12
Security Protocols for Mobile Communications
Divya Priyadharshini M.1*, Divya R.1, Ponmurugan P.1 and Balamurugan S.2
1 Department of Electrical and Electronics Engineering, Sri Krishna College of Technology, Kovaipudur, Coimbatore, India
2 Department of Research and Development, Quantis IS and CS Technologies, Coimbatore, India
Abstract
Internet of Things is the bread and butter for the future wireless network communications. The advancement in these technologies is also demanding advanced security. The chapter begins with the introduction to communication networks and importance of the security of network. It has also summarized the various available mobile communication technologies, the threats faced by them and the measures undertaken for avoiding those threats. In the proposed method section an approach for integrating LoRaWAN and 5G has been discussed with security challenges faced by the system. By integrating the systems low power, low latency and higher efficient system is achieved. RFID along with PLS is used to address the security issues discussed along with result and performance measures. Further the chapter concludes by summarizing the proposed method and its analysis.
Privacy and data confidentiality will be a severe problem in 5G networks PLS provides data security, asymmetric cryptographic algorithm provides location security. In the proposed system a LoRa connected 5G system, RFID authentication along with PLS is used, which will address most of the 5G security problems. By this, eavesdropping, jamming and data piracy are avoided by using PLS and by using RFID for authentication security issues are avoided.
Keywords: Mobile communications, security protocols, 5G network, Lora security, security threats, wireless communications, 5G security, network security
12.1 Introduction
In affluent communication devices connected environment, a secure communication and key exchange are indispensable security issues. Mobile communications has poor user interface, limited processing capability, and complex network protocol. Also the security is laborious and demanding than other communication systems [1]. To design a successful mobile communication device, mobile applications and operating conditions plays integral roles, since some hardware aspects make the security design hard. The arena of mechanisms has the following eight players, such as:
- Authentication management
- Identity and confidentiality management
- Protection of the privacy of users
- Security between the terminals and the network
- Security on network interfaces
- Security visibility and configurability
- Cryptographic algorithms
- Protection against DoS attacks [2].
Mobile communication security is defined in terms of confidentiality, authentication, integrity, and non-repudiation of the data which is transmitted. These demands are fulfilled using various cryptographic techniques which are strong and cannot be easily breached; but they may cause complications while designing [3]. Data confidentiality is ensured by end-to-end encryption between the two communicating parties. The mechanism used for encryption depends upon the technology in which it is used. Data authentication is an asymmetric service and it depends on the security protocol used. The solutions for authentication and data privacy can be achieved by running additional protocols at the data link layer. User identification for sensitive applications has to run an additional protocol with server database. Like authentication non-repudiation is also asymmetric unlike the fact that the recipient will know the origin of the message. Example: Digital Signature [4].
Mobile communication security is difficult because of its complex architecture. It has been developing exponentially and is used by almost every sapiens on the planet earth. Network architecture depends on the communication protocol layer. It is an abstract way to represent the data communication model and implementation [5]. It has five layers namely physical, data link, network, transport, and application as shown in Figure 12.1.
The physical, data link, and network layers are node to node layers whereas the transport and application layers are end to end layers and a gateway between them. Authentication and non-repudiation can be implemented on application layer since they need end to end protection and confidentiality can be implemented in any of the layers. The security protocols which we have in use can be said metaphorically as infant steps toward a long journey [6]. The user should not be naive about the security concerns and the operations but at the same time the evidence provided should be intellect and intuitive. Security protocols are set of defined rules which concentrate on the security of the communication device. Mobile communication has reached its fifth generation of mobile devices, its security issues and protection techniques will be discussed later in this chapter.
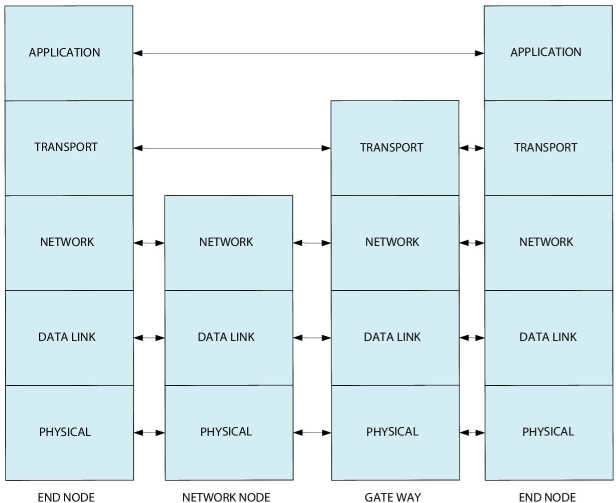
Figure 12.1 Communication protocol layers.
12.2 Evolution of Mobile Communications
Communication is an art which differentiates us from other beings in the planet. Mobile communication has grown drastically from the year 1987 when Guglielmo Marconi demonstrated his first radio communication [7]. Mobile communication evolution can be divided into three phases: pointer phase, commercial phase, and wireless communication. The pioneer phase includes the early experiments carried out from 1927 to 1947. The mobile communication came to reality during the Second World War. The commercial phase includes the commercialization of radio and television from 1946 to 1968.
