Protecting your kids
Abstract
Children are raised with computers, mobile devices, and the Internet. It’s become as normal an environment as the local park, and has opened new ways for them to be exposed to potential threats. Many parents are at a loss of how to protect their children, but in this chapter we’ll discuss methods and tools to safeguard them.
Keywords
Cyber safety; filters; blocking; parental controls; child safety; teens
The latest generations are raised online, with children introduced to technology at an early age and growing up with it in hand. A child may begin using computers or other devices as young as preschool age, interacting with what’s on a screen in schools, libraries, or at home. As they progress in age, they may be expected to do research online, and experience the peer pressure of having their own tablets or smartphones. It doesn’t take long before they know their way around the Internet, and begin downloading apps or other files, playing online games, or interacting with others. Because of the prevalence of technology in their lives, it’s important to establish restrictions, set expectations, and help them stay safe online.
Protecting Your Kids
Even if your child knows how to use the technology, it doesn’t mean they have the experience and maturity to deal with situations and people they meet online. Regardless of their age, what and who they encounter can be overwhelming. The use of smartphones, tablets, and other mobile devices also means that you may not be around when your child encounters problems. While technology has added a new layer of complexity to effective parenting, it doesn’t make things hopeless. There are ways to monitor and maintain your child’s activity, even when you’re physically not there to help them.
Keeping kids safe online isn’t a single-step process. As with anything in parenting, the restrictions you place on your kid’s Internet usage when they’re younger will change over time. As you work to raise responsible, selfregulating individuals, what you teach and supervise will change as they grow closer to adulthood, and you gradually shift control of their Internet usage to them. When it comes to Internet safety, you need to revisit things you’ve taught and change limitations on a periodic basis, keeping in mind the rules you set should be a combination of:
![]() Supervision—where you oversee, regulate and help direct their online activity.
Supervision—where you oversee, regulate and help direct their online activity.
![]() Education—where you teach them the dos and don’ts of online behavior, as well as the prevention and solutions to various risks so they know how to avoid and deal with potential problems.
Education—where you teach them the dos and don’ts of online behavior, as well as the prevention and solutions to various risks so they know how to avoid and deal with potential problems.
![]() Tools—which consist of software, hardware, and settings that help you and your child limit risks and assist in monitoring online activity.
Tools—which consist of software, hardware, and settings that help you and your child limit risks and assist in monitoring online activity.
The Internet may expose your kids to an array of problems, and it can be difficult realizing that many of them are variations of what parents have contended with for generations. Your mother may have worried about an objectionable magazine under the mattress, rumors of a weird stranger hanging around the school, or being told about the school bully. The core problems and concerns of protecting your child are essentially the same in the real and virtual world. You need to teach children to be cautious and respectful of others, treat others as they want to be treated, abide by your family’s values, and avoid potentially harmful material and situations. To keep them safe, you need to do everything you can.
A difference between your generation and today’s is that kids have increased availability and access to material and interactions that may be unsafe and disturbing. They now have access to a greater scope of people and content. While it may have been unlikely that you had to deal with a school bully at home, view child pornography, or come in contact with identity thieves and sexual predators, these and other threats are a legitimate risk to a growing child with Internet access. This doesn’t mean that the Internet should be avoided, just that you need to minimize the risks. Doing nothing only increases the likelihood of a problem.
Passwords for Kids
Basic security is the first step to protecting a child. As we saw in Chapter 2, Before connecting to the Internet, strong passwords are important to prevent unauthorized access to online accounts, software, and devices. Unfortunately, although children are taught how to use computers in the early grades of school, any passwords they’re given are often generic, easily guessed, and often identical to other students. This means it’s usually up to parents to teach children that they need to use passwords that are:
![]() A mix of uppercase letters (A, B, C,…), lowercase letters (a, b, c,…), numbers (0, 1, 2,…), and special characters (` ~ ! @ # $ % ^ & * ( )_ - +={ } [ ] | : ; " ' <> , . ? /)
A mix of uppercase letters (A, B, C,…), lowercase letters (a, b, c,…), numbers (0, 1, 2,…), and special characters (` ~ ! @ # $ % ^ & * ( )_ - +={ } [ ] | : ; " ' <> , . ? /)
Coming up with secure and memorable passwords can be seen as a game for younger children, but if they have problems coming up with their own passwords, there are a number of kid-friendly password generators that can help:
![]() DinoPass (www.dinopass.com)
DinoPass (www.dinopass.com)
![]() Password Bird (www.passwordbird.com)
Password Bird (www.passwordbird.com)
Children also need to be aware that passwords should never be shared. They may feel that a friend can be trusted with it, or be fooled or pressured into revealing it. They should know that under no circumstances should they ever share this information (except with you), or change the password afterwards without your knowledge.
If they’re limited to only using a family computer, there are other options for security. As we discussed in Chapter 1, What is cyber safety?, fingerprint readers and facial recognition features (such as Windows Hello in Windows 10) can make it easy to login to a machine. Rather than needing to remember a password, you simply need to place your finger on a scanner, or let the camera on your computer recognize the characteristics of your face or eyes.
Search Engines
Popular search engines commonly have settings that allow you to set your preferences when searching for content. By checking the options available, you’ll often find settings that will filter your results, so there is less chance of violent, pornographic, or other adult content appearing in the results. While some adult text, images, or video results may still make it into the results, you’ll usually find that they are drastically fewer than what you see when their SafeSearch settings are off. On Bing, you would turn on SafeSearch by doing the following:
1. Visit www.bing.com/account/general.
2. In the SafeSearch section, select the Strict option to filter all adult content from results, Moderate to filter adult images and video but not text, or Off to not have results filtered.
On Google, you would turn on the SafeSearch settings by doing the following:
1. After logging onto Google, visit the settings page at www.google.com/preferences.
2. In the SafeSearch filters section, click on the Turn on SafeSearch checkbox so it appears checked.
3. Click Lock SafeSearch link next to this, and login if prompted. Confirm that you want to lock the SafeSearch settings by clicking Lock SafeSearch.
Kid-Orientated Search Engines
There are also search engines for younger children, in which filtering is on and can’t be disabled, so that adult content isn’t mixed in with the safe results you and your child are looking for. Some of the ones available for kids include:
![]() KidRex (www.kidrex.org)
KidRex (www.kidrex.org)
![]() KidzSearch (www.kidzsearch.com)
KidzSearch (www.kidzsearch.com)
Parental Controls
Parental controls are features or software that allow you to monitor and restrict what a person does online. There are a wide variety of programs that do such things as block and filter websites and content, record their activities, limit their time online, and view their browsing history and communications. While the features in parental control software vary, some will log keystrokes, take screenshots of what they’re doing, log chats on various sites or apps, and record where they are by providing reports on the location of a laptop, tablet, phone, or other device. Some of the popular parental control software available include:
![]() Net Nanny (www.netnanny.com)
Net Nanny (www.netnanny.com)
![]() Safe Eyes (www.internetsafety.com/safe-eyes-parental-control-software.php)
Safe Eyes (www.internetsafety.com/safe-eyes-parental-control-software.php)
![]() CYBERsitter (www.cybersitter.com)
CYBERsitter (www.cybersitter.com)
![]() WebWatcher (www.webwatcher.com)
WebWatcher (www.webwatcher.com)
![]() MMGuardian (www.mmguardian.com)
MMGuardian (www.mmguardian.com)
As we’ll see in this chapter, parental control software is generally user friendly and fairly straightforward to use. Some, such as Microsoft’s Family Safety, are free while others require purchase or a subscription to use all or any of the features. Some parental control software are designed for certain devices or platforms, so you may need to use different products if you’re planning to install it on various phones, tablets, laptops, and PCs. For example, while Microsoft Family Safety is available for Windows Vista and higher, you’d need to install something else on your child’s iPhone. Also, some products may have some features that work on a phone, but aren’t available on tablets. Before deciding on a parental control product, ensure that the features available suit your needs.
The level of control you’ll place on them will depend on their age, maturity, and any situations and issues your child’s dealing with. If you think using such tools are a little extreme, and that you’re one of the few thinking of using them, consider that in a survey of parents of teens aged 13–17 (Anderson, 2016):
![]() 39% of parents have used parental controls to manage their child’s online activities.
39% of parents have used parental controls to manage their child’s online activities.
![]() 16% have used them to restrict cellphone usage.
16% have used them to restrict cellphone usage.
![]() 16% have tracked their child’s location through monitoring tools.
16% have tracked their child’s location through monitoring tools.
