The purpose of this chapter is to provide you with enough information to tackle the challenge of securing your WLAN infrastructure. This book repeatedly mentions the need for a security posture because security in your network is only as strong as the weakest link. This chapter provides an overview of key security components in WLANs, fundamental security vulnerabilities, key WLAN security standards, and security management challenges.
The fundamental premise of security in networked environments is that no network is truly secure. Even a network that is not connected to the Internet can be compromised if physical access can somehow be obtained. This point further drives home the point that there is no perfect way to secure a network.
To approach security, you need an awareness of the components that determine how to secure your infrastructure while maintaining an attitude of elevated paranoia. You should always assume that at some point in time there will probably be an attempt to break into your network with the goal of compromising intellectual property or disrupting your business.
Attacks don’t necessarily come from the outside. Research from the Computer Security Institute (CSI) and the FBI has shown that most security attacks come from the inside of an enterprise: (http://www.gocsi.com/forms/fbi/csi_fbi_survey.jhtml). (The document is free after registering at the CSI website.)
These attacks can be intentional, such as a disgruntled employee, or unintentional, as in the case where a computer is infected by a virus. The unintentional act is more likely to happen and probably more destructive. Armed with this state of healthy paranoia, you can strike the delicate balance between how much you invest to secure your infrastructure and the degree of difficulty an attacker needs to overcome.
The broadcast nature of a wireless network effectively raises the importance of authentication, encryption, and hashing. Starting with Authentication, you want to be sure that only permitted parties can communicate with your APs. Because you are effectively broadcasting your message over the ether, everyone can potentially hear every communication. Encryption is, therefore, needed to ensure communication privacy. Finally, the broadcast environment makes it relatively easy to capture, modify, and resend a message. Hashing your messages will address this problem.
Literature on information security typically uses the example of communication between two people. This section does the same, using the example of communication between Tony and Kelly. The specific security challenges that Tony and Kelly face when communicating are
Tony and Kelly need to know that they are indeed communicating with each other. This is known as authentication of the communicating parties.
Tony and Kelly want to be sure that only they can interpret the message exchange. Encrypting the messages into ciphers that only Tony and Kelly can decipher achieves this goal. Keys are used to lock and unlock the messages. These keys can be static or dynamic, and symmetric or asymmetric (Public/Private). The combination of the respective key characteristics determines how secure the solution is but also the computational cost.
Finally, Tony and Kelly want to be sure that the messages have not been tampered with while the messages were in transit. This is achieved by attaching a checksum (hashing) to the message that is recomputed and compared upon receipt. If the checksum is the same, the messages have not been tampered with.
It is not impossible to ensure secure wireless communications. Securing WLANs is possible if done correctly. However, heightened awareness is required to ensure that you don’t overlook a critical component and thus create a back door.
Depending on how you decide to combine the security elements mentioned in the preceding section, different security models are appropriate. This section describes the most commonly adopted models, which include the following:
By providing no method of authentication, encryption, or hashing, your network is most open to attack. However, an attack doesn’t necessarily mean that an individual wants to break into your network with malicious intent. It can also mean that an individual inadvertently attaches to your WLAN and uses your network resources.
Even though this model leaves you most open to unauthorized use of your WLAN, sometimes you will choose not to authenticate users or encrypt data. One such situation is when you want to provide your guests with WLAN connectivity.
Because WLANs use radio as a transmission medium, the first line of defense—physical medium control and containment—as offered by wired networks is not present. Indeed, LANs are somewhat protected by their physical structure, with some or all parts in a building or underground. To provide some kind of physical isolation similar to wired LANs, the 802.11b standard defined the Wired Equivalent Privacy (WEP) security protocol. WEP intends to provide some degree of privacy by encrypting the information between the radio endpoints.
Because WEP was designed when WLANs were in their infancy, it is not surprising to see that WEP turned out to be less effective than initially expected. WEP does not provide true end-to-end security because it only operates at the two lowest layers of the OSI model: the physical and data link layers.
Note
Any time you expose a standard to the general community, you risk compromising the standard because hackers can reverse-engineer the standard to develop an exploit.
In addition, WEP uses a static symmetric key to encrypt the data. The key’s static nature is a challenge because key management becomes complicated and a vulnerability is created that propagates to other parts of the security chain. Key management challenges include
Distributing keys
Supporting timed changes
Determining how to address the physical loss of end devices
Finally, WEP employs a key length of 48 or 128 bits. Given the continued and accelerated growth in computing power, standard desktops are now capable of quickly breaking these keys through exhaustive searches.
Authentication and authentication protocols control access to a network. Keep in mind that authentication does not secure the data that is transmitted on the network. Authentication protocols are designed to ensure that the user or device that is attempting to communicate is indeed whom it claims. It is analogous to a secured door in a large office building. By swiping your identity card, you are “authenticating” yourself. If the card is permitted access, the door is unlocked. Note that in this analogy, the card is authenticated, not the person carrying the card. Furthermore, the ID card does not provide security after you’re inside the door. As such, you can make the distinction between two forms of authentication: One is authentication of the user, and the other is authentication of the device.
User-based authentication is probably the most common form of authentication deployed in today’s enterprises. Users are given a password that only they are supposed to know. A system challenges the user to provide a username and password. After the pair is checked against a corresponding database, the user is either granted or declined access.
This method’s considerations and challenges include password strength and password management. Because in-depth coverage falls outside of the scope of this book, refer to other resources, such as Security and Usability: Designing Secure Systems That People Can Use by Lorrie Faith Cranor and Simson Garfinkel (O’Reilly Press, 2005), if you are interested in learning more.
Machine-based authentication goes a step further and verifies the identity of the devices that attempt to join your WLAN. Machine-based authentication is credential-based with the credential hard-coded in the device. This credential is a password of sorts for the machine. Like a person, the machine must be registered to be able to use the network. This credential is either derived or stored locally, or it can be dynamically assigned.
These methods will vary in complexity, but all are tied to an authentication service that is present in the core infrastructure.
The most common mechanism used by enterprises to secure WLANs is the incorporation of both encryption and authentication. Both can be provided in numerous ways. Authentication and encryption have evolved to combat numerous attacks, vulnerabilities, and protocol shortcomings. This evolution has also increased their complexity.
