Chapter 2, “Business Considerations” discussed the value of mobility in your organization and provided frameworks for identifying the specific areas where WLANs can be most beneficial. You learned about the mobilization of existing applications as well as applications that you can successfully enable and leverage when a WLAN is deployed.
Chapter 2 did not discuss all applications and services that a WLAN can enable. Although some applications and services are important in today’s business environment, they are not critical for WLANs. Consider these as “nice-to-haves” instead of “must haves” in your WLAN.
This chapter introduces you to these supporting services. The chapter outlines what the benefits of these services are, why they are more challenging to make available, and which recommended practices should be considered for provisioning them.
The services under consideration can roughly be grouped into two sets:
Supplementary WLAN services make use of the transport mechanism provided by WLANs to provision a higher-order application. Voice and video fall within this category.
Complementary WLAN services extend the availability of the transport system at the device level. The accessibility of the WLAN is expanded to a larger user community or the WLAN is used for device-specific procedures. Guest WLAN access and RF location services are examples of complementary services.
The rationale for layering supplementary services onto your WLAN is that it increases the value of your WLAN for your user community. The transport medium becomes completely transparent to the user, and the entire application suite that is available on the wired networks is made available on the wireless network. The WLAN thus effectively mobilizes all your applications and users.
Regrettably, this mobilization is not always easy to achieve because some applications are substantially harder to transfer to a WLAN environment. For example, voice and video are real-time and latency sensitive applications that demand deterministic network transport. Chapter 1, “Introduction to Wireless LAN Technologies,” revealed that WLANs are susceptible to many internal and external influences. The number of WLAN users, physical obstacles, and other devices that operate in the same frequency band all have an impact on throughput and latency. As such, it might seem like a dichotomy to plan to deploy voice and video applications on a WLAN. This chapter shows that this is not the case.
The situation for complementary services is slightly different. Because you will already have deployed a WLAN, you can extend its application to additional services, thereby increasing the value you derive from this technology. Many of today’s organizations are characterized by a high degree of fluidity in terms of individuals visiting office locations. Customers, consultants, and temporary staff are all examples of people who come and go on a daily basis and who could benefit from basic Internet connectivity. Guest networks become a viable complementary WLAN service for this transient community because it provides public hotspot-like connectivity. This chapter covers the benefits and challenges related to supporting guest WLANs.
A final complementary service that this chapter discusses is WLAN location services, which use the WLAN to determine the physical location of WLAN-connected devices. This chapter concludes by covering some of the benefits of location services as well as common implementation considerations.
Voice over IP (VoIP), which enables telephony over an IP infrastructure, is a complex topic in its own right. Given the importance of VoIP technology, this section explains the basic considerations for enabling VoIP on your WLAN. Refer to the “Additional Resources” section at the end of this chapter for books that cover VoIP, which is a communication protocol, and IP telephony, which is a communication application, in more detail.
Many of the benefits that are found in wired VoIP are directly applicable to wireless VoIP. Strategic benefits include the enabling of rich-media content integration and distribution. Operational advantages consist of ease of maintenance and support through consolidation of the PBX infrastructure and avoiding the need to support an additional technology. Lastly, financial gains can consist of reduced toll-charges by routing internal calls across the organization’s network instead of the public network.
The challenges of enabling telephony over IP are in the IP protocol itself. Basic IP is by design a best-effort protocol. No distinction is made between the types of communication sessions and no guarantees are made regarding timely delivery of packets. E-mails, web traffic, voice, and video are by default all treated as equal. IP will only try to deliver the packets, and the handling of dropped packets is left up to the applications. Therefore, some higher-order mechanism is required to enable more deterministic behavior of the best-effort protocol. This is the domain of quality of service (QoS). QoS refers to a collection of tools and techniques for classifying, marking, and providing priority handling of traffic.
Classification of traffic is done based on parameters such as protocols, network addresses, devices, application types, or even time of day. Marking of Layer 2 frames and Layer 3 packets is then performed to enable different priority processing of traffic. QoS mechanisms thus effectively engineer the traffic so that it exhibits a more deterministic behavior. WLANs employ 802.11e, a standard that was ratified by the IEEE in 2005, to provide Layer 2 QoS enhancements for WLAN applications by augmenting the IEEE 802.11 Media Access Control (MAC) layer.
802.11e provides two different types of enhancements. Both types enable the creation of traffic classes. However, the granularity with which these classes can be manipulated is slightly different. Enhanced Distributed Coordination Function (EDCF) is the simpler version of 802.11e and only provides a best-effort QoS. The more complex version, named Hybrid Coordination Function (HCF), offers more granular configuration possibilities, but has not been widely deployed.
Note that Wireless Multimedia (WMM) is an alternative WLAN QoS standard defined by the WLAN Alliance. WMM can be considered to be a subset of 802.11e. It was developed while the industry waited for the IEEE to ratify 802.11e. Now that this ratification has occurred, WMM is less of a consideration for new deployments. However, it is still a supported technology by many vendors.
