Chapter 6
Introduction to Blockchain Technology
Ishaani Priyadarshini
University of Delaware, Newark, Delaware, USA
Email: [email protected]
Abstract
Data is one of the most valuable assets. With cyber criminals becoming increasingly skillful in their attempts to steal valuable data, cybersecurity tends to be one of the greatest global concerns, making cyber defense mandatory. In the past, various techniques have been proposed owing to the security needs of various institutions; however, security assaults know no bounds, hence resulting in either the techniques being weakened or futile. The latest approach to protect valuable data is blockchain technology. In this chapter we will be taking a look at the concept of blockchain technology and how it is crucial to the security industry. As we delve a bit more into the details, we will be taking a look at the characteristics of blockchain technology, its structure, types, architecture and workings. Since Bitcoin is one of the most widespread applications of blockchain technology, this chapter also highlights the workings of bitcoins. Later on, we discuss a few of the challenges faced by this technology and its scope in the future.
Keywords: Blockchain, Bitcoin, cybersecurity
6.1 Introduction
One of the biggest cybersecurity issues faced by individual computer users as well as corporate firms is data theft, not only because it threatens an individual’s privacy, but also because it defeats one of the primary purposes of cybersecurity, i.e., confidentiality. Over the last few decades, several techniques have been proposed to deal with the issue, and many of them have been short lived, the reason being highly skilled cyber criminals. The latest addition is blockchain technology. Data dispersed over the network is prone to pilferage and plagiarism and often it is impossible to trace back to the cyber criminal. Blockchain technology eliminates the issue on many levels. A blockchain may be defined as a distributed database incorporating information or a book that marks all the events and transactions, executed and shared among concerned parties. The transactions are verified and information entered can never be erased. Every transaction made has a verifiable record. Blockchain technology finds its use in financial as well as non-financial sectors.
Blockchains are public registers such that all transactions are accumulated in a list of blocks [1]. When several blocks keep being added on, it leads to a chain-like formation. Blockchain technology is primarily based on the concepts of cryptography and distributed systems. Encryption techniques have been known to obscure content, such that it is available only to the intended users. But certain information needs to be available to specific groups of people, and it invites additional risk of the information getting manipulated. Blockchains tackle the issue. When data is accessed and updated, any change made is recorded and verified. Thereafter, it is encrypted so that further changes cannot be made. These changes are then updated into the main records. It is a repetitive process and every time a change is made, the information is preserved in a new block. It is fascinating to note that the first version of the information is well connected to the latest one. Thus, the changes made could be seen by everyone, but only the latest block can be modified. Blockchain imitates a distributed database by incorporating information duplicated across the network in real time. This means that the database has multiple locations and the records are public and easily verifiable. Since there is not a centralized version, data corruption is futile. Modifying records is tedious, thus making it easier to detect if someone is trying to do so. Thus, a blockchain could be thought of as a piece of data that has the following properties:
- It is constantly updated. This makes it easier for the users to access and modify data anytime.
- It is a distributed system in the sense that duplicated copies of data are stored and span the network. Updating one record updates every other copy in real time.
- It has verified data. When data is modified, it has to be verified by users using cryptographic techniques.
- The data is secure because cryptographic techniques and distributed systems do not allow tampering of data and security techniques.
One way of classifying blockchains is as permissionless blockchains and permissioned blockchains. Permissionless blockchains are open, they can be connected and abandoned by any peer as a reader or writer. They are decentralized and the information is readable by users. Permissioned blockchains authorize limited readers and writers. They are managed by a central entity which decides which individuals can read or write [2].
6.2 Need for Blockchain Security
Blockchain technology offers a way to share data and ensure transparency. The parties involved are guaranteed that the data they are dealing with is error free and cannot be changed. This feature is not only beneficial in the technical domain, but also finds its use beyond that. The following are a few reasons that make blockchain technology a favorite in many domains:
- It ensures transparency. Blockchain technology is an open source technology, such that other users cannot modify it. Logged data within a blockchain is difficult to alter, which makes it a relatively secure technology.
