In this chapter
You might find it hard to believe, but the personal computer is now more than 20 years old, and so is the MS-DOS operating system. At one time, more than 95% of all the tens of millions of personal computers sold used MS-DOS as the operating system. Nowadays, almost all systems use a variation of the Windows operating system, although DOS compatibility is still provided through DOS subsystems. Previously, in Windows 95/98, you could boot into an MS-DOS command prompt, bypassing the Windows user interface. With the release of Windows ME, this capability is no longer available.
The objective of this chapter is to familiarize those of you who are less experienced computer users with the inner workings of your system. If you are an old hand and already familiar with the way your computer and DOS interact, you might want to skim through this chapter on your way to Chapter 2, “Starting DOS.”
For those readers who have been using computers only a short time or who have never checked out the inner workings of a PC, this chapter provides a quick introduction that gives you the basics. Knowing this information enables you to better exploit the features of DOS and gives you more control over your computing environment.
Although MS-DOS is by far the most prevalent variant of the DOS family, one other version from IBM needs to be mentioned. Now that Microsoft has quit developing MS-DOS as a standalone product, this version is the only alternative for someone wanting new and advanced features of the operating system.
IBM has continued to develop the initial DOS product since its inception. It has released upgraded versions containing many of the same features of the upgraded MS-DOS versions.
The latest version is called PC DOS 2000. Some of the new features include Y2K compliance, support for the REXX programming language, PCMCIA cards, unattended scheduling, and remote installation.
In 1981, IBM introduced the IBM PC, which became the worldwide standard for personal computers. This standard endures to this day—even through all the subsequent upgrades in technology.
In the early 1980s, IBM manufactured and sold more than half of all the personal computers sold. As the decade wore on, however, IBM's grip on computer sales weakened and scores of manufacturers introduced models of their own. All these manufacturers adopted the basic hardware architecture that made the original IBM computers a de facto standard.
The heart and soul of any personal computer is its central processing unit (CPU). The CPU is a microprocessor chip capable of receiving input, processing data, and producing the results as output. DOS-compatible personal computers have long been based on the Intel family of microprocessors and their clones.
Everything in your computer is designed around the needs of the CPU. The CPU is plugged or soldered into the main circuit board of your system, which is where the term motherboard comes from. The motherboard also contains the core group of components needed to build a complete computer system.
The CPU communicates to the rest of the system via the system bus. The system bus provides a communications highway where the CPU can “talk to” memory chips, as well as to peripheral devices installed in the expansion slots along the bus.
Note
The word peripheral comes from the Greek language and means around the center. As it is used in computer jargon today, a peripheral is any device that is connected to your computer's CPU, either by an expansion slot card or plugged into a port.
In your system, DOS plays the role of the traffic cop, organizing the flow of data in the computer and offering services that programs can use. DOS directs the activities of your system's CPU and helps the CPU to communicate instructions and receive information from other parts of the system. In other words, DOS makes all the separate components inside your computer system work together as if they were all one single machine.
When you install a video card or a modem into an expansion slot in your computer, it must conform to certain standards. These standards ensure that both DOS and the CPU know how to interface with the device.
It is not unusual for some peripheral devices, such as parallel and serial communications ports, to be built directly onto the motherboard of the computer. These devices also must conform to the standards that allow DOS and the CPU to control them.
To perform operations, your computer uses binary numbers to represent both data and program instructions. Binary numbers use the binary digits 0 and 1 in various combinations to represent everything you do with your computer. Binary digits are usually called bits, which is an abbreviation of binary digits.
Computer memory is nothing more than thousands—or millions—of individual switches that can have one of two states: on or off. The binary digit 0 represents off, whereas 1 represents the on condition. Eight bits arranged together form a byte; the arrangement of bits within the byte can produce one of 256 (28) possible values.
Each one of the 256 possible values of a byte is arranged into an extension of the ASCII (American Standard Code for Information Interchange) code. The original ASCII code used seven bits to represent 128 different characters. After the eighth bit was added, ASCII could represent up to 256 characters. Officially, this set is called the PC 8 Symbol Set but has come to be known—somewhat inaccurately—by computerists all over the world as the ASCII Extended character set.
