Wireless networks are usually more challenging to manage than wired networks. The physical aspects of a typical wired network are stable and predictable; the transport medium itself, “the wire,” does not change. Wireless networks, however, operate in a very dynamic environment. User experience can differ from day to day, depending upon factors such as the number of concurrent users, interference, multipath effects, and even time of day; for example, the radio frequency (RF) “landscape” of a WLAN will be different at 6 a.m. than it will be at 3 p.m. during a typical working day. Furthermore, because of the unlicensed nature of WLANs, there is always the risk that neighboring networks will spring up to interfere with what was previously a stable environment. Finally, wireless technology is relatively new, and many experienced networking professionals are still unfamiliar with the solutions, challenges, and strategies for carefully managing this environment.
When you take the WLAN’s unique physical properties into account, a WLAN can still be considered as simply another transport mechanism. As such, many of the standard management strategies that are tried and tested in the wired networking world are equally applicable to wireless networks; the common themes of fault and configuration management, performance tuning, and operational support need only be slightly modified to ensure that your WLAN is as stable, reliable, and secure as your wired network.
You must also consider the two general approaches to WLAN architectures—the centralized model and the distributed model—and the tools that are available to you. When considering the specifics of WLAN management, you can view it as having three facets:
RF management
Host management
Client management
However, before delving into these topics, you must address a more fundamental question; that is, you must determine what strategy your enterprise will adopt for wireless network management.
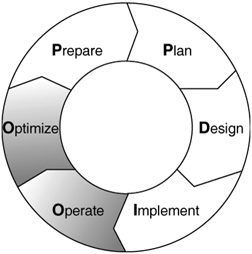
Managing the WLAN can be considered part of two phases of the PPDIOO solutions lifecycle: operating and optimizing. Unlike previous phases, operating and optimizing your WLAN can have a long duration because they are ongoing even while you begin to plan, prepare, design, and implement the next generation of your wireless network.
Management strategies for WLANs are the day-to-day manifestations of operations and optimization. As a refresher, Figure 8-1 illustrates the PPDIOO solutions lifecycle.
How should the enterprise manage its WLAN? What tools should be used? What strategy should be adopted? These are the challenging questions that you should answer before the wireless network is being deployed.
No single product offers a complete solution. Some recommendations can be made safely, however, as follows:
Use vendor-specific wireless management tools were possible.
Integrate wireless management into the existing network management framework.
Use fault management, configuration management, accounting management, performance management, and security management (FCAPS) methodologies as a pointer to the standard areas that your wireless management system should address.
Define a client management process. This is overlooked by FCAPS. (You learn more about FCAPS later in this chapter in the “FCAPS” section.)
Develop in-house tools to plug any gaps not addressed by the vendor-specific wireless management tools and to satisfy any unique reporting or management requirements that you might have.
Another fundamental decision that you must make is whether to handle wireless network management in-house or to outsource this activity to a trusted partner. Most enterprises will likely manage their own networks, but outsourcing this activity is no longer uncommon.
Managing the WLAN in-house is perhaps the most common approach. Most enterprises will have their own dedicated IT support staff. In these circumstances, it makes sense for your IT organization to treat the wireless network no differently from the rest of your IT infrastructure. It is simply considered another transport medium, similar to the wired network but with some unique characteristics.
Some enterprises choose to outsource the implementation and deployment of their WLAN but choose to retain management responsibilities. This choice is common in sensitive industries or areas, such as finance, government, or military organizations, but it is by no means limited to these. Providing native access to your network is often considered a security and business risk. This reasoning is especially understandable when you consider that WLAN management entails the ability to capture and analyze all traffic, which is not something that every enterprise is comfortable with a third-party undertaking.
The disadvantages of retaining responsibility for WLAN management are also worth noting. Although WLANs are just another network, the fact remains that they require wireless-specific skills. Your existing IT support staff will need to familiarize themselves with this new technology and the unique management and security challenges it presents. This familiarity can often be achieved through on-the-job training, but this training typically entails a steep learning curve, increased risk of poor management performance. Staff in training can sometimes be a risk because they can be unaware of errors or can cause security breaches, and so on. A more prudent approach is to engage in professional training that is supplied either by the WLAN equipment vendor or by one of the many independent IT training organizations.
When your IT staff are suitably trained or familiar with the WLAN technologies, you still must define, develop, and adopt an appropriate WLAN management strategy. This process entails selecting the appropriate tools, ensuring proper integration, and developing systems and procedures to automate as much activity as possible. On-the-fly, reactive management is not a safe or prudent approach for an enterprise-class wireless network.
Outsourcing wireless network management is an attractive option for many enterprises that do not have the resources and skills in-house. This option avoids the need to train your IT staff in wireless technologies. Indeed, many enterprises outsource their network management entirely. In such a situation, wireless network management is just another service that is provided by your trusted third party. Both tangible and intangible, costs are involved in this approach, such as the monetary cost of engaging the vendor and the administrative cost of managing their activity. In the end, the expense might be lower than employing or training staff yourself. In the outsourced model, the responsibilities that remain with you are to monitor the key performance indictors (KPIs) and Service Level Agreements (SLAs) that you have set with the external vendor and to ensure user satisfaction. Careful economic (strategic, tactical and financial) consideration is required to determine what is most beneficial for your specific environment.
