Beyond technology—dealing with people
Abstract
This chapter discusses issues with dealing with people online. It discusses how netiquette is used to provide guidelines of proper behavior, and the issues of believing there’s anonymity online. We also discuss some of the problem people online, such as trolls, cyberstalkers, and others who range from annoying to dangerous. We’ll look at a number of ways that people are meeting online and how to bridge the gap between meeting in cyberspace and the real world.
Keywords
Cyber safety; online dating; trolls; cyberstalking; netiquette; profiles; identities
One of the main reasons we go online is to interact with others. You may be playing games with others on sites or a game system, writing blogs to share your insight, posting pictures for distant family members, hoping to meet a special someone or share your deepest thoughts and desires with a stranger. Whatever the reason, whether the relationship is cursory or long-standing, you will meet people on the Web. These interactions can have different dynamics from the real world, and bring with them their own set of risks.
Netiquette
There are rules of behavior for any social situation, including what to do online. Netiquette is short for network etiquette, and are conventions on socially acceptable conduct when engaging others on the Web. Just as there are socially agreed upon rules when talking on the phone (such as answering with “hello,” and ending a conversation with “goodbye”) there are similar concepts when using social media, chat rooms, and other Web-based technology.
The reason netiquette is important is because of the way most interactions are conducted online. If you and I had a face-to-face conversation, part of how you’d understand the meaning of what I said would be by watching my facial expressions, body language, and hearing the inflections in my voice. Since most online conversations are textual, these visual and audio cues aren’t available, so you wouldn’t be able to interpret what I really mean by a comment. If you posted a picture, and I commented “nice hair,” you couldn’t tell by simply reading the words if the statement was sarcastic, flattering, or nasty.
The rules of netiquette weren’t invented by a single person. As with any social convention people organically come to agree on what is considered proper behavior as they participated in Bulletin Board Systems and later the Internet. Certain codes were developed over time, and were expected from others who joined after they’d been established.
Largely, the core rules of netiquette involve interacting with someone as you would want to be treated, but remembering that they can’t actually see you. Some of the basic rules of netiquette you should be aware of include:
![]() Not typing in capital letters, as IT LOOKS LIKE YOU’RE SHOUTING.
Not typing in capital letters, as IT LOOKS LIKE YOU’RE SHOUTING.
![]() Remember where you are. The rules for your behavior depend on where you’re posting, so look at how others are conducting themselves before jumping in. One room may allow rude comments and dirty jokes, while another will expect you to be on your best behavior.
Remember where you are. The rules for your behavior depend on where you’re posting, so look at how others are conducting themselves before jumping in. One room may allow rude comments and dirty jokes, while another will expect you to be on your best behavior.
![]() Respect the privacy of others. While you may not have a problem saying something about yourself, others might. Mentioning the name of someone’s child, where they work, the state of their relationship, or other details, may offend the person you’re talking about.
Respect the privacy of others. While you may not have a problem saying something about yourself, others might. Mentioning the name of someone’s child, where they work, the state of their relationship, or other details, may offend the person you’re talking about.
![]() Apologize for your mistakes, and forgive others. Just as you’d want someone to pardon your mistakes, excuse others when they make one.
Apologize for your mistakes, and forgive others. Just as you’d want someone to pardon your mistakes, excuse others when they make one.
![]() Use your power wisely. If you have the ability to perform an action that affects others (such as deleting their posts, kicking them out of chat rooms), don’t let it go to your head. Don’t do things to others that you don’t want done to you.
Use your power wisely. If you have the ability to perform an action that affects others (such as deleting their posts, kicking them out of chat rooms), don’t let it go to your head. Don’t do things to others that you don’t want done to you.
![]() Be authentic and helpful. You may be an expert or be able to provide advice to others on a problem they’re having. By showing you’re helpful and knowledgeable, it will make everyone’s experience a better one.
Be authentic and helpful. You may be an expert or be able to provide advice to others on a problem they’re having. By showing you’re helpful and knowledgeable, it will make everyone’s experience a better one.
![]() You don’t need to comment on everything! Some people feel the need to weigh in on every topic or post, regardless of whether they have anything relevant to say. If someone asks a question, and you can’t help them, don’t answer “I don’t know.” Simply ignore the post and move on.
You don’t need to comment on everything! Some people feel the need to weigh in on every topic or post, regardless of whether they have anything relevant to say. If someone asks a question, and you can’t help them, don’t answer “I don’t know.” Simply ignore the post and move on.
Emoticons
Emoticons are small pictures or keyboard strokes that convey a mood or facial expression. For example, if you were to type :) it looks like a smiley face, if you’d turned your head. Similarly, :(looks like a frown, and :P looks like a silly expression of someone with their tongue hanging out. Some sites like Facebook, email, and chat programs will actually convert these into actual pictures of a smiley face, frown, or other image. They may also offer you the option of clicking on an icon to select a picture to include in your post, which helps convey a particular feeling.
When making comments, emoticons are useful in expressing your intentions, and will help a person realize you’re joking or upset. However, you should only use them in informal conversations and emails, and not ones where you’re trying to maintain a level of professionalism.
Understanding the Lingo
The longer you’re online, the more you’ll notice abbreviations, acronyms, and slang being used. In many cases, these are used to decrease the amount of typing required to write a text message, comment in chat, or respond to a particular post. Some of the common ones you’ll come across include:
![]() A person may shorten a phrase to letters and numbers that sound similar or identical. “See you” is written as cu, “see ya” is written as cya, and “hater” is shortened to h8r.
A person may shorten a phrase to letters and numbers that sound similar or identical. “See you” is written as cu, “see ya” is written as cya, and “hater” is shortened to h8r.
![]() Acronyms may be used to shorten a phrase to a few characters. For example, btw is an acronym for “by the way,” lol is “laughing out load,” brb is “be right back,” imho is “in my humble opinion,” and rotflol is “rolling on the floor laughing out load.” Acronyms are also used on sites to describe certain content, such as FAQ standing for “Frequently Asked Questions.”
Acronyms may be used to shorten a phrase to a few characters. For example, btw is an acronym for “by the way,” lol is “laughing out load,” brb is “be right back,” imho is “in my humble opinion,” and rotflol is “rolling on the floor laughing out load.” Acronyms are also used on sites to describe certain content, such as FAQ standing for “Frequently Asked Questions.”
![]() Comments may be shortened to obtain information. For example, in chat rooms, a person might start a conversation with a/s/l, meaning “age/sex/location.” What they are asking is your age, gender, and a rough idea of where you are. This is done to find basic information and determine if you have the basic qualities for further discussion. If they want to later engage in sex chat (discussed later in this chapter), they will do this to ensure you’re of legal age, a gender they’re attracted to, and (possibly) within a meeting distance. Often, location is merely asked as a springboard to start further conversation, such as asking “How’s the weather there?”
Comments may be shortened to obtain information. For example, in chat rooms, a person might start a conversation with a/s/l, meaning “age/sex/location.” What they are asking is your age, gender, and a rough idea of where you are. This is done to find basic information and determine if you have the basic qualities for further discussion. If they want to later engage in sex chat (discussed later in this chapter), they will do this to ensure you’re of legal age, a gender they’re attracted to, and (possibly) within a meeting distance. Often, location is merely asked as a springboard to start further conversation, such as asking “How’s the weather there?”
