CHAPTER 12
SMARTPHONE TRIGGERED SECURITY CHALLENGES - ISSUES, CASE STUDIES AND PREVENTION
Saurabh Ranjan Srivastava1, Sachin Dube1, Gulshan Shrivastaya2, Kavita Sharma3
1 Malviya National Institute of Technology, Jaipur, India.
2 National Institute of Technology, Patna, India
3 National Institute of Technology, Kurukshetra, India
Email: [email protected]
Abstract
In today’s rapidly evolving technological scenario, mobile computing devices are always at an increased risk of being attacked and exploited. Mobile security challenges comprise threats such as physical theft or accidental loss of the device, mobile malware, unauthorized access, mobile-based fraud, espionage and much more. Here, phone calls, SMS, Bluetooth, and web access act as potential security threat channels to a smartphone device. This chapter classifies the various types and details of security threats to a smartphone device. Further case studies about exploits of smartphones by terrorists, user data theft and Smartphone-based fraud are discussed. The chapter concludes with the preventive measures that can be used to improve the security of mobile devices and user data, keeping them from being exploited and attacked.
Keywords: Smartphones, mobile computing, trigger
12.1 Introduction
Today mobile phones have almost replaced personal computers and laptops by merging a combination of technologies, to fulfil the basic computational and communication necessities of today’s generation. The evolution of mobile devices with constantly growing processing power and larger storage memories, matching the potential of desktop computers can be considered as a true revolution in the world of information technology. This revolutionary growth in complexity and portability has placed mobile devices as extensions of our personality. These extensions store and manage our contacts, messages and emails, track our current location, remember our preferences and appointments and even follow us everywhere.
Due to their portability and versatility of applications, smartphones and tablets are fast becoming the preferred tools for internet browsing, online transactions, auctions and purchases and so on. The ease of interface access for every mobile application has rendered skills and underlying technologies as almost meaningless constraints for the use of these devices. Similar to every technology that created a radical impact in the life of the common masses, and was later exploited for misuse, mobile technology is also under the same spectrum. As the evolution of mobile phones constructed a thriving path for the growth of civil society, it also raised possibilities for cyber criminals to exploit mobile devices as a channel or medium of attack and exploitation.
12.2 Classification of Mobile Security Threats
The wide range of security threats that can attack or exploit mobile computing devices can be categorized into the following categories, which are discussed ahead in this section.

12.2.1 Physical Threats
Mobile devices have become common for computing and communication requirements among people because of their portable dimensions and high computing potentials. Due to these features, these gadgets are valuable and demand precautions for their physical security. In addition to the costly hardware that can be resold on the black market of gadgets, the information relevant to a user or organization can also be highly sensitive and worth far more. Due to these factors, stolen and lost mobile devices are one of those most frightening security threats. In terms of threats to physical security, mobile devices such as smartphones, tablets, PDAs, etc., without authentication check mechanisms like passwords, screen locks or fingerprint scans are at high risk [1, 2]. Such undefended devices always remain vulnerable to loss and compromise the stored sensitive information. In the worst case of loss or theft, the hackers or cyber criminals find one mechanism or another to bypass any form of authentication check and gain access to user sensitive information stored on the device.
12.2.2 Web-Based Threats
Modern mobile devices are designed to be persistently connected to WiFi networks or packet data internet to access web services. A major threat to the security of mobile devices arises through these networks. To execute web-based threats on a mobile device, its user must be prompted to visit an unsafe site and naively trigger a malicious process. Web-based threats can be classified into the following classes.
Applications such as email, messaging, Facebook, WhatsApp and Twitter are commonly used to spread links of malicious websites designed to scam the receiving users. Such scams are known as phishing scams [2]. Upon accessing such websites, the user is tricked into feeding his sensitive information like passwords or account numbers, which is captured by criminals for later exploit. The next level of possible threat connected to malicious links is drive-by downloads which automatically download a malicious application on user’s mobile device as they access such links. Some of such malicious apps prompt the user to click on or open the download for execution, while other apps can even start automatic execution. Another class of threats is known as browser exploit that utilizes the vulnerabilities present in the web browser installed on the mobile device or applications connected to it such as PDF file reader, flash player, shockwave file player or even image viewer, to damage the normal functionality of the device.
12.2.3 Application-Based Threats
Malicious mobile applications are often connected to websites with acceptable looks and behavior. As discussed in web-based threats, such malicious applications present a wide range of security threats to a mobile device. In continuation to this sequence, even legitimate software applications can also be exploited for deceitful purposes.
Application-based threats fit into one or more of the following classes. The first class of application-based threats is malware. Malware is an intentionally written piece of code to perform malicious actions on a target device [3]. Modern malware applications are capable of adding charges to a user’s phone bill, sending unwanted messages to contacts, accessing user’s private data or even hand over the control of the mobile device to a remote hacker without the knowledge of the user.
The next class of threatening applications for a mobile device is spyware. Spyware is a malicious application similar to malware, only it does not cause any visible harm to the normal functioning of the mobile device. Instead, a spyware silently collects user’s private data without their knowledge or consent. Text messages, phone call history logs, geographical location, browser history, contact list, private photos, contact lists and emails are some of the user data, which are generally targeted by spyware applications. Such data collected by spyware is exploited for financial fraud, blackmailing and even espionage cause a deep risk of privacy threats to the mobile device user. Another type of application-based threat is caused by vulnerable applications that contain faults exploitable for malicious intentions [28]. Such applications are generally legitimate ones with weaknesses due to improper designs or insufficient testing. Vulnerable applications allow access to sensitive user data for a criminal intent, execute fraudulent activities, disrupt the normal functioning of a service or even allow downloads of other similar malicious applications on the user’s device.
12.2.4 Network-Based Threats
Modern mobile devices are designed to ensure connectivity to local wireless networks (WiFi, Bluetooth) as well as cellular packet data networks to access web-based services. Threats from such networks are classified under network-based threats. Network exploits utilize flaws present in mobile operating systems or even the platform software on which the wireless or cellular networks function. On connecting to the user’s mobile device, these threats can provide the channel to an application or web-based threats [4].
WiFi sniffing is a common class of network threat that captures user data traveling through the network between the device and the network access points. Sending unencrypted data such as usernames, passwords or financial details via websites or applications lacking any security measures puts to privacy and security of user data at potential risk.
