Physical Security Essentials
William Stallings, Independent consultant
Most people think about locks, bars, alarms, and uniformed guards when they think about security. While these countermeasures are by no means the only precautions that need to be considered when trying to secure an information system, they are a perfectly logical place to begin. This chapter discusses physical security and with some overlapping areas of premises security. Physical security is a vital part of any security plan and is fundamental to all security efforts–without it, cyber security, software security, user access security, and network security are considerably more difficult, if not impossible, to initiate. Physical security refers to the protection of building sites and equipment (and all information and software contained therein) from theft, vandalism, natural disaster, manmade catastrophes, and accidental damage (from electrical surges, extreme temperatures, and spilled coffee). It requires solid building construction, suitable emergency preparedness, reliable power supplies, adequate climate control, and appropriate protection from intruders.
Keywords
physical security; logical security; premises security; cyber security; information system hardware; physical facility; supporting facilities; personnel; environmental threats; technical threats; human caused threats
Platt1 distinguishes three elements of information system (IS) security:
• Logical security. Protects computer-based data from software-based and communication-based threats.
• Physical security. Also called infrastructure security. Protects the information systems that house data and the people who use, operate, and maintain the systems. Physical security must also prevent any type of physical access or intrusion that can compromise logical security.
• Premises security. Also known as corporate or facilities security. Protects the people and property within an entire area, facility, or building(s) and is usually required by laws, regulations, and fiduciary obligations. Premises security provides perimeter security, access control, smoke and fire detection, fire suppression, some environmental protection, and usually surveillance systems, alarms, and guards.
This chapter is concerned with physical security and with some overlapping areas of premises security. We begin by looking at physical security threats and then consider physical security prevention measures.
1 Overview
For information systems, the role of physical security is to protect the physical assets that support the storage and processing of information. Physical security involves two complementary requirements. First, physical security must prevent damage to the physical infrastructure that sustains the information system. In broad terms, that infrastructure includes the following:
• Information system hardware. Including data processing and storage equipment, transmission and networking facilities, and offline storage media. We can include in this category supporting documentation.
• Physical facility. The buildings and other structures housing the system and network components.
• Supporting facilities. These facilities underpin the operation of the information system. This category includes electrical power, communication services, and environmental controls (heat, humidity, etc.).
• Personnel. Humans involved in the control, maintenance, and use of the information systems.
Second, physical security must prevent misuse of the physical infrastructure that leads to the misuse or damage of the protected information. The misuse of the physical infrastructure can be accidental or malicious. It includes vandalism, theft of equipment, theft by copying, theft of services, and unauthorized entry.
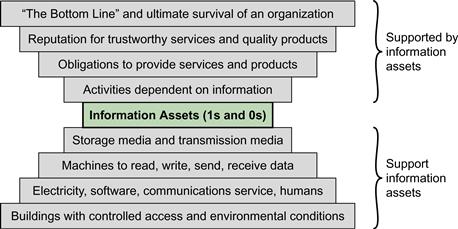
Figure 4.1, based on Bosworth and Kabay2 , suggests the overall context in which physical security concerns arise. The central concern is the information assets of an organization. These information assets provide value to the organization that possesses them, as indicated by the upper four items in Figure 4.1. In turn, the physical infrastructure is essential to providing for the storage and processing of these assets. The lower four items in Figure 4.1 are the concern of physical security. Not shown is the role of logical security, which consists of software- and protocol-based measures for ensuring data integrity, confidentiality, and so forth.
The role of physical security is affected by the operating location of the information system, which can be characterized as static, mobile, or portable. Our concern in this chapter is primarily with static systems, which are installed at fixed locations. A mobile system is installed in a vehicle, which serves the function of a structure for the system. Portable systems have no single installation point but may operate in a variety of locations, including buildings, vehicles, or in the open. The nature of the system’s installation determines the nature and severity of the threats of various types, including fire, roof leaks, unauthorized access, and so forth.
2 Physical Security Threats
In this pat of the chapter, we first look at the types of physical situations and occurrences that can constitute a threat to information systems. There are a number of ways in which such threats can be categorized. It is important to understand the spectrum of threats to information systems so that responsible administrators can ensure that prevention measures are comprehensive. We organize the threats into the following categories:
We begin with a discussion of natural disasters, which are a prime, but not the only, source of environmental threats. Then we look specifically at environmental threats, followed by technical and human-caused threats.
Natural Disasters
Natural disasters are the source of a wide range of environmental threats to datacenters, other information processing facilities, and their personnel. It is possible to assess the risk of various types of natural disasters and take suitable precautions so that catastrophic loss from natural disaster is prevented.