The wireless era from 1947 is a remarkable growth phase in history of mankind which paved way for various developments in our society. The basic architecture of a mobile cellular phone was designed with the following principles: Low power transmitters, small coverage, reuse of frequency, increasing capability of computing by cell splitting, off hands and central control modes. The first commercial mobile was introduced in 1983 [8]. The first analog cellular systems were developed in Japan and Europe which faced severe downfall. Then the digital cellular systems came into existence with the advantages of advanced digital modulation techniques, low bit rate digital voice coding, reduction of overhead signals, robust control, less interference and improved efficiency. Examples are GSM, CSMA, and FDMA.
In addition to cellular communication other wireless communications were also developed which were application specific used in fire, police medical and emergency personnel circuit. The following are the other wireless communications developed [9]: Paging is a one way communication which mimic mobile communication it as first installed in 1956 in London hospital. The sender sends an alphanumeric message through a call center. Paging systems can be a private or public system [10]. Private Mobile Radio (PMR) is a fixe base station communication which uses both FM and AM. It operates in VHF and UHF bands [11]. Mobile satellite communications which was developed in early 1970s includes telephone and telex services [12].
Existing mobile communication systems, security challenges, and methods of protection are discussed briefly below:
Global System for Mobile Communications is commonly called as GSM which is a second generation mobile communication technology (2G). It is a massive commercial hit despite its weaknesses which includes weak cryptographic algorithms, meager protection against attacks and weak architecture [13]. These insufficient security issues led to new security goals such as confidential user identity, authentication, data concealment and signal information privacy. 2G uses circuit switched scheduling for transmission. The above said security issues can be overcome using authenticated key agreement (AKA) protocol with aid of Subscriber Identity Module (SIM) [14].
Universal Mobile Telecommunications System (UMTS) or the widely called 3G (third generation) systems have demanding data transfers. Here the security is provided with mutual authentications and enhanced encryption algorithms [15]. 3GSM has enhanced protection in the network layer but still faces attacks like denial of service (DoS) and capture of identity. To counterattack these problems integrity protection for critical signaling messages and temporary identity are used [16].
Long Term Evolution (LTE) also the fourth generation of mobile communication uses an IP-based packet-switched architecture and improved radio layer. It offers Voice and Small messaging services (SMS) as IP-based services rather network services [17]. Threats in 4G system includes physical threats, attacks on the privacy of the user, unauthorized access of IMS, lack of privacy and data loss, DoS, and DDoS. These many threats can be overcome by introducing industrial standards to provide physical safety, usage of IPS Intrusion Prevention System, usage of secured gateways, virtual private network and enhanced encrypting algorithms and anti-virus software [18].
GSM opened new mechanism for enhanced security for user anonymity and privacy, halting weaknesses in security was succeeded by altered network security in UMTS. UMTS can be characterized as malleable architecture for solving flaws in the security. It still had susceptibility which was overcome by LTE [19]. LTE responded by using well-founded cryptographic algorithms, security in its embedded architecture which was IP based and mutual authentication mechanisms. It was laid bare to new issues like spamming, espionage, malware distribution, IP spoofing, data and services theft, Distributed Denial of Service (DDoS), etc. [20].
12.3 Global System for Mobiles (GSM)
The GSM idea was formed in 1982 and it was implemented in the year 1991 in Europe. The architecture of GSM comprises of three subsystems namely Mobile station (MS), Base Station Subsystem (BSS), and Network Subsystem (NSS). Mobile Station (MS) will have the mobile phone (ME) and the SIM (Subscriber Identity Module) which stores the IMSI (International Mobile Subscriber Identity Module) and the secret Key that is used in the authentication processes [21]. Figure 12.2 shows the components in a GSM architecture and they are:
- Base Station Controller (BSC)
- Base Station (BS)
- Mobile services Switching Center (MSC)
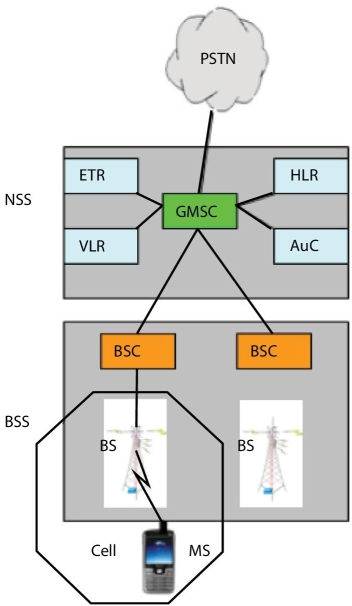
Figure 12.2 Components of GSM.