Even though many of the VoIP benefits and challenges are shared between wired and wireless LANs, some challenges are either unique to WLANs or compounded by the nondeterministic behavior of wireless networks. The following sections focus on these unique challenges by taking a closer look at WLAN voice devices as well as specific hurdles that must be overcome to enable VoIP on WLANs.
Telephony is traditionally associated with dedicated devices. These devices are the handset that you encounter on desks or mobile telephony handsets. However, the advent of VoIP has made it possible to convert any general purpose computing device into a telephone. Today, telephones not only come in hardware, but they also come as software applications. These software versions of phones are colloquially known as SoftPhones. A SoftPhone application can effectively turn a desktop, laptop, or PDA into a fully featured telephone. Hence, you should not consider dedicated WLAN telephony handsets as the only viable alternative for WLAN VoIP.
Various vendors manufacture and sell these WLAN VoIP handsets, and they look and feel like traditional mobile handsets. The difference is that they use 802.11 instead of analog radio as the transport mechanism. This is similar to the IP phones that you find on desks which use 802.3 instead of analog TDM.
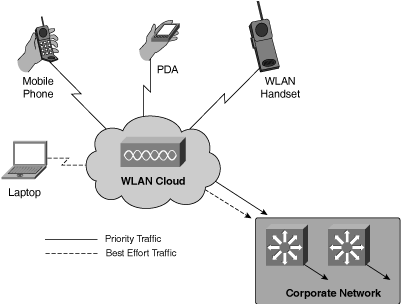
To enable consolidation of mobile telephones, several vendors are currently working on dual-mode handsets. These handsets are capable of interfacing with both WLANs and cellular networks giving users the option to select the most cost-effective connection. Cellular phones are likely to soon form an integral part of voice devices that your WLAN needs to support. Figure 4-1 summarizes the many different types of WLAN voice devices that you can encounter.
Figure 4-1 shows that WLANs can mobilize voice on devices that traditionally are not considered as mobile telephony devices. Remain sensitive to this fact and include your strategy for supporting these devices and telephony in your architecture and design. Chapter 5, “Guidelines for a Successful Architecture and Design,” covers this topic in greater detail.
The nondeterministic behavior of an IP network can plague the deployment of telephony in the IP environment. Specifically, latency caused by the nondiscriminating network as well as dropped IP voice packets can have a significant detrimental impact on voice quality. WLANs compound these challenges in three ways. The first two are caused by the shared nature of the medium. Not only is available throughput shared among users, but access to the medium is also granted on a first-come, first-serve basis. The third challenge relates to the speed with which wireless voice devices can roam from cell to cell.
Whereas bandwidth and latency considerations are important in wired networks, they are critical in wireless environments. The focus in this case is edge connectivity because backhaul connectivity is assumed the same irrespective of the wired or wireless connectivity provided to the end user.
The contention that occurs in wired VoIP environments for network access is between different applications on a client that require network access. The client is connected via a dedicated connection to an access switch, and applications compete for access to the network. QoS mechanisms can be used to classify, mark, and provide priority queuing. This alleviates many of the bandwidth and latency challenges in wired networks.
Unfortunately, this is not the case for WLANs because they share access to the transport medium among all connected stations. As such, contention for airspace access occurs not only inside of the client, but also between the clients. Even though a client could provide a higher priority queue for its time-sensitive applications such as voice (and video), the client must still compete with neighboring clients for airspace access.
Because of the aforementioned situation, it is difficult to guarantee timely access to the medium for voice traffic. 802.11e extends QoS mechanisms to the WLAN Media Access Control (MAC) layer to increase the probability of gaining access to the network. The simpler method, EDCF, is a “best effort” QoS method where high priority traffic is given a slightly higher transmission probability than lower priority traffic.
The more complex type is HCF, which is the 802.11e version that provides features like bandwidth control, fairness between stations, classes of traffic, jitter management, and so on. As such, WLAN QoS can be configured with much greater precision with HCF. Even though this method provides more granularity, it has not been widely implemented yet due to its complexity.
If voice is indeed a critical application for your environment, ensure that both QoS as well as sufficient bandwidth is provisioned. Avoid situations where many clients are part of the same cell because this will prevent excessive access contention. Chapter 5 provides strategies for determining the appropriate number of access points for your environment.
A challenge that is unique to WLANs is that of roaming clients. Stations that are on the move transfer their association from one access point to another. When this transfer occurs, the device must re-authenticate with the authentication, authorization, and accounting (AAA) infrastructure, thereby introducing a possible momentary interruption in service. This is especially noticeable in voice applications where any interruption can result in lost packets and a corresponding impact on voice quality.