- It reduces transaction costs significantly. A blockchain does not need a third party to complete peer-to-peer and business transactions. Since no middlemen are involved in the transaction, the process is faster.
- Transaction settlements are quicker for blockchain technology as compared to traditional banks which rely on working hours and protocols. The location at different parts of the world further contributes to the delay. But blockchain does not have any such restrictions, thereby allowing faster transaction settlements.
- It promotes decentralization since there is not central data hub. This allows individual transactions to be authenticated. When information is updated to different servers, even if the information comes across adversaries, a trivial amount of data will be compromised.
- Since third parties are not involved in the transactions any more, users and developers take the initiative, thus introducing user controlled networks.
- It tracks the movement of goods, hence leading to transparency. This also simplifies several other management processes.
- In the case of irregularities being detected, one can always trace back to the point of origin, which makes investigations easy for executing required actions. This leads to quality assurance.
- Blockchain technology eliminates human error since it records data and protects it from being altered. Since records are verified everytime they pass from one node to the next, accuracy is guaranteed. This ultimately leads to accountability.
- Smart and sophisticated contracts can be easily validated, singed and enforced using blockchain technology.
- Blockchain technology eliminates electoral fraud, thus leading to clarity in voting.
- Reliability of blockchain technology is contemplated for stock exchanges.
- Energy supply can be accurately tracked.
- Blockchain technology encourages peer-to-peer global transactions. Cryptocurrency transactions are fast, secure and cheap.
- Blockchain technology leads to data objectivity. It not only preserves integrity of data but can also alert users if data is modified. Even if data is breached for an organization, it cannot be used, thus a balance is maintained between security and governance.
- Blockchain technology is used to authenticate devices. It may soon replace passwords, thus eliminating human intervention. This is because it does not promote centralized architecture.
- Since every transaction is time stamped and signed digitally, it highlights non-repudiation. Even with the system’s new iteration, previous records will be stored in the history log. This leads to traceability.
6.3 Characteristics of Blockchain Technology
In the previous sections, we have familiarized ourselves with the concept of blockchain technology. We now know that blockchains serve multiple purposes. The purposes are based on some characteristics, which are presented below [1, 2].
- Decentralization: Blockchain technology does not rely on a centralized transaction system to validate transactions. The involvement of central trusted agencies leads to cost and performance issues. Since a third party is not required for blockchains, they rely on cryptography and algorithms to maintain data consistency in distributed networks.
- Persistence: Validating transactions is quick in blockchain technology. Invalid transactions may be dropped off. Transactions which are already a part of the blockchain may neither be deleted nor rolled back. Data tampering could be easily realized.
- Anonymity: Users interacting with blockchains are assigned system-generated addresses. This masks the identity of the user.
- Auditability: Transactions in real time rely on previous unspent transactions. As crrent transaction gets incorporated into the blockchain, the status of unspent transactions changes to spent. This makes verifying and tracking transactions easy.
- Public Verifiability: The correctness of the state of system can be confirmed by any user. This is not the case in systems that rely on central trust agencies. Users need to communicate with the agencies to obtain information about the correct state.
- Transparency: Blockchain data is updated for public verifiability. However, the amount of information may be restricted to users depending on their privileges.
- Privacy: Although privacy is easier to achieve in centralized systems, blockchains with specific protocols can allow a certain level of privacy to safeguard sensitive information.
- Integrity: Blockchain technology protects against unauthorized modifications, leading to data integrity. Since the system allows public verifiability, data integrity can be verified by anyone.
- Redundancy: Blockchain technology relies on decentralized architecture. This means that data is duplicated across all writers, unlike centralized systems which rely on backups and physical servers to achieve data redundancy.
- Trust Anchor: The trust anchor is the entity responsible for providing read and write access to a system. They are the highest authorities and they possess grant and revoke rights.
