9
The Socio-Behavioral Cipher Technique
Harshit Bhatia1*, Rahul Johari2† and Kalpana Gupta3‡*
1 Reval India Private Limited, Gurugram, India
2 USICT, GGSIPU, Delhi, India
3 C-DAC, Sector-62, Noida, India
Abstract
The primitive and the traditional symmetric key cryptographic systems made use of a limited number of input keys with single encryption function for securing the data before the data can be transmitted over unsecure network. Such limited key cryptographic functions did not withstand the test of time and have become obsolete over time. With the advent of social networking era, the network traffic has also increased rapidly and this increase in unsupervised and unsecure traffic demands a strong and a secure symmetric key technique. This chapter presents a secure and an efficient symmetric key technique that harnesses the readily available social profiling information of the sender for encryption and decryption of the data blending the social behavior of the sender along with the cryptography.
Keywords: Cryptography, symmetric-key, encryption, social, behavioral, profiling
9.1 Introduction
With the increase in human footprint on the internet, there has been a rapid increase in the network traffic too. Much of the data that flows through the internet via the network highway enters and leaves from social network as the social networking has seen an exponential growth over the past years. This expansive data circulates across various nodes through the interconnected web present between the actual source and the destination. This information, often, travels unhindered and in plain-text form without any form of secure jacket encompassing around it. With the increase in social information of individuals arising from various social networking websites, the sensitivity of the data has also increased. Ever-increasing social data along with sensitive information poses serious need for advancing security tools that may cater to the social networks too.
There are several symmetric and asymmetric cryptography techniques available that cater to providing security of data [1, 2]. However with the increased social footprint of humans, there has been a need to find new and better cryptographic technique that can factor in the social profiling information of humans too within the encryption function. This unique collaboration of social profiling information of the user along with the encryption keys being fed to the encryption function will account for a technique that would be less penetrable to several attacks. The proposed technique is an approach that makes judicious use of the social footprint of the user and makes use of this social footprint on user on the internet to do social profiling of user. This social profiling information is further bundled together with an encryption function to generate the cipher text. The technique has been created to be able to provide an increased level of security of data for the social networking websites traffic, however just not limited to the social network.
9.2 Existing Technology
In [3], author(s) have discussed the need for cryptography in network security and various cryptographic algorithms used for network security. A discussion has been done on the advantages, disadvantages, and usage of various algorithms.
Cryptography is used for the purpose of security on web. However, like everything, this has its pros and cons too. Similarly, there are uses and misuses. So, in [4], author(s) have discussed the misuses of cryptography in web security. The experiments were conducted on ASP.NET to show how cryptographic algorithms were compromised in ASP.NET web applications. Author(s) have also suggested some measures to curb attacks on web security.
With the evolution of big data, the amount of data being produced is being increasing at incredible rates. With data being processed digitally, the attacks on data are very common these days. So, it is important to secure it. In [5], author(s) have discussed cryptography and security in relation with digital signatures. Digital signatures are used for binding identity to the information and making it secure with encryption. Still, attacks are possible on digital signatures. Author(s) have also discussed the attacks on digital signatures.
In [6], author(s) have presented a tool called SHAVisual for visualization of cryptographic algorithm: SHA (Secure Hash Algorithms) 512 algorithm.
In [7], author(s) have proposed a new cryptography algorithm. Then, comparison of the same has been made with the existing cryptography techniques in terms of throughput of key generation, to generate encryption text and to generate decryption text. Analysis has also been taken into consideration regarding how much prone it is to brute force attacks, in other words, how secure it is. The algorithm involves arithmetic and logical mathematical operations. According to the results presented, this algorithm has better performance in comparison to existing algorithms. The algorithm shows high throughput and high security features.
Visual cryptography came into existence to overcome the challenges of traditional cryptography algorithms, that is, they have larger computational times. Comparatively, visual cryptography involves less computing power. Although visual cryptography has easy encryption and decryption methods and other benefits, but it is still not a success due to its implementation features. It requires a new key every time. If same key used, then, one must compromise with the security. There are numerous applications of visual cryptography. In [8], author(s) have discussed one of the features of visual cryptography, that is, user authentication. Traditional visual cryptography techniques have vulnerabilities, so, author(s) have proposed a new system protocol based on visual cryptography technique for user authentication to server. This protocol can be used for the creation of secured channel between two parties.
In [9], author(s) have presented a visualization tool called VIGvisual for learning of cryptography algorithm vignere cipher. The tool involves both encryption and decryption techniques. In author(s) opinion, tool is versatile, efficient and user friendly.
In [10] author(s) have attempted to develop a bi-lingual machine translation tool for sentences in simple present and past sentences. The translation of the user interface of a knowledge-based system has been automated. The project executes the transformation process of well-structured simple present and past sentences written in Arabic language to a well-structured English sentence by using dictionary as a means for translation. The methodology which has been adopted is dependent on the basic structural components such as the parts of speech of a language that are necessary for translations.
Elliptic Curve Cryptography is replacing cryptographic techniques because of its high level of security. In [11], author(s) have further improvised ECC algorithm by replacing the mapping the characters to affine points in the elliptic curve with the pairing up of ASCII values of the text. First, this change reduces the overall cost of the algorithm by removing the mapping operation. Second, with this change there is no longer any need to share the lookup tables between sender and receiver. Further this algorithm can encrypt and decrypt any text of ASCII values.
In [12] author(s) have used already existing affine cipher technique to be implemented at the encryption phase of the storage part where a confidential data such as credit card detail is to be stored. The cipher technique has been achieved along with the mapping of plain text characters to cipher text being generated in Hindi language characters.
