4
Threats and Attacks to ICS
4.1. General principle of an attack
In general, an industrial control system (ICS) is subject to threats, generated by sources of threats. These sources of threats use an attack vector to carry out an attack.
The attack may be directed at the control command system (BPCS) that controls the physical system, or it may be directed at the safety instrumented system (SIS), so as to create damage when the system uses safety functions.
The path or means used to access the target system is called the “attack vector”.

Figure 4.1. Vector of attack and vulnerability. For a color version of this figure, see www.iste.co.uk/flaus/cybersecurity.zip
The objective of a computer attack is to create damage to one of the installation’s assets. Different types of damage are possible:
- – the asset may be corrupted, so that the system performs incorrect actions, or provides incorrect results, or information is lost;
- – the asset can be spied on: information related to the asset is accessible to persons who should not have access to it;
- – the property may become unavailable or very slow, so that use of the system or network becomes impossible or impractical, which is particularly problematic for a real-time control system or a security system.
To successfully create this damage, an attacker has a number of options that may be logical or physical, i.e. through computer access or physical access.
Logically, an attacker may attempt to access the content of the memory of the attacked device, to copy or modify it, or will attempt to have the device execute a series of commands. It may also seek to spy on or modify communications between the device and its environment.
Recent devices use identification and authentication mechanisms coupled with rights control, which means that, to execute commands or access memory, a user, who may be a human or a machine, must prove its identity. When this is done, they are given a number of options to read or write data, or to execute commands. The older devices do not have these possibilities.
Similarly, communications between two devices may use identification and authentication mechanisms, and in some cases some protocols be encrypted, i.e. made unreadable by an observer who does not have the mechanism or code for decryption. Again, these possibilities only exist for recent equipments.
To slow down a system, an attacker has two main possibilities:
- – if he/she has successfully entered a system, he/she can seek to initiate the execution of many processes;
- – from the outside, he/she can flood the system with requests to prevent its normal operation, as in the case of a denial-of-service (DoS) attack by machine networks that overload a server. He/she can also, if he/she has access to the network, send it restart or resynchronization commands, which will disrupt its operation.
To these possibilities are added the physical actions performed on the device. An attacker can:
- – steal the device;
- – recover it (management of discarded equipment, loss of keys, etc.);
- – add a spy device (keylogger, for example);
- – destroy it.
At this stage, we can distinguish several types of actions that have a negative impact on the information system:
- – unintentional actions, such as a user mistakenly formatting a storage device;
- – malicious actions by users with authorized access to the system, such as an administrator from whom a company has separated and who wishes to harm it;
- – malicious actions by unauthorized persons who have successfully obtained legal identifiers (fraud, deception, brute force, use of default identifiers, etc.);
- – malicious actions without identifiers, which use different techniques to bypass identification and authentication mechanisms.
Only the last category is based on technical skills and hardware and software vulnerabilities; the first three are related to the human factor and organizational aspects.
From a technical point of view, in the latter case, an attacker will attempt to bypass the identification and authentication system, on hosts or in network exchanges, and/or attempt to bypass the rights management system to successfully perform actions beyond what is allowed. To do this, different techniques are used and are presented below.
It is important to note that, in the case of ICS, there are still many devices for which identification is not required, and that most protocols are not secure. If an attacker succeeds in accessing the industrial network, he/she can relatively easily listen and modify exchanges, and he/she can act on the connected devices.
Different means can be combined to penetrate a target system and develop the ability to perform malicious actions in a sustainable manner. This is called an advanced persistent threat (APT) attack. It goes through several stages:
- – a recognition phase: research, identification and selection of targets and their vulnerabilities. The targets can be technical (servers, PLCs) or human (personnel in the target company);
- – a phase where the malware (often of the backdoor type) is transmitted to the victim by email, via a malicious website or removable memory, or by exploiting a vulnerability in the target system;
- – an exploitation phase: once the malware is installed secretly on the target, it spies, or waits for commands from the attacker. It can also attempt to copy itself onto the other stations of the network.
Many ICS attacks exploit this principle, such as the Stuxnet attack or the attack on the Ukrainian electricity distribution system presented below.
A primary attack can also generate a secondary attack (Figure 4.2), the objective of the primary attack being to install malware that can be used as a relay for other attacks (Hutchins et al. 2011).
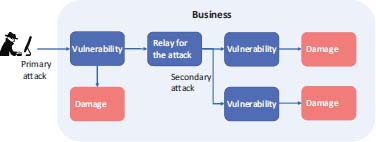
Figure 4.2. Primary and secondary attacks. For a color version of this figure, see www.iste.co.uk/flaus/cybersecurity.zip
A complete threat assessment for an information system reveals threats other than those linked to computer attacks (Lévy-Bencheton et al. 2015). We can mention the threats:
- – linked to physical phenomena such as fire, floods, etc.;
- – linked to physical sabotage, which can impact communications in particular;
- – due to equipment failures;
- – due to energy losses for operation and cooling;
- – due to human factors: pandemic, strike, various absences, etc.