![]() Comments shortened to hide information. You’ll often people (especially teenagers) using terms in chat, texts, and posts that are used to hide what’s being said from parents. Some of these include 9 for “parent watching,” 99 for “parent gone,” PIR for “parent in room,” and NIFOC for “naked in front of camera.”
Comments shortened to hide information. You’ll often people (especially teenagers) using terms in chat, texts, and posts that are used to hide what’s being said from parents. Some of these include 9 for “parent watching,” 99 for “parent gone,” PIR for “parent in room,” and NIFOC for “naked in front of camera.”
While some terms have been around for decades, the language of the Internet does change with new terms appearing frequently. If you’re unsure of what’s being said, there are some sites that serve as a dictionary of Internet jargon, which you can use to decipher what’s being said:
![]() Internet Slang (www.internetslang.com)
Internet Slang (www.internetslang.com)
![]() NetLingo (www.netlingo.com)
NetLingo (www.netlingo.com)
![]() Urban Dictionary (www.urbandictionary.com)
Urban Dictionary (www.urbandictionary.com)
Anonymity
Anonymity is the state of having your identity hidden, so it isn’t visible to others. An Internet Service Provider (ISP) or a site you’ve logged onto may know your identity, but you want to remain anonymous to others, and not have personally identifying information shared with third parties. People may also want different levels of privacy for what they do online, ranging from a basic desire for confidentiality to complete secrecy.
Although we’ve talked about privacy settings throughout this book, staying anonymous online often goes beyond the basic settings. For most people, a need for anonymity often varies between sites and situations. While you always want personal, sensitive, and financial information to be kept private, there are moments when you may want to hide many or all details of your identity. You may setup an account to chat online with an alias, use online dating, or engage in peer-to-peer file sharing with torrents. In these and other circumstances, you may want a higher level of anonymity because there’s a greater need for discretion or an activity presents greater risks.
The Effect Perceived Anonymity Has on People
There are good reasons why people want to remain anonymous. Perhaps you’ve read an article, and want to make a comment, but don’t want to get into a big discussion on how your views conflict with the norm or other people’s opinions. In these cases, the site may allow you to post anonymously, so the site knows your identity, but it’s hidden from others. If the ability to review a product or provide an opinion wasn’t there, you might decide it’s not worth weighing in with your opinion. While anonymity gives you the freedom to express yourself, it can also make you feel there’s no culpability of your actions.
A price of anonymity is accountability. When people hide their identity or use an alternate persona online, they may feel they have freedom to say or do what they want. The person may post comments they wouldn’t normally say to your face, visit sites, and view content they might otherwise never consider looking at, and do things that are contrary to their normal behavior. Because they feel no one knows who they are, the restraint of thinking they’ll get caught or “what would so-and-so think if I did this?” is removed. The social constraints that keep their conduct and actions in check aren’t there, and this can cause some people to act differently and take risks they wouldn’t normally take.
Being Wary of Others and Yourself
The effect anonymity has on some people can be extreme. Some people will post inflammatory comments and derogatory remarks in the hopes of starting an argument, or simply to cause problems. Others may go a step further and bully another person, posting negative comments, creating rumors, and making their online experience a miserable one. Others may lurk in the shadows, watching what you do and post online, as they stalk you from a distance. The belief that they’re hidden and disconnected physically from others who might hold them accountable can give these people a false sense of power.
While we’ll discuss these and other threats later (in this and other chapters), you should be aware of how the perception of anonymity can affect you and others. It can make people engage in activities that they wouldn’t normally do. While you would never shoplift a DVD from a store, you might feel free to download a movie without paying for it. Since it’s online, you might view illegal downloads as a game or not entirely real because no physical items have been taken. Though others can’t physically see or hear you, the rules of conducting yourself are often the same as real life. It may be tempting to bend your morals and beliefs, but it’s important to maintain what you believe in, and remember that what you do online can affect someone else behind another computer.
The Falsehood of Anonymity
Many people go online thinking their identity is already anonymous. They haven’t logged onto an account or the site allows them to use an alias, and they believe no one can see who they are. In most cases, they couldn’t be further from the truth. There are many ways that sites can capture where you go and what you do, including:
![]() When you visit a site, the Web server can retrieve your IP address, the site that you came from, the type and version of browser you’re using, and a considerable amount of other information. Using the IP address alone, someone could identify who is logging in.
When you visit a site, the Web server can retrieve your IP address, the site that you came from, the type and version of browser you’re using, and a considerable amount of other information. Using the IP address alone, someone could identify who is logging in.
![]() Your ISP can analyze your activities, which may be used to see if you’re downloading copyright materials with BitTorrent technology.
Your ISP can analyze your activities, which may be used to see if you’re downloading copyright materials with BitTorrent technology.
![]() Social media sites can also track you through the social network plugins on sites, where you can click “Like” or retweet.
Social media sites can also track you through the social network plugins on sites, where you can click “Like” or retweet.
This isn’t to say that there aren’t ways to maintain a level of anonymity online. There are ways to conceal your identity to a higher degree than normal so others can’t see what you’re doing online.
The Flip Side of Anonymity
Just as many people bask in the belief that they’re hidden online, there are many others who seek attention online. Social media has provided the ability to quantify the attention we receive from others, and get a perception (real or false) of our popularity. Some of the ways that this is done include:
![]() How many “friends,” subscribers, fans, and followers we have on Facebook, YouTube, and other sites.
How many “friends,” subscribers, fans, and followers we have on Facebook, YouTube, and other sites.
![]() The number of “likes” and comments posted in response to something we’ve said, and how many times it’s been shared or retweeted to others.
The number of “likes” and comments posted in response to something we’ve said, and how many times it’s been shared or retweeted to others.
![]() The number who have viewed your photo or video on Flickr or YouTube, or viewed your page on sites like Facebook and LinkedIn.
The number who have viewed your photo or video on Flickr or YouTube, or viewed your page on sites like Facebook and LinkedIn.
The ability to measure the attention we receive and influence we might have over others is both a positive and negative feature. If you post a comment, the number of likes you receive can give you an idea of what’s appealing to your audience. More importantly, let’s face it, this makes you feel good. You may also have social media accounts for your professional activities, where you write articles or make videos to share your expertise, share content others have created, or promote your business somehow. By seeing that a particular post is liked by a high number of people, you now have a good indication of what other content you should create and share in the future.
While seeing how people respond to your posts and the interaction of showing you like a post are beneficial, there are downsides to how social media quantifies your life:
![]() Quality of posts may suffer. Rather than providing accurate information or showing your genuine feelings, you’ll see many people pandering to popular opinion, or posting items to solely generate likes and shares.
Quality of posts may suffer. Rather than providing accurate information or showing your genuine feelings, you’ll see many people pandering to popular opinion, or posting items to solely generate likes and shares.