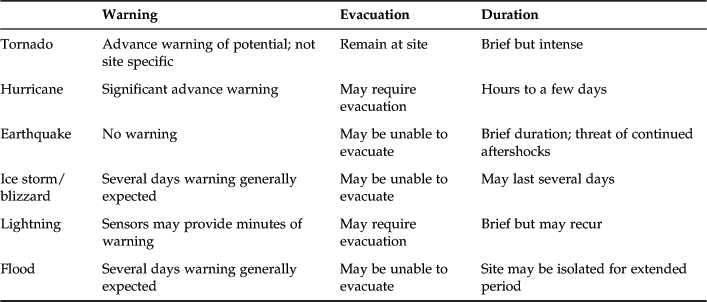
Table 4.1 lists six categories of natural disasters, the typical warning time for each event, whether or not personnel evacuation is indicated or possible, and the typical duration of each event. We comment briefly on the potential consequences of each type of disaster.
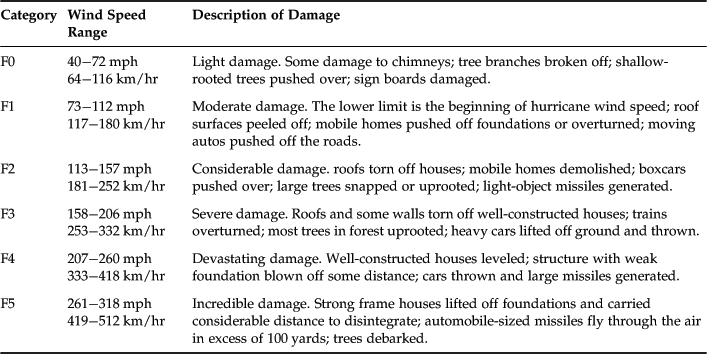
A tornado can generate winds that exceed hurricane strength in a narrow band along the tornado’s path. There is substantial potential for structural damage, roof damage, and loss of outside equipment. There may be damage from wind and flying debris. Off site, a tornado may cause a temporary loss of local utility and communications. Offsite damage is typically followed by quick restoration of services. Tornado damage severity is measured by the Fujita Tornado Scale (see Table 4.2).
Hurricanes, tropical storms, and typhoons, collectively know as tropical cyclones, are among the most devastating naturally occurring hazards. Depending on strength, cyclones may also cause significant structural damage and damage to outside equipment at a particular site. Off site, there is the potential for severe regionwide damage to public infrastructure, utilities, and communications. If on-site operation must continue, then emergency supplies for personnel as well as a backup generator are needed. Further, the responsible site manager may need to mobilize private poststorm security measures, such as armed guards.
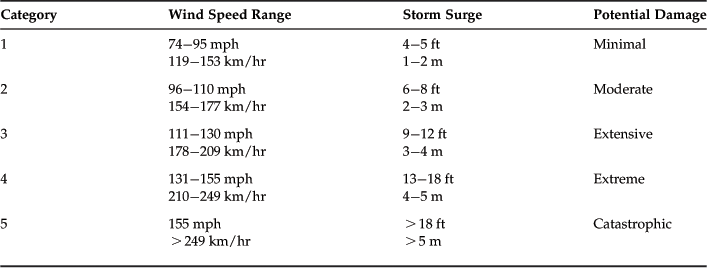
Table 4.3 summarizes the widely used Saffir/Simpson Hurricane Scale. In general, damage rises by about a factor of four for every category increase.
A major earthquake has the potential for the greatest damage and occurs without warning. A facility near the epicenter may suffer catastrophic, even complete, destruction, with significant and long-lasting damage to datacenters and other IS facilities. Examples of inside damage include the toppling of unbraced computer hardware and site infrastructure equipment, including the collapse of raised floors. Personnel are at risk from broken glass and other flying debris. Off site, near the epicenter of a major earthquake, the damage equals and often exceeds that of a major hurricane. Structures that can withstand a hurricane, such as roads and bridges, may be damaged or destroyed, preventing the movement of fuel and other supplies.
An ice storm or blizzard can cause some disruption of or damage to IS facilities if outside equipment and the building are not designed to survive severe ice and snow accumulation. Off site, there may be widespread disruption of utilities and communications and roads may be dangerous or impassable.
The consequences of lightning strikes can range from no impact to disaster. The effects depend on the proximity of the strike and the efficacy of grounding and surge protector measures in place. Off site, there can be disruption of electrical power and there is the potential for fires.
Flooding is a concern in areas that are subject to flooding and for facilities that are in severe flood areas at low elevation. Damage can be severe, with long-lasting effects and the need for a major cleanup operation.
Environmental Threats
This category encompasses conditions in the environment that can damage or interrupt the service of information systems and the data they house. Off site, there may be severe regionwide damage to the public infrastructure and, in the case of severe hurricanes, it may take days, weeks, or even years to recover from the event.