6.4 Types of Blockchains
In the previous sections, we have taken a look at the “permissioned” and “permissionless” blockchains. However, there is another way to classify blockchains. This classification is done on the basis of blockchain networks. Blockchains have been known to be of three types, which are defined as follows:
- Public Blockchains: These blockchains are open and transparent, implying that anyone can read, write or audit these. They can be reviewed by anyone at any given point of time. The decentralized consensus mechanism is responsible for decision-making since no one is in charge. The proof of work (POW) and proof of stake (POS) are taken into account when making decisions. These have no access restrictions and anyone can participate in transactions and validations. Some common public blockchains are Ethereum and Bitcoin [4].
- Private Blockchains: These blockchains are confined to an individual or organization. An authority is responsible for read-write operations. This authority is also responsible for selectively giving read-write access to users. The mining rights may also be given selectively, thus making it similar to a centralized system, although it is cryptographically secured and also cost-effective. In this blockchain, not everyone can read, write, audit or make transactions. They are permissioned blockchains. A bankchain is a typical example of a private blockchain.
- Consortium or Federated Blockchains: These blockchains have one or more in charges for decision-making. They are semi-permissioned and are represented by a group of companies or individuals. This leads to faster transactions and offers multiple points of failure, thereby preserving data. The members are responsible for making transactions/decisions. They can read, write, audit and mine data. Common examples of consortium blockchains are R3 and EWF (Energy Web Foundation).
6.5 The Architecture of Blockchain Technology
The single version of truth provided by blockchain makes use of digitally signed blocks and algorithms to carry out quick and real-time transactions and documentations, which are further encrypted. The idea was proposed by Satoshi Nakamoto, who wanted to create a cryptocurrency (Bitcoin) that does not rely on centralized architecture and intermediaries. Blockchains incorporate blocks which are based on pointers that connect data from previous blocks. These blocks may not be altered easily, thereby ensuring security. New block validations also rely on consensus algorithms.
The end-to-end transaction of blockchain follows certain mechanism. In this section we will take a look at the architecture of blockchain technology responsible for its functioning. The blockchain technology architecture is based on the following components [9]:
- Blockchain Platform: The blockchain may be defined as an application that runs on a distributed network. It is a decentralized transaction system which is transparent in the sense that any node handling a blockchain software is capable of handling the entire blockchain. The corresponding data is stored in either a flat file or a relational database. Google’s LevelDB is accountable for storing metadata. The installed application gets synced from server to nodes. The servers encompass transaction records based on cryptographic protocols and consensus algorithms. Since the software is robust, it is virtually impossible to break into the applications running. The transactions do not need third parties for authentication and validation. The transactions are verified by nodes in a peer-to-peer network. When many nodes agree with respect to their blocks in individual databases, they are said to be in consensus. The three main layers of blockchain are illustrated in the diagram shown in Figure 6.1. As we can see, the clients supported are full, web and mobile. The blockchain layer is responsible for maintaining chain of blocks, whereas the protocol and client layers provide peer-to-peer protocol and consensus rules.

Figure 6.1 Blockchain architecture diagram.
- Blockchain Nodes: Blockchain technology operates on the collaborated peer-to-peer (P2P) network and internet protocol of the internet. In a P2P network, there is no centralized node, and all nodes are capable of providing and consuming services. The nodes in a blockchain are responsible for maintaining duplicate copies of the database which contain information related to payment and ownership. Transactions lead to nodes agreeing on updates. Nodes are responsible for different functions in a blockchain. They connect to peers and validate blockchains. Full nodes contain duplicated database in order to verify transactions without relying on additional lookups. Nodes that store some part of the database verify transactions using simple payment verification (SPV). Miner nodes are used to confirm transactions so that they can become part of the blockchains. This is done by adding data into data structures (Block), based on cryptographic protocols. Committed blocks cannot be modified since it may lead to invalidation of all other blocks, which is done to ensure data integrity. Hence, rollbacks are unattainable.