These threats do not fall into the category of attacks, but are to be taken into account in the risk analysis.
4.2. Sources of threats
As presented in the previous section, there are several categories of threat sources. A classification is useful for risk analysis because, on the one hand, it allows all relevant sources to be systematically considered and, on the other hand, it makes it possible to choose countermeasures that must be adapted to the source’s capabilities.
An initial classification is provided by the NIST guide SP800-82. It shows all sources capable of causing damage to an information system (Table 4.1). It can be noted that most of them are not of human origin.
For those of human origin, in the National Institute of Standards and Technology (NIST) classification or in that proposed in the EBIOS method (Table 4.2), a distinction is made between violations that are caused by human error without malicious intent and those that are malicious. It is the latter that are taken into account, explicitly or not, when considering cybersecurity.
It is useful to distinguish between internal and external threats, as they operate in a completely different context. Internal threats have authorized access, based on their access rights, and can therefore cause damage without the need to pass a technical vulnerability. If they do, they can operate from the local network, and therefore have extensive possibilities. Typical examples are those of a former malicious employee or a malicious external provider. Countermeasures for internal threats are essentially organizational: limited access rights, double validation for administrators, management of staff arrivals and departures, etc.
External threats must use other vectors of attack, such as the Internet, or social engineering. In order to implement appropriate countermeasures, the following levels are distinguished:
- – malicious people using robots that systematically and automatically “scan” for vulnerabilities;
- – amateur hackers, with limited capabilities, who find attack software on the Internet, and who do not necessarily target a given installation;
- – advanced hackers, with advanced technical skills, such as pirate groups;
- – organizations with very large or even unlimited resources, such as States, criminal organizations or, to a lesser extent, a competing company.
This classification is used in the context of risk analysis. Depending on the installation under consideration, risks for the relevant categories are analyzed. The company must ask itself who can attack it and why.
A more detailed catalogue of sources of threats may be useful. They are associated with the various risk analysis methods (Chapter 9) or in the NIST SP800-82 standards (Stoufferet al. 2015), NIST SP 800-30 (Joint Task Force 2012), ISF IRAM (Jenkins 2014), ISO 27005 (IEC 2011) and BSI Threat Catalog (Bundesamt für Sicherheit 2011).
Table 4.1. Different types of sources (adapted from NIST SP800-82)
| Type of source | Description |
| Malicious human action | |
|
Individuals, groups, organizations or States seeking to exploit the organization’s dependence on information resources (for example, information in electronic form, information and communication technologies, as well as communications and information processing capabilities provided by these technologies) |
| Human error | |
|
Unintentional actions carried out by individuals in the course of carrying out their daily responsibilities |
| Technical system | |
|
Equipment failures, lack of environmental control, software design or implementation defects, resource depletion |
| Natural and anthropogenic environment | |
|
Natural disasters and failures of critical infrastructure on which the organization depends, but which are beyond the organization’s control |
Table 4.2. Source classification (EBIOS)
| Deliberate human sources |
| Internal human source, malicious, with low ressources |
| Internal, malicious human source, with significant resources |
| Internal human source, malicious, with unlimited resources |
| External human source, malicious, with low resources |
| External, malicious human source, with significant resources |
| External, malicious human source, with unlimited resources |
| Human sources acting in an accidental manner |
| Internal human source, without malicious intent, with low ressources |
| Internal human source, without malicious intent, with significant capabilities |
| Internal human source, without malicious intent, with unlimited capabilities |
| External human source, without malicious intent, with low ressources |
| External human source, without malicious intent, with significant capabilities |
| External human source, without malicious intent, with unlimited capabilities |
| Non-human sources |
| Malicious code of unknown origin |
| Natural phenomenon |
| Natural or medical disaster |
| Animal activity |
| Internal event |
4.3. Attack vectors
To carry out an attack, a threat source uses a means or vector of attack. Table 4.3 presents the main vectors used in ICS. The choice of attack vector is made in such a way as to exploit a system vulnerability.