Inappropriate Temperature and Humidity
Computers and related equipment are designed to operate within a certain temperature range. Most computer systems should be kept between 10 and 32 degrees Celsius (50 and 90 degrees Fahrenheit). Outside this range, resources might continue to operate but produce undesirable results. If the ambient temperature around a computer gets too high, the computer cannot adequately cool itself, and internal components can be damaged. If the temperature gets too cold, the system can undergo thermal shock when it is turned on, causing circuit boards or integrated circuits to crack.
Another temperature-related concern is the internal temperature of equipment, which can be significantly higher than room temperature. Computer-related equipment comes with its own temperature dissipation and cooling mechanisms, but these may rely on, or be affected by, external conditions. Such conditions include excessive ambient temperature, interruption of supply of power or heating, ventilation, and air-conditioning (HVAC) services, and vent blockage.
High humidity also poses a threat to electrical and electronic equipment. Long-term exposure to high humidity can result in corrosion. Condensation can threaten magnetic and optical storage media. Condensation can also cause a short circuit, which in turn can damage circuit boards. High humidity can also cause a galvanic effect that results in electroplating, in which metal from one connector slowly migrates to the mating connector, bonding the two together.
Very low humidity can also be a concern. Under prolonged conditions of low humidity, some materials may change shape and performance may be affected. Static electricity also becomes a concern. A person or object that becomes statically charged can damage electronic equipment by an electric discharge. Static electricity discharges as low as 10 volts can damage particularly sensitive electronic circuits, and discharges in the hundreds of volts can create significant damage to a variety of electronic circuits. Discharges from humans can reach into the thousands of volts, so this is a nontrivial threat. In general, relative humidity should be maintained between 40% and 60% to avoid the threats from both low and high humidity.
Fire and Smoke
Perhaps the most frightening physical threat is fire. It is a threat to human life and property. The threat is not only from the direct flame but also from heat, release of toxic fumes, water damage from fire suppression, and smoke damage. Further, fire can disrupt utilities, especially electricity.
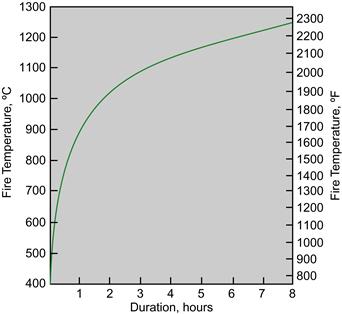
The temperature due to fire increases with time, and in a typical building, fire effects follow the curve shown in Figure 4.2. The scale on the right side of Figure 4.2 shows the temperature at which various items melt or are damaged and therefore indicates how long after the fire is started such damage occurs.
Smoke damage related to fires can also be extensive. Smoke is an abrasive. It collects on the heads of unsealed magnetic disks, optical disks, and tape drives. Electrical fires can produce an acrid smoke that may damage other equipment and may be poisonous or carcinogenic.
The most common fire threat is from fires that originate within a facility, and, as discussed subsequently, there are a number of preventive and mitigating measures that can be taken. A more uncontrollable threat is faced from wildfires, which are a plausible concern in the western United States, portions of Australia (where the term bushfire is used), and a number of other countries.
Water Damage
Water and other stored liquids in proximity to computer equipment pose an obvious threat. The primary danger is an electrical short, which can happen if water bridges between a circuit board trace carrying voltage and a trace carrying ground. Moving water, such as in plumbing, and weather-created water from rain, snow, and ice also pose threats. A pipe may burst from a fault in the line or from freezing. Sprinkler systems, despite their security function, are a major threat to computer equipment and paper and electronic storage media. The system may be set off by a faulty temperature sensor, or a burst pipe may cause water to enter the computer room. For a large computer installation, an effort should be made to avoid any sources of water from one or two floors above. An example of a hazard from this direction is an overflowing toilet.
Less common but more catastrophic is floodwater. Much of the damage comes from the suspended material in the water. Floodwater leaves a muddy residue that is extraordinarily difficult to clean up.
Chemical, Radiological, and Biological Hazards
Chemical, radiological, and biological hazards pose a growing threat, both from intentional attack and from accidental discharge. None of these hazardous agents should be present in an information system environment, but either accidental or intentional intrusion is possible. Nearby discharges (from an overturned truck carrying hazardous materials) can be introduced through the ventilation system or open windows and, in the case of radiation, through perimeter walls. In addition, discharges in the vicinity can disrupt work by causing evacuations to be ordered. Flooding can also introduce biological or chemical contaminants.
In general, the primary risk of these hazards is to personnel. Radiation and chemical agents can also cause damage to electronic equipment.
Dust
Dust is a prevalent concern that is often overlooked. Even fibers from fabric and paper are abrasive and mildly conductive, although generally equipment is resistant to such contaminants. Larger influxes of dust can result from a number of incidents, such as a controlled explosion of a nearby building and a windstorm carrying debris from a wildfire. A more likely source of influx comes from dust surges that originate within the building due to construction or maintenance work.