![]() Keeping score of your life. Some, especially children and teens, may gauge their popularity by how many people subscribe to their YouTube channel, become Twitter and Instagram followers, and so on. The scores become a measure of self-worth and can be seen as a warped reflection of how they’re doing in life.
Keeping score of your life. Some, especially children and teens, may gauge their popularity by how many people subscribe to their YouTube channel, become Twitter and Instagram followers, and so on. The scores become a measure of self-worth and can be seen as a warped reflection of how they’re doing in life.
![]() Lowering security settings to increase the audience. If a person is obsessed with increasing the numbers of likes and followers, they may lower their security and privacy settings to increase the number of people who can see their posts. Rather than creating a new public account, they may make the mistake of allowing personal information to become visible by allowing everyone to see it.
Lowering security settings to increase the audience. If a person is obsessed with increasing the numbers of likes and followers, they may lower their security and privacy settings to increase the number of people who can see their posts. Rather than creating a new public account, they may make the mistake of allowing personal information to become visible by allowing everyone to see it.
![]() Adding people you don’t actually know exposes you to new threats. Someone may be proud that they have hundreds of Facebook friends, but they don’t actually know all of them. The number of friends and followers becomes a status symbol to some people, but adding all those people may have let in troublemakers, bullies, pedophiles, identity thieves, and other threats. You may have secured your settings so that personal information and private photos aren’t viewed publically, but if you accept any stranger’s friend request, you’re giving everyone access anyway.
Adding people you don’t actually know exposes you to new threats. Someone may be proud that they have hundreds of Facebook friends, but they don’t actually know all of them. The number of friends and followers becomes a status symbol to some people, but adding all those people may have let in troublemakers, bullies, pedophiles, identity thieves, and other threats. You may have secured your settings so that personal information and private photos aren’t viewed publically, but if you accept any stranger’s friend request, you’re giving everyone access anyway.
Annoying and Abusive People
Dealing with the people you’ll meet online can be a varied experience. You’ll meet nice people in other areas of your country or the world, who have interests and outlooks similar to yours. You’ll keep in touch with family and connect with friends you haven’t seen in years, allowing you to maintain relationships that might have drifted or been lost. Unfortunately, there are also a lot of jerks on the Web. These are people who irritate, annoy, and anger you by the things they post and the comments they’ll make. Even worse, there are those who are insulting, abusive, and even frightening.
As we’ll see in the sections that follow, certain types of negative behavior are more prevalent among certain groups, so what you’ll experience online may depend on your age, gender, and the types of sites you visit. While no one is immune to being the target of abuse, you should be aware of where and when you’re more susceptible to it. By knowing this, you’ll be more prepared when it happens, and better able to make an unemotional decision on how to handle it.
Online Harassment
Anyone can be the target of unwelcome behavior. Someone may inadvertently insult you, expose a secret you’d rather have kept private, or show unrequited affection. If it’s an accident or wasn’t meant to be malicious, you’ll probably just blow it off. You might confront the problem, by letting them know they hurt your feelings, or that the comments were unwelcome. If someone challenges you, makes a rude observation, or says something you oppose, you might even be a little defiant and contest what they have to say. Where it becomes a serious problem is when the undesirable statements are repetitive, excessive, or extremely offensive.
According to a 2014 study by the Pew Research Center (Duggan, 2014), 22% of those surveyed experienced less severe forms of online harassment, inclusive to name calling and being publicly embarrassed. Of these, men are more likely to be the targets. In addition, 18% experienced more severe forms, inclusive to ongoing harassment over an extended period of time, sexual harassment, physical threats, and stalking. The study found that:
![]() 32% of men and 22% of women have been called offensive names
32% of men and 22% of women have been called offensive names
![]() 24% of men and 20% of women have been embarrassed online on purpose
24% of men and 20% of women have been embarrassed online on purpose
![]() 10% of men and 6% of women have been physically threatened
10% of men and 6% of women have been physically threatened
![]() 8% of men and 7% of women have been harassed for a sustained period of time
8% of men and 7% of women have been harassed for a sustained period of time
About half of the people who were harassed didn’t know who was responsible, because the aggressor was either a stranger or the real identity of the person(s) responsible wasn’t known. This can happen if the person created a fake account, used an alias, or took other steps to hide their identity. Perhaps more frightening is that the other half were known to the victims. This means that the harasser had some kind of relationship with and/or felt so comfortable with bullying the person that they didn’t even try and hide who they were.
Being the target of some kind of abuse can happen anywhere on the Internet, but the most common places may surprise you. Of those targeted by harassment, they reported the most recent incident occurred on the following types of sites:
If you’ve ever been the victim of online abuse, you can see from this that you’re far from alone. The perpetrators and targets of online harassment can involve any age, gender, social, or ethnic background, regardless of where they live or work. While younger Internet users have a greater chance of being targeted, this doesn’t mean that older users should believe they’ll never see or experience this kind of behavior.
Trolls and Flamers
As we’ve seen, the threat of harassment can come in a variety of forms, and there are different types of annoying, abusive, and menacing people you’ll come across online. A Troll is someone who posts or responds with comments in the hopes of getting some kind of reaction. In doing so, they may make derogatory comments, or say something that will upset people. This may be some racist, sexist, or offensive remark that will draw others into responding.
The meaning of the term is similar to that of a flamer, which is someone who posts inflammatory comments in the hopes of inciting an argument. By posting something outlandish or offensive, called flamebait, the hope is that someone will then respond, possibly resulting in drawing in other users and resulting in a flame war where multiple people are exchanging arguments, offensive comments, and insults.
If it sounds like some kind of psychotic game, you wouldn’t be far from wrong. Trolls and flamers generally fight with people as a form of entertainment, and enjoy the emotional responses they receive as a result of their posts. In a 2014 study on the behavior entitled “Trolls Just Want to Have Fun,” it was suggested that people who enjoy and engage in this type of behavior have traits that show signs of “narcissism, Machiavellianism, psychopathy, and sadistic personality” (Buckels et al., 2014). In other words, they enjoy hurting people with their comments, so they do so as a way of having fun.
The way to deal with trolls and flamers is to look at what they want, and not give it to them. They are posting these comments in the hopes of getting a reaction, so don’t give them one. If you don’t respond, you haven’t added fuel to their fire, and you’ve extinguished any flame war before it’s begun. If you ignore them, you’ve won and they’ve eventually go away and bother someone else.
Creeping
Creeping is the act of someone viewing another person’s profile or page, and following their activity without their knowing. This isn’t the same as seeing someone’s posts appear on your wall, keeping up-to-date with a friend or family member’s pastimes, or checking out someone you’ve just met to see if they’re okay or a threat. When someone creeps a page, it’s to watch what you’re doing, without your knowledge, possibly for disturbing reasons.
A person will creep another person’s page to monitor them. A jealous boyfriend, girlfriend, or spouse may watch their significant other’s page to ensure they’re behaving in a way that’s expected. It’s also common practice after a breakup. A 2012 study (Lukacs, 2012) found that 88.2% of people spent time looking at, analyzing, or creeping their ex’s profile. If you think the easy solution to this would be to simply unfriend or block your ex, you’d be wrong. The study also found that those who’d been unfriended used another person’s account (such as logging in with a mutual friend’s account) to view their ex’s activity.