Data encryption can be achieved in many ways. Encryption can be performed using either symmetric or asymmetric, that is public/private, key pairs, and the keys can be either statically or dynamically assigned. Asymmetric keys are typically harder to break because it requires more computational horsepower. Similarly, dynamically assigned keys generate more computational overhead. However, the automation greatly simplifies key management. As the computing power of clients has increased, the encryption on the WLAN has evolved from the simple but hard to manage WEP to complex but easy to manage certificate-based key pairing. The later section “Encryption” will go into more detail on this subject.
Overlay security solutions employ higher levels of the OSI model to secure communications. Even at these higher levels, the same basic security features exist: encryption, authentication, and hashing. However, given the availability of additional information and embedded intelligence, the result is a higher degree of security sophistication. As such, Virtual Private Networks (VPN) and generic routing encapsulation (GRE) tunneling provide a more secure form of end-to-end communications. Both solutions work on the premise that a secure virtual communications tunnel is constructed between the communicating endpoints through which all data is securely sent. The use of an overlay security solution can sometimes cause disruption because the “tunnel” is a virtual point-to-point connection that needs to be reestablished anytime the connection is broken. Overlay solutions can also cause an added burden to the user or administrator. The user must complete an additional layer of security (setting up a VPN), and the administrator needs to manage all the virtual tunnels.
The nature of wireless communications makes defending against attacks very difficult but extremely necessary. Threats come in many forms. The vulnerability and exposure of your network comes from inside and outside your network. Arguably, the internal troubles typically outnumber the external threats.
Security threats surface as disruption in service, unintentional leaks, and industrial espionage. Both professionals and amateurs carry out attacks against WLAN security shortcomings, which is facilitated by a plethora of publicly available tools. Even then, it might not be a person but rather a byproduct of a careless design. The following describes three profiles of people who can compromise a network.
The malicious hacker—. This is the person who actively tries to exploit security weaknesses of the network. This person’s intent is to cause mischief, steal intellectual property, or cause business disruption.
The unaware employee—. The unaware employee is becoming more common. This is a person who has unintentionally opened a vulnerability either directly (such as by installing a rogue AP) or indirectly (such as acting as a catalyst for the spread of a computer virus).
The war driver—. War driving is when individuals or groups drive around and actively look for unprotected WLANs. In some cases, people mark the streets or sidewalks with chalk to indicate the presence of unprotected WLANs, which is also known as war chalking.
Now that we know who can carry out WLAN attacks, we will outline the different attack strategies that can be employed. The attack strategies are interception, rogue APs, and denial of service.
Because there is no physical link in wireless and because radio transmissions are not contained by physical boundaries, data can be intercepted. Any data that is intercepted is compromised as it can be reassembled, resulting in loss of intellectual property or exploitation of other safeguards.
You can, however, put security protocols into place to mitigate or thwart the threat of interception. This is covered in the next section. Interception provides a catalyst for malicious behavior in one of two ways:
Eavesdropping—. Data sent over a wireless medium can be captured over time. Given enough time, even encrypted data can be decrypted, although well-developed encryption techniques will extend this time from days to years.
Impersonation—. Commonly known as “man-in-the-middle” attacks, even when the data is sufficiently protected against prying ears, devices can be impersonated. This can lead to service availability attacks or inadvertent data capture with the latter leading to the possibility of encryption cracking.
Rogue access points are by far the most elusive culprits in a WLAN deployment. Many vendors are building solutions that will tackle the problem of rogue APs. Basically, rogue APs are internal or external to your network and can either create a security hole or cause enough interference to disrupt service. Internal rogues usually occur when an employee introduces an AP to the internal network.
Ongoing commoditization has resulted in a steep drop in the price of access points. As the cost barrier is removed, some people will not only purchase an AP, but also independently decide to “plug” the personal AP into the network in an attempt to gain more freedom and mobility. One way to thwart this problem is to provide ubiquitous WLAN coverage. However, you can’t be sure that this solution will stop the practice entirely.
Roque APs are typically not intentionally malicious, but require more effort to detect and mitigate. They threaten the network’s well-being and the integrity of the wireless space. Because WLANs rely on the availability of channels of the RF spectrum, having competing devices in the same RF space will likely disrupt your WLAN service.
A sometimes overlooked security threat is the overloading of the network that results in the inability to access the network. This Denial of Service (DoS) is a very real threat and can be easily carried out against a WLAN. These attacks, although usually intentional, can sometimes happen by accident. DoS as a security concern can never be ruled out because it can never be completely avoided. DoS has one critical effect on the enterprise: the denial of access to the RF space and thus the lack of network access. You learned in Chapter 2 that there is an opportunity cost associated with unavailability of network access. As the organization becomes more dependent on information and network access, this opportunity cost can rapidly escalate with downtime.
WLANs employ specific methods for encryption, hashing, and authentication. Figure 7-1 illustrates the general elements that make up the embedded WLAN security.
Encryption is the action taken to mask the elements in a data stream. This is done by applying a variable (key), which is known by a sending station and a receiving station, to an algorithm that encodes and decodes the transmission. In this section, you will find three basic flavors of encryption that have been applied to WLANs for securing over-the-air transmissions. Each is still suitable for use today. However, they are typically not used in Enterprise environments as they are insufficiently robust.
The initial encryption method was WEP, which provided sufficient protection in early WLAN deployments. Over the years, the ability and desire of people to crack encryption algorithms and break cyphers has increased. As such, more robust encryption schemes are continuously developed to offset weakened methods and to retain the possibility of secure communication. WLANs have thus seen the displacement of WEP by the schemes named CCMP and AES. Let us compare these three methods.
WEP is an encryption algorithm that is built into the original 802.11 standard. WEP encryption uses the RC4 stream cipher with either 40- or 104-bit keys and a 24-bit initialization vector. WEP was initially deployed as a static key written onto the client, which caused a burden on key management.
CCMP is a 128-bit keys cipher with a 48-bit initialization vector (IV), which helps prevent replay attacks. The Cipher Block Chaining Message Authentication Code (CBC-MAC) component of CCM provides data integrity and authentication.