Before choosing the outsourcing option, you must be comfortable with the fact that your network traffic will be visible to the third party, that access to your network infrastructure will be required, and that due diligence is undertaken to ensure that security and business processes are not compromised. Outsourcing removes some of the headaches of WLAN management from you and your enterprise, but it should only be undertaken after a prudent risk and business case review.
FCAPS (fault, configuration, accounting, performance and security), the ISO model for network management, is a functional approach that segments management areas into discrete categories, which allows the network manager or management framework to address each in turn and ensure that no area is overlooked. FCAPS is a model, not a product. Many network management applications and designs adopt FCAPS, and internally developed procedures and tools can also be architected along these lines. Even if your management product, framework, or application does not mention FCAPS, the five areas covered by this model are probably addressed. If they are not, then there is value in identifying the gaps in your management strategies. FCAPS is therefore useful to assist the network manager in ensuring that a structured, methodological approach is taken to network management and that haphazard or reactive management techniques and strategies are avoided.
FCAPS was born “in the wired world” of centrally managed environments. As mentioned earlier, wireless networks present many unique challenges. Chief among these is the dynamic nature of the transport medium. So although FCAPS is a useful tool, or indeed a useful mindset, with which to approach wireless network management, you must ensure that it is either updated or enhanced to include the distinct aspects of the wireless environment or only used as a tool to help guide your management strategies.
The next sections briefly examine the five functional areas of FCAPS and its shortcomings.
In this area, service-impacting events are identified and resolved. The network is monitored for problems, and when identified, they are isolated and corrected. This functional area keeps the network running. Downtime is minimized, and the network is kept operational. Fault management is perhaps the most well-known area of network management.
Within the configuration management functional area, the network is monitored, the status or design is maintained, and any changes to network components are carefully planned, recorded, managed, and performed. Subjects such as the IP addressing scheme, routing tables, wireless VLAN and Service Set Identifier (SSID) assignment, and information on the physical devices and their logical layout are handled in the configuration management area. Moves, adds, and changes are also dealt with here because they affect the configuration of the network. Reporting on planned and past changes forms part of this functional area.
Accounting management is focused on the user and is the domain where data about network usage is collected, collated, reported, and then acted upon. The gathering of statistics allows the network manager to monitor usage, detect inefficiencies, bill users or groups for access (if applicable), and produce trending reports to assist in proactive design and reconfiguration. Accounting management allows you to monitor the actions of users, make better use of the available resources, and plan accordingly for improvements. Reporting on historical use, called trend reporting, is an important facet of this functional area.
Performance management is similar to accounting management in that you collect data from the network, but you monitor the physical equipment and medium rather than users. In the performance management functional area, you collect data on network resource utilization, set thresholds for reporting and alerting, and make changes to fine-tune the network. Performance management can be as simple as monitoring CPU or network interface utilization or as complex as full end-to-end application monitoring. The concept is simple, however: Monitor the network, identify problems or chokepoints, and fine-tune the environment.
The security management functional area of FCAPS defines the process and procedures for network security. The network is monitored for compliance to the security posture, risks are identified, events are logged, and audit trails are created.
FCAPS addresses management in the traditional environment, which typically means a wired network with a clearly defined hierarchical architecture, static endpoints and deterministic behavior. Unlike WLANs, relatively few external factors can affect a wired environment.
Wireless networks, on the other hand, are subject to many outside factors, and the endpoints (that is, the wireless client devices) are mobile in nature. They can change their location, their IP address, and even the status of their connectivity (online versus offline) on a regular basis in the dynamic radio environment. The dynamic nature of clients’ connectivity often does not represent a fault. Because of the lack of any specific client management area in the FCAPS model and the fluid nondeterministic nature of WLANs in general, FCAPS should not be considered a comprehensive system for wireless management. Instead, FCAPS is useful in helping you focus on the traditional areas that require attention. It can be considered a subset of a robust enterprise-class wireless network management framework. FCAPS is a useful tool, but you should not use it as the sole method for conceptualizing and even designing your management toolset.
Historically, WLANs have been approached in a manner similar to wired networks. Because the access points were deemed access layer devices, or edge devices, they were considered no differently from a typical Layer 2 switch. Both provided connectivity to the network, after all.
Most enterprise networks rely upon intelligent devices. This includes access layer switches and (historically, once again) access points. Control and management were provided “at the edge,” so the devices required a degree of intelligence—that is, configurability and manageability. The access points were considered “intelligent” or “autonomous” because they were effectively standalone devices. Each access point stored all the features, settings, and configuration and acted as a unique, intelligent host on the network. In other words, if you had a WLAN with 25 access points, you had to configure and manage each of the 25 devices. The rest of the network infrastructure (the switches to which the APs were connected) did not require wireless-specific awareness. This is the so-called distributed model, also known as the autonomous AP architecture, and many products and manufacturers still use this framework.
Recently the centralized model, commonly known as the thin AP or centralized AP architecture, has gained popularity. This pardigm approaches WLAN intelligence differently. Instead of embedding the intelligence into the access points themselves, it is centralized into the device to which the AP is physically or logically attached. The attachment points are typically dedicated appliances (so-called “wireless LAN controllers”) that act as a centralized management system for the access points. The APs are configured and managed not individually but centrally from these controllers. Conversely, this model requires dedicated wireless controllers (or wireless switches).
Often, the WLAN controller automatically configures the access point settings entirely, obviating the need for IT staff to configure each device with specific or distinct radio settings, for example. On the other hand, this system sometimes results in reduced configurability, removing your IT staff’s ability to fine-tune or mold the wireless network to your particular needs. In these circumstances, you can disable the automatic “self configuring” features while retaining the other benefits of the centralized model.