In [13], author(s) have focused on cryptography, its goals, terms of cryptography, algorithms, attacks. A review has been presented on cryptography, mainly focusing on security and time constraints. In author(s) opinion, depending upon the security level, cryptography algorithm must be chosen.
Visual cryptography refers to encryption of visual information in which decryption is not anymore, a digital process but a mechanical one. In [14], author(s) have focused on the application area of visual cryptography such as data hiding, securing images, color imaging, multimedia, et al. Encryption of data in visual cryptography has been explained.
In [15], author(s) have discussed the data hiding techniques and cryptographic algorithms. The reasons for evolution from early stage cryptographic algorithms to present cryptographic techniques have been explained. Their advantages and disadvantages have also been taken care in the discussion. Cryptography and steganography are also explained. Both aim at data security but with different approaches. In cryptography, data is encrypted as well as hidden from the attackers but in steganography, data is also encrypted but not hidden from anyone. Its real meaning is hidden.
Dynamic nature and the limited resources of sensor nodes pose a challenge in implementation of secure wireless sensor networks. Clustering of the sensor networks is a solution for this, but security is an issue in this. In [16], ECC algorithm has been used for the generation of unique 176-bit encryption binary strings for each sensor. This algorithm is robust to brute-force attack, HELLO flood attack, selective forwarding attack, and compromised cluster head attack.
9.3 Methodology
The author[s] have proposed a lightweight cryptographic technique in the literature that is aimed at increasing the security of the data by harnessing the social profiling information of the end user. The proposed system is a symmetric key cryptographic technique which employs the same domain of keys for the process of encryption as well as decryption. The technique uses a series of mathematical operations on the plain-text input and returns an encrypted cipher text by performing the operations in a pre-defined order.
By symmetric key cryptography, we refer to the class of cryptosystems which use the same set of keys for both encryption of the data at the sender’s end, as well as for decryption of cipher text received on receiver’s end to obtain the original plain text that was meant to be transmitted. Both sender and receiver share their set of keys by means of a secure channel. The keys must always be kept secret between the sender and receiver and this forms as one of the necessary conditions for the symmetric key ciphers to work. The method by which the keys are shared between the sender and receiver via a secure channel is out of the scope of this technique and the literature here makes no comment on how the keys must be shared. The technique proposes the cryptosystem wherein the keys are being used by the technique to encrypt and decrypt the transmitted text.
The increase in the social data has brought into the picture the need to harness the readily available social information to protect the same unsecure information that is being transmitted out. The proposed technique makes use of the fact that social information of the sender is readily available and should be made use of, to secure the data that sender is transmitting out to the receiver and hide it from unauthorized sniffer or attacker to gain access to information. For the same purpose, the social profiling information of the sender is made use of. The social profiling process points to the building of the identity of the user based on several social network activities and social network data that is readily available with the consent of the user from the user’s local machine itself.
9.3.1 Key Arrangement
The primary candidate for building a secure symmetric cryptographic technique is the choice of the keys that ascertain the invulnerability of the technique to various threats. The good choices of strong keys, like good passwords, need to be hard to guess as well as must be bigger in size to counter the traditional attacks on them. The choice of the keys is critical to the security of the key and therefore the keys must be carefully handpicked. It is often noticed that a bad and small encryption key falls prey to attacks when used even on secure algorithms. To counter this problem of how to determine good candidates for secure encryption keys, a good technique must make that choice on the parameters and variables available to it. Often the most serious threat to an encryption technique is from the end user itself. To elaborate upon this statement, if the user chooses an easy to guess and a simple encryption key then it opens up the technique to a series of attacks. Therefore, reducing the human interaction element from the input domain and automating the process could also add to the security of the technique.
Keeping the above picture in perspective, the proposed technique makes use of an automated key selection procedure where the technique takes the keys from encryption environment itself without asking for the input from the end user. The cipher technique is focused on bringing the social aspect of end user into the cryptographic methodology and hence the social profiling information of the end user/sender makes for one of the primary keys in the technique.
The technique has a domain of five encryption keys that are kept secure and secret. The keys are not provided by the sender to the technique, hence, it adds to the security of the encryption technique and also makes it automated to be run. The sender only provides the plain text to the technique, and the cryptosystem encrypts the text before sending it to the receiver.
9.3.2 Key Selection
The first key is derived from the social profiling information of the user. The social profile, as explained above, is the social identity of the user which is derived from the data obtained from social networking information of the user. This technique makes use of the user’s social browsing habits to identify the social interests of the user and hence, ascertain the field that patronizes the user’s browsing. The browsing habits of user are analyzed over a period of 24-h window to predict the behavioral pattern of internet browsing by making use of the available browsing habits of user.
The cookies that are stored on the machine running the cryptographic technique (sender’s system) are used to serve the purpose of the web profiling of the user. Data from the cookies are read by the technique and the websites browsed by the user over a period of 24-h is analyzed. These websites are then matched against a table of stored websites and the type of category that website belongs to. For instance, there are a set of pre-defined categories available with a list of sets belonging to each category, like Sports, Movies, Education, Music, Games, News, Finance, etc. The websites are matched against these categories and the category with the greatest number of matched websites is chosen. This predicts the user’s interest area and this interest area has a predefined encryption defined against it which is then used as one of the encryption keys. The key-category pair value changes periodically over a period of time so as to exempt any kind of pattern to be formed by making use of same keys. For the websites that do not match any of the pre-defined categories a counter for miscellaneous category is incremented and if the miscellaneous category is maximum then the key is picked up from the miscellaneous key-category pair and that is used as the first encryption key.
The second key is selected by using the physical address of the machine (MAC address) that is running the cryptographic technique and from which the first key was selected. The alphanumeric MAC address is converted into a numerical key and the colon separators are removed from between. The alphabets are mapped into a corresponding number where A is mapped to 1, B to 2, and so on till Z is mapped to 26. The obtained number serves as the second key of cryptographic system.