- Core Network (CN)
- Visitor Location Register (VLR)
- Public Switched Telephone Network (PSTN)
- Equipment Identity Register (EIR) [22]
The remarkable innovation in GSM is the SIM and the secret key (Ki) associated [23]. It has a step by step process in authentication and as show in Figure 12.3.
Step 1: Network sends 128 bit random (RAND) challenge to the ME
Step 2: Algorithm A3 (The MS Authentication Algorithm) for the secret key (Ki) to respond, SRES
Step 3: If SRES matches then it proceeds to the next step
Step 4: Algorithm A8 (The Ciphering Key Generation Algorithm) to challenge session key (Kc)
Step 5: Algorithm A5 (The Stream-Ciphering Algorithm) sends encrypted data to BS
Vulnerabilities in GSM include Masquerading or ID Spoofing in which the attacker disguise as authorized personnel and accesses unauthorized resources, discloses unauthorized information and information flow, alters the resources and information without authorization, repudiation of actions, and DoS (denial-of-service) [24]. Some of the other vulnerabilities in GSM are:
- Use of false BS to interpret communication
- Encryption in only on the crust and so cipher keys and authentication are exposed
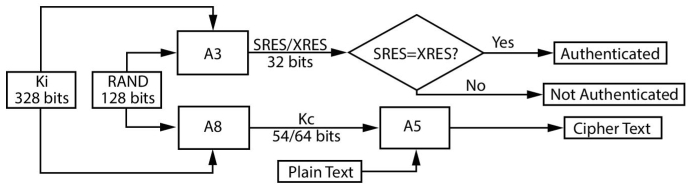
Figure 12.3 Flowchart of GSM operations.
- Data integrity is at stake
- Less flexible for security upgrade
- Lack of user visibility
12.4 Universal Mobile Telecommunications System (UMTS)
UMTS was first established in A USIM is used for the authentication processes. UMTS security systems have to be built on the existing 2G systems which have the following advantages: Identity confidentiality, network authentication, radio interference encryption, removable SIM with a hardware module security without assistance, SIM authentication by subscriber. The additional features of security in UMTS include a) Integrity Protection of Signaling Information b) Integrity Protection of Signaling Information c) Ciphering/Integrity Protection d) Trust and Confidence by Published Algorithms d) Authentication Failure Indication e) Enhanced UMTS Authentication and Key Agreement Mechanism f) USIM Control of Cipher/Integrity Key Usage. The following diagram Figure 12.4 explains the UMTS system Architecture [25].
Authentication and Key agreement (AKA) in UMTS consists of two phases in operation phase one is Generation of Authentication Vectors and the other phase is Authentication and Key Agreement. After receiving the request for data from the service network, the authentication center creates “n” number of authentication vectors namely [26]:
- RAND—A random number
- XRES—an expected response
- CK—A cipher key
- IK—an integrity key
- AUTN—an authentication token
For the security architecture of UMTS we need various 3G standard security algorithms. These security algorithms are used in the process of integrity protection and encryption of the message transmitted [27]. Thus preserving the security of the message transferred between the mobile and the RNC. KASUMI algorithm comprising of f8 algorithm for ciphering and f9 algorithm for the integrity protection is used. Ciphering algorithm is used for encryption and integrity is achieved by calculating the cryptographic checksums for the signaling messages.
In spite of the complex security and complex algorithms in 3G, security breaches happen in this system. Any security threat faced by the fixed host connected to the Internet is also faced by the 3G terminal. When a new user is registering for the first time a clear text is sent to the IMSI acknowledging the user. A false base station (BS) can be created and the user is out of reach from the SN thus an active attack is possible. The authentication key Authentication and Key Agreement (AKA) protocol is unidirectional. Calls connected to the network can be easily hijacked and the eavesdropper disables the encryption [28]. This intruder disguised attack is called man-in-the-middle attack. Thus the same attack can be replayed. Data integrity and user authentication are under stake due to weak encryption.
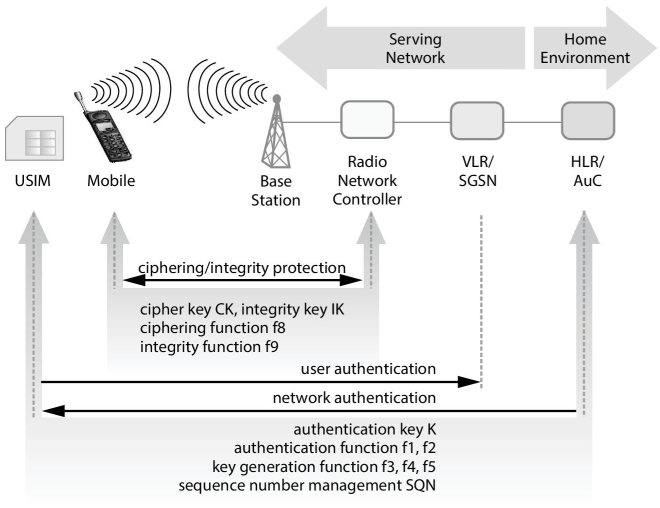
Figure 12.4 UMTS security architecture.