- Network Protocol Stack: Blockchain nodes can discover and contact other valid nodes. The blockchain message exchange follows the process of handshaking between nodes to exchange information over the network. The Blockchain Overlay Network is responsible for allowing different types of blockchains to synchronize and manages their operations. This layer can be used to support other applications as well. The information flow in blockchain technology is depicted in Figure 6.2, along with, the blockchain network architecture.
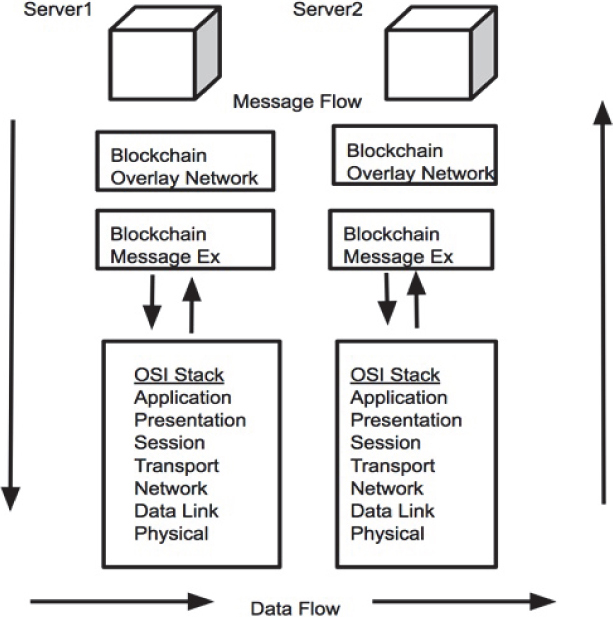
Figure 6.2 Network architecture of blockchain.
Transactions: Blockchains are used by applications to timestamp transactions. The records in a blockchain exist as transactions and blocks. Transactions may be created by clients or client applications. They have significant data that contributes to the blockchain. Sequence of transactions are stored in blocks and these blocks are created by miner nodes. In the illustration given in Figure 6.3, it is clear that when a transaction is registered in a system, a newly generated transaction is added to the blockchain node network. Minor nodes check the validity, after which it undergoes a cryptographic hashing technique to generate a unique sequence of characters. It is collaborated by other transactions and newly generated hash is stored with other metadata in a data structure header. This creates a block for which the header serves as key. This can lead to creation of the succeeding child block.
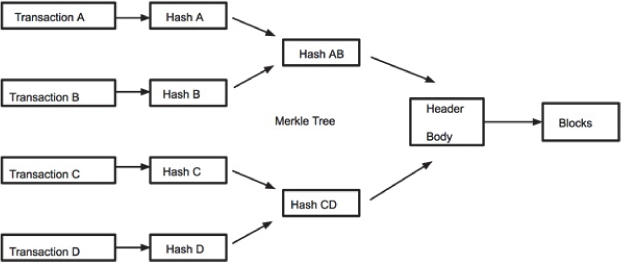
Figure 6.3 How transactions get converted to blocks.
In Figure 6.3, we can see how a number of transactions get converted into blocks, which eventually are formed into chains. The transactional data part incorporates the set of transactions. The Merkle root is a data structure which forms part of the block header. The idea is that previously recorded transactions cannot be changed unless the block recording it and the following blocks are changed. The hash value of the previous block header is also apart of block incorporation transaction records, thereby forming chains.
6.6 How Blockchain Technology Works
In the previous section, we have taken into account the architecture for blockchain technology. In this section we will be dealing with how it works. The most widespread application of blockchain technology is the digital currency Bitcoin, which is created electronically and does not need a central authority to enable payment transactions. It was coined by a software developer by the name Satoshi Nakamoto in 2008. He used mathematical proofs to come up with an electronic payment system that could lead to transactions in a secure, verifiable and and inflexible way. There are a few features of bitcoin that make it different from the traditional digital currencies across the world.
- Decentralization: As blockchain technology is decentralized, bitcoins are maintained by volunteer coders and dedicated computers over the world. A lot of individuals prefer bitcoins due to the non-involvement of third parties for transactions. It eradicates the double spending problem in such a way that digital assets cannot be reused. Certain cryptographic protocols and algorithms ensure integrity of the transactions.