Equipment with moving parts, such as rotating storage media and computer fans, are the most vulnerable to damage from dust. Dust can also block ventilation and reduce radiational cooling.
Infestation
One of the less pleasant physical threats is infestation, which covers a broad range of living organisms, including mold, insects, and rodents. High-humidity conditions can lead to the growth of mold and mildew, which can be harmful to both personnel and equipment. Insects, particularly those that attack wood and paper, are also a common threat.
Technical Threats
This category encompasses threats related to electrical power and electromagnetic emission.
Electrical Power
Electrical power is essential to the operation of an information system. All the electrical and electronic devices in the system require power, and most require uninterrupted utility power. Power utility problems can be broadly grouped into three categories: undervoltage, overvoltage, and noise.
An undervoltage occurs when the IS equipment receives less voltage than is required for normal operation. Undervoltage events range from temporary dips in the voltage supply to brownouts (prolonged undervoltage) and power outages. Most computers are designed to withstand prolonged voltage reductions of about 20% without shutting down and without operational error. Deeper dips or blackouts lasting more than a few milliseconds trigger a system shutdown. Generally, no damage is done, but service is interrupted.
Far more serious is an overvoltage. A surge of voltage can be caused by a utility company supply anomaly, by some internal (to the building) wiring fault, or by lightning. Damage is a function of intensity and duration and the effectiveness of any surge protectors between your equipment and the source of the surge. A sufficient surge can destroy silicon-based components, including processors and memories.
Power lines can also be a conduit for noise. In many cases, these spurious signals can endure through the filtering circuitry of the power supply and interfere with signals inside electronic devices, causing logical errors.
Electromagnetic Interference
Noise along a power supply line is only one source of electromagnetic interference (EMI). Motors, fans, heavy equipment, and even other computers generate electrical noise that can cause intermittent problems with the computer you are using. This noise can be transmitted through space as well as nearby power lines.
Another source of EMI is high-intensity emissions from nearby commercial radio stations and microwave relay antennas. Even low-intensity devices, such as cellular telephones, can interfere with sensitive electronic equipment.
Human-Caused Physical Threats
Human-caused threats are more difficult to deal with than the environmental and technical threats discussed so far. Human-caused threats are less predictable than other types of physical threats. Worse, human-caused threats are specifically designed to overcome prevention measures and/or seek the most vulnerable point of attack. We can group such threats into the following categories:
• Unauthorized physical access. Those who are not employees should not be in the building or building complex at all unless accompanied by an authorized individual. Not counting PCs and workstations, information system assets, such as servers, mainframe computers, network equipment, and storage networks, are generally housed in restricted areas. Access to such areas is usually restricted to only a certain number of employees. Unauthorized physical access can lead to other threats, such as theft, vandalism, or misuse.
• Theft. This threat includes theft of equipment and theft of data by copying. Eavesdropping and wiretapping also fall into this category. Theft can be at the hands of an outsider who has gained unauthorized access or by an insider.
• Vandalism. This threat includes destruction of equipment and destruction of data.
• Misuse. This category includes improper use of resources by those who are authorized to use them, as well as use of resources by individuals not authorized to use the resources at all.
3 Physical Security Prevention and Mitigation Measures
In this part of the chapter, we look at a range of techniques for preventing, or in some cases simply deterring, physical attacks. We begin with a survey of some of the techniques for dealing with environmental and technical threats and then move on to human-caused threats.
Environmental Threats
We discuss these threats in the same order.
Inappropriate Temperature and Humidity
Dealing with this problem is primarily a matter of having environmental-control equipment of appropriate capacity and appropriate sensors to warn of thresholds being exceeded. Beyond that, the principal requirement is the maintenance of a power supply, discussed subsequently.
Fire and Smoke
Dealing with fire involves a combination of alarms, preventive measures, and fire mitigation. Martin provides the following list of necessary measures3:
• Choice of site to minimize likelihood of disaster. Few disastrous fires originate in a well-protected computer room or IS facility. The IS area should be chosen to minimize fire, water, and smoke hazards from adjoining areas. Common walls with other activities should have at least a one-hour fire-protection rating.
• Air conditioning and other ducts designed so as not to spread fire. There are standard guidelines and specifications for such designs.
• Positioning of equipment to minimize damage.
• Good housekeeping. Records and flammables must not be stored in the IS area. Tidy installation of IS equipment is crucial.
• Hand-operated fire extinguishers readily available, clearly marked, and regularly tested.
• Automatic fire extinguishers installed. Installation should be such that the extinguishers are unlikely to cause damage to equipment or danger to personnel.
• Fire detectors. The detectors sound alarms inside the IS room and with external authorities, and start automatic fire extinguishers after a delay to permit human intervention.