While some sites like LinkedIn allow you to see who’s viewed your profile, most do not. In many cases you won’t be aware if someone’s creeping your page unless you hear about it. If you hear the person is using another friend’s account, you could unfriend or block their account, as we’ll see later. If it’s your understanding that they’re using a school or work computer to creep your profile, you could complain to them. Using the computer in this way could be a violation of the school or employer’s acceptable use policies, which could result in disciplinary action.
Cyberstalking
Cyberstalking is the act of persistent and unwanted contact from someone online. It may involve any number of incidents including threats, libel, defamation, sexual harassment, or other actions in which to control, influence, or intimidate their target. Stalking a person online may also involve stalking the person in real life. In many states and countries it is illegal, and could result in criminal charges as a named offence or under harassment and stalking laws.
There have been a number of prominent cases involving cyberstalking, including the incident involving actress Patricia Arquette. In 2011, she deactivated her Facebook account on the advice of her security people due to problems with an online stalker. She decided to only communicate with fans through Twitter and advised fans in her last post to only accept friend requests from people they know.
Cyberstalking doesn’t only affect the rich and famous. According to a 2014 study by the Pew Research Center (Duggan, 2014), 18% of those surveyed said that they had seen someone stalked, while 8% reported that they had been stalked. It also found that women are more likely to experience online sexual harassment or cyberstalking then men. Of these, women aged 18–24 experienced a disproportionately high number of incidents, with 26% having been cyberstalked, and 25% being the target of sexual harassment. This isn’t to say that men aren’t targeted by this type of behavior. The survey found that 7% of men aged 18–24 reported being stalked online, and 13% experienced sexual harassment.
Because cyberstalking could ultimately result in violence, if you’re a target it’s important that you take action as soon as possible. Contact the police and report the crime(s) that have been committed. Gather as much evidence as you can about the incidents. This would include printouts or screenshots of posts and messages, documenting dates and times of incidents, and any other information you might have. You should also evaluate your privacy and security settings, and change the passwords for any email and social media accounts, in case the person has gained access to them. As we’ll see in this and other chapters, many sites also have features to report harassment and other problems, possibly resulting in the person’s account being disabled or removed.
Protecting Yourself
When you’re faced with a problematic user, it can seem hopeless when you’re staring at their annoying or abusive posts. As mentioned, if you feel threatened, then calling the police is an important step. If it hasn’t come to that and you want to avoid potential problems, there are steps you can take. In addition to the preventative measures we’ve already discussed, you can limit your exposure to the person, seek support, and report problems.
Thinning the Herd
Every so often, it’s a wise idea to go through the friends and followers you have and remove ones that have no redeeming value to your online experience. Perhaps they were added so you could have more neighbors in a game you no longer play, they used to date a friend but that relationship is over, you have a nasty relative who posts disagreeable things, or a friend you no longer want a relationship with. Ever few months at least, you should go through the friends you and your children have on Facebook and other sites, and remove ones that are no longer relevant or shouldn’t be there.
For those you want to keep but limit access, you should utilize lists. As we saw in Chapter 6, Protecting yourself on social media, you can add people to the Restricted list in Facebook so that they can only see your public posts and the posts they’re tagged in. People in such lists might be your boss, a family friend who isn’t really a personal friend, and others you want to remain friendly with but limit what they can see. It may also include people you’re having some problems with, so you can still see their page, but they can’t see any of your private posts.
Unfriend, unfollow, unjoin
Limiting exposure to people who are annoying or abusive also involves removing them from your real life, and your online world. A good cull of the groups you belong to but no longer find relevant, and former friends who shouldn’t have access to your life involves unfriending, unfollowing, and unjoining.
Unfriending a person on Facebook removes their access, so they’ll only be able to view publically accessible content. The person isn’t notified, so they’ll only notice if they review their list of friends, or visit your page and notice the option is there to add you as a friend. To unfriend someone, go to your profile page, and click the Friends link on the navigation bar below your cover photo. When the list of friends appears, do the following:
Just as you may have grown tired of a friend, you may no longer wish to be part of a group. To unjoin a group, you would visit their page, hover your mouse over the button on the cover photo that says Joined, and then click Leave Group on the dropdown that appears.
In some cases, you may not have added the person as a friend, but are simply following them. In doing so, you can see their posts on your newsfeed. In other cases, you may want to keep them as a friend or stay in a group, but don’t want to see their posts anymore. To remove their posts from your feed, simply visit their page, hover your mouse over the button that says Following on their cover photo, and then click Unfollow.
Twitter also allows you to stop following someone. To stop seeing tweets from a particular person or group, visit their page, click on the Following button below their header photo. The button should now say Follow, indicating you are no longer following them.
Blocking people
Blocking a person prevents them from contacting you and removes their ability to see your profile and content. The ability to block someone is a common feature in many apps and social networking sites, allowing you to use their services without having to deal with unwanted users. The method of blocking someone varies from app-to-app and site-to-site. In the paragraphs that follow, we’ll show you methods available on some of the most popular apps and sites.