The next form of network threat to mobile devices is known as WiFI spoofing, which is executed by hackers by creating bogus WiFi access points for web access generally by using malicious WiFi routers. These WiFi points appear to be freely available public WiFi networks at public places, such as hotels, libraries, airports, railway stations or even coffee shops or hotels, with sufficiently familiar names like “Coffehouse Freenet” or “Airport Free WiFi” to attract users to connect to them. In worst cases, such malicious services prompt the user to create a user account with a username and password to access the free services. A large number of naive or ignorant users create accounts on such access points by using the same combination of email or username and password, that they use for many other services. This allows hackers to capture the victim’s sensitive user information and exploit it for malicious intent. Hence, extreme precaution must be taken while connecting to any new WiFi access point at any public place. In addition to this, users must never use personal details and regular account details to create accounts on such services. Instead, they should always use a unique combination of username and password to create a login on any new service. Compared to random or anonymous WiFi access spots with minimum or no security features, the paid wireless networks controlled by business groups with much more protected and controlled access should be preferred. Analysis of network traffic between router and mobile device of a victim user is known as session hijacking in cybersecurity terms.
In the case of mobile devices, a network attack known as sidejacking is employed to capture data from vulnerable data traffic. For this purpose, hackers use various tools to automate session hijacking via sidejacking attack [24]. A similar tool of this class has been developed by Mozilla as a plugin for Firefox web browser known as “Firesheep.” Firesheep [31] automates sidejacking between vulnerable WiFi networks and victim mobile devices to capture and exploit data traffic using a packet sniffer. Risk of compromise of wireless networks and mobile hotspots can be minimized by disabling automated search and by using secure wireless networks.
12.2.5 Data Transfer-Based Threats
Use of weak encryption algorithms or improper implementation of strong encryption techniques by the application developers can lead to cracked encryption threats. In the first case, many times developers use fragile encryption algorithms with well-known vulnerabilities only to speed up the development process [3, 5]. Such fragility attracts attackers to crack the applications and capture sensitive user data. In the later case, back doors or deficiencies are left open by developers while working with strong encryption techniques, which can also lead to the same impact on the privacy or security of user data. For example, multiple messaging applications provide encryption of user data only at sender and receiver ends. This leaves sufficient space for attackers in intermediate networks to capture the data and exploit it for malicious intent without any requirement of user details and passwords. Satisfactory enforcement of encryption practices through the network only practices encountering data transfer-based threats.
12.2.6 Improper Session Management-Based Threats
Many applications make use of runtime-generated access tokens to enable network access to connected devices. These access tokens also facilitate connectivity between the network and devices without repeated re-authentication for a predefined time limit. Applications with sufficient security features, generate new and confidential access tokens to enable network access for every session. Improper handling of session variables like access tokens, by the application, can naively leak them to malicious actors, risking the entire communication to illegitimate exploits.
12.2.7 Bluetooth-Based Threats
Bluetooth technology allows mobile devices to wirelessly exchange data among devices as well as connect peripherals like mouse and keyboards. But mobile devices with Bluetooth in the activated mode, set to be discoverable for other devices, are exposed to attacks such as blue snarfing, blue jacking and blue jugging discussed below [5]. Theft of private and sensitive user data, such as phone call logs, browsing history, GPS details, contacts, email communications and text messages, can be executed by using malicious software applications via Bluetooth. This theft of user data via Bluetooth is referred to as a Bluesnarfing attack. Hackers execute Bluesnarfing attacks by scanning for nearby devices with enabled Bluetooth via their smartphone or laptop. Applications used for bluesnarfing can steal data from victim’s mobile device in silent and undetectable mode. The worst aspect of bluesnarfing attack is that turning off Bluetooth on the device cannot guarantee security. This is because a mobile device with enabled but hidden Bluetooth can also be discovered and exploited by making a guess of its MAC address through brute force attack [25].
A Bluesnarfing attack causes theft of user data from the device, while a Bluebugging attack leads to the silent broadcast of anonymous and unwanted messages to other Bluetoothenabled devices without the victim’s consent and knowledge. A Bluejacking attack is executed by backdoor bypassing of victim’s mobile device access leading to silent compromise of control of their device. A bluejacking attack is capable of creating new entries in the address book, typing and transmitting new text messages and even transferring files via Bluetooth.
12.2.8 Application Platform-Based Threats
Despite thorough scanning, every mobile application submitted even to trusted online download platforms like Apple’s iTunes and Android Play Store cannot be guaranteed to be genuine and safe in all terms. Some suspicious applications may lead to unauthorized access to user credentials, siphoning of internet data or even make silent unapproved purchases from the user’s account. In the year 2010, a Vietnamese app developer was blacklisted from iTunes store by Apple Inc. The reason for this penalty was that he apparently charged users for books which they never purchased via his app. The developer committed this fraud only to boost his rating in the iTunes store and improve his ratings. To prevent such exploits, the users should try to install and use mobile apps of only trusted vendors and developers [26]. In a case where it is required to install an app from a new developer, a thorough study of app details like developer name, affiliations, user ratings and permissions required by an app, must be done.
A major category of such suspicious apps is free mobile apps available on these platforms. Such suspicious free mobile apps, like games or utility apps, are more likely to exploit device features and compromise user data. They are usually capable of accessing the internet, tracking user location and even accessing sensitive data. For example, 94% of gambling mobile games provided as free apps demand a user’s permission to send text messages, use the phone camera and even to make outgoing phone calls [26]. The users must be alert and substantiate the intent of such a free gaming app asking for access to these features.
But parallel to genuine application platforms mentioned above, there are also third-party application stores that provide alternative apps for users. Downloading and installing apps from these unauthorized platforms on a device can be very hazardous for the end user. Such application stores always remain at high risk of being run by cyber criminals by hosting fake copies of legitimate applications altered to execute fraudulent activities.
12.3 Smartphones as a Tool of Crime
The vulnerabilities of mobile computing infrastructures exist in device hardware, application designs, coding standards, wireless connectivity and even in data transfer protocols. Such vulnerabilities always risk the profits of mobile computing at the cost of cybersecurity threats. The increasing attention of cyber criminals on the mobile sector is a matter of serious concern for everyone. High prices, portability and immense computing potential of mobile devices make them a focus of criminal exploits [6]. But above all, the extensive dependence of common folks on their mobile devices for every little thing they require makes these machines a lucrative target for cyber criminals. In this scenario, user data like contacts, emails, bank details, and passwords are at stake.