![]() 61% have checked which sites their teen visited.
61% have checked which sites their teen visited.
While it is important to respect privacy, it shouldn’t be at the cost of your child’s safety. Let them know that in allowing them to have their own email account, phone, or other device, you’re reserving the right to check how it’s being used. It doesn’t necessarily mean that you don’t trust them, but you want to ensure they’re safe, and there are strange and creepy people out there who could cause them harm. In doing so, parental control software can be useful in keeping an eye on your child when you’re not physically able to supervise what they’re doing online and who they’re doing it with.
Understanding What They’re Using
To keep track of what a child is doing, you need an understanding of what they’re using. Once you know the apps they have installed, browsers being used, and devices they have access to, you’ll have a greater understanding of how they’re using the Internet, be better able to identify potential problems, and know what needs monitoring. A common feature of parental control software is the ability to control what apps are allowed on the PC, phone, or tablet, and may be used to see what’s been installed.
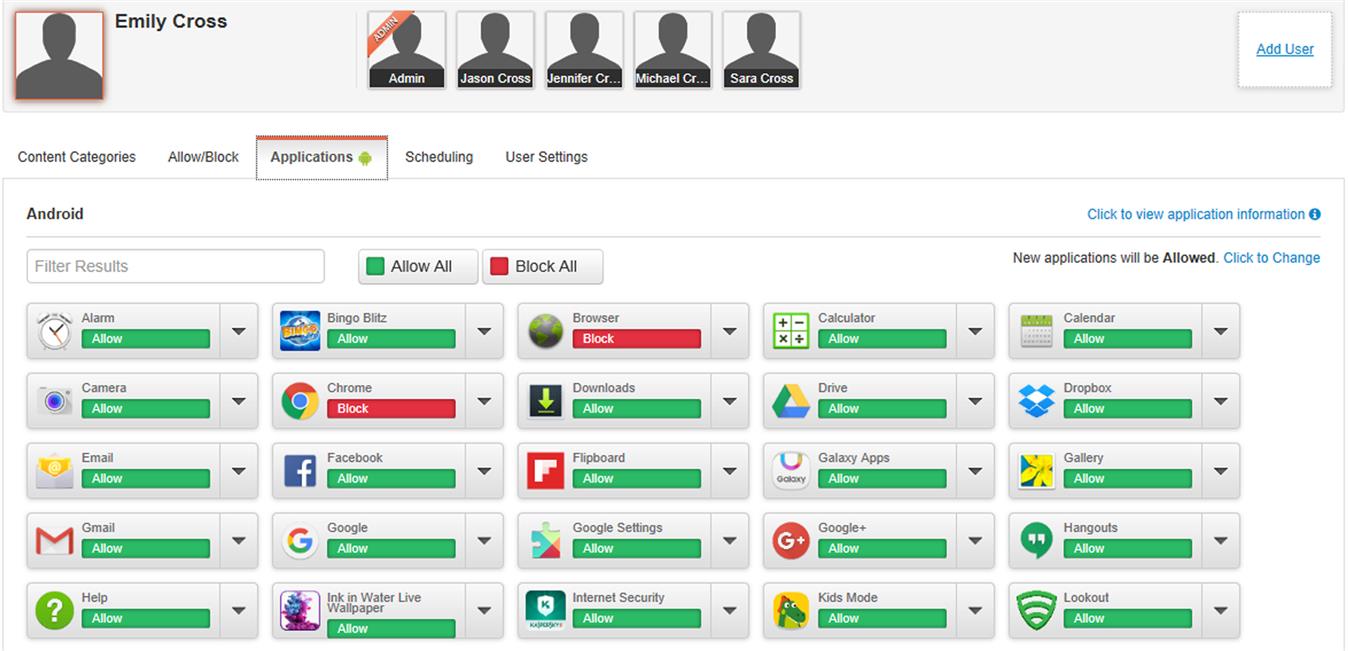
As seen in Fig. 10.1, after installing Net Nanny on a tablet or phone, you can logon to their site to see what apps are on the device, and click on them to allow or block their use. By blocking an app, they’re prevented from using it, until you change the restriction. You can also click on the Click to Change link in the upper right-hand corner of the screen to specify whether new applications are allowed to be installed, or if the child needs to contact you for permission to install something new.
In looking at the listing, you’ll be able to see if they’re using certain apps for popular sites or services. This may indicate a need to view their account and identify any issues that require a discussion or the need to block the app. Because sites aren’t always accessed through an app, and most are commonly through a browser, you should also try and keep abreast of what’s popular. For example, a study by Pew Research Center (Lenhart et al., 2015) shows the social media platforms most often used by teens are:
Parental Controls in Windows
While there are numerous products available that can be installed on phones and tablets, Microsoft does provide a free program and site that can be installed on Windows Vista and higher, and is included in Windows 8.1 and up. You would setup the Family Safety controls in Windows by first logging on with an Administrator account. As we saw in Chapter 1, What is cyber safety?, each member of your family should have their own account for Windows. Children can initially be setup with a child account or you can switch an existing account to a child’s account. In Windows 8.1 you would switch the user account for your child to a child account by doing the following:
1. From the search screen, type PC Settings. When PC Settings appears, click Accounts in the left pane.
2. Click Other Accounts. When the list of current accounts appears, click on the account you wish to change, and then click Edit.
3. On the Account Type dropdown lists, select Child and then click OK.
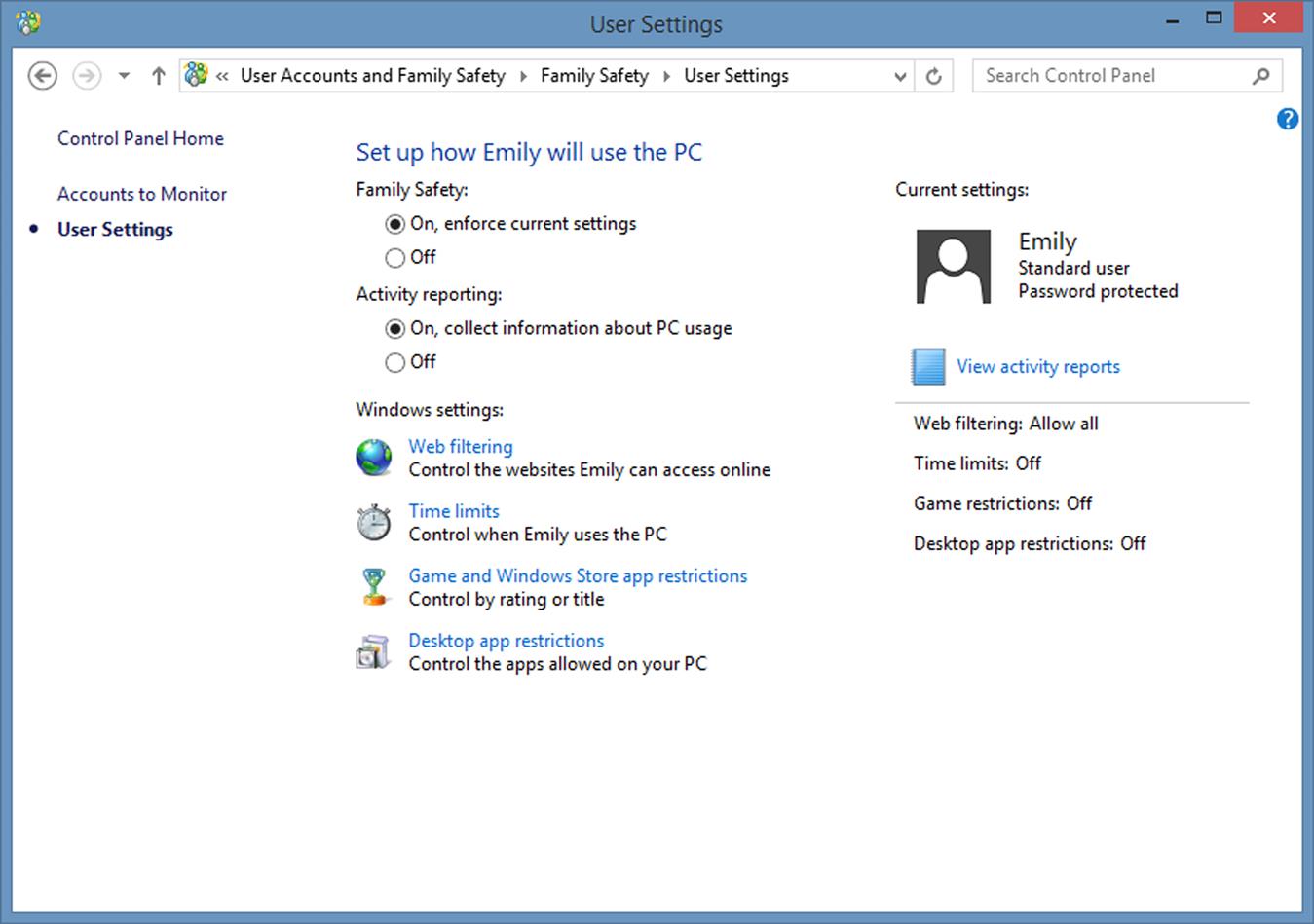
Once a user is set as having a child’s account, you can then set restrictions. As seen in Fig. 10.2, you can configure the account so your child has time limits, constraints on the websites they can visit, restrictions on apps they can use, and your ability to monitor them. The settings are adjustable to what you’re comfortable with and feel is suitable.
