has an active internal security surveillance system.
The reality of this is, although deemed secure, you are on camera in your own home. If you have a provider watching, they obviously have policies in place to protect your privacy; however, what if they are hacked? What if stored information is exposed? Although not likely, it is possible. What if those same cameras had a flaw and can be hacked by a neighbor or someone passing by?
You check your e-mail before you leave the house on your laptop configured with a webcam. You pack up to leave and grab your mobile phone and tablet and get into your car.
As we will discover while exploring this chapter, there are new forms of malware and hacking applications that allow an intruder to take over your device completely and view your surroundings from your webcam. Mobile devices are also exploitable via apps that also perform this behavior.
Your drive to work roughly passing 10 traffic lights before pulling in and parking in the parking garage. There is video surveillance feeds in the garage. You enter work and each entrance/exit and floor contains surveillance equipment.
As we have learned in earlier chapters, traffic lights (as well as bridges and other infrastructures) are protected with cameras that track your location. Surveillance systems are normally installed in public places such as parking garages and at the entrance of company locations. These same systems are also located within company work spaces.
You dock your work laptop (with integrated webcam) and get to work briefly checking your mobile devices that are directly sitting next to you. Each time you leave your desk to move within the office, you take your phone with you.
The same risks at home have now transferred with you to work. You are working on a system with a webcam (usually, directly integrated into your laptop or workstation) and your mobile devices are always close by.
You leave for lunch and go to mall to eat in the food court with a few friends. The mall has video surveillance feeds. After work, you drive back home (10 traffic lights) and settle in for the evening.
When you leave work, you pass all of the same surveillance gear you encountered on your journey into work and, similarly, where you go there will be more.
After dinner, you decide to load a game on your Microsoft Xbox and join a few friends online to play games. Later, you check your social media sites online and Skype with a friend.
You are back at home with the same possible threats but now you have opened even more by using other cameras located in your home.
Although this evidence may seem overwhelming, nothing can be further from the truth – it is possible that you are always on camera. In this chapter, we will look into each of these threats, how they have been exploited in the past, and, if possible, why it is important to be vigilant in securing against them.
Security Surveillance Systems (Private Home)
Systems put in place at home to protect your belongings, from intrusion and otherwise, can be helpful. There are actual cases where these systems have been helpful in not only preventing crime but also solving cases of crimes that have been committed. There are two classes of these types of surveillance systems. One you set up and monitor yourself or a professional system that is monitored by a third party. These systems can be internally and externally located at your home. Obviously, you would want these systems to be located.
In the summer of 2013, an arrest was made on a man who conducted a home intrusion in New Jersey and assaulted a woman in front of two small children. Jewelry was stolen and the suspect fled. A “nanny cam” had been installed in the woman’s home used to keep an eye on the sitting services while away from the home. These webcams are common so that those who put their kids in the hands of others can be watched, so they can monitor how their children were handled that day. The suspect wanted in this home invasion had been captured on camera, and during investigation by the local law enforcement as well as the Federal Bureau of Investigation (FBI), an arrest was made to take the man into custody. As we can see, security systems do in fact provide a wealth of value when they are used for good. As seen in Figure 6.1, the camera caught the invasion and provided all of the evidence required to prosecute this attacker.

Figure 6.1 Home Invasion Caught on Nanny Cam
So, what about the privacy of the nanny? Was it disclosed that there was a nanny cam installed? Although this question may not even come up because of the nature of how successful this cam had been in capturing a criminal; however, this is also a concern because if not disclosed, this camera would be watching those entering the home and recording their actions without their knowledge or consent. This is where the argument comes in – where does privacy end and security begin? On one hand, a criminal was caught and taken off the streets. If the hired daycare or sitter watching children did something heinous, it would be caught. These are positives and gain the support of many, but what about privacy of those who do not know they are being recorded such as a good babysitter who cares for the children and never know that their private conversations on their cell phone are overheard and so on.
Another concern with personal home security systems is that they can be hacked. Most systems work off of wireless networking and TCP/IP, therefore, if not secured correctly, can be easily penetrated and remotely used. Your living room has now become a prime time television for a stalker.
If you are not using a personal security system and have installed camera systems for a third party vendor or company to monitor for you, you should be aware that this means that a third party has the ability to see what you do in the name of “security.” If these personal security systems monitored by a third party are exploited by someone attacking the vendor, then you could also be at risk.
Security Surveillance Systems (Businesses)
Systems put in place at businesses mirror those previously discussed when we did an overview on home-based security systems. Businesses need to protect their interests and assets the same way that a personal home owner would, and more so, because they are responsible for activities of their workforce. For example, what if someone in the office stole a piece of equipment and/or stole something from another co-worker? What if a crime is committed? There are legal implications that need to be considered.