Table 4.3. Main vectors of attack
| Category | Threats and vectors of attack |
| Network | Adjacent internal wired networks such as IT network or DMZ using compromised equipment Compromised equipment with multiple network interfaces and belonging to two networks Wi-Fi networks Compromised equipment on the local network Internet connections Cloud connections Split tunneling (simultaneous access to protected resources via VPN and Internet for example) Wireless Wi-Fi networks Industrial or IoT wireless networks (Hart, Zigbee, etc.) |
| Physical access | Removal media on USB port or other USB keyboard socket (keylogger) Serial and other ports (SATA, Display port, HDMI, etc.) RJ45 ports Direct access via keyboard/mouse Flash memory cards |
| ICS equipment | USB and other ports Open network logic ports (http, ftp, etc.) Configuration or program transfer software Traffic sent to the equipment (Modbus, etc.) |
| Applications | Network logic ports User data entry (local or Web interface) Data entry files Data reading via libraries OS vulnerability (e.g. data access via other applications) |
| People | Social engineering by email Social engineering by telephone Corrupted client email and attachments Internet browser |
| Suppliers | Supply of electronic components, boards Updates or supply applications, operating system or firmware |
4.4. Main categories of malware
A computer, network equipment, ICS component or IoT equipment are programmable devices with a memory area containing both data and programs. Some zones are not modifiable, some others are modifiable, but keep the data when the power supply is interrupted, some still are cleared when the device is switched off. When a system is started, it executes a predefined and unmodifiable program that allows us to start a start program located at a given address. An attacker can try to modify the memory areas, insert malicious code into the boot address, or execute this malicious code by modifying the stack (section 4.5.1).
In addition, systems connected to a Transmission Control Protocol (TCP)/Internet Protocol (IP) network operate by listening to the network via logical ports. We talk about “open ports”. Each port is assigned a default software: for example, port 23 is listened to by Telnet and port 502 is used by Modbus. An attacker can therefore try to use vulnerabilities related to protocols and applications using these ports to modify data, steal passwords or execute code on a workstation or equipment.
These various possibilities are exploited by malware. We distinguish different categories presented in the following sections.
4.4.1. Virus/worms
A virus is malicious software that installs itself in a hidden way on a computer or equipment and is able to replicate itself from one computer to another. In general, to infect a system, a virus attaches itself to another software. When the latter is executed, the virus is executed and can infect the host machine and attempt to replicate itself. The biological metaphor is adapted to describe the behavior of this type of program. However, to contaminate or replicate, it must be executed via the contaminated software or directly. This can happen automatically, in the case of USB sticks with a self-executing file. Most often, it is the user who runs the program himself, after being misled about the nature of some software or of an attachment.
A worm is a type of virus that spreads over the network, often using a vulnerability to perform remote execution over the network. Nowadays, there is no longer any real distinction between worms and viruses.
4.4.2. Trojan horse
A Trojan horse is software that seems to do one thing, and can, in fact, do it, but embeds malicious software. The analogy to the famous story from Greek mythology is very appropriate: the giant wooden horse, an offering in appearance, actually hid Greek warriors. In the case of computers, the Trojan horse deceives the user and makes sure that the hidden malware is installed on his/her machine. The latter can then perform its hidden actions, for example spying and sending the user’s information to a pirate server.
4.4.3. Logical bomb
A logical bomb is a category of malware that installs itself in a hidden way, in a Trojan horse for example, and triggers actions at a date predefined by the hackers.
4.4.4. Rootkit
A rootkit is malicious software that installs itself in a hidden way, and whose purpose is to provide privileged user access to an attacker, who therefore has almost all the privileges to perform all actions on an operating system.
4.4.5. Spyware
Spyware is software that spies on users and records their activities. As a general rule, it is installed without the user’s knowledge. Spyware can perform a wide range of activities. It can record keystrokes (an action commonly known as keylogging), when the user connects to specific websites. It can record sound and/or image or anything else.
It can use a backdoor to send its information to a hacker server.
4.4.6. Back doors
A backdoor is a hidden feature of a software or operating system that is most often introduced at the time of development and allows access to specific options or bypassing the normal authentication procedure. Originally, the objective was to allow the recovery of lost passwords or simply for entertainment purposes, as was the case with software that displays special animations in the About window when typing a special sequence. With the networking of computer systems, this functionality has become a vulnerability, especially when authentication is hard coded.
In addition, there are many cases where the back door is implanted during manufacture in software, equipment (camera) or telephones for illegal purposes, such as data theft. There are also many malware programs that implement such a feature.
4.4.7. Botnet
A botnet is a network of machines connected to the Internet, each of which executes a “bot”, i.e. robot software responsible for responding to commands or executing predefined actions. Malicious “robot” software is distributed by one of the means mentioned above, such as viruses or emails. They are installed silently on targeted workstations or equipment and wait for orders. The consequences are benign for the user on the surface, however, this makes it possible to build armies of machines equipped with malicious software, the botnet.
These zombie machines, which can be computers or equipment connected to the Internet such as cameras or industrial Internet of Things (IIoTs), are used to carry out other attacks. They can send spam or perform distributed denial of service (DDoS) attacks.

Figure 4.3. DDoS attack by a botnet. For a color version of this figure, see www.iste.co.uk/flaus/cybersecurity.zip

Figure 4.4. Percentage of ICS computers attacked by a botnet in 2017
(source: CERT)
4.4.8. Ransomware
Ransomware is a type of malware that prevents or limits users’ access to their system, either by locking the system screen or by locking users’ files. To recover access, a ransom must be paid. The most modern ransomware families, collectively classified as crypto-ransomware, encrypt certain types of files on infected systems and force users to pay the ransom via certain anonymous online payment methods to obtain a decryption key (cryptocurrency).
