Chapter 5
Physical Device Tracking
Abstract
This chapter explains how to track movement and activity through a physical tracking device. It also covers the different tracking devices and Web consoles used for tracking and locating.
Keywords
Physical tracking
Tracking device
Health trackers
Wearable Technology
Location services
RFID
iCloud
Device fingerprint
Asset tracking
Pedometers
Smartwatch
Physical tracking
In the previous chapter, we covered the fundamentals of tracking and focused on the mobile device that is likely to be your cell phone, although we find ourselves carrying it or within devices that can also be tracked, such as your car. We carry our cell phones everywhere we go, which basically gives those with access a clear line of sight into your movement, activities, communications, and more. However, beyond the cell phone, we use many other products, services, devices, and applications that also track our behavior. In this chapter, we will look at not only the mobile phone but also other mobile devices that can be tracked. We will also look at other devices that you may not know can be tracked, such as your vehicle.
Another interesting trend emerging in today’s technology is the “physical tracking” of items with devices. Other devices also exist that help those who are forgetful. New devices are coming to market that allow you to place trackers on items you would normally misplace, for example, a set of keys. More commonly, tools are being sold to “track your pets” with sensors that only operate with Bluetooth and can only be tracked so far; some offerings can track you within larger radiuses. Another growing trend is with wearable technology where a new market has opened. This technology allows tracking and the data collected is used with an application so that you can track your health, diet, and medical condition. As shown in Figure 5.1, the number of devices coming to market to “track” a plethora of things, such as health, is increasing exponentially.

Figure 5.1 Health Tracker
Other physical tracking such as finding a lost phone has been around for some time now; however, the technology has been evolving. By registering a device online, offerings such as Apple’s MobileMe (iCloud) allows for the recovery of a lost or stolen device by tracking it. Our vehicles are now coming equipped from the factory with tracking devices installed in them. LoJack, which has been around for years, is also another form of advanced anti-theft device that allows tracking and recovery of a stolen car. LoJack can also be used with other devices such as laptops. Surveillance gear to track someone physically is also emerging, such as universal serial bus (USB) devices, that can be placed within a car or on a person (perhaps in a pocketbook) to track movement of an individual without their knowledge.
As you can see, tracking is nothing new and it’s growing at an alarming rate. It’s growing in availability and ease of use. It’s being offered as a service for the forgetful and appearing as a standard feature in devices everywhere. This goes beyond the tracking being done without your knowledge. Within the chapter, we will also make reference to tracking without technology, stalking, etc.; however, the bulk of this chapter will revolve around the technical tracking devices used to physically bug you with or without your knowledge.
Device fingerprint
When you are charged with a crime and go through the process of getting fingerprinted, your details are added to a database so that you can be tracked. As fingerprints are unique to an individual, it seems likely that if you are caught after being fingerprinted, you can be a possible target of investigation if your prints show up at another crime scene. Similar to physical human fingerprinting, devices can also leave a unique mark.
With technology, you need to understand that there are unique characteristics that pinpoint or associative you to a device.
As you can see, tracking is done every day, in many ways so that devices you use, places you go, and things you buy can all be tracked. It is possible that when you leave your home in the morning and go to work – go out to lunch and then back to work and return home – your entire day and everything you have done can be tracked. The credit cards you used, the calls you made, and the ticket you got on a busy intersection can all be used to track your patterns, your movements, and your ultimate location.
The lines can blur as well; fingerprint device can be used to access systems through biometrics. Although this topic is outside the range of topics we cover in this book, it should be noted that biometric devices use fingerprint data, as shown in Figure 5.2, where the biometric device can be seen in a Windows Device Manager.
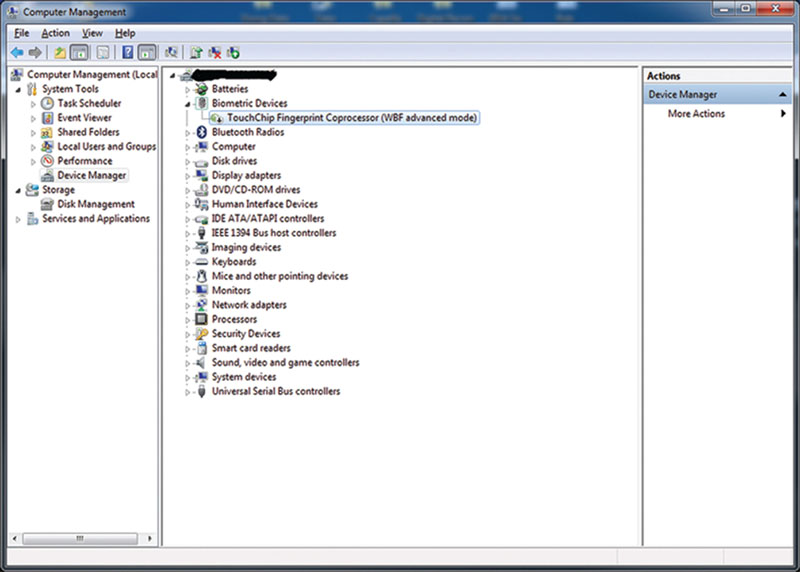
Figure 5.2 Biometric Device
This is a way to mitigate your device being accessed, which will only allow you access into it based on your biometric credentials.
Tracking for Reconnaissance Today
As we can see, tracking can be done without your knowledge and at many different levels. Your mobile device, although helpful and a needed fixture of your person, is now a mobile tracking device that can be used to find you, evade your privacy at any moment, or as a tracking tool for another malicious user, stalker, attacker, or threat.
Before we get into how to track a phone, for example, it’s important to understand the first steps to protecting yourself as much as possible. First, do not leave your phone unattended. Do not leave it unlocked. Do not leave it without a password. Use a strong password scheme. Make sure that nobody is shoulder surfing you when you use your phone. In Chapter 8, mitigation strategies will be covered in detail; however, it’s important to note here that by practicing simple security steps, such as those listed above, you lessen the attack surface significantly.
Before we get to mitigation, let’s recapitulate what we have learned in earlier chapters about why someone would track you in the first place. Tracking is done for good reasons and on purpose. As a company, we need to know how many units we sold this quarter for financial statements. We track the units, the progress, and so on. This can be manipulated, however, for example, if we wanted to see what demographic purchased specific units and then we build a campaign to market to the specific demographic. This is good but questionable. This is a good example of simple tracking for logistical purposes turned into a marketing campaign. Another good reason would be hospitals that do bed tracking to keep inventory of their patients. They can use chips such as radio-frequency identification (RFID) to do this tracking. We also have to consider patient security and confidentiality. We can encrypt or secure this data to ensure safety. What if this information got into the wrong hands? Now we can start to see how good tracking can be further manipulated into a danger zone. As shown in Figure 5.3, the number of devices using RFID is increasing and allowing for advanced tracking of devices.

