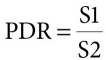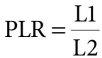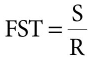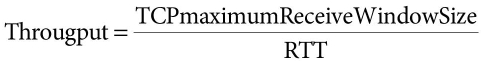13
Use of Machine Learning in Design of Security Protocols
M. Sundaresan1* and D. Boopathy2†
1 Department of Information Technology, Bharathiar University, Coimbatore, Tamilnadu, India
2 Department of Information Technology, Bharathiar University, Coimbatore, Tamilnadu, India
Abstract
Machine learning is an application of artificial intelligence that provides systems with the capacity to learn automatically and improve them from previously acquired experience without being explicitly programmed. Network security protocol is a type of network-related protocol that ensures the protection and integrity of data while transmission over a network connection. Network security protocols describe the processes and methodology to protect the network data from any unlawful attempt to evaluate or extract the contents of data. The growth of network communications creates the cloud services as major breakthrough to change the resource utilization and it provides all types of services to the end users. The security breaches and data-security-related threats are together creating a major issue in cloud services. The user’s data are targeted as prey by the offenders and the active attacks or passive attacks were initialized to analyze the weakness in the cloud services. The identified weakness will be used as a loophole by attackers to execute their attacks on the cloud service. Moreover, the cloud services are designed to maintain and provide the data security to their users. In particular, most of cloud concerns are depending on the third party service providers to protect them from the data security related threats. These types of dependency need to be eradicated, and in addition, the cloud concerns need to be designed and thus create the cloud services with self-defending protocols against different attacks. The JOKER (Joint and Offensive Kinetic Execution Resolver) technique is a self-defending security methodology, and it can avoid the attacks and be able to protect the data by itself from passive attacks and data security related threats.
Keywords: Self-defending protocol, security protocol, data protection, privacy, active attacks, passive attacks
13.1 Introduction
The system invaders and security hackers generally concentrate on the user’s data. Data is the key point which contains general and confidential information of users. Hence the data will meet different attacks on three states, and they are data at transmission, data at process, and data at rest [1]. Based on the states of data, the offenders will choose different attack types, and they are – active attacks and passive attacks [2]. Figure 13.1 illustrates the active attack, and passive attack is illustrated in Figure 13.2. The active attack is used to change the system resources, make some modification on data, cause damage to the user’s system, and create threat to integrity and availability [2]. The passive attack is used to utilize the information from the system, and provide threat to confidentiality [2]. The most important need for avoiding the active attack is detection of the attacks earlier and for avoiding the user from passive attack is preventing that user’s data. From the awareness point of view, it must be noted that with reference to the active attack the victim can get informed about the attack, but in passive attack the victim is not at all aware of the attack.
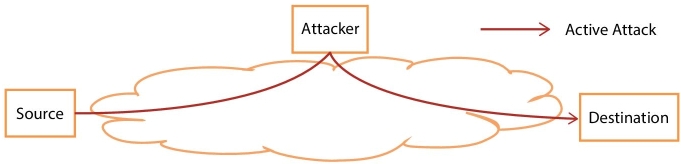
Figure 13.1 Active attack.
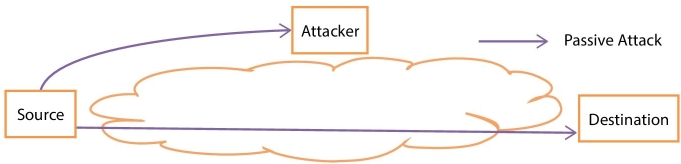
Figure 13.2 Passive attack.
The data security has three key points, and they are as follows: Confidentiality, Integrity, and Availability (i.e., CIA) [3]; and they can be broken by using both active and passive attacks. It shows that the data in transmission from source to destination are at risk, and further the data retrieval from cloud storage and processing the retrieved data in cloud applications are also at risk, and finally data at storage, i.e., at rest, are under risk too. The growth of digital industry makes the users by default to depend on the cloud storage for many services; in those services the cloud related data storage is obligatory. The cloud storage provides the data access at “on-demand method” and easy usage of data by different online processes when required. By default, each and every technology has its negative part too, in the cloud data storage the negative part is—data related attacks and related threats. The present scenario shows that the users cannot avoid the cloud data storage but they need to protect their data from unauthorized persons and its related threats. These things must be taken care of by the cloud service providers, but up-to now they are trying hard to safeguard the user’s data from security related threats. But apart from the common users, last year (2017) some companies including Deep Root Analysis, UK National Health Services, Verizon Communications, Yahoo, Uber, TIO Networks faced the security breaches, and data thefts [4].