AES was developed for securing sensitive but unclassified material by the U.S. government. By directive of the National Institute of Standards and Technology (NIST), a replacement for the Data Encryption Standard (DES) and to a lesser degree 3DES was commissioned. The specification required a symmetric algorithm using a block encryption of no less than 128 bits in size. Note that AES also forms the underlying encryption algorithm used in CCM. Its requirement and subsequent ratification by the U.S. government prompted acceptance by the general public.
The capability of AES encryption to remain protected is estimated to be years as opposed to weeks or days of current encryption methods.
Hashing prevents man-in-the-middle attacks as it ensures that messages that have been tampered with, while they were in transit, can be identified by the receiver. This is independent of whether the message is encrypted. This section details Temporal Key Integrity Protocol (TKIP) and Message Integrity Check (MIC), which we refer to as radio side protection throughout this chapter. Both of these are used to maintain the integrity of the information sent over the RF.
You can think of TKIP as a wrapper or enhancement for WEP. WEP is still the underlying encryption standard, but TKIP significantly improves the security by addressing its weak hashing capabilities. Using TKIP, every key is “rehashed,” effectively giving each packet its own key. Because the attacks upon WEP rely on capturing tens of thousands of packets that use the same key to attempt to identify the actual key, TKIP never reuses the same key. As such, it greatly reduces the risk of the key being discovered.
TKIP is also part of the WPA standard.
In order to combat the ability of a hacker to intercept, examine, and forward on a packet to an AP, there is a need to provide an additional layer of radio side protection. This is done through the insertion of an 8-byte MIC placed between the data portion of the 802.11 frame and the 4-byte Integrity Check Value (ICV). The MIC field is encrypted along with the frame data and the ICV. This is essentially a cyclic redundancy check (CRC) for wireless and is intended to prevent replay attacks, that is replay of an intercepted packet.
Table 7-1 summarizes the different security models described.
Authentication is the process in which the identity of a user or device is validated. This is typically done using passwords or certificates. Note that authentication assumes some degree of implicit trust. For example, the use of passwords assumes that it is only known by the authenticating entity. The same is true for certificates as they, in theory, can be handed off to somebody else. Furthermore, in the case of certificates, you need to trust the authority that extends the certificates.
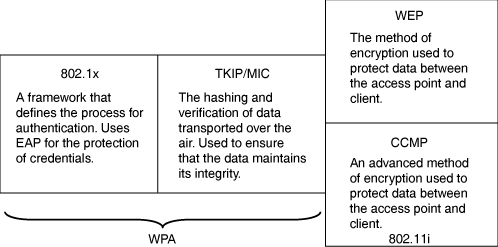
This book does not cover this topic in-depth. However, you should be aware of these nontrivial challenges regarding trust and authentication. In the remainder of this section, we cover the methods and frameworks that are commonly used in WLANs—specifically, 802.1x, Wi-Fi Protected Access (WPA), and 802.11i.
The 802.1x standard is a framework that defines a common process of communication for both wired and wireless LAN-based devices to initiate and secure point-to-point authentication. The 802.1x LAN standard can be applied to any subset of the 802 family. Its mainstream debut came at the time when WLAN products hit the mass market. Because standalone WEP was already known to be weak, 802.1x found a niche in which it could help to ensure the secure transmission of data in a WLAN. It is very important to understand that the standard only outlines the framework for communication. This freamework allowed vendors to provide various underlying authentication methods (which you learn more about in the section “EAP Types”), each with its own distinctive features.
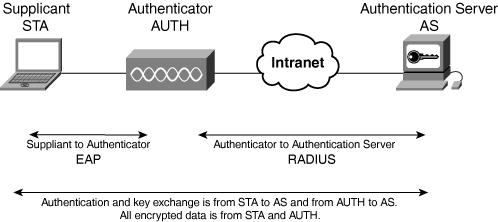
The framework defines mutual authentication of devices and recommends the use of RADIUS as an authentication protocol. There are three key components to the 802.1x framework:
Supplicant (STA)—. The client device that is requesting access. Typically this device is enabled by software, which performs the actual process.
Authenticator (Auth)—. Plays the role of the middle man, providing an entry point from an untrusted network to a trusted one.
Authentication server (AS)—. Acts as the validation point of contact. The authentication server maintains a database of all known authenticators and also maintains entitlement for the user or device. This user database can reside on a separate system.
The authentication communication between a client device and the authentication server is broken into two stages, as shown in Figure 7-2:
The first mode is Extensible Authentication Protocol (EAP), or EAP over LAN (EAPoL), which is the encapsulation format.
The second mode is RADIUS, where the credentials are passed for validation against the authentication database.
Note
In Figure 7-2, the supplicant can be any end device (laptop, desktop, PDA, phone). The authenticator can be a switch or AP.
Wi-Fi Protected Access (WPA) is a standard developed by the Wi-Fi Alliance primarily as a method for interoperability between Wi-Fi vendors. The Wi-Fi Alliance is a coalition of vendors with the charter of finding a common solution for wireless security. The WPA standard helps to mitigate the inherent shortcomings of WEP by protecting the transmission of data in the RF space by mandating the use of TKIP, MIC, and 802.1x.
WPA has two modes:
EAP and RADIUS in enterprise mode
Pre-shared keys (PSK) in non-RADIUS environments
WPA is built to support WEP as the encryption method, whereas the second phase of WPA, WPA2, supports the addition of CCMP for authentication.
Table 7-2 summarizes the features of the different WPA types.
Table 7-2. Differences Between WPA Types at a Glance
WPA Enterprise Mode | WPA PSK Mode |
|---|---|
Requires an authentication server | Does not require an authentication server |
Uses RADIUS protocols for authentication and key distribution | Uses shared secret keys for authentication |
Centralizes management of user credentials | Provides device-oriented management of user credentials |
Uses 802.1x as an identity framework | -- |
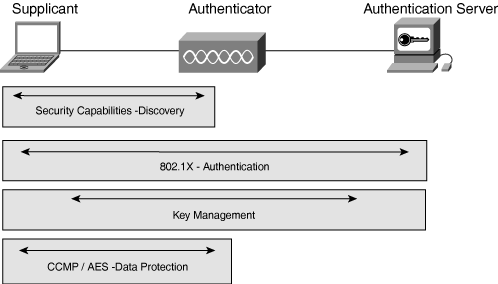
Based on WPA, the IEEE has ratified 802.11i as a wireless security standard to help provide a more robust method of protection. This standard introduces new and stronger encryption and hashing methods. It expands the initial validation (handshake) between the AP and client while still using 802.1x for the actual authentication process. 802.11i also mandates the use of AES. The principle enhancements are
Discovery—. A four-way handshake to authenticate the AP and client
Authentication—. The 802.1x framework for end-to-end authentication
Key management—. Method through which systems derive an encryption key that ensures integrity for the whole session
Data Protection—. Encryption of parts of the data packet
Figure 7-3 illustrates the relationship between these four parts of 802.11i. Each shaded area refers to one of the four functions listed previously.