To configure these settings for your child you would follow these steps:
1. Right-click on the Start menu, click Control Panel, and then click User Accounts and Family Safety.
2. Click Set up Family Safety for any user, and when the list of accounts appears, click on the account you wish to change.
3. At the top of the screen that appears, ensure that Family Safety is turned On.
4. If you want to monitor what your child does on the computer, ensure that Activity Monitoring is turned On. Once on, you could click View Activity Reports to see when they’ve used the computer, the most popular sites they visit, their most used apps and programs, and a list of pages that have recently been blocked so they can’t see them.
Filtering and blocking
In Family Safety, once you turn on restrictions, Windows will automatically turn on SafeSearch settings on the most popular search engines, including Google, Bing, Yahoo!, and others. As we discussed, this will prevent adult images from appearing in Web search results and image searches. You can also setup filtering and blocking to prevent access to sites with certain content. To do this, you would go to the Family Safety screen in Control Panel that we showed you earlier, click on the account you wish to change, and do the following:
1. Click Web Filtering. You’ll now see options to either allow the user to use all websites, or so that the user can only use the websites you allow. Click the second option to filter what sites they can use.
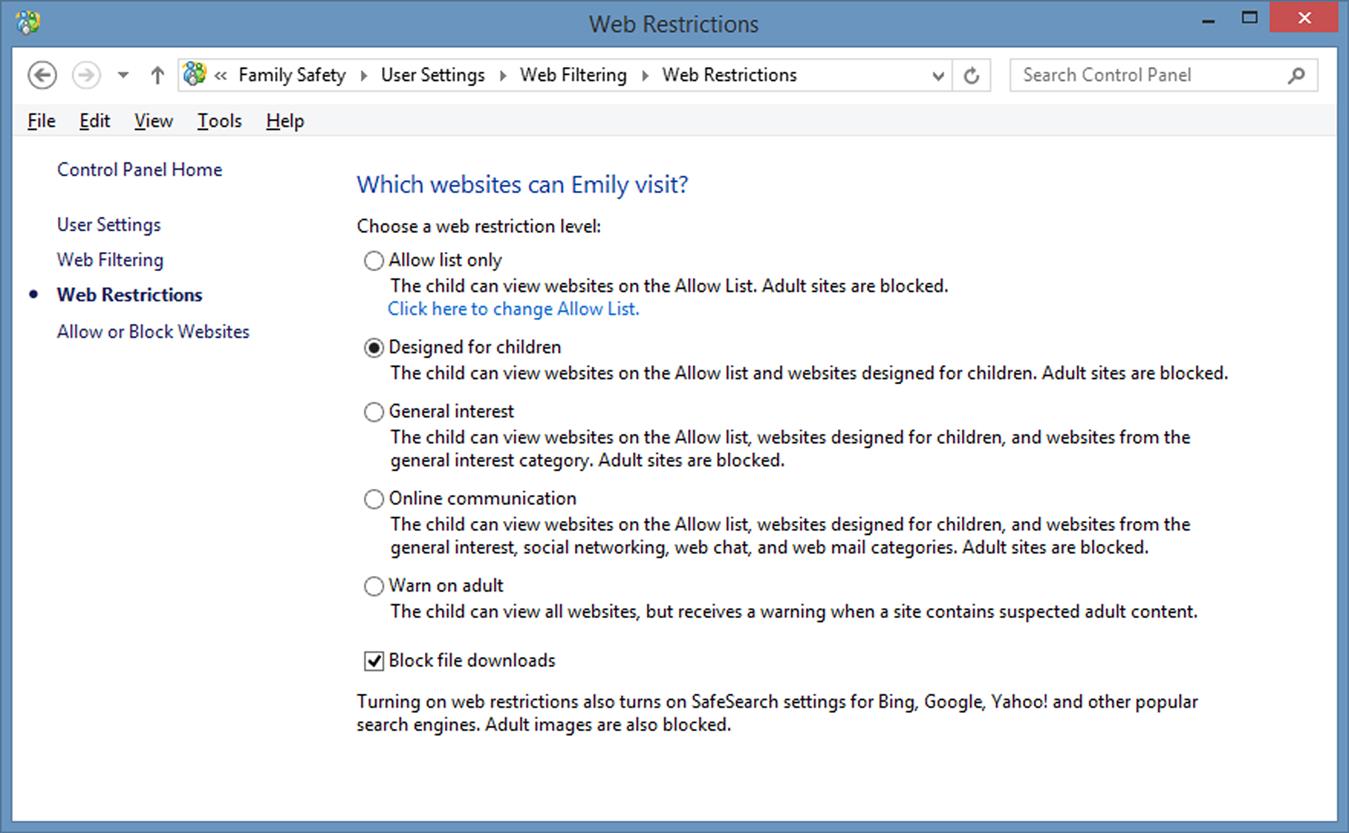
2. Click Set web filtering level, and a page similar to Fig. 10.3 will appear.
3. Click on a restriction level for your child. Each option gets progressively more permissive, so select the one that best suits the age and maturity of your child. Options include:
a. Allow list only, which let’s your child view sites that have been added to the Allow List. These are sites you’ve specified through the screen to allow or block websites. Adult sites are also blocked.
b. Designed for children, which allows everything from the previous setting, blocks adult sites, and allows sites that have been designed for children.
c. General interest, which allows everything from the previous settings, blocks adult sites, and allows sites categorized as general interest.
d. Online communication, which allows everything from the previous settings, blocks adult sites, and allows social networking, Web mail, and chat.
e. Warn on adult, which allows the user to view any site they try and visit, but will warn them if there may be adult content.
4. Click on the Block file downloads checkbox, so it appears checked. This will prevent the child from downloading files, which could contain viruses or other malware.
5. On the left pane of the screen, click Allow or block specific websites.
6. In the Enter a website to allow or block box, enter the URL of a website you want to allow or block. If you want to allow the child to access the site, click the Allow button. If you don’t want the child to visit a site, click the Block button. Depending on the button you clicked, the site will now appear below in either the list of Allowed websites or Blocked websites. If you made a mistake in adding a site, simply click on the site in the list and then click the Remove button.
Limiting Time and the Times They’re Allowed Online
Children spend a considerable amount of time on the Internet. One study of children aged 9–16 in 25 countries found that 93% of children go online at least once a week, with 60% of them going online daily or almost every day (Livingstone et al., 2011). A more recent study found that 24% of teens aged 13–17 were online “almost constantly,” 56% were online several times a day, 12% went on once each day, 6% went on weekly, and just 2% went online less often (Lenhart et al., 2015). The lack of exercise, eyestrain, stress, and lack of meaningful contact with others, possibly resulting in antisocial behavior, can be a legitimate concern, and are only some of the reasons why you should limit their time on devices.
Many parents limit their kids’ time online, and use such restrictions as a form of discipline. A Pew Research Center survey of parents of teens aged 13–17 found that 55% limited the amount of time or times their child could go online each day, and 65% have taken away their child’s phone or Internet privileges as punishment (Anderson, 2016). Some of the ways you can set limitations is by explaining the risks associated with spending too much time online, finding activities that take them away from the Internet (such as sports, reading, hobbies, or family events), inviting their real-life friends over, and so on.
If you have a very young child, you can control access by keeping your tablet and phone out of reach, and by setting up passwords/PINs on the device to prevent access. As they get older, parental controls can be useful in limiting how long and what times your kids are allowed to go online and/or use the device. In doing so, you could allow them to use the computer or device during certain times and a limited number of hours on school days, and more time on weekends.