Both the centralized and distributed models have their advantages and disadvantages. The traditional, distributed architecture provides a robust system that does not rely upon dedicated wireless appliances. Access points can be installed anywhere on the WLAN, and each site (small offices, remote branches, individual buildings) does not require additional equipment in the form of a dedicated controller. The access points contain all the configuration and settings required and use common operating systems, such as those already familiar to your IT support staff. A distributed model is very scalable because new APs can be installed wherever you have a free Ethernet port.
The centralized “wireless switch” or “wireless controller” architecture simplifies deployment. Almost all the wireless settings are configured centrally, and there is no (or reduced) need to configure each access point. Many products that adopt this approach also include added features, such as VPN tunnel termination, guest networking capabilities, and wireless intrusion detection systems. The wireless management is provided by either the controller or, more often, another separate WLAN management appliance. The centralized model can often make small or medium installations very easy to deploy. On the other hand, the centralized model does not scale as well because it requires dedicated controllers for each WLAN site and may even require several controllers for larger buildings or deployments. This can rapidly become costly and a deployment challenge in its own right.
The manufacturer of the product that you select will most likely dictate whether you use a centralized or distributed architecture. Some manufacturers, such as Cisco Systems, offer both. In either case, some fundamental WLAN management strategies are necessary for both models, and neither obviates the need for a carefully considered and robust management framework. Despite what any marketing or sales people tell you, there will always be a need for a holistic approach that takes into account more than just the simple “intelligence” or configurability of the access point.
This section describes the particulars of wireless network management. You learn about the unique, particular areas that you must address in your enterprise WLAN management strategy. As mentioned previously, wireless networks are in some ways just another transport medium and can be considered in the same way as traditional wired networks, but in other ways, they present their own challenges and exhibit their own unique characteristics. This directly influences the manner in which you must manage your WLANs.
Management of the RF spectrum is the most obvious characteristic that is unique to the wireless environment. Radio communications can present serious problems for a poorly designed network. As such, the management of the RF spectrum is traditionally considered the most difficult and time-consumingaspect of building a WLAN. RF management typically refers to the following. You should ensure that your management toolset addresses each of the following dimensions of RF management:
Channel allocation—. Your management toolset should be capable of assigning relevant channels; these are dependent upon which IEEE standard you are using on a particular access point.
Transmit power—. Manage the transmit power of your access points. In many circumstances, you will need to change the transmit power to address interference, extend access in poorly covered rooms, or reduce prevent power due to radio coverage from extending beyond the physical boundary of your buildings. Several WLAN management solutions offer proactive, dynamic, or automatic tuning of transmit power. When used by several access points in conjunction, this setup is often referred to as self-healing WLANs. The wireless network can detect areas of poor coverage or a failed access point and automatically increase power to correct error.
Interference detection—. Nearby WLANs installed by others, poorly shielded microwave ovens, older analog wireless phones, and even baby monitors can create interference. Anything that transmits in the 2.4-GHz or 5-GHz frequency range is a potential interfering device. You should be able to detect interference and, ideally, locate it. You can achieve detection and location by using native WLAN management features that some products offer or you can use standalone wireless sniffers. These are usually handheld devices that IT engineers use to scan and analyze network traffic. Your management strategy should take this into account regardless of the specific tool you choose.
Note
Sniffing is passive interception of network traffic, usually with a view to analyzing it later to gain access to information stored in the captured data. Sniffing is possible on both wired and wireless networks, but it is much easier in the latter because the sniffing device does not need to be physically connected to the network. In the wireless environment, you only need a wireless card to capture traffic transmitted by nearby access points or other client devices. Sniffing can be undertaken with dedicated devices designed explicitly for that purpose or, more commonly, by regular laptops or PDAs with special software. Sniffing is deemed to be “passive” because the sniffing device does not need to send traffic or advertise its presence; it simply “listens” to the network and stores any traffic it can.
IT professionals often use sniffing when they are troubleshooting network problems because the capture and analysis of traffic allows careful and detailed examination into every packet. However, many hackers also use sniffing in an attempt to gain access to a network. Traffic is captured, and the hacker attempts to read the data. Robust encryption, like that offered by WPA, is essential for enterprise-class WLANs. Although it is very difficult to prevent sniffing, strongly encrypted traffic is impossible to decipher and is therefore protected.
A simple but useful analogy is to think of sniffing as “eavesdropping.” In normal circumstances, it is impossible to stop someone from listening to your conversation. But if you are talking in code, it does not matter as much.
Rogue AP detection—. Rogue AP detection is a critical aspect of any WLAN management framework. Often considered a security issue, rogue AP detection is usually (but not exclusively) achieved through RF detection capabilities. This is provided by either the native WLAN management feature-set inherent in the product you select or, once again, provided by standalone or handheld wireless sniffer devices. It should be noted that RF-based rogue AP detection should not be considered the only method of identifying rogue APs, but rather one part of a multifaceted strategy. This is discussed in more detail in Chapter 7, “Security and Wireless LANs.”