802.11i uses EAP as the end-to-end transport for authentication and 802.1X (EAPoL) to encapsulate these EAP messages over WLANs.
During the discovery phase, participants determine the parties with whom they will communicate. The AP informs the client which security features are required to be used for communications.
Authentication employs 802.1x as a framework and further specifies the following:
The use of centralized network admission policy—at the AS.
Determination of the STA as to whether it does indeed want to communicate.
Mutual authentication between the STA and Auth.
Generation of a master key as a side effect of authentication.
Use of a master key to generate session keys.
Key management also uses the 802.1x framework with the addition of a four-way handshake, which ensures that the client and AP are valid devices (trusted). Because the session key used in client and AP transmissions is valid for the length of the session, an additional mechanism was added to the protocol to help maintain the integrity of the key. Specifically, the following actions take place (four-way handshake):
The Extensible Authentication Protocol (EAP) is a framework for sending authentication information and encryption keys from the authentication server (AS) to the client (STA) and AP (Auth). The authentication methodology—password-based, public key infrastructure (PKI), or certificate—is set by the organization.
The EAP session thus adopts the following event sequence:
A wireless client associates with an access point, which prohibits the client from gaining access to anything (except the authentication server) on the network until it has logged in and authenticated.
The client (STA) and AP (Auth) perform a mutual authentication (handshake). The AP receives an authentication request from the client and sends back a challenge. The client then completes this challenge. The AP then forwards the information to the authentication server (AS), using the client’s and AP’s credentials.
When successful, the client and authentication server derive an encryption key. The key can be derived in several ways, and each EAP type defines the specifics. Additionally, during the process, the client and server also derive a broadcast key. All data is subsequently encrypted using this key pair.
As a further measure to maintain integrity, the key pairs can be changed at regular intervals. The AAA server manages this function.
The following list describes different EAP types. Note that this is not a comprehensive catalog of all EAP types. However, it does include all the mainstream versions:
EAP-TLS (Transport Layer Security)—. Developed by Microsoft as a LAN-based authentication type.
EAP-LEAP (Lightweight Extensible Authentication Protocol)—. The Cisco version that was developed exclusively for WLAN security. It is also known as Cisco-EAP.
EAP-PEAP (Protected Extensible Authentication Protocol)—. Developed by Microsoft, Cisco, and RSA Security.
EAP-FAST (Flexible Authentication via Secure Tunneling)—. Second-generation WLAN security EAP type from Cisco.
EAP-TTLS (Tunneled Transport Layer Security)—. Developed by Funk Software and Certicom.
Table 7-3 summarizes the features of different EAP types.
This section provides guidelines for building a secure WLAN. These recommended practices are offered as tried and tested methodologies for addressing this challenging topic. Every enterprise comes with its own unique environment, infrastructure, and security challenges, but by following these suggestions and tailoring them to your specific needs, you can be sure that you have addressed the most common security issues encountered today.
One of your first decisions is whether your wireless network will be trusted or untrusted. This is an architectural issue, but it has a fundamental impact upon the security model you adopt. In the trusted model, you consider your WLAN to be an integral part of your intranet. The WLAN lies inside your secured fortress. In the untrusted model, you regard your WLAN as an extranet. The WLAN lies outside the secured perimeter of the organization. As such, you should make this decision very early in the planning or design phase of the PPDIOO lifecycle.
Trusted wireless networks are fully integrated into the existing enterprise network. It is assumed that the integrity of the network is implicitly protected. WLAN security is placed at the network edge, where the clients or devices authenticate and the traffic is encrypted. From a security perspective, trusted wireless networks are the preferred type of deployment today.
The advantages of a trusted WLAN include
Ease of use
Variety of EAP mechanisms
Possibility of single sign-on
Capability to roam across Layer 2 and Layer 3
Ability to support wireless voice and multicast traffic multicast traffic
In an untrusted wireless network, the assumption is that the network integrity is easily compromised. This assumption indicates that security does not exist or is incapable of providing necessary protection. Data in an untrusted WLAN is therefore considered “open,” and hence there is the need to be explicit about security.
The advantages of an untrusted WLAN include:
No differentation among traffic as all traffic is considered suspect.
Isolation of WLAN attacks as the WLAN is separate from the enterprise network.
No additional infrastructure is needed to support WLAN security.
A security posture is a framework of terms, protocols, standards, and policies that relate to protecting your wireless environment. It should at a minimum provide guidelines for
The particular encryption protocols you choose
The authentication method and standards adopted
Your password policy
A user access policy
A list of the devices and clients your WLAN will support
The critical steps of selecting an authentication mechanism and encryption strategy for your WLAN are discussed next.
Note
A common mistake when developing a security plan is to confuse authentication with encryption. Authentication is the process of validating an end user or device, whereas encryption is the function of hiding the original text in a cipher.
Earlier in this chapter, you learned about the two authentication types: user-based and machine-based. The most commonly adopted and recommended authentication mechanism is EAP. An added advantage of EAP is that it supports both types of authentication. Your choice of EAP type is impacted by many factors, including the following:
The client devices you intend to support
Your existing security policy
Your existing security infrastructure
The capabilities of your security system to support different authentication methods, especially different ones, simultaneously
Some EAP mechanisms make it extremely difficult to compromise a WLAN; however, they are correspondingly difficult to set up and maintain in large deployments. If security is of the utmost importance, this additional operational overhead is probably acceptable. On the other hand, some EAP mechanisms offer less protection and should not be seriously considered for an enterprise-class deployment. Carefully consider the tradeoffs between robustness of the authentication scheme, ease of management, and computational requirements on the client’s end. Unavailability of appropriate software on clients typically limit the type of EAP you can practically use. Supporting a wide range of devices adds more analysis of the EAP type selection process. Refer to the section “EAP Types” for more information.