Besides basic security, these cameras also provide a deterrent feature. Those who believe they will be caught are less likely to commit a crime. When you work for a company, go through on-boarding, and use the company’s resources, it should not come as a surprise to you that you will be monitored.
Where this seems to cross borders is, what type of business are we talking about? For example, if this is a fortune 500 company where workers come in to do business everyday, it may not seem inappropriate to have security cameras placed in common areas; however, what if the business we are talking about is a school? What if it was a church? What if your right to privacy was invaded based on the business that was under surveillance?
Another concern is what if business systems then invaded your personal privacy at home? A great example of this can be seen when a school district in Pennsylvania during 2010 activated student webcams on school-loaned laptops used by the students. Parents were not informed and student privacy (and safety) was put at risk.
It can be said that in some instances, these cameras provide protection, can be used as a deterrent, and, in some cases, prevent or solve crimes, whereas in some instances, it can be used to commit crimes and evade your privacy. In such situations, understanding your surroundings and doing due diligence (covered in Chapter 8) will help you mitigate risks as much as possible.
Security Surveillance Systems (Public)
If you are a fan of popular television drama, there are many shows available where crime is investigated by pulling camera footage to establish a timeline, to show specifics on “who was at the location” and otherwise. Although this is exciting on drama TV, it should be considered that these activities really do take place. As a matter of fact, many crimes are investigated in this manner. Part of doing Digital Forensics is recovering data stored on systems to re-enact a crime or offer evidence of a crime taking place.
Traffic lights, bridges, traffic cams for news outlets, and many other areas where we publically congregate are increasingly being put under video surveillance. Are we at risk or will this offer protection? There is much debate in this area; however, we can highlight examples where this type of surveillance was deemed to be helpful. The Boston Marathon example is one that sheds light on the helpfulness of video surveillance in public areas. As seen in Figure 6.2, the two suspects caught performing this heinous act were caught because law enforcement officials sifted through all available public video surveillance to put together the timeline and acts of terrorists performing an attack.

Figure 6.2 Boston Marathon Video Surveillance
As mentioned, this is a good thing. The wrongdoers were captured because of the fact that they were caught in the act by the video footage. This advocates for more video surveillance to be placed in public places in order to stop these types of activities all together or to deter those from doing them. What the public may not know is, in order to provide this level of security video must be recorded at all times.
What the public may not know as well is, advanced computing systems are in place to scan video surveillance footage stored in databases that perform facial recognition as an example. Software is being developed to do advanced mining of data to create maps, pinpoint location, and other highly questionable tasks that if in the wrong hands could spell trouble for anyone’s privacy.
Regardless, you should be made aware that you are under surveillance. This can be done by anyone who is using this technology by posting a sign to let those in the vicinity know that it is taking place. As seen in Figure 6.3, the signs can alert the public that the area that they are in is under surveillance.

Figure 6.3 Video Surveillance Warning Signs
This technology is also considered closed-circuit television (CCTV). CCTV is the technical name for a “network” of video cameras, viewing stations, and a digital video recorder (DVR) system that records, stores, and allows you to retrieve video data. DVR systems that store data generally have hard disks that store the data they record. Since video is generally large in size when stored, the disk drives used to store them need to be large in size. Generally, the quality of the video can be lessened to decrease the amount of size it can be when stored. This will create a problem when forensics is done in a criminal case. It can be argued that the picture is not “clear” so it cannot accurately show the identity of someone accused.
Other types of public surveillance you should be concerned about are with law enforcement. Generally, police officers have recording equipment as part of standard issue on all police cruisers and other transportation equipment. Some enforcement agents also use body worn video cameras to show all actions taken while doing their work. Although this can help the enforcement agent, it can also create issues with privacy on routine stops or if you were suspected but innocent of a crime. The material is still recorded regardless.
According to the American Civil Liberties Union (ACLU), there are major problems with public video surveillance. The opinion is that video cameras and CCTVs are being made more and more of a necessity based on the fear brought on by the media, the government, and the voice of terrorism. Obviously, some form of this security is needed, specifically around high target areas or national landmarks but the proliferation of it to every corner of our lives is deemed ineffective.
As an example, when criminologists and other experts have reviewed cases based on terrorism, video cameras did not deter their consideration or ability to attack at all.