Figure 5.3 RFID Tracking
How can this type of tracking be used for bad? It can be turned into malicious intent when the tracking is used for surveillance and reconnaissance of targets such as people simply using their mobile phones. They may turn on location tracking so that they can allow applications on their devices to assist with finding things and giving specific directions, for example, but what if that location-based service (LBS) was used to further exploit buying patterns. What if it was used to track location? What if it got into the wrong hands?
Bad reasons … and there are many, need to be considered when you think about how to safeguard your identity and privacy. Reconnaissance and surveillance techniques used to gather information about a target are nothing more than the exploitation of information that can be gathered through the myriad of ways available. The ability to track a target today is exponentially growing easier as more and more users move to mobile devices and more and more devices come to market to allow for tracking abilities. A rule of thumb is to limit your exposure. Only use what you need and be cautious. Think about why you want to use a service, device, or application before using it and consider the risks. Also apply common sense to every situation you are in.
Application Installation Versus Physical Device
There are also different ways in which you can be tracked; some ways are application specific and others are physical device specific. If you access a server to download files, you likely do this via an IP-based device that then connects to another IP-based device. Yes, the addressing can be spoofed; however, this can be easily mitigated if you know what to look for. Also, you need to consider that every movement you make in an application-centric world can be logged, which allows system administrators to look through logs and review activity. If you are at work and visit a questionable website against company policy, it’s likely that you can and will be found doing so.
So what about physical devices? In this section, we will review some of the devices that you can use to track things; however, some of them can also track you!
As shown in Figure 5.4, the number of devices coming to market that people are wearing and carrying is becoming a concern to those who want to maintain privacy. With physical devices, you find that they can be clipped anywhere and can perform functions such as tracking your blood pressure or how far you have walked; however, it is when it is married to an application that the concern should set in.