In practice, the data are stored in public resource or private resource and made them available for usage by connecting that resource into the internet, and then the connected resources will surely meet the data related threats. The defenders need to enrich the defense methods rapidly to defend the attacks and prevent the data to be available from unauthorized persons. The above discussed contents from different perspectives are taken into consideration and are applied to design the JOKER Self-defending Protocol.
The Figure 13.3 illustrates the Secured Cloud Data Storage Prototype Model (SCDSPM) [5–8] which was already designed and tested to create the secured cloud storage environment. The results which were obtained from that SCDSPM achieved the objectives of the design. But SCDSPM was designed for storage of data in safer manner and also to avoid the user’s files from data mishandling-related problems. In this chapter, the JOKER protocol is concentrating on transferring of data to the destination securely without being affected by any one of the passive attacks (i.e., tapping attack).
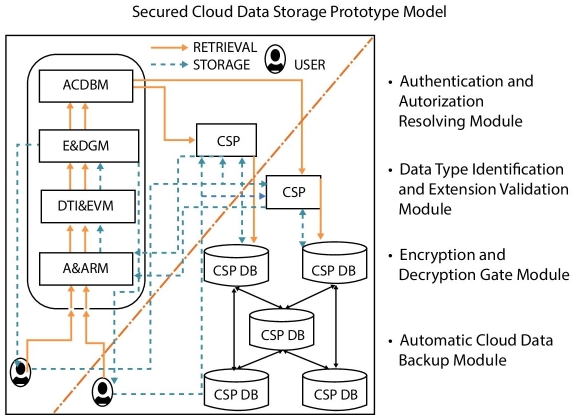
Figure 13.3 Secured cloud data storage prototype model (SCDSPM).
The security protocol is used to analyze, prevent, and defend the security threats. The cyber war is already going on between countries and some incidents happening around the world provide evidence for it. Those cyber attacks were done at destination successfully from the located source somewhere. Nowadays systems and gadgets are connected to the internet and those things are treated as our third eye. That third eye is always keeping us on surveillance and tracks all our activities through internet. This information shows that most of the gadgets are getting vulnerable and making us a prey to the hackers. Sometimes the attack may target shutting down resources or taking the information away from systems.
In this technological era, the weapon of the enemy will be either cyber terrorism or cyber warfare. Some years ago, one of the top 10 countries made a cyber attack on a south Asian country’s nuclear plant. Whether the system resources were connected to the internet or not, the attack will reach the target system in any mode like malware, man-in-middle attack, and infected hardware. The government and industries are learning some lessons from each and every cyber attack experienced in the past.
The security protocols are basically core—designed at the introduction of internet—related security issues. Later, some modifications and improvements took place on the existing security protocols and were made available for public use. The international standards, country jurisdictions, government regulations, and standards are prepared to confirm the users’ safety in communications. The attacks can be either active or passive attacks. In active attacks the system resources can be altered and will affect the specific operation. The passive attacks are done to learn something or make the use of information from the target systems without affecting the system resources.
The security protocols, which are used in communication sector, need to be redesigned to defend the upcoming attacks. The worms, viruses, security breaches and security attacks are then changing attacking strategies every new and then, and moreover, the existing defense methods are not able to figure out those attacks and made the resources a prey. So the new type of security protocol is in need and that too one which concentrates on the machine learning. Once the security protocol is designed with machine learning, then it can get the capability of defending the upcoming attacks automatically. This kind of security protocol can be adapted by any kind of online applications, which need security from the future attacks.
Machine learning concept is taken into consideration in the JOKER protocol. The machine learning is defined as “Machine learning is an application of artificial intelligence (AI) that provides systems the ability to automatically learn and improve from experience without being explicitly programmed. Machine learning focuses on the development of computer programs that can access data and use it learn for themselves. [9]”
The security protocol is defined as “Network security protocols are a type network protocol that ensures the security and integrity of data in transit over a network connection. Network security protocols define the processes and methodology to secure network data from any illegitimate attempt to review or extract the contents of data”. [10]
Section 13.2 reviews the related works concerning the existing self-defending security protocol methods and its related works. Section 13.3 deliberates the JOKER protocol; JOKER protocol’s working methodology, JOKER protocol’s procedure, and JOKER protocol’s Pseudo code. Section 13.4 analyses the simulation of experimental results, features of the JOKER protocol and the comparison of the JOKER protocol. Section 13.5 presents the conclusion derived from the findings, and the advantages of the JOKER protocol, and finally its related future enhancements.
