Chapter 4
e-Commerce Security: Threats, Issues, and Methods
Prerna Sharma, Deepak Gupta, Ashish Khanna
Maharaja Agrasen Institute of Technology, New Delhi, India
Email: [email protected], [email protected], [email protected]
Abstract
In the era of the demonetization and promotion of a cashless economy, ecommerce has taken center stage. An amalgam of fast internet and advanced processors is acting as a catalyst in the development of multiple e-commerce applications and their usability. Credit for the popularity of e-commerce also goes to the convenience provided by seller and buyer transactions from anywhere at any time. Furthermore, scalable high-speed transactions with lower operating costs have led to e-commerce acceptability worldwide, thus helping to expand businesses and promoting a new form of economy via e-commerce. However, traditional practitioners of business are going to leave no stone unturned to stop this flood of e-commerce transactions in the shadow of secure and authentic transactions. Therefore, in order to create a fearless environment for buying and selling over the internet, highly secure, reliable, and authentic e-commerce applications are needed. The above discussion demonstrates the importance of security for the successful implementation of e-commerce. This chapter explains the issues and problems associated with the security of worldly goods and transactions in e-commerce components and activities. Since a large amount of public money is involved in the transactions, the role of information security and privacy is not exaggerated in this kind of business. Many issues like identity theft and cyber fraud are obstacles that discourage customers from getting involved in e-commerce. Education of the public on e-commerce security issues has taken a back seat until now; it should be encouraged as trust and security are huge challenges to be addressed so that one can insulate the e-commerce system from prevailing attacks. In this chapter we will address different types of application-specific security threats, security challenges, and vulnerability issues at various levels of the system. Furthermore, we will throw light on how to deal with various security threats, issues, and present a comparative analysis of various methods used in e-commerce security in order to perform secure payment transactions in an efficient manner.
Keywords: e-Commerce security, e-commerce threats, e-commerce issues, e-commerce methods, e-commerce architecture, e-commerce life cycle
4.1 Introduction
In the era of demonetization and promotion of cashless economy, the internet has given a distributed platform to expand businesses, thus giving birth to a new form of economy known as e-economy via e-commerce. In the new economy, the internet has grown into an influential and universal communication mechanism to assist in the consummation and dispensation of business transactions [17]. Whereas, e-commerce can be explained as buying and selling of goods and services online by using user interactive GUI platforms. It has revolutionized the way trade is carried out and today e-commerce has attained center stage in commerce transactions. In other words, an amalgam of fast internet and advanced processors is acting as a catalyst in the development of multiple e-commerce applications and their usability. The credit for the popularity of e-commerce also goes to the convenience provided to the seller and buyer of transacting from anywhere and at any moment. Furthermore, scalable high-speed transactions with lower operating costs have led to the acceptability of e-commerce worldwide. Thus, helping to expand businesses and promoting a new form of economy via e-commerce [1].
However, the traditional practitioners of business are going to leave no stone unturned to stop this flood of e-commerce transactions in the shadow of secure and authentic transactions, and this lack of trust can severely affect buyers and sellers, who may choose to refrain from the use of the internet and recrudesce to traditional methods of doing business; as this aspect can turn technology into a curse in spite of a boon [2]. Therefore, in order to create a fearless environment for buying and selling on the internet, to oppose the above-mentioned misconception and insecurity among the clients, and to create a conducive environment for e-commerce security threats, the security issues should be properly reviewed and addressed by highly secure, reliable, and authentic e-commerce applications. Countermeasures must be implemented so that it does not discourage use of e-commerce operations.
The above discussion demonstrates the importance of security in e-commerce in order for its implementation to be successful. This chapter explains the issues and problems associated with the security of worldly goods and transactions in the e-commerce components and activities. Since a large amount of public money is involved in the transactions, the role of information security and privacy is not exaggerated in this kind of business. Many issues, like identity theft and cyber fraud, are obstacles that discourage customers from getting involved in e-commerce. Awareness of e-commerce security issues has taken a back seat until now, although it should be encouraged, as trust and security are huge challenges to be addressed to insulate the e-commerce system from a set of prevailing attacks. In this chapter we will address different types of application-specific security threats, security challenges, and vulnerability issues at various levels of the system. This chapter also aims to study an e-commerce security life-cycle model and proposes comparative analysis of various methods of e-commerce security. Furthermore, it throws light on to how to deal with various security threats and issues, and presents a comparative analysis of various methods used in e-commerce security in order to perform secure payment transactions in an efficient manner.