Figure 5.4 Physical Tracking Devices
As shown in Figure 5.5, the physical devices (such as ones people may put on their pet) can be tracked through the Internet (the cloud) to a computer of mobile device. Once it does so, it can then be tracked with all of the fingerprinting information we mentioned earlier.
Figure 5.5 Tracking Through the Cloud
Physical and application tracking is beginning to blur. You can, in fact, place a physical tracking device in the car of an unsuspected person (perhaps your significant other) to track their whereabouts, but it’s not until this device is viewed in an application console or the device is linked to an application that you can view the tracking information. Therefore, it should be noted that physical and application-based (or logical) tracking go hand in hand when tracking targets today.
Physical Device Tracking
There are many ways tracking can be accomplished. If the device is Bluetooth-based, it will emit a signal to other devices and those can be tracked by the system. If wireless, it will use 802.11-based technologies to be tracked by the central system. A global positioning system (GPS) is used to pinpoint the physical device location directly or through triangulation. As discussed earlier in this chapter, a GPS can use a satellite or a series of satellites to track movement of a device. For good purposes, GPS can provide you with mapping data for trips as well as to find a lost device. However, for malicious purposes, GPS can show an attacker your exact position worldwide. Geolocation data can also be used to track device usage by using information from other sources. TCP/IP can be used to assist with Geolocation. IP addresses can be tracked if it’s an IP-based system.
As shown in Figure 5.6, the devices that can be used for tracking may use different technologies to allow for target tracking. For example, some are USB devices that, once placed, need to be retrieved. Some use GPS technology to communicate with a server that can allow it to be tracked and mapped.

Figure 5.6 Wireless Tracker
Physical device tracking is a concern for those who are being stalked. For example, if an attacker is interested in learning your location, where you go and what you do, and wants to track you, they simply need to place a tracking device on you or in something you own, such as your car. You may never find it if it is placed in your car. An example could be, if a significant other wanted to see where you go on while you say you are at work. Are you stopping by a motel during the day? The physical tracker could give your location.
Some technologies are used for purposes of locating trucks in a fleet, as shown in Figure 5.7. Asset tracking is used to ensure that a fleet of trucks can be mapped and monitored for many purposes, one being to be able to give the customer accurate shipping information. It can also be used in emergencies.