4.5. Attacks on equipment and applications
4.5.1. Buffer overflow and integer overflow
A buffer overflow attack attempts to place more data in a memory area than it can contain. This can corrupt other variables, block the system, or, when the zone is properly placed, write to the subroutine call stack and cause malicious code to be executed. In Figure 4.5, the variable buffer is a table of four characters, numbered 0 to 3. Writing beyond that is illegal. If no control is performed, writing from buffer (Abshier 2004) to buffer (Pollet 2010) allows to modify the return address, and thus cause the execution of a malicious code that will have previously been loaded at the chosen address. More details can be found in Howard and Leblanc (2002).

Figure 4.5. Attack by buffer overflow. For a color version of this figure, see www.iste.co.uk/flaus/cybersecurity.zip
There are also vulnerabilities related to integer overflow. These vulnerabilities are often found by random software testing (fuzzing tests). A flaw of this well-known type is related to the Secure SHell (SSH). By sending a frame designed to exploit the flaw, was possible to get connected as “root” (CERT VU#945216 vulnerability).
4.5.2. Attack by brute force
A brute force attack is a trial and error method used by some software to decode encrypted data such as passwords or data encryption keys. Just as a criminal can “break” a safe by trying many possible combinations, a brute force cracking application goes sequentially through all possible combinations of legal characters. Brute force is considered an infallible approach, although it takes a long time. In reality, software programs performing this type of attack combine brute force and a dictionary approach: they will first test the usual passwords, then the dictionary words, then classical variations, before systematically testing all combinations.
Encryption systems are designed so that the time required is such that this method is not feasible on a human scale. However, new means of calculation (quantum computing) could reduce this time. For this reason, some guides require that the authentication system can be updated on equipment, such as the Industrial Internet Consortium’s IIoT good practices described in Chapter 6.
This approach cannot be used directly, as most systems crash after a few attempts. This approach is most often used on encrypted password files that have been previously stolen.
Finally, it should be noted that the effectiveness of this type of attack is closely linked to the strength of the passwords, which must be chosen in a relevant way (ANSSI 2012b).
4.5.3. Attack via a zero day flaw
A “zero day” attack is an attack that exploits vulnerabilities that have not been fixed or made public. Often, this type of attack includes attacks targeting vulnerabilities known to the public but not yet fixed.
Software vulnerabilities can be discovered by hackers, security companies, researchers, government intelligence services, software vendors themselves or users. If discovered by hackers, they can be used to set up attacks also called “exploits”. An exploit will be kept secret for as long as possible. It can be sold on the cybercrime black market.
4.5.4. Side-channel attacks
In general, side-channel attacks use information leaks such as execution time, power consumption or electromagnetic leaks observed during the normal execution of a cryptographic algorithm to infer secret information such as encryption keys (Appendix 1).
It is important to note that the quality of the algorithm is not in question, either its principle or its implementation, rather it is observation of its functioning that allows it to be bypassed. In a way, this method is similar to opening a safe with a stethoscope.
The most well-known approaches (Joye and Olivier 2011) use:
- – consumption analysis, either directly during an encryption operation (single power analysis) or by making repeated observations and using statistical methods (differential power analysis);
- – analysis of computing time (Kocher 1996), for example to validate or invalidate a password;
- – the electromagnetic waves emitted.
The risk associated with this type of attack depends on the physical accessibility of the equipment, which can be easy for an Internet of Things (IoT) device, and the level of integration of the component. It is more complex with a System on a Chip (SoC, section 11.12.4), and countermeasures to smooth consumption are implemented in recent circuits.
4.5.5. Attacks specific to ICS equipment
Equipment such as PLCs are particular computer systems, which can therefore be subject to the same attacks. For example, since many PLCs work with VxWorks, they have vulnerabilities such as the CVE-2015-7599 vulnerability. This, due to a problem of unchecked integers overflow, allows a user to execute arbitrary code or to create a DoS.
However, ICS equipment also has functional vulnerabilities: it is possible, by using “normal” commands in an inappropriate way, to create malfunctions. These commands are, for example, a reset device, sending a malformed request, forcing a stop, synchronizing the clock, etc. It is therefore important to prevent any intrusion into the industrial network in order to avoid the generation of commands of this type.
It is also possible to insert malware into the program sent to the PLC (Govil et al. 2018). This program is written in one of the languages specific to PLCs (Chapter 1), such as the Ladder Language. However, it is possible to insert malicious actions that affect the actions, the measurement values or even create a DoS. Transfers to the PLC are not very secure, so this type of attack should be considered.
Other attacks to consider are those related to the modification of the PLC firmware (Basnight et al. 2013; Schuett et al. 2014).