Another concern by the ACLU is that CCTV is prone to serious abuse. For example, in 1997, a police official used information captured by a police database to blackmail patrons of a gay club. Other forms of abuse such as institutional abuse and personal abuse are also possible. Targeting, discrimination, and other concerns also top the list.
The ACLU is also concerned about the lack of limits of controls on camera use, for example, public CCTV systems that can do facial recognition. The US Supreme Court since the late 1960s has used the verbiage “reasonable expectation of privacy” to assist with adding a level of privacy to police searches. The Fourth Amendment to the US Constitution allows for protection against police-based video searches; however, today no rules stop the abuse of CCTV. Some protection against video searches conducted by the police exists, but there are currently no general, legally enforceable rules to limit privacy invasions and protect against abuse of CCTV systems.
Another concern is that growing and uncontrolled use of video surveillance systems will change the face of society as we know it, as public citizens will begin to act differently when they know they are being watched and monitored at all times.
Satellite Surveillance Systems
Government/military agencies use satellite-based surveillance systems to perform reconnaissance operations domestically and globally. One may argue that these systems invade privacy; however, they have also proven to establish and maintain global security. Again, in the wrong hands this information could be problematic for anyone who deem privacy important, but what about security? Let’s discuss an example where these satellite systems have proven to be helpful.
Reconnaissance satellites are generally ones that observe the Earth and can zoom in to view everything and anything from space to Earth’s surface. Generally, used for military operations or law enforcement intelligence, these systems allow for high-resolution viewing, eavesdropping visually, and, at times, with audio and recognition.
As seen in Figure 6.4, the capture of Osama Bin Laden was largely done by observing the compound in which he was suspected (and later found to be inhabiting) via satellite. These same techniques were used in the second Iraq war to find Saddam Hussein.
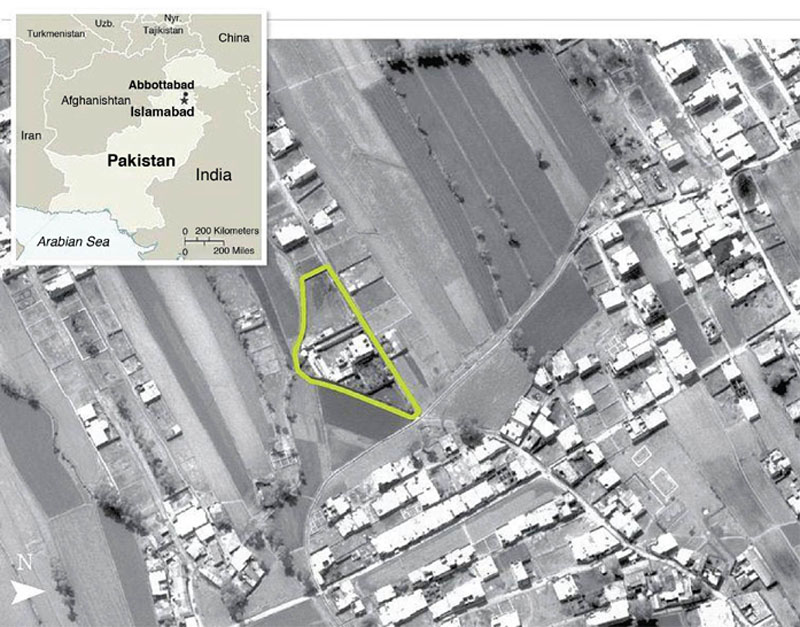
Figure 6.4 Using Satellite for Military Operations
Again, we can see where it is helpful, but this same technology can be used to track anyone, anything, and at any time globally and that when used by a malicious entity could prove to be considerably damaging. On a smaller scale, Google Earth and other tools allow for this level of pinpointing (nonmilitary grade) via latitude and also longitude.
PC devices and webcams
Now that we have reviewed video surveillance and its many applications, we should look at video at the PC level. Web cameras (or webcams for short) are not new and have been around for years. They allow a user of a PC to incorporate video into software on their PC such as Webex, chatting software (such as Apples iChat), and Skype. Although this technology has been in use for years, it has grown to become more of a threat over recent years. As seen in Figure 6.5, the webcam can be a device either mounted on a PC or integrated directly into it.

Figure 6.5 PC Webcams
As this technology has not evolved much since its inception, what has evolved is the nature of the attacks that can be done with it. In 2013, the FBI conducted a probe after Miss Teen USA Cassidy Wolf made a complaint that she had been a victim of sextortion. Later, after the investigation, Jared James Abrahams was arrested for using Blackshades and remotely penetrating her computer and viewing her through her webcam. He made copies of images and sent them to her demanding sexual favors. Cassidy Wolf immediately brought this issue to the authorities and after law enforcement involvement, made the arrest of Abrahams. Abrahams had also pled guilty to not only conducting this operation but also against 100–150 other women.