12.5 Long Term Evolution (LTE)
Overcoming the security drawbacks of the third generation the fourth generation LTE has better cryptographic algorithms than UTMS. The authentication is done by AKE (Authentication Key Exchange) Protocol which includes Key Establishment Protocols and Entity Authentication Protocols. Both symmetric and asymmetric protocols are used for the
encryption [29]. The symmetric algorithms have the same key whereas the asymmetric algorithms have different keys. Furthermore there are three more algorithms used in the process and they are: a) Key Generation Algorithm b) Encryption Algorithm c) Decryption Function. By these algorithms confidentiality for the data is preserved, which means the data is available only for the authorized personnel. Cryptographic algorithms are defined by two main properties security and non-malleability. Hash functions are also used in securing 4G systems, the properties include: collision resistance, pre-image resistance, 2nd-preimage resistance [30]. MAC (Message Authentication Codes) or keyed hash functions assure us with computational ease and creation of new MAC codes any input. By using MACs Integrity, Data Origin authentication and confidentiality of the message is preserved. Despite these many security algorithms to secure the messages sin the 4G communication systems, there are still possible threats to the systems. The following are some of the threats to 4G systems [31]:
- Eavesdropping: Listening to the message sent by unauthorized personnel is known as eavesdropping, which leads to various other severe threats to the system.
- Modification of messages: when messages are eavesdropped there are good chances of modification of messages sent.
- Replay: when the attacker has modified the message and injects it in the line at that moment or latter such attacks are replay. These attacks are overcome by preplay adversaries.
- Denial of Service: These attacks are those which prevent the authorized access when host is trying to communicate with many clients. DoS is of two types namely, resource depletion attacks and connection depletion attack. DoS cannot be completed avoided but the frequency attacks can be minimized [32].
- Typing attacks: these attacks replace the protocols of message form one field to the other field. MAC cryptographic action avoids these typing attacks.
- Cryptographic Attacks: These are simple encryption techniques based attacks to decipher the key. It is impossible to find such attacks and also a counter measure for the attack.
- Protocol Interaction: These attacks run a new protocol within a known protocols and malicious of long term keys are used.
- Hijacking and Spoofing: inserting affective packets in the line, substituting traffic, and breaching firewalls include hijacking and network snoop. These can be avoided by having strong authentication methods; Figure 12.5 shows the LTE security architecture [33].
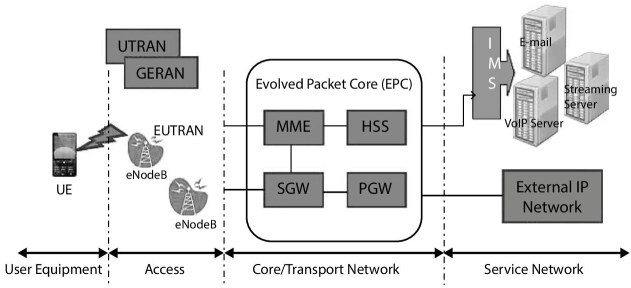
Figure 12.5 LTE security architecture.
Generally every attack and their possible solutions can be classified as:
- General architecture
- Threats
- Distributed network and open architecture
- Decentralized accountability for security
- Complex business models (IS/Service sharing)
- Minimizing security spend
- Solutions
- Interoperability standards
- Security audits with remediation commitments
- Strong partner agreement
- Security Budget
- Threats
- User equipment (UE)
- Threats
- Physical attacks
- Lack of security standards and controls on UEs
- Risk of data loss, privacy
- Application layer: virus, malware, phishing
- Solutions
- Subscriber education
- Industry security standards and controls on UE
- Antivirus
- Strong authentication, authorization, OS encryption
- Threats
- Access
- Threats
- Physical attacks
- Eavesdropping, Redirection, MitM attacks, DoS
- Rogue eNodeBs
- Privacy
- Solutions
- Physical security
- Network monitoring, IPS systems
- Authentication, authorization, encryption
- Security Architecture
- Threats
- Evolved Packet Core (EPC)/Transport and Service
- Threats
- Unauthorized access
- DoS and DDoS attacks
- Overbilling attacks (IP address hijacking, IP spoofing)
- Solutions
- Security Architecture: VPNs, VLANs
- Encryption, IKE/IPSec
- Network monitoring, management and load balancing
- Threats
- Service network
- Threats
- Security Architecture: VPNs, VLANs
- Encryption, IKE/IPSec
- Network monitoring, management and load balancing
- Solutions
- Security Architecture: VPNs, VLANs
- Encryption, IKE/IPSec
- Network monitoring, management and load balancing
- Threats
12.6 5G Wireless Systems
Fifth generation of communication systems are beyond 4G with the legacy of it and also added features of radio communications and Internet of Things. The advancements include: increased density of users of broadband, device to device communications and machine type communications. It has goals of lower errors is communication thus decreasing latency, low energy consumption and better communication with Internet of Things, increased bandwidth, increased number of connected devices, reliability,
coverage, increased battery life and reduction of energy usage. Figure 12.6 shows the architecture of 5G wireless communication systems [34].