Figure 5.7 Fleet Location Tracking
As we can see, tracking is only bad when maliciously used but it’s hard to control. It really depends on who uses the technology and why they use it – are they using it for the wrong reason? Then it is considered a problem. That being said, we really need to understand the fundamentals of being safe with the technical landscape growing toward allowing ourselves to be tracked.
You should always consider that you can and will be tracked. This should give you the edge you need to check yourself for tracking devices. Consider that you should always review what “tracking” you will allow of yourself with tracking technology. For example, if you use a health tracker, does it contain sensitive information you do not want to share? If this device connects to an application, do you want it to save this information? Where is it saved? On a central database server? Who has access to this data? As shown in Figure 5.8, the devices that map your location are always targets of misuse. You can quickly use a device on your phone that allows the tracking of your exact location at all times.
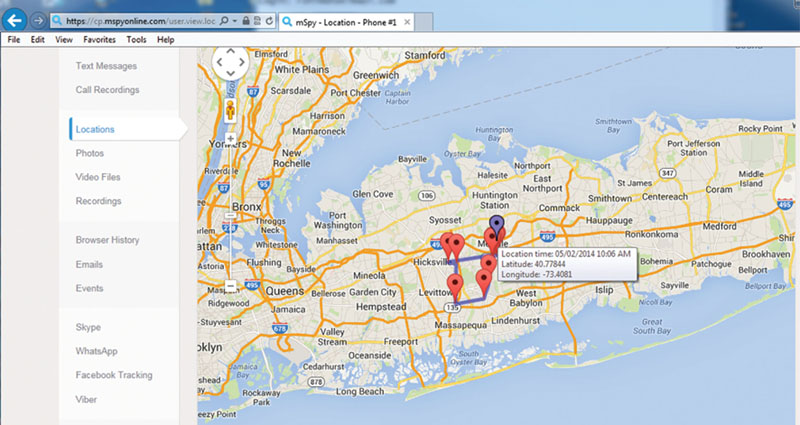
Figure 5.8 Physical Location Tracking Via Console
When using LBS, GPS, or any other application that uses a positioning and locating system, you can quickly become the target of another person or group. We discussed in earlier chapters how the government can track your activity and location, so consider it possible that others can too. When you sign on to Facebook, it tracks the device in which you signed in to it with. Facebook calls it security; however, it can be considered privacy infringement.
As shown in Figure 5.9, the mapping that can be done when you are being tracked is significant. For example, you can be tracked based on pattern. Your work routine, where you shop, and what main roads you take. As an example, it could be found that you take the same major road to work every day and are usually in the location at a specific time.
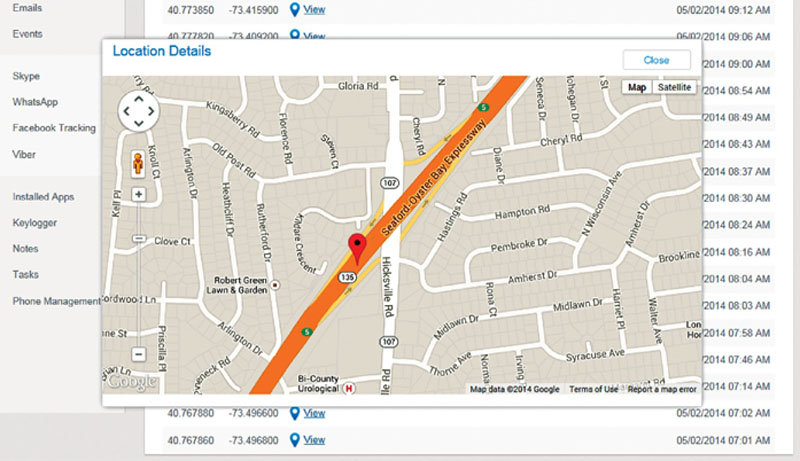
Figure 5.9 Pinpointing Location
This level of tracking is concerning. What if this information got into the wrong hands? What if someone is doing this without your knowledge? These are all the reasons why you should always consider the risks when using tracking devices. You can always review your devices (or choose not to use them) for tracking. Yes, your phone could still be tracked, we made this clear; however, you could also check for extra applications or services (such as LBS) that can help track you.
The best way to stay anonymous is, if you do not want to be tracked, leave your mobile device (and all tracking devices) at home when you leave the house. Consider that you will be on video camera and you could be tracked in your vehicle (license plate is a fingerprint), for example; however, you could take the bus. Disguise yourself. Sounds pretty crazy, doesn’t it? That’s because it is – you literally have to strip yourself of any traceable devices and travel in disguise to remain anonymous!
The only way to mitigate this threat is to limit exposure. Consider and weigh the risks of using tracking technology. Do not leave your car unlocked and do not leave your purse out of sight. Do spot checks. Leave your phone locked and on your person. Be slightly paranoid to remain safe.
Safe Devices Used Against You
Although we have talked about how physical devices used for good can be used maliciously, we have not talked about the new breed of technology that is also becoming more prevalent. Wearable technology is becoming more than a fad; it’s becoming what we will be using in the future almost exclusively. As wearable technology starts to increase in popularity and becomes more important in our work and our personal lives, as security professionals we need to prepare for the coming storm.
As shown in Figure 5.10, the devices that track your heart rate, what you ate for lunch, how far you have walked, and what your emotional state was today are being developed into wearable technology fused with application-specific back-ends that manipulate this data.

Figure 5.10 Wearable Technology
As with any new technology, we must always be considerate of accidental or malicious access, leak, or corruption of data. Wearable technology is today’s mobile laptop from years ago. When laptops first came to light and “going mobile” seemed brand new, laptop drives were fully encrypted. Now we make sure that we do so in case the laptop is stolen. We will be able to do this as well with wearable technology; however, what is more concerning is its ability to “track” your location, which is our focus. Pedometer use is growing as more people become health conscious. This means that an application tracks where you go and how long it took you to get there. This is data that in the wrong hands could be used against you. As shown in Figure 5.11, new technology is allowing you to track your health, for example, your blood pressure. What if you didn’t want anyone to know you had a heart condition? High blood pressure? Well, you’re recording this information in a tracking device that, if it got into the wrong hands, could be used against you.

Figure 5.11 Wearable Technology
The answer to this dilemma is to encrypt the data. In order to protect against data breaches outside of tracking your location, you need to ensure that all the data collected is secure. The threat is at the network layer, wherein in few instances, these devices use Bluetooth that could connect and emit data to other Bluetooth-enabled devices (or emitters) and send and receive data. As shown in Figure 5.12, the devices you wear could transmit data to unauthorized devices and your protected data can be stolen in real time before it can be secured without your knowledge.

Figure 5.12 Wearable Technology
It is also possible to gather location information in this fashion. That being said, these devices (such as smartwatches) could also be used for spying. For example, someone may be checking their time and, unbeknown to you, taking your picture or recording video or audio.
Other devices, such as the ones shown in Figure 5.13, can be used to track your luggage, which, if in the wrong hands, can show your vacation patterns; this becomes good for those who are looking to commit crimes against your home and personal belongings when you are away. What is worse than leaving your light on a timer to show that you are at home when in fact your wearable technology tells an attacker a different story! That is, if you didn’t post pictures of you on vacation on Facebook while you are out of town.