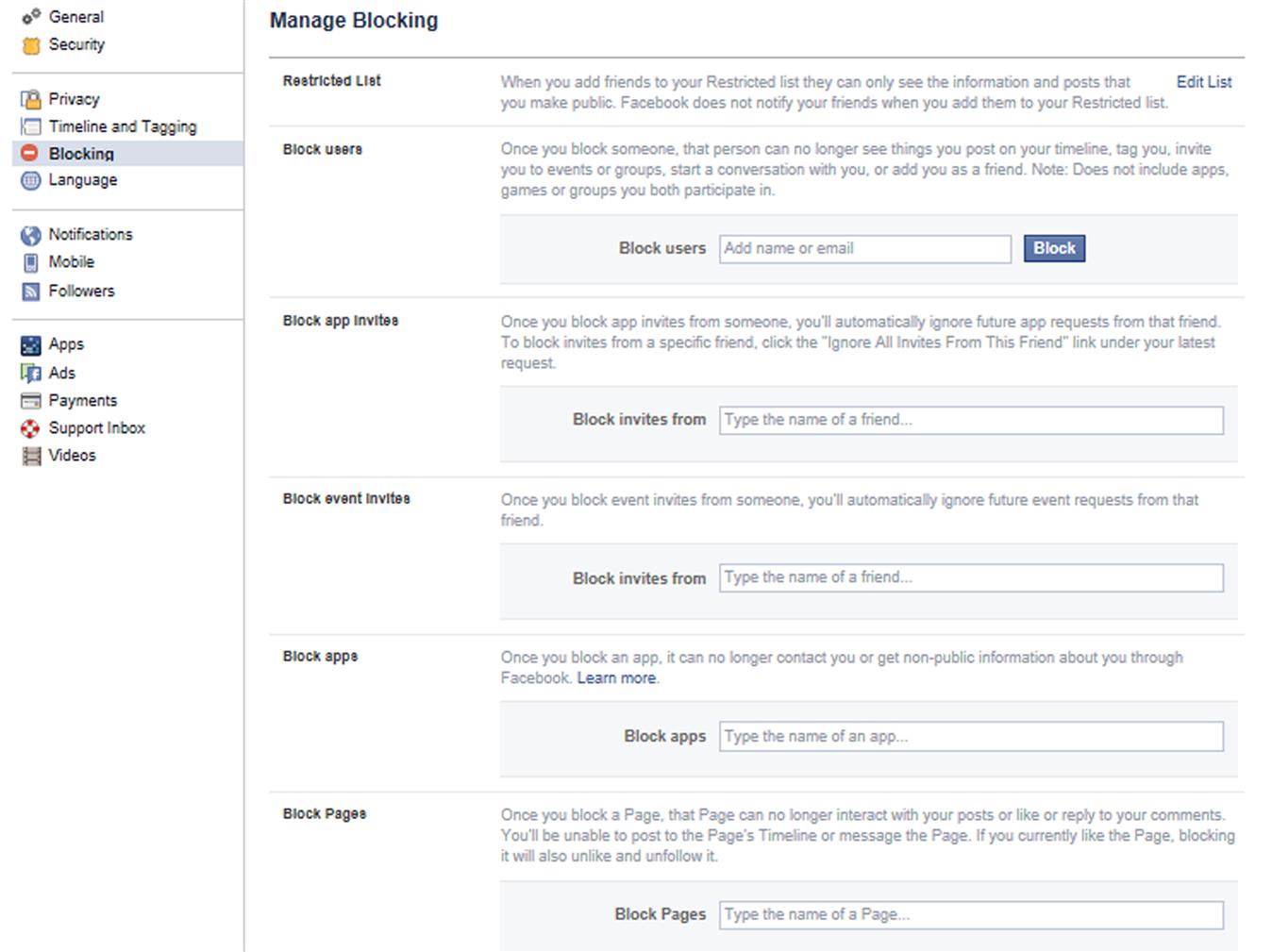
Blocking in Facebook is done by clicking the downward arrow in the top right-hand corner of the top navigation bar, and then clicking Settings. Click on Blocking in the left-pane of the screen that appears, and you’ll see a screen as shown in Fig. 9.1.
As seen in Fig. 9.1, Facebook allows you to block users, invitations, apps, and pages. The settings on this page include:
![]() Restricted list, where you can add and edit the people on your Restricted list, which we discussed in Chapter 6, Protecting yourself on social media.
Restricted list, where you can add and edit the people on your Restricted list, which we discussed in Chapter 6, Protecting yourself on social media.
![]() Block users, where you can add names of people you want to block, so they no longer see your posts, can tag you, invite you to events or groups, send messages/start conversations, or add you as a friend. The exclusions to anyone added is that they can still interact with you in any apps, games, or groups you’re in.
Block users, where you can add names of people you want to block, so they no longer see your posts, can tag you, invite you to events or groups, send messages/start conversations, or add you as a friend. The exclusions to anyone added is that they can still interact with you in any apps, games, or groups you’re in.
![]() Block app invites, which will ignore any invitations to join games or other apps sent by the person.
Block app invites, which will ignore any invitations to join games or other apps sent by the person.
![]() Block event invites, which will ignore any event invites from the person.
Block event invites, which will ignore any event invites from the person.
![]() Block apps, which prevents any apps from contacting you or getting nonpublic information about you.
Block apps, which prevents any apps from contacting you or getting nonpublic information about you.
![]() Block pages, which blocks any pages from liking your posts, or replying to comments, and prevents you from posting on the page or messaging it. If you’ve liked the page, this will automatically unlike and unfollow the page.
Block pages, which blocks any pages from liking your posts, or replying to comments, and prevents you from posting on the page or messaging it. If you’ve liked the page, this will automatically unlike and unfollow the page.
Twitter also allows you to block someone. In doing so, they can’t follow you, send Direct Messages to you, add your account to their lists, tag you in photos, view your tweets, who’s following you, who you’re following, or your content (photos, videos, lists, or favorites). When you block the person, they won’t receive any notification of it. To block someone on Twitter, you’d do the following:
On Instagram you can block someone so they can’t see your profile or posts. You’d do this through the app, by tapping on their username to open their profile. Once you’re on their profile, tap the icon with the depiction of three dots, and then tap Block User.
Snapchat also provides ways to block users. To block a user who’s added you, so they can’t view your stories, or send your snaps and chats, you would start by going to your profile screen. On this screen, Added Me, find their name and tap the gear-shaped icon next to their name, and then tap Block. To remove them from your list of friends, tap Delete. If you wanted to remove a person from your friends, you can tap My Friends on your profile, tap their name, tap the gear-shaped icon below their name, and then tap Block. There are times when you’ll be in chat with someone and want to block them from there. To do this, you would swipe left of the user’s name, tap the icon with three bars, and then tap Block.
While the steps involved in blocking a person vary between apps and sites, you will see similarities in the process of how to block them. To get detailed instructions on a app or site we didn’t cover, you should check the help section for the site and search for how to block someone.
Does losing anonymity help?
You might think that a possible solution for getting rid of trolls and stalkers is to remove their ability to remain anonymous on sites. However, as we saw earlier, about half of the people experiencing online harassment were able to identify the person. This is consistent with what can be seen on sites that removed anonymity. While you used to be able to post anonymous comments about a video on YouTube, in late 2013 Google forced people commenting on videos to associate comments with their Google+accounts. If you visit YouTube, you’ll still see plenty of nasty remarks being posted, showing that trolls have no problem with others knowing who they are.
If you’re a blogger or have some other site you own and control, you may have the ability to ban commenters from responding to the content you post. On YouTube, when someone posts a comment, you’ll get a notification that has an arrow in the upper right of the comment. Upon clicking this, you can choose to remove the comment, report it as spam or abuse, or hide it. If you choose to hide it from the channel, the user is added to the hidden users list on your channel, and he or she is blocked from posting comments on videos.
Bloggers and YouTubers also have the ability to manage comments that have been added, preventing them from being seen until they’re approved. While it won’t protect you from seeing any negative or derogatory comments people may post, it will save you possible embarrassment from others seeing them. By checking the settings available to you, you can limit the exposure of such comments, and report them as they come in.
Reporting abuse
As you’ve seen, there are mechanisms on sites and apps for dealing with annoying and abusive people, allowing you to minimize the exposure of their comments, make it so you no longer see them, or block them so that they can’t bother you anymore. There are times when you’ll want to take an extra step and report what they’ve posted. You can take steps to delete and remove links and content, and also report those posts to the site.
If someone has created a page, group, or profile that’s designed to embarrass or harass you, you can report it on Facebook by going to their profile, clicking  , and then clicking Report. You would then follow the instructions to report the problem.
, and then clicking Report. You would then follow the instructions to report the problem.
You can also report issues to Facebook through the following steps:
1. In your browser, go to www.facebook.com/help/contact/274459462613911.
2. Click the link that is most closely related to your problem. Options include Someone is threatening to share things that I want to keep private and Other abuse and harassment.
