Appendix 2
Blockchain and IIoT Security
A2.1. Blockchain principle
The first blockchain was developed for the Bitcoin cryptocurrency. It appears that the concept is quite broad and the applications of blockchain are very numerous.
A blockchain operates using Distributed Ledger Technology (DLT). It is a database system with specific features:
- – it stores transactions in a distributed way by replicating them on the nodes of a peer-to-peer network (P2P);
- – it operates in a decentralized manner, i.e. without a central authority or control body;
- – it is secure and stores transactions immutably in blocks. Each transaction is verified and recorded using cryptographic techniques to create a history in the form of a chain of blocks.
Records in which transactions were recorded existed before the birth of computer technology in the paper form, particularly in accounting (ledger is the term used in accounting). A central authority was in charge of keeping it and checking the validity of the entries.
With DLT technologies, registry management offers additional capabilities, since it operates without central authority and in a distributed manner.
The blockchain uses the ECC cryptography algorithm (cryptography on elliptic curves) and the SHA-256 hash to provide solid cryptographic evidence for data authentication and integrity.
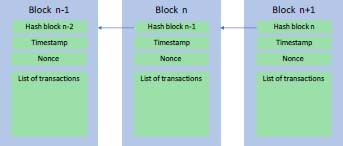
Each block contains a list of transactions and a hash from the previous block. The blockchain therefore has a history of all transactions, and constitutes an unforgeable shared register available to all, without central authority.
In the Bitcoin chain, a block is validated by determining a parameter (called nonce) that makes it possible to obtain a hash starting with a certain number of zeros. Miners compete to solve this problem. The solution found is called Proof of Work. The number of zeros defines the degree of difficulty of the validation. For the Bitcoin infrastructure, it varies so that for the average mining time is around 10 min.
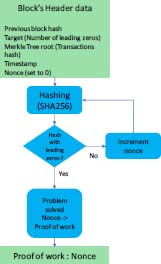
The concept initially proposed by the Bitcoin blockchain has been generalized. Different approaches exist, and they are characterized by:
- – the mechanism to guarantee trust, called the consensus mechanism, which makes it possible to validate a block and guarantee its integrity. There are mechanisms other than proof of work such as proof of stake;
- – the mechanism for propagating and synchronizing blocks between network nodes. In addition to the Bitcoin method, there are other solutions such as propagation based on headers, or unsolicited sending.
The choice of the approach depends on the degree of opening of the blockchain. Indeed, there are public blockchains, blockchains with controlled access and private blockchains. Depending on the type, the level of trust of the nodes is different and, therefore, the consensus mechanism is adapted. Whenever possible, the type that is the least time consuming to calculate is chosen.
A2.2. Smartcontracts
The notion of smartcontracts was proposed by the blockchain Ethereum. It was launched in July 2015 and since then a large number of similar platforms have emerged, such as HyperLedger.
Unlike the Bitcoin blockchain, which is mainly used for digital currency transactions, the Ethereum blockchain has the ability to store records and, more importantly, to execute smart contracts. The term “intelligent contracts” was invented by Nick Szabo in 1994.
An intelligent contract is an IT protocol designed to facilitate, verify or digitally apply the negotiation or execution of a contract. Smart contracts allow credible transactions to be carried out without third parties. These transactions are traceable and irreversible.
More concretely, a smart contract is a piece of code that resides on a block string and is identified by a unique address. An intelligent contract includes a set of executable functions and state variables.
Any user of the blockchain network can trigger the contract functions by sending transactions to the contract. Transactions include input parameters required by the contract functions. When executing a function, the contract status variables change according to the logic implemented in the function. Contracts can be written in different high-level languages (such as Solidity close to Javascript). The Ethereum blockchain allows the use of Ethereum Virtual Machines, which are the mining nodes and which are capable of ensuring a reliable and inviolable execution of these programs or contracts.
The contract code is executed on each node participating in the network as part of the verification of new (mining) blocks.
A2.3. The contributions of the blockchain for the Industrial Internet of Things
A blockchain is a distributed and secure database system that does not use trusted third parties and capable of performing secure actions. This type of infrastructure could therefore provide solutions to the problems of securing Industrial Internet of Things (IIoTs), and much work is currently being done to explore its possibilities.
A2.3.1. PKI Infrastructure
Since blockchain technology provides a distributed and unalterable information registry, it appears to be potentially appropriate for public key storage and management. This could allow for better availability and robustness compared to using a centralized server.
A2.3.2. Object identification
The blockchain has an address space of 160 bits, more than the IP6 space, which is 128 bits. It can therefore provide an address for 1.46 × 1048 pieces of equipment (Globally Unique Identifier [GUID]). An identification using the blockchain would be decentralized and would no longer require a centralized system for address distribution.
For management of the ownership of assets (equipment), the blockchain can also provide a reliable solution. It can be used to register and give identity to connected IoT devices, with a set of complex attributes and relationships that can be downloaded and stored on the distributed blockchain registry. Among these attributes, it is possible to include successive owners.
A2.3.3. Communications security
With a blockchain, the management and distribution of keys is completely eliminated, as each IoT device will have its own GUID and asymmetric key pair when it connects to the blockchain network. This can also significantly simplify other security protocols, since it is not necessary to manage and exchange PKI certificates during the initialization phase of the transaction.
A2.3.4. Firmware update
By using smartcontracts, which are secure because they are in the blockchain, and activated by a transaction, the secure distribution of updates is greatly simplified.
A2.3.5. Automatic execution of actions
With a smartcontract, a self-executable code that can be integrated into each IoT chip could determine what action to take when a condition is met. These actions would only be performed if an incoming transaction was authenticated.
For example, an intelligent sensor could initiate automatic actions, or a supply-chain system could be coupled with invoicing.
A2.4. The limitations of blockchain
Blockchain does not solve all problems and this promising technology is still in its infancy. Currently, a number of limitations exist. This technology is expensive in terms of network bandwidth and computing time (and therefore energy). It can have a relatively long response time compared to a centralized architecture.
In addition, blockchain has vulnerabilities (Li et al., 2017): for example, it is enough to convince 51% of the nodes to make a fact a truth, which can be a problem on small networks.