WLAN vendors have addressed this by introducing fast Layer 2 roaming, which reduces the time to re-authenticate (usually to less than 100 ms or so) as the station moves its association from one access point to another. This fast roaming capability limits the disruption of the voice stream as packet loss is minimized.
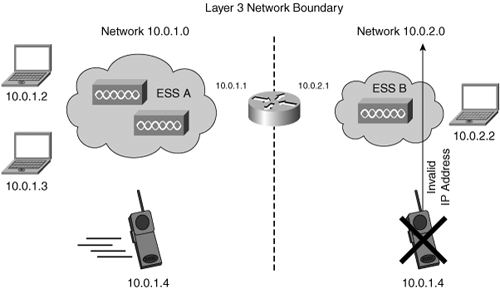
An additional challenge caused by roaming occurs when a station crosses an Extended Service Set (ESS) boundary. When a client transfers its association to an AP in a different ESS, it effectively moves into a different IP subnet. This is known as Layer 3 roaming, as the client device has moved from one IP subnet to another. Routing issues arise as the station’s old IP address is invalid and VoIP sessions can terminate under these circumstances. If no additional measures are taken, the active call will be dropped. Figure 4-2 illustrates the effect of mobile VoIP handsets roaming across ESS boundaries and the resulting invalid IP address in the new ESS.
Given that most organizations have far more than a single ESS, roaming with mobile voice devices can become a significant challenge if not addressed in the architecture. Multisite or campus locations will have a hard time maintaining voice sessions throughout the campus. Various solutions do exist to address this roaming challenge, and each has its benefits and challenges. These include Mobile IP Protocol and “predictive” tunneling solutions. Almost all vendors have moved to some type of tunneling technology to solve the ESS roaming problem. The tunneling solutions are essentially the same as those discussed later in this chapter for constructing guest networking solutions. Mobile IP is typically deployed only in difficult environments such as moving vehicles.
Voice on WLANs brings along a number of considerations that are not necessarily related to the network, but rather to the physical attributes of the devices. These considerations include battery life and physical security of the clients.
Battery life is important no matter what kind of mobile device you use. It is especially significant when contemplating voice because voice is a real-time form of communication. It is certainly more annoying to lose an active voice session due to battery power depletion than having your laptop warn you of an impending shutdown.
As always, remain sensitive to security of the device. As opposed to a laptop or desktop, mobile voice-enabled devices are typically smaller and harder to physically control and secure. Security of mobile voice devices should not necessarily be thought of in terms of compromise of your network. Authentication information could indeed be extracted from the device facilitating other attacks. A greater liability is the information that is stored on the device such as phone books or the ability to make calls from an active phone, which can result in financial or legal burdens. Use security features such as PIN codes and policy administration tools to protect access to the devices. For a more in-depth treatise on security in wireless environments, refer to Chapter 7, “Security and Wireless LANs.”
Video is another commonly used application. It is used for broadcasting news, hosting video conferences, and distributing learning modules. Just like voice, video over IP is a complex and challenging topic on its own. Therefore, this section does not provide an in-depth technical overview of all the challenges and solutions that are related to enabling IP video, but instead serves to familiarize you with key concepts of video as it applies to production enterprise-class WLANs. This section introduces the different types of video traffic as well as the challenges that are specific to implementing video in WLAN environments. Refer to the “Additional Resources” section at the end of this chapter for resources that cover Video over IP in more detail.
You need to consider the following three parameters when evaluating video over IP-based WLANs:
This section briefly describes each parameter.
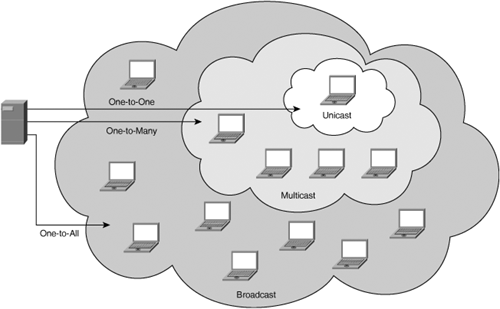
The distribution mechanism refers to the manner in which video is transported across the communications infrastructure and how stations tune into respective viewing sessions. Generally speaking, data can be transmitted as broadcast, multicast, or unicast. The differentiation is based on the number of stations that receive the data, and it is independent of the semantics of the underlying data.
A broadcast transmission sends the data to everybody. Broadcast is one-to-all. In multicast, data is sent only to stations that have explicitly requested to be sent the data. In this case, the network creates copies of the transmission when, and only when, different paths are needed to reach the subscribers. Multicast is thus one-to-many, and its advantage is that it makes more optimal use of network resources by creating copies of data only when required. Finally, unicast sessions transport data between a single sender and receiver. Unicast is one-to-one. Figure 4-3 illustrates that unicast is a subset of multicast, which is a subset of broadcast.