4.2 Literature Review
In the domain of e-commerce, secure transaction is one of the key issues that restrict consumers and establishments engaging in commerce. A lot of research is going on in the direction of secure and authentic transactions. Some of the work done in the past is discussed below.
Dieter Gollmann et al. [1] have talked about colossal growth of the internet and its services, and its active role in commerce territory apart from the academic one. Sengupta et al. [3] have put forward an e-commerce security life-cycle approach, and significant standards and laws in e-commerce security. Also, various security requirements to protect the e-commerce system from threats have been identified. Ladan [5] has presented an overview of the architectural framework of e-commerce and also elucidated various ecommerce security issues and security measures at different levels of e-commerce system.
Gautam and Singh [6] discuss online security for proficient payment transactions, which acts as an indispensable management and technical tool. Jarnail Singh [9] has provided guidelines for the security of e-commerce in order to enhance customer confidence in online transactions. He finds that low level security on the web servers of e-commerce and on customers’ sites is the issue to be addressed.
Ahmad and Alam [15] have proposed a model of e-transaction on the basis of PGP and ECC. This chapter signifies how PGP efficiently handles customer order of information and security of payment using dual digital signature. Kraft and Kakar [16] have explored latest market trends for e-business and the vital role played by e-commerce in the retail market. The modern practices of e-commerce and development of e-commerce have been researched and acknowledged.
4.3 e-Commerce
e-Commerce is extensively used for the purchasing and retailing of goods online. However, only transactions made through digital online fund transfers measures can be considered ecommerce transactions. With each passing day, m-commerce and e-commerce are playing a more important role in internet-based retail marketing. The number of people worldwide using this technology is increasing day-by-day. To understand e-commerce security issues an understanding of the following key characteristics of e-commerce is essential.
4.3.1 Characteristics of e-Commerce Technology
Some of the key characteristics of e-commerce are as follows [3]:
- Automated processing: The generation and processing of multiple payments has been automated by the payer with little effort and cost involved.
- Immediacy of result: Real-time payments because of automation results in payment immediacy.
- Improved accessibility: Accelerated usage of computing and communication technology with suitable software empowers access of payment services even to small enterprises that earlier could only be accessed by large organizations via dedicated network.
- Global reach: The new payment system curtails geographical factors; allows business transactions on a cross-country basis. It affects certain thrust areas such as extent of payment market place, adaptation of payment schemes to regulatory regimes and many more.
- Ubiquity: e-Commerce can be operated from anywhere whereas the traditional business market is defined by a physical place.
- Loss of collateral information: Earlier transacting parties used to validate individual payments on the basis of collateral information that they relied upon. Whereas these days new technology waives off or alters collateral information with transactions.
- Interactivity: In the 21st century the two-way communication mode is acknowledged between businesses and consumers.
- New business model: They are in place to make use of new payment technologies for disintermediation of customers from banks.
4.3.2 Architectural Framework of e-Commerce
Client-server architecture is the base of e-commerce architecture. Client is basically an application which makes use of GUI to send a request to a server for certain services; the server in turn provides the requested services to the client.
In this architectural framework, client denotes customer and server denotes business application. This business application is set up on a web server (computer program) which provides services to the customer in the form of HTML pages or files.
The two different types of client-server architecture of e-commerce are [4]: two-tier architecture (Figure 4.1) and three-tier architecture (Figure 4.2).
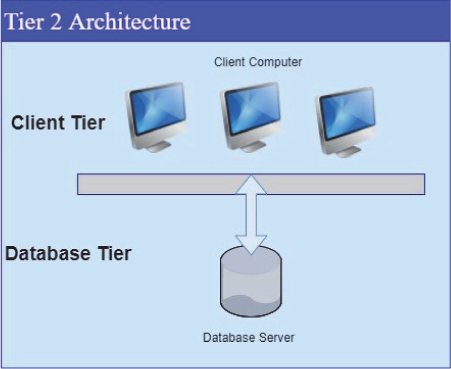
Figure 4.1 Two-tier e-commerce architecture.