Location-based services (LBS)—. This term describes the features that allow a WLAN to track the location and movement of wireless devices. These can be WLAN network adaptors in laptops, PDAs, or wireless phones, or dedicated radio transmitters (often known as “asset tags”) that are fixed to equipment specifically to enable asset tracking. For example, in many hospitals, LBS is used to track expensive diagnostic or medical equipment; in some manufacturing plants, LBS is used to track the movement of forklift trucks or equipment as it moves around the factory floor. This capability is also known as Radio Frequency Identification (RFID). Note that RFID is a generic term and quite often refers to cheaper, non-WLAN-based technologies used in the retail market. RFID is a form of LBS.
Wireless Intrusion Detection Systems (WIDS)—. WIDS are tools that allow you to identify aberrant radio activity within your WLAN. They are a wireless-based version of the Intrusion Detection System (IDS) used in wired networks to detect suspicious or security compromising activity. WIDS provide ongoing, continuous monitoring of the RF range, detecting threats, attacks, and interference that spot checks or snapshots can overlook. WIDS can be implemented by dedicated sensors, standalone handheld devices (which tend to be less useful because of their intermittent use by IT staff), or by the native WLAN infrastructure itself; the access points themselves can scan the airwaves while providing network connectivity to your users. WIDS can detect rogue access points, denial of service (DoS) attacks, and insecure ad-hoc networks (peer-to-peer WLANs that users configure with their own clients) that compromise security.
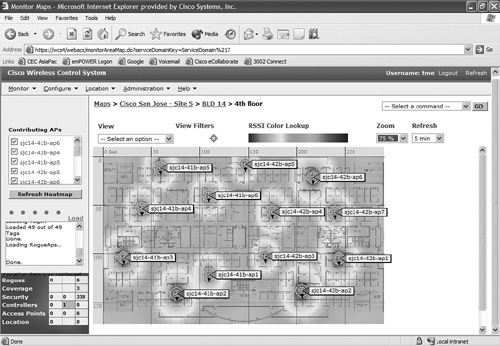
Visualization—. Because WLANs are very dynamic and nondeterministic in nature (radio cells can change over time based upon transmission or a changing physical environment), IT staff can never be certain of the coverage at a particular moment. To help combat this challenge, many WLAN equipment manufacturers developed the concept of visualization. These reporting and monitoring tools provide a map of your floor plan along with visual cues as to the size and location of radio cells. The maps are called heat maps because they are similar to the colored maps used to show varying levels of heat in oceanography or geographical sciences. Color is used to show the various levels of signal strength.
Visualization is extremely useful for the IT organization. At one glance, your IT support staff can see the current state of coverage (without having to walk around measuring it), the signal strength, and any gaps or “holes” in the WLAN. Because floor plans and heat maps are very intuitive, this system greatly enhances the speed and ease with which your support organization can troubleshoot problems. Figure 8-2 is an example of a visualization tool. The different shades in the “heat map” reflect differing signal strengths.
Note
Many of the preceding RF management issues are addressed or managed in a centralized manner by the wireless switch products or the dedicated WLAN management appliances offered by most enterprise-class solutions. In many cases, you will configure these settings once on the WLAN controller or even allow the WLAN controller to configure these options automatically for you. Alternatively, you might create templates and automate the configuration of the APs, leaving the management appliance to automatically configure the access points. This option reduces management costs but takes control away from your IT staff. In small to medium deployments, and even in some large environments, the operational cost savings can be significant.
All IT and network support staff should be familiar with host management. In many ways, this is the easiest area of WLAN management. Depending upon the architecture of your WLAN (centralized versus distributed), you might need to manage every individual access point, or you might be able to use a centralized management toolset.
Most enterprise-class WLAN equipment now offers dedicated WLAN management appliances. This is true for not only the centralized models but also the distributed intelligent AP models. The Cisco Wireless Control System (WCS) is an example of a dedicated WLAN management appliance.
With host management, you must consider issues such as the following:
Access point configuration
IP address
Host name
SSID(s)
VLAN(s)
Security settings
EAP mechanism
Encryption protocol
AAA settings
RF settings
Transmission power
Frequency band (802.11a, 802.11b, 802.11g)
Channel allocation
Managing the equipment
Firmware management
Image (or operating system) management
Client management is one of the hidden challenges in supporting a wireless network. Unlike the wired environment, where hosts are usually static and their interoperability and connectivity to the network are well understood, WLANs tend to have a wide variety of clients that require ongoing monitoring, management, and support. For example, as WLAN security standards evolve, the various client adaptors often need software and firmware updates to keep abreast of these new developments. Wireless devices also usually need specific WLAN client software. This is especially true if you require functionality to that provided by modern operating systems such as Windows XP or MacOS.
In a typical WLAN environment, you have to support several operating systems, different makes and models of laptop (each with different wireless adaptors), and many wireless devices (such as mobile bar-code readers, wireless VoIP handsets, or embedded wireless intelligent systems in manufacturing or factory equipment). The combination of these different endpoints, from different manufacturers and each running different software, makes ensuring a stable, consistent, and secure environment a chakkenging task.
Your wireless management strategy cannot afford to ignore these unique requirements. WLAN client management is often overlooked when large-scale enterprise deployments are undertaken, resulting in a haphazard, costly, and reactive approach that doesn't effectively support those hundreds or thousands of devices.
Many wireless client software come with their own management application. The application centrally defines and distributes profiles, updates client security postures, and even polls devices for reporting information. However, in the typical heterogeneous environment, using a single standard hardware adaptor and software client is not possible. In these circumstances, you have two choices: You can accept the inevitable burden of supporting and managing disparate wireless platforms, or you can adopt a third-party cross-platform wireless software client.