The impact that clients have on your EAP selection are directly related to the following questions:
Does your enterprise certificate require a Certificate Authority (CA)?
Do you use shared keys, which require a public key infrastructure (PKI)?
What client platforms will you support?
What client authentication systems are you already using?
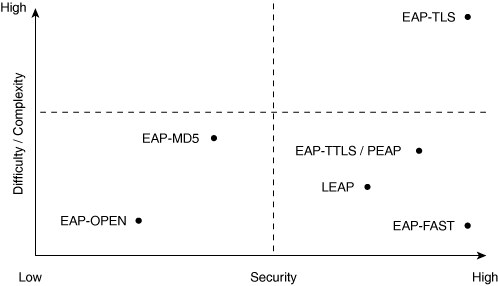
Different EAP types strike a different balance between complexity and security. Figure 7-4 depicts the trade-off for common EAP types.
Another significant decision for wireless security is choosing an appropriate encryption type for your environment. Although you might be inclined to choose the most secure option available, this choice might not be practical for your environment. Complexity, computational power, and user convenience are also key considerations. Yet again, a balance is required.
Currently, the most popular standard is 802.11i using the Advanced Encryption Standard (AES). AES’s benefit of robustness comes at the expense of increased computational overhead. Devices that intend to use AES should be foreseen of sufficient computing power so that they can process encryption transparently without negatively impacting other tasks of the device. Therefore, the more practical issue you need to consider is determining the most secure method that all your approved devices can handle given their existing compulational horsepower. An alternative strategy is to deploy multiple security types in function of the capabilities of the devices you support.
In any networked enterprise, it is important to have a password policy, and it is highly likely that you have already defined yours.
In some enterprise deployments, a completely separate set of user credentials is used to provide access to the wireless network. One-time passwords (OTPs) are a good example. Users do not enter their “native” credentials to access the WLAN; instead, they use a randomly generated OTP provided by a smart card or by software on the client device.
Just like any of the other security decisions you make, the password policy must take into account conflicting goals such as ease of use, deployment, and support (for users and devices).
Here are some considerations:
OTPs:
Select a smart card vendor or manufacturer if you have not already.
Consider the back-end infrastructure to support the OTP system.
Consider the operational overhead and support impact of deploying OTP software or physical smart cards to every user.
Native user credentials:
Implement a strong password policy that requires complex passwords: a mixture of uppercase, lowercase, and extended characters.
Require passwords that are longer than the usual eight characters.
Wireless-only alternate user credentials:
Consider the overhead of maintaining a set of alternate user credentials.
Consider the impact of users having to remember another set of credentials.
Alternatively, if you choose to store or cache the credentials on the device, you must assess the risk of them being compromised.
Note
There is an added risk concerning the protection of authentication credentials when they are cached on a device. Sometimes, however, this does not outweigh the benefits of caching credentials. For example, hospitals often store user IDs and passwords on devices so that doctors are not troubled with entering them.
Defining a clear and consistent security policy is an essential part of securing your WLAN. This WLAN security policy should provide quidelines for
Who has “ownership” of the RF airspace within the enterprise?
Who can install access points or WLANs?
What operating systems are supported?
What client devices are supported?
Note
A security policy is a collection of practices and guidelines that set a standard for behavior and use on the network. A security policy is different from a security posture in that a security posture represents a collection of actions that are used to provide a level of protection for the network.
Policies and procedures only set guidelines. As such, specific measures must be in place to reduce risk. Configuring your access points correctly is a critical step in securing your WLAN. We recommend that you specifically address the following parameters of access points.
As described in Chapter 1, “Introduction to Wireless LAN Technologies,” the Service Set Identifier (SSID) is analogous to a network name. It is used only to identify your network to client devices. Hence, it is not a true security measure. SSIDs are part of operational recommended practices. They are the first step toward compromising your network. Any default setting is an open invitation for malicious attack and therefore should be changed. An added security measure is not allowing your SSID to be broadcast openly. This measure helps to eliminate any accidental discovery of the SSID. If broadcasting the SSID is necessary (such as guest networks), it should be put into a separate network space, such as VLANs.
To secure your WLAN, you must also implement a policy to manage your APs so that standards can be updated and enforced. The following list outlines the essential steps:
Create a management VLAN—The management VLAN should be created on the wired interface of the access point. It is used to separate management traffic, such as SNMP and SSH, from data traffic. By limiting management to a particular VLAN, you can provide a more secure path for critical traffic to prevent it from being “overheard.”
Disable non-secure protocols—Specifically, disable the following protocols:
Telnet—. Although Telnet allows for remote administrative logon to the access point, it is not a secure protocol as it transmits all—including password—data in clear text. Disable Telnet on all VLANs, including the management VLAN.
HTTP access—. HTTP access to the access point provides users and operational staff with the ability to configure the device through a web browser. Once again, this is typically an insecure feature and should be disabled if at all possible. If your support staff absolutely must have HTTP access to the access points, then it should be limited to the wired management VLAN only. However, because the risk of transmission in clear text, we strongly recommend that HTTP access be disabled altogether.
Other non-essential management protocols—. Nonessential management protocols should be disabled. For example, if you are not using SNMP, RMON, or CDP in your existing network management framework, disable the protocols on the access points.
Enable secure protocols—Enable the following protocols:
Secure Shell Protocol (SSH)—. Provides the same functionality as Telnet (remote access to a command-line interface on the access point) but provides communication over a secure channel.
TACACS or RADIUS—. Use TACACS or RADIUS to provide a centralized authentication framework for device administration. This will mean you do not have to manage individual admin accounts on each access point and will ensure that you can easily update and control all administrative access to the wireless devices.
SNMP—. Simple Network Management Protocol (SNMP) is a set of protocols commonly used to manage network devices. If you use SNMP, you should configure strong and complex community strings and change them often. Additionally, you might want to consider using SNMP Read Only if possible because it will prevent SNMP devices from changing access point configuration; however, this might not be possible depending upon how you manage your network.