The third key is chosen to be the current timestamp when the user starts the execution of the encryption mechanism. The current timestamp in milliseconds is used as the key and ensures every round of execution of cryptographic technique ensures a new key and hence makes it difficult for the attacker to sniff around and obtain the flowing encrypted data out of the system as plain text. The third key needs to be co-prime with the number of characters in the encoding standard being used. For instance, the illustration uses the ASCII character set, hence the third key needs to be co-prime with 256. If that is not the case, then the nearest upper bound co-prime of current timestamp with 256 is used as the third key.
The geographical coordinates of the user also form a basis of the social profile of the user. The demographic information is therefore used as the last two keys of the crypto system. The latitude and longitude serve as the fourth and the fifth key respectively and they are easily calculated with the user’s current location.
The set of five chosen keys is selected in such a manner that they are always unique to every user, every machine and every encryption round. This setup is similar to the rotational key setup where the keys are changed periodically. The advantage of such a unique keyset is that they are always hard to guess or be obtained easily by the attacker and thus, this increases the overall security of the encryption cryptosystem by manifolds.
9.3.3 Mathematical Operations
Another candidate that decides the effectiveness as well as the security of the technique is the operations that are being performed on the text using the keys to encrypt the data. The symmetric key cypher technique uses the same set of keys for both the encryption as well as decryption of the data. Along with the same set of keys, the symmetric cipher technique also uses the same set of mathematical operations for encryption and the counter mathematical operations for decryption of the data. By counter mathematical operation, we refer to the family of mathematical operation where the use of an operation with a key would map the characters to a different set of characters, and the use of a different operation with same keys on the new character set gives back the original text. This second operation is referred to as the counter operation to the first operation. A very primitive example of this is the operation Addition and counter operation is Subtraction. If we add 5 (mapped as key) to a number 10 (original text), we get 15 (cipher text). If we subtract the same key, 5, from the cipher text, 15, we get the original text back which was 10.
The proposed cryptographic system has introduced a lightweight cryptography technique that makes use of primitive mathematical operation which makes the technique fast without making any compromise on the security of the data being transmitted. A good technique must be secure as well as be quick to avoid any kind of notable delays in transmitting data between sender and receiver. The operations that are being used by any technique must also be easy to implement in the hardware system. Often using heavier mathematical operations requires more expensive hardware implementations and therefore adds to the overall cost of transmitting data. The proposed technique makes use of cheaper mathematical operations which are both cost-effective as well as faster in terms of processing speeds.
The technique makes use of the following mathematical operations to encrypt the data in a predefined order (discussed in next two sections):
- Addition
- Subtraction
- XOR
- Multiplication
- Bit dispersion
The bit dispersion mathematical operation garbles the length of the text by varying the plaintext length to that of the final cipher text length. This makes it harder for the attacker to map the length of the plain text to that of the cipher text thereby decreasing the probability of linear attacks on the technique. The use of multiple mathematical operations along with the use of multiple keys to encrypt and decrypt the data makes it harder to decipher the cipher text.
9.3.4 Algorithm
This section presents the algorithm of the socio-behavioral cipher technique. First algorithm deals with the selection of the first key from the social web profiling of the user and loading of other four keys:
- Step 1: Start
- Step 2: read cookies <= 24 hours
- Step 3: store website name from cookies → website[n]
- Step 4: initialize i → 1
- Step 5: load category database containing pre-defined websites
- Step 6: if website[i] = db(category, website)
- Step 7: increment category count
- Step 8: increment i
- Step 9: Repeat steps 7 through 9 till i > n
- Step 10: choose max_count(category)
- Step 11: choose key against max_count(category) → K1
- Step 12: fetch MAC address
- Step 13: convert(MAC) to ASCII → K2
- Step 14: get current timestamp in milliseconds → K3
- Step 15: if coprime(K3, 256) is false
- Step 16: nearest_coprime(K3, 256) → K3
- Step 17: fetch current location latitude → K4
- Step 18: fetch current location longitude → K5
- Step 19: end
The above algorithm shows how the five keys are loaded into the system and are made available for the cryptographic technique to be used. Second algorithm depicts the encryption process performed on these keys:
- Step 1: start
- Step 2: accept plaintext from user → PT
- Step 3: load keys K1, K2, K3, K4, K5
- Step 4: convert PT to ASCII decimal → P
- Step 5: XOR(P, K1) → E1
- Step 6: Subtract(E1, K2) → E2
- Step 7: Multiply(E2, K3) → E3
- Step 8: Addition(E3, K4) → E4
- Step 9: Dispersion(E4, K5) → C
- Step 10: return final Cipher Text as ASCII character → CT
- Step 11: end
Similarly, the decryption algorithm works with encryption steps performed in a counter fashion. The decryption process is intuitive and therefore the algorithm has not been presented in this text.
9.3.5 Encryption Operation
This section brings forward a conjectural adoption of the discussed cryptographic technique in the previous sections on a sample plaintext and input keys. The example illustration uses the ASCII character set to work on for the technique; however, the actual implementation of the technique is not limited to the ASCII character set and can easily work on the Unicode characters too.