12.4 Types of Mobile Phone-Related Crimes
Activities associated with criminal usage of mobile phones can be considered as mobile crimes. Such activities make use of one or more potential uses of mobile devices to commit crimes. Here we discuss various types of mobile crimes.
Physical Theft: The ease of carrying mobile devices make them highly susceptible to physical theft. Criminals are able to demand an attractive price for stolen mobile devices on the black market due to their pricey hardware. But for a user, who is a victim of mobile theft or physical loss, the damage extends to the loss of the sensitive and private user information stored on the device [7]. Modern mobile devices are well equipped with character- or sequence-based passwords, biometric access restrictions [19], user data encryption and data erasing mechanisms to minimize the information loss. Also, regular and automatic backup of user data on cloud-based locations can almost neutralize the damage of data loss due to physical theft of a mobile device.
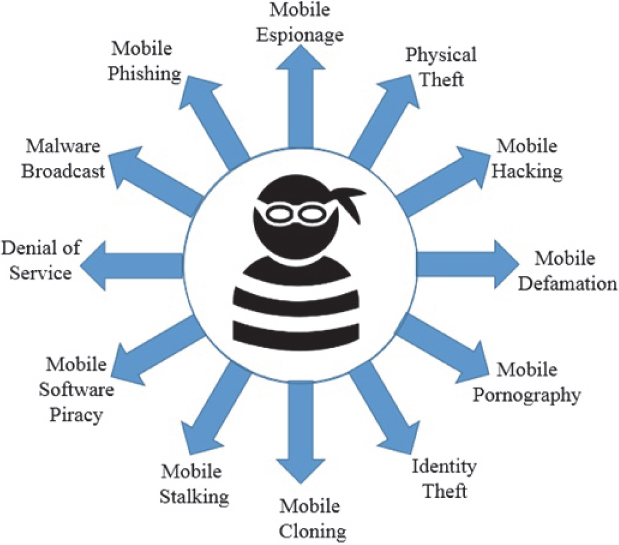
Mobile Hacking: Any illegitimate intrusion into a computing device and/or network without the consent of its owner can be termed as hacking or, more specifically, cracking. This definition also covers the acts breaching the security of mobile devices, communication systems and/or networks [8]. To implement mobile hacking, intentionally written scripts or malicious applications are utilized by hackers to target mobile devices and systems connected to them.
Mobile Cyber Defamation: Transfer or broadcast of intentionally written derogatory, humiliating and obscene information, offensive to the reputation and/or survival of a person or organization, causing them physical and/or financial loss is referred to as defamation [8]. Use of mobile applications, such as SMS, emails or phone calls, to commit acts of defamation can be classified as mobile defamation.
Mobile Pornography: Pornography is considered a crime in many countries. After the advent of the Internet and computer technology, the spread of pornography has taken a tremendous leap. Use of mobile devices, communication systems, internet and connected mobile-based services for creation and transmission of pornography is covered under mobile pornography [7, 9]. Mobile pornography has kept pace with evolving mobile devices. In India, mobile pornography is a punishable offense under section 67B of the amended Indian Information Technology Act, 2000, with a maximum sentence of 5 years and fine of up to 10 lakhs rupees.
Mobile Identity Theft: User information, such as email conversations, SMS messages, phone contacts, call logs and browsing history are generally stored on mobile devices. In addition, these devices also store and transfer sensitive information like financial details and health records, etc. Therefore, it has become critical to safeguard such information on mobile devices to prevent any unexpected loss.
Every person with a mobile phone has a unique 10-digit number that he willingly shares and exchanges with friends as well as strangers, depending on the required circumstances. People also download and install various mobile apps that require a valid mobile number to continue services [9, 10]. They even write and exchange their mobile numbers on public documents like medical prescriptions, official pages and survey forms of grocery stores to claim reward points. With the advent of the internet of things (IoT)-based technologies, now smartphones are being optimized to perform all sorts of remote control functions from controlling the locks and lights in homes to collecting sensor-based data. These data, in turn, are collected and stored in databases, having much more than social security numbers, totally exposed to fraudsters, thieves and scammers which can lead to identity theft via mobile devices.
Mobile Cloning: Transfer of secured device sensitive data from one phone to another phone to make it an exact replica of the original phone is referred to as mobile cloning. After cloning, calls and messages can be exchanged by both phones, while the owner of the original phone is billed for all activities of the cloned phone. In CDMA phones, ESN (electronic serial number) and MIN (mobile identification number) are presented on an EPROM chip. To clone a CDMA phone, the ESN/MIN pair on the EPROM chip must be copied onto an EPROM chip of another CDMA phone. In the case of GSM phones, cloning of an original SIM card to another SIM can complete the task of cloning [8, 10]. A new generation of devices known as “magic” phones scans their surroundings to copy the identities of nearby phones in use.
Mobile Stalking: Continuous and repeated acts of threatening and harassment targeting a victim’s life, public image and property is covered under stalking, Making use of mobile devices like smartphones for following the victim’s location without their consent, vandalizing their property, making harassing communications via call or messages, and posting threatening messages or objects is termed mobile stalking. If left unchecked, stalking may lead to serious acts of violence or damage to victims and their belongings.
Denial-of-Service Attack: A DoS attack is another type of cyberattack aimed at flooding the victim’s computing resources with fake or bogus input to disrupt normal services. Making use of mobile devices, to flood a victim’s email inbox, SMS inbox folder or phone memory, depriving them of normally entitled services, can be classified as a mobile DoS attack.
Mobile Software Piracy: Illegal copying, forging or distribution of genuine and copyright protected mobile software products with an intention to fake or damage the original software is covered under mobile software piracy.
Mobile Malware Dissemination: After the era of desktop and laptop targeted malware applications, new malware threats are constantly evolving along with the improving architectures of mobile devices. Malware, including Trojan, worm, virus, ransomware and spyware, can rigorously damage normal functionalities of mobile devices. Also, malware infected mobile devices also pose a high risk of infecting other connected devices in their networks [3, 28].