13.2 Review of Related Literature
Sung-Ju et al. proposed an on-demand routing scheme identified as “Split Multipath Routing” that creates and uses various paths of maximally disjoint paths. Route recovery process and control message overhead will be minimized by the provision of the multiple routes. The proposed protocol uses a per-packet allocation method to allocate data packets into various routes of active sessions. This traffic distribution efficiently utilizes available network resources and prevents nodes of the route from being congested in heavily loaded traffic situations [11].
Rob et al. proposed a formal model for a fragmentation and a reassembly protocol running on top of the consistent Controller Area Network bus, which is broadly used in automotive and aerospace applications. Even though, the Controller Area Network bus comes with an in-built mechanism for prioritization, the authors argue that this is not sufficient and so want to provide another protocol to overcome the shortcoming [12].
Yan et al. introduced a new R-tree node-splitting algorithm. R-tree is widely used in geographical information systems, Computer Aided Design systems, and spatial databases. Linear node-splitting algorithm could construct an R-tree fast and efficiently, by partitioning the minimum bounding rectangle of the node. Then the authors found that this node-splitting algorithm would generate uneven nodes. After that they also developed an algorithm to balance those uneven splitting results to meet the demands of the R-tree definition. Finally they improved the node-splitting algorithm by considering the siblings of the splitting node [13].
Kiran et al. designed a Multi-radio Hybrid node that performs traffic splitting over a Multi-Hop Ad-hoc wireless network. The multi radio nodes have a WiMAX and a WiFi Radio that are used in transmitting data traffic over two different radio channels. In this proposed work the mobility aspect of the network was considered. The implementation was executed by using the AODV Routing protocol and the Bee Hive Routing algorithm on these nodes, which compared the Throughput and End-to-End delay for data transmission in the network [14].
Jatinder et al. explained how we can detect passive attack and then detailed on how to develop prevention from passive attacks. The detection of passive attacks was done by using the concept of key loggers and the registry files concept. Here preventive methods from passive attacks used the concept of virtual keyboards and the Network Access Control concept during online transmission of data. The authors explained the network security and unethical hacking. The major benefit of combining these concepts is that it helps to check the behavior of the network whether it is secure or not secure during data transmission from source to destination [15].
Katharina et al. proposed and presented an analysis of mixing strategies as a counter measure to trace analysis attacks in Tor [16].
Fan et al. proposed a traffic reshaping technique to thwart traffic analysis. The proposed technique creates multiple virtual Media Access Control interfaces over a single wireless card, and then it dynamically schedules the data packets over these interfaces, thereby reshaping the packet features on each virtual interface. The features of original traffic are obscured and unavailable for the adversary to infer the users’ online activities. The proposed technique evaluates the performance of traffic reshaping through trace-based experiments. The acquired results showed that the traffic reshaping was effective and efficient in defending against the traffic analysis related attacks [17].
Xinwen et al. suggested statistical pattern recognition as a primary technology to evaluate the effectiveness of active traffic analysis attacks and the equivalent counter measures. The evaluation shows that the sample entropy of ping packets’ round trip time is an effective feature of statistics to discover the payload traffic rate. Also the Xinwen and others proposed the simple counter measures that can significantly reduce the effectiveness of ping-based active traffic analysis attacks. The experiments discussed here validate the effectiveness of the proposed scheme, which can be used in other scenarios too [18].
13.3 Joint and Offensive Kinetic Execution Resolver
The data in cloud storage needs protection with minimum of three layers. The First layer is encryption layer where the data need to be encrypted with the international encryption standards along with the user’s country level data regulations. The Second layer is authorization layer where the persons who are authorized to use the data must be defined in this layer and moreover, their identity needs to be verified within this layer. The third layer is data authentication layer, from where the data are getting authenticated and the data-transferred destination must be verified, whether the data transmission to the destination is legally permitted by the country’s regulations or not. These things must be covered in the data protection. Figure 13.4 illustrates the data covered with all the three layers.
Communication between two nodes will transfer the data from source to destination and this transmission needs to be taken care of by cloud service provider. The literature study defined some issues related to the network attacks and its measures to solve the problems. But in reality the growth of information industry creates a chance to make the existing data handling and transmission methods vulnerable.
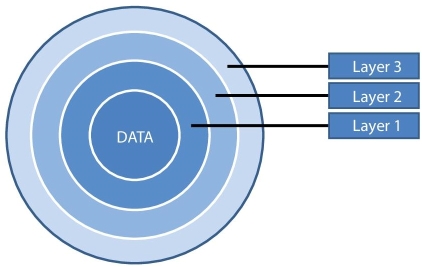
Figure 13.4 Data protected with the three layers.