This highlights the use of creepware, and through this probe and others like it, 90 other people were arrested in a hacker sting of other using this software. During this sweep, the co-creator of Blackshades was also arrested. The remote administration tool (RAT) was used to access the webcams of unsuspecting victims and spy on them. This arrest led to the development of counter-spy software (SnoopWall) that can be used to thwart these types of attacks.
Creepware
According to a report by Symantec (maker of anti-malware software), creepware is a growing issue. Creepware is the buzz word for a RAT used in conjunction with a Trojan to access and control your system without your knowledge. Essentially, it needs to be installed on your system; however, with spoofing e-mail and other common methods, getting it installed is generally not an issue for someone not savvy with keeping their systems clean, those not using anti-malware software, or those just tricked into installing it. Someone could also locally install it without your knowledge.
There are many flavors of the software to include but not limited to Blackshades (W32.Shadesrat), Poison Ivy (Backdoor.Darkmoon), and DarkComet (Backdoor.Krademok). Symantec and other malware fighters have said that you should be aware that the software running can remain undetectable to the common eye and you will need to scan for it to ensure that it gets cleaned off. Obviously, due diligence helps as well – never install something on your system from an untrusted source.
Mobile Devices
Mobile devices pose the same exact threat as PC systems do. Your video camera can be used against you no matter what device you use or what vendor you select. If the device has a camera, software can be installed to use it for malicious reasons. As we covered in Chapter 4, mobile devices can be tracked everywhere they go. Now, you can also install an app on it (hidden of course) and the video can be remotely accessed by an attacker.
Another concept to wrap your head around is just how in depth that spying can go. According to a new research, a form of visual malware (also called PlaceRaider) can be used to create 3D models using your camera to build models of your environment in order to create a map. This highly advanced surveillance tool can be used to reconstruct a physical environment. Because this technology is new and has been created by the US Naval Surface Warfare Center, it is being claimed to be out of reach of the general hacker. This does bring to light that the government, however, can pull off such surveillance should be a concern.
Another concern may be false devices. This may seem very “James Bond” to you, but … dummy devices are used to spy on you as well, such as a fake mobile device that is really a recording device. As seen in Figure 6.6, the wireless charge-coupled device (CCD) spy camera/cell phone CN-SPY008 is a device that contains a color CCD camera and wireless video and audio used to capture data inconspicuously.
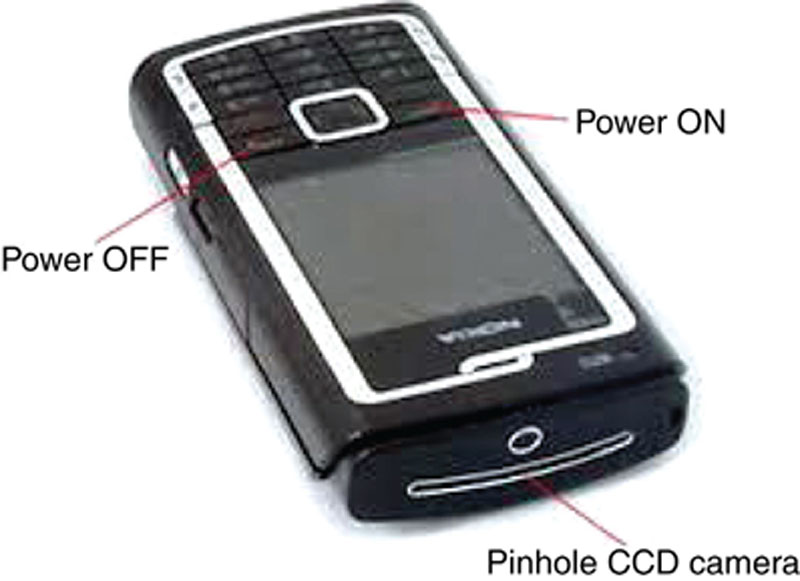
Figure 6.6 A Fake Surveillance Device
All of these devices should concern you. James Bond just became more advanced and anyone with a credit card can find, purchase, and use these stealth devices. Hackers can penetrate your legitimate devices or government agencies can access your devices for information.
Gaming Consoles
One of the biggest and growing threats today is with gaming consoles. Sony Playstation, Nintendo Wii, and Microsoft Xbox are few of the providers of devices that essentially do it all; however, they fly under the radar because they are not generally seen as a mobile device, a PC, or an entertainment system. What is interesting is, they are all three and much more. These gaming consoles have network connectivity, the ability to integrate into your systems and TV, and allow for the same as well as more application usage than all of these devices put together. They fly under the radar because they are generally not viewed as more than just being game consoles.