Mobile Phishing: To a certain extent, risk of malware propagation can be encountered by using updated anti-virus software products. But another class of social engineeringbased attacks that trick the users of mobile devices to fall prey to malicious exploits, is phishing attacks. Phishing attacks can trick a victim mobile user to naively handover their user details, login credentials, financial information, browsing history or download malware on their mobile device [29]. To execute these attacks, a sufficiently harmless and reasonable looking link to a website is sent to the victim’s mobile device by the cyber criminals. The link can be embedded into a webpage, a text message or an application-specific message such as WhatsApp, etc. The formal and sophisticated language of the approach of such links generally makes even the experienced user believe the context and click on them. After clicking the link, malicious applications or processes, crafted specifically for target devices, are triggered to execute in the background of the mobile device. After execution, such attacks are capable of stealing sensitive data or even damaging the normal functioning of the device. Phishing attacks via mobile phones can be further elaborated into the following categories [7, 8]:
Vishing: The act of scamming or tricking a mobile user by making use of telephonic conversation to unknowingly surrender his sensitive information to be exploited for identity theft is known as vishing [12]. Generally, in vishing attack, the attacker impersonates a worker or official of a genuine business group and tricks the user by threatening service disruption, official penalty or promising a significant profit.
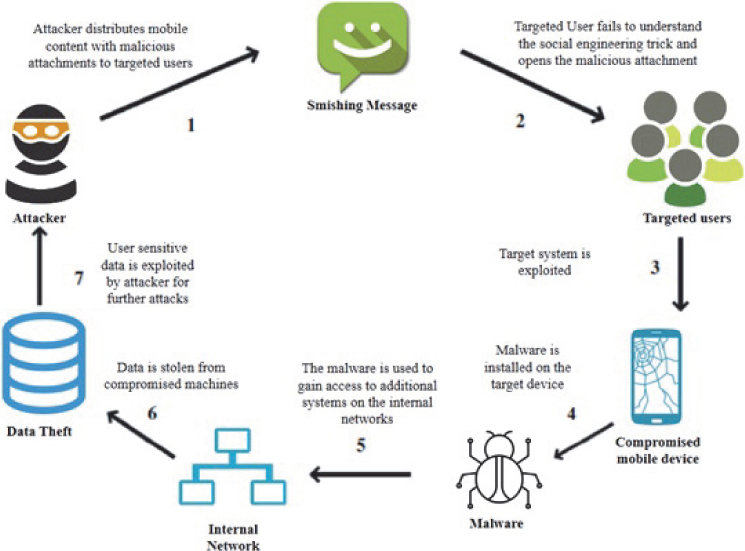
The attempt to approach a potential victim when executed via an SMS message instead of a phone call constitutes the next class of mobile phishing attacks called SMiShing. SMiShing attacks prompt the user to unknowingly download and install a malware onto their mobile device by clicking on a deceptive text link. Usually, instead of a clear sender phone number, SMiShing messages are received from a number “3949” like the source. Such messages, instead of a genuine smartphone number, are sent via an email address to hide the identity of the attacker. Often such messages contain a URL or phone number linked to an automated voice response system. These systems ask users about their sensitive user data that requires their immediate attention. Instead of immediate disruption of services, the aim of SMiShing is to track the user or steal sensitive user information by downloading malware [12, 13].
A hybrid format of phishing attacks are lottery scams or advance fee frauds that are delivered by emails or text messages to the target user. The content of such attack messages displays catchy lines like “your credit is waiting,” “claim your trip to Australia” or “you have won,” and so on. Lottery scam attacks trick the victim into believing that they have won a large sum of money, which will be accessible after handing over their sensitive information or paying a hefty sum of money.
Because the nature of phishing attacks make them difficult to recognize, the best possible strategies to prevent them are to scan the addresses and names of every digital content, read every SMS and email carefully to ensure its origin, check for grammatical errors and totally avoid opening any attachments linked to the message [14].
Mobile Espionage: Espionage refers to silent spying or monitoring of individuals or groups to obtain confidential data without the owner’s consent and knowledge. But espionage via mobile devices can be considered as a mobile and more elaborate version of the same. Modern mobile devices are equipped with high computational capacities, huge memory banks, movement tracking GPS, good resolution camera and accessories like the microphone to enhance user experience. With these capabilities, a mobile device becomes an attractive tool for hackers and cyber criminals to execute espionage. Besides these features, the sensitive data shared by users in real time build a sufficient reason for the growing concern of governments and organizations for their data security. The advent of monitoring apps like Mobistealth [11] that exploit aforesaid capacities of a mobile device, raised red flags over the possible exploitation of such features by attackers for cyber espionage. For competitors, unfiltered discussions about strategic plans, innovations, financial information, legal discussions, and more highly desirable business information can be made available through espionage. Espionage is a potential tool for nations for silent monitoring of its citizens’ activities and foreign rivals to ensure safety and security. Gathering conversational data, verbal commands and requests and pairing these with location data provide powerful profiling information desired by advertisers. Swept up in this information gathering may be sensitive corporate or client information. For malicious actors like hackers and cyber criminals, motivated by a variety of reasons, including economic, political, social or personal, smartphones serve as a potential attack vector.
12.5 Types of Mobile Fraud
Frauds committed using mobile devices comprise a wide range of cheats and tricks to motivate the potential target to surrender to the malicious intent of the hackers or criminals. Here, the malicious intent may include to influence the victim to purchase substandard, overpriced or non-existent products or services, to make phone calls or send text messages to links of such products, to unknowingly subscribe the expensive subscriptions of these services or in worst case, to surrender their sensitive data, such as financial details, etc., to the criminals. For a user with fair experience of desktop computing and email communication, figuring out a malicious email from its awkward language, misspelt words or poor graphics is not a very tough task. In most cases, the users simply delete such spam emails without even opening them. But the same is not the case with mobile fraud [8, 9]. A reason for this is that because till now, mobile fraud is less widespread as compared to junk email. SMS messages also have much higher delivery and open rates relative to emails. Besides this, a single and comprehensive SMS spam filtering mechanism is far from evolving. In this section, we will discuss various mobile-based frauds.