The JOKER protocol includes finding the availability of nodes, creating the different routes to reach the destination, finding the shortest path routes among the created routes to transfer the data in different routes, encrypting the data, splitting the encrypted data into packets, and jumbling the data packets. Finally it will send the jumbled data packets to the destination. The JOKER protocol is illustrated in Figure 13.3 as design methodology and its related working model as illustrated in Figure 13.4 and the JOKER protocol process are defined in procedure and pseudo code sections. The JOKER protocol is able to self-defend itself by using the non-uniform packets transmission. By default most of the users are linked with more than one application at-a-time. While transferring the data packets under the JOKER protocol, all other applications packet transmissions also take place simultaneously between the user’s ends to different service provider’s end. So, it is difficult to figure out what other routes are used to transfer the data packets, and also it is unpredictable whether in passive attack all the data were captured by attackers from user end, then merging of those captured packets are not possible because of split and jumble process. The total number of data packets is not predictable by attackers and moreover, to complete the non-complete data packets into complete data packets is also impossible.
For example, the data are divided into 50 data packets and those data packets are transferred to the destination through different routes. An attacker captures one route’s data packets and tries to know the information from that captured data packets is not possible, because it is only a part of the transferred data packets. Even if all the data packets were captured by attacker, then merging the data packets into the correct data packets is again not at all possible. The “self-defend” is defined here as “not to provide the information to the attacker even though all the data packets were captured by the attacker”. It must be remembered that the passive attack will affect the confidential nature of the user data and as a result, the cloud service users will lose their trust on their cloud service providers. While designing this JOKER protocol, the SCDSPM model was kept under consideration. The SCDSPM was designed to create and maintain the security to the user’s data in cloud storage; however, it is unavoidable that the data might be captured during the time of transmission. To overcome the data capturing at the time of data transmission will be partly avoidable by this JOKER protocol. In fact the JOKER protocol will add more efficiency to the SCDSPM.
13.3.1 Design of JOKER Protocol
The Joker method has been explained in the following diagrams. The diagram illustrates both the Source to destination and destination to source flow.
Figure 13.5 shows the design of the JOKER protocol, Figure 13.6 to Figure 13.8 explain the step by step working model of single source to single destination. Figure 13.9 illustrates the working methodology of more than one resources connected to one destination, Figure 13.10 illustrates the working methodology of one source connected to multiple destinations. Figure 13.11 illustrates the working methodology of multiple sources connected to two destinations; Figure 13.12 illustrates the working methodology of multiple sources connected to multiple destinations. The short forms shown in Figure 13.5 to Figure 13.12 are S = Source, D = Destination, and I = Intermediate.
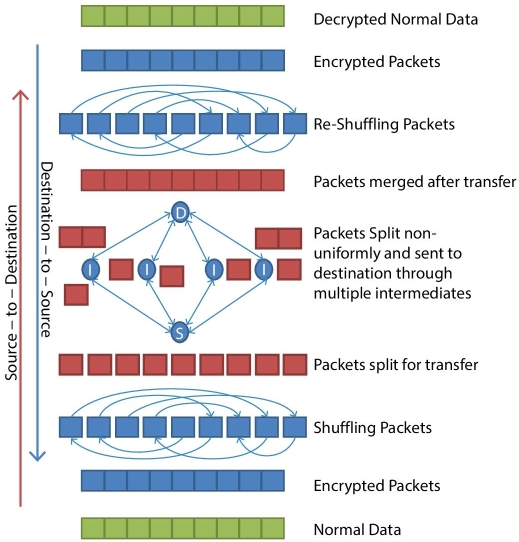
Figure 13.5 Design of the JOKER protocol.
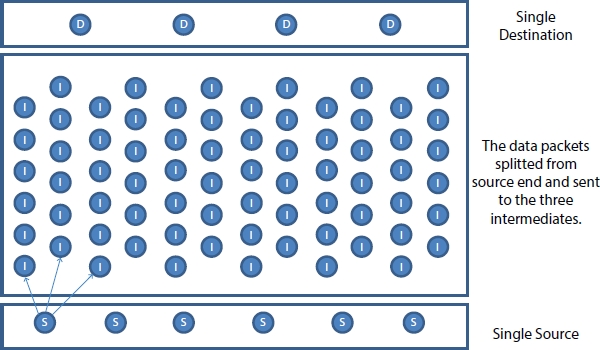
Figure 13.6 Design of the JOKER protocol—first step.