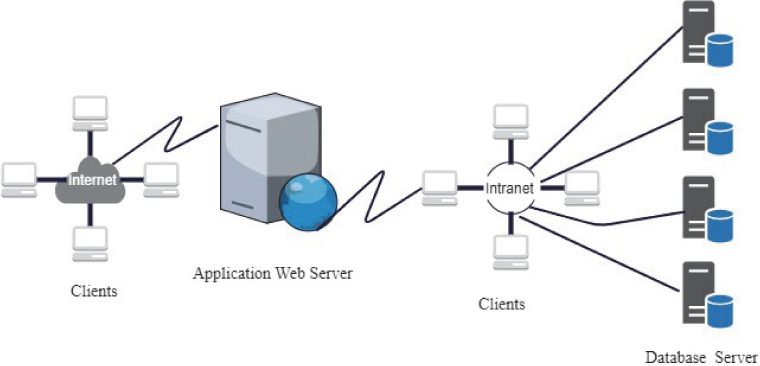
Figure 4.2 Three-tier e-commerce architecture.
4.3.2.1 Two-Tier Architecture
In this architecture data rests on the server whereas business application/logic and user interface rests on the client. The client process makes user interface available, which collects and presents the data on the customer’s computer. Thus, this part of the application is known as the presentation layer.
The server process makes sure of the availability of interface that frames the data stored/database. Thus, this application is known as the data layer.
Although the business logic/application mostly resides on the client side, it can also reside on the server side. Business logic performs various functions of validating data and monitoring security and permissions.
4.3.2.2 Three-Tier Architecture
To address the limitation of two-tier architecture, three-tier architecture emerged in the 1990s. In this architecture, business logic is separated from user interface and from data access. Hence, all three are maintained as independent modules. Thus, in this architecture there are three tiers involved:
- Top tier: User interface services; Text input session; Dialog management: Display management
- Middle tier: Process management services; Process development and process monitoring; Process resourcing
- Third tier: Database management services; Data consistency; Centralized process logic; Localizing the system functionality.
Operation: In the e-commerce system, a client sends a request via the internet, which passes a firewall that filters the packets destined for wrong address or wrong ports. The web server treats the request by calling an application which accesses a database server in order to modify, update or read a record or records stored in the database and further replies with an HTML page or file. These servers are in addition connected to huge networks [5].
4.3.3 Advantages and Disadvantages of e-Commerce
We have discussed many of the characteristics of e-commerce in the section above. The internet aids in forming virtual communities, which are basically groups of people having common interests. These virtual communities become ideal target markets. There are various advantages of performing business online from the perspective of different stakeholders, as shown in Table 4.1.
Table 4.1 Advantages of e-commerce.
| S.No | e-Commerce Stakeholders |
Advantages |
| 1 | Organization |
Low cost Fewer employees involved Global reach, even to remote areas Easier management of inventory |
| 2 | Client/Customer |
Customized experience Can compare prices easily of same products/services Products/Services available at a mouse click Wider range of choices available |
| 3 | Society |
Promotes cashless economy, which in turn curbs black money Provides online services in various sectors Prices of products are kept in check as no middlemen, such as wholesalers, retailers, etc., are involved. |
If we look at e-commerce operations from the point of view of various stakeholders, there are many drawbacks associated with them, as shown in Table 4.2.
Table 4.2 Disadvantages of e-commerce
| S.No | e-Commerce Stakeholders |
Disadvantages |
| 1 | Organization |
Data privacy issues Not everything can be sold, such as perishable products or, expensive luxury items Highly competitive Problem of adherence to legal standards |
| 2 | Client/Customer |
Look and feel not available before buying Internet connectivity required Product delivery not instantaneous Products not available when server is down When delivered, product may not be as expected |
| 3 | Society |
Security of data like leakage of data Knowledge of using internet is limited |
4.4 Security Overview in e-Commerce
Security is the need of the hour when operating online, as the network’s vulnerability to attack is manifold. Information is one of the most vital enterprise assets. For any organization, information should be valued and suitably secured [18]. Hence, we will discuss the purpose of security in e-commerce and different levels of the system where security is a prerequisite.