Another type of attack concerns the OPC/DCOM protocol. The OLE for Process Control (OPC) version is a technique that appeared in 1995 and is not very secure (Chapter 2). OPC allows an attacker to list system properties or exploit vulnerabilities by buffer overflow. The OPC protocol has been replaced by the OPC/UA standard proposed by the OPC Foundation, which is much more secure.
Dragonfly malware has used these vulnerabilities. The Havex module uses the OPC standard to collect information on industrial control devices. It then sends them to the command and control server (C&C) where they are analyzed by hackers.
4.5.6. Attacks on IIoT systems
IIoT-based systems are networked systems in which each node is a more or less sophisticated programmable device. It is subject to the same vulnerabilities as traditional computer equipment.
In addition to traditional attacks, IIoT-based systems are sensitive to specific attacks and can be used as a platform to conduct specific attacks.
Among these specific attacks, we can mention the following:
- – physical attacks, by auxiliary channel, by observing consumption to deduce the keys (section 4.5.4) (Mangard et al. 2007) or to carry out reverse engineering;
- – attacks on energy resources, by preventing the equipment from going into rest mode to exhaust its energy (denial of sleep) (Raymond et al. 2009);
- – attacks on system software, which are complex to update;
- – attacks on network addition and removal features.
These aspects are detailed in Chapter 5, on vulnerabilities.
It should also be noted that the stakes of data attacks may be higher than in the case of traditional ICS. Let us quote, for example:
- – attacks aimed at recovering data to build an image of the activity of a company, a person or a manufacturing process (for example, deducting that a place is occupied from the consumption or switching on of lamps);
- – attacks aimed at modifying data transmitted in order to fraud, such as Spanish electricity meters (Illera and Vidal 2014).
Conversely, IIoT equipment can be used as an attack platform, and because of their large number, they present a significant threat. This is the case when:
- – they are corrupt, to enroll them in a botnet in order to carry out DoS attacks;
- – they are used to saturate the local communication network (radio or Wi-Fi).
In more traditional attacks on IoT devices, malware attempts to modify the firmware, or insert malicious code at boot time. IIoTs are more vulnerable because they are often physically isolated and can be the subject of electronic analyses or reverse engineering.
4.6. Site attacks and via websites
The Structured Query Language (SQL) injection attack is an attack in which malicious code is inserted into strings that are then transmitted to an SQL server instance for analysis and execution. Any procedure that builds SQL statements must be checked for injection vulnerabilities, as an SQL server will execute all syntactically valid queries it receives. Even the queries with parameters can be manipulated by a qualified and determined attacker. A simple example is the following instruction, in which the grayed-out term has been added:
As this term is always true, it makes it possible to select all users. This type of attack is particularly dangerous when used on a website.
A Cross-Site Scripting (XSS) attack is a type of attack in which an attacker injects data, such as a malicious script, into content from trusted websites. Cross-site script attacks occur when an unreliable source is allowed to inject its own code into a web application, and this malicious code is included in the dynamic content provided to the victim’s browser. This is the case, for example, in forums, if the content entered by users is not validated. The injected code is often Javascript, and can be used to steal identification data. More details are provided in (DGS 2007). An example of a possible attack on an industrial system is explained in the ICS-ALERT-13-304-01 vulnerability. This flaw affected the SCADA/HMI Nordex Control 2.
4.7. Network attacks
4.7.1. Man-in-the-middle
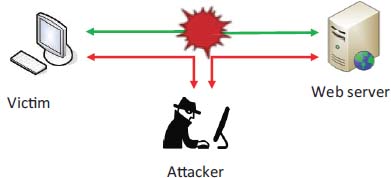
Figure 4.7. MitM attack. For a color version of this figure, see www.iste.co.uk/flaus/cybersecurity.zip
The principle of Man-in-the-Middle attacks (MiM or MitM attacks) is to pass communications between two stations through a relay without the knowledge of the two stations in communication (Figure 4.7). This can be done using different techniques:
- – the poisoning of the ARP cache (ARP Cache Poisoning) described in Chapter 2: if both workstations are on the same local network, it is possible, even relatively easy, for the attacker to force the communications to pass through his computer by posing as a “relay” (router, gateway). It is then quite simple to modify these communications;
- – DNS-Spoofing: a DNS server translates a site name (for example www.myscadasupplier.com) into an IP address. The attacker alters the DNS server(s) in order to redirect to it communications for a website;
- – Internet Control Message Protocol (ICMP) redirection: using the ICMP, an attacker can send a fake message to a router to redirect a victim’s data flow to his/her own machine. This option must therefore be blocked in routers.
With this type of attack, an attacker cannot only capture all traffic, including sensitive data such as usernames and passwords, but can also delete connections at will and manipulate content to deceive the victim. This attack works even if the traffic is encrypted, as the attacker can substitute his/her private/public keys when establishing the call.