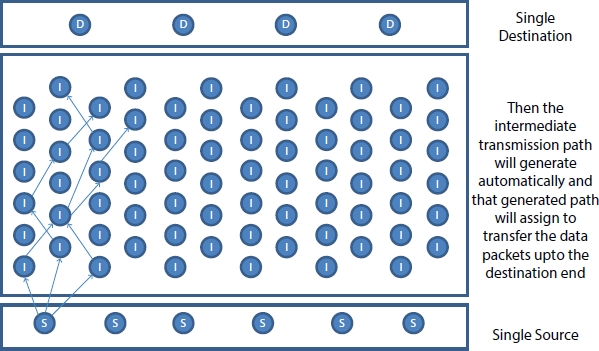
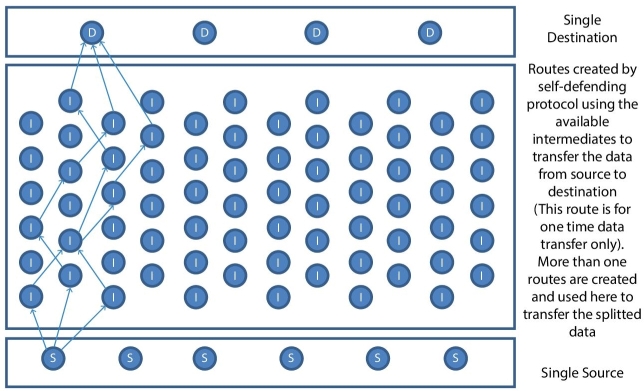
Figure 13.8 Design of the JOKER protocol—third step.
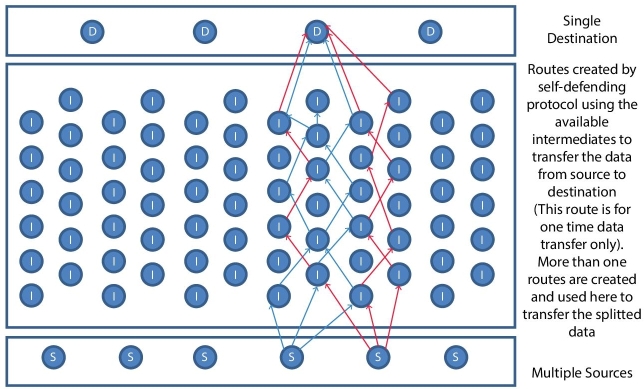
Figure 13.9 Design of the JOKER protocol—more than one sources.
The Node availability and Classification, Route Identification, Route Allocation, Re-Routing, while the data transmission from source to destination will be automatically taken cared by JOKER protocol. The Methodology and design show the possibility of JOKER protocol implementation.
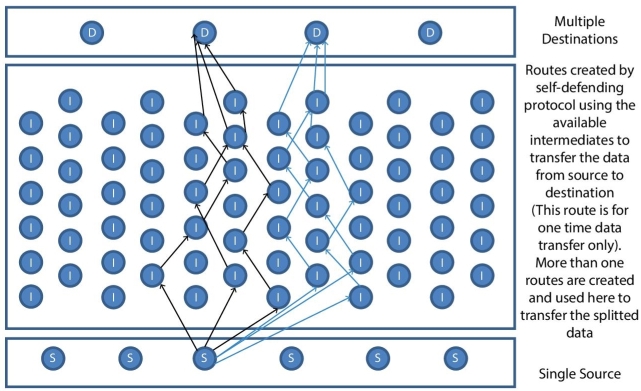
Figure 13.10 Design of the JOKER protocol—more than one destination.
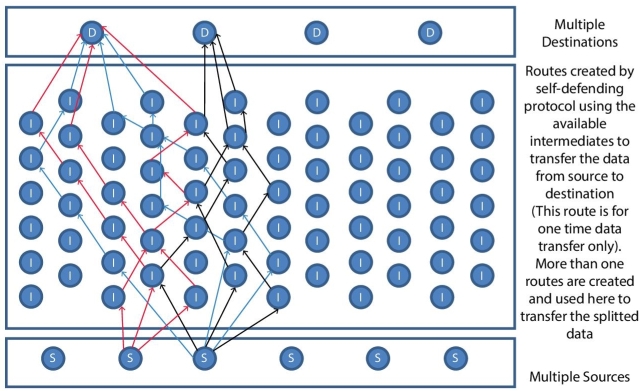
Figure 13.11 Design of the JOKER protocol—more than one sources and destinations.