4.4.1 Purpose of Security in e-Commerce
- Authentication: This ensures that only the right user has access to data [6].
- Non-repudiation: This is a form of confirmation from the user that they have indeed performed an action, so that they have cannot deny performing that action in the future.
- Privacy: This gives control to the user on how much of their data can be given/distributed to third parties.
- Confidentiality: This is the state of keeping data private so that it cannot be accessed by any unauthorized person/party.
- Availability: This means that all the data is available to a user that they are entitled to or have the right to access.
- Integrity: This ensures that data received by a user is the same that was transmitted by sender, that is, no change or manipulation of data has occurred while transmitting data.
- Encryption: This means encoding data in such a way that it cannot be understood directly by reading it.
4.4.2 Security Element at Different Levels of e-Commerce System
Security of the e-commerce system is of immense significance, thus it must be ensured at various component levels, i.e., hardware, software and environment. The pervasiveness of computing systems has placed computer devices everywhere, and they have become so prevalent as to blend into the background. They are also part of the emerging wireless environment [11].
4.4.2.1 Hardware
The devices that make up the system, such as web servers, network devices, and database servers, are critical points of the system and are susceptible to various network attacks. Thus, measures like a properly configured firewall must be taken. Web servers and database servers should be insulated from various other networks by using DMZ (demilitarized zone), which is a network that stands between a protected network and an external network. Thus, an additional layer of security is introduced in the network.
4.4.2.2 Software
The smooth operation of an e-commerce software security system requires a security OS, web server software, database software and web browser. The operating system should be configured properly, as it is quite vulnerable. In order to fix holes in security, there should be a regular updating of software and routinely released patches.
4.4.2.3 Environment
Environmental security refers to securing physical access to the network by using a manual guard, CCTV, various logs or other methods.
4.5 Security Issues in e-Commerce
We have already discussed security elements at different levels of the e-commerce system, now let’s talk further about various security and vulnerability issues at these levels [5].
4.5.1 Client Level
These days customers tend to get their hands on an e-commerce system in different ways, such as wireless networks, mobile devices, etc. These modes are vulnerable to security hazards, as an outsider can eavesdrop on wireless communication. Thus, there is a need for password protection so that an outsider cannot intervene and access sensitive information. In addition, there is always a chance of misplacing the mobile device.
Security issues with respect to mobile devices and wireless networks which further affect e-business are:
- Captured and retransmitted messages: This refers to an attacker getting hold of a message of a legitimate user and replaying it by altering the message to the same receiver or a different one so that the attacker can gain unauthorized access to important information [7].
- Eavesdropping: This attack happens on unsecured network and also when the information being transmitted is not encrypted. Thus, an outsider can eavesdrop on a vulnerable network and can easily gain access to sensitive data.
- Mobile device pull attack: In this type of attack, the attacker controls the mobile device as a source of propriety data and control information. Data can be obtained from the device itself through the data export interfaces, a synchronized desktop, mobile applications running on the device or the internet servers [8].
- Mobile device push attack: In this type of attack, the attacker uses the mobile device to plant a malicious code and spread it to infect other elements of the network. Once the mobile device inside a secure network is compromised, it can be used for attacks against other devices or servers in the network [8].
- Lost device: A mobile device should always be protected with a password as there is always a chance of its getting lost or stolen and an unauthorized user can access it.
4.5.2 Front-End Servers and Software Application Level
It is observed that in a software system there is always a chance of bugs/faults being left by low-skilled software developers. The e-commerce security system is expected to be flexible, standards based and interoperable with other systems.
Keeping security advisories and patches updated is quite difficult, as communication network standards and protocols keep on changing. Hackers are opportunistic and make the most of these vulnerabilities by using viruses and malicious software to infect the ebusiness system and steal customer information.
4.5.3 Network and Server Level
Most of the networks are dependent on other networks which are privately owned and managed, whose security measures are not known to us; therefore, its control is also not available to us. Encryption is used to secure data moving across a network. The network operator is responsible for transporting information securely.
- DoS: Whenever hackers launch a denial-of-service attack, it turns out to be one of the most bothersome security issues faced by e-business today. It is characterized as a categorical effort by attackers to prevent users from using an e-business system.