Missed Call Scams: Generally, every mobile phone user receives missed calls on their device. But in the case of a missed call scam, a missed call may be of a very short duration from an unknown number usually from a foreign location. As the targeted victim is unable to recognize the calling number, they simply call back. This call from victim’s device may get redirected to a premium rate service, costing them an unexpected money charge or even more.
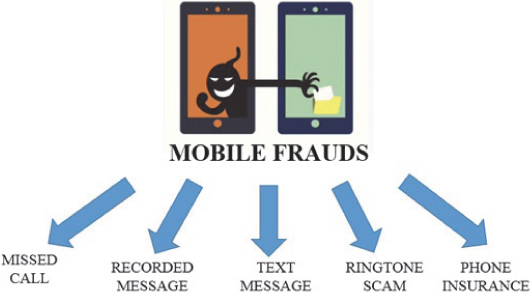
Recorded Message Scam: In this format of mobile fraud, the user is prompted by a recorded message played on a phone call to call back on another number telling him that he has won a prize, and must call on the next number to claim it. But the next provided number may be the premium rate service number, as discusses in the missed call scam section, resulting in the user incurring a hefty call charge. In addition to this, the above-mentioned prize may also be another fraudulent ringtone or caller tune subscription service, causing further loss to the victim.
Text Message Scams: The user receives an SMS text message from an unknown sender containing a very friendly language, like “Hey, it’s Mike. I’m back New Jersey! When can we catch up and hang out?”” Assuming such message to be from the wrong sender, the user naively calls back on the number, just to confirm that it’s a wrong number. But in the case of a text message scam, the victim again is charged with a hefty premium rate for the call or a high rate lengthy SMS exchange similar to above formats of mobile fraud.
Ringtone Scams: Ringtone scams prompt the target mobile user with an offer to download or subscribe to a very cheap or even free ringtone. On accepting such offer, the victim user mistakenly subscribes to another costly fraudulent service that keeps on sending more ringtones and continues charging high premium rates for them. A basic difference among such fraudsters and legitimate ringtone selling companies is that, unlike genuine ringtone selling companies, the ringtone scammers keep hiding the true cost of their offers and services.
Phone Insurance Scams: After collecting data from newly registered mobile users from a shop of mobile devices or from a mobile network provider, fraudsters call the target users with offers to sell smartphone insurance for the newly purchased device. On falling victim to such scams, the user ends up with no insurance at all or with a very poor and costly phone insurance policy.
12.6 Case Studies
12.6.1 Mobile Identity Theft
One of the fastest growing types of threats to the security of the common masses is mobile identity theft. A major cause of this is the dominance of mobile devices such as smartphones and tablets in every sphere of modern society [10, 16]. The possible implications of mobile identity theft are discussed in this section.
- Gather User Information: A mobile number is a unique communication entity reserved for an individual user or single group. Due to this uniqueness, many social media platforms, mobile apps and financial applications demand mobile numbers of their users as social identifiers. This fact leads to the possibility of a criminal or hacker to search for a smartphone number in a search engine or a website and collect information about a target user sufficient to exploit it for malicious intent. Such malicious intent may include social engineering scams or even financial damage simply by figuring out the true online identity of the victim. For example, if a user’s cell phone number is connected to his Facebook account, someone could use it to try and obtain his name either through the site’s general search by using the forgot password feature at login and entering the number instead of a name or email address [15].
- Launch SMiShing Attacks and Phone Scams: If a user’s smartphone number gets into the hands of a criminal, they can use it to their advantage and try to scam the user via text messages which may be sufficiently convincing, especially if the scammer has done their homework on the user prior to their attempt.
- Take over User’s Mobile Account: People search or reverse-lookup websites allow anyone to find out information about a cell phone number, including the carrier network provider, name and city/state associated with the number. Using information collected about the user, they will impersonate the user either in-person or over the phone to gain access to their mobile account. This enables them to upgrade for new phones for free (which they can sell for a profit), add additional lines or take over their number entirely (known as a SIM swap) [17]. They might also try to open up a mobile account at a different carrier using that information.
- Gain Access to Financial Accounts: Beyond wreaking havoc on a mobile account, access to a mobile phone number enables cyber criminals to exploit the connected accounts by using SMS text message-based two-factor authentication. If the criminals own the control of the phone number linked to these accounts, the text message, email communication or even a phone call sent to verify a victim user’s identity will be sent to them instead of the real owner. This could enable them to change the passwords and get access to victim’s accounts, possibly leading to unauthorized charges on credit cards or a siphoning of bank accounts.
- Terrorist Uses of Smartphone: Similar to criminals, terrorists have also worked up elaborate mechanisms to fraudulently acquire random cell phone numbers and devices under unsuspecting victims’ names. For extremely low prices, numbers and devices are accessible to terrorists for exploitation in their malicious objectives. Some such issues are presented below.
- Burner Phones: A burner phone is an inexpensive and mostly refurbished mobile phone [18] designed for temporary use, after which it may be discarded. Burner phones are mostly purchased with prepaid minutes and without a contract. Using phones and increasing balances purchased with cash rather than a credit card and having no contract with a service provider clearly imply that no record of the user connected to the phone number can’t be traced. If the user suspects that the number has been traced or compromised, they can just dump the phone and purchase a new one, which would have a totally new number. Today, a large civil population uses smartphones, and smartphone numbers are increasingly being used as unique profile identifiers that connect user data across multiple databases. Moreover, phone numbers aren’t subject to privacy requirements like credit card details and social security numbers and thus are shared frequently. As a result, mobile number privacy is a growing security issue. An easy method of increasing mobile security is the use of burner phone mobile apps or services rather than using an actual device, which provides a temporary phone number that can be provided instead of the user’s actual cell number. One such application is the Burner mobile app [19] service, that has numbers that usually expire after a certain time period. These numbers can be used by paying for them with in-app purchases. If they lapse, they’re burned. The premium subscription gives the user a permanent second number. When a user calls via Burner, it actually calls Burner, which in turn replaces a relay call to the number you want to reach. Details of the Paris terror attacks [20] reveal that instead of encryption, consistent use of prepaid burner phones helped the terrorists to remain off the radar of the intelligence services. The three terrorist teams in Paris used only new phones, activated minutes before the attacks and discarded after use. Later, the investigators found a Samsung phone in a dustbin near a theater. The phone had a Belgian SIM card used only since the day before the attack. The phone was used to call just one other unidentified number in Belgium. As police pieced together the movements of the attackers, they found yet more burner phones.