The security requirements of 5G include [35]:
- It requires improved resiliency and availability against signal based threats
- Special design for decreased latency
- Compliance with exiting 3G and 4G networks
- Provides public safety and mission critical communications
- Robust and can withstand jamming attacks
- Improved security for small cell nodes
Like other systems here also authentication, confidentiality, integrity, and availability are the four main security goals to be achieved. There are mainly four attacks which interrupt services in the 5G communication network and they are [36]: eavesdropping, jamming, DoS and DDoS, MITM. Eavesdropping and traffic analysis are both passive attacks. Eavesdropping has an intruder in between the sender and the receiver and listens to the messages sent. Traffic analysis includes the information theft such as identity, location and communication parties. Due to sudden increase in technology improvement eavesdroppers have taken advantage of information theft. Jamming is disrupting the communication between the two users it may also prevent the users from using the radio communications [37]. Jamming is an active attack and resource allocation strategy is used between the jammer and the fusion center.
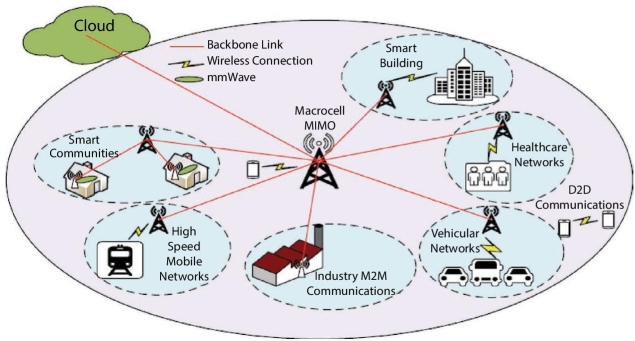
Figure 12.6 5G security architecture.
A DoS attack is an active attack which violates the availability of resources for the authorized user. Jamming techniques can be used for launching a DoS attack. DoS expand as Denial of Service attack. DoS and DDoS are potential threats for the service providers. DoS attack the physical components and the network infrastructure. Based on the attack it can be found whether the attack was for the device or for the network infrastructure. In a MITM attack the intruder takes control of the Communication channel between the users or the legitimate parties. Authentication between the mobile device and the base station can avoid the false base station attacks. It is active attack, which can be implemented on any layer [38]. It is a very common attack which forces the user to communicate with the false base station.
Many researches are still under progress for a stronger security mechanism, as discussed earlier any security mechanism developed should have entity authentication, message authentication, data confidentiality, privacy, availability, and integrity. Several technologies are used for the security mechanism like, HetNet, Network Functions Virtualization (NFV), massive MIMO, Software Defined Network (SDN), D2D, Software Defined Radio (SDR), Cloud Radio Access Network (C-RAN), and IoT [39]. These technologies are used for the extensive use for the spectrum flexibly, storage, computing, and technology access.
When authentication is considered 5G requires complex authentication methodologies since authentication among, service provider, user, and the mobile management entity. Cyclic redundancy check based authentication is suggested since authentication between the user device and the service provider is necessary because of the amount of information communicated regularly. It can be implemented as network only, service provider only or authentication by both the network and service provider only [40]. Confidentiality considers both the data confidentiality which protects from passive transmission attacks and the data privacy. Data encryption and cryptographic methods have been used for the data confidentiality. Anonymity of the user data is essential in 5G communication. Availability denotes the robustness of the system under attacks like DoS, jamming, or DDoS. Resource allocation is usually preferred for availability or a pseudorandom time allocation strategy is used. Integrity is when there is no confidence over the origin of the messages [41]. There will be no notification even if the message was change or modified. Message integrity can be achieved using authentication systems. Data communication is chosen over voice communication hen integrity attack are taking place. Power control, relays, artificial noise, signal processing are various methods used in the security of the more modern 5G communication systems.
12.7 LoRA
There are various wireless transmission systems like Bluetooth Low Energy (BLE), LoRaWAN, ZigBee, and Z-Wave based on energy level, coverage range, and usage. Low power wide area networks (LPWAN) are used in low power consumption based applications; LoRAWAN is an application of LPWAN [42]. We are just taking only infant step toward LoRA and researches under the progress for the security of LoRAWAN. AES is used in two step levels for the security of the data transmitted. One is between the device and the gateways, whereas the other is on the application level. Figure 12.7 shows the architecture of LoRA.
The advantages of LoRa include: a) increased batter life because of asynchronous nodes and communicates only when needed, b) high network capacity because of adaptive data rate and multi modem transceiver in the gateways, c) different device classes because of downlink communication latencies, d) security because of two layered security is achieved. Security is achieved in both network and the application layers. AES128 secret key is used for secret key exchange and authentication, these key changes every session for making communication more secure [43–45].