To setup time limits in Microsoft Family Safety, you would do the following after going to the Family Safety screen we discussed earlier:
1. Click on the name of the account you want to change, and then click Time Limits.
2. To set the number of hours the child can use the computer, click Set time allowance.
3. To set the hours, select the option to use the PC for an amount of time. In the Weekdays and Weekends dropdown lists, set the number of hours and minutes they can use the computer during the week and on weekends, respectively.
4. Click the back button to return to the previous screen, and click Set curfew to set when the child can go on the computer.
5. Click on the option to set the time ranges they’re allowed on. When the grid appears, click and drag your mouse across the day and time periods. Areas that are marked will dictate when they’re permitted on the computer.
Deciding on Age Appropriate Limitations
The ages and settings you configure are up to you, and you can set it to be as restrictive or permissive as you see fit. Parental controls commonly provide suggested settings based on age ranges, but you may decide to adjust them since you’re the one who knows your child best. You may feel that time settings aren’t necessary, certain apps are inappropriate, and certain types of filtered content should be allowed. These should be reviewed occasionally to fit your child best as they get older.
In deciding on what’s age appropriate, you shouldn’t let your child pressure you. You might hear the argument that everyone in their class has a tablet or phone and is allowed to use them how and when they want, or that they’re the only ones who aren’t allowed to play a certain game. Maybe it’s true, but it isn’t a compelling reason for them to have a device or access certain content. Just because other parents allow a young child to play Mature-rated games, watch Restricted or 17+movies, or allow them to have their own Facebook and YouTube accounts (who have an age limit of 13 or older) it doesn’t mean you should allow it. Even if it’s true that other kids have or are allowed to do something, trust in your opinion of whether your child is old enough or has the maturity to handle it.
Location of Computer
The location of where a child is able to use a computer, laptop, tablet, or other device can have an impact on their safety. If a computer, laptop, or gaming system has been setup in or near a common area of the house, such as a living room, your child will be less likely to encounter problems. You’ll be nearby if they have questions, need help, or supervision, and your presence can be a deterrent to doing something that they know they shouldn’t. The same also holds true for younger children being limited to using a tablet or other device at home.
Location
As a child gets older and more mobile with devices, you may want to keep track of where they are, making sure they’re really at school, a friend’s house, or other places they’re supposed to be. According to a survey released on 2016, 16% of parents have used monitoring tools on their teen’s phone to track their child’s location (Anderson, 2016). This may be done through features in parental control software, locator apps, GPS trackers, or antitheft software. Such measures not only help to ensure a child’s safety, but are useful to anyone who’s worried about losing or having their phone, laptop, or other devices stolen.
Lost or Stolen
When a computer or mobile device is lost or stolen, you can always go out and purchase a new one, but the information you’ve lost can be devastating. There may be photos that aren’t stored elsewhere, music and books you’ve paid for, as well as other data that may be difficult or impossible to replace. Even worse, you could have credit card numbers or other financial data that could be used to make purchases and ruin your credit.
Protecting yourself involves taking steps before your computer or mobile device is gone. As we’ve discussed in previous chapters, physical security is important to make sure no one can easily walk off with a device and it’s vital to use the security settings available on the devices, apps, and accounts to prevent unauthorized access. In addition, you should document the make and model of the device, as well as any serial numbers that can be used to identify it if it’s later recovered.
Antitheft
As we saw in Chapter 1, What is cyber safety?, phones and tablets have settings that control whether its location can be tracked, enabling apps and websites to show where the device is at a given moment. If turned on, the device may use a combination of data from your cellular network, Wi-Fi, Bluetooth, and GPS to determine where it is. In the case of a computer or laptop, connections to the Internet (such as Wi-Fi) may be used in making a rough estimate of its location. This data may then be used by apps that are installed, and sent to websites to provide location-specific services, such as finding your device when it’s lost or stolen.
Many phones and tablets come with antitheft features that can be activated, allowing you to manage the device remotely and determine its approximate location. These features may include:
![]() Viewing the location, where it displays where the device is on a map.
Viewing the location, where it displays where the device is on a map.
![]() Playing a sound, which will ring or play a loud sound, helping you find it even if the sound is turned off.
Playing a sound, which will ring or play a loud sound, helping you find it even if the sound is turned off.
![]() Locking the device, where you can lock the screen and optionally set a new password, preventing others from using it.
Locking the device, where you can lock the screen and optionally set a new password, preventing others from using it.
![]() Displaying a message, which allows you to show a custom message on the home screen, even if the device is locked, which can be used to provide contact information for returning the phone.
Displaying a message, which allows you to show a custom message on the home screen, even if the device is locked, which can be used to provide contact information for returning the phone.
![]() Wiping the device, which deletes all data and settings from the device.
Wiping the device, which deletes all data and settings from the device.
![]() Flagging the device as stolen, which deletes all data and settings from the device, and registers it as stolen.
Flagging the device as stolen, which deletes all data and settings from the device, and registers it as stolen.
While the features offered on your phone or tablet may vary, the native antitheft software on a device is usually free and may require activation. In addition to turning on the Location Settings on the device itself, this is done by going to the device manufacturer’s or operating system’s site to turn on and use the features. For example:
![]() If you have an Apple device, you can log onto iCloud.com with your Apple ID or use the Find My iPhone app. Once Lost Mode is turned on, any attempts to use Apple Pay on the device is also suspended.
If you have an Apple device, you can log onto iCloud.com with your Apple ID or use the Find My iPhone app. Once Lost Mode is turned on, any attempts to use Apple Pay on the device is also suspended.
![]() If you have a Windows Phone, you can log onto account.microsoft.com/devices and click Find My Phone.
If you have a Windows Phone, you can log onto account.microsoft.com/devices and click Find My Phone.
![]() If you have an Android device, you can use Android Device Manager (www.android.com/devicemanager).
If you have an Android device, you can use Android Device Manager (www.android.com/devicemanager).
![]() If you have a Samsung device, you can use Samsung’s Find My Mobile (https://findmymobile.samsung.com).
If you have a Samsung device, you can use Samsung’s Find My Mobile (https://findmymobile.samsung.com).
![]() If you have a Blackberry, you can use Blackberry Protect (http://ca.blackberry.com/devices/features/security/protect.html).
If you have a Blackberry, you can use Blackberry Protect (http://ca.blackberry.com/devices/features/security/protect.html).
In addition to the native software on a phone or tablet, there are also software products that can be installed on computers, laptops, and other mobile devices. Using antitheft software, locator apps, or certain parental control products, you can view where it’s located on a map and remotely lock it. Some products also provide features to log keystrokes, take screen captures, and perform other actions that may help identify who’s using it and where it is. Antitheft software may also provide the ability to remotely wipe the laptop, phone, or other mobile device, so that they won’t have access to its data. Some of the popular antitheft products available include:
![]() Lojack for Laptops (http://lojack.absolute.com)
Lojack for Laptops (http://lojack.absolute.com)
![]() Lock It Tight (www.lockittight.com)
Lock It Tight (www.lockittight.com)
![]() Prey Anti-Theft (www.preyproject.com)
Prey Anti-Theft (www.preyproject.com)
![]() Hidden (www.hiddenapp.com)
Hidden (www.hiddenapp.com)
![]() Lookout (www.lookout.com)
Lookout (www.lookout.com)
Many antitheft products also include a spy cam feature, which will take photos of anyone in front of the device and save it to their website. This can be useful in showing who’s taken a device and where it’s located. You may find that someone you know has the device, such as a friend, family member, coworker, or fellow student, allowing you to recognize who has it. If you don’t know the person, it can be used as evidence, and may help police discover who took the device.
Other apps and sites
Even if you don’t have antitheft protection setup on your laptop or device, you may still be able to determine its location. Apps and accounts installed on the device that are allowed to access location information may send it via the Internet to their related sites. For example, if your phone has a Google app installed and an account setup, it can be used to send your location information to Google. Such data can be used to determine commute predictions, provide location specific advertising, and where the device has been or is currently located.
After logging onto your Google account, you can visit https://maps.google.com/locationhistory/, and (once turned on) see a map detailing all the locations you’ve been with your device. In the lower left-hand corner, you’ll see an area informing you whether or not Location History is turned on or off. If you want to turn it on, click Enable Location History, and when prompted, click Turn On. To prevent Google from tracking you, you would turn off the feature by clicking Pause Location History, and then clicking Turn Off when prompted.