- Session interception and message modification: The attacker can transmit altered messages by hijacking a session. They can also add a malicious host between client host and server host, which is popularly known as man-in-the-middle. In this case, data communication passes through the attackers’ host.
- Firewall loophole: A firewall is a software or hardware device installed between back-end server and corporate network. It is usually implemented at network protocol layer and fails to protect the system at higher protocols. Hackers sense unfixed firewall loopholes and try to access price lists, email lists, catalogs, etc.
4.6 Security Threats in e-Commerce
e-Commerce has a tendency to be at a higher stratum for risk and attacks. In e-commerce, data are the key to track consumer shopping behavior to personalize offers, which are collected over time using consumer browsing and transactional points [19]. Server level is the physical place where all of these transactions happen. The server is regarded as the central repository for one’s e-commerce business abode that entails a definite website which displays one’s products and services, the database of the customer and the mechanism of payment. If any attack takes place on the server, then it proves to be a huge setback as there is a potential of losing everything. Thus, taking the initiative when it comes to security should be done to a much greater extent. Now, let us discuss various e-commerce security threats in detail [9].
Distributed Denial-of-Service (DDos): In this type of attack the availability of a target system (e-commerce) comes into question, as millions of customers are unable to access an online system which is overwhelmed with traffic from multiple sources. In this type of attack a botnet is formed in which multiple devices are connected online; these devices tend to generate fake traffic flooding the target system, which results in the service being denied to legitimate customers. This attack affects not only the target site but also creates a congestion problem over the entire network (Internet), as shown in Figure 4.3.

Figure 4.3 DDOS attack.
It becomes difficult to control or stop the attack as one cannot differentiate between genuine traffic and attack traffic. An attacker may restrain you from getting your hands on email, websites, and online accounts that the affected computer depends on [10].
A DDoS attack consists of four elements [11]:
- Victim: The target host who is going to deal with the burden of the attack.
- Attack daemon agent: This is an agent program that performs the attack on the victim. It is set up mostly on the host computer but tends to affect both host and target computer. These daemons tend to gain access and infiltrate the host computer.
- Control master program: Coordinates the attack.
- Real attacker: Although being the mastermind of the attack, it stays in the background by using the control master program.
SQL Injection: As the name of the attack suggests, there must be an SQL query which has been inserted while the user inputs the data; as the query gets executed at the client end, the attack comes into operation. This is one of the most common web hacking techniques in which code is injected that might create havoc in the database, as shown in Figure 4.4.

Figure 4.4 SQL injection attack.
The causes of SQL injection are as follows [12]:
- Running of software applications that welcome data from inauthentic internet users.
- Unable to validate the data.
- This data is further used in dynamic SQL query to database backing the application.
SQL injection results in: in identity spoofing, alteration of existing data, revealing all the data on the system, making data unavailable by destroying the data.
Price Manipulation: As the name suggests, the original price is manipulated to different value. This type of attack, which is depicted in Figure 4.5, is very common in online shopping cart platforms and payment gateways. In this attack the final payable price is manipulated by the attacker at will. In coding, the programmer makes use of hidden fields in order to store value of total item cost; a hacker can tamper with a value stored on their browser, thus the total amount that is payable is modified by the attacker. Supposedly, the value of an item is modified from Rs.2000/- to Rs.200/-, then it becomes exciting for the customer but unfortunate for the seller.
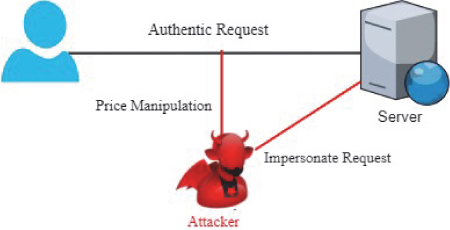
Figure 4.5 Price manipulation.
Session Hijacking: A session is a sequence of interactions maintained over a single connection between two nodes or end points, as shown in Figure 4.6. As the name of the attack suggests, the session control is taken over by the hijacker as they steal a valid session ID which allows them to enter or keep an eye on data or extract it. By changing the route of packets with their system an attacker can take part in the conversation of other users [14]. It is a combination of sniffing and spoofing.

Figure 4.6 Session hijacking attack.