Threats for the LoRA are the same as in 5G system and the security measures are still under study. Various studies have proposed various security protocols and these protocols are validated every day.
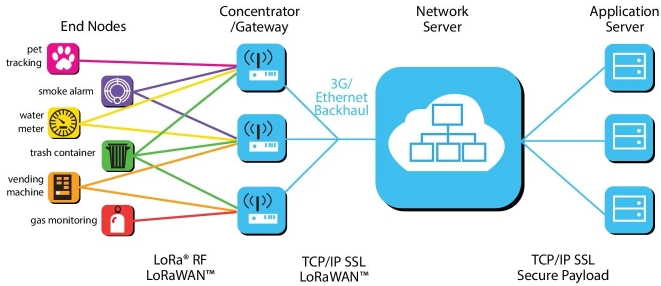
Figure 12.7 Architecture of LoRA.
12.8 5G Integrated With LoRA
LoRaWAN (Low Range Wide Area Network) is a low power network which can connect to billions of devices. With IoT (internet of Things) reaching its pinnacle, researches have begun in the integration of 5G (fifth generation of mobile communications) with LoRa [46]. By the integration of LoRa and 5G networks low power consumption and low latency can be achieved. 5G will have numerous sensors which are IoT and can handle affluent mobile devices at a single time. All the connected devices can be monitored and controlled in the cloud with IoT.
With myriad devices interconnected in a network having 5G and IoT under consideration security is a big issue. Threats and breach of 5G network added to the problems like viruses, wormholes which are faced in internet has to be addressed. 5G network faces threats like eavesdropping, jamming, Dos and DDoS, Man in the middle (MITM) attacks. LoRa also faces security issues like wormhole attack, replay attack and jamming. For authentication issues authentication and key agreement (AKA) protocol based entity authentication is implemented and for the message authentication cyclic redundancy check authentication is implemented [47]. Encryption avoids eavesdropping incase the eavesdropper is strong or multiple leaks cryptographic algorithm, physical layer security is used. Resource allocation strategy detects jamming in 5G networks. Privacy and data confidentiality will be a severe problem in 5G networks PLS provides data security, asymmetric cryptographic algorithm provides location security.
In the proposed system a LoRa connected 5G system, RFID authentication along with PLS is sued, which will address most of the 5G security problems. By this, eavesdropping, jamming, and data piracy are avoided by using PLS and by using RFID for authentication security issues in authentication are avoided. To integrate with LoRA the following four options are considered: via 3GPP access network, via non-3GPP untrusted access network, as a part of eNodeB, and virtually as a part of core network [48].
Features of implementing the integration of 5G with LoRA includes interface of communication and traffic, better security mechanism, instant resource management, quality of service, scalable, support in today’s available commercial products, and complexity of mechanism. This integration has enabled the user for cost efficient and energy efficient communication portal. The cloud stores all the collected data and transmission logs. The cloud has to be secure as well. Security threats include [49]:
Replay attacks: It is so commonly possible and can be achieved using any LoRA transceiver. Once the intruder gets hold of a user he can totally block the user for the network form constant replaying the message.
Eavesdropping: Crib dragging methods can be easily used to receiver or encrypt the message transmitted in the air. LoRA implements the channel confidentiality through AES in counter mode.
Bit Flipping Attack: A non-readable bit flipped message is used for the authentication as an integrity check. LoRA avoids the integrity check which in turn opens the gates for the attack.
ACK Spoofing: Where a captured message is delayed and it can be used in acknowledging selectively the receipt of an unrelated message successfully even it is not available in the backend.
Identification and connection of the messages are also considered as the vulnerabilities in the LoRA; hardware itself is simple and unprotected, which could be dangerous. The system is always at is weakness at its link [50].
12.9 Physical Layer Security and RFID Authentication
PLS (Physical layer security) is the new way to secure the 5G integrated with LoRA environment. Typical active attacks in this system is anticipated as man-in-the-middle attack (MITM), replay attack, denial of service (DoS) attack, and distributed denial of service (DDoS) attack. Having RFID for the authentication will avoid the unauthorized join in the network problems. Thus the problem of replay, ACK spoofing, bit flipped attacks can be avoided since the messages will be already authenticated using RFID and hence the communicating device in under the control. Having PLS will avoid the common problems like eavesdropping, jamming, and spoofing. The implementation of this security mechanism is done as such in the 4G and 5G systems.
12.10 Conclusion
5G mobile communication network will have affluent wireless devices connected and the issues faced on security front will be enormous. The evolution of mobile communication and its generations are discussed along with the security measures taken in each generation. The future is in the hands of wireless communication. A novel security method for the LoRa integrated 5G network is introduced. The security protocol includes PLS and RFID securing. The results and performance analysis have proven well suited for the futuristic communication systems. The future of the proposed work extends unto securing the system from wormholes.