4.7.2. Denial of service
A DoS attack is an attack designed to prevent a system or service from operating normally. It can exploit a known vulnerability in a specific application or operating system, or use certain vulnerabilities in specific protocols or services. In a DoS attack, the attacker tries to prevent authorized users from accessing either specific information or the computer system or the network itself. This can be accomplished by causing the system to shut down unexpectedly (e.g. by buffer overflow) to cause a cessation of service or by flooding it with requests (e.g. with a botnet).
A DoS attack can also be used in conjunction with other actions to gain unauthorized access to a computer using a MitM attack.
In the context of ICS, a DoS of a system in charge of controlling a physical equipment can have serious consequences, since the physical system continues to evolve over time (it is said to be real time). If the system under attack is the SIS, the security of persons and property may be affected.
A DoS attack conducted by a network of computers or connected objects is called a DDoS (Distributed DoS) attack. It can also be conducted using a TCP/IP vulnerability (SYN flood) (Chapter 2).
4.7.3. Network and port scanning
Computers and equipment connected to a TCP/IP network communicate using ports. There are 65535 TCP and UDP ports that can be opened, i.e. for which the system is ready to open a communication. A number of ports from 1 to 1,023 have a predefined role: for example, port 21 is used for FTP communications, port 80 for the web server. Some of the communication modules ready to accept a communication on one of these ports have vulnerabilities: for example, FTP servers on port 21 may allow anonymous connections. These are of course ideal targets and significant vulnerabilities (Mathew et al. 2014).
During an intrusion attempt, a port scan allows us to know if there is a device at an address, and then to know its functionalities and possible vulnerabilities. The approach of the analysis is often as follows:
- – test to see if the host is active;
- – test to know if the host is behind a firewall;
- – detection of the OS or the type of equipment;
- – port scanning;
- – looking for vulnerabilities.
The intrusion attempt is performed by testing known vulnerabilities on identified ports. For example, for port 80, which is the port used for websites, automatic software sends requests to attempt SQL injections, cross-site scripting attacks or buffer overflow attempts. For port 22, used by SSH, connection attempts can be made by a brute force attack.
The nmap software allows “scanning” a computer network and opens ports. The PLCSCAN utility allows detection of the PLCs present on a network (Figure 4.8).
Detecting port scanning activity is therefore important, as it is a precursor incident that can identify an attempted attack.
Figure 4.8. Network scanning
4.7.4. Replay attack
A replay attack is an attack that consists of intercepting packets from the network, possibly by a MiM mechanism, and then reusing them to forward them to the recipient. It is not necessary to understand or decipher them.
For example, if a sender sends an encrypted name and password to a recipient to authenticate himself, it is possible for a hacker, by reusing the same sequence, to usurp the sender’s rights.
An attack of this type is possible against certain types of vulnerable PLCs: an attacker with access to the OT network can steal session numbers and add arbitrary commands to stop or restart the PLC.
4.8. Physical attacks
If the attacker can obtain physical access to the target, a number of additional attacks are possible.
First, it can simply destroy or degrade the equipment. This possibility aside, he can:
- – connect devices to spy on data (including passwords), such as a keylogger that connects to the keyboard wire and captures all user entries, or via the JTAG test port;
- – steal memory cards or mass memories to copy or modify them;
- – steal equipment in order to carry out reverse engineering and possibly detect vulnerabilities that can be used remotely;
- – simply use the live keyboard-mouse device to attempt an intrusion or the screen to steal information.
A physical attack may also be carried out on discarded equipment for the purpose of stealing data or passwords.
4.9. Attacks using the human factor
4.9.1. Social engineering
One of the weakest links in IT system security is the human aspect. In addition to human errors, unintentional (carelessness) or deliberate (conscious non-compliance with the rules), the human user can be a victim of so-called social engineering techniques.
These methods are based on lies, misrepresentation, blackmail or greed. The attacker can, for example, contact a system administrator and pretend to be an authorized user, asking to have a new password. Another common strategy is to pose as a member of a supplier’s staff who needs temporary access to perform emergency maintenance.
These techniques also rely heavily on phishing scams that aim to abuse the “naivety” of users to retrieve their credentials.
There are two types of phishing: mass phishing, using generic emails, and spear phishing, which is carried out after investigation of the target and the company, and can be much more difficult to detect.
Examples of an attack may include the following:
- – the receipt of an email using the company’s logo and colors;
- – a request to perform an operation such as updating personal data or confirming the password;
- – a connection to a fake site identical to that of the company and controlled by the attacker;
- – the recovery by the attacker of the login/passwords (or any other sensitive data) entered by the customer on a fake site.
This site may be an equipment manufacturer site and, for example, provide updates.
Such an attack occurred in early 2018: a fake patch for Meltdown/Specter Patch vulnerabilities attempted to install malware. The emails appeared to come from the German Federal Office for Information Security (BSI), and linked to an imitation site, with an SSL certificate (https:). The site was not official, but tried to encourage users to install the patches, which were actually malware.