Cross-Site Scripting (XSS): In this type of attack a malicious script is attached to trusted websites from a compromised site. On adding malicious script the attacker gains access to sensitive information, session cookies, etc. It is a special case of code injection. Here, the end user’s browser has no clue whether it is a trustworthy script or not. Thus, it goes goes ahead and executes this script. These scripts change and rewrite the HTML page content. This process is schematically shown in Figure 4.7.
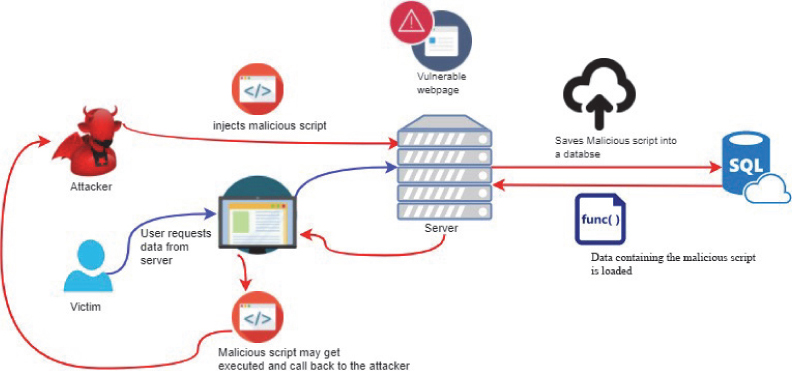
Figure 4.7 Cross-site scripting attack.
4.7 Security Approaches in e-Commerce
The security of the most crucial information of a customer, such as credit card data, should be of highest priority when transactions are carried out online. Security measures that should be ensured in e-commerce architecture are DMZ, firewalls, SSL, SET, data encryption, intrusion detection, digital signature and certificates [5].
Demilitarized Zone (DMZ): This is a special local network that holds sensitive data which is to be saved from unauthorized access. It lies between the internet and an internal network. It consists of external facing servers (front-end servers, back-end servers) and firewalls. The job of a firewall is not only to protect the front-end server but also to filter traffic between the corporate network and back-end servers. It provides an additional level of security as access to internal servers and data via internet in the internal LAN remains unreachable. An external node has access to what is available in the DMZ.
Firewalls: When a computer gets connected to the internet it becomes open to attack. A firewall, which is either hardware- or software-based, monitors and controls the traffic that either comes in or goes out of a computer based on predetermined security rules. It can be configured to let packets from specific IP addresses and ports enter or block them. Thus, it acts as a barrier between a trusted network and untrusted network.
Data Encryption: Encryption technology converts plain text into unreadable format, which prevents a third party from viewing the text. Hence, crucial information, such as credit card numbers, financial transactions and personal data, can be protected. It offers a technique to find out whether any alteration/modification of data has occurred over an unsecured network when the data is received. Data is transmitted over a secure network such as SSL, using secure protocol such as HTTPS.
There are two types of encryption techniques:
- Symmetric key encryption
- Asymmetric key encryption
Intrusion Detection System (IDS): IDS evenly monitors real-time network traffic. When it come across an attack signature or suspicious activity it becomes attentive and generates an alarm to alert the system or network administrator. Sometimes it responds to the malicious traffic by simply blocking the user from accessing the network. It can also prevent denial-of-service attacks. It should be installed in front of a firewall.
Digital Signature and Certificate: This supports e-commerce security features authentication and integrity. A digital signature certificate (DSC) is a secure digital key that certifies the identity of the holder, which is issued by a certifying authority (CA). It typically contains your identity (name, email, country, APNIC account name and your public key). Digital certificates use public key infrastructure, meaning that data that has been digitally signed or encrypted by a private key can only be decrypted by its corresponding public key. A digital certificate is an electronic “credit card” that establishes your credentials when doing business or other transactions on the Web [13].