The ASCII characters are first encoded into the decimal number notation to perform the mathematical operations on them. The bit dispersion method accepts an ASCII character in binary form of 8 bits each and then groups the binary bits of the entire plaintext together, and then groups them into buckets of 7 bits each and then converts these 7 bits of binary bits into the corresponding ASCII character which is forwarded as the final cipher text. If the last bucket has bits less than 7 then the last bucket is appended with trailing zeroes as the padding bits. The example illustrates the process of encryption and the section that follows talks about the decryption process in detail on the sample plaintext and an input of five keys. The actual keys that the technique uses have been defined in the previous section but have been briefed below:
- Key 1: Social Profiling key based on category
- Key 2: Physical MAC address
- Key 3: Current timestamp in milliseconds
- Key 4: Latitude of current location
- Key 5: Longitude of current location
The example below illustrates a sample plaintext as well as it assumes simpler values of the five private keys that are always kept private between the sender and receiver and are not shared with the outside world.
- Plaintext- PROFILE
Let the private keys be (assumption: The example mentioned below uses smaller values of the five encryption keys for making the mathematical calculations easy and simple for demonstration purposes).
- K1 = 17,
- K2 = 29,
- K3 = 37,
- K4 = 47,
- K5 = 30
The technique makes use of following sequential mathematical operations to obtain a cipher text which is then transmitted to the receiver over an unsecure channel:
- E1 = (PT XOR K1)
- E2 = (E1 - K2) mod 256
- E3 = (E2 * K3) mod 256
- E4 = (E3 + K4) mod 256
- E5 = (E4 XOR K5)
- C.T. = bit dispersion (E5)
Table 9.1 describes the process with the help of an example and briefs the working of the technique and Figure 9.1 shows the encryption through a flowchart.
9.3.6 Decryption Operation
The process of the decryption is used to obtain the plain text from the cipher text at the receiver’s end. The secret keys have already been shared between the sender and the receiver. The final cipher text was obtained from the bit dispersion method, so the decryption process must begin with the reverse bit-dispersion method. This process takes the Cipher text and converts the ASCII values into binary bits which are then grouped together as character stream. This character stream is then converted back by regrouping into the 8-bit binary bits and discarding the additional padding (if any). The 8-bits are converted back into the ASCII numbers which become the input for the further mathematical operations of the decryption process. Mathematically, the process is carried out as follows:
- Cipher text, C is >lq(}!b<
- K1 = 17,
- K2 = 29,
- K3 = 37,
- K4 = 47,
- K5 = 30.
- The modulo multiplicative inverse to be used for the decryption process is depicted below:
K3 = 37 and K3-1 = 173 (K3 must be co-prime with 256 for inverse to exist.)
The resultant final message which is the Plain-Text can be formulated by the receiver by employing the use of following specified mathematical steps:
- Dc = reverse bit dispersion (C)
- D1 = (Dc XOR K5)
- D2 = (D1 - K4) mod 256
- D3 = (D1 * K3-1) mod 256
- D4 = (D3 + K2) mod 256
- P.T = (D4 XOR K1)
D1, D2, D3, and D4 are intermediate decryption step texts obtained and C is the input cipher text to the decryption algorithm along with five keys. Dc is the output of the reverse bit dispersion function.
The final plain text is denoted as D5 and can easily be derived as it is received at the receiver’s end. In order to ensure the security of the crypto-system, the sender and receiver must keep both the private keys as well as the order in which the mathematical operations are being performed as secret between the two of them and must be only shared over a secure channel (The key transmission and sharing is out of scope of the literature here). The length of cipher text and plain text are different thus avoiding the linear mapping of characters.
The above example has been simulated in Java with the same keys and plaintext as above. The actual implementation, also made in Java, only accepts the plaintext from the user and computes the keys as described in the previous sections.
Tables 9.1, 9.2, 9.3, and 9.4 list out the illustrative example along with each of the steps that have been performed on the plaintext along with the assumed set of keys. The entire process that has been briefed in the previous two sections has been illustrated in a tabular form for better understanding. Further, Table 9.5 lists out a sample database of websites along with categories, which are used for the computation of the Key 1. Table 9.6 has a sample list of websites that have been obtained from the user cookies which are cross-referenced against the websites sample list in Table 9.5. The matching websites against each category increment the value of counter for that category. The category with maximum value at the end of the cookie list is picked up from the pool and the key associated with the chosen category is used as Key 1. The categories that are to be used as listed below:
Table 9.1 Encryption table.
| P.T. | E1 = (P.T. XOR K1) | E2 = (E1 - K2) mod 256 | E3 = (E2 * K3) mod 256 | E4 = (E3 + K4) mod 256 | E5 = (E4 XOR K1) |
| P(80) | (80 XOR 17) = 65 (A) | (65 − 29) mod 256 = 36 ($) | (36 * 37) mod 256 = 52 (4) | (52 + 47) mod 256 = 99 (c) | (99 XOR 30) = 125 (}) |
| R(82) | (82 XOR 17) = 67 (C) | (67 − 29) mod 256 = 38 (&) | (38 * 37) mod 256 = 126 (~) | (126 + 47) mod 256 = 173 (¡) | (173 XOR 30) = 179 (|) |
| O(79) | (79 XOR 17) = 94 (^) | (94 − 29) mod 256 = 65 (A) | (65 * 37) mod 256 = 101 (e) | (101 + 47) mod 256 = 148 (ö) | (148 XOR 30) = 138 (è) |
| F(70) | (70 XOR 17) = 87 (W) | (87 − 29) mod 256 = 58 (:) | (58 * 37) mod 256 = 98 (b) | (98 + 47) mod 256 = 145 (æ) | (145 XOR 30) = 143 (Å) |
| I(73) | (73 XOR 17) = 88 (X) | (88 − 29) mod 256 = 59 (;) | (59 * 37) mod 256 = 135 (ç) | (135 + 47) mod 256 = 182 (╢) | (182 XOR 30) = 168 (¿) |
| L(76) | (76 XOR 17) = 93 (]) | (93 − 29) mod 256 = 64 (@) | (64 * 37) mod 256 = 64 (@) | (64 + 47) mod 256 = 111 (o) | (111 XOR 30) = 113 (q) |
| E(69) | (69 XOR 17) = 84 (T) | (84 − 29) mod 256 = 55 (7) | (55 * 37) mod 256 = 243 (≤) | (243 + 47) mod 256 = 34 (“) | (34 XOR 30) = 60 (<) |
Table 9.2 Bit dispersion operation.