The first 32 ASCII codes represent common commands used by the CPU and peripherals for such activities as making the speaker beep, telling a printer to use compressed print, controlling data transmissions, and so on. The rest of the ASCII codes represent letters, numerals, and graphic characters. Therefore, a method is needed to store this information and make it available to the CPU.
To store information, your computer typically uses three kinds of memory:
Random access memory (RAM)
Read-only memory (ROM)
Disk-based storage
Each type of memory plays a different role in your system.
Random access memory, or RAM for short, is a volatile form of memory. Volatile means that it can hold information only when electrically powered. If you turn off the power, all the information stored in RAM chips is lost. Think of RAM as an electronic chalkboard where information can be written and erased at will. When you turn off the computer, RAM is erased automatically. As you will see later in this chapter, RAM is broken down into three categories, determined by the way the computer addresses memory.
Read-only memory, or ROM for short, is a close cousin to RAM, with one important exception: The information stored on ROM is nonvolatile. ROM information is permanently recorded on the circuits of the chip during manufacturing and cannot be erased. When you turn off the computer's power, this information is not lost. When you turn the computer on again, the information stored in ROM is once again available to the CPU and to DOS. Your computer uses ROM to store instructions and programming, as you will see later in this chapter.
The third type of computer memory is disk storage. If you have the typical computer system, you can use both floppy disks and a hard disk (often called a hard drive) to store information while the computer is turned off. Disk storage uses metal or plastic disks coated with a magnetic material to record and play back information in much the same way as a stereo system uses magnetic tapes to record and play back music. Disk storage comes in a sometimes bewildering array of formats. Later in this chapter, you will find the information you need to demystify disk storage.
Although you might think of your computer system as a single machine, it actually is made up of many discrete peripheral devices. Strictly speaking, your computer is the CPU and its attached RAM. By themselves, the CPU and RAM can do nothing useful because there is no way to provide input for the CPU to work with, and no way for the CPU to provide output in a form you can understand and use. Without peripheral devices, a computer is worthless. Without an operating system such as DOS, your computer would be the modern equivalent of the Tower of Babel.
Every part of your computer except the CPU and memory is a peripheral device. Key boards, disk drives, printers, and monitors are all examples of peripheral devices. One of the most basic jobs DOS performs for you is to provide the standards and programming necessary to add peripheral devices to your system so that you can get some work done.
Back in the wild and woolly days of personal computers, before the IBM PC, each computer maker employed its own standards and peripheral devices. If you had an Apple II computer, you couldn't share disks with anyone who didn't have an Apple II. If the keyboard for your TRS-80 broke, you couldn't replace it with a keyboard from any other type of machine. Worst of all, if you went from an Apple II to another kind of computer, you had to learn a whole new set of commands.
One of the ancestors of DOS was an operating system called CP/M (Control Program for Microcomputers). CP/M standardized the commands necessary for using a computer, many of which are still used in DOS, but each different computer manufacturer still used different standards for peripheral devices and disk formats. According to legend, IBM investigated using CP/M as its operating system for the first PCs. As the rumor goes, there were differences in time frames, engineering, and personalities, so IBM turned to a small upstart company called Microsoft. If things had gone differently, this book might have been titled Special Edition Using CP/M!
The simultaneous introduction of the IBM Personal Computer and DOS changed the computing world forever. For the first time, because of standardization, users could walk into a computer store and buy disk drives, video cards, keyboards, and other peripherals made by other companies to put into their IBM or compatible computers.
Peripherals that are sold today for personal computers adhere to two standards: hardware and software. The hardware standards ensure that peripherals can fit into your system without doing damage and that they can communicate with the CPU. The software standards imposed by DOS ensure that the peripheral becomes an integral, functioning part of your computer system.
When you flip the power switch on your computer system, you set into motion a series of steps that must occur before you can see the DOS prompt, which signals that your computer is ready for use. No doubt you have seen these steps performed, possibly without realizing their significance. This set of steps is called booting the computer. This phrase refers to the old saying “pull yourself up by the bootstraps,” meaning to make something of yourself from nothing. That's exactly what booting does; it makes that expensive paperweight on your desk into a fully functional computer.
The first of these steps is the activation of the Power On Self Test (POST). The Power On Self Test is a program that has been recorded on a ROM chip located on the motherboard of your system. This program gets the ball rolling. First, it loads instructions into RAM for the CPU to follow. These instructions tell the computer to perform a quick self-diagnostic check of the hardware. One of the first things you see when you turn on the computer, therefore, is the system counting and testing the installed RAM.