Finding a Device Finds a Person
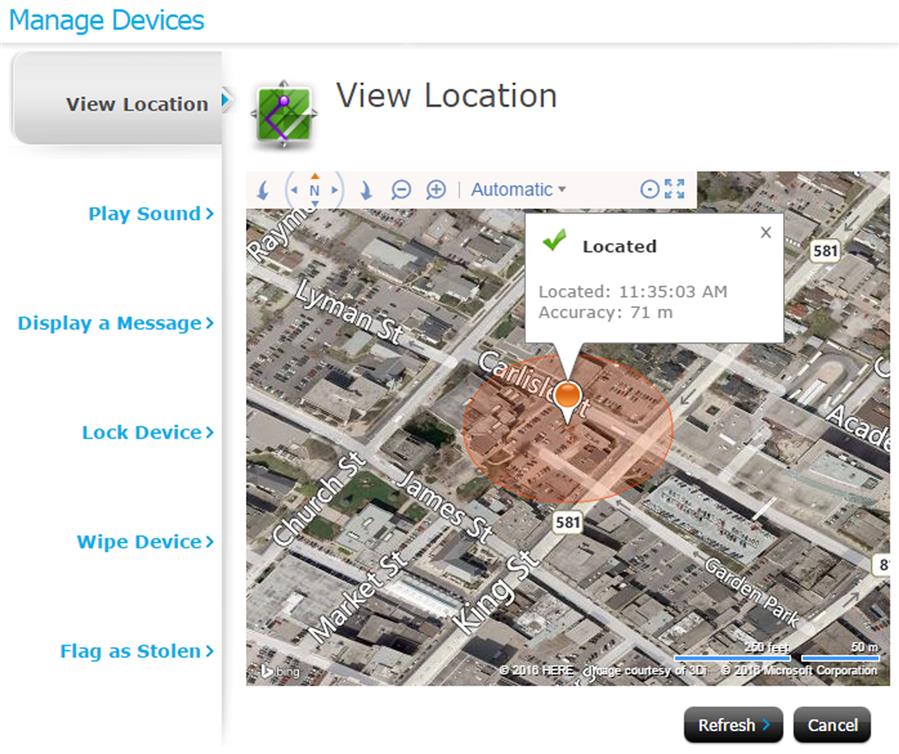
One of the easiest ways to find a device is to use a feature that shows the approximate location of the device on a map. As seen in Fig. 10.4, in viewing the location, a picture of where it is, the time it was located, and the accuracy of its location within a certain distance is displayed. By zooming in and out of the map, you can identify where it is, making it relatively easy to retrieve.
While such apps and sites can be helpful in finding lost or stolen devices, it’s also important that they can be used to track you. Anyone with access to the site or software that shows a device’s location could use it to see where you are, and possibly discern what you’re doing. This can be useful if you’re trying to see where your children are, or disconcerting and dangerous if a suspicious or abusive partner is monitoring your whereabouts. To avoid others from seeing you or your child’s location, make sure that you’ve used a strong password that’s changed regularly to prevent someone from logging in and seeing where you are at any given time.
An app’s ability to determine your location is in your control. To see what apps are using location services, you should review the privacy settings on your phone. As we showed in Chapter 1, What is cyber safety?, if you don’t want your location being available to any app, you can turn location services off. When installing an app, you may also be able to disable its ability to track you by not granting it permission to see your location. If you don’t want your child adjusting these settings, parental control software often has a feature that prevents or limits access.
Finding it safely
While antitheft software and location features can help identify where a device is, it’s also important to remember that it shows the whereabouts of anyone who has it. A thief may be unwilling to part with his or her new acquisition, and could become violent. One of a numerous examples occurred in February 2016, when a 23-year-old man used an app to track his stolen phone to a church parking lot. Upon arriving, he used the app to make his phone ring, heard it inside a vehicle, and was shot and killed when he went to retrieve it (Beasley, 2016). If your phone is stolen, and you use such a feature to track it, always notify the police so they can recover it. Nothing is worth your safety, so let law enforcement take care of it.
Report It Stolen
Once you realize a computer, laptop, or other device is stolen, report it. Once reported, it may be returned to you if it’s later found, and police will provide an incident or report number that you can give your insurance company. Beyond the police, there may be others who need to know it’s missing. If it’s a device that was issued to you by your employer, they’ll need to know if there was corporate data on it, and the Information Technology department may be able to wipe it so any sensitive settings or data is erased. If it was taken at school, you’ll want to report the theft to campus police or the school’s office.
In reporting it lost or stolen, don’t presume detectives are diligently working around the clock to reunite you with your property. An extreme example of how the theft of such devices are considered a low priority was when Joshua Kaufman had his MacBook stolen in 2011. Using antitheft software, Kaufman did his own investigation, found the person with his laptop, and still had difficulty getting the culprit arrested. The software took photos of 27-year-old Muthanna Aldebashi using the computer, logging onto his Google account, and showed email with the name of a cab company he worked for. After submitting the evidence to police, Kaufman found they were unwilling to help and ignored his follow-up emails. Writing about it and posting the pictures on http://thisguyhasmymacbook.tumblr.com and Twitter, his story went viral, and after Good Morning America contacted the Oakland Police Department, an arrest was finally made and Kaufman got his laptop back (Thanawala, 2011).
Even though your expectations may be low in reporting a stolen phone or computer, you can increase your chances of recovering it by working with the police. By using the antitheft software, you can lock the device so it can’t be accessed by the thief, and tell the officer where it’s currently located. Remember that police can’t access this data without your help, so having it ready when an officer shows up to take your report allows for a quicker recovery.
Unfortunately, such tools only work if the phone, tablet, laptop, computer, or other devices can connect to the Internet. If the thief doesn’t connect the computer to the Net and simply removes and wipes the hard disks, or removes the SIM card and prevents Wi-Fi access to a phone or tablet, the antitheft software will never receive any messages to lock, wipe, or reveal its location. In such cases, your only choice is to replace it or hope it’s recovered.
You may also be able to increase your chances of recovering a device by registering them on sites that may be used by pawn shops, second-hand buyers, or police to identify lost or stolen items. When recovered, checking the database will identify you as owner, making it easier to return what’s been stolen. Some of the sites available include:
![]() Immobilize (www.immobilize.net)
Immobilize (www.immobilize.net)
![]() CheckMEND (www.checkmend.com)
CheckMEND (www.checkmend.com)
![]() Trace (www.tracechecker.com)
Trace (www.tracechecker.com)
![]() Stolen Register (www.stolenregister.com)
Stolen Register (www.stolenregister.com)
![]() Stolen 911 (www.stolen911.com)
Stolen 911 (www.stolen911.com)
Also, don’t forget that you haven’t just lost the phone, but all the data on it. When someone has access to your accounts and sensitive information, you should take steps to change your passwords, contact banks, issuers of credit cards, and other organizations related to any data that may have been compromised.
Blacklists
If your mobile device is stolen or lost and irrecoverable, you should contact your carrier and report it stolen. In doing so, they can add the device’s International Mobile Equipment Identity (IMEI) number to a national blacklist. The IMEI is a 15-digit number that uniquely identifies the device, and any IMEI that appears on a blacklist can’t get service from carriers, and is blocked by wireless service providers. Essentially, the device is unusable because it can’t be used to make calls or connect to the Internet.
If you’re buying a used phone, it’s important to check whether the IMEI has been added to a blacklist. To do this, you first need the device’s IMEI number. On most mobile devices, you can dial *#06# to see a message that displays the number. You can also find a device’s IMEI and serial number on the device by doing the following:
![]() On an iPhone, iPad, or iPod Touch, tap Settings, tap General, and then tap About.
On an iPhone, iPad, or iPod Touch, tap Settings, tap General, and then tap About.
![]() On an Android device, tap Settings, tap About phone/About table, and then tap Status.
On an Android device, tap Settings, tap About phone/About table, and then tap Status.
![]() On a BlackBerry, tap Settings, tap About, tap the Category dropdown, and select General to view the serial number or Hardware to view the IMEI.
On a BlackBerry, tap Settings, tap About, tap the Category dropdown, and select General to view the serial number or Hardware to view the IMEI.