Video is an application that permits different timings of transmissions. Users can either retrieve and view video when they want to, which is known as on-demand viewing, or they can tune into sessions that are broadcast at predetermined times. This is identical to the options for viewing television. You either tune into a particular broadcast and subordinate time to content, or you use on-demand to view programs when it is most convenient for you, in which case you subordinate content to time.
Real-time streaming video applications typically use multicast because it is a more efficient distribution mechanism. Viewers subscribe to a particular stream, and the network ensures that only the relevant streams are branched to subscribed viewers. In this manner, redundant copies of the video streams are avoided. Streaming video is, therefore, ideal for distributing the same information to a large numbers of viewers at predetermined times. Company meetings or earnings updates are prime examples.
On-demand video is retrieved at the discretion of the viewer. These types of video applications employ unicast transport for distribution because the probability that multiple viewers would retrieve exactly the same content at exactly the same time is extremely low. Examples of content that is ideally suited for on-demand are online education modules or archived videos.
A third distinguishing factor in video is the quality of the video. Video is a data-intensive application that not only needs to send image data, but also audio information. Video formats such as MPEG-4 and AVI attempt to reduce the volume of data by compressing the stream before storage or transmission, and decompressing the information during playback. However, even with this compression, video remains data intensive.
A strategy for easing the burden of video on communications networks is to make the same content available in different degrees of quality. Image size and quality can be tailored to best match the available bandwidth. Users can be presented with the choice between a high-bandwidth or low-bandwidth stream to try to ensure a more consistent video experience.
Many of the considerations that are true for voice are directly applicable to video. Video too is sensitive to network latency, and appropriate QoS measures should be implemented to construct a more deterministic network environment. Video, however, is more challenging than voice because it compounds some of the challenges that are encountered with VoIP.
Not only is video much more data intensive than voice, but it is also truly continuous in nature. Voice communications typically have some breaks as people pause between sentences to take a breath. This is not the case for video. As such, limiting latency and jitter is critical. Use QoS classification, marking, queuing, and traffic engineering techniques to ensure that video is given preferential treatment over less time-sensitive information but avoid scenarios in which video could drown out all other communication.
Remain sensitive to the fact that video is usually less mission critical than voice. Make use of a tiered classification and marking strategy for applications. Assign network control traffic the highest priority. Follow it with voice, then video, and finally best-effort data traffic. Note that this classification scheme is highly simplified and that you should use more granular tiers if this better suits your needs.
Another challenge that you face when porting video applications to WLANs is that all video sessions automatically become broadcast communications. This is irrespective of whether the sessions were originally broadcast, multicast, or unicast. The reason is found in the nature of RF communications. As is the case for any communication, access points broadcast data across the airwaves to all attached stations. Even though a single station might be tuned into the video stream, all stations receive the video data. Stations that are not tuned in will disregard the video data. Not only does this force the clients to perform redundant work, but it also ties up the airwaves.
Conversely, the broadcast nature of WLANs can work to your advantage as well. Because broadcast is a superset of multicast communication, WLANs are ideally suited for multicast video sessions. Clients need only to not disregard the video data that is broadcasted from the access points to subscribe to a particular session. However, there is a particular problem with multicast and WLANs. Because all stations have to be able to receive the multicast stream, the network has to enter a “lowest common denominator” mode. For example, if a single station operates at 1 Mbps, even if all others are operating at 54 Mbps, all multicast traffic will be transmitted at 1 Mbps.
Because video is a data-intensive application, the broadcasting thereof can lead to a significant increase in medium access contention. Carefully plan the architecture and design of your WLAN if you intend to support video. Pay considerable attention to bandwidth capacity planning and client-to-access point ratios. Chapter 5 provides recommended strategies and tactics for tackling this challenge.
A final consideration in enabling video applications on WLANs is setting the correct user expectations. QoS is not a substitute for bandwidth, and it is also not the saving grace for a multi-access medium such as WLANs. Video is ultimately best served by dedicated high-bandwidth connections. This is especially true for videoconferencing applications that tie together audio, video, and web applications. Videoconferencing is not as forgiving as some other video types and also doesn’t offer the ability to make efficient use of bandwidth. Set the proper expectations with the user. Emphasize that the capability of the WLAN should not be compared to the current capabilities of the wired network, especially with regard to multimedia applications.
Guest networking is a term used to describe the provision of network access to nonemployees where connectivity is usually limited to Internet access. Guest networks are typically considered and implemented as logical external networks. They avoid the need for visitors such as customers, contractors, and external vendors to access your native enterprise network to obtain Internet connectivity. Conceptually, guest networks are very similar to public hotspots, like those commonly found in airports, cafes, and hotels. The main difference is that the users of enterprise guest networks are usually not charged for access.
Note
Although it is not strictly required, guest networks are most commonly wireless in nature. Guest networks could be implemented as wired networks and integrated into the existing wired network. However, this is a much more complex endeavor than configuring WLANs to provide a guest networking service.