Next, the POST checks to see that the system setup is still valid. Your system contains a special kind of chip called a Complementary Metal-Oxide Semiconductor, or CMOS, that stores information about your system's configuration. CMOS chips are used because they need only a trickle of power, which can be supplied by a battery, to retain the stored information for several years. Your system's date and time settings are stored on this chip, along with information about installed floppy disk drives, hard disk configuration, and other system configuration information that can vary from manufacturer to manufacturer. If the system setup is okay, the POST passes on to the next step: loading the operating system.
When the self test is satisfied that everything about your system is in order, it is time to load DOS using another program found on your system's ROM chips—the bootstrap loader. This program's job is simple and to the point: Find the operating system's loader on the disk and make it run. By default, the first place it searches is drive A, to see whether you have a bootable floppy disk inserted into the drive. If the program fails to find a disk in drive A, it next looks to your hard disk. When the loader finds a valid operating system (in this case DOS), it starts the program found on the boot sectors of the disk. Most computers today will allow you to specify in the BIOS where you want the computer to look for the operating system loader—for example, going straight to the hard drive and bypassing searching the floppy drive.
Completely describing all the steps involved in booting DOS might take several pages and bore you to tears, so the following description is somewhat simplified. When the ROM bootstrap loader finds a disk with a bootable copy of DOS, it transfers control to that disk's boot sectors, where the DOS loading program takes over.
The first file loaded is IO.SYS. IO.SYS places into memory the basic input/output services DOS provides. After this file is loaded, the second file, MSDOS.SYS, is loaded. Between these two files, DOS sets up the many services it offers to programs, such as file handling, printer handling, and so on.
MSDOS.SYS completes the foundation for providing DOS services to your system. After it is loaded, it checks the disk's boot directory (normally C:) to see whether a file named CONFIG.SYS is present. If this file is found, it is loaded into memory, converted to all uppercase letters, and interpreted. Each line of CONFIG.SYS specifies some type of configuration information, such as a device driver to be loaded or a system setting to be made. After these settings are established, COMMAND.COM is loaded.
COMMAND.COM is the user interface to DOS. Its job is to evaluate whether commands presented to DOS from the keyboard or from batch files are legal. If the commands are legal, they are run. If a command is not legal, COMMAND.COM is responsible for issuing one of those error messages that can prove so frustrating to new users.
Just before COMMAND.COM turns the computer over to you, the user, it checks to see whether a file called AUTOEXEC.BAT is present in the boot directory. AUTOEXEC.BAT is a standard batch file that usually contains commands to customize your DOS installation. The only thing special about AUTOEXEC.BAT is that it gets run automatically during bootup.
To understand the memory issues that surround DOS and your computer system, you first need to know a bit of history. When Intel designed the 8088 and 8086 processors on which the first generation of DOS computers (PCs and XTs) was based, Intel thought that no user would ever need more than one megabyte (1MB) of memory. Most of the computers then in use had only 64 kilobytes (64KB) of memory, so this speculation might have been reasonable at the time. The problem is that this speculation was wrong—very wrong.
Shortly after the release of the IBM PC, Lotus released a hot new spreadsheet program called 1-2-3. Soon businesses were buying PCs by the carload just to run Lotus 1-2-3. It wasn't long before users found they could build large spreadsheets that exceeded the memory limits of their computers.
A few years later, IBM introduced the PC-AT, based on Intel's 80286 processor. The AT's processor was faster than those used in PC and XT machines, and it had the capability to access up to 16MB of memory using a new processor feature called protected mode. Unfortunately, DOS was never enhanced to take advantage of this capability, so software developers never used the full capabilities of the 80286 chip. Many ATs lived and died without ever running protected-mode software.
Later still, Intel developed 80386 and 80486 chips that addressed up to 4 gigabytes (4GB) of memory. Until Windows 3.0 came on the scene, precious little software was able to run the computer's protected mode. Instead, users simply used these machines as fast PCs. Users who needed more memory than the original 1MB had to rely on a memory scheme called expanded memory, which was created collectively by Lotus, Intel, and Microsoft.