Once you have the number, you can then use various sites on the Internet to determine whether it’s being sold legally. If you’re purchasing a used iPhone, iPad, iPod Touch, or Apple Watch, you can visit iCloud’s Find My iPhone (www.icloud.com/activationlock/), enter either the device’s IMEI or serial number, and see if the activation lock has been disabled. If it was stolen, and someone used Find My iPhone to lock the device, it’s unusable until the correct Apple ID and password have been entered. Many carriers and resale sites like Swappa (www.swappa.com/esn) also provide the ability to check the IMEI or serial number. Telecommunications sites in some countries may also provide the ability to check if a device is blocked by that nation’s service providers, as in the case of:
![]() Canadian Wireless Telecommunications Association (www.protectyourdata.ca/)
Canadian Wireless Telecommunications Association (www.protectyourdata.ca/)
![]() Australian Mobile Telecommunications Association (www.lost.amta.org.au/IMEI)
Australian Mobile Telecommunications Association (www.lost.amta.org.au/IMEI)
Remote wiping
When you’re sure that the device is stolen or can’t be recovered, there comes a time when you should consider wiping it. When you remotely wipe a device, it deletes any data and settings on the device and does a factory reset. This means that any apps or accounts that may be used in locking or locating it are erased on the device, and can’t be used to identify where it is or protect it, so you should be careful when you choose to take this step.
As we’ve mentioned, antitheft features may need to be activated on a phone prior to using the features, so you will need to setup your mobile device first. For example, before you can remotely wipe an android device, you need to set it up to be locked and erased. To do this, go to the Android Device Manager site (www.google.com/android/devicemanager), and log in with the Google account associated with your device. Once you’ve selected the device you want to configure:
1. Click on Set up Lock & Erase
3. Drag down the notification bar, and tap Android Device Manager
5. Switch Remote Locate and/or Remote Lock and Factory Reset so they’re enabled.
Once the Android device is setup to be remotely wiped, you can then erase it by going to the Android Device Manager site, clicking on the Erase button, and then confirming it when prompted.
It’s important that you back up your computer and any mobile devices on a regular basis, and keep a list of accounts and passwords you use up-to-date. If you lose the device and need to wipe it, your files, apps, accounts, and other data will be erased. Even if it’s later returned to you, anything on it will be gone. You’ll want to have a recent backup and list of accounts and passwords stored in a safe location so you can use them to restore the data and regain access to any sites and systems you use.
Once you’ve wiped a device that’s no longer being used or available to you, you should revoke its access from any online sites and services that use it. For example, you may have setup the phone or tablet to access social media sites through various apps, or work with particular accounts.
Resale
A device being stolen isn’t the only time you’ll want to wipe a device. Prior to selling an old computer, laptop, phone, tablet, or other mobile device, you should remove any personal data that the new owner could use to access you or your child’s online accounts or see sensitive information. For phones and tablets, you should backup your data (including any contacts), log out of any services like email or social media accounts, and remove the SIM card and any SD cards used for additional storage. Even though you’re selling the device, you may be able to use the SIM and SD card on your new phone or tablet. Once done, you can wipe the data and do a factory reset, which essentially reverts the device to the state when you originally bought it.
Once you’ve wiped a device that you’ll no longer be using, you should also revoke its access to any online accounts it may have been setup to use. For example, if you have a Google account, you would go to http://myaccount.google.com, and then:
2. In the left pane, click Device activity & notifications
3. Under Recently used devices, click on Review Devices
4. Click on the device you want to remove, and then click the Remove button to revoke that device’s access to your account.
You should also take steps to remove any data from laptops, computers, or storage devices (such as an external hard disk) before its resale or disposal. Taking the extra step of formatting the hard disk(s) will make sure any files or sensitive data stored on it are erased. Wiping the data correctly is important. Depending on how you format the drive, data may be left behind.
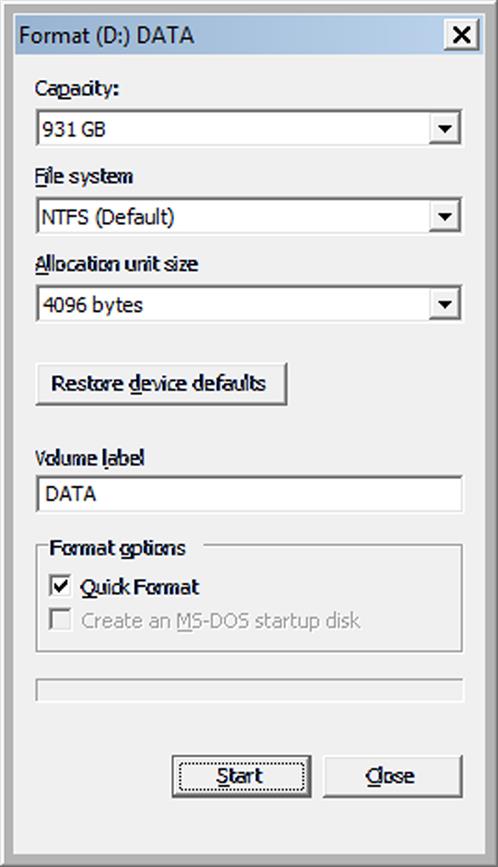
In Windows Explorer (or File Explorer), you can format a drive by right-clicking on a drive letter, and then clicking Format on the context menu that appears. Once done, a dialog box similar to what’s shown in Fig. 10.5 should appear. In looking at it, you’ll notice that Quick Format is the default option. It’s quick because it wipes the file table, but doesn’t actually wipe the drive. If you uncheck the Quick Format option on Windows Vista and up, the disk will be formatted and overwrite all of the existing content with zeros.
Until data is overwritten it can still be recovered. Even if the drive is quick formatted, so long as the disk isn’t used and data isn’t written to it, you can still use recovery tools to unformat the drive and restore the data. For an additional measure of safety, you should use a tool that will overwrite data on the disk multiple times. Tools like CCleaner (www.piriform.com/ccleaner) can be used to securely erase the drive. Other tools like Eraser (http://eraser.heidi.ie) use different methods and patterns to overwrite data multiple times, making it impossible to restore. It also has features that allow you to schedule overwriting free space on your drive, so that any deleted files are securely erased at regular intervals.
Talking About What’s Inappropriate
The Internet is no different from any new environment. When your child was very little, you probably told them look both ways before crossing the street, and explained doing so might prevent them from being hit by a passing car or bike. You also probably explained the etiquette of human interaction by saying please and thank you, being mindful of others and wary of strangers. In the same way, children need to understand the risks, remedies, and acceptable behavior of being online so they can stay out of trouble.
Because children use computers and the Internet at an early age, it’s wise to start training as soon as they begin using technology. If you think your child is too young, consider that a preschooler watching his or her favorite TV show will hear invitations to “visit us online” at a particular URL, or may even use a computer preloaded with children’s sites and software at a daycare or library. Even though a child may have restricted exposure, they should understand that there are limits to when and how long they can use a device.
Letting them know what they can use on a computer or other device is also important to learn early. While you’ll probably be sitting beside them as they interact with an educational game or site at first, eventually they’ll need to know what icons they can click on and sites they can visit. As they get older, they’ll realize there are sites and apps for specific age ranges and uses, and not all of them are ones that they’re allowed to use. This can be helpful in starting a discussion on what’s age appropriate, and talking about age restrictions and ratings on games and apps.
At all times, regardless of your child’s age, they should feel comfortable discussing the Internet, problems they encounter, and feel free to ask for help. Staying supportive and positive will help them in keeping the lines of communication open as they get older. You should also realize that any discussions won’t be a one-time thing. You’ll often need to repeat the information, allowing them to soak it in over time.
Your child isn’t the only one you should discuss the rules with. You should let any babysitters, parents of your child’s friends, and others who may look after the child know about the limits you’ve imposed. Doing so will add consistency in what the child is allowed to do, regardless of where he or she is.
Setting Expectations
As your child gets older, they should have a clear understanding of what you expect from them online, your values, and what’s considered appropriate. They should also have an understanding of what’s age appropriate for them, and what they shouldn’t show a younger brother or sister. While they’ll come to realize that what’s forbidden at one age may be permitted later, they should know that some rules apply to any age and that you follow similar rules. These include:
![]() Don’t reveal passwords, and use secure passwords, as we discussed earlier.
Don’t reveal passwords, and use secure passwords, as we discussed earlier.
![]() Never share personal information online. This includes addresses, school names, where they currently are or will be later, phone numbers, birthdates, age, and so on.
Never share personal information online. This includes addresses, school names, where they currently are or will be later, phone numbers, birthdates, age, and so on.
![]() Realize that a person may not be who they claim to be online. Just because they say they’re a friend-of-a-friend or someone they know may not be the case.
Realize that a person may not be who they claim to be online. Just because they say they’re a friend-of-a-friend or someone they know may not be the case.
![]() Acceptable sites. A younger child should be limited to a list of specific sites, but they should understand that as they get older, certain kinds of sites or content are never allowed.