13.3.2 Procedure
The procedure for the JOKER protocol:
- Step 01: Start the process
- Step 02: Select the data to transfer from source to destination
- Step 03: Analyze the selected data to apply the encryption process
- Step 04: Apply the encryption process when the analyzing process has finished
- Step 05: Analyze the encrypted data to split into packets
- Step 06: Split the packets and prepare those packets for jumbling process
- Step 07: Jumble the data packets and make them prepared to send in non-uniform method
- Step 08: Need to set the transferring path from source to destination through automatic path selection method
- Step 09: Send the jumbled data packets from source to destination through selected path
- Step 10: Once the data packets received at the destination end; merge those data packets
- Step 11: Re-jumble the data packets to get the actual data packets in-order
- Step 12: Analyze the re-jumbled data packets to verify whether the data are in order
- Step 13: Apply the Decryption process on to the received and analyzed data packets
- Step 14: Final output of Data received after the decryption process
- Step 15: Stop the process
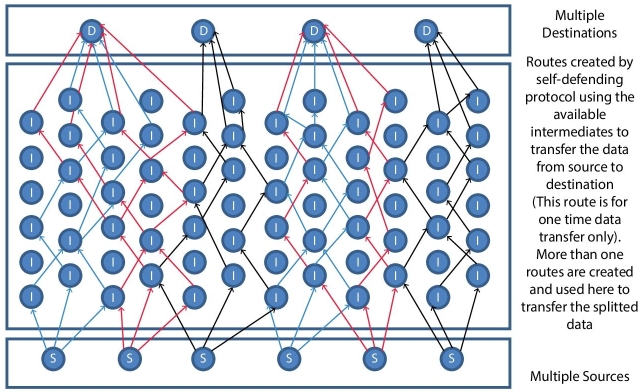
Figure 13.12 Data transmission method in JOKER protocol—all sources and all destinations.
The same process will take place while the data transfer from the destination to source end and the process will be started from STEP 01 of the procedure.
13.3.3 Procedure
The following pseudo codes explain the data transferring from source to destination. The pseudo code is explained as three types: preparing to send the data, set the transferring path to send the data, and process at the destination.
Preparing to send the data:
Select the data transfer to send
Analyze the selected data for encryption process
If
Selected data are appropriate for encryption process Then forward them to next step
Else
Intimate that selected data are not appropriate for encryption process
Apply the Encryption process on the analyzed data
Split the data into data packets
Apply the jumble process on those data packets
Make them ready to transfer
Set the transferring path to send the data:
Get the Source Details
Get the Destination Details
Analyze the intermediates availability
Fix the different Routes to reach the destination from available intermediates
Analyze and Select the Shortest route from the different routes
If
Destination is reachable by selected intermediates Then forward to next process
Else
Destination is not reachable again Analyze the shortest route from different routes
Verify the destination to send the packets
Send the split data packets with non-uniform manner through the selected route
Procedure at the Destination:
Merge the received split data packets from different intermediates Apply the Re-jumble process
Verify the re-jumbled process to confirm whether all the packets are received
Apply the decryption process which was applied for transmission process Store the decrypted data in storage
13.3.4 Simulation Details and Parameters
The Network Simulator 2 (NS2) was used to simulate the JOKER protocol. It is an open-source event-driven simulator designed specifically for research in computer communication networks [19].
13.3.4.1 Packet Delivering Ratio Calculation
The packet delivery ratio is used to measure the ratio of data packets received by the destinations to those which were generated and transferred by the sources.
Equation (13.1) shows the packet delivery ratio calculation formula. PDR = Packet Delivery Ratio, S1 = Number of packets received by the each destination, and S2 = Number of packets generated by the each source [20].
13.3.4.2 Packet Loss Ratio Calculation
The packet loss ratio is used to calculate the ratio of data packets loss during the data being transferred from the source to destination [21].
Equation (13.2) shows the packet loss ratio calculation formula. PLR = Packet Loss Ratio, L1 = Number of lost packets, and L2 = Number of sent packets.
13.3.4.3 Latency (Delay) Calculation
Latency is a measure of delay. In a network, latency measures the time it takes for some data to get to its destination across the network [22].
It is usually measured as a round trip delay—the time taken for information to get to its destination and back again [22].
Equation (13.3) shows the delay calculation formula where FST = Frame Serialization Time, S = Packet size (bits), and R = Transmission Rate Packet size (bits per second).
13.3.4.4 Throughput Calculation
The “throughput” in network refers to the average data rate of successful data or message delivery over a specific communications link.
Network throughput is measured in bits per second (bps) [23].
Equation (13.4) shows the throughput calculation formula where TCP = Transmission Control Protocol, RTT = Round Trip Time. This calculation considers only when transmission is done without packet loss.
13.4 Results and Discussion
The obtained testing results were verified to calculate the parameters which include Packet Delivering Ratio Calculation, Packet Loss Ratio Calculation, Latency (Delay) Calculation and Throughput Calculation to identify whether the JOKER protocol is able to achieve the data transmission from source to destination or not.