4.8 Comparative Analysis of Various Security Threats in e-Commerce
Table 4.3 Comparative analysis of various security threats in e-commerce.
| No. | Threats |
Security Features Affected |
Site/Assets |
Severity |
Protecting Threat Methods |
Network Affected |
| 1 | DDoS |
Availability |
Server |
High |
Access control, firewall |
Lossofaccess to system |
| 2 | SQL Injection |
Integrity Confidentiality Non-repudiation |
Client |
High |
Blocking, Digital certificate verification antivirus |
Attackercanbecome administrator ofdatabase |
| 3 | Price Manipulation |
Authorization Modification Encryption |
Communication Network |
Moderate |
Encryption Digital Signature |
Attacker modifies theprice value |
| 4 | Session Hijacking |
Authentication Confidentiality |
Communication Network |
Moderate to High |
Encryption Digital Signature |
Session is hijacked after gaining authentication |
| 5 | XSS |
Integrity Confidentiality Authorization |
Client |
Moderate to high |
Firewall |
Attacker gets access to sensitivedata abuse of credentials |
4.9 e-Commerce Security Life-Cycle Model
e-Commerce security is a continuous process, which cannot be viewed in modular form as one-time provided service. It has become an integral part of e-commerce transactions where data is of utmost value, as it includes personal information of individuals’ credit card numbers, financial transactions, etc. Electronic word-of-mouth has been framed by digital technologies which in turn proposes potential for eliciting credible information that influences consumer behavior [20]. It is the responsibility of the security system designer to ensure that system properties are not affected by various security attacks [3].
The steps to designing system security are [14]:
- Model the system.
- Identify the properties of the system that are to be safeguarded when met with an attack.
- Model the adversary.
- Ensure that the properties are safeguarded when under attack.
Security Requirement Specification and Risk Analysis: At the initial stage, information needs to be gathered that answers the following questions:
- What are the assets of the organization that are to be protected?
- What are the threats associated with those assets?
- What are the access control policies?
- What is the operational infrastructure?
- What are the services required to access the asset?
- What is the access control mechanism for the services?
Security attributes that are to be protected are authentication, privacy, authorization, and integrity.
Security Policy Specification: Security requirement specification and risk analysis report is input at this phase; e-commerce security policy is generated as output. Policies are basically high-level rule-based statements.
Questions that need to be answered regarding security policy issues are:
- What types of services can users access?
- What are the information classes present in the organization that are required to be encrypted before transmitting?
- How can sensitive client data be protected?
- Corporate network remote access is associated with which class of employees?
- How are security breaches to be dealt with?
Security Infrastructure Specification: Analysis of security requirement specification and security policy specification takes place at this stage of the life cycle. In this phase one finds a list of security tools needed to protect assets. It is basically the implementation of the security policy. Some instances are:
- Applying password aging and expiration.
- Demanding complex passwords.
- Recording in a written log all physical access made to servers.
- Giving physical access to building via badges.
Testing e-Commerce Security: Several tests are conducted on the system to answer the following questions:
- How effective is the security infrastructure?
- What are the functions of the access control mechanism?
- What operational context is specified?
- How vulnerable is the infrastructure to new threats and exploits?
The main objectives of this phase are verification of the following aspects:
- Security requirements specification
- Configuration of security tools
- Gap between proposed security infrastructure and the implemented infrastructure
- Limitation of the proposed security infrastructure
Requirement Validation: This phase analyzes the extent to which security requirements of the e-commerce organization is fulfilled in accordance with security policy and implemented security infrastructure. The entire process/cycle starts again if change is incorporated into the business goal, operational environment and technology. A new set of security requirements comes into play which stimulates the new cycle of the software engineering life cycle shown in Figure 4.8.

Figure 4.8 Security engineering life cycle.
4.10 Conclusion
e-Commerce is growing at an immense pace. Many technologies have come together to assist propagation of e-commerce these days. This industry is vulnerable to many threats and issues are being addressed slowly and steadily. To protect one’s place of business being proactive is the first line of defense against security threats. Educating consumers on security issues is a vital element of e-commerce security architecture which is still in its infancy. Becoming familiar with threats, issues and protection methods will help in avoiding network vulnerability to outside elements. Ignorance is itself a threat, as fraudsters are on the lookout for online shoppers committing novice errors that they can take advantage of. In this chapter, we discussed e-commerce architecture, security issues, security threats, protection methods for safe and secure online shopping and security engineering life cycle that helps to familiarize us with various safeguards.