The key questions that you need to answer when considering guest networks are
The following sections tackle these questions by discussing the business rationale for providing guest networking capabilities, the components that are required to enable the service, and finally, the main implementation considerations for deploying WLAN guest networks.
Before deciding to implement guest networks, you should validate the business drivers for providing this complementary service in your environment. The value proposition of wireless guest networks is not necessarily the same as the rationale for deploying WLANs in general because it is usually related to one of the following considerations:
Business agility
Security
Liability protection
The following sections explore each of these considerations in more detail.
Guest networking is made available to nonemployees as an amenity. By ensuring your users can access the Internet, you improve their experience when at your site. This can be important in industries that have a high degree of public interaction or organizations that have many visitors.
A guest portal is often used, so the visitor is greeted with a Web page when they first use the service. Typically, this will include a welcome page, perhaps a legal disclaimer, and maybe an authorization or check box for them to acknowledge.
After guests successfully obtain Internet access, they can use their own remote access solution to connect to their corporate infrastructure. Guests thus effectively extend their organization’s Intranet to your own site making their full suite of productivity applications available to them. For example, they can download their e-mail, browse their internal website, and retrieve voicemail.
A particularly useful application of guest networks can be found in product demonstrations. When a sales representative visits your office, he can access all applications and information that would be available to him if he were at his own corporate offices. As such, a full-featured demonstration can be delivered without being encumbered by the potential unavailability of tools and data.
Many enterprises do not allow nonemployees to access the network. This simple security policy avoids the risk associated with visitors introducing viruses to the network, snooping, hacking, and other undesirable activity. However, visitors can benefit from Internet connectivity to gain access to their own enterprise networks (to check e-mail, access files, and so on). A policy decision to altogether prohibit access therefore negatively impacts the productivity of your visitors.
A guest networking solution addresses this conflict. You can provide visitors, contractors, and vendors access to the Internet, while avoiding the ability to access your enterprise network. Guest traffic is separated and tunneled securely on your network and to the Internet; thus creating an isolated and secure environment for your visitors to work in.
Internet traffic can typically be tracked to its source. Therefore, all Internet traffic that originates from an enterprise can easily be identified as having come from that enterprise’s network. Employees usually sign an acceptable use policy when hired. They agree not to undertake malicious or illegal behavior, such as hacking or deliberately spreading viruses. However, guests are not required to sign such employee agreements.
Protect yourself from legal liability by implementing a portal in which users need to read and explicitly accept a policy for acceptable use prior to connecting to your wireless guest network. In the unfortunate case of a crime or unacceptable behavior, you can audit records, identify the offending guest, and take appropriate action.
A guest network imposes two distinct requirements:
The guest network must somehow uniquely identify itself—. This is achieved in guest WLANs by using a dedicated Service Set Identifier (SSID).
Guest traffic must be transported to and from the Internet in an isolated and secure fashion—. This is done by using IP tunneling protocols to create virtual conduits between the access point and the Internet.
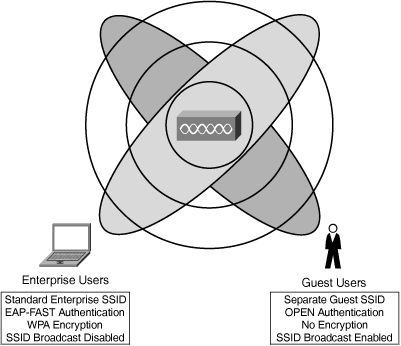
A dedicated guest SSID is created on the same access point that services the enterprise WLAN to produce a separate Layer 2 network. The benefit of adding an additional SSID is that it avoids the need to purchase, deploy, and support additional access points. The incremental guest WLAN SSID thus uniquely identifies the virtual WLAN that is dedicated to guest traffic. This not only makes the separation of guest and production traffic possible, but it also enables the definition of different association and authentication policies for your guests and regular users.
Configure your guest SSIDs with “OPEN” authentication and no encryption to provide open access in the same manner as public hotspots. This essentially permits any laptop to associate with the AP. Furthermore, configure the access points to broadcast the SSID so that the guest SSID can readily be discovered by any station that wants to attach to the guest network. Figure 4-4 illustrates how a dedicated guest SSID creates a virtual WLAN that is separate from the WLAN that is identified by the enterprise SSID.
Note
The broadcasting of SSIDs for the enterprise WLAN is discouraged for security reasons because it makes the identification of the SSID more difficult and lowers the risk of accidental or malicious association.
These steps ensure that all visitors can locate and associate with the SSID, and use the guest networking service, without having to resort to substantial configuration changes on their laptop. WLAN client software can be used to select the same public WLAN profile that is applied to access public hotspots.