• Equipment power-off switch. This switch must be clearly marked and unobstructed. All personnel must be familiar with power-off procedures.
• Emergency procedures posted.
• Personnel safety. Safety must be considered in designing the building layout and emergency procedures.
• Important records stored in fireproof cabinets or vaults.
• Records needed for file reconstruction stored off the premises.
• Up-to-date duplicate of all programs stored off the premises.
• Contingency plan for use of equipment elsewhere should the computers be destroyed.
• Insurance company and local fire department should inspect the facility.
To deal with the threat of smoke, the responsible manager should install smoke detectors in every room that contains computer equipment as well as under raised floors and over suspended ceilings. Smoking should not be permitted in computer rooms.
For wildfires, the available countermeasures are limited. Fire-resistant building techniques are costly and difficult to justify.
Water Damage
Prevention and mitigation measures for water threats must encompass the range of such threats. For plumbing leaks, the cost of relocating threatening lines is generally difficult to justify. With knowledge of the exact layout of water supply lines, measures can be taken to locate equipment sensibly. The location of all shutoff valves should be clearly visible or at least clearly documented, and responsible personnel should know the procedures to follow in case of emergency.
To deal with both plumbing leaks and other sources of water, sensors are vital. Water sensors should be located on the floor of computer rooms as well as under raised floors and should cut off power automatically in the event of a flood.
Other Environmental Threats
For chemical, biological, and radiological threats, specific technical approaches are available, including infrastructure design, sensor design and placement, mitigation procedures, personnel training, and so forth. Standards and techniques in these areas continue to evolve.
As for dust hazards, the obvious prevention method is to limit dust through the use and proper filter maintenance and regular IS room maintenance. For infestations, regular pest control procedures may be needed, starting with maintaining a clean environment.
Technical Threats
To deal with brief power interruptions, an uninterruptible power supply (UPS) should be employed for each piece of critical equipment. The UPS is a battery backup unit that can maintain power to processors, monitors, and other equipment for a period of minutes. UPS units can also function as surge protectors, power noise filters, and automatic shutdown devices when the battery runs low.
For longer blackouts or brownouts, critical equipment should be connected to an emergency power source, such as a generator. For reliable service, a range of issues need to be addressed by management, including product selection, generator placement, personnel training, testing and maintenance schedules, and so forth.
To deal with electromagnetic interference, a combination of filters and shielding can be used. The specific technical details will depend on the infrastructure design and the anticipated sources and nature of the interference.
Human-Caused Physical Threats
The general approach to human-caused physical threats is physical access control. Based on Michael,4 we can suggest a spectrum of approaches that can be used to restrict access to equipment. These methods can be used in combination:
• Physical contact with a resource is restricted by restricting access to the building in which the resource is housed. This approach is intended to deny access to outsiders but does not address the issue of unauthorized insiders or employees.
• Physical contact with a resource is restricted by putting the resource in a locked cabinet, safe, or room.
• A machine may be accessed, but it is secured (perhaps permanently bolted) to an object that is difficult to move. This will deter theft but not vandalism, unauthorized access, or misuse.
• A security device controls the power switch.
• A movable resource is equipped with a tracking device so that a sensing portal can alert security personnel or trigger an automated barrier to prevent the object from being moved out of its proper security area.
• A portable object is equipped with a tracking device so that its current position can be monitored continually.
The first two of the preceding approaches isolate the equipment. Techniques that can be used for this type of access control include controlled areas patrolled or guarded by personnel, barriers that isolate each area, entry points in the barrier (doors), and locks or screening measures at each entry point. Physical access control should address not just computers and other IS equipment but also locations of wiring used to connect systems, the electrical power service, the HVAC equipment and distribution system, telephone and communications lines, backup media, and documents.
In addition to physical and procedural barriers, an effective physical access control regime includes a variety of sensors and alarms to detect intruders and unauthorized access or movement of equipment. Surveillance systems are frequently an integral part of building security, and special-purpose surveillance systems for the IS area are generally also warranted. Such systems should provide real-time remote viewing as well as recording.
4 Recovery from Physical Security Breaches
The most essential element of recovery from physical security breaches is redundancy. Redundancy does not undo any breaches of confidentiality, such as the theft of data or documents, but it does provide for recovery from loss of data. Ideally, all the important data in the system should be available off site and updated as near to real time as is warranted based on a cost/benefit tradeoff. With broadband connections now almost universally available, batch encrypted backups over private networks or the Internet are warranted and can be carried out on whatever schedule is deemed appropriate by management. At the extreme, a hotsite can be created off site that is ready to take over operation instantly and has available to it a near-real-time copy of operational data.
Recovery from physical damage to the equipment or the site depends on the nature of the damage and, importantly, the nature of the residue. Water, smoke, and fire damage may leave behind hazardous materials that must be meticulously removed from the site before normal operations and the normal equipment suite can be reconstituted. In many cases, this requires bringing in disaster recovery specialists from outside the organization to do the cleanup.