On Twitter, you can report abuse by visiting the person’s profile, clicking the gear-shaped icon, and then clicking Report. You can then select that They’re being abusive or harmful, and report the issue you’re having.
If the problem is on another site, don’t worry. Other sites commonly have links or contact email in which you can notify the site about a problem. In many cases, this is the domain name preceded by abuse@ (e.g., [email protected]), but you should check the site to ensure this is the correct way of notifying them about an abusive user.
If you have the person’s email address, you may be able to see the ISP they’re using for Internet access. In such a case, you could notify their Internet provider of the harassment, in the possibility they will remove him or her as a subscriber. Without Internet, they won’t be able to harass you online.
If you’re experiencing any threatening comments, or are fearful for your safety, you should always contact the police so that the matter can be fully investigated and/or you can get help obtaining a restraining order. Don’t dismiss abusive behavior, hoping that it won’t escalate.
Online Chat
Online chat refers to any type of communication in which messages are sent in real time between two or more people. While discussion boards and email are used to post or send a message that may be responded to later, the various programs and protocols used for chatting allow people to send and receive messages instantly. Communication between those involved in a chat may be text-based or use streaming technology to allow people to actually talk (using their voice) and see one another via live video.
While chatting online can introduce you to people you never would have met, and may even provide a spirit on online community where the same people chat together regularly, it is not without its potential threats. Some of the things to remember include:
![]() You’re talking with strangers, so be aware of what you say. Don’t provide any personal information, inclusive to your name, address, credit card information, names of family members, where you work, and so on.
You’re talking with strangers, so be aware of what you say. Don’t provide any personal information, inclusive to your name, address, credit card information, names of family members, where you work, and so on.
![]() Be careful of links. It’s common for someone chatting to send a link, but this may download a potential virus or a site with malware.
Be careful of links. It’s common for someone chatting to send a link, but this may download a potential virus or a site with malware.
![]() Disable automatic downloads, if that is a feature of the program being used.
Disable automatic downloads, if that is a feature of the program being used.
![]() Leave your profile blank or enter false information.
Leave your profile blank or enter false information.
![]() If you have problems, report them to the moderator or site. You can also log out, change your username, and log back in. Block or ignore (iggy) anyone who gives you a problem so that they can’t contact you or see what you’ve typed.
If you have problems, report them to the moderator or site. You can also log out, change your username, and log back in. Block or ignore (iggy) anyone who gives you a problem so that they can’t contact you or see what you’ve typed.
Picking an Alias
When you chat online, you’ll often use an alias. The alias is a username that others will see when viewing a list of people visiting a room, or when communicating with you privately. This helps to shield your real identity, so that people can’t directly see who they’re talking to. When choosing an alias, don’t use any names that reveal who you are, where you work, your marital status, if you have children, or other personally identifying features. There are a number of sites that can help you create usernames for chat rooms and other purposes, including:
![]() SpinXO (www.spinxo.com)
SpinXO (www.spinxo.com)
![]() Cool Name Generator (http://cool.namegeneratorfun.com/)
Cool Name Generator (http://cool.namegeneratorfun.com/)
![]() Name Generator (www.namegenerator.biz/screen-name-generator.php)
Name Generator (www.namegenerator.biz/screen-name-generator.php)
Instant Messaging
Instant Messaging (IM) is used to send messages in real time. Traditionally, this has been limited to text-based messages, although some sites and apps also have the ability to communicate with voice or video. When using IM, you would keep the messages relatively short to keep communication flowing at a reasonable pace. To use IM, you would have to install client software that used a specific protocol to chat with others using similar software. Some of the clients available include AOL Instant Messenger or AIM for short (www.aim.org), Pidgin (www.pidgin.im), and eBuddy (www.ebuddy.com/). These traditional IM clients have been overshadowed in recent years by the proprietary IM software included with phones and other mobile devices, such as Blackberry Messenger and Apple’s iMessage.
Another popular method of using IM is with the integrated features in social media sites. Rather than install additional software or apps, you could IM using the chat features on sites like Facebook. In 2011, Facebook partnered with Skype (www.skype.com) to provide a video call feature. Rather than simply type your message, you could now choose to engage in video chat as well. To turn off this feature, you would do the following:
Chat Rooms
Chat rooms are areas in which people can gather to engage in real-time conversations, generally using text-based communication. There are a number of sites on the Internet where you can find chat rooms focusing on various topics, interests, ways of life, or providing forums for general discussion, although other sites may only provide a single chat area. You may see forums for moms to chat, issues with sexuality, and so on, although these often go into more general discussion that don’t reflect the room’s name. In the main chat room there will be groups of people who are all chatting with one another, although two or more people can open a private chat room to communicate privately. Some of the chat sites on the Internet include:
![]() Delphi Forums (www.delphiforums.com), which provides multiple rooms. After setting up an account and profile, you’ll be able to join the room(s) you wish and engage others in conversation. Some rooms require a 48-hour wait before you can enter, which prevents those who have been banned from a room just creating a new account and going back in.
Delphi Forums (www.delphiforums.com), which provides multiple rooms. After setting up an account and profile, you’ll be able to join the room(s) you wish and engage others in conversation. Some rooms require a 48-hour wait before you can enter, which prevents those who have been banned from a room just creating a new account and going back in.
![]() Chat Rooms Online (www.chat-rooms-online.com), which provides multiple rooms, but doesn’t require creation of a profile if you go on as a guest.
Chat Rooms Online (www.chat-rooms-online.com), which provides multiple rooms, but doesn’t require creation of a profile if you go on as a guest.
Chat rooms generally have moderators, who are responsible for ensuring the rules of the room are followed. A variation of netiquette is used in chat rooms called chatiquette, which govern the acceptable behavior in most rooms. While some rules like not typing in caps are the same as those used in netiquette, there are others that are unique. For example, prior to going into private chat with someone, it’s commonly expected that you should ask first in the main room. You may see someone ask you “can I PM you?” meaning they want to private message or go into a private room with you. Those who are bothering people in the room and ignoring the rules are often “kicked” from the room, and moderators may ban them so they can’t reenter.
Different rooms may have different rules, so you should hesitate before jumping into conversation. Some rooms may strictly forbid offensive remarks and rude behavior, while others may have a more laissez faire attitude and let anything happen. Lurking is the act of not participating in the main chat room’s discussion, but simply reading what’s being said. By taking this step, you can see if the room meets your approval, and if the group that’s on there seem like the kind of people you want to interact with.
While the people who go into chat rooms are predominantly nice, they also attract trolls and people who want to engage in cybersex, which we’ll discuss later. It’s important to remember that you don’t really know who you’re talking to, and that everyone’s a stranger. It can be difficult to retain this mindset as you get comfortable. However, if you have a problem, feel free to use the button to ignore a pest and block any communication from them.
Web Cams
Web cams are cameras that are built-in or connected to your computer, allowing you to take digital photos or video of yourself. They may be used for video conferencing, taking pictures that can be used to update a profile, or used to create videos and pictures that can be shared with others.