Future Scope: This paper can be used by research practitioners as a base for e-commerce security issues, threats and protection methods detailed in this chapter. Susceptibility of network to attacks and advancement in technology needs customers to be aware of ecommerce security issues so that the e-commerce industry can be insulated from fraud. Privacy concerns of consumers can be entertained by shielding huge amounts of personal information posted on the internet and also by stressing usable security to aid individuals with security controls that make sense to them and can be easily put to use [21].
References
1. Gollmann, D. (2010). Computer security. Wiley Interdisciplinary Reviews: Computational Statistics, 2(5), 544-554.
2. Marchany, R. C., & Tront, J. G. (2002). E-commerce security issues. In System Sciences, 2002. HICSS. Proceedings of the 35th Annual Hawaii International Conference on (pp. 2500-2508). IEEE.
3. Sengupta, A., Mazumdar, C., & Barik, M. S. (2005). e-Commerce security A life cycle approach. Sadhana, 30(2-3), 119-140.
4. Thiru, “E-commerce architecture”. http://www.myreadingroom.co.in/notes-and-studymaterial/66-e-commerce/517-e-commerce-architecture.html
5. Ladan, M. I. (2014, August). E-Commerce security issues. In Future Internet of Things and Cloud (FiCloud), 2014 International Conference on (pp. 197-201). IEEE.
6. Gautam, R., & Singh, S. (2014). Network Security issues in E-commerce. International Journal of Advanced Research in Computer Science and Software Engineering, 4(3), 130-132.
7. Pham, Q., Reid, J., McCullagh, A., & Dawson, E. (2008). Commitment issues in delegation process. In Proceedings of the sixth Australasian conference on Information security-Volume 81 (pp. 27-38). Australian Computer Society, Inc..
8. Doukas, C., Pliakas, T., & Maglogiannis, I. (2010). Mobile healthcare information management utilizing Cloud Computing and Android OS. In Engineering in Medicine and Biology Society (EMBC), 2010 Annual International Conference of the IEEE (pp. 1037-1040). IEEE.
9. Jarnail Singh (2014). Review of e-commerce security challenges. International Journal of Innovative Research in Computer and Communication Engineering (An ISO 3297: 2007 Certified Organization) Vol. 2, Issue 2, ISSN(Online): 2320-9801 ISSN (Print): 2320-9798.
10. Kumar, P. A. R., & Selvakumar, S. (2011). Distributed denial of service attack detection using an ensemble of neural classifier. Computer Communications, 34(11), 1328-1341.
11. Kulkarni, A., & Bush, S. (2006). Detecting distributed denial-of-service attacks using kolmogorov complexity metrics. Journal of Network and Systems Management, 14(1), 69-80.
12. Dougherty, C. (2012). Practical identification of SQL injection vulnerabilities. United States Computer Emergency Readiness Team (US-CERT).
13. Digital Certificate https://www.emudhradigital.com/
14. Baitha, A. K., & Vinod, S. (2018). Session Hijacking and Prevention Technique. International Journal of Engineering & Technology, 7(2.6), 193-198.
15. Ahmad, K., & Alam, M. S. (2016). E-commerce Security through Elliptic Curve Cryptography. Procedia Computer Science, 78, 867-873.
16. Kraft, T. A., & Kakar, R. (2009). E-commerce security. In Proceedings of the Conference on Information Systems Applied Research, Washington DC, USA.
17. Delone, W. H., & Mclean, E. R. (2004). Measuring e-commerce success: Applying the DeLone & McLean information systems success model. International Journal of Electronic Commerce, 9(1), 31-47.
18. Hong, K. S., Chi, Y. P., Chao, L. R., & Tang, J. H. (2003). An integrated system theory of information security management. Information Management & Computer Security, 11(5), 243-248.
19. Akter, S., & Wamba, S. F. (2016). Big data analytics in E-commerce: a systematic review and agenda for future research. Electronic Markets, 26(2), 173-194.
20. Flanagin, A. J., Metzger, M. J., Pure, R., Markov, A., & Hartsell, E. (2014). Mitigating risk in ecommerce transactions: perceptions of information credibility and the role of user-generated ratings in product quality and purchase intention. Electronic Commerce Research, 14(1), 1-23.
21. Jang-Jaccard, J., & Nepal, S. (2014). A survey of emerging threats in cybersecurity. Journal of Computer and System Sciences, 80(5), 973-993.