SNMP traffic should be limited to a particular list of host devices (SNMP network management tools) or subnets. IP address filtering (also known as Access Control Lists, or ACLs) is a common security feature, and in this circumstance, it allows you to limit the devices that will send and receive SNMP traffic.
Many access points and network devices allow you to configure Layer 2 MAC address spoofing prevention. This step prevents devices from using a MAC address other than their own. Many attacks are based upon spoofing a different MAC address, and this step will help mitigate that risk.
Note
Publicly Secure Packet Forwarding (PSPF) is a Cisco feature that allows you to prevent inter-client communication on WLANs. This means that two stations cannot consciously or, more importantly, inadvertently share files with others that use the same AP. PSPF allows network access to client devices without providing other capabilities of a LAN, such as peer-to-peer. This feature is especially useful for public wireless networks like those installed in airports or on college campuses.
Access points can transmit at various signal strengths. The higher the signal strength, the greater the distance that RF propagates, and therefore the greater the covered area. To avoid the risk of unauthorized users connecting to your WLAN, it is important not to let your radio signal “bleed” uncontrolably into the surrounding area.
By reducing the transmit power, you can more carefully manage your cell size and design, controlling the degree to which your WLAN extends outside of your physical building or office space.
Managing the power and range improves security by reducing the potential threats to your WLAN. Although this technique reduces the footprint that an attacker can use to exploit the network, it only prevents casual discovery. DoS attacks are still a possibility as an attacker can still transmit into your network causing radio interference.
Directional antennas allow you to shape the coverage area of your WLAN. Although not a security setting per se, directional antennas can, like reducing transmit power, help ensure that wireless coverage does not bleed into areas that you do not want to cover. Even when physical and logical security are tight, there is no reason to extend your footprint into uncontrolled areas.
You should physically secure the access points. Many manufacturers provide mounting brackets that allow you to physically lock down access points. This is important because access points can contain information on the configuration of your network. Ensuring physical security of the device not only protects your capital assets but also removes one more potential area where attackers can target your deployment.
The authentication, authorization, and accounting (AAA) architecture you use is important for all network security, and WLANs are no different. WLANs require a method to authenticate users and to manage an encryption key exchange. AAA systems provide the industrial strength authentication management system needed to support this in a scalable and resilient fashion. As a backbone service, the AAA systems need to have a breadth of support for EAP types and must be scalable.
Remembering that EAP is the recommended method for securing the radio transmissions of your WLAN, you should ensure that your AAA service can support an EAP type. The EAP family of protocols is “extensible,” meaning many varieties are available, including several proprietary versions. Some AAA servers do not support all EAP mechanisms. If you already have an existing AAA server in your infrastructure, it is crucial that you ensure that it supports the EAP mechanism you choose for your WLAN. Alternatively, you could install a dedicated AAA server or servers for WLAN use only. However, this is likely to be cost-prohibitive because more devices need to not be acquired but also managed on an ongoing basis.
Like all centralized services on a network, it is important that your AAA infrastructure is scalable and stable. Because AAA servers are fundamental to a secure network, their availability and reliability are essential for a secure network. If you are deploying a large-scale or global network, it’s important to plan your AAA architecture accordingly. Centralizing all authentication on a single system is not good practice; it’s better to use a distributed system with several AAA servers to avoid a single point of failure. A distributed AAA architecture not only has better resilience and disaster recovery capabilities but also provides the added benefit of load-balancing among available AAA servers. In global deployments, for example, it’s common to have AAA servers regionally dispersed. Not only does this ensure that you have a resilient system, but it also keeps authentication traffic regional.
Some solutions allow AAA services to reside locally, which means that the authentication is performed on the AP or switch servicing that WLAN. This solution can be attractive for very large-scale deployments where you might have hundreds or thousands of local WLANs (for example, small retail stores or bank branches).
Remember that losing connectivity to your AAA server means that users cannot authenticate; therefore, the WLAN—as a transport medium to the network as a whole—is unavailable. As such, a robust AAA architecture is essential.
A necessity of any network is ensuring physical security of the environment. Your wireless network is no different and in some cases can be considered more susceptible to attacks by intruders because APs are typically not placed in secured wiring closets, but rather in open areas. It is therefore essential, for many reasons, that you have good physical security in your office space and adjacent areas.
Note
Many large corporations have sizeable parking lots or public areas that surround their office buildings. It is prudent to make your security staff aware that uninvited or “suspicious” visitors might be attempting to eavesdrop on your WLAN. Educate them to be aware of potential war walkers and war drivers.
A robust wireless security posture, a strong wireless security policy, and comprehensive security procedures are all devalued if your user population is unaware of them or ignorant of the risks of poor behavior. As such, communication with your users about security is a fundamental aspect of securing your WLAN. The vast majority of your users will be welcome partners in your ongoing security efforts if they are engaged successfully and educated on how to help.
Consider using multiple communications methods to provide your user community with a comprehensive source for information about the wireless network. Include FAQs, user education documents, WLAN news bulletins, deployment updates, and even links to software and external resources. We recommend that, at the very minimum, you engage in communications with your WLAN users regarding the following three topics:
WLAN security policy—. Your wireless security policy should be clear and concise when communicated to your users. Make the policy easy to understand and free from as much technical jargon as possible.
Fundamentals of wireless—. Educate your users about the benefits and the fundamentals of wireless networking. The vast majority of users will work with you to secure your network through responsible actions. For example, when people understand the risks associated with rogue access points, most will refrain from installing them. Treat your users as partners, and they will greatly assist you in securing your network.
Updates on security developments—. Your network users are best served when they know what developments happen in the wireless security world, including current risks, common types of attack, and possible intrusion efforts (hacks). Network security is a constantly evolving area with new attacks and tools being developed continuously. It is important to remain aware of developments in this area and pass that information on to the user community in a timely manner.