Companies such as Meetinghouse Data Communications (http://www.mtghouse.com) provide wireless client software that is supported on a variety of operating systems and on the most common wireless adaptors. Additionally, they provide comprehensive client management features, including centralized profile management and client configuration, which is discussed in more detail later. Many companies have adopted these cross-platform clients because of these features.
Another nonexclusive option is the use of client management tools that your enterprise might have already deployed to help support existing computer systems. Tools such as Microsoft SMS and Altiris Client and Mobile Manager allow you to distribute software and applications to your end-user devices. These tools can help manage your clients, but they might not address the wireless-specific requirements such as profile creation and updating.
Finally, the need to flash adaptor firmware is an uncommon occurrence. However, it is sometimes required, and you should therefore plan for it accordingly. Flashing the firmware updates the “embedded” software on the adaptors. This is sometimes necessary when the manufacturer distributes bug fixes or new features. Ensuring that your cards have the latest firmware before or during the installation is highly recommended (see Chapter 6, “Wireless LAN Deployment Considerations”).
WLANs present several unique management challenges. Many relate to the physical aspects of the wireless environment, whereas some are the result of the dynamic nature of the wireless network and its mobile users and devices. Knowledge of these challenges will help ensure that you do not overlook these areas in framing your management strategy for the enterprise-class WLAN. Some of the most commonly experienced problems and challenges you will face include the following:
The dynamic nature of the transparent medium
The mobility of endpoints
The persistence of endpoints
The nature of mobile endpoints
Wireless security management
These challenges are fundamental in nature and simply characteristic of the wireless environment. None is insurmountable, and examining each in turn can assist in addressing them in your management strategy.
Wired networks are deterministic in nature. That is, they function on a predictable basis with very little outside influence on their operation. Wireless LANs, on the other hand, can be considered statistical or probabilistic in nature. As mentioned in the introduction to this chapter, the wireless LAN will function differently depending upon the number of users associated to a particular access point, the amount of traffic generated by those users and devices, and outside interference, either from nearby but external networks or from factors such as the physical environment.
Most enterprise-class WLANs are made up of several access points providing large areas of coverage in one or more buildings. However, the dynamic nature of the transport medium, the RF spectrum upon which 802.11 WLANs are based, means that one cell will by its very nature have different characteristics from another cell. This can even be the case in the same building. The cell’s size and shape are dependent not only on the transmission power of the access point but also on such effects as the composition of walls and floors, the location of physical obstacles such as furniture, the existence of other nearby devices using similar radio frequencies, and so on.
A carefully designed WLAN is capable of withstanding the vast majority of these effects. However, the fact remains that a wireless LAN’s behavior is isolated in both time and space. Appreciation of this fact prepares the network manager to face these challenges and to ensure that the tools he or she puts in place can help identify unique radio-based problems, often before they negatively impact the end users.
WLANs enable and promote mobility. Thus, at any point in time, a mobile device could be at any location on the network. Mobile devices, such as laptops, PDAs, or even wireless-equipped vehicles or manufacturing equipment, can roam from access point to access point. In a wired environment, the network manager (or network management toolset) knows and can predict where a particular endpoint is. In the vast majority of cases, endpoints are literally “wired” to a jack and, in turn, a switched port on your networking infrastructure. That is not so in the wireless LAN. Devices move about the building, campus, or factory floor. Without specific tools or reports, it is often difficult, or even impossible, to identify a wireless device’s location. Indeed, they will often change IP addresses on a daily basis, sometimes more often. Layer 3 (inter-subnet) roaming results in the client being assigned a new IP address.
Most wired networks are a collection of physically static devices that present a degree of “persistence” in their connectivity. That is, they usually remain online and connected for long periods of time, if not indefinitely.
In the wireless space, especially with the introduction of PDAs, Application-Specific Devices (ASD) such as bar-code scanners, wireless voice handsets, and smart phones, wireless-enabled devices come online and go offline on an irregular, unpredictable basis. Of course, that is not to say that all mobile devices are going offline all the time, but rather the nature of many mobile devices (such as PDAs) is such that a system cannot automatically assume they are online at a particular time.
Management tools and strategies that rely upon persistence of connectivity—the ability to reliably contact, ping, identify, or locate end devices—will not handle such an environment well. A toolset that automatically generates reports and alerts on hosts or devices that it can no longer contact might generate many false-positive alerts or alarms, for example. Management tools that rely upon agents (or specific management software) might create erroneous alerts if they cannot consistently contact these devices on a predictable basis.
Remember that access points are not the only wireless devices on your network. Each client device is also fitted with a radio and an antenna. So not only does your WLAN present you with the challenge of dealing with many (sometimes hundreds or thousands) access points, but each client device also needs to be dealt with.
Typically, an enterprise-class WLAN will standardize upon the infrastructure required for the WLAN; that is, the design will detail what specific products are used, how the infrastructure devices are configured, and so on. Such standardization is quite often not the case when it comes to client devices. There are often many different makes and models of laptops or mobile devices within the company. Even laptops that come with embedded wireless adaptors and that are manufactured by the same vendor will sometimes have different radio interfaces. It is not uncommon for an enterprise to have a mixture of different makes of laptops, different platforms (for example, Windows 2000, Windows XP, Linux, and MacOS), different client adaptors, and differing versions of firmware and client software. Contrast this with the wired network, where the vast majority of devices are easy to install; that is, you literally plug them into the network and they work. You do not have to worry about whether the wireless network adaptors have the latest firmware, whether the correct software application and version have been installed, or whether the configuration of the software is completed and appropriate profiles have been created.