- Smartphone Bomb: Generally, two smartphones are used in the bomb-making process; one to call the other, which then transmits a signal to a circuit board and triggers the explosion [21]. Smartphones are basically small and sophisticated radio devices that translate a radio signal into an equivalent electrical pulse and convert that current into sound. If a smartphone is integrated with a bomb as a triggering device, the electrical impulse generated by the smartphone is adequate to create a detonation charge to trigger the main explosive compound of the bomb. Crafting a mobile phone into a remotely detonable bomb trigger is very easy and cheap due to the availability of online information and spare parts. Exploding such bombs also simply requires dialing the mobile number of the SIM in the phone connected to the detonator. The 28-year-old terrorist, Ahmad Khan Rahami, the suspect in twin bombings at locations in New Jersey and New York, admitted the use of smartphones [22] to detonate his homemade bombing devices. The Nokia 105 smartphone is a favorite device among ISIS fighters [23]. The cheap, durable and long battery life Nokia 105 phone is the most popular remote bomb-triggering device among ISIS organizations for detonating bombs. ISIS has assembled and deployed improvised explosive devices across the battlefield on a large scale, causing a large number of civilian and military casualties.”
12.6.2 Data Theft by Applications
Parallel to malicious mobile applications, in recent times some genuine applications have also been found to be continuously stealing data related to user communications and preferences. Such information is collected from data audio codecs of the call, duration of user calls, timestamps of user activities, frequently accessed contacts and far more. A similar case of data theft by a genuine chat application called “WhatsApp” was brought to light by researchers at the University of New Haven [27, 30].
The information stolen in real time was noted to be transferred to the official servers of WhatsApp1. The researchers created some experimental participant users to conduct the experiment and tested the hypothesis of data theft by the app. After that, the users were authenticated by making calls on WhatsApp via a communication channel created by Opus codec at 8 and 16 KHz frequencies. Later, upon analyzing the destination IP addresses and relay servers for the calls, the experiment revealed that the application was stealing sensitive user data like call’s audio codec, phone numbers and timestamps of calls. The analysis of message exchange mechanism between the relay servers of the app and an Android version of the app also exposed the collection of data accumulation pattern of WhatsApp via FunXMPP2 internet protocol. After this experimental case study of WhatsApp, it can be concluded that leakage, theft or silent monitoring of user information is also possible via even the most trusted and safe-looking mobile applications.
12.6.3 SIM Card Fraud
One of the most sophisticated and unusual techniques of mobile fraud that leads the criminals to access victim’s financial details is SIM card fraud. A combination of social engineering and exhaustive surveys paves the way for attackers to smoothly conduct this attack.
To start with, loosely handled, stolen or misplaced bank account statements of a potential target provide the access to bank details to attackers. After locating a potential target, the attackers conduct exhaustive social engineering and survey to collect and assemble sufficient personal information about the target from their social media account profiles including the details of their contact number and service provider. This survey enables the attackers to answer basic security questions to be asked by the mobile service provider of the target user.
Now the attackers call the target, convincing them to shut down their phone temporarily, either by repeatedly making blank calls or posing as a call for an upgrade from the mobile service provider. During the period when the phone of the target user is shut down, the attackers call the service provider of the target, pretending to be the target user and claim that their phone is damaged or lost. In such situations, the service provider company asks basic security questions which are successfully answered by the attacker, confirming the identity of the target. This leads the service provider to cancel the existing SIM and activating a new SIM possessed by the attacker.
Now, the attacker contacts the bank of the target user with their new SIM card and claims to have forgotten their access password. After asking basic security questions similar to the mobile service provider, the bank also sends a one-time access code or one-time password (OTP) to the phone number of the target user, which is actually received by the attacker.
Now the attacker opens a fake parallel account in the bank of the targeted user in his name and ultimately drains the user’s money into this new fake account without the user’s consent and knowledge. The worst part of this fraud is that the mobile user victim is totally unaware of this attack until their mobile seizes to operate or they are unable to access financial details of their bank accounts. By then, the attackers drain all the money from the victim’s fake account to finalize this attack.
12.7 Preventive Measures and Precautions
12.7.1 Against Physical Loss and Theft of the Mobile Device
Physical loss of device due to theft or misplacement is a severe security threat because in addition to the financial damage of the device’s cost, the user also loses total physical control over their data. Concerning human nature and accidental possibilities, such physical losses cannot be guaranteed to stop, but their impacts can be sufficiently reduced if the users adopt the following measures:
- Check security features provided by the mobile service provider: Generally, all mobile service vendors provide sufficiently strict security policies to help the users in protecting their data. Provision of secret security questions and PIN numbers are examples of these securities. Unique password combinations and random security questions, having no connection to the user’s social media profile are preferable for best use of these security features. It is also preferable for users to go through the security policy statements of service providers before signing up for any contract with them.
- Don’t store critical information on the mobile device: Sensitive information details, such as account passwords, PIN numbers, financial details, etc., are at high risk for loss or theft if stored in texts or emails. Theft or loss of mobile devices must be immediately shared with the service providers to help them remotely deactivate the device as soon as possible. After this, the user must change passwords of all connected online accounts accessible through their stolen device.
- Setting up sufficiently strong access passcodes: In case of theft or loss, a strong passcode safeguards user’s data to a satisfactory level. Lack of any passcode or knowledge of this passcode by many people risks the security of the data present on the device to a great extent.
- Regular and cloud-based backup: Mobile users must regularly back up their data stored on their devices on secondary storage devices such as external backup drives or memory cards. To improve the security level and accessibility, same data can also be saved to cloud-based backup services. This will allow the user to remotely access, update and restore their data from any location in case their device is lost, stolen or is even accidentally erased.
- Proper erasing of data before switching to a new device: Before recycling, donating or even reselling the mobile device, erasing the data efficiently from the old device helps to protect its privacy and security. For this purpose, certain devices, as well as software applications, are available that ensure satisfactory deletion of old data.
- Installing tracking apps on the device: Modern mobile devices are equipped with remote tracking, locking and even data wiping features. Multiple unsuccessful login attempts can lead to self-destruction of stored data on the device. Several applications are now also available to provide these features.