If your company provides remote access services to your users, then a home wireless networking policies and guidelines are recommended. Many large enterprises allow their users to connect to the corporate network from home. In many circumstances, these remote access services are provided not only by standard analog modems but also by “always on” high-speed connections, such as cable modems, xDSL, ISDN, and even dedicated Frame Relay or WAN links. In all cases, it is very important to publish strict guidelines on the acceptable use of wireless devices at the home. Consider that these services effectively extend the corporate network to your users’ homes. The WLAN access point that is installed at the home is no different than a rogue AP and hence brings along the same risks.
The different strategies for mitigating these threats are discussed next. Note that not all the solutions enable the full extension of the corporate network to the WLAN-enabled home.
A policy decision could be made simply to ban the use of wireless access points on corporate equipment at users’ homes. This is in some ways the easiest solution but the one that has the most negative impact on the user. However, any such ban needs to be preceded with education on the merits of such a position.
A list of recommended or supported WLAN devices can be created, with specific configuration guidelines for each. Your users can then configure their access points using the instructions provided to conform with corporate security requirements.
A list of recommended practices specifically for home wireless networking can be provided for your users. These best practices might not provide detailed configuration guidelines for every make and model of access point, but they should provide the users with advice on the “high-level” concepts of configuring their devices securely.
Provide a simple step-by-step guide such as the sample presented here. A dual approach consisting of a “quick setup” as well as a more comprehensive and detailed version is ideal:
Change default SSID—Your access point will come with a default SSID when you install it. Change this as soon as possible to avoid the compromise of the AP.
Disable SSID broadcast—Access points broadcast their SSIDs by default. This is not necessary for most home wireless networks. Disabling this feature will not allow neighbors to easily discover your home WLAN.
Enable WPA-PSK—Most access points now support WPAPSK (Wi-Fi Protected Access – Pre-Shared Key). This encryption and key management standard greatly increases the security of your home wireless network. WPA-PSK is configured on both your access point and any devices you use on the wireless network (desktop and laptop PCs, and so on). As it is configured by using a shared secret on all devices. Create a shared secret that is at least 20 characters long and not easy to guess.
Change the default admin login password—Change the default password for the admin account on your access point to avoid unauthorized users gaining the administrative access that allows configuration of the AP. The default password is well known and hence it defeats its purpose. Change it to something only you know or will remember. Choose a strong password and not one that is easy to guess such as “password” or “1234”.
Change default IP address—Access points come pre-configured with a particular IP address when they are installed. Typically, it is 192.168.1.x (where x is a number between 1 and 254). Most hackers are familiar with these IP addresses. You should change this value and choose an IP address in the range 192.168.x.1 (where x is a number between 2 and 254 to make it harder for a hacker to infiltrate your network). For example, you could change the default IP address to 192.168.153.1.
Reduce DHCP scope—Home wireless access points usually act as Dynamic Host Configuration Protocol (DHCP) servers. This means they provide your desktop or laptop with an IP address when requested. Most access points provide IP addresses from a “pool” of available numbers. This pool can contain up to 253 IP addresses. Because you are likely to have only a handful of devices requiring an IP adress, consider reducing the DHCP pool number. For example, if you have only a single laptop you want to use on your home WLAN, you could reduce the DHCP pool to only one or two addresses. This change will reduce the risk of unauthorized users from accessing your WLAN.
Reduce transmit power—Most access points transmit at the maximum power possible when initially installed. This sometimes has the unwanted result of expanding the coverage of your home wireless network outside or into neighboring areas. Reduce the transmit power to provide only the coverage you require.
Use static IP addresses—Assigning individual IP addresses to end devices and disabling DHCP will help control who has access as you limit the possibilities for unwanted people to access your network.
Enable MAC address filtering (advanced and optional step)—It is possible to configure most access points with a list of MAC addresses that are the only ones permitted to use the WLAN. With this technique, you effectively “filter” the network and only allow the devices with the MAC addresses you select. This technique helps prevent unwanted users from accessing your home wireless network. Be sure to select the correct MAC address (the one of your WLAN NIC) if your computer has more than one network interface.
Disable web access (advanced and optional step)—You can disable web access on your access point. By doing so, attackers cannot log on or configure your access point using a web browser. Note that this means you also will be unable to log on to your access point and will have to use the command-line interface thereafter. Therefore, this option is suitable only for advanced users.
Mobile devices such as PDAs and “smart phones” present their own security challenges. A policy and support plan for these devices is recommended for every corporation. If you choose to support these devices on the wireless network, you should ensure that they, like the rest of your client devices, are detailed in your security posture statement. Many issues will need to be addressed including, but not limited to, the following:
One of the most difficult aspects of an effective and successful WLAN deployment is client management. This ability to control—both physically and logically—the expectations and capabilities of client devices is paramount. The threat of a client performing actions that mimic an AP is serious because this is sometimes the cause of DoS attacks. To mitigate any possibility of the client device being the weak link in the security of the WLAN, there also must be active control as to which clients are supported and what their abilities are.
Beyond developing a policy and list of supported client devices, the policy needs to outline attributes of the devices. Controlling these attributes helps to ensure that devices not supported in your security policy are not permitted on the network, thereby strengthening your overall security posture.
You should consider the following three aspects of a client device:
Platform—. Define what platforms are supported. This not only includes the make and model but also specific wireless adaptor cards that client devices may use.
OS—. Specify a list of supported operating systems and the particular revision level. This will not only ensure a consistent and uniform security posturebut also make it easier for your operations staff to isolate problems as several degrees of variability are removed.
Client software—. Define a single common wireless client software application. This can be as simple as selecting the native client capabilities in the operating system (Windows XP Wireless Networking, for example), the client software provided with mobile devices and laptop computers, or a standard third-party client for use across all devices (such as that offered by Funk or Meetinghouse).
Although not specifically a wireless issue, user laptops and desktops should be provided with regularly updated anti-virus software. WLANs, just like any network, can propagate viruses if the client devices are not configured with appropriate software.
Some wireless software is available that allows a laptop or desktop computer to act as an access point. This software-enabled access point or soft AP is considered a major threat because it is usually a trusted device. The soft AP creates the same security threat as the unauthorized installation of rogue access points. In some ways the soft AP can be a more dangerous threat because many hackers will use them to stage attacks. As the successful hacker can turn any computer in an AP, he is not tied down anymore by the physical placement of regular APs. In essence, the soft AP could enable a hacker to place an AP wherever there is a computer. As such, we recommend that you disallow the use of this software capability and make it very clear in your wireless security policy that such software is unacceptable. Actively detecting soft APs is very difficult and this is another reason why radio-based rogue access point detection is of critical importance.