The second requirement is to transport all guest traffic in an isolated and secure manner from the access point to the Internet. Tunneling protocols such as LWAPP, GRE, or IPsec provide an efficient mechanism for performing this task. The protocols erect virtual conduits between the access point and the Internet gateway through which all guest traffic must pass.
This is essentially identical to the use of VPN tunnels to provide secure remote access to the enterprise network across the Internet. The minor difference in the case of guest WLANs is that the tunnels cross the private intranet versus the public Internet in the case of VPN remote access. The principal, however, is identical. Tunneling traffic isolates it from the rest of the network and provides a secure path to the destination.
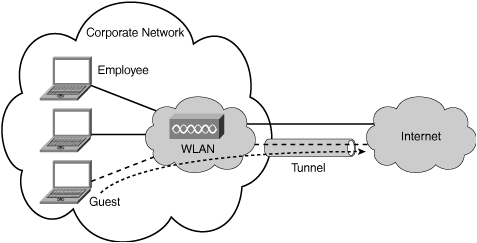
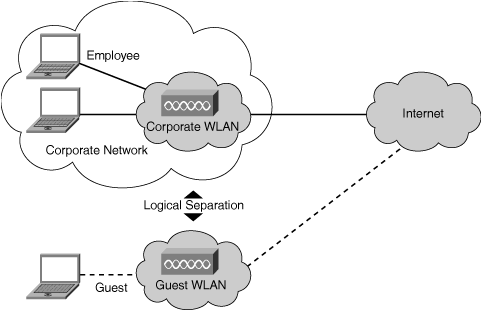
Note that even though guest WLAN traffic traverses the same physical infrastructure of the enterprise network, it is entirely separated on a logical basis. Although the same access points, switches, and routers are used to transport data, for all intents and purposes the guest network is a completely separate network. Figure 4-5 shows the physical configuration of a WLAN that is tunneling guest traffic onto the Internet. Figure 4-6 shows the corresponding logical configuration of the same network; highlighting the fact that the guest network appears as a logically separated entity.
Guest WLAN capabilities can be provisioned in different ways. Many WLAN vendors provide equipment with “built in” support for guest networking capabilities. The WLAN gear can be configured to create the SSID, the tunnels, and even a guest portal. For example, these features are offered in the centralized WLAN controller-based solution from Cisco Systems.
Alternatively, you can purchase dedicated equipment that is specifically designed to provision guest services. These network appliances are usually placed in a centralized location in your network and provide guest networking services to several buildings, often along with additional security capabilities.
Finally, it is possible to engineer a solution using the capabilities of your switches and routers. This last option is not recommended because it does not scale well and requires significant technical expertise to implement and maintain correctly.
Several topics should be considered before implementing guest networking. Whereas this service can add significant value, it also introduces additional complexity to the WLAN. Some of the issues you should consider before implementation include the following:
Guest portal
Legal disclaimers and acceptable use policies
Ease of use
Support
Logging and auditing
The next sections describe each of these in greater detail.
Develop a guest portal to be the public face of your guest network. Make it aesthetically pleasing; include your corporate identity; and, depending upon your security policy, require the guest user to record their name, acknowledge a legal disclaimer, or sign an acceptable use policy.
Include a legal disclaimer with your guest network. You should engage independent legal counsel to ensure that the disclaimer conforms with local legislation and that you are protecting your enterprise from any legal liability that might accrue from misuse by your guests. Display the acceptable use policy on the guest portal and require that guests agree to comply with the policy prior to granting access to the Internet. Having users select an I Accept box or type their name into a Signature field works well for this purpose.
Make the guest networking solution easy to use. When providing guests with access to a guest network, you should not require specific software or configuration changes to their laptops.
Implement the guest networking solution with its own SSID configured with OPEN authentication and no security settings. Ensure that the SSID is broadcast. Because the guest network is logically isolated from your enterprise network, and only provides access to the Internet, this should not present any security concerns. As always, ensure that your Information Security department review and approve your design prior to making it available to visitors.
Minimize the support burden of your guest networking solution. Because the users will primarily be guests, you do not want to expend operational cycles on supporting them. Keep the system easy to use and produce some basic guidelines for your guests to lighten the support burden. Frequently Asked Questions (FAQ) sheets can be produced that tell the guest what SSID to use, how to navigate the guest portal, and to help with basic connectivity troubleshooting.
Log the activity of your guest users. Your enterprise might already log Internet activity by your own staff, which should make it easier if you decide to log guests also. At the minimum, keep records of the number of sessions, the identity and IP address of the guest users, and the time and date of their session.
The term location-based services (LBS) is sometimes used interchangeably with WLAN location services, but LBS more correctly denote services that provide the user with information about the physical location of the client device. Conversely, WLAN location services provide telemetry information on WLAN devices. This information is used by many applications to provide visibility of mobile devices, asset location and tracking information, inventory and supply chain management support, presence data, Emergency 911 (E911) event triggers, and many others.