- Limited Supply: Growing demand and constant supply lead to increase in the value of asset. Bitcoins are limited and their supply is regulated by sophisticated algorithms.
- Pseudonymity: Bitcoin transactions do not require the identity of the sender. There is no third party to verify the identity. For a transaction to take place, all that is required is a transaction request. The protocols analyze previous transactions and make sure that the sender has sufficient bitcoins to send and the authority, before the transaction takes place.
- Immutability: Bitcoin transactions are irreversible. This is because whenever a transaction takes place, it stores the added new information in the blocks.
- Divisibility: The smallest unit of bitcoin is one part of a hundred million, roughly a hundredth of a cent. It is called as satoshi and has an edge over traditional currencies because it can also lead to microtransactions.
Traditional commerce has its own limitations ranging from financial fraud to transaction costs. Bitcoin proves to be an effective solution. Let us take a look at how blockchain technology works in relation to the popular bitcoins.
Blockchain technology eliminates the involvement of third parties for transaction validation and relies on cryptographic proof for the same [9, 10]. Transactions are secured using digital signatures. The receiver has a public key to which each of the transactions is sent. The receiver uses the private key of the sender to digitally sign the transactions. The cryptocurrency owner must prove ownership of the private key in order to spend the currency. The receiver of the digital currency must verify the signature and ownership of the private key using the sender’s public key for the transaction to be successful.
Once the transaction takes place, it is communicated across all the nodes of Bitcoin, which has to be verified first and then registered. The validity of each transaction is a must before it is added to the public ledger. To record a transaction, a node must verify two things:
- The cryptocurrency is actually owned by the spender. This is done by verifying the digital signature.
- The spender is equipped with sufficient cryptocurrency to carry out the transaction. This could be done by checking every transaction recorded in the spender’s account.
The illustration in Figure 6.4 exhibits the working mechanism of blockchain technology.
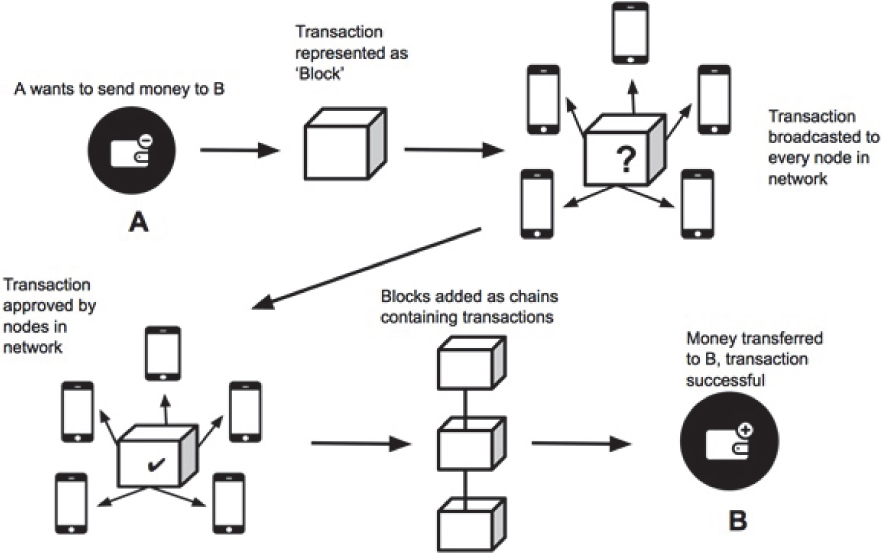
Figure 6.4 Cryptocurrency transaction using blockchain technology.