5 Threat Assessment, Planning, and Plan Implementation
We have surveyed a number of threats to physical security and a number of approaches to prevention, mitigation, and recovery. To implement a physical security program, an organization must conduct a threat assessment to determine the amount of resources to devote to physical security and the allocation of those resources against the various threats. This process also applies to logical security.
Threat Assessment
In this part of the chapter, we follow Platt5 in outlining a typical sequence of steps that an organization should take:
1. Set up a steering committee. The threat assessment should not be left only to a security officer or to IS management. All those who have a stake in the security of the IS assets, including all of the user communities, should be brought into the process.
2. Obtain information and assistance. Historical information concerning external threats, such as flood and fire is the best starting point. This information can often be obtained from government agencies and weather bureaus. In the United States, the Federal Emergency Management Agency (FEMA) can provide much useful information. FEMA has a number of publications available online that provide specific guidance in a wide variety of physical security areas (www.fema.gov/business/index.shtm). The committee should also seek expert advice from vendors, suppliers, neighboring businesses, service and maintenance personnel, consultants, and academics.
3. Identify all possible threats. List all possible threats, including those that are specific to IS operations as well as those that are more general, covering the building and the geographic area.
4. Determine the likelihood of each threat. This is clearly a difficult task. One approach is to use a scale of 1 (least likely) to 5 (most likely) so that threats can be grouped to suggest where attention should be directed. All the information from Step 2 can be applied to this task.
5. Approximate the direct costs. For each threat, the committee must estimate not only the threat’s likelihood but also its severity in terms of consequences. Again a relative scale of 1 (low) to 5 (high) in terms of costs and losses is a reasonable approach. For both Steps 4 and 5, an attempt to use a finer-grained scale, or to assign specific probabilities and specific costs, is likely to produce the impression of greater precision and knowledge about future threats than is possible.
6. Consider cascading costs. Some threats can trigger consequential threats that add still more impact costs. For example, a fire can cause direct flame, heat, and smoke damage as well as disrupt utilities and result in water damage.
7. Prioritize the threats. The goal here is to determine the relative importance of the threats as a guide to focusing resources on prevention. A simple formula yields a prioritized list:
![]()
where the scale values (1 through 5) are used in the formula.
8. Complete the threat assessment report. The committee can now prepare a report that includes the prioritized list, with commentary on how the results were achieved. This report serves as the reference source for the planning process that follows.
Planning and Implementation
Once a threat assessment has been done, the steering committee, or another committee, can develop a plan for threat prevention, mitigation, and recovery. The following is a typical sequence of steps an organization could take:
1. Assess internal and external resources. These include resources for prevention as well as response. A reasonable approach is again to use a relative scale from 1 (strong ability to prevent and respond) to 5 (weak ability to prevent and respond). This scale can be combined with the threat priority score to focus resource planning.
2. Identify challenges and prioritize activities. Determine specific goals and milestones. Make a list of tasks to be performed, by whom and when. Determine how you will address the problem areas and resource shortfalls that were identified in the vulnerability analysis.
3. Develop a plan. The plan should include prevention measures and equipment needed and emergency response procedures. The plan should include support documents, such as emergency call lists, building and site maps, and resource lists.
4. Implement the plan. Implementation includes acquiring new equipment, assigning responsibilities, conducting training, monitoring plan implementation, and updating the plan regularly.
6 Example: A Corporate Physical Security Policy
To give the reader a feel for how organizations deal with physical security, we provide a real-world example of a physical security policy. The company is a European Union (EU)-based engineering consulting firm that specializes in the provision of planning, design, and management services for infrastructure development worldwide. With interests in transportation, water, maritime, and property, the company is undertaking commissions in over 70 countries from a network of more than 70 offices.
Figure 4.3 is extracted from the company’s security standards document. For our purposes, we have changed the name of the company to Company wherever it appears in the document. The company’s physical security policy relies heavily on ISO 17799 (Code of Practice for Information Security Management).
7 Integration of Physical and Logical Security
Physical security involves numerous detection devices, such as sensors and alarms, and numerous prevention devices and measures, such as locks and physical barriers. It should be clear that there is much scope for automation and for the integration of various computerized and electronic devices. Clearly, physical security can be made more effective if there is a central destination for all alerts and alarms and if there is central control of all automated access control mechanisms, such as smart card entry sites.
From the point of view of both effectiveness and cost, there is increasing interest not only in integrating automated physical security functions but in integrating, to the extent possible, automated physical security and logical security functions. The most promising area is that of access control. Examples of ways to integrate physical and logical access control include the following:
• Use of a single ID card for physical and logical access. This can be a simple magnetic-strip card or a smart card.