References
- 1. Ahmad, I., Liyanage, M., Shahabuddin, S. et al., Design Principles for 5G Security, in: A Comprehensive Guide to 5G Security, pp. 75–98, 2018.
- 2. Ali, M., Khan, S.U., Vasilakos, A.V., Security in cloud computing: Opportunities and challenges. Inf. Sci., 305, 357–383, 2015.
- 3. Amraoui, H., Habbani, A., Hajami, A., Bilal, E., Security & cooperation mechanisms over mobile ad hoc networks: A survey and challenges. 2017 International Conference on Electrical and Information Technologies (ICEIT), 2017.
- 4. Apoorv, R. and Mathur, P., Smart attendance management using Bluetooth Low Energy and Android. 2016 IEEE Region 10 Conference (TENCON), 2016.
- 5. Aras, E., Ramachandran, G.S., Lawrence, P., Hughes, D., Exploring the Security Vulnerabilities of LoRa. 2017 3rd IEEE International Conference on Cybernetics (CYBCONF), 2017.
- 6. Bluetooth Low Energy Mesh Networks: A Survey. Sensors, 17, 7, 1467, 2017.
- 7. Brauer, S., Zubow, A., Zehl, S. et al., On practical selective jamming of Bluetooth Low Energy advertising. 2016 IEEE Conference on Standards for Communications and Networking (CSCN), 2016.
- 8. Cao, J., Ma, M., Li, H. et al., A Survey on Security Aspects for LTE and LTE-A Networks. IEEE Commun. Surv. Tutorials, 16, 1, 283–302, 2014.
- 9. Dabbagh, M., Hamdaoui, B., Guizani, M., Rayes, A., Software-defined networking security: Pros and cons. IEEE Commun. Mag., 53, 6, 73–79, 2015.
- 10. Dohler, M. and Nakamura, T., 5G Mobile and Wireless Communications Technology, 1st edition, Cambridge University Press, 2016.
- 11. Foster, G., Vahid, S., Tafazolli, R., SON Evolution for 5G Mobile Networks, in: Fundamentals of 5G Mobile Networks, pp. 221–240, 2015.
- 12. Hrri, J. and Bonnet, C., Security in Next Generation Mobile Networks, in: Wireless and Mobile Network Security, pp. 409–435.
- 13. LTE Advanced Networks-Secure Data Sharing Strategy for D2D Communication technique. Int. J. Mod. Trends Eng. Res., 4, 4, 187–196, 2017.
- 14. Markelj, B. and Zgaga, S., Mobile Security: Two Generations of Potential Victims, in: Advances in Cybersecurity 2017, pp. 65–76, 2017.
- 15. Monshizadeh, M. and Yan, Z., Security Related Data Mining. 2014 IEEE International Conference on Computer and Information Technology, 2014.
- 16. Monshizadeh, M., Khatri, V., Gurtov, A., NFV security considerations for cloud-based mobile virtual network operators. 2016 24th International Conference on Software, Telecommunications and Computer Networks (SoftCOM), 2016.
- 17. Nguyen, H. and Iacono, L.L., RESTful IoT Authentication Protocols, in: Mobile Security and Privacy, pp. 217–234, 2017.
- 18. Oca, E.M.D. and Mallouli, W., Security Aspects of SDMN, in: Software Defined Mobile Networks (SDMN), pp. 331–357, 2015.
- 19. Padgette, J., Scarfone, K., Chen, L., Guide to bluetooth security. NIST Special Publication 800, 121, 25, 2012.
- 20. Pavia, J., Lopes, D., Cristovao, P. et al., The evolution and future perspective of security in mobile communications networks. 2017 9th International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT), 2017.
- 21. Perez, A., Security Mobile Network, in: Implementing IP and Ethernet on the 4G Mobile Network, pp. 193–203, 2017.
- 22. Powering the Internet of Things With 5G Networks, in: Advances in Wireless Technologies and Telecommunication, 2018.
- 23. Qiao, J., Shen, X., Mark, J. et al., Enabling device-to-device communications in millimeter-wave 5G cellular networks. IEEE Commun. Mag., 53, 1, 209– 215, 2015.
- 24. Sharma, V., You, I., Leu, F.-Y., Atiquzzaman, M., Secure and efficient protocol for fast handover in 5G mobile Xhaul networks. J. Netw. Comput. Appl., 102, 38–57, 2018.
- 25. Shim, K., Do, T.N., An, B., A physical layer security-based routing protocol in mobile ad-hoc wireless networks. 2018 20th International Conference on Advanced Communication Technology (ICACT), 2018.
- 26. Spectral coexistence for next generation wireless backhaul networks, in: Access, Fronthaul and Backhaul Networks for 5G & Beyond, pp. 307–335.
- 27. Doelitzscher, F., et al., Understanding cloud audits, in: Privacy and Security for Cloud Computing, Springer, London, 125–163, 2013.