The JOKER protocol in this chapter is a combination of multiple techniques, which is combined to achieve the particular objective, i.e., to defend the passive attack in transmission of data.
The results of the JOKER protocol were analyzed with these parameters to verify whether this technique achieves its objective or not.
The JOKER protocol is designed to add more security to the SCDSPM, so the results of this JOKER protocol were partly compared with the parameters of existing models.
The number of packets generated and sent by the source to the destination was received as it is, i.e., Packet Delivery Ration is achieved 100%. While the users were transferring the data from source to destination, the packet loss did not occur, i.e., Packet Loss Ratio is 0%. The comparison of latency calculation of the JOKER protocol with existing TCP method is shown in Table 13.1 and Figure 13.13.
Table 13.1 Latency parameter details.
| Parameters File Size | Latency (in s) | |
| Existing | JOKER | |
| 1 MB | 08 | 09 |
| 3 MB | 25 | 24 |
| 6 MB | 51 | 48 |
| 10 MB | 95 | 89 |
| 20 MB | 182 | 171 |
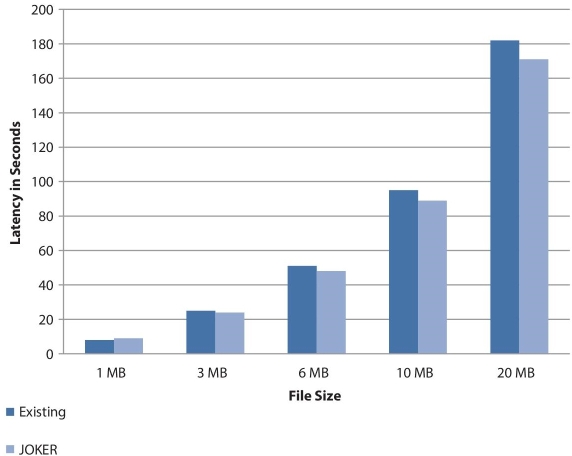
Figure 13.13 Latency parameter analysis.
The comparison of throughput of the JOKER protocol with existing TCP method is shown in Table 13.2 and Figure 13.14. The comparison shows that the JOKER protocol is better in latency and throughput parameters than the already existing method.
The JOKER protocol tries to transmit the data from source to the destination without giving a chance for the tapping attack which is considered as one of the passive attacks.
Table 13.2 Throughput parameter details.
| Parameters Number of Nodes | Throughput (Kbit/s) | |
| Existing | JOKER | |
| 10 Nodes | 8192 | 8100 |
| 15 Nodes | 12288 | 12589 |
| 20 Nodes | 16384 | 16852 |
| 30 Nodes | 32485 | 32245 |
| 50 Nodes | 48758 | 48587 |
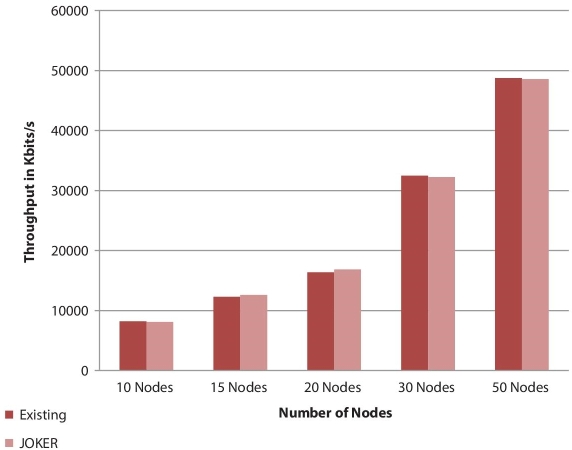
Figure 13.14 Throughput parameter analysis.
13.5 Conclusion and Future Scope
The tapping is one of the passive attacks which are not known by the victims. The confidential nature of the user’s data becomes questionable under this attack. The main purpose of this attack is to surveillance the user’s data without their knowledge and also to collect their information to know about their activities. This is also affecting the user’s privacy in online. The JOKER protocol is one of the ways to split and send the data to the destination through multiple intermediates. Those available intermediate nodes are not permanent. This technique will use different routes at each and every time, when the user tries to send the data from the source to the destination. The JOKER protocol was simulated and the results turned out in positive manner.
The JOKER protocol has some limitations and, they are the JOKER protocol was simulated by using the simulator and results were compared with existing, based on simulator scenario results. While implementing the JOKER protocol into the real time scenario, that time the result may vary while comparing to existing methods. But whatever it may be, the JOKER protocol is using machine learning technique to select and send the data packets from the source to the destination. The Machine learning concepts and their methodologies were not fully discussed in this chapter, because the research of this JOKER protocol is still under enrichment to provide the better performance than its own results, i.e., which results were produced and acquired from the simulator work by using the JOKER protocol. In future this JOKER protocol will be extended to test in the real time scenario and then based on the results and refinements, the JOKER protocol will come to real time usage.