Acceptable sites. A younger child should be limited to a list of specific sites, but they should understand that as they get older, certain kinds of sites or content are never allowed.
By setting boundaries before they get their own accounts or devices, you’ll be better able to set expectations, modify settings, and install software to monitor and protect them. Once they have their own accounts and devices, you’ll find you’re in for a more difficult time-changing settings and monitoring the way it’s used.
Conduct
As we saw in Chapter 9, Beyond technology—dealing with people, there are expectations on how to act online. Netiquette shows us the accepted behavior in dealing with others, and they should know that there are trolls and other abusive people who may make things difficult for them. They should know what you expect from them, and what they can expect from others.
A person’s conduct also relates to how they present themselves online. Impersonating an older person can attract someone who thinks you’re of age, inviting discussion that isn’t suitable for a child, and possibly accessing content that may be disturbing. One study found that 44% of online teens admitted to lying about their age to access a site or sign up for an online account (Lenhart et al., 2011). It’s important they understand that sites put such limitations in place to protect those under a certain age from viewing inappropriate content.
Your child should also know what’s appropriate to post and share with others, including anything they write, photos, videos, and other content they create. Once online, it can be difficult to remove and may be available for others to see in years to come. If it violates the policies of the site being used, it could also result in their accounts being disabled or deleted. At all times they should go with the philosophy that if they have to hide what they’re doing, they shouldn’t be doing it.
Content
While parental controls can block and filter certain content, it doesn’t mean your child shouldn’t have an understanding of what they are and aren’t allowed to view. Explain to your child why the settings are as you’ve configured, so they know to avoid certain sites and apps that you’ve deemed inappropriate. After all, just because parental control software prevents them from visiting such sites on your computer, doesn’t mean they’re blocked on a friend’s tablet or a public computer (such as one at school or a library). Explain your concerns with certain content so they know what to avoid.
As we saw in Chapter 5, Cybercrime, a common target of identity theft is children. Let your child know that it’s important not to share personal information. They should know that emails, online forms, questions asked when creating an account, and even surveys or questionnaires may be phishing expeditions designed to provide details. To prevent particularly sensitive information like national identification numbers (e.g., Social Security Number) from being shared, keep such documentation out of their reach. If they don’t know it, they won’t be tempted to share it. (Lenhart et al., 2011).
Teens may also use various tools to send texts with photo or video. For example, Skype (www.skype.com) is popular with Web chatting, while apps like Snapchat (www.snapchat.com) allow you to send an image or video that the recipient can only view for a certain period of time (such as 10 seconds or so) before disappearing. Because people using Snapchat believed the photo was deleted and gone forever, the 2014 hack dubbed the “Snappening” in 2014 was a surprise to many when thousands of images were stolen and leaked on the Internet. Being that a large portion of Snapchat users are underage teenagers, the seminaked or naked photos appearing online were a shock to many. Even if the software streams video or promises to delete or make an image disappear after a set time, the seconds its visible is often long enough to make a screenshot of it.
Your child should also know that just because someone said something, it’s not necessarily true. Anyone can create a blog or web page, and appear like they’re giving expert advice. If they were looking for information about how to deal with personal problems, how their bodies are changing, relationship advice or other facts of life, they could get skewed facts or inaccurate details. Let them know that you’re available as a resource, and they can talk to you or get your opinion on the articles they read.
Contact
Most parents want to know who their child associates with. You might have conditions on meeting their friends before they go out, and meeting the parents before dropping them off at a sleepover. The question is, do you really know who they’re associating with online?
Even though many social media sites may have age limitations, many parents allow an underage child to have an account. A child may have their own Facebook account or YouTube channel under a false age, so they can associate with classmates or share homemade videos. If they do, you should have an agreement with them so you can monitor their account, and preview any content they publish. You should also do such things as:
![]() Make sure they know that just because someone asks to be a “friend,” they may not be. Don’t blindly accept friend or buddy requests. For younger children, they should ask you first if they can accept.
Make sure they know that just because someone asks to be a “friend,” they may not be. Don’t blindly accept friend or buddy requests. For younger children, they should ask you first if they can accept.
![]() A person may pose as someone they aren’t online. A person seeming to be a child could actually be an adult with a fake profile.
A person may pose as someone they aren’t online. A person seeming to be a child could actually be an adult with a fake profile.
![]() Make younger children understand that many people have the same name, so they shouldn’t make or accept friend requests without talking to them at school or by calling first.
Make younger children understand that many people have the same name, so they shouldn’t make or accept friend requests without talking to them at school or by calling first.
![]() Even if it is a friend, someone else could be using their account. Their real friend may have lost a phone or had their account hacked, meaning a stranger is actually texting, or it could be the friend’s sibling or someone else posing as them.
Even if it is a friend, someone else could be using their account. Their real friend may have lost a phone or had their account hacked, meaning a stranger is actually texting, or it could be the friend’s sibling or someone else posing as them.
![]() Never agree to meet anyone online, or do anything that makes you feel uncomfortable.
Never agree to meet anyone online, or do anything that makes you feel uncomfortable.
![]() If it is a friend of your child that you know, and they’ve made arrangements to meet, always meet at a safe location. Again, it could be someone posing as them.
If it is a friend of your child that you know, and they’ve made arrangements to meet, always meet at a safe location. Again, it could be someone posing as them.
It’s wise to review your child’s friend list occasionally to ensure they are people you know. If your child has 300 friends, chances are that they aren’t people they know. Going over the list will help you understand who their friends are, where they met, and how long they’ve known each other. For younger children, you should limit it to trusted relatives and only friends of theirs that you know. Anyone you’re unsure of, or who is posting questionable material should be removed.
Cyberbullying
A few decades ago, a child might be limited to being bullied on the playground or the walk home from school. Once in their house, they had the comfort of knowing they were safe until the next school day. With the Internet, those days are long past, and a bully can torment your child online, no matter where they are or what time it is.
Cyberbullying is the act of harassing someone online, and may take the form of aggressive comments, offensive names, or embarrassing someone on purpose. While the act of bullying is most associated with children and teens anyone can be the victim of online harassment. If you think that it’s a limited problem, consider that even if your child isn’t bullied directly, they can still experience the cruelty second hand. In one study (Lenhart et al., 2011) it was found that 88% of teens using social media had seen someone being cruel or mean to another person, with 12% of them saying they witnessed it frequently and 15% saying they were the target.
The effects of bullying can last for years after its ended, and have a negative impact on a child’s confidence, self-image, and feelings of self-worth. They can experience anxiety, depression, and other psychological effects, and in the most extreme circumstances even have thoughts of selfharm or even attempt/commit suicide. This isn’t intended to frighten you as a parent, but to provide a better understanding of the need to step in and help, so the child isn’t left to fight his or her own battles.
If they encounter someone bullying or pressuring them to do things they shouldn’t, your child should have a clear understanding that they should immediately come to you. When they do, keep a clear head. If the bully is someone your child knows in real life, you can try and get others involved. Since schools commonly have antibullying policies, you should check the website of your child’s school district and review the policy. Once you know what they can and should do under their policy, let the school know about the problem. You should also keep a record of any incidents, just in case you need to contact the police. Depending on your child’s age, the police could intervene and talk to the bully’s parents, or possibly charge the teen bully with harassment, threatening, or assault if that’s occurred.
For online bullying, take screenshots of any incidents that show your child is being harassed. These can be used to backup any claims and shown, if necessary, to the school or police. Even if you don’t know a bully in real life, you can block the person from contacting you and report them to the site. In doing so, their account may be disabled or deleted. Let your child know that they shouldn’t engage the cyberbully online, or react in any way, but should work with you to save the evidence and not to delete it. This may also help the child feel that they’re fighting back with you as an ally.
In talking to your child, let them know that bullying of any kind is wrong. While making a cruel comment to a post may seem funny, and joining in the mob mentality may make you feel part of the crowd, it’s not acceptable. Even though it’s online, it affects someone in real life.
Calls
Today, a bully can use a variety of tools to harass someone. One study found that after ending a relationship, 22% of teens experienced their ex using the Internet or cellphone to call them names, put them down, or say cruel things about them. Fifteen percent said their former partner used such technologies to spread rumors about them (Lenhart et al., 2015). Bullies may also use various technologies to automate the process of harassing someone.
While you may have made one or two prank calls to someone, there are free and commercial sites that allow you to send a recorded prank call from a phone number that’s not your own. Some allow you to enter someone else’s number, while others will send it from an anonymous number. Using this, the cyberbully can enter your phone number, click a button, and the service will repeatedly call you over and over again a set number of times.