4.9.2. Internal fraud
The fact that an authorized user knowingly uses his or her access to harm the security of an organization is called internal fraud. The user may be an employee, a consultant or a subcontractor. This case is to be distinguished from the user who provides their access details, either through negligence or because they has been misled. This problem remains a taboo subject for many companies, while it is increasing significantly (Cole 2017). There are different categories of fraudsters: the occasional fraudster, the recurrent fraudster, the person who is deliberately hired to carry out fraud and group fraud. The problem is particularly important for privileged users such as managers or administrators (Ware et al. 2017).
These attacks are made possible by organizational vulnerabilities:
- – weaknesses in internal control and operational monitoring procedures;
- – permissive management of IT authorizations;
- – lack of segregation of duties and rotation.
Appropriate organizational measures are therefore to be planned.
4.10. History of attacks on ICS
The first known attack on an ICS was in 1982 on a gas pipeline in Russia. A Trojan horse introduced into a Supervisory Control And Data Acquisition (SCADA) system caused the pipeline to explode. Since then, many attacks have taken place. Table 4.4 presents the most well-known attacks.
An important milestone was the 2007 attack demonstration by the Idaho National Laboratory. This one, called Aurora, was done to demonstrate how a cyber-attack could destroy the physical components of the power grid. In this attack, the attacker uses a communication protocol vulnerability to access the control network of a diesel generator. This allows it to run a malicious computer program that has been designed to open a circuit breaker, wait for the generator to desynchronize and immediately close the circuit breaker. Such actions, carried out fast enough so that the protection system cannot detect the problem, led the diesel generator to explode, which can be seen on the video of the experiment (Idaho National Laboratory n.d.). Since most electrical network equipment uses this type of communication protocol, the experience highlights a vulnerability that is of particular concern.
A few years later, Stuxnet (Falliere et al. 2011) made its mark on the history of cybersecurity of industrial systems and raised awareness of the vulnerability of SCADA systems. According to anonymous sources, Stuxnet was a computer worm developed to slow down Iran’s nuclear program. Stuxnet specifically targeted PLCs used by centrifuges to separate nuclear materials for uranium enrichment purposes. It would have allowed the destruction of 20% of production capacity.
The principle of Stuxnet’s operation is, on the one hand, to propagate between the machines of a Windows network, and on the other hand, when it detects a programming environment for a PLC of a certain type, to set up a module that modifies the program sent to the PLC when it is transmitted. This modification alters the behavior of the control system and degrades the centrifuges controlled by untimely and hidden speed variations.
In more detail, Stuxnet is introduced into the target environment via a drive connected to a USB port. The worm then spreads across the computer network using several Windows vulnerabilities:
- – it replicates itself via removable drives exploiting a vulnerability allowing automatic execution via LNK/PIF files (BID 41732);
- – it spreads in a local network via a vulnerability in the Windows spooler (print queue manager), which allows remote code execution (BID 43073);
- – it spreads via SMB, a shared file access system, by exploiting the Remote Procedure Call (RPC) remote code execution of the Microsoft Windows Server service (BID 31874).
Once installed on a workstation, if this workstation runs the Step 7 development environment, Stuxnet modifies the library that communicates with the PLC. It can therefore add the malicious code to the sent program and hide the return from the PLC.
Another turning point occurred very recently in 2017. This is the attack called TRITON (Ferguson 2018), designed to attack Triconex security systems, particularly those installed in industrial petroleum units. The precise location of the facilities affected by the attack has not been revealed, but it is assumed that these units were located in Saudi Arabia. The objective of this attack was to disable the security systems. From this situation, it is possible either to shut down the unit using the SIS or to allow the installation to pass through in a dangerous state. In the case of a process control error, either by accident or caused by another attack, the consequences could have been dramatic. A bug discovered the attack.
TRITON’s intention to harm is clear, since this type of system is intended to guarantee the physical safety of the facility and the population. Causing a SIS to malfunction means ensuring that an industrial accident can occur in the event of operational disruptions.
At the IoT level, a well-known demonstration is the attack on Philips Hue lamps in 2016. This demonstration was carried out by researchers (Ronen et al. 2017) who succeeded in taking control of a network of connected Philips Hue brand lamps. These bulbs are connected via a Zigbee network, and the user can use a remote control to control the intensity or color of the light they emit. These bulbs had a significant security breach.
As the researchers explain, the encryption keys used by the connected bulbs to communicate with each other are all the same, allowing a bulb infected with malware to easily transmit it to other lamps. The flaw exploited by the researchers is the Zigbee protocol used by Philips Hue light bulbs to communicate with each other. They say they were able to retrieve the encryption keys used to authenticate messages exchanged between the bulbs.
Many other attacks have taken place, with consequences of varying significance. Table 4.4 presents the most well-known attacks.