References
- 1. https://www.ed.ac.uk/arts-humanities-soc-sci/about-us/information-security-and-governance/what-information-do-i-have-to-protect/the-three-states-of-information. Accessed on 01/08/2018.
- 2. https://techdifferences.com/difference-between-active-and-passive-attacks.html. Accessed on 01/08/2018.
- 3. https://developer.mozilla.org/en-US/docs/Web/Security/Information_Security_Basics/Confidentiality,_Integrity,_and_Availability. Accessed on 01/08/2018.
- 4. https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/year-in-review-notable-data-breaches-for-2017. Accessed on 01/08/2018.
- 5. Boopathy, D. and Sundaresan, M., Securing Public Data Storage in Cloud Environment. ICT and Critical Infrastructure: 48th Annual Convention of Computer Society of India, Visakhapatnam, India, December 2013, pp. 555–562.
- 6. Boopathy, D. and Sundaresan, M., Secured Cloud Data Storage—Prototype Trust Model for Public Cloud Storage. International Conference on Information and Communication Technology for Sustainable Development, Ahmadabad, India, July 2015, pp. 329–337.
- 7. Boopathy, D. and Sundaresan, M., A Framework for User Authentication and Authorization using Request based One Time Passkey and User Active Session Identification. Int. J. Comput. Appl., 172, 10, 18–23, August 2017.
- 8. Boopathy, D. and Sundaresan, M., IDOCA and ODOCA – Enhanced Technique for Secured Cloud Data Storage. Int. J. Intell. Eng. Syst., 10, 06, 49–59, December 2017.
- 9. https://www.expertsystem.com/machine-learning-definition/. Access on 22/09/2018.
- 10. https://www.techopedia.com/definition/29036/network-security-protocols. Access on 22/09/18.
- 11. Lee, S.-J. and Gerla, M., Split Multipath Routing with Maximally Disjoint Paths in Ad hoc Networks. IEEE International Conference on Communications, Finland, 2001.
- 12. van Glabbeek, R. and Hofner, P., Split, Send, Reassemble: A Formal Specification of a CAN Bus Protocol Stack. Models for Formal Analysis of Real Systems (MARS 2017), EPTCS 244, June 2017, pp. 14–52.
- 13. Liu, Y., Fang, J., Han, C., A New R-tree Node Splitting Algorithm Using MBR Partition Policy. 17th International Conference on Geoinformatics, USA, 2009.
- 14. Kiran, K., Shivapriya, T., Singh, A.A., DeepaShenoy, P., Venugopal, K.R., Patnaik, L.M., Traffic Splitting in a Mobile Ad-hoc Multi-radio Network. 2013 Annual IEEE India Conference (INDICON), Mumbai, 2013.
- 15. Teji, J., Chuchra, R., Mahajan, S., Gill, M.K., Dandi, M., Detection and Prevention of Passive Attacks in Network Security. Int. J. Eng. Sci. Innov. Technol., 02, 06, 247–250, 2013.
- 16. Kohls, K. and Pöpper, C., Traffic Analysis Attacks in Anonymity Networks. ASIA CCS 2017, Abu Dhabi, pp. 01–03, 2017.
- 17. Zhang, F., He, W., Liu, X., Defending Against Traffic Analysis in Wireless Networks Through Traffic Reshaping. 31st International Conference on Distributed Computing Systems, USA, pp. 593–602, 2011..
- 18. Fu, X., Graham, B., Bettati, R., Zhao, W., Active Traffic Analysis Attacks and Countermeasures. Proceedings of the 2003 International Conference on Computer Networks and Mobile Computing, China, pp. 1–9, 2003.
- 19. https://www.isi.edu/nsnam/ns/. Accessed on 01/08/2018.
- 20. https://www.igi-global.com/dictionary/packet-delivery-ratio/21749. Accessed on 01/08/2018.
- 21. https://en.wikipedia.org/wiki/Packet_loss. Accessed on 01/08/2018.
- 22. https://www.sas.co.uk/blog/what-is-network-latency-how-do-you-use-alatency-calculator-to-calculate-throughput. Accessed on 01/08/2018.
- 23. https://en.wikipedia.org/wiki/Throughput. Accessed on 01/08/2018.
Notes
- * Corresponding author: [email protected]
- † Corresponding author: [email protected]