Blockchain technology was the result of developing a mechanism for Bitcoin transactions that the entire network would agree to. Initially, before blockchain technology was developed, and only bitcoins prevailed, transactions did not always come in order; thus, there was a need to eliminate double spending of the cryptocurrency. The transactions are passed from node to node in a bitcoin network; hence, the order in which the transactions are received at a node, might not be the actual order of the transactions taking place. For example, Transaction A might occur before Transaction B, but the number of nodes Transaction A has to pass could be more than that of Transaction B, thus leading to Transaction B being recorded in a node first. This was a challenge in a distributed network and Bitcoin solved this problem using blockchain technology. The transactions were then placed in blocks, thus leading to blockchains. This means that all the transactions taking place in a block have occured at the same time. The blocks are then arranged linearly in a chronological manner, in such a way that a given block is linked to the previous block by its hash value.

Although the proposed method eliminated a lot of issues, one problem still remained unsolved. Multiple blocks could have been created at a given time for different nodes. Several blocks could have arrived at different nodes for different points. The problem was solved using a mathematical puzzle wherein a block could be accepted in a blockchain if it could answer a specific mathematical problem. This is referred to as proof of work, as the node which generates a block must prove that sufficient resources have been invested to solve the puzzle. This means that there is need to develop a mechanism so that the entire Bitcoin network can agree regarding the order of transactions, which is a daunting task in a distributed system in Figure 6.6.

Figure 6.6 Blockchain generation from unordered transactions.
6.7 Some Other Case Studies for Blockchain Technology
As we know, Bitcoin is the most popular case study of the blockchain technology. However, blockchain technology is not only limited to working of cryptocurrencies. In this section we will take a look at a few other use cases of blockchain technology. They are as follows [2, 7]:
- Supply Chain Management: The supply chain management (SCM) workflow consists of a number of services ranging from manufacturing, storage, production, etc., to delivery and consumption. It involves multiple writers and the data that must be stored is huge. When a product moves from one hand to another, the transactions will be recorded, thereby reducing time delays and eliminating human error. Orders, receipts, shipment notifications, etc., could be tracked down easily. Physical goods could be linked to serial numbers, barcodes, digital tags, etc. Moreover, information can be shared between vendors and suppliers.
- Interbank and International Financial Transactions: Blockchain technology is being adopted by financial institutions for several reasons. Cross-border transactions become a lot more quicker and cheaper. Better trade accuracy along with shorter settlement process is the key to share trading. Smart contracts in the form of commercial transactions and agreements can be ensured. It strengthens identity management, which is required for banking. Since the transactions are transparent and traceable, it leads to better loyalty programs and rewards, thereby enhancing the overall performance.
- Decentralized Autonomous Organization (DAO): A DAO relies on smart cards for functioning. There is no central management, although there are rules specified in the smart contracts, which define how the organization should behave. The organizations must be managed in a decentralized manner, hence creating the demand for permissionless blockchains. Sometimes, dedicated permissionless blockchains may also be required. These systems are usually built on top of an existing blockchain technology with its own currency.
- Land Registry: The data pertaining to land registry may be moved to safe and transparent infrastructure secured using cryptographic protocols. South African startup by the name of ChromaWay is already working on the same [8].
- Proof of Ownership: One of the most common case studies for blockchain technology is proof of ownership of intellectual property. A public blockchain at the time of stamping could be used to manifest ownership at a later time. The digital object along with the identity of the owner could be committed using a hash to provide sufficient evidence of ownership.
- e-Voting: One of the most important public demands for e-voting is privacy, since votes must be anonymous to avoid any sort of intimidation. However, there must also be public verifiability, so as to preserve integrity of the votes. Since a lot of parties are involved in voting who do not trust each other, one of the reasonable solutions is the use of blockchain technology.
6.8 Challenges Faced by Blockchain Technology
Blockchain technology is one of the most revolutionary technological advances in recent times. It has been adopted by industries belonging to several domains like finances, healthcare, cloud storage, etc. Despite its supremacy in the technological world, there are several concerns pertaining to blockchain technology. Following are some of the challenges faced by blockchain technology [2].