Note
The term LBS is also used in cellular telephone networks to denote services offered to subscribers. For example, cellular phone users might receive a Simple Message Service (SMS) message notifying them of sales or special offers in retail stores nearby. However, in the context of this chapter, this discussion focuses on LBS and WLAN location services as they relate to 802.11-based wireless networks only.
With a robust LBS solution, an organization can easily answer questions such as the following:
What do I have?
How much of it do I have?
Where is it?
What is its status?
The following sections demonstrate why the capability to answer the aforementioned questions is valuable for various industries and provide an overview of technical considerations that need to be made when deploying LBS capabilities.
WLAN location services incorporate location information with pertinent content to provide incremental value to a user. In essence timely and accurate information on the whereabouts and status of an entity is used to provide a more relevant service. These services are typically classified into three families, as follows:
Tracking services—. These services provide the location and utilization information to optimize processes in workforce, and asset and logistics management. For example, tracking services can reduce duplication and accelerate logistics in inventory management.
Information services—. These services use location data to identify which information is most relevant for a specific position. For example, different maps might be presented to you depending on your whereabouts. LBS can be integrated into mobile resource management solutions (MRM) that target mobile workforce productivity.
Safety and security services—. These services rely on location information to provide safety and security enhancements. For example, the whereabouts of children in theme parks can be tracked by providing them with active wristbands.
The location information can be of significant benefit in multiple industries by enabling otherwise difficult-to-realize efficiencies. The following sections take a closer look at how various industries are using these location services.
Hospitals spend millions of dollars on the latest technology to provide the best level of care to their patients. This often results in the use of very expensive, but mobile, assets, such as electronic and automated IV pumps, vital signs monitors, and even gurneys. Not only can the loss or misplacement of these devices create a financial burden for the hospital, but the lack of the device can also prohibit timely patient care. The ability to track, locate, and recover these mobile assets is, therefore, absolutely critical for the hospital or health center.
Some hospitals combine WLAN voice with location services. This allows hospital staff to carry WLAN-based VoIP handsets that include a “panic button” or key-code that, when pressed, will page all appropriate staff that are located nearby.
In some instances, patients themselves have been provided with location tags. The WLAN can then be used to locate the patient, and even provide an automatic link to the patient information system. The synergy of an existing WLAN infrastructure, location services, WLAN voice, and back-end hospital systems thus enables a faster response time and improved patient care.
Location services can offer improved business knowledge by automating and simplifying supply chain management. The ability to identify exactly how many items are in production, where they are located in the assembly line, and the current rate of manufacture is critical for operations managers who rely on timely and accurate information to finely tune the production process. Intimate knowledge of the goods and their whereabouts is, therefore, essential.
Location services can also be used by robotic delivery mechanisms and warehousing vehicles to automatically store and retrieve equipment, and monitor stock levels in real time. The use of a WLAN-based solution avoids the enterprise from having to deploy a proprietary, nonstandard RFID solution instead.
Personal security for customers is very important in the entertainment and leisure industries. In Europe, some theme parks have used WLAN location services to provide an online, active, and real-time positioning solution for visitors to track the location of children. Children are provided with active location tags embedded in wristbands or name badges. This provides additional safeguards for security staff and park management, and peace of mind for parents.
The most common logistics operation performed with handheld wireless devices is inventory taking. Almost every large retail chain and distribution center use some type of wireless network to assist with the mundane, but necessary, task of counting things.
WLAN location services can provide incremental value in these environments by providing online, active, and real-time information on asset location. In the car rental business, identifying whether vehicles have been returned and whether they are in the garage, workshop, or cleaning bay improves the response time and productivity of the business. The business can improve its operating margins by ensuring quick turnaround of its vehicles.
Transport and shipping companies are in the business of timely delivery of packages on time. This is only possible by ensuring that distribution and dispatch centers operate smoothly, accurately, and expeditiously. Location services assist in this by making sure that pallets and crates can be tracked and identified accurately. By attaching asset tags to the pallets and crates, the transport and shipping business can guarantee that the data provided to its back-office system is accurate.
WLAN location services are usually provided by leveraging the existing infrastructure to provide information on the location of 802.11 client devices. These devices not only include standard wireless network client devices (laptops, PDAs, WLAN phones, and so on), but also asset or location tags.
Note
WLAN asset or location tags are small devices about the size of a box of matches. They contain a battery and an 802.11 transmitter that regularly transmits beacons. The beacons are received by the access points and interpreted by location service applications.
There are three ways location can be calculated, each with increasing accuracy. The options are identifying the closest access point, using RF triangulation to determine an approximate position, or making use of RF fingerprinting to pinpoint the exact location. Use the method that gives you the desired degree accuracy:
Closest AP—. This method is the simplest way to identify location, but it is also the least accurate. The WLAN location service queries the access points to determine where a particular client is associated or which AP reports the strongest signal. While this gives general location information, the accuracy is limited to the size of the radio cell.