These devices also ask for your personal information, your financial information, and other data in order to allow you to interact with the vendor to get software, team up with other players, and interact with both vendor and gamers. Having read about all of the threats associated with surveillance thus far, this one should worry you the most. Consider your children use this system in their bedrooms, or perhaps you do. You may be under surveillance.
Microsoft’s Xbox (360 and now Xbox One) uses a motion detection system that functions off of a video camera called the Kinect. As seen in Figure 6.7, the Kinect can capture motion, allow players to view each other, and much more.

Figure 6.7 Microsoft’s Xbox Kinect System
According to researchers, this platform is considered highly sensitive to causing privacy issues. Children use it, it’s located in private locations in the home, it’s not secure by default … these are but a few of the high-level concerns many have about the system.
The system has also been found to be crawling with child predators and has even been considered to be a channel in which terrorists communicate. Because of this issue, earlier this year, Edward Snowden released that the UK version of the NSA (GCHQ) had considered using the Kinect for mass surveillance. The program called “Optic Nerve” was said to have targeted over a million users for facial recognition database collection. Because of this release of information, Microsoft responded that they did not authorize this and that they were concerned. Their response would be to expand their use of encryption and bolster security. It should be considered that the Xbox One now ships with the Kinect by default and has already sold millions of units. This means that these systems are everywhere and could potentially be used as a surveillance tool. The Xbox One has additional privacy controls that can be used; however, the question of how safe it really is still remains.
This can be said for any game console that allows for video interaction. As more and more consoles are shipped with interactive gear, this threat only grows. To mitigate these threats beyond applying controls to them, simply not using them is advised and/or if your children use them ensure that they only use them under supervision, with privacy controls enabled, and in a common area in the home.
Legal and ethical concerns
In this section, we will review case law in regard to how webcams can be used to spy against individuals and how they are brought forth in a court of law. In the following case, we will read about the Plaintiff Mr. Lammle who filed a claim against his then employer, the defendant, Ball Aerospace & Technologies Corporation, when Mr. Lammle was informed that his position had been filled after taking two separate leaves of absence.
Among other claims, Mr. Lammle also alleged that he was “falsely accused” of sleeping on the job and a webcam allegedly was used to spy on him. Mr. Lammle did not come forth with any evidence to establish the truth of each of these allegations.
In conclusion, the Defendant’s Motion for Summary Judgment is granted. “Judgment shall enter in favor of the Defendant on all of the Plaintiff’s claims, and the Clerk of the Court shall close this case.”
Summary
The increased use of mobile devices with cameras, PCs with webcams, and camera systems installed at homes, businesses, and out in the general public are growing at an alarming rate, and the threats are growing to expose security issues with them that violate your privacy. In this chapter, we have looked at the growing use of this technology, what the technology is capable of, what purposes are served for good and evil, and why we should be concerned.
As we discussed these topics and how they relate to reconnaissance and surveillance, it will become evident that you are now always on camera. We carry one with us everywhere we go. There tends to be a camera located everywhere. Let’s consider this example: You wake up and get ready for work, while in your home you are on camera as your home has an active internal security surveillance system. You check your e-mail before you leave the house on your laptop configured with a webcam. You pack up to leave and grab your mobile phone and tablet and get into your car. Your drive to work roughly passing 10 traffic lights before pulling in and parking in the parking garage. There is video surveillance feeds in the garage. You enter work and each entrance/exit and floor contains surveillance equipment. You dock your work laptop (with integrated webcam) and get to work briefly checking your mobile devices that are sitting directly next to you. Each time you leave your desk to move within the office, you take your phone with you. You leave for lunch and go to mall to eat in the food court with a few friends. The mall has video surveillance feeds. After work, you drive back home (10 traffic lights) and settle in for the evening. After dinner, you decide to load a game on your Microsoft Xbox and join a few friends online to play games. Later, you check your social media sites online and Skype with a friend.
We can go on and on but I think you get the picture. You are on camera 24 hours a day and this does not include the government’s ability to pinpoint and track your whereabouts via satellite. This does not include military or law enforcement being able to use satellite tracking. In this chapter, we discussed all of the ways you may or may not know you are being captured on the camera and how you protect yourself. Digital surveillance is here to stay and will probably become more invasive over time, so learning how to mitigate threats and being aware of new threats is the key to regaining your privacy.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