Rogue access points are access points that are located within your enterprise and that were not installed by your IT department or approved vendors. They present a very serious security threat when connected to your network as they are improperly configured with little or no security settings.
A robust rogue AP detection system is critical for any secure wireless network. Indeed, rogue AP detection is critical because there is no such thing as a “non-wireless” network anymore; if you haven't deployed a WLAN, you can only assume that there is no WLAN as staff are purchasing cheap access points and installing them themselves, often without realizing the security implications.
It should be noted that the vast majority of rogue access points come from your own users, and only a small minority are from malicious hackers. Most user-installed rogue APs are not intended to compromise security but are attempts at benefiting from wireless networking without realizing the risks of poorly configured devices. If you have a comprehensive entitlement policy and wide coverage area, you will reduce the likelihood of rogue APs being installed in the first place.
Detecting rogue access points can be challenging. A combined approach of client-based reporting, radio-based detection, and network scanning is the best method.
Client-based reporting can be as simple as asking your users to report suspicious access points to the IT department. These can be nonstandard (enterprise) AP models, APs in unusual locations such as hidden under desks, and consumer-grade access points on desks or in cubicles. This reporting will allow your IT team to investigate and address the threat if it turns out to be real.
Additionally, some solutions now available on the market allow for wireless clients, such as laptops, to actively and automatically report a list of access points they have encountered to back-end management system. This reporting is entirely transparent to the user, but it allows your wireless management framework to construct a picture of all the access points in your enterprise. If an access point is reported but is not listed or managed by your network management system, there is a chance that it is a rogue.
Radio-based detection uses your own access points, or dedicated scanners, to actively monitor the RF spectrum and report all radio devices they detect. Effectively, your access points are “auditing the airwaves” and drawing up a picture of the radio frequency use in your enterprise. Most of the leading manufacturers provide radio-based rogue access point detection services with their products. These often have the advantage of providing you with a graphical representation of what your radio network looks like, using floor plans and colored cells or clouds to represent each 802.11 cell.
Radio-based detection can also be carried out manually by IT staff using handheld wireless network analyzers or laptops with software designed specifically for this purpose. These include popular tools such as AirMagnet, Kismet, and AirSnort.
Network-based detection is the third essential pillar of a robust rogue access point detection system. Network-based detection uses internally developed or publicly available tools to scan the wired network for devices that match a particular signature or “fingerprint.” These devices scan for familiar MAC addresses, specific open TCP ports, and particular protocols and processes that might be running on a device. These tools can even attempt to log on to the device and note its response. By combining several criteria and automating the process into regular scripted jobs, network-based reporting can quickly produce a list of suspicious devices. Your IT department can then use this list to investigate the devices and act accordingly. One of the most popular publicly available pieces of software that can be used for this purpose is WinFingerPrint (http://winfingerprint.sourceforge.net/).
After you have identified a rogue access point, you need to act. The potential responses can be categorized under three headings: remove, reclassify, and remediate.
You can remove the rogue access point from the network. You can achieve this by disabling the network switch port to which it is attached (if applicable), or you can confiscate the device or instruct the owner to comply with your IT polices and power-off or remove the rogue access point. If the device is not physically within the confines of your enterprise, you might need to “work around” the problem and reconfigure some of your access points to remove the interference and contention.
You can reclassify many rogue access points, especially those identified during the initial discovery phase, as friendly and therefore no longer a security risk. Friendly APs can be those that are internal to your network, such as those in labs. Conversely, friendly APs can be external, such as those in shared office spaces where another company manages and controls the APs. Keep the knowledge of the function or ownership of these friendly APs for reference later when you audit rogues.
Finally, you simply might want to remediate some rogue access points and ensure that they are supported by your IT department and have the correct configuration. This choice can be due to a valid requirement for WLAN coverage in a particular area, or it simply can be due to a bad configuration in an access point that was officially supported.
Many corporations opt for dedicated wireless intrusion detection systems (wireless IDSs). Many leading wireless equipment manufacturers also provide this service with their solutions. Wireless IDSs are a more advanced and dedicated approach to radio-based rogue access point detection. They often use dedicated “scanners” (often access points themselves, but sometimes cheaper scan-only devices) and specialized software. They can also be used to detect client behavior that you might want to prevent, such as the creation of ad-hoc wireless networks and client-to-client file-sharing networks.
Wireless IDSs provide a very good level of security and are often used by corporations that want to restrict or ban the use of wireless networks entirely. However, every large-scale enterprise-class network can benefit from the added security they provide.
This chapter outlined the many threats to security that happen both intentionally and unintentionally. These are vulnerabilities that you can avoid through proper planning and education. Today’s threats include the interception of encrypted data and denial of service attacks. This potential negative business impact has created a great deal of emphasis on security practices, protocols, and the ability to protect against malicious attacks. The risk, however, does not stop there—considerations in the policy and methodology of WLAN security protection must also act as a defense against casual or incidental acts that result from the unaware employee or user.
Today, WLAN security is built on identification of the client, authorization of the user, and encryption of the data. Because wireless communication cannot be perfectly confined to an area, this three-tiered security framework is essential for protecting the WLAN. 802.1x is the foundation framework for the authentication process and is aided by EAP. Over time, many different standards have evolved with the intent of protecting the WLAN. Currently, 802.11i has become the newest standard being specifically developed for the WLAN to address security. WLAN security will continue to be one of the foremost considerations when building a WLAN solution for the enterprise. This chapter covered the fundamental information needed to develop a holistic and robust security plan for the WLAN.
The WLAN must be protected through preemptive actions. This begins with building standards based on best practices for the configuration of the client and AP. Further efforts are put into securing the physical space, monitoring for rogue APs, and taking charge of the airspace. Underpinning all these efforts is the ability to provide client education and to ensure that the integrity of the network remains intact by thwarting accidental events.
Finally, you should be able to place as much trust in the security of the WLAN as you would with the traditional wired network. No solution is infallible, but with proper planning, education, and monitoring, you can feel safe with whichever solution you deploy.