Enterprise-class wireless networks should always have a robust security framework. This is discussed in detail in Chapter 7. The typical security posture will detail not only the Extensible Authentication Protocol (EAP) mechanism used for authentication and the encryption protocol used for data integrity, but also fundamental characteristics such as the SSID.
Simply defining these protocols on the wireless infrastructure (the access points or WLAN controllers) is not enough. You must also configure each client device with the correct settings. Each SSID/VLAN might require different security postures. You might have separate virtual WLANs for voice, data, and guest networking that each require different security settings. Many users will also have wireless at home or will use public wireless services while traveling. These will also have different security requirements and settings. In short, every WLAN client will almost certainly have multiple security postures.
To configure and manage the wide variety of devices and user groups correctly and appropriately, you can use profiles, which are usually a collection of network and security settings required to ensure connectivity. The wireless software on every device is configured with the correct security settings (for example, SSID, EAP mechanism, and encryption protocol), which are then saved for repeated use. The user can then simply select the appropriate profile for his or her current location.
For example, a typical user’s laptop might have one or more profiles for the following:
Enterprise WLAN: Finance
Enterprise WLAN: Manufacturing
Home WLAN
Public Wireless Hotspot
Defining, configuring, and managing these profiles—the client’s wireless security settings—must be done in a scalable and supportable manner. If the security profile in your wireless network changes, you must have an easy way to update the client devices appropriately. Manually reconfiguring hundreds or thousands of devices is a costly and error-prone effort. The more client platforms you have, the more difficult this task becomes.
Many manufacturers do not address this challenge and instead rely upon the customer (you!) to handle it. As mentioned previously, most wireless clients come with specific client software, and some operating systems provide limited native wireless support. But this situation presents the enterprise with the unenviable prospect of configuring each make and model laptop and each operating system on a case-by-case manner. There are different ways to approach this task, as described in the following sections.
You can adopt third-party wireless client software and install it on every laptop, regardless of the wireless adaptor or operating system. As mentioned earlier, companies such as Meetinghouse Data Communications provide universal wireless clients that address this problem. Not only do they support most common wireless adaptors and operating systems, but they also provide centralized client and profile management. It is possible to clearly define, distribute, and update profiles for your entire client population.
The disadvantage of this option is that the third-party client software must be purchased for each device—that is, usually the third party charges a per-seat licensing fee. Conversely, this system can save the enterprise money in the long term by reducing the operational overhead of supporting and managing your various clients.
A centralized self-service model provides your user population with a one-stop shop for their wireless security settings. Usually a web page where any client device, regardless of operating system, can connect, this centralized location provides instructions on how to configure common settings or, in some cases, scripts that can automate the process for the user. This approach avoids the requirement for IT support staff to “touch” every client device, but it transfers the effort onto your users. Note that this approach can sometimes result in increased technical support calls to your helpdesk as users misinterpret instructions or make mistakes configuring their systems. However, it is more cost-effective and less resource-intensive than having your IT staff visit and configure each device manually.
Standardizing on a single client hardware platform will often provide the enterprise with a method of client security management. Some wireless adaptor and laptop manufacturers provide wireless client software with their systems. If you can standardize on such a system (be it a laptop or operating system), you might be able to use some basic centralized client management features to create and manage profiles.
Manually configuring clients for WLAN security settings is the least attractive and most expensive option. Indeed, it is really a “do nothing” approach. You leave it entirely up to your end users to configure their clients, whatever the client may be. The IT support staff simply publish or communicate the settings (EAP mechanism, SSID, and encryption protocol) used for the enterprise WLAN, and the users configure their own devices.
In some circumstances, you might need to have a manual process in addition to one of the previously described detailed options simply because a particular client device has no management features. ASDs (such as bar-code readers or wireless-enabled manufacturing equipment), for example, must be manually configured by your IT support staff. As such manual configuration is a costly but sometimes unavoidable option.
To successfully manage any network, timely and accurate information is required. Not only is current and up-to-date information necessary (that is, “snapshots” of the WLAN in its current state), but also historical reporting capabilities are required to help identify trends. Additionally, alerting capabilities are important. WLAN reporting includes three related areas, as described in the following sections:
Standard/systematic reports
Trend reports
Alerts
Standard/systematic reports are the standard set of reports that your network management toolset can generate on a regular basis. They are often called canned reports because they report upon common queries. Your IT staff can run these reports when needed or on a regular basis, such as daily, weekly, or monthly. These reports tend to be repeatable, with their reporting criteria remaining static.
Some examples include reports on the make, model, or configuration of access points in your wireless network, the number of access points in a particular region or theater, a snapshot report on the number of clients associated to a particular access point, the top ten traffic-generating clients or access points, and so on.
The following list includes more detailed possibilities for sample standard reports:
Detailed status
Associations
QoS details
Security settings
Per VLAN clients
Host name/IP address/MAC address/serial number
Power status
RADIUS authentications
Per VLAN Client report
EAP/MAC failed authentication
Failed authentication
AP memory utilization
AP CPU utilization
AP packet statistics
AP packet errors
AP radio utilization
Associated clients statistics
Ethernet interface utilization
Uptime
Note
Although it is impossible to list all aspects of WLAN reporting, the lists in these sections include some areas that you might want your WLAN management toolset or framework to monitor. These lists should not be considered exclusive or comprehensive but rather indicative of the kinds of reporting metrics. Values listed in the reports are examples only.