RF triangulation—. This method is considerably more accurate than the closest AP method. In this scheme, signal strength readings are reported from the access points that detect the location tag or client device. This allows the WLAN location service to calculate the general area using triangulation algorithms. RF triangulation does not take into account environmental factors, such as interference, multipath, and signal attenuation. As such, RF triangulation results can be rendered inaccurate due to these adverse environmental effects.
RF fingerprinting—. This method uses a record of the radio signature of the entire area that is monitored. Effectively, the “fingerprint” of each location (usually on a grid basis) is compared to real-world data transmitted by the tag. By comparing both, the WLAN location system can quite accurately determine the tag or client’s location. For example, RF fingerprinting can incorporate a building map that includes the known propagation effects of the building topography such as attenuation from walls or furniture. Knowing these propagation effects, the WLAN location system can more accurately determine the tag or client’s location.
Location services are computationally intensive, especially when real-time information is required. As more devices are tracked, the more difficult it becomes without dedicated resources. Although many WLAN vendors offer location services, the more robust and scalable enterprise solutions rely on dedicated servers or appliances to offload the CPU-intensive activity from the access points or WLAN controllers.
In addition to the type of location service you want to provide and how you want to support and integrate it, you need to carefully consider privacy matters, tag battery life, and tag security when implementing WLAN location services in your organization.
Privacy is a concern when tracking the location and historical movement of users. Inform the user when utilizing WLAN location services in the enterprise to track wireless client devices such as laptops, user ID tags, or WLAN phones.
Tag battery life for WLAN-based asset or location tags range from three to five years. Although this might sound like a sufficient amount of time for most business applications, some thought should be put into scalability and longevity of the system. The more accurate the real-time information you need, the more often the tag must transmit its location. (This is a configurable option on most tags.) The more often a tag transmits its location, the quicker it exhausts its battery. A careful compromise is thus required. Ensure that you fine-tune the system to collect location information on a sufficiently regular basis, without expending more battery life than necessary.
Tag security should be considered. When tags are used to track the location of valuable assets, it is important that they are securely fixed and, if possible, hidden from view. Also make sure that the tag can be removed when required.
In this chapter, you learned that supplementary services of voice and video can be layered onto WLANs. Many of the benefits that these applications bring to wired environments are directly applicable in the wireless environment. However, carefully consider the challenges of enabling VoIP and video on WLANs and leverage QoS techniques to remedy some of the problems.
You learned about the implications of having to support voice on a diverse set of WLAN devices and identified the importance of having a robust architecture and design. If your WLAN deployment contains multiple ESSs, remain sensitive to the hurdles created by roaming clients. Chapter 5 covers these topics in greater detail.
This chapter also covered the commonly encountered types of video traffic as well as the challenges that are specific to implementing video in WLAN environments. You learned about the different distribution mechanisms, timing of the distribution, and the ability to tune quality to deliver more consistent video experiences. Keep in mind that a robust QoS foundation is critical but that it also does not resolve all challenges imposed by multi-access media such as WLANs. Set the proper expectations with your users.
Guest WLANs and location services were the complementary services that this chapter introduced. Guest WLANs support network access to nonemployees by providing basic Internet connectivity to them. Use dedicated guest SSIDs as well as IP tunneling protocols to move traffic to and from the Internet in an isolated and secure manner.
Finally, WLAN location services were introduced as a practical method for providing telemetry information on WLAN client devices. The value of LBS-enabled tracking, information, and security and safety services was discussed, and examples were provided of how various industries make use of this solution.
The proper mix and implementation of these supplementary and complementary services will extend the success and value of your WLAN for your company. Part II of the book focuses on the specifics of how to architect and design an enterprise class wireless LAN, what the recommended practices are for deploying and managing it, and how to construct and implement a security framework for the WLAN.
Cisco Systems, Inc. “IP Videoconferencing Solution Reference Network Design (SRND).” http://www.cisco.com/application/pdf/en/us/guest/netsol/ns280/c649/ccmigration_09186a00800d67f6.pdf. 2002.
Cisco Systems, Inc. “Cisco Gigabit-Ethernet Optimized IPTV/Video over Broadband Solution Design and Implementation Guide.” http://www.cisco.com/en/US/partner/netsol/ns340/ns394/ns158/ns88/networking_solutions_design_guide_book09186a00804abca9.html. 2005. (Requires Cisco.com registration.)
Davidson, Jonathan, J. Peters, and B. Gracely. Voice over IP Fundamentals. Cisco Press 2000.
Durkin, James F. Voice-Enabling the Data Network. Cisco Press 2002.
Hattingh, Christina, and T. Szigeti. End-to-End QoS Network Design: Quality of Service in LANs, WANs, and VPNs. Cisco Press 2004.