- Scalability or Network Size: With a large number of transactions taking place everyday, with each block storing data, and new blocks being generated, scalability becomes a challenge. If a blockchain is not supported by a robust network, there may be several system failures. Storage optimization of blockchains or redesigning the blockchains altogether may prove to be beneficial in dealing with scalability problems.
- Privacy Leakage: Blockchains do not guarantee transactional privacy. Bitcoin transactions may reveal personal details about users [5]. IP addresses may be traced back to user pseudonyms despite the use of firewalls and network address translators [6]. Anonymity is one way to deal with privacy issues.
- Selfish Mining: Selfish mining leads to insecurity of blockchains. It relies on a small amount of hashing power to make the network vulnerable. The mined blocks are kept without broadcasting and public may be able to access the private branch only if certain requirements are fulfilled. Hence selfish miners can mine private chains without the fear of losing to competitors, hence availing more revenue.
- Initial Cost: Initial setup of blockchain technology is expensive as it incorporates software cost and qualified personnel expertise. Huge demand and limited supply also contribute to the same.
- Integration with Legacy Systems: Moving to a blockchain-based system may be done by either rebuilding the entire system (new blockchain based) or fusing the existing system with blockchain technology. Eradicating legacy systems may not be easy, thus the feasible solution would be to make changes to an existing system that can support blockchain technology. This may require time, money and skills.
- Energy Consumption: Validating transactions on blockchain requires computing complex mathematical algorithms for transaction verification and network security. Computations consume a lot of power and energy.
- Public Perception: Since blockchain technology is recent, lot of people are unaware of it. Many find it synonymous with bitcoins. Before the technology is adopted and applied across several domains, people must be made aware of it.
- Privacy and Security: Initially blockchains were made visible to the public. However, in order to protect data and restrict access, blockchains are made permissible. This requires a lot of planning and exercise
- Complexity: Blockchain technology is based on new vocabulary which incorporates several jargons. People who are involved in work related to blockchain technology must familiarize themselves with the phrases.
- Human Error: The data contained in blockchain may not be reliable, thus events must be recorded accurately.
- Unavoidable Security Flaw: One of the remarkable security flaws in blockchains is that if more than fifty percent of the systems used as a service tell a lie, the lie becomes truth and is referred to as a “51% attack.” Hence it is important to monitor mining pools.
- Politics: Several public disagreements have cropped up between community sectors since Bitcoin protocols can digitize governance models. There have been reports about forking of blockchains, wherein a blockchain protocol is updated.
6.9 The Future of Blockchain Technology
We know that technologies like blockchain are capable of diminishing cyber risks, which are a global concern. Apart from that, blockchain technology is being used in several industries for providing specific benefits. More and more organizations are adopting blockchain technique and hopefully blockchain technology is the future of the internet. Since cryptocurrencies are are increasingly being used and financial institutions are relying on blockchaining methods, global banking may change. In this section, we will take a look at how this technology will impact the future [2, 11-15].
- Blockchain Testing: Blockchain performances may be falsified to lure users for earning profit. It is important to know which blockchain would fit business requirements, thereby making blockchain testing mandatory. There are two phases to support this. In the standardization phase, blockchains are tested based on certain criteria for validation. The testing phase witnesses blockchains being tested for different criteria.
- Eliminating the Process of Centralization: Although blockchain technology is based on decentralization, selfish mining could easily take advantage of the 51% attack. This would defeat the purpose of decentralization, hence few methods must be proposed to handle the issue.
- Big Data Analytics: When big data is combined with blockchains, it may lead to data management and data analytics. Data management ensures that data is stored and secured whereas data analytics handles transactions.
- Blockchain Miscellaneous Applications: Blockchains could be adopted by traditional organizations for better working of their systems. The concept of smart contract could be implemented with blockchains [6].
- Combating Crime: Blockchain technology (software) has the potential to track down criminals. Apparently, it will be much cheaper than the already existing methods
- Banking Sectors: Central banks could be replaced by blockchains in the near future. The infrastructure costs, cross-border payments and security trading could be reduced by blockchain technology.