Using a Web cam, you can put a face to the words as you’re chatting, or conduct real-time conversations “face-to-face.” This can be done using programs like Skype, which allows you to make voice or video calls. As we mentioned, sites like Facebook also provide the ability to engage in video discussions. If you have a camera installed, when you click on the name of the person you want to chat with, you would then click on the camera-shaped icon at the top of the discussion. A new window would appear allowing you to chat.
In general, you should never agree to engage in any kind of intimate act, remove clothes, or do anything on camera that might be considered embarrassing or incriminating if revealed to someone else. You should always go on camera with the thought that others may see it. If anyone does threaten to blackmail you, don’t agree to their demands and contact the police immediately.
Even if you don’t do webcamming, the webcam may still be used to watch or record videos of you. RATting refers to a Remote Access Trojan (RAT) being installed on a computer for the purpose of acquiring remote access of that machine. Once a RAT is installed, a hacker gains administrative access to the machine, and may gain control of your webcam. They can turn it on, watch you without your realizing it, and either live-stream or record what’s happening for others to watch. To avoid having your system exploited and used in this way, you should have antivirus and antimalware software installed with the latest updates, and use a firewall. This will block and remove any known remote administration tools that may have been installed. If you have an external camera that plugs into your computer, look to see if the light is on showing it’s been activated. You could also consider removing it when it’s not being used. Obviously, if it’s not attached, no one can use it without your knowledge.
Online Gaming
The ability to communicate with others has been integrated into a wide variety of programs, including online games. If you go on Facebook, you may have blocked the chat feature, but people may still send messages to you in the various games you’ve signed up to play. The app may have a feature visit the playing environments of your neighbors or allies and send messages. Generally, this comes part-and-parcel with the game, and the only way to stop others from communicating with you is to uninstall the app.
Most games that are online and multiplayer allow voice communication with other players. This not only includes computer games, but also those designed for game systems like Sony PlayStation, Nintendo Wii, and Microsoft Xbox. While you’re playing with others, you can talk to them and/or send text messages through the game system. While this has benefits in the game, it also exposes you to stalkers, trolls, and other potential threats that come from dealing with people online.
There are also virtual environments where you can chat. Massively multiplayer online role-playing games like World of Warcraft and virtual worlds like Second life (www.secondlife.com) allow you to create a humanoid representation of yourself called an avatar. Using the avatar, you can interact with other players, and talk online with them using voice or text-based methods.
Romance scams
While you might have to kiss a few frogs to find a prince, sometimes you just get warts. As you might expect, online romance has attracted criminals who use promises of affection and companionship for personal gain. A cybercriminal will review your profile to see what kinds of music books, and movies you like, review your posts and tweets, and determine your likes and dislikes. Using this, the scammer will pretend to have shared interests, make flattering comments, entice you with promises, post attractive photos that are supposedly them, and gain your trust. Once this is done, they’ll ask favors, asking you to pick up or resend packages on their behalf, or request money to deal with a family tragedy or some other hardship. The cybercriminal may use chat rooms, dating sites, social media, or other sites to meet a victim.
According to the 2014 Internet Crime Report (Internet Crime Complaint Center, 2014), this scam generated 5883 complaints to the Internet Crime Complaint Center and resulted in victims collectively losing $86,713,003. While people from every demographic and both genders have fallen for this scam, women who are over the age of 40 predominantly fall victim.
Online Dating
Online dating is the process of trying to form a relationship for romantic or sexual reasons. While you can meet people through social networks, chat rooms, or any other online venue, finding a relationship through online dating typically involves a site or app specifically designed for this purpose. In using a dating service or app, you may be provided with matchmaking where your interests and motivations are aligned with others who have similar interests. Others may simply provide the ability to peruse a database of people, or search on the basis of age, sex, location, and other factors.
Even though you may be taking steps to find Mr. or Ms. Right, not everyone uses these services for the same reason. Some of the steps you should take to protect yourself include:
![]() Try to be as anonymous as possible. Never give away information that identifies you, such as your surname, where you work, or other details in your profile or when initially making contact.
Try to be as anonymous as possible. Never give away information that identifies you, such as your surname, where you work, or other details in your profile or when initially making contact.
![]() Keep any contact information private, inclusive to your email, phone number, and address. The services you use may include temporary phone numbers for texting, internal messaging, or other features that allow you to communicate so they won’t have access to you directly.
Keep any contact information private, inclusive to your email, phone number, and address. The services you use may include temporary phone numbers for texting, internal messaging, or other features that allow you to communicate so they won’t have access to you directly.
![]() Take things slowly. You may be excited at the prospect of a relationship, but you shouldn’t be quick to reveal personally identifying information or sensitive details too fast. Remember the person is still a stranger, even though you may have exchanged messages or talked to one another.
Take things slowly. You may be excited at the prospect of a relationship, but you shouldn’t be quick to reveal personally identifying information or sensitive details too fast. Remember the person is still a stranger, even though you may have exchanged messages or talked to one another.
Traditional versus Extramarital
Commonly, people use traditional dating sites in the hopes of finding someone to have a long-term relationship or sexual partner. While many of the people on these sites are single, there are also those who are married. A famous site that caters to extramarital affairs is Ashley Madison (www.ashleymadison.com), where single or married people can connect with other women or men. Couples also use the site to meet others to join them in discreet sexual encounters. If you think few people would consider using this service, you’d be wrong. It’s a membership site that boasts over 42 million members across 53 countries. Of course, even if you aren’t using a site that has the clear intention of being an extramarital dating service, it doesn’t mean that the person you’re meeting isn’t already in a relationship.
Being in a relationship and using sites to find another partner opens you to the risk of being identified by someone you know. Other information included in your profile could also cause serious embarrassment. When Ashley Madison was hacked in 2015, there were details of people’s sexual fantasies and interests included in the profile data. Once the hackers made this available for download on another site, members were identified, and according to the Toronto Police Department it led to two people committing suicide and others being victims of extortion.
Online dating provides a unique situation of balancing privacy with openness. When you are looking for a relationship online, the site may use a matchmaker algorithm to match you with someone, or people may browse profiles to find someone they like. To attract someone who’s compatible requires you to provide honest information, which also makes it a useful source of intelligence for cybercriminals. As we discussed in Chapter 5, Cybercrime, someone may use this as the basis to obtain personally identifying information that can be used for identity theft and other crimes. It may also be used for webcam blackmail, extortion, and romance scams. It’s important that you limit what you reveal, and think of how a piece of information may be used. If it personally identifies you or could be embarrassing, keep it private. You can always leave some mystery and reveal some details when you are confident you can trust the other person.
Sites
There are a number of dating sites on the Internet to meet with someone in the hopes of achieving a romantic or sexual relationship. These services may be free, cost a subscription fee, or provide some free access but provide other features at a cost. They also typically require you to create a profile and may require you to fill out an online questionnaire to obtain additional information so they might better find a compatible match for you. Most allow you to upload photos and videos to allow others to see what you look like. The features of dating services vary, with some providing the ability to engage in text-based chat, Voice Over IP voice chats, and webcam chats. Some of the popular sites include:
![]() eHarmony (www.eharmony.com)
eHarmony (www.eharmony.com)
![]() Match.com (www.match.com)
Match.com (www.match.com)
![]() Zoosk (www.zoosk.com)
Zoosk (www.zoosk.com)
![]() PlentyOfFish (www.pof.com)
PlentyOfFish (www.pof.com)
If you think a traditional dating site is safer and more secure than nontraditional ones like Ashley Madison, you’d be wrong. In 2011, both eHarmony and PlentyOfFish were hacked. In the same year, a woman claimed she was raped after meeting someone on Match.com and sued the site, wanting them to do background checks to prevent registered sex offenders from signing up. After the suit was filed, Match.com announced it would screen new members. Regardless of the site you use, you need to be careful, safeguarding both your information and yourself.