| Obtained E5 | 125 | 179 | 138 | 143 | 168 | 113 | 60 | |
| E5 binary | 01111101 | 10110011 | 10001010 | 10001111 | 10101000 | 01110001 | 00111100 | |
| Cipher | 0111110 | 1101100 | 1110001 | 0101000 | 1111101 | 0100001 | 1100010 | 0111100 |
| Cipher Text | 62 | 108 | 113 | 40 | 125 | 33 | 98 | 60 |
Final transmitted cipher text for CRYPTO plaintext is >lq(}!b<.
Table 9.3 Reverse bit dispersion operation.
| Obtained C | 62 | 108 | 113 | 40 | 125 | 33 | 98 | 60 |
| C in binary | 0111110 | 1101100 | 1110001 | 0101000 | 1111101 | 0100001 | 1100010 | 0111100 |
| Re-Dispersed | 01111101 | 10110011 | 10001010 | 10001111 | 10101000 | 01110001 | 00111100 | |
| Dispersed ASCII | 12 | 17 | 138 | 14 | 16 | 113 | 60 |
Table 9.4 Decryption table.
| Dc | D1 = (C XOR K5) | D2 = (D1 − K4) mod 256 | D3 = (D2 * K3−1) mod 256 | D4 = (D3 + K2) mod 256 | D5 = (D4 XOR K1) |
| } (125) | (125 XOR 30) = 99 (c) | (99 − 47) mod 256 = 52 (4) | (52 * 173) mod 256 = 36 ($) | (36 + 29) mod 256 = 65 (A) | (65 XOR 17) = 80 (P) |
| | (179) | (179 XOR 30) = 173 (¡) | (173 − 47) mod 256 = 126 (~) | (126 * 173) mod 256 = 38 (&) | (38 + 29) mod 256 = 67 (C) | (67 XOR 17) = 82 (R) |
| è (138) | (138 XOR 30) = 148 (ö) | (148 − 47) mod 256 = 101 (e) | (101 * 173) mod 256 = 65 (A) | (65 + 29) mod 256 = 94 (^) | (94 XOR 17) = 79 (O) |
| Å (143) | (143 XOR 30) = 145 (æ) | (145 − 47) mod 256 = 98 (b) | (98 * 173) mod 256 = 58 (:) | (58 + 29) mod 256 = 87 (W) | (87 XOR 17) = 70 (F) |
| ¿ (168) | (168 XOR 30) = 182 (╢) | (182 − 47) mod 256 = 135 (ç) | (135 * 173) mod 256 = 59 (;) | (59 + 29) mod 256 = 88 (X) | (88 XOR 17) = 73 (I) |
| q (113) | (113 XOR 30) = 111 (o) | (111 − 47) mod 256 = 64 (@) | (64 * 173) mod 256 = 64 (@) | (64 + 29) mod 256 = 93 (]) | (93 XOR 17) = 76 (L) |
| < (60) | (60 XOR 30) = 34 (“) | (34 − 47) mod 256 = 243 (≤) | (243 * 173) mod 256 = 55 (7) | (55 + 29) mod 256 = 84 (T) | (84 XOR 17) = 69 (E) |
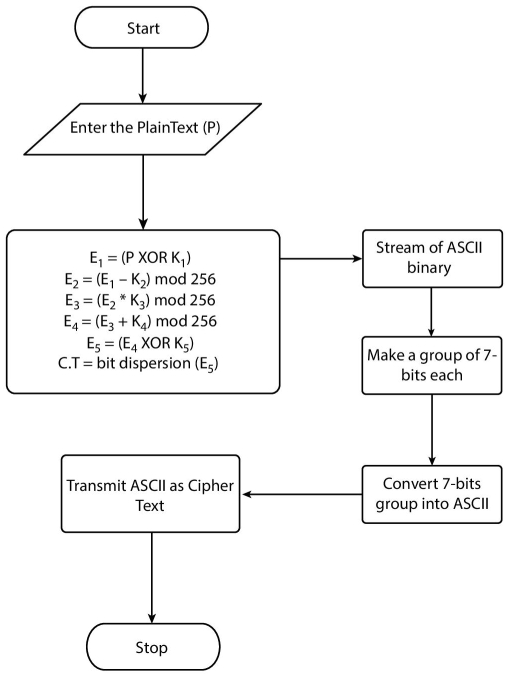
Figure 9.1 Flowchart for encryption.
- News
- Music
- Movies
- Games
The Tables 9.5 and 9.6 indicate the list of websites (the links of each website used here have been added to the references section at the end of the chapter). The website list in the user’s cookie database shows the usage of the list of websites, which the user has accessed over the past 24 h. The count of the matches of websites with the category names is listed below:
| News | Music | Movies | Games |
| The Hindu | SoundCloud | The Internet Archive | Miniclip |
| Times of India | YouTube | Retrovision | Armor Games |
| NDTV News | SoundClick | Roku Channel | Kongregate |
| India Today | AudioMack | Sony Crackle | NewGrounds |
| Deccan Chronicle | Jamendo | Pluto TV | Steam |
| The Indian Express | Amazon Music | PopCornFlix | Nitrome |
| The Financial Express | CCTrax | Hulu | AddictingGames |
Table 9.6 List of websites obtained from cookies.
| Cookies |
| The Hindu |
| YouTube |
| SoundClick |
| Hulu |
| Steam |
| Amazon Music |
| NDTV News |
| Roku Channel |
| YouTube |
- News: 2
- Music: 4
- Movies: 2
- Games: 1
This list clearly indicates that based on browsing habits of the user over a period of 24 h, the user has a preference of music over other three categories. Hence, the key associated to the category music is picked and is chosen as the key 1.