By using features that may be already included on your phone, or contacting your phone service provider for help, you may be able to use features that will block such calls. There are services that will block a number you specify, or any numbers where the number is unknown, unavailable, or private. They may suggest you dial *60 and set up call screening, which allows you to block numbers from calling you. The phone company may also suggest you trace the call by dialing *57 the next time you receive a prank call, and following the recorded prompts. In doing so, police may be able to use the information to arrest the person harassing you.
The site the bully is using may also have features to add your number to a do-not-call list. By visiting Stop Prank Calls (www.stopprankcalls.com), you’ll find a list of links to a page on the most popular prank call sites, where you can enter your number so no more calls are sent from the site. If you know the bully’s number, add their number as well. This will prevent them from sending a prank call to their phone, having it forwarded to an IP phone, which then is set up to call you. The bully could have your phone number or theirs removed from the do-not-call list, but most sites will only remove it for a fee. If they try again, it can become a costly endeavor for the person harassing you.
Sites that make such anonymous calls aren’t the only issue with unwanted calls from a bully. If the person has setup an IP phone number, you may find it difficult to track where the calls are coming from. Unlike a landline, you can purchase a phone number with an area code corresponding to other locations throughout the world. For example, Skype allows you to purchase a number that allows local calls for area codes in different countries. Similarly, if you have a Gmail (www.gmail.com) account, you can use Google Phone to make calls. If this is the case, and the person is switching between numbers, you may need to attempt blocking several different numbers.
Another option is parental control software or call-blocking apps, which you could use to create a whitelist of people who may call the phone, and/or a blacklist of blocked numbers. If all else fails, you could simply get a new phone number. If you keep the number private, and don’t share it with anyone associated with the bully, they’ll be unable to call.
Online Predators
An online predator is someone who sexually exploits a child over the Internet. The pedophile may lure the child gradually through gifts or affection; coerce them through threats or extortion, or other methods where the predator will attempt to get what they want. This may be an attempt to get the child to pose for suggestive or explicit images, or meet in person so they can be sexually abused.
Because a pedophile targets children, he or she will be aware of the latest fads, music, and interests of an age group they’re interested in. They may spend significant time getting to know the child, and because they know what the child likes, can pose as one online. By talking to the child in chats, messages, or comments in posts, he or she will get to know the child, build trust, and lower inhibitions. Because a child may be curious about sex, the predator may share child pornography with them, introducing a sexual aspect to the conversation and/or finding what he or she likes. He or she may then ask your child to take a similar picture of themselves, engage in video chat, or meet secretly in person.
While most pedophiles are adult men, they can also be female. They may be strangers, but may also be someone you know, such as a bodyfriend or relative. The threat of your child being approached sexually online can also occur with someone closer to your child’s age. For example, someone in their early twenties may seek out a young teen, or an adolescent may desire a young child. To protect your child, you should be aware of anyone your child is interacting with online, and certain signs that they’re at risk, such as:
![]() The presence of child pornography on the computer. The predator may introduce such imagery to convince them that sex between a child and adult is normal, to engage in a sexual discussion, or get the child to take a nude or seminude picture of themselves.
The presence of child pornography on the computer. The predator may introduce such imagery to convince them that sex between a child and adult is normal, to engage in a sexual discussion, or get the child to take a nude or seminude picture of themselves.
![]() The time your child spends online. Because adults generally work during the week, the time spent finding children is often limited to the evening and on weekends. A tendency to go on the Internet after dinner and on weekends may indicate they’re spending time with an adult.
The time your child spends online. Because adults generally work during the week, the time spent finding children is often limited to the evening and on weekends. A tendency to go on the Internet after dinner and on weekends may indicate they’re spending time with an adult.
![]() Sudden gifts, packages, or mail from someone you don’t know.
Sudden gifts, packages, or mail from someone you don’t know.
Another indication that something’s wrong is seen in the calls they receive, and discussions they’re having. Phone sex may be a precursor to trying to meet the child for real sex, so review numbers on your child’s phone and to your house. Look for sudden phone calls from numbers you don’t recognize, long distance numbers, or calls from adults asking to speak with your child. Also, try to listen to how they’re responding to audio conversations on game systems where headsets are used to chat, as well as audio or video chat to determine whether they’ve taken a sexual turn or they’re responding to odd questions. If they suddenly turn off the monitor, or take action to prevent you from seeing or hearing what’s being said, it can also indicate they’re involved in a sexual conversation.
Children targeted by a sexual predator will often become withdrawn from the family, and distance themselves from those they previously trusted. The child may have been told to keep a secret, the predator may be working to cause discord or drive a wedge between the child and family, and/or the child may have already been victimized.
To protect your child from online predators, you can use parental software to monitor their internet activities and check their accounts manually, which allows a greater chance of detecting a problem early. You should also talk to them about any suspicions or concerns you might have. If they know about a potential danger and how online pedophiles work, there’s a greater likelihood that they’ll be able to recognize the threat before it goes too far. They should know:
![]() Never give out their phone number, address, or other personal information to anyone online, and never agree to meet anyone they’ve met online. If they do, a virtual threat may become a real one.
Never give out their phone number, address, or other personal information to anyone online, and never agree to meet anyone they’ve met online. If they do, a virtual threat may become a real one.
![]() Never download files or pictures from an unknown source.
Never download files or pictures from an unknown source.
![]() Never reply to messages that are suggestive, indecent, or mean in any way.
Never reply to messages that are suggestive, indecent, or mean in any way.
![]() Trust their instincts. If they suspect a problem, are asked to do anything that makes them uncomfortable, or told not to tell or trust their family, they should end any communication and tell their parents, a teacher, or another responsible adult that’s around.
Trust their instincts. If they suspect a problem, are asked to do anything that makes them uncomfortable, or told not to tell or trust their family, they should end any communication and tell their parents, a teacher, or another responsible adult that’s around.
If your child is contacted by a sexual predator, you should report it. Contact the police, and report it online. In the United States, you can report it to the National Center for Missing and Exploited Children (www.missingkids.com), while in Canada you can contact the Canadian Centre for Child Protection (www.cybertip.ca). Your child should know that if they were targeted by a sexual predator, it’s not their fault and nothing they did was the cause of it.
Privacy
Everyone has an expectation of privacy, even children. These expectations grow as we mature, but as we saw in previous chapters, the reality of privacy on the Internet may not match a person’s expectations. Regardless of whether you’re the parent of a young child or teen, they should understand that what they say and do online may not necessarily be private.
If you’re using parental controls or other monitoring software, it’s important for your child to know that you have the ability to see and limit what they’re doing even if you’re not physically there. They should know that you’re not necessarily doing this because you don’t trust them, but to help them if they encounter any problems. For example, if they were bullied, any logging might help prove there’s a problem to police or teachers. Similarly, blocking certain sites will protect them from seeing disturbing content, and lowering the risks of getting malware. They should also know that you’re willing to discuss any restrictions, so that you can compromise without jeopardizing their safety and the security of any devices they’re using.
Just as you might reserve the right to go into their bedroom, they should understand that any technology and accounts they use will also be open to your review. If you feel they may be at risk, you may feel the need to review their email, contacts, friends on social media, and other aspects of their life online. If you’re concerned that doing so is being overprotective, keep in mind that 43% of parents of teens know the password to their kid’s email account, and 35% know the password to at least one of their child’s social media accounts (Anderson, 2016).
Your child should also understand that you’re not the only one who can see what they’re doing online, and the lack of anonymity they have. If they’re using a computer at someone else’s house, there’s no way of knowing if there’s a keylogger installed, which can capture any passwords or other information entered. Schools and libraries may also monitor what’s happening on the computers they use, allowing them to log the sites they visit and other activities. Let them know that you’re not the only one who may be watching.
You should configure the privacy settings on any social media or other online accounts your child uses. You should review these settings with them, and understand that these should be changed, and no personal information should be added to profiles. If you don’t require them to check with you before creating new accounts, it’s especially important they learn how to do it themselves.
Summary
Understand that kids accept technology and have a good understanding of it. In discussing it with them, you may find they even know more than you. Even if they seem to be an expert on how to use it, it doesn’t mean that they’re able to handle the social interactions and problems they may encounter online.
As we saw in this chapter, there are a number of tools you can use online to protect your child and the devices they use. These include parental controls, antitheft software, and other software that can be installed to provide security. Combined with this is a need to talk to your children, and make them understand the basic steps in keeping themselves safe online, so they know the pitfalls and possible solutions available to them.