Apps
Sites aren’t the only method of meeting someone online. Apps like Tinder (www.gotinder.com) can be installed on iOS and Android devices. When you use Tinder, you swipe left on your device to review different people looking to meet, and swipe right to like them. If you and the other person both like each other, you can then message one another and see where things go from there. Who views your Tinder profile is anonymous, so you never know who views your picture and profile. Other popular dating apps include:
![]() Hinge (www.hinge.co)
Hinge (www.hinge.co)
![]() Coffee Meets Bagel (coffeemeetsbagel.com)
Coffee Meets Bagel (coffeemeetsbagel.com)
A common feature in dating apps is that they’ll connect to another account, such as Facebook, as a form of verification. Of course, you could easily create a fake account. Some will also do this to gather additional information from your Facebook profile to provide additional details about your interests, people you both know, things you have in common, and so on. There are also apps that are put out by dating sites, extending the services to mobile devices.
Meeting People in Person
It can be exciting to take that first step of meeting someone in person, whom you’ve only known as an online entity before now. Making physical contact with a stranger, regardless of how long you’ve communicated online, is a major step that can have major consequences. When meeting someone in person, remember that your physical safety is your primary goal:
![]() There’s safety in numbers. Meet in a public place, where there are lots of people around.
There’s safety in numbers. Meet in a public place, where there are lots of people around.
![]() Don’t meet anyone in secret. Let your friends and family know who you’re meeting, where, and when you’ll be home. You should make arrangements to contact a friend or family member, so they’ll know you’re okay and got home safe.
Don’t meet anyone in secret. Let your friends and family know who you’re meeting, where, and when you’ll be home. You should make arrangements to contact a friend or family member, so they’ll know you’re okay and got home safe.
![]() Don’t rely on the person you’re meeting. Use your own transportation to meet them, or have a friend drop you off and pick you up at a specific time.
Don’t rely on the person you’re meeting. Use your own transportation to meet them, or have a friend drop you off and pick you up at a specific time.
![]() Bring your mobile phone, so you have a way to contact a friend or 911 if a problem arises.
Bring your mobile phone, so you have a way to contact a friend or 911 if a problem arises.
While it may seem like a good idea to meet for drinks, alcohol can impair your judgment. Also, if the person has brought you an open drink, there’s the possibility he or she may have slipped a drug in it. There are a number of drugs that can be used to inebriate or knock out a person, including those that are odorless and tasteless. You want to walk away from an enjoyable date, and not be the victim of a date rape.
Protecting Yourself
There are a number of steps you can take to protect yourself when using sites where you’ll interact with new people. Some of these include:
![]() Limiting information. As we’ve said before, be careful about what you add to your profile and reveal in conversation with others. As we saw in Chapter 5, Cybercrime, the details about yourself can slowly come over time, eventually revealing more than you meant to say. You should try and be aware of what you’re saying, and think before you type.
Limiting information. As we’ve said before, be careful about what you add to your profile and reveal in conversation with others. As we saw in Chapter 5, Cybercrime, the details about yourself can slowly come over time, eventually revealing more than you meant to say. You should try and be aware of what you’re saying, and think before you type.
![]() Keep your contact details private. Don’t reveal your phone number, address, where you work, or other information that would enable a person to find you in person.
Keep your contact details private. Don’t reveal your phone number, address, where you work, or other information that would enable a person to find you in person.
![]() Remember that some apps will connect with other accounts, such as Facebook, revealing people you’re friends with, interests, and other details. Consider creating a separate account for dating and chat.
Remember that some apps will connect with other accounts, such as Facebook, revealing people you’re friends with, interests, and other details. Consider creating a separate account for dating and chat.
![]() Be careful of opening any attachments in messages, as they could be malware.
Be careful of opening any attachments in messages, as they could be malware.
![]() Don’t access your accounts from public computers, or with public Wi-Fi hotspots. It’s possible that someone could acquire your username and password. Public computers and Wi-Fi could also be used to see what sites you’re visiting and what you’re doing, as you’d reveal your activity to anyone who might be monitoring the network or has a clear view of the computer screen.
Don’t access your accounts from public computers, or with public Wi-Fi hotspots. It’s possible that someone could acquire your username and password. Public computers and Wi-Fi could also be used to see what sites you’re visiting and what you’re doing, as you’d reveal your activity to anyone who might be monitoring the network or has a clear view of the computer screen.
Checking Whether a Person Is Who They Say They Are
Just because a site doesn’t do a background check on its users doesn’t mean you can’t. If you’re interacting with someone on a regular basis, through a dating site, or considering meeting the person, you should research them as much as possible. This not only includes any profile on the site you’re using, but other sources of information that may be related to the person. You can find a considerable amount of information on a person’s social media accounts, search engine results, and other resources.
There are also online offender registries, such as those that allow you to look up registered sex offenders in a particular area. These can be useful in determining the threat level of a person, and cost nothing but your time. If you’re meeting a person, you might also consider doing a criminal background check. While this may seem extreme, remember that dating services, apps, and sites don’t do these. Depending on what you find about a person’s background, you could be incredibly thankful that you took the time to check the person out.
Reviewing profiles
While we discussed creeping earlier, doing a little cyber-snooping can be useful in vetting a person. As you chat with a person online, you may find that they say things that are contradictory to what’s on the site’s profile, or other sites where they have an account. Someone may say they’re single on a chat site, but their Facebook profile may indicate otherwise. Similarly, they may say things to impress you or falsely create an emotional connection, but checking what they’ve said on other sites may indicate their lying or grooming you for something inappropriate or illegal.
Image search
A useful way of determining the validity of a person is doing an image search. If someone has sent you a photo of themselves, you can upload it into a search engine, where it’s compared to other photos found online. In using it, you may find the photo is a stock photo of some model, or on sites that are totally unrelated to who the person says they are. To do an image search on Google, do the following:
1. In your browser, to go https://images.google.com, and click the camera icon beside the search box.
2. If the photo you’re checking is online, paste the URL into the box in the Paste image URL tab, and click Search by image. If you have a copy of the photo, click on the Upload an image tab, and then click Browse. Navigate to the photo, select it, and then click Open.
Summary
In this chapter we’ve discussed some of the common practices and etiquette of interacting with people electronically, and the potential problems of communicating with others online. While most people you meet online will be genuinely nice people, there are those who can make things difficult and even dangerous. Now that we’ve looked at dealing with others, let’s move on to Chapter 10, Protecting your kids, to find how you can protect your kids and other family members.