- 28. Wang, M., Yan, Z., Niemi, V., UAKA-D2D: Universal Authentication and Key Agreement Protocol in D2D Communications. Mobile Netw. Appl., 22, 3, 510–525, 2017.
- 29. Wang, W. and Hu, L., A Secure and Efficient Handover Authentication Protocol for Wireless Networks. Sensors, 14, 7, 11379–11394, 2014.
- 30. Wang, Y. and Alshboul, Y., Mobile security testing approaches and challenges. 2015 First Conference on Mobile and Secure Services (MOBISECSERV), 2015.
- 31. Wei, L., Hu, R.Q., Qian, Y., Wu, G., Energy Efficiency and Spectrum Efficiency of Multihop Device-to-Device Communications Underlaying Cellular Networks. IEEE Trans. Veh. Technol., 65, 1, 367–380, 2016.
- 32. Yasmin, R., Petajajarvi, J., Mikhaylov, K., Pouttu, A., On the integration of LoRaWAN with the 5G test network. 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), 2017.
- 33. Yrjo, R. and Rushil, D., Cloud computing in mobile networks—Case MVNO. 2011 15th International Conference on Intelligence in Next Generation Networks, 2011.
- 34. Zhang, J., Xie, W., Yang, F., An Architecture for 5G Mobile Network Based on SDN and NFV. 6th International Conference on Wireless, Mobile and Multi-Media (ICWMMN 2015), 2015.
- 35. Dolezilek, D. and Hussey, L., Requirements or recommendations? Sorting out NERC CIP, NIST, and DOE cybersecurity. 2011 64th Annual Conference for Protective Relay Engineers, 2011.
- 36. Wei, D., Jafari, M., Lu, Y., On Protecting Industrial Automation and Control Systems against Electronic Attacks. 2007 IEEE International Conference on Automation Science and Engineering, 2007.
- 37. Wei, D., Lu, Y., Jafari, M. et al., Protecting Smart Grid Automation Systems Against Cyberattacks. IEEE Trans. Smart Grid, 2, 4, 782–795, 2011.
- 38. Coutinho, M., Lambert-Torres, G., Silva, L.D. et al., Anomaly detection in power system control center critical infrastructures using rough classification algorithm. 2009 3rd IEEE International Conference on Digital Ecosystems and Technologies, 2009.
- 39. Coutinho, M., Lambert-Torres, G., Silva, L., Lazarek, H., Improving Detection Attacks in Electric Power System Critical Infrastructure Using Rough Classification Algorithm. Proceedings of The Second International Conference on Forensic Computer Science, 2007.
- 40. Ten, C.-W., Manimaran, G., Liu, C.-C., Cybersecurity for Critical Infrastructures: Attack and Defense Modeling. IEEE Trans. Syst. Man Cybern. Part A Syst. Humans, 40, 4, 853–865, 2010.
- 41. Su, S., Duan, X., Zeng, X. et al., Context Information based Cyber Security Defense of Protection System. 2007 IEEE Power Engineering Society General Meeting, 2007.
- 42. Huang, Y., Esmalifalak, M., Nguyen, H. et al., Bad data injection in smart grid: Attack and defense mechanisms. IEEE Commun. Mag., 51, 1, 27–33, 2013.
- 43. Berthier, R., Sanders, W.H., Khurana, H., Intrusion Detection for Advanced Metering Infrastructures: Requirements and Architectural Directions. 2010 First IEEE International Conference on Smart Grid Communications, 2010.
- 44. Mander, T., Cheung, R., Nabhani, F., Power system DNP3 data object security using data sets. Comput. Secur., 29, 4, 487–500, 2010.
- 45. Ten, C.-W., Govindarasu, M., Liu, C.-C., Cybersecurity for electric power control and automation systems. 2007 IEEE International Conference on Systems, Man and Cybernetics, 2007.
- 46. Queiroz, C., Mahmood, A., Tari, Z., SCADASim—A Framework for Building SCADA Simulations. IEEE Trans. Smart Grid, 2, 4, 589–597, 2011.
- 47. Khurana, H., Bobba, R., Yardley, T. et al., Design Principles for Power Grid Cyber-Infrastructure Authentication Protocols. 2010 43rd Hawaii International Conference on System Sciences, 2010.
- 48. Xie, L., Mo, Y., Sinopoli, B., Integrity Data Attacks in Power Market Operations. IEEE Trans. Smart Grid, 2, 4, 659–666, 2011.
- 49. Srivastava, A., Morris, T., Ernster, T. et al., Modeling Cyber-Physical Vulnerability of the Smart Grid With Incomplete Information. IEEE Trans. Smart Grid, 4, 1, 235–244, 2013.
- 50. Gamage, T.T., Roth, T.P., Mcmillin, B.M., Crow, M.L., Mitigating Event Confidentiality Violations in Smart Grids: An Information Flow Security-Based Approach. IEEE Trans. Smart Grid, 4, 3, 1227–1234, 2013.
Note
- * Corresponding author: [email protected]