12.7.2 Against SMiShing Attacks
As discussed earlier, SMiShing attacks act as bait for mobile users who are potential targets for exploitation by cyber criminals. Generally, SMiShing attempts are social engineering attacks embedded in text or phone call formats to prompt the victim to naively attempt the security violation of their device. But following precautions can save the mobile users from SMiShing attacks to a great extent.
- Never click on a suspicious link or number: On receiving a text message or phone call with a suspicious content or from an unknown source prompting to perform a specific action by clicking on a link or dialing a given number, the user must never perform the suggested action. This inactivity will automatically disarm the thrown bait of the remote fraudster or cyber criminal.
Even if such a message prompts in a prohibitive way like to stop receiving such messages in the future, click the NO button at the bottom or if you do not wish to receive such messages in the future, simply respond by texting “NO”; the user must avoid performing the suggested negative action, as it might lead to the same consequential exploits mentioned above. - Confirm the validity of the source: On receiving such doubtful communication, the target user should always try to ensure its originating source or sender. This search for its source can be done on search engines or address directories over the web.
- In case of imposters, confirm from the original authorities: If a doubtful message or call pretending to be from one of the known sources, prompts the user for certain action, it is better to contact the original authority to confirm the message. For example, if a user receives a message from his bank such as “Your policy reward points are about to lapse in 2 days, click on the link to claim your points.” Here, instead of clicking on the link, and possibly surrendering their financial information, the user should contact their bank directly to confirm the validity of the message.
- Never provide any personal or sensitive information: The scope of personal or sensitive information ranges from financial details, one time passwords (OTP), user account details to even name and address of the target user. SMiShing links commonly threaten the target mobile users with blocking or disruption of a specific service such as blocking of account or credit card penalties. Surrendering any such information may lead to serious consequences against the security of linked data. Instead, the users must remember that any authorities of any legitimate service will never ask them about their sensitive information. In case of persisting doubt, the users must themselves contact the authorized personnel of the service.
12.7.3 Against App-Based Attacks
- Download from trusted application platforms only: Try to always download a mobile application from trusted mobile app download platforms like “Google Play Store”3 for Android device and “iTunes”4 for Apple devices. Applications loaded on these platforms are thoroughly tested and confirmed for their behavior and security by the authorities to maintain the trust and repute of the hosting companies. Apps downloaded from unknown or untrusted platforms may carry malware or spyware that can risk the security of the user data and device [29].
- Exhaustively examine the details of the app before downloading: Ratings provided by users, history and reviews about the authors and update history of the app must be carefully examined before installation of any app even from the most trusted sources mentioned above. This check can save the user from any unexpected loss or damage due to the app, previously experienced by other users.
- Check the app permissions before installation: The user must cautiously read and then grant permissions to the new app for accessing the device data and services. This scrutiny is extremely important for any app to know its intended future behavior after installation on the device. Any unexpected demand for access permission like access to the camera for a gaming app must be reported accordingly.
- Checking phone bill: In cases of abnormal data exchange, sudden deprecated battery life or heating of the device, do check the bill incurred due to the device. The bill may project unexpected rises due to suspicious calling charges or unexpected text message exchanges.
- Install security app: The users must install a security application that scans the behavior of every app installed on the device. In case of any spyware or malware, the security app will alarm the user of the abnormal behavior of the app.
12.7.4 Against Identity Theft and SIM Card Fraud
To protect cell phone number, there are certainly some actions that the users can take to protect themselves from falling victim to cell phone number identity theft.
- Staying vigilant: The users must get in the habit of checking their bank and phone accounts frequently to make sure there’s no suspicious activity. Staying up-to-date with any attacks that have hit companies they shop with will make sure that they aren’t among the victims.
- Utilizing the safeguards provided by companies: The email based or one-time password (OTP)-based authentications can certainly be exploited by criminals. But their utter absence can expose the user against higher proximity of attacks.
- Creating a PIN number for mobile phone accounts: Creation of PIN for mobile services is an optional security process provided by the services providers. But a PIN-based access creates an extra layer of security for the user’s account by enforcing a 4 or 6 digit access restriction prior to performing any crucial account changes.
- Use of unique and strong security access combinations: Strong passwords consist of a unique combination of alphabets, special characters and numbers with a sufficient length. Similarly, selection of security questions and their answers must be unrelated to any social media profile of the user.
- Do not make personal information public: Too much exposure of personal information on social media can help criminals to answer security questions to access the details of the target user. If information about common facts like hometown, spouse name, details of family members, own and their birthday, mother’s maiden name, the name of the first pet, is available on users’ social media profiles, it may risk the security of user data to a great extent. In addition, the users must keep checking their social network privacy settings to ensure that their information isn’t easily harvestable.
- Use a virtual number for noncritical use: One of the best ways to limit the amount of personally identifying data tied to a main contact number is to avoid sharing it with anyone except the closest trusted individuals. Use of virtual numbers for nonpersonal matters can help to sustain privacy in such cases. Virtual numbers can accept text messages and phone calls and can be set to forward to the actual contact number to avoid missing any genuine and important communications.
- Establish a PIN or password with the mobile carrier: All mobile service providers allow their users to set up an additional password or SIM-based PIN code that can be required to make any changes to the mobile account. This safeguard mechanism can critically help in case of SIM card-based fraud. Here, even if the criminal acquires a new SIM with user’s number, he won’t be able to access it without the SIM-based PIN code.
- Report suspicious activity immediately: If the phone suddenly becomes disconnected and restarting it doesn’t make any changes to the signal, or the phone bill has sudden unknown hikes, or the phone is receiving multiple repeated nuisance calls, the user must contact their mobile carrier immediately.
The sooner such abnormalities as observed and acted upon, the lesser is the extent of damage caused. Users must be also on alert for suspicious phone calls or messages pretending to be from their mobile carrier.
12.8 Conclusion
Modem mobile communication technologies have empowered individuals and organizations to utilize them for real-time communication and data transfer to their advantage. This advantage is embedded with risks of cybersecurity of the linked devices and the data they manage. To counter these risks, effective management policies, adequate training and comprehensive knowledge of such exploits and their preventions are crucial for safe and uninterrupted productivity. The quest for the upgrade of security threats and improvement of security mechanisms will go on in parallel with the evolution of the capacities of the mobile devices in order to keep connected mobile users and their resources safe and protected.