Today, the current family of Intel chips is the Pentium group. They include the Pentium, Pentium MMX, Pentium II, Pentium III, and Pentium IV CPUs. Also, other companies, such as AMD, now are making Intel-based CPUs that are in direct competition with the Pentiums. The Pentium-based CPUs can address more than 4GB of memory, depending on the operating system and CPU version.
RAM is classified in three ways: conventional memory, expanded memory, and extended memory. Understanding the distinctions can be quite useful.
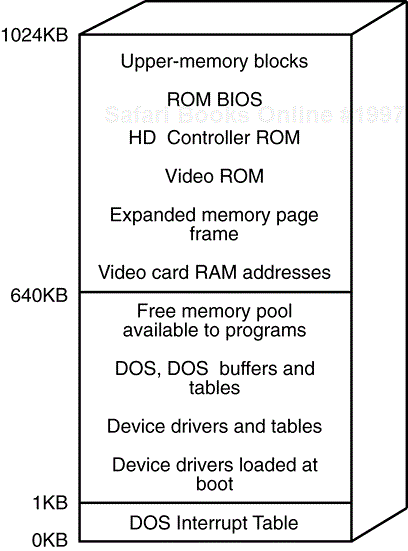
As you've already learned, the generation of personal computers that preceded DOS and the IBM PC used, at most, 64KB of random access memory. The Intel 8088 processor addressed up to 1MB—which was, at the time, a significant advance. Of this 1MB, 640KB was made available for DOS and applications programs to use. The remaining 384KB was reserved for system use. Figure 1.1 shows the way conventional memory is used under DOS.
As you can see in the figure, DOS places a table of available services into memory, beginning at byte 0. When DOS loads the rest of itself into memory, it occupies memory addresses beginning at 1KB. The space from 1KB to 640KB is reserved for DOS and whatever programs you might run. Addresses of more than 640KB (the infamous 640KB barrier) are reserved for addresses for ROMs and for accessing video card memory.
In DOS, memory addresses use a segment:offset notation to pinpoint an exact location where data or program instructions can be stored. These address locations are always specified using the hexadecimal number system. Each segment is 64KB in length, but each segment begins only 16 bytes up from its neighbor. The offset portion of the address specifies how many bytes the address is from the beginning of the segment.
Programmers soon discovered that an extra block of usable memory can be gained by specifying the last possible segment in the 1MB area in the segment portion of the address. Using this trick opens up an extra 64KB (minus the 16 bytes that fall below the 1MB line) of memory, more than 1MB that can be addressed without sending DOS and the processor into never-never land. Thus, the high memory area was born.
This newly discovered high memory area was almost immediately grabbed by network designers. They saw this area as a safe place to put their data buffers, which didn't take RAM away from running programs that were already beginning to feel the squeeze of the 640KB barrier.
Beginning with the release of DOS 5.0, users could employ unused addresses between 640KB and 1MB to run DOS, programs, and device drivers by using HIMEM.SYS and EMM386.EXE to make this space available. You use the LOADHIGH and DEVICEHIGH DOS commands to place programs, device drivers, and even portions of DOS itself into the upper memory area.
→ For more information about using upper memory blocks, see Chapter 19, “Configuring Your Computer,” p. 441.
When Lotus 1-2-3 users and others began demanding a way to access more than the 640KB memory provided by the conventional memory scheme, Lotus, Intel, and Microsoft worked together to come up with the Expanded Memory Specification (EMS), also known as the LIM 3.2 specification. This specification was adopted before the Intel 80286 processor hit the market. EMS was an immediate hit, which in part accounts for the fact that few software companies even tried to exploit the enhanced memory addressing capabilities of the 80286 processor. Programs that needed more than 640KB memory could easily be modified to adhere to the EMS system, so there was no great push for DOS to use the chip's protected mode, which could address up to 16MB of RAM.
The Expanded Memory Specification makes more memory available to processors running in real mode, the name given to the mode of operation that mimics the original 8088 processor used in PCs and XTs. The LIM specifications reserve a 64KB area of memory in the upper memory block (the area between 640KB and 1MB) for use as a page frame.