Figure 5.13 Wearable Technology
These threats are still under review and security systems will be built to ensure safety, but But this does not mean we are there yet nor does it mean you should bypass protecting yourself until it is. To mitigate against wearable technology threats, you should consider protecting yourself.
Location Tracking and Wearable Technology
Embedded within the mobile phones technology is a service called LBS; it is growing in popularity with wearable technology, specifically Google Glass and smartwatches. This allows location data to assist with providing enhanced functionality. The applications are developed so that you do not have to input information; the information required is simply queried from your device. As we discussed, in Apple’s iPhone, the operation system (iOS) is deployed with a standard LBS functionality that allows applications to be able to track where you are and report it to the querying application. Maps can use LBS to track your current location on a map for the purpose of making your life easier.
As shown in Figure 5.14, the growth of smartwatches has begun and they will soon be mobile computing devices with the same baked-in technology of most tablets or smartphones. That being said, LBS will need to be disabled or refined within them as well. Yes, you still need to consider and mitigate threat with Bluetooth; however, location tracking of your smartwatch is also a concern today.

Figure 5.14 Using Smartwatches (Casio)
Today, we are watching smartwatches evolving quickly. Google Android is currently leading the effort with their smartwatch offerings. As with mobile devices (phones and tablets), they are still vulnerable to penetration and could be hijacked and manipulated by an attacker. They can also track your location. As shown in Figure 5.15, the smartwatch does not look like a mobile device; however, it is a computer-based mobile device that you wear as a watch.

Figure 5.15 Using Smartwatches (FiLIP)
As a final example, the FiLIP smartwatch is used by parents to help track a child’s location. You can program this limited use phone for a child so that it contains a few numbers and can be dialed easily, especially in an emergency; however, what it does do well is help you track the location of your child. This technology is continuing to grow and you should not only be prepared for it, but you should embrace it because it is not going away. You can limit your exposure to it by awareness that is what we intend to show you in this chapter. You can secure your privacy but you need to know the difference between how technology can be misused, what the threats are, and mitigate them if possible.
Legal and ethical concerns
As explained in this chapter, tracking is done with ease and we, as consumers, can make it even easier. Although we await more cyberlaw-related crime in this arena, we can review some of the other cases that are brought to light where even companies such as Microsoft are involved in a civil action. In this case, Microsoft was accused of cybertracking. Although this case seems baseless, it shows that more case law will be coming in the future based on wearable technology, especially Google Glass.
The following memorandum from the US District Court, Eastern District of Pennsylvania, involves the plaintiff Antonio A. Ransom who brought a civil action against Microsoft (Bill Gates), William Clark, Diondre King, Beyock Williams, and Neicy Clerk alleging that the defendants could run electricity through his heart to produce a heart attack, and that the defendants “put him on the Internet and kept track of him.” Ransom asks to the court to order the defendants to stand trial for cyber stalking, electronic harassment, body electronic surveillance, and torture interference.
The court dismissed the complaint as factually and legally frivolous. Ransom will not be given leave to amend because amendment would be futile.
Summary
In this chapter, we discussed the threats associated with tracking, wearable technology, and why you should be concerned. In previous chapters, we covered the fundamentals of tracking and focused on the mobile device that is likely to be your cell phone, although we find ourselves carrying it or within devices that can also be tracked, such as your car. We carry our cell phones everywhere we go that basically gives those with access a clear line of sight into your movement, activities, communications, and more. However, beyond the cell phone, there are many other products, services, devices, and applications we use that also track our behavior. In this chapter, we looked at not only the mobile phone but also other mobile devices that can be tracked. We also looked at other devices that you may not know can be tracked, such as your vehicle.
Another interesting trend emerging in today’s technology is the “physical tracking” of items with devices. Other devices exist that help those who are forgetful. New devices are coming to market that allow you to place trackers on items you would normally misplace, for example, a set of keys. More commonly, tools are being sold to “track your pets” with sensors that only operate with Bluetooth and can only be tracked so far; some offerings can track you within larger radiuses. Another growing trend is with wearable technology where a new market has opened. This technology will allow tracking and the data collected is used with an application so you can track your health, diet, and medical condition. In sum, you should attempt to limit your digital footprint, always be concerned about how much information you share, and be cautious of how much you expose yourself and your data to those not privy.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