9.3.7 Mathematical Modeling
The Socio-Behavioral Cipher Technique employs the use of several mathematical operations for the purpose of the Encryption as well as Decryption operation. These mathematical operations have been revisited in this section to be depicted as mathematical equations. As a widely known fact, the encryption operation can be thought of a s a mathematical operation that takes in a series of mathematical operation(s) and a domain of plain- text and outputs a cipher text. This cipher text can be mathematically depicted to be obtained by a cipher function, C(q) parsed through mathematical operations. This function can be used in reverse to obtain the initial plain-text and this operation is known as the decryption operation.
- C(q) = BitDispersion (E5(q)) where, E5(q) = (E4(q) XOR K5(q)),
- and, E4(q) = (E3(q) + K4(q)) mod 256,
- and, E3(q) = (E2(q) * K3(q)) mod 256,
- and, E2(q) = (E1(q) - K2(q)) mod 256,
- and, E1(q) = ((P(q) XOR K1(q))
- where P(q) is plaintext length of size Nn,
- E(q) is the encryption function set which is composed of the five Encryption steps E1(q), E2(q), E3(q), E4(q), and E5(q), and K(q) is the private key set comprised of five keys K1(q), K2(q), K3(q), K4(q), and K5(q), which are being used by the encryption function set, each encryption function consuming individual keys on each single character of plain-text of size Nn. However, the bit dispersion operation that is being used here scrambles the obtained text and it is impossible to have on-to-one-character mapping between the cipher text and plain text, hence the cipher text length is different from that of plain text and length of cipher text C(q) can be denoted as m*
- The results of each encryption operation have been denoted as intermediary steps by E1…E5 and the result obtained is encoded as a numerical value which needs to be converted into the corresponding ASCII value. This value is finally transmitted as the cipher text from sender to the receiver end. The process of decoding the values of a cipher text of length “n” is performed by taking each functional integral value and then individually converting the integer to its corresponding ASCII character set, where the number is a “Real Whole number” and is in the range 0 < Cx(q) < 255, where Cx(q) represents the individual character from the set of Cipher text C, comprised of {C0(q), C1(q), C2(q),… Cn(q)}.
- The text obtained as a result of applying the Encryption function at step E5(q) is fed to the method ‘Bit Dispersion’ where it groups the set of input bits and scrambles them into a new group of bits that constitute the final cipher text. The method takes in a set of numerical values in Base10 Decimal form and then converts them to Base2 Binary format. The Base10 to Base2 (Decimal to Binary) conversion is done for every individual number which is a part of the input set of ‘Bit Dispersion’ method. The conversion rule for each bit qi can be summarized as:
Q1 = qi/2 where qi denotes the decimal bit and operation returns a remainder y0,
Q2 = y0 2 where the operation returns a remainder as y1, until the quotient Qx is 0.
The final Binary number that is obtained has x number of bits where this x denotes the step where Quotient was 0 and x will always belong to a set of Natural Integer. The number of bits will be in the range 0 < x < 9, since the mathematical operations are using the MOD operation with 256, hence the number of bits can never be greater than 8. The final binary text for each individual decimal number can be denoted as y0 y1 y2 y3 y4 y5 y6 y7 where the “y” denotes the remainders at every step.
- The “Bit Dispersion” method is aimed at accepting a number, converting the Integer number to a binary number and then perform bit scrambling operation to return a new Binary number which is then converted back to the Integer number which is the final output. The Decimal to Binary conversion returns an 8-bit binary number for every single decimal number, as explained above. All the binary values are then clubbed together and a group of 7 bit each is formed from these. The group of 7 binary bits is converted back to Decimal number and this forms the Cipher Text. The E5(q) is composed of “n” number of numbers where ‘n’ is the length of plain-text and can be denoted as:
E5(q) = R1 R2 R3 ….. Rn
Each Ri can be denoted as Binary number of 8 bits each as y0 y1 y2 y3 y4 y5 y6 y7
Thus, E5(q) = y0R1 y1R1 y2R1 y3R1 y4R1 y5R1 y6R1 y7R1 y0R2 y1R2 y2R2 y3R2 y4R2 y5R2 y6R2 y7R2 ..... y0Rn y1Rn y2Rn y3Rn y4Rn y5Rn y6Rn y7Rn C(q) = y0R1 y1R1 y2R1 y3R1 y4R1 y5R1 y6R1 y7R1 y0R2 y1R2 y2R2 y3R2 y4R2 y5R2 y6R2 y7R2 y0R3 y1R3 y2R3 y3R3 y4R3 .......
Converting the group of 7 Binary bits into the Decimal bits will return a set with a different length than “n” since the text has been scrambled. The new length of cipher text is denoted as “m*” and the final cipher text which is the result of the “Bit Dispersion” method is shown:
C(q) = C1 C2 C3 ……. Cm*
- The Binary to Decimal operation is also required where the transformation occurs when converting the Base2 binary value to a Base10 Decimal number. This operation is important to obtain the final Cipher Text number. The transformation takes in an 8-bit binary number which is represented as y7 y6 y5 y4 y3 y2 y1 y0 which is then converted into a single Base10 Decimal denoted as ‘R’ and can be computed as shown below:
Table 9.7 Time calculation.