• Single-step user/card enrollment and termination across all identity and access control databases.
• A central ID-management system instead of multiple disparate user directories and databases.
As an example of the utility of this integration, suppose that an alert indicates that Bob has logged on to the company’s wireless network (an event generated by the logical access control system) but did not enter the building (an event generated from the physical access control system). Combined, these two events suggest that someone is hijacking Bob’s wireless account.
For the integration of physical and logical access control to be practical, a wide range of vendors must conform to standards that cover smart card protocols, authentication and access control formats and protocols, database entries, message formats, and so on. An important step in this direction is FIPS 201-2 (Personal Identity Verification (PIV) of Federal Employees and Contractors), issued in 2011. The standard defines a reliable, governmentwide PIV system for use in applications such as access to federally controlled facilities and information systems. The standard specifies a PIV system within which common identification credentials can be created and later used to verify a claimed identity. The standard also identifies federal governmentwide requirements for security levels that are dependent on risks to the facility or information being protected. The standard applies to private-sector contractors as well, and serves as a useful guideline for any organization.
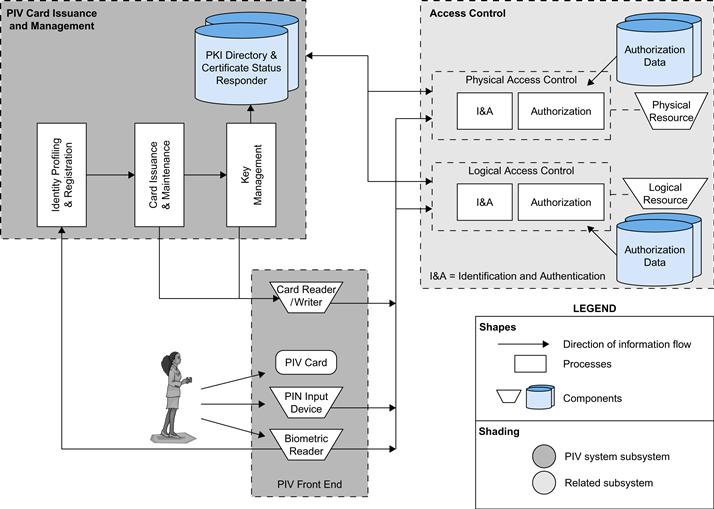
Figure 4.4 illustrates the major components of FIPS 201-2 compliant systems. The PIV front end defines the physical interface to a user who is requesting access to a facility, which could be either physical access to a protected physical area or logical access to an information system. The PIV front-end subsystem supports up to three-factor authentication; the number of factors used depends on the level of security required. The front end makes use of a smart card, known as a PIV card, which is a dual-interface contact and contactless card. The card holds a cardholder photograph, X.509 certificates, cryptographic keys, biometric data, and the cardholder unique identifier (CHUID). Certain cardholder information may be read-protected and require a personal identification number (PIN) for read access by the card reader. The biometric reader, in the current version of the standard, is a fingerprint reader.
The standard defines three assurance levels for verification of the card and the encoded data stored on the card, which in turn leads to verifying the authenticity of the person holding the credential. A level of some confidence corresponds to use of the card reader and PIN. A level of high confidence adds a biometric comparison of a fingerprint captured and encoded on the card during the card-issuing process and a fingerprint scanned at the physical access point. A very high confidence level requires that the process just described is completed at a control point attended by an official observer.
The other major component of the PIV system is the PIV card issuance and management subsystem. This subsystem includes the components responsible for identity proofing and registration, card and key issuance and management, and the various repositories and services (public key infrastructure [PKI] directory, certificate status servers) required as part of the verification infrastructure.
The PIV system interacts with an access control subsystem, which includes components responsible for determining a particular PIV cardholder’s access to a physical or logical resource. FIPS 201-1 standardizes data formats and protocols for interaction between the PIV system and the access control system.
Unlike the typical card number/facility code encoded on most access control cards, the FIPS 201 CHUID takes authentication to a new level, through the use of an expiration date (a required CHUID data field) and an optional CHUID digital signature. A digital signature can be checked to ensure that the CHUID recorded on the card was digitally signed by a trusted source and that the CHUID data have not been altered since the card was signed. The CHUID expiration date can be checked to verify that the card has not expired. This is independent of whatever expiration date is associated with cardholder privileges. Reading and verifying the CHUID alone provides only some assurance of identity because it authenticates the card data, not the cardholder. The PIN and biometric factors provide identity verification of the individual.
Figure 4.5, adapted from Forristal,6 illustrates the convergence of physical and logical access control using FIPS 201-2. The core of the system includes the PIV and access control system as well as a certificate authority for signing CHUIDs. The other elements of Figure 4.5 provide examples of the use of the system core for integrating physical and logical access control.