References
1. Becher, M., Freiling, F. C., Hoffmann, J., Holz, T., Uellenbeck, S., & Wolf, C. (2011, May). Mobile security catching up? revealing the nuts and bolts of the security of mobile devices. In Security and Privacy (SP), 2011 IEEE Symposium on (pp. 96-111). IEEE.
2. Li, Q., & Clark, G. (2013). Mobile security: a look ahead. IEEE Security & Privacy, 11(1), 78-81.
3. Jain, A. K., & Shanbhag, D. (2012). Addressing security and privacy risks in mobile applications. IT Professional, 14(5), 28-33.
4. La Polla, M., Martinelli, F., & Sgandurra, D. (2013). A survey on security for mobile devices. IEEE communications surveys & tutorials, 15(1), 446-471.
5. Miller, K. W., Voas, J., & Hurlburt, G. F. (2012). BYOD: Security and privacy considerations. It Professional, 14(5), 53-55.
6. Burge, P., Shawe-Taylor, J., Cooke, C., Moreau, Y., Preneel, B., & Stoermann, C. (1997). Fraud detection and management in mobile telecommunications networks.
7. Badhe, A. (2016). Click Fraud Detection In Mobile Ads Served In Programmatic Exchanges. International Journal of Scientific Technology & Research, 5(4), 1.
8. Barson, P., Field, S., Davey, N., McAskie, G., & Frank, R. (1996). The detection of fraud in mobile phone networks. Neural Network World, 6(4), 477-484.
9. Shawe-Taylor, J., Howker, K., & Burge, P. (1999). Detection of fraud in mobile telecommunications. Information Security Technical Report, 4(1), 16-28.
10. Wang, W., Yuan, Y., & Archer, N. (2006). A contextual framework for combating identity theft. IEEE Security & Privacy, 4(2), 30-38.
11. Sivaramarajalu, R. V., Krishna, J. H., & Kumar, R. S. (2012). Security Threats of Smart Phones. International Journal of Data & Network Security, 1(3), 51-53.
12. Candia, J., Gonzlez, M. C., Wang, P., Schoenharl, T., Madey, G., & Barabsi, A. L. (2008). Uncovering individual and collective human dynamics from mobile phone records. Journal of physics A: mathematical and theoretical, 41(22), 224015.
13. Shahriar, H., Klintic, T., & Clincy, V. (2015). Mobile phishing attacks and mitigation techniques. Journal of Information Security, 6(03), 206.
14. Foozy, C. F. M., Ahmad, R., & Abdollah, M. F. (2013). Phishing detection taxonomy for mobile device. International Journal of Computer Science Issues (IJCSI), 10(1), 338-344.
15. Hoofnagle, C. J. (2007). Identity theft: Making the known unknowns known. Harv. JL & Tech., 21, 97.
16. Tachikawa, K. (2003). A perspective on the evolution of mobile communications. IEEE Communications magazine, 41(10), 66-73.
17. Lee, S., & Park, S. (2005, July). Mobile password system for enhancing usability-guaranteed security in mobile phone banking. In International Conference Human Society@ Internet (pp. 66-74). Springer, Berlin, Heidelberg.
18. Liao, K. C., Lee, W. H., Sung, M. H., & Lin, T. C. (2009, August). A one-time password scheme with QR-code based on mobile phone. In INC, IMS and IDC, 2009. NCM’09. Fifth International Joint Conference on (pp. 2069-2071). IEEE.
19. Trewin, S., Swart, C., Koved, L., Martino, J., Singh, K., & Ben-David, S. (2012, December). Biometric authentication on a mobile device: a study of user effort, error and task disruption. In Proceedings of the 28th Annual Computer Security Applications Conference (pp. 159-168). ACM.
20. Chen, C. L., Lee, C. C., & Hsu, C. Y. (2012). Mobile device integration of a fingerprint biometric remote authentication scheme. International Journal of Communication Systems, 25(5), 585-597.
21. Felt, A. P., Finifter, M., Chin, E., Hanna, S., & Wagner, D. (2011, October). A survey of mobile malware in the wild. In Proceedings of the 1st ACM workshop on Security and privacy in smartphones and mobile devices (pp. 3-14). ACM.
22. Chin, E., Felt, A. P., Sekar, V., & Wagner, D. (2012, July). Measuring user confidence in smartphone security and privacy. In Proceedings of the Eighth Symposium on Usable Privacy and Security (p. 1). ACM.
23. Chen, Y., Trappe, W., & Martin, R. P. (2007, June). Detecting and localizing wireless spoofing attacks. In Sensor, Mesh and Ad Hoc Communications and Networks, 2007. SECON’07. 4th Annual IEEE Communications Society Conference on (pp. 193-202). IEEE.
24. Riley, R. D., Ali, N. M., Al-Senaidi, K. S., & Al-Kuwari, A. L. (2010, August). Empowering users against sidejacking attacks. In ACM SIGCOMM Computer Communication Review (Vol. 40, No. 4, pp. 435-436). ACM.
25. Callaghan, M. J., Harkin, J., & McGinnity, T. M. (2006). Case study on the Bluetooth vulnerabilities in mobile devices. IJCSNS International Journal of Computer Science and Network Security, 6(4), 125-129.
26. Lee, G., & Raghu, T. S. (2014). Determinants of mobile apps’ success: Evidence from the app store market. Journal of Management Information Systems, 31(2), 133-170.
27. Lim, S. L., & Bentley, P. J. (2013, June). Investigating app store ranking algorithms using a simulation of mobile app ecosystems. In Evolutionary Computation (CEC), 2013 IEEE Congress on (pp. 2672-2679). IEEE.
28. Gutmann, P. (2007). The commercial malware industry. In DEFCON conference.
29. Ramu, S. (2012). Mobile malware evolution, detection and defense. EECE 571B, Term Survey Paper.
30. Karpisek, F., Baggili, I., & Breitinger, F. (2015). WhatsApp network forensics: Decrypting and understanding the WhatsApp call signaling messages. Digital Investigation, 15, 110-118.
Barth, A. (2011). Network Working Group J. Hodges Internet-Draft PayPal Intended status: Standards Track C. Jackson Expires: February 6, 2012 Carnegie Mellon University.