S. no. Operations Time taken 1. First encryption E1(q) ∆T0 2. Second encryption E2(q) ∆T1 3. Third encryption E3(q) ∆T2 4. Fourth encryption E4(q) ∆T3 5. Fifth encryption E5(q) ∆T4 6. Final cipher text C(q) ∆T5 7. Computing social key ∆T6 8. Decimal to binary conversion ∆T7 9. Bit dispersion operation ∆T8 10. Binary to decimal conversion ∆T9 11. ASCII to character mapping ∆T10 12. Character to ASCII mapping ∆T11 - R = (y0 × 20) + (y1 × 21) + (y2 × 22) + (y3 × 23) + (y4 × 24) + (y5 × 25) + (y6 × 26) + (y7 × 27)
- The decimal numbers must be mapped into a corresponding ASCII character before it can be transmitted. The process of encoding the Decimal number to ASCII character and decoding the ASCII character to the decimal number will not alter the length of the input and will always return an output of same length as that of the input. The encoding operation is useful to compute the final encrypted cipher text which will be transmitted to the receiver and is also used to obtain the final plain-text on the receiver’s end. However, the decoding operation is used by the sender to convert the plain-text into the decimal numbers to perform mathematical operations on to it and is also used by the receiver to change the received cipher text into decimal numbers to be able to perform decryption operations on to it.
- The execution time can be broken into 12 parts as specified by Table 9.7 and average execution time, T, can be denoted as, T = (∆T0 + ∆T1 + ∆T2 + ∆T3 + ∆T4 + ∆T5 + ∆T6 + ∆T7 + ∆T8 + ∆T9 + ∆T10 + ∆T11)/12.
- The Socio-Behavioral Cipher Technique has an O (n) time complexity (denoted in Big-Oh notation) where n is the total characters in the input plain-text.
9.4 Conclusion: Future Scope and Limitations
The Socio-Behavioral cipher technique is a light-weight and a robust crypto technique which has a minimalistic execution time of encrypting the data. The technique is fast but is also secure by making use of multiple keys and multiple operations. The technique does not require heavy computations and have any additional hardware requirements to implement the crypto-system. The use of cost-effective mathematical operations along with the automatic selection of keys by the crypto-system, make it a secure technique. The cipher technique’s unique key selection mechanism and its use of the social browsing habits of the sender have blended the field of cryptography with the web profiling of user’s browsing behavior. This unique blend of social networking with cryptography makes the technique accurate to be used in the world where social data marks the majority of every day’s network traffic flowing via the internet.
The Socio-Behavioral Cipher Technique has been compared with its predecessor Triplicative Cipher Technique [19], where the running time has been compared of the two techniques. The results draw a clear picture toward the more advanced Socio-Behavioral technique which is both faster as well as stronger of the two cipher techniques as is depicted in the Figure 9.2. The cryptographic technique was simulated on a Java based simulation environment whose specifications are listed in Table 9.3. The output of the simulation is depicted by Figure 9.3.
The proposed innovative Socio-Behavioral technique is a symmetric key cryptographic technique; however, in the future, efforts would be made to extend it to be an asymmetric key cryptographic technique. The asymmetric cryptographic technique instead of a single key domain which is used for both encryption and decryption, a pair of public and private key is used, which is turn is helpful to enhance the prevailing level of security. Currently, the Socio-Behavioral technique uses a series of concrete yet simple mathematical operations on the user’s plain-text input and returns an encrypted cipher text by performing the operations in a pre-defined order. However, in future, the current work would be extended to pick the mathematical operations from a pool of operations in a random order that would change with every cycle of encryption. After such an implementation, a comparison of the two techniques would be carried out and the results would be compared. Currently, the proposed technique makes use of an automated key selection procedure. Similarly, in future it is proposed to come up new and innovative ways and means as to how the technique would take more keys from encryption environment itself without prompting for the input from the end user creating a perfect socially compatible cryptographic environment. Not only this, though the current cipher technique is focused on bringing the social aspect of end user into the cryptographic methodology but in future more social profiling information like Caching of Facebook and Instagram details of the end user/sender would be taken into consideration. The newly proposed technique is currently using only five keys, but the new and improved version of this technique would use more keys and the results would be compared in order to achieve efficient and socio secure encryption technique.
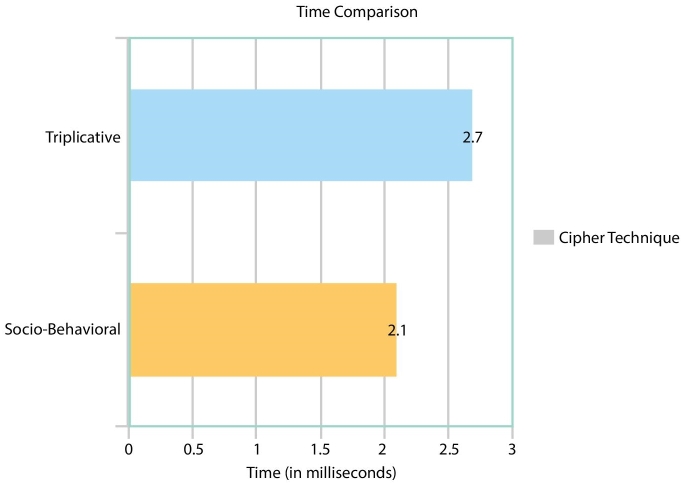
Figure 9.2 Comparison of the results of triplicative and socio-behavioral cipher technique [19].