Trending reports are similar to standard reports, but they present the information over a period of time instead of as a snapshot. They are often presented in graphical format, showing how the reported characteristic has changed over a particular period, such as the maximum number of associated or authenticated clients on a particular access point, the CPU utilization of access point, the interface utilization on a particular port, and so on. As their name implies, trending reports identify trends and help ensure that your IT department can proactively plan capacity, upgrade, reconfigure, or fine-tune the network as the environment evolves and user behavior and network utilization changes.
The following list includes sample parameters for trending reports:
Group of access points
RF utilization
Ethernet utilization
Number of associations
Number of authentications
Number of failed authentications
Maximum client associations
Maximum client associations graph
Maximum percentage errors
Single access point
RF transmission statistics
Ethernet transmission statistics
RF and Ethernet utilization graph
RF and Ethernet utilization table
Top N busiest clients
Top N client error rate
Alerting is the capability to generate alarms when certain criteria are met. Alerts are useful to identify and remedy undesirable events. They enable reactive action on the part of your IT staff. When an alarm is created and your network management framework has been alerted, IT staff can correct (or in some circumstances, simply acknowledge) the problem.
Examples of common alerts include notification when the CPU utilization of an access point reaches 80 percent or higher, when the number of associated clients peaks above 20 users or devices, and when channel utilization is above 85 percent. They are excellent indicators of complications on the network and are often used to help direct the attention of your IT staff to problem areas, often before the user population realizes or experience difficulties.
The following list includes more detailed possibilities for alerts:
Access point
Do not broadcast SSID
SNMP reachable
CPU utilization above 60 percent
CPU utilization above 80 percent
Memory utilization above 60 percent
Memory utilization above 80 percent
Ethernet interface
Ethernet port status
Ethernet port utilization above 60 percent
Ethernet port utilization above 80 percent radio interface
RF port status down
RF port utilization above 30 percent
RF port utilization above 40 percent
RF port packet errors above 10 percent
RF port packet errors above 20 percent
RF port WEP errors above 10 percent
Max retry count 60 to 90 per interval
Max retry count above 90 per interval
Associated client count 15 to 30 per AP
Associated client count above 30 per AP
Associating rate 60 to 90 per poll
Associating rate above 90 per poll
Authentication rate 60 to 90 per poll
Authentication rate above 90 per poll
Interference detection (if possible)
Network/radio policies
Rogue AP detection (if possible)
Ad-hoc network detection (if possible)
Detection of 100 association requests over 15 minutes
You have many options for adopting a toolset for WLAN management. A robust WLAN management strategy is just as important as the actual tools used. So far in the chapter, you have learned about the various areas and topics that such a strategy should encompass. Now let us consider the actual tools that can help implement such a strategy.
Most enterprise-class wireless network solutions provide some native management features. These are often a combination of support for open management standards and dedicated network management products or appliances.
Dedicated, vendor-specific management systems are an important part of any robust WLAN management framework. Such tools are typically worth the price. The added functionality and management capabilities they provide not only help decrease the support burden on your IT staff (and thus decrease the cost), but they also assist in providing dedicated and specific management and reporting capabilities that are closely tied to the vendor’s equipment. In effect, they are tailor-made to monitor, manage, and report upon the particular vendor’s equipment.
Such tools typically come with canned reports that will reduce the need for your team to define their own. In some circumstances, they can be fully or partly integrated with existing management frameworks, avoiding isolation and the use of standalone management tools for the WLAN. Vendor-specific management systems provide such features as
RF management
Rogue AP detection
Host management
Configuration management
Image management
Interference detection
Wireless intrusion detection
Wireless planning and optimization
Examples of vendor-specific management systems include the following:
Several independent, nonvendor-specific tools are available that provide enterprises with dedicated wireless tools. Typically these concentrate on WLAN network analysis, reporting, and sniffing. They are used to monitor the WLAN, capture and analyze traffic, and provide detailed information about the RF environment. Rather, they can be used for rogue AP detection, interference detection, traffic analysis, security analysis, site surveying and planning and troubleshooting activities. They do not manage the infrastructure and cannot be used to configure WLAN controllers or switches.
Examples of third-party WLAN management tools include the following:
AirMagnet
AiroPeek
Sniffer Pro Wireless
Thales Air Defence
Wireless Valley LANPlanner
Helium Networks SiteScout and SiteSense
Fluke Networks EtherScope and OptiView network analyzers
Most large enterprise customers will already have an existing network management system in place, usually for their wired network and associated services and applications. In many circumstances, these can be extended to provide a modicum of wireless management, such as host monitoring and reporting of device status. They tend to not provide wireless-specific reporting and usually only monitor up to the access point. In effect, they are blind to the wireless side of the access point.
However, in some circumstances, these tools sufficient to address many of your basic needs. These tools will certainly provide reporting and alerting on the status of the access points and various WLAN controllers and management appliances (if you have deployed these). Finally, most vendor-specific tools can be integrated with common network management platforms. This capability allows the enterprise to continue to use the common network management platform as its primary toolset; the vendor-specific WLAN management tools can be launched directly from the common network management application.