If the integration of physical and logical access control extends beyond a unified front end to an integration of system elements, a number of benefits accrue, including the following7:
• Employees gain a single, unified access control authentication device; this cuts down on misplaced tokens, reduces training and overhead, and allows seamless access.
• A single logical location for employee ID management reduces duplicate data entry operations and allows for immediate and real-time authorization revocation of all enterprise resources.
• Auditing and forensic groups have a central repository for access control investigations.
• Hardware unification can reduce the number of vendor purchase-and-support contracts.
• Certificate-based access control systems can leverage user ID certificates for other security applications, such as document esigning and data encryption.
Finally, let’s briefly look at a physical security checklist. The effectiveness of the recommendations in the physical security checklist is most useful when initiated as part of a larger plan to develop and implement security policy throughout an organization.
8 Physical Security Checklist
While it may be tempting to simply refer to the following checklist as your security plan, to do so would limit the effectiveness of the recommendations. Some recommendations and considerations are included the following checklist: “An Agenda For Action For Physical Security”).
9 Summary
Physical security requires that building site(s) be safeguarded in a way that minimizes the risk of resource theft and destruction. To accomplish this, decision-makers must be concerned about building construction, room assignments, emergency procedures, regulations governing equipment placement and use, power supplies, product handling, and relationships with outside contractors and agencies.
The physical plant must be satisfactorily secured to prevent those people who are not authorized to enter the site and use equipment from doing so. A building does not need to feel like a fort to be safe. Well-conceived plans to secure a building can be initiated without adding undue burden on your staff. After all, if they require access, they will receive it–as long as they were aware of, and abide by, the organization’s stated security policies and guidelines. The only way to ensure this is to demand that before any person is given access to your system, they have first signed and returned a valid Security Agreement. This necessary security policy is too important to permit exceptions.
Finally, let’s move on to the real interactive part of this Chapter: review questions/exercises, hands-on projects, case projects and optional team case project. The answers and/or solutions by chapter can be found in the Online Instructor’s Solutions Manual.
Chapter Review Questions/Exercises
True/False
1. True or False? Information system hardware includes data processing and storage equipment, transmission and networking facilities, and online storage media.
2. True or False? Physical facility includes the buildings and other structures housing the system and network components.
3. True or False? Supporting facilities under scores the operation of the information system.
4. True or False? Personnel are humans involved in the control, maintenance, and use of the information systems.
5. True or False? It is possible to assess the risk of various types of natural disasters and take suitable precautions so that catastrophic loss from natural disaster is achieved.
Multiple Choice
1. What are the three elements of information system (IS) security?
2. In broad terms, which of the following is not included in the critical infrastructure?
B. Information system hardware
3. Which of the following are threats?
4. Which of the following is not a human-caused threat?
A. Unauthorized physical access
5. Dealing with fire involves a combination of alarms, preventive measures, and fire mitigation. Which of the following is not a necessary measure?
A. Choice of site to minimize likelihood of disaster
Exercise
Problem
A company’s physical security team analyzed physical security threats and vulnerabilities for their systems. What type of vulnerabilities did the company focus on?
Hands-On Projects
Project
An engineering company operating within a highly regulated industry, in which privacy and compliance are of paramount importance, wanted to compare itself relative to its peers in physical security provision and establish a baseline from which to quantify improvement. Please identify the best practices; compare organizational and outsourcing models; compare security technologies utilized; and, calibrate investment in physical security against its peers.
Case Projects
Problem
This case study illustrates how a company uses intelligent video processing (a sub-system of its video surveillance system) to detect intrusions at land ports of entry. Virtual fences are integrated into each facility to compliment both the facility’s perimeter physical security system (composed of a combination of fences, gates, and barriers) and the video surveillance system. What should happen if these virtual fences are breached?
Optional Team Case Project
Problem
A company wants to further develop its access control system (ACS) use of video, proximity-based ID cards, biometrics, RFID, VoIP, and remotely controlled gates for manned and unmanned access control. What does the company need to do to further develop its ACS?
1F. Platt, “Physical threats to the information infrastructure,” in S. Bosworth, and M. Kabay, (eds.), Computer Security Handbook, Wiley, 2002.
2S. Bosworth and M. Kabay (eds.), Computer Security Handbook, Wiley, 2002.
3J. Martin, Security, Accuracy, and Privacy in Computer Systems, Prentice Hall, 1973.
4M. Michael, “Physical security measures,” In H. Bidgoli, (ed.), Handbook of Information Security, Wiley, 2006.
5F. Platt, “Physical threats to the information infrastructure,” in S. Bosworth, and M. Kabay, (eds.), Computer Security Handbook, Wiley, 2002.
6J. Forristal, “Physical/logical convergence,” Network Computing, November 23, 2006.
7J. Forristal, “Physical/logical convergence,” Network Computing, November 23, 2006.