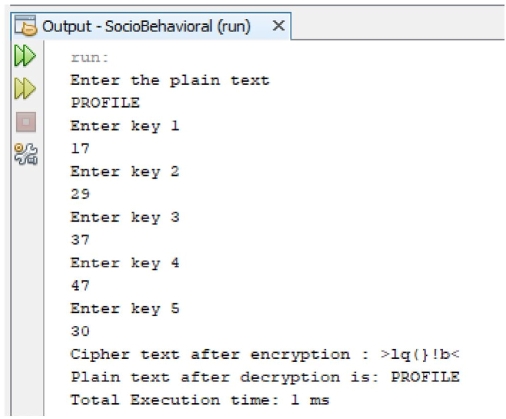
Figure 9.3 Output for socio-behavioral technique simulation as example illustration.
Table 9.8 Simulation table.
| Simulation environment | |
| O.S. used | Windows 10 Pro 64 bit |
| Processor | Intel Core i5 3230M |
| RAM | 8 GB |
| Simulation Env | NetBeans IDE |
| IDE version | 8.2.0 build 201403101706 |
| Development Lang | Java |
| Build Version | 1.8.0 build 25.25-b02 |
References
- 1. Forouzan, B.A., Cryptography and Network Security, Special Indian Edition, McGraw-Hill, published in India by arrangement with the McGraw-Hill Companies, Inc., New York, 2007.
- 2. Stallings, W., Cryptography and Network Security-Principles and Practices, fourth Edition, Pearson, printed in the United State of America, 2007.
- 3. Preneel, B., Cryptography for network security: Failures, successes and challenges, International Conference on Mathematical Methods, Models, and Architectures for Computer Network Security, Springer, Berlin, Heidelberg, 2010.
- 4. Duong, T. and Rizzo, J., Cryptography in the web: The case of cryptographic design flaws in asp. net, Security and Privacy (SP), 2011 IEEE Symposium on. IEEE, 2011.
- 5. Devi, T.R., Importance of cryptography in network security, Communication Systems and Network Technologies (CSNT), 2013 International Conference on. IEEE, 2013.
- 6. Ma, J. et al., SHAvisual: A secure hash algorithm visualization tool, Proceedings of the 2014 conference on Innovation and technology in computer science education, ACM, 2014.
- 7. Nilesh, D. and Nagle, M., The new cryptography algorithm with high throughput, Computer Communication and Informatics (ICCCI), 2014 International Conference on. IEEE, 2014.
- 8. Sabitha, S., User authentication using visual cryptography, Control Communication and Computing India (ICCC), 2015 International Conference on. IEEE, 2015.
- 9. Li, C. et al., Vigvisual: A visualization tool for the vigenere cipher, Proceedings of the 2015 ACM Conference on Innovation and Technology in Computer Science Education, ACM, 2015.
- 10. Singh, L. and Johari, R., CLCT: Cross Language Cipher Technique, International Symposium on Security in Computing and Communication, Springer International Publishing, pp. 217–227, 2015.
- 11. Singh, L.D. and Singh, K.M., Implementation of text encryption using elliptic curve cryptography. Procedia Comput. Sci., Jan 1, 54, 73–82, 2015.
- 12. Gupta, A., Semwal, S., Johari, R., METHS: Mapping from English Language to Hindi Language for Secure Commercial Transactions, IEEE International Conference on Computing Communication and Automation 2.
- 13. Kumar, M.G.V. and Ragupathy, U.S., A Survey on current key issues and status in cryptography, Wireless Communications, Signal Processing and Networking (WiSPNET), International Conference on IEEE, 2016.
- 14. Pandey, A. and Som, S., Applications and usage of visual cryptography: A review, Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO), 2016 5th International Conference on. IEEE, 2016.
- 15. Bhardwaj, A. and Som, S., Study of different cryptographic technique and challenges in future, Innovation and Challenges in Cyber Security (ICICCS-INBUSH), 2016 International Conference on IEEE, 2016.
- 16. Elhoseny, M., Yuan, X., El-Minir, H.K., Riad, A.M., An energy efficient encryption method for secure dynamic WSN. Secur. Commun. Netw., Sep 10, 9, 13, 2024–31, 2016.
- 17. Singh, L. and Johari, R., CLCT: Cross Language Cipher Technique, International Symposium on Security in Computing and Communication, Springer International Publishing, pp. 217–227, 2015.
- 18. Jain, I., Johari, R., Ujjwal, R.L., CAVEAT: Credit Card Vulnerability Exhibition and Authentication Tool, Second International Symposium on Security in Computing and Communications (SSCC“14), Springer, pp. 391–399, 2014.
- 19. Johari, R., Bhatia, H., Singh, S., Chauhan, M., Triplicative Cipher Technique. Procedia Comput. Sci., 78, 217–223, 2016.
- 20. https://timesofindia.indiatimes.com/
- 21. https://www.thehindu.com/
- 22. https://www.ndtv.com/
- 23. https://www.indiatoday.in/
- 24. https://www.deccanchronicle.com/
- 25. https://indianexpress.com/
- 26. https://www.financialexpress.com/
- 27. https://soundcloud.com/
- 28. https://www.youtube.com/
- 29. https://www.soundclick.com/
- 30. https://audiomack.com/
- 31. https://www.jamendo.com/
- 32. https://music.amazon.com/
- 33. https://cctrax.com/
- 34. https://archive.org/details/movies
- 35. http://retrovision.tv/
- 36. https://channelstore.roku.com/browse/movies-and-tv
- 37. https://www.sonycrackle.com/
- 38. https://pluto.tv/
- 39. https://www.popcornflix.com/
- 40. https://www.hulu.com/
- 41. https://www.miniclip.com/games/en/
- 42. https://armorgames.com/
- 43. https://www.kongregate.com/
- 44. https://www.newgrounds.com/
- 45. https://store.steampowered.com/
- 46. http://www.nitrome.com/
- 47. http://www.addictinggames.com/
Notes
- * Corresponding author: [email protected]
- † Corresponding author: [email protected]
- ‡ Corresponding author: [email protected]