- Industries: Blockchains may create new industry opportunities and distort the existing ones. The transactions will be quick and efficient, with no third party intervening between two end parties.
- Governments: Finance in many nations may be influenced by cryptocurrencies.
- Human Factor: The human factor for authentication authentication may be eliminated completely.
6.10 Conclusion
In this chapter, we have introduced one of the most contemporary technologies. Cybersecurity happens to be the foremost priority of any nation or organization. Blockchain technology offers advanced security measures which are difficult to breach. We have taken a look at what blockchain technology is and why it has been needed in recent times. There are certain characteristics of blockchain technology that make it a favorite among cryptographers and we have discussed those characteristics. On the basis of blockchain networks, three types of blockchains are known, which we have also highlighted in this chapter. Apart from that, the architecture and working of blockchain technology is also presented. Bitcoin is one of the applications of blockchain technology, which we have emphasized in this chapter, along with some other case studies. Even though blockchain technology is modern day savior of security issues, there are still some challenges facing it, a few of which are presented in this chapter. Finally, the presumed effects of blockchain technology in the future have been listed.
References
1. Zheng, Z., Xie, S., Dai, H., Chen, X., … Wang, H. (2017, June). An overview of blockchain technology: Architecture, consensus, and future trends. In Big Data (BigData Congress), 2017 IEEE International Congress on (pp. 557-564). IEEE.
2. Wst, K., … Gervais, A. (2017). Do you need a Blockchain?. IACR Cryptology ePrint Archive, 2017, 375.
3. Types of Blockchains, retrieved from https://en.wikipedia.org/wiki/Blockchain#Types_of_blockchains
4. Barcelo, J. (2014). User privacy in the public bitcoin blockchain. URL: http://www.dtic.upf.edu/![]() barcelo/papers/20140704_User_Privacy_in_the_Public_Bitcoin_Blockchain/paper.pdf (Accessed 09/05/2016).
barcelo/papers/20140704_User_Privacy_in_the_Public_Bitcoin_Blockchain/paper.pdf (Accessed 09/05/2016).
5. Szabo, N. (1997). The idea of smart contracts. Nick Szabo’s Papers and Concise Tutorials, 6.
6. Dejan Jovanovic, Blockchain Case Studies, Retrieved from https://medium.com/@dejanjovanovic_24152/blockchain-case-studies-2271d37d3ed, 2017
7. Pete Rizzo, Sweden’s Blockchain Land Registry to Begin Testing in March, Retrieved from www.coindesk.com/swedens-blockchain-land-registry-begin-testing-march/, 2017
8. Vamsi Chemitiganti, The Architecture of Blockchain, Retrieved from http://www.vamsitalkstech.com/?p=1615, 2016.
9. Saberi, S., Kouhizadeh, M., Sarkis, J., … Shen, L. (2018). Blockchain technology and its relationships to sustainable supply chain management. International Journal of Production Research, 1-19.
10. Scott, B. (2016). How can cryptocurrency and blockchain technology play a role in building social and solidarity finance? (No. 2016-1). UNRISD Working Paper.
11. Zheng, Z., Xie, S., Dai, H., Chen, X., … Wang, H. (2017, June). An overview of blockchain technology: Architecture, consensus, and future trends. In Big Data (BigData Congress), 2017 IEEE International Congress on (pp. 557-564). IEEE.
12. Ver, R., … Antonopoulos, A. M. (2018). Blockchain Revolution How the Technology Behind Bitcoin Is Changing Money. ADC Publishing Book.
13. Atwood, M., … Yonis, A. (2018). Blockchain Technology Explained: The Simplified Guide On Blockchain Technology (2018) Blockchain Wallet, Blockchain Explained.
14. Bhardwaj, S., … Kaushik, M. (2018). BlockchainTechnology to Drive the Future. In Smart Computing and Informatics (pp. 263-271). Springer, Singapore.
15. Anascavage, R., … Davis, N. (2018). Blockchain Technology: A Literature Review.