Table 4.4. Attacks on ICS
| Year | Attack | Description | Consequences |
| 2018 | Alert (TA18-074A) | IS-CERT alert about an attack on US infrastructure, multiple attack path, including social engineering techniques | Information retrieval on ICS |
| 2017 | BrickerBot | Similar to Mirai with permanent destruction of contaminated objects | Attacks and deactivation of objects |
| 2017 | TRITON | Attack on SIS security automatons (Triconex), Remote Access Trojan (RAT) | Shutdown of the installation, potential industrial disaster |
| 2017 | WannaCry | Massive attack affecting more than 300,000 workstations using a Windows flaw and performing data encryption, then a ransom request, virus spreading via a Windows flaw (EternalBlue) | Financial losses (ransom), production shutdown |
| 2017 | Petya | Attack on accounting software in Ukraine. Same vulnerability as Wannacry | Financial losses (ransom), production shutdown |
| 2016 | Philips Hue | Attack demonstration with takeover of a Philips Hue lamp network Vulnerability protocol and physical IoT attack |
Demonstration of real scale vulnerability |
| 2016 | Mirai or DYN | Attack of Dyn servers by DDoS contamination of connected objects (camera, DVR players, etc.) using identifiers by default launch of a DDoS (request flooding) attack on servers translating site names into IP addresses | Internet blocking, name servers no longer providing services |
| 2016 | Lappeenranta Building attack | Attack on the heating system of a building in Finland (managed by Valtia), DDoS | Loss of heating |
| 2015 | BlackEnergy | Power outage for 6 h affecting 230,000 people in Ukraine, Spear phishing email to install a Trojan | Power supply failure |
| 2015 | German Steel Mill Cyber attack | Takeover of the control system of a blast furnace that generated massive damage, Spear Phishing email and Trojan | Physical damage |
| 2014 | DragonFly | Attacks against energy companies by compromising ICS equipment, Remote Access Trojan (RAT): Havex/Energy bear Email (pdf), Watering hole attack | Sabotage |
| 2014 | Sandworm | Attack on General Electric and Siemens software Zero Day Vulnerability Windows CVE 2014 4114 (OLE exec) |
Sabotage |
| 2012 | Telvent Canada attack | Access to the administration tools of the control system Malware distribution via social engineering |
Information theft SCADA software |
| 2011 | Night Dragon | Extraction of confidential information relating to oil and gas projects. Social engineering and root control | Data theft |
| 2011 | Duqu | Parts of the code almost identical to Stuxnet, designed only for industrial espionage without containing destructive functions | Data theft |
| 2010 | Stuxnet | Several years of infiltration into the Natanz uranium enrichment complex, damage to more than 900 uranium enrichment centrifuges Complex attack exploiting Windows and Step7 vulnerabilities |
Degradation of centrifuges |
| 1999 | Gazprom (Russia) | Takeover of the distribution panel controlling gas flows from pipelines Trojan and internal complicity |
Stopping of production |
| 1982 | Pipeline attack | Attack on a pipeline in Siberia, Trojan on SCADA | Gas pipeline explosion |
4.11. Some statistics
Table 4.5 presents the most frequent attacks identified by BSI 54 (Federal Office for Information Security 2016). It should be noted that those using the human factor are in the lead. The incidents reported by sector in the United States by CERT in 2014 are shown in Figure 4.9. Of these, 55% correspond to APT attacks.
These incidents, although limited in number, are increasing sharply according to Kaspersky (Kaspersky Lab 2018).
Table 4.5. The most frequent attacks
| No. | Top 10 2016 | Top 10 2014 |
| 1 | Social engineering and phishing | Malware via Internet Infection and Intranet |
| 2 | Malware spread via removable media and external hardware | Malware spread via removal media and external hardware |
| 3 | Malware via Internet Infection and Intranet | Social engineering |
| 4 | Intrusion via remote access | Human error and sabotage |
| 5 | Human error and sabotage | Intrusion via remote access |
| 6 | Control components connected to the Internet | Control components connected to the Internet |
| 7 | Technical failures and cases of force majeure | Technical failures and cases of force majeure |
| 8 | Compromise of Extranet and Cloud components | Compromising smartphones in the production environment |
| 9 | (D)DoS attacks | Compromise of Extranet components and Cloud components |
| 10 | Compromise of Extranet and Cloud components | (D)DoS attacks |
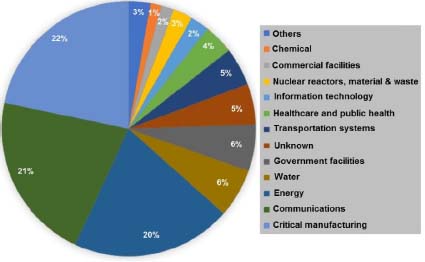
Figure 4.9. Sectors affected by attacks. For a color version of this figure, see www.iste.co.uk/flaus/cybersecurity.zip