Examples of network management platforms include the following:
CA Unicenter
Cabletron Spectrum
Tivoli TME 10
IBM NetView
SunNet Manager/Solstice
CiscoWorks
HP Network Node Manager
BMC Software Inc. PATROL Visualis
Many cross-technology, network-based management tools and standards can be used or leveraged in managing WLANs. You will perhaps find that some of these, such as SNMP (Simple Network Management Protocol), are already in use within your enterprise. Others, such as syslog or NetFlow, can depend upon your environment. These protocols are often leveraged by existing network management systems and in-house developed tools and scripts.
SNMP is the open Internet standard for collecting network management information on TCP/IP networks and is defined by the IETF 1157 RFC. It can also be used to configure certain settings.
Note
You can find all RFCs online at http://www.ietf.org/rfc.html, where you can search by RFC number. If you do not know the RFC number, you can find it at the IETF RFC index at http://www.ietf.org/iesg/1rfc_index.txt.
SNMP uses Management Information Bases (MIB) that define what information is available and what settings can be made. Each device will have a MIB that provides this data. The network management tool can then use SNMP to collect the information or make the changes that the MIB allows.
SNMP is very rarely used manually. It is a protocol for other tools and scripts. You will find that almost all network management tools and applications use SNMP in some way, even if it is hidden from the IT support professional.
SNMP is useful because it can also be used by custom-written tools and scripts that your IT support staff can develop. If these skills do not exist in-house, then it is advised not to manually manipulate SNMP settings on your network hardware.
Syslog is a distributed logging service. Originally written for the UNIX operating system, it is now common on many network infrastructure devices and systems. Unlike SNMP, which can be used to change settings or configure systems, syslog is a “one-way” protocol. It simply sends logging information to a syslog recorder. This recorder can then be used to review and analyze the logs. Syslog is a useful tool for collecting information, but it is not as robust as SNMP and could be considered an alternative if no SNMP skills exist within your organization but your staff is familiar with this protocol instead.
NetFlow is a Cisco standard for capturing and analyzing network traffic. It is typically used in large enterprises for accounting, network planning and analysis, monitoring (including application monitoring), and user traffic analysis. It does not normally form part of an everyday wireless network management toolset, but it is useful if your IT support staff need to review traffic patterns or troubleshoot esoteric or hard-to-define problems. NetFlow also forms the basis of the upcoming IETF IPFIX standard, which you can learn more about at http://www.ietf.org/html.charters/ipfix-charter.html.
AAA servers, by their very nature, provide accounting information on users being authenticated on the network. Most enterprise WLANs will require users to provide credentials and passwords before gaining access; the user must log on before using the network. Accounting information and AAA server reports can therefore be useful in helping your IT support staff optimize the network.
By analyzing AAA and RADIUS reports, you can sometimes identify problems that might have otherwise been difficult to discover. For example, multiple logon failures can point to a problem with a user’s credentials, timeouts for all users at a particular location can point to a WAN congestion, and so on. So although RADIUS accounting and AAA reporting are not management tools in themselves, the visibility they offer into the “backend” processes can often help in troubleshooting and fine-tuning your network.
Most network equipment provides varying degrees of “built-in” traffic analysis and reporting tools. Network routers and switches can be configured to collect data on traffic they handle. Statistics on IP packets and interface utilization can be generated. Each equipment vendor provides different methods of enabling these features.
This additional data can help in many ways, including capacity planning, fault identification, and resolution or simple troubleshooting.
Internally developed tools are those that are created by your IT support staff, usually using scripting and programming languages, that are specific to your enterprise. Because these tools are unique to each environment, there are few guidelines that can be offered. Some enterprises develop tools internally to plug gaps in their management framework. These tools could be automated access point configuration utilities that leverage a scripting language and the AP command-line interface to log on to the device and update settings, up to customized utilities that update or reconfigure client devices. They are often developed to leverage common network management tools and standards such as SNMP or syslog (for reporting).
Managing your wireless network falls under both the operating and optimizing phases of the solutions lifecycle. It is an ongoing effort that will help ensure the success of your WLAN.
When defining your management strategy, one of the first decisions you should make is whether to handle support in-house or to outsource this activity to a trusted partner. You can use the FCAPS model to help define your management strategy. The underlying architecture of your network will help guide you when considering centralized WLAN management versus a distributed model. Centralized WLAN management avoids having to configure and manage each access point but usually requires dedicated WLAN controllers or switches.
There are three common topics when considering WLAN management. You must be able to manage the RF portions of your WLAN, you must be able to manage the physical infrastructure or hosts, and you must also consider client management, which is often the most challenging aspect of all.
WLANs, by their very nature, are more difficult to manage than regular wired networks. Client devices on a WLAN are constantly on the move, create more load on your AAA as they repeatedly authenticate and reauthenticate, and are not as predictable in their location as normal wired network clients such as desktop computers. WLANs are also based upon radio frequency technologies, and radio is a very dynamic and constantly changing medium, subject to interference, contention, and environmental factors.
Another important topic that you should not overlook is managing the security framework of your WLAN. Because WLANs transmit their traffic via radio waves, you must ensure that you have a strong security architecture to maintain the integrity of your network and the data on it. Do not overlook security management because this is an area where you will most likely need to regularly audit, fine-tune, and revise.
You can address all these challenges with a robust management framework and tools. Many options are available to you, including those provided by the manufacturers of the equipment you installed all the way to independent third-party solutions that you can purchase and integrate with existing systems you might already have. Finally, do not overlook the possibility of using dedicated wireless diagnostic tools for your IT staff and even developing some tools and utilities in-house if you have the technical resources available.