Shortly after the EMS specification was adopted, several companies—including AST Research, at the time the largest seller of add-on memory boards—came up with an Enhanced Expanded Memory Specification (EEMS). This new expanded memory scheme used a backfilling technique that eliminated the need for the page frame in upper memory and allowed expanded memory to reside inside the 640KB range. In fact, some early EEMS products required users to remove any RAM in their system above the 256KB mark, which provided 384KB of expanded RAM to be situated within conventional memory addresses.
The Expanded Memory Specification has always been, and will always be, a kludge. Life today would be much simpler for those folks who support computer users if the hardware and software manufacturers had taken a “bite-the-bullet” attitude when the 80286 processor became available and built systems to use extended memory.
The DOS Expanded Memory Manager (EMM386) made old-fashioned EMS boards obsolete because it simulated expanded memory using the extended memory.
The Extended Memory Specification (XMS) is a simpler way of making memory addresses of more than 1MB available to your programs. Extended memory is simply an extension of conventional memory addresses. The 384KB system memory area is still present under XMS, so programs can use the conventional 640KB memory area and addresses greater than 1MB.
To implement extended memory, the protected mode operations of the processor (80286, 80386, 80486, or higher) are turned on. DOS accomplishes this task by loading HIMEM.SYS at bootup from the CONFIG.SYS file. HIMEM, which is an extended memory manager, enables DOS to address memory above the conventional 1MB mark.
Few DOS programs take advantage of the availability of extended memory. Windows and Windows programs, however, routinely use extended memory.
RAM is volatile storage. As soon as the power goes off, RAM goes to sleep. ROM provides a permanent storage medium, but you can't write files to ROM. What is needed is a third method of storing data and programs. DOS stands for disk operating system, so if you get the notion that disks are used for permanent storage of data and programs, give yourself the afternoon off.
One of the major functions of DOS is to facilitate the reading and writing of data stored on disks. Disks are circular platters of plastic or metal coated with a magnetic emulsion similar to that used to produce cassette or video tapes.
By offering standardized disk services, DOS saves programmers countless hours of work because their programs can simply ask DOS to read or write a disk. The programmer is spared the task of writing code to store data. These DOS file services also provide an added benefit to computer users: Because DOS takes care of placing files onto disks, any file created by a DOS program can reside on the same disk as any other DOS file.
When a program writes to a disk, DOS ensures that the data is stored as a named collection of information called a file. DOS rules determine naming conventions. A legal DOS filename can be from one to eight characters, followed by an optional period and a one- to three-character extension. A filename's extension is most often used to indicate the type of file being stored.
Note
In the case of Windows 95/98/ME, you can use long filenames in Windows, but when you are looking at the files from DOS, the filenames are shortened to the standard 8.3 format. The name is shortened by taking the first six characters of the filename and then adding a tilde (~) followed by an incrementing value, starting with 1.
Windows NT/2000 shows the long filename for files and directories in the command prompt window.
For more information on this and other DOS file operations, see Chapter 8, “Managing Your Files.“
Floppy disks are wafer-thin plastic disks coated with a magnetic emulsion and encased within a protective sleeve. The original IBM PC used floppy disks measuring 5 1/4 inches across. Today, 3 1/2-inch floppies have become the industry standard. The advantages of the 3 1/2-inch format are the greater data density (the disks hold considerably more information than the physically larger 5 1/4-inch disks) and the hard plastic sleeve that better protects the disks from damage.
Floppy disks are most commonly used to store data to be archived or transferred to another computer. The biggest disadvantages of floppy disks are that reading and writing on floppies is relatively slow, and they do not hold enough information to accommodate today's larger programs and data files.
Hard disks are nonremovable, high-capacity, rigid platters sealed inside a dust-free casing. For increased storage capacity, several platters can be stacked within a single hard disk drive where multiple pickup heads are used to read and write the stored information. You can find more detailed information about magnetic disks in Chapter 7, “Preparing and Maintaining Disks”
Another storage technology finding wider use today is removable media. This technology uses cartridges that can hold anywhere from 100MB to 2GB of data. The most popular brand is Iomega, with the Zip (100MB–250MB) and Jaz (1GB–2GB) disks and drives. Another newer option is the LS-120 floppy disk, which uses a special 3 1/2-inch floppy disk and drive and can hold up to 120MB of data. The best thing about this solution is that the LS-120 drive can still read standard floppies, which eliminates the need